98d3b0999a72497c1c657e97c25bc931.ppt
- Количество слайдов: 131
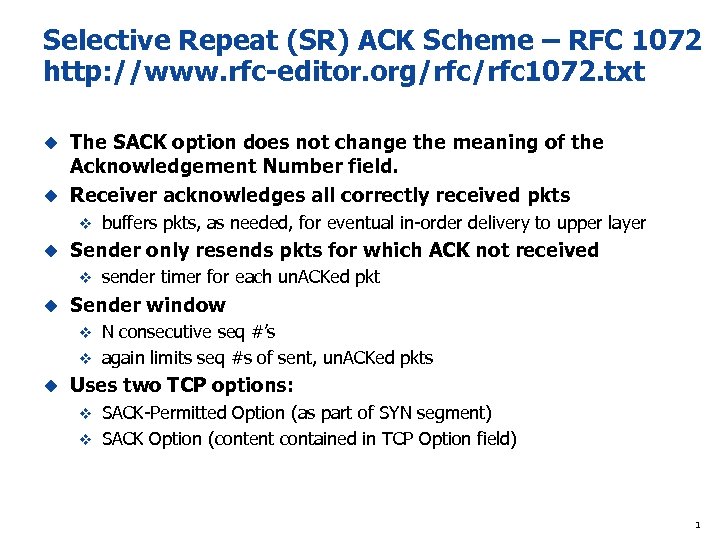 Selective Repeat (SR) ACK Scheme – RFC 1072 http: //www. rfc-editor. org/rfc 1072. txt The SACK option does not change the meaning of the Acknowledgement Number field. u Receiver acknowledges all correctly received pkts u v u Sender only resends pkts for which ACK not received v u buffers pkts, as needed, for eventual in-order delivery to upper layer sender timer for each un. ACKed pkt Sender window N consecutive seq #’s v again limits seq #s of sent, un. ACKed pkts v u Uses two TCP options: SACK-Permitted Option (as part of SYN segment) v SACK Option (content contained in TCP Option field) v 1
Selective Repeat (SR) ACK Scheme – RFC 1072 http: //www. rfc-editor. org/rfc 1072. txt The SACK option does not change the meaning of the Acknowledgement Number field. u Receiver acknowledges all correctly received pkts u v u Sender only resends pkts for which ACK not received v u buffers pkts, as needed, for eventual in-order delivery to upper layer sender timer for each un. ACKed pkt Sender window N consecutive seq #’s v again limits seq #s of sent, un. ACKed pkts v u Uses two TCP options: SACK-Permitted Option (as part of SYN segment) v SACK Option (content contained in TCP Option field) v 1
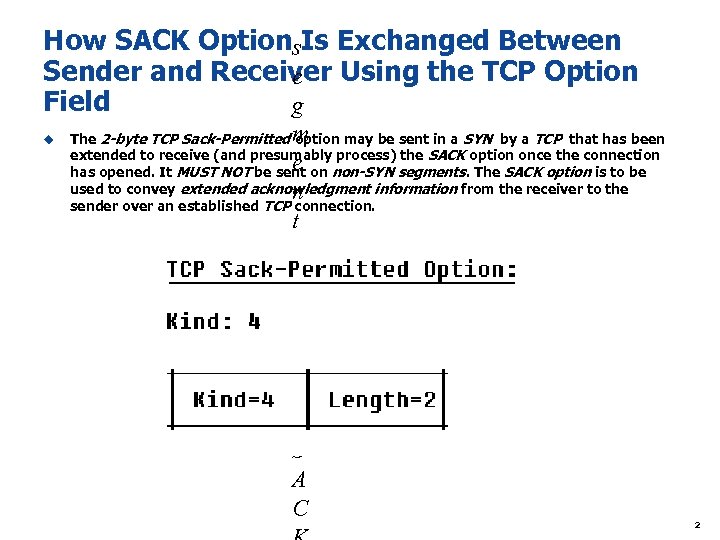 How SACK Option Is Exchanged Between s Sender and Receiver Using the TCP Option e Field g u m e n t s. T h e S A C The 2 -byte TCP Sack-Permitted option may be sent in a SYN by a TCP that has been extended to receive (and presumably process) the SACK option once the connection has opened. It MUST NOT be sent on non-SYN segments. The SACK option is to be used to convey extended acknowledgment information from the receiver to the sender over an established TCP connection. 2
How SACK Option Is Exchanged Between s Sender and Receiver Using the TCP Option e Field g u m e n t s. T h e S A C The 2 -byte TCP Sack-Permitted option may be sent in a SYN by a TCP that has been extended to receive (and presumably process) the SACK option once the connection has opened. It MUST NOT be sent on non-SYN segments. The SACK option is to be used to convey extended acknowledgment information from the receiver to the sender over an established TCP connection. 2
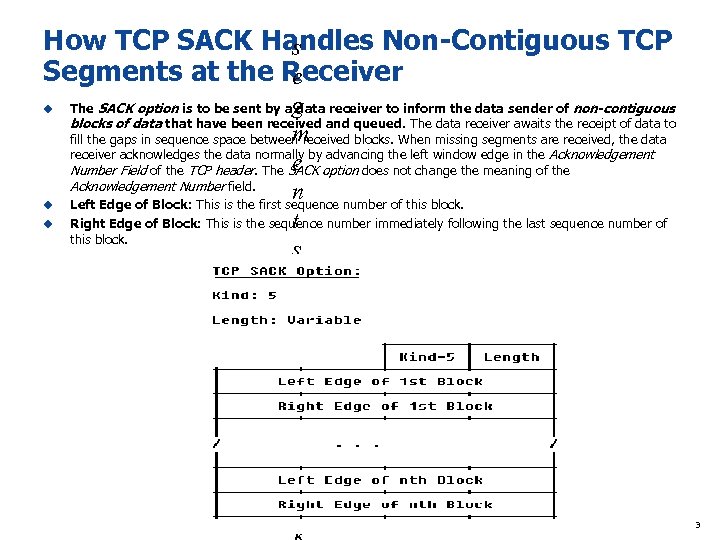 How TCP SACK Handles Non-Contiguous TCP s Segments at the Receiver e u u u g m e n t s. T h e S A C The SACK option is to be sent by a data receiver to inform the data sender of non-contiguous blocks of data that have been received and queued. The data receiver awaits the receipt of data to fill the gaps in sequence space between received blocks. When missing segments are received, the data receiver acknowledges the data normally by advancing the left window edge in the Acknowledgement Number Field of the TCP header. The SACK option does not change the meaning of the Acknowledgement Number field. Left Edge of Block: This is the first sequence number of this block. Right Edge of Block: This is the sequence number immediately following the last sequence number of this block. 3
How TCP SACK Handles Non-Contiguous TCP s Segments at the Receiver e u u u g m e n t s. T h e S A C The SACK option is to be sent by a data receiver to inform the data sender of non-contiguous blocks of data that have been received and queued. The data receiver awaits the receipt of data to fill the gaps in sequence space between received blocks. When missing segments are received, the data receiver acknowledges the data normally by advancing the left window edge in the Acknowledgement Number Field of the TCP header. The SACK option does not change the meaning of the Acknowledgement Number field. Left Edge of Block: This is the first sequence number of this block. Right Edge of Block: This is the sequence number immediately following the last sequence number of this block. 3
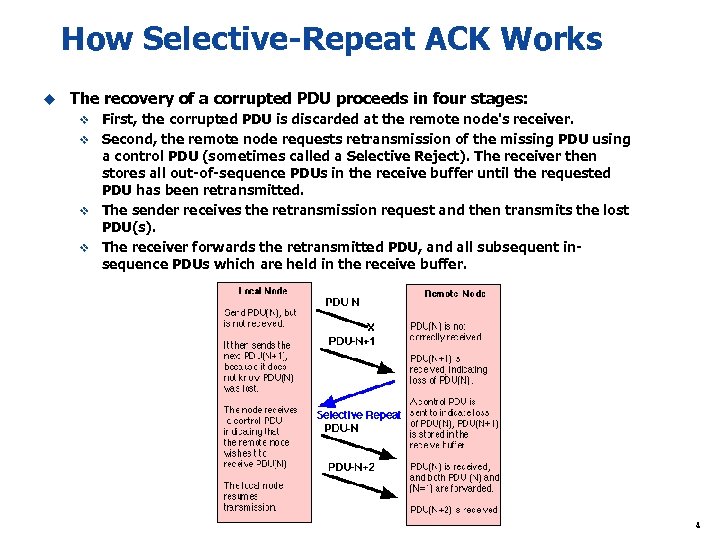 How Selective-Repeat ACK Works u The recovery of a corrupted PDU proceeds in four stages: First, the corrupted PDU is discarded at the remote node's receiver. v Second, the remote node requests retransmission of the missing PDU using a control PDU (sometimes called a Selective Reject). The receiver then stores all out-of-sequence PDUs in the receive buffer until the requested PDU has been retransmitted. v The sender receives the retransmission request and then transmits the lost PDU(s). v The receiver forwards the retransmitted PDU, and all subsequent insequence PDUs which are held in the receive buffer. v 4
How Selective-Repeat ACK Works u The recovery of a corrupted PDU proceeds in four stages: First, the corrupted PDU is discarded at the remote node's receiver. v Second, the remote node requests retransmission of the missing PDU using a control PDU (sometimes called a Selective Reject). The receiver then stores all out-of-sequence PDUs in the receive buffer until the requested PDU has been retransmitted. v The sender receives the retransmission request and then transmits the lost PDU(s). v The receiver forwards the retransmitted PDU, and all subsequent insequence PDUs which are held in the receive buffer. v 4
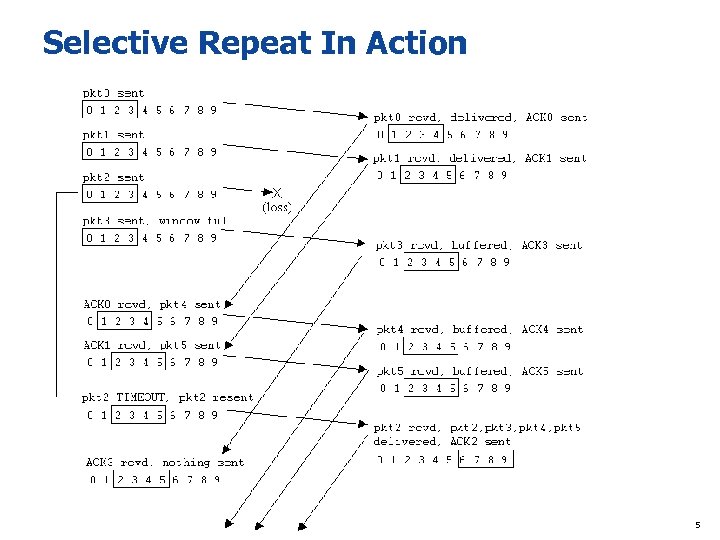 Selective Repeat In Action 5
Selective Repeat In Action 5
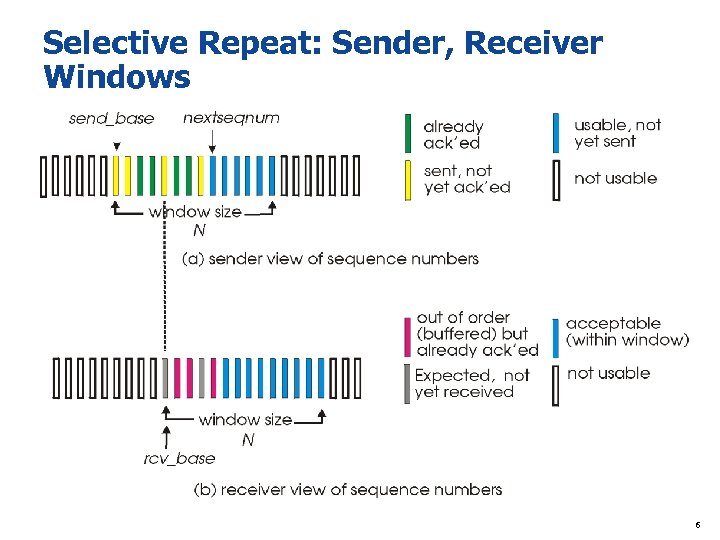 Selective Repeat: Sender, Receiver Windows 6
Selective Repeat: Sender, Receiver Windows 6
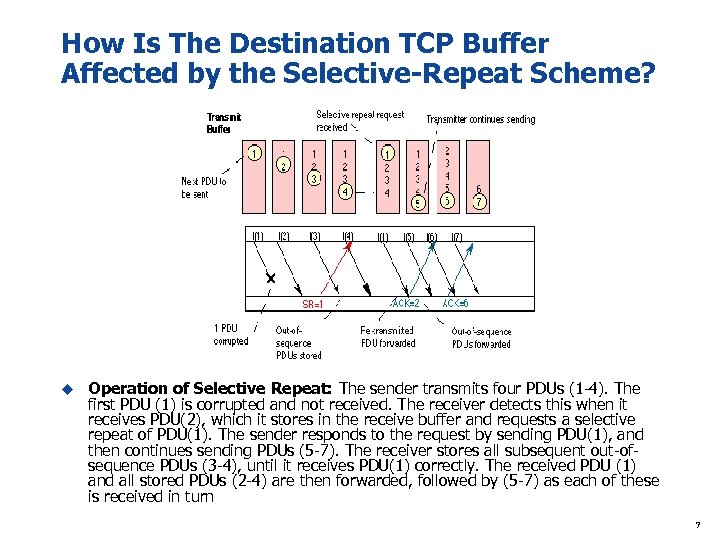 How Is The Destination TCP Buffer Affected by the Selective-Repeat Scheme? u Operation of Selective Repeat: The sender transmits four PDUs (1 -4). The first PDU (1) is corrupted and not received. The receiver detects this when it receives PDU(2), which it stores in the receive buffer and requests a selective repeat of PDU(1). The sender responds to the request by sending PDU(1), and then continues sending PDUs (5 -7). The receiver stores all subsequent out-ofsequence PDUs (3 -4), until it receives PDU(1) correctly. The received PDU (1) and all stored PDUs (2 -4) are then forwarded, followed by (5 -7) as each of these is received in turn 7
How Is The Destination TCP Buffer Affected by the Selective-Repeat Scheme? u Operation of Selective Repeat: The sender transmits four PDUs (1 -4). The first PDU (1) is corrupted and not received. The receiver detects this when it receives PDU(2), which it stores in the receive buffer and requests a selective repeat of PDU(1). The sender responds to the request by sending PDU(1), and then continues sending PDUs (5 -7). The receiver stores all subsequent out-ofsequence PDUs (3 -4), until it receives PDU(1) correctly. The received PDU (1) and all stored PDUs (2 -4) are then forwarded, followed by (5 -7) as each of these is received in turn 7
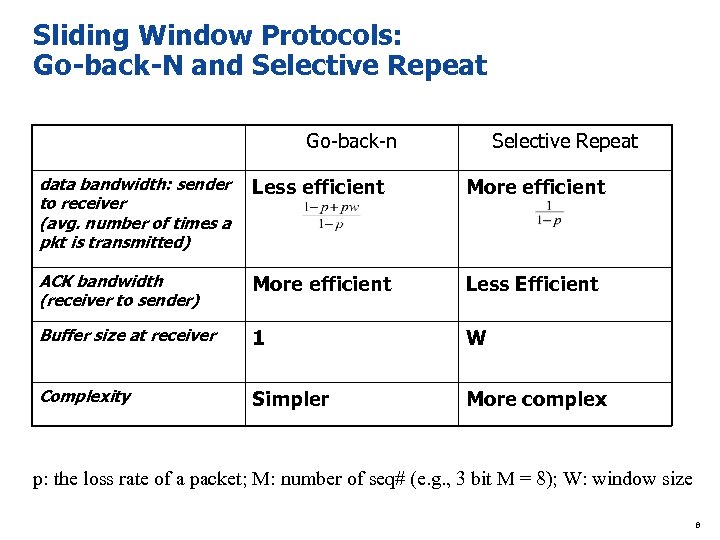 Sliding Window Protocols: Go-back-N and Selective Repeat Go-back-n Selective Repeat data bandwidth: sender to receiver (avg. number of times a pkt is transmitted) Less efficient More efficient ACK bandwidth (receiver to sender) More efficient Less Efficient Buffer size at receiver 1 W Complexity Simpler More complex p: the loss rate of a packet; M: number of seq# (e. g. , 3 bit M = 8); W: window size 8
Sliding Window Protocols: Go-back-N and Selective Repeat Go-back-n Selective Repeat data bandwidth: sender to receiver (avg. number of times a pkt is transmitted) Less efficient More efficient ACK bandwidth (receiver to sender) More efficient Less Efficient Buffer size at receiver 1 W Complexity Simpler More complex p: the loss rate of a packet; M: number of seq# (e. g. , 3 bit M = 8); W: window size 8
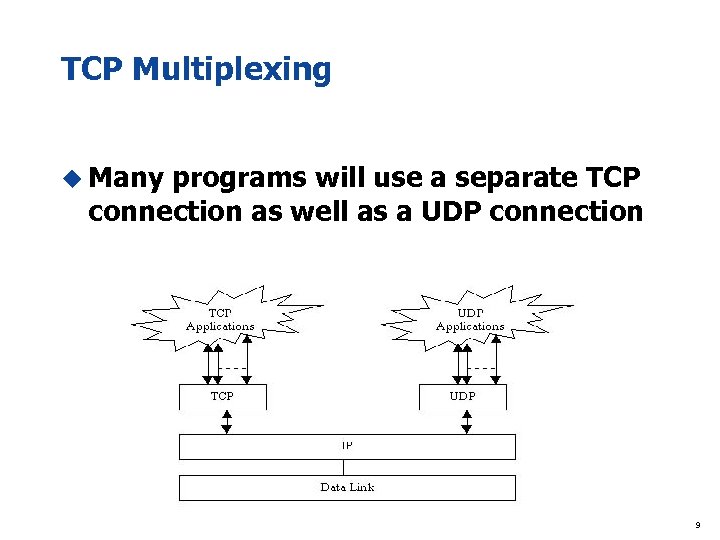 TCP Multiplexing u Many programs will use a separate TCP connection as well as a UDP connection 9
TCP Multiplexing u Many programs will use a separate TCP connection as well as a UDP connection 9
 TCP Multiplexing u By specifying ports and including port numbers with TCP/UDP data, multiplexing is achieved u Multiplexing allows multiple network connections to take place simultaneously u The port numbers, along with the source and destination addresses for the data, determine a socket 10
TCP Multiplexing u By specifying ports and including port numbers with TCP/UDP data, multiplexing is achieved u Multiplexing allows multiple network connections to take place simultaneously u The port numbers, along with the source and destination addresses for the data, determine a socket 10
 11
11
 Advanced Topic MPLS Switching/Routing 12
Advanced Topic MPLS Switching/Routing 12
 Concept of Traffic Engineering (TE) u Concerns with the performance optimization of operational networks u This concern was due to the fact that IGP routing always selects least-cost path from source to destination that can lead to overutilized and under-utilized links u Need a tool that allows us to “steer” traffic so that can lead to more balanced flow of traffic across links based v MPLS 13
Concept of Traffic Engineering (TE) u Concerns with the performance optimization of operational networks u This concern was due to the fact that IGP routing always selects least-cost path from source to destination that can lead to overutilized and under-utilized links u Need a tool that allows us to “steer” traffic so that can lead to more balanced flow of traffic across links based v MPLS 13
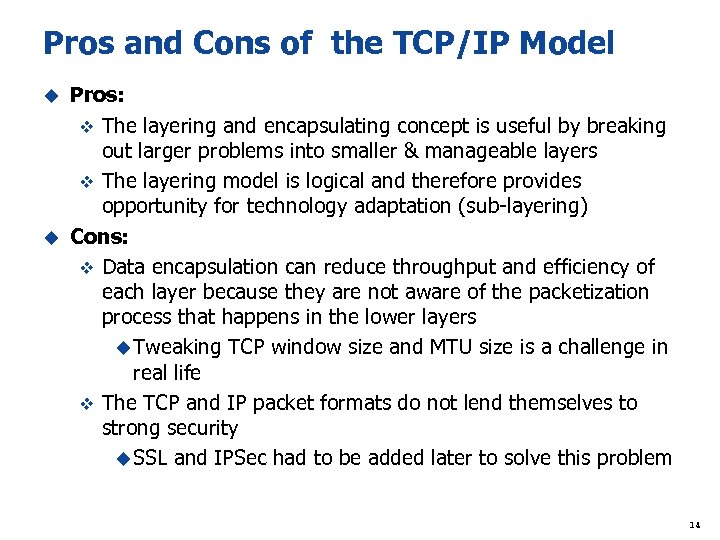 Pros and Cons of the TCP/IP Model Pros: v The layering and encapsulating concept is useful by breaking out larger problems into smaller & manageable layers v The layering model is logical and therefore provides opportunity for technology adaptation (sub-layering) u Cons: v Data encapsulation can reduce throughput and efficiency of each layer because they are not aware of the packetization process that happens in the lower layers u Tweaking TCP window size and MTU size is a challenge in real life v The TCP and IP packet formats do not lend themselves to strong security u SSL and IPSec had to be added later to solve this problem u 14
Pros and Cons of the TCP/IP Model Pros: v The layering and encapsulating concept is useful by breaking out larger problems into smaller & manageable layers v The layering model is logical and therefore provides opportunity for technology adaptation (sub-layering) u Cons: v Data encapsulation can reduce throughput and efficiency of each layer because they are not aware of the packetization process that happens in the lower layers u Tweaking TCP window size and MTU size is a challenge in real life v The TCP and IP packet formats do not lend themselves to strong security u SSL and IPSec had to be added later to solve this problem u 14
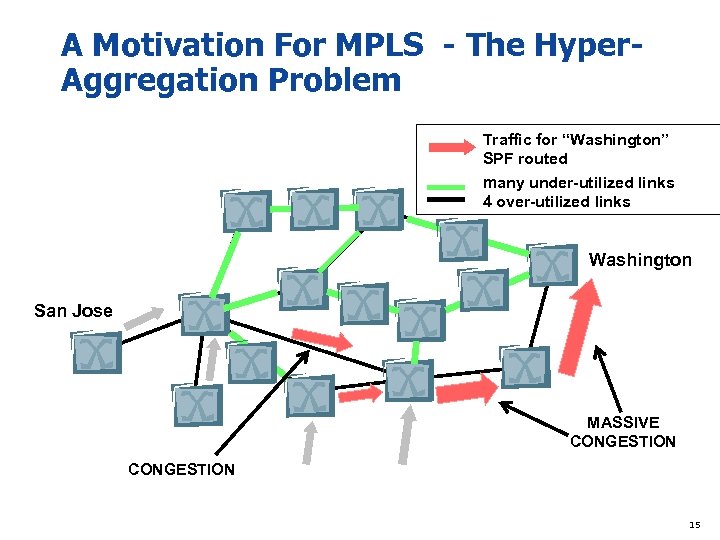 A Motivation For MPLS - The Hyper. Aggregation Problem Traffic for “Washington” SPF routed many under-utilized links 4 over-utilized links Washington San Jose MASSIVE CONGESTION 15
A Motivation For MPLS - The Hyper. Aggregation Problem Traffic for “Washington” SPF routed many under-utilized links 4 over-utilized links Washington San Jose MASSIVE CONGESTION 15
 How Is MPLS Used? u One of the primary original goals of MPLS, boosting the performance of software-based IP routers, has been superseded as advances in silicon technology have enabled line-rate routing performance implemented in router hardware. u In the meantime, additional benefits of MPLS have been realized, notably VPN services (layer 2 or layer 3) and traffic engineering. 16
How Is MPLS Used? u One of the primary original goals of MPLS, boosting the performance of software-based IP routers, has been superseded as advances in silicon technology have enabled line-rate routing performance implemented in router hardware. u In the meantime, additional benefits of MPLS have been realized, notably VPN services (layer 2 or layer 3) and traffic engineering. 16
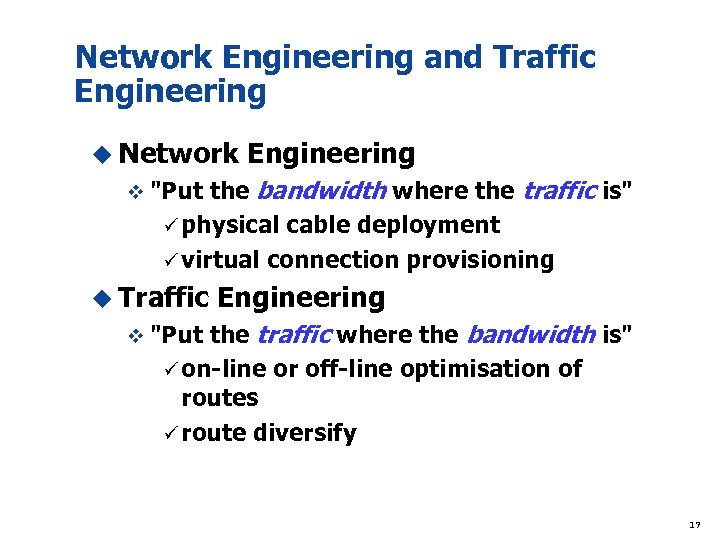 Network Engineering and Traffic Engineering u Network Engineering v "Put the bandwidth where the traffic is" ü physical cable deployment ü virtual connection provisioning u Traffic Engineering v "Put the traffic where the bandwidth is" ü on-line or off-line optimisation of routes ü route diversify 17
Network Engineering and Traffic Engineering u Network Engineering v "Put the bandwidth where the traffic is" ü physical cable deployment ü virtual connection provisioning u Traffic Engineering v "Put the traffic where the bandwidth is" ü on-line or off-line optimisation of routes ü route diversify 17
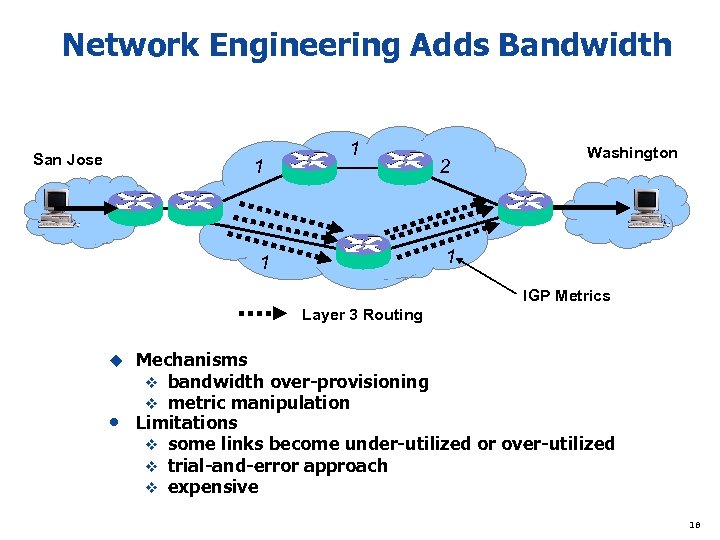 Network Engineering Adds Bandwidth San Jose 1 1 2 Washington 1 1 IGP Metrics Layer 3 Routing u • Mechanisms v bandwidth over-provisioning v metric manipulation Limitations v some links become under-utilized or over-utilized v trial-and-error approach v expensive 18
Network Engineering Adds Bandwidth San Jose 1 1 2 Washington 1 1 IGP Metrics Layer 3 Routing u • Mechanisms v bandwidth over-provisioning v metric manipulation Limitations v some links become under-utilized or over-utilized v trial-and-error approach v expensive 18
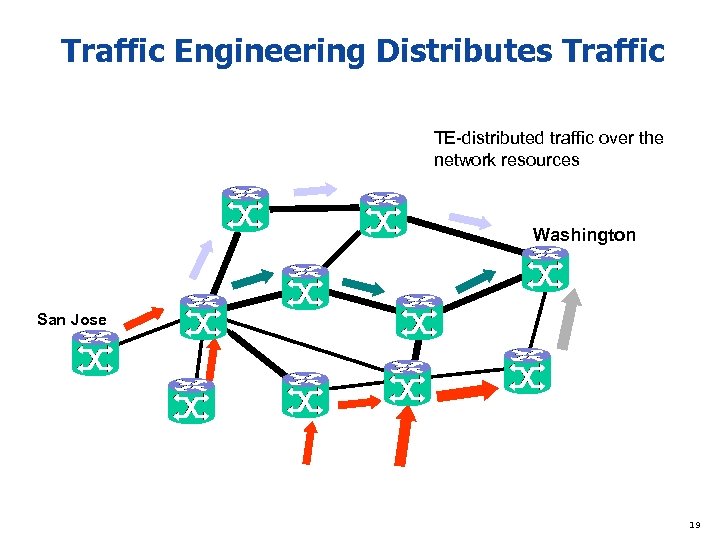 Traffic Engineering Distributes Traffic TE-distributed traffic over the network resources Washington San Jose 19
Traffic Engineering Distributes Traffic TE-distributed traffic over the network resources Washington San Jose 19
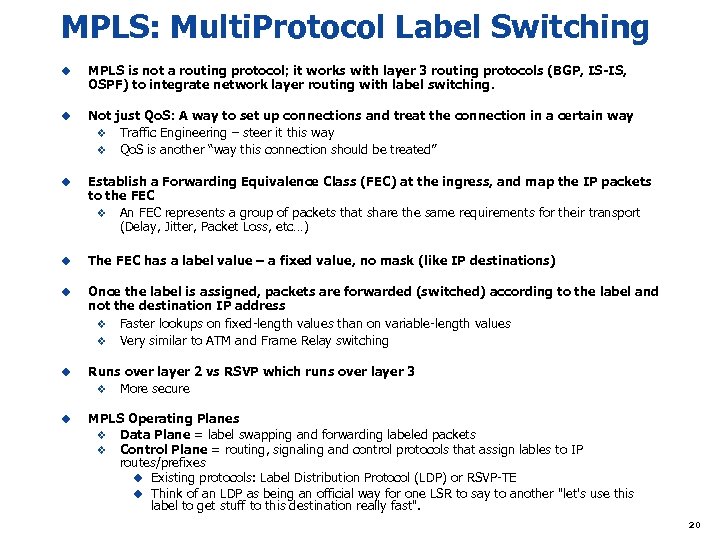 MPLS: Multi. Protocol Label Switching u MPLS is not a routing protocol; it works with layer 3 routing protocols (BGP, IS-IS, OSPF) to integrate network layer routing with label switching. u Not just Qo. S: A way to set up connections and treat the connection in a certain way v Traffic Engineering – steer it this way v Qo. S is another “way this connection should be treated” u Establish a Forwarding Equivalence Class (FEC) at the ingress, and map the IP packets to the FEC v An FEC represents a group of packets that share the same requirements for their transport (Delay, Jitter, Packet Loss, etc…) u The FEC has a label value – a fixed value, no mask (like IP destinations) u Once the label is assigned, packets are forwarded (switched) according to the label and not the destination IP address v Faster lookups on fixed-length values than on variable-length values v Very similar to ATM and Frame Relay switching u Runs over layer 2 vs RSVP which runs over layer 3 v More secure u MPLS Operating Planes v Data Plane = label swapping and forwarding labeled packets v Control Plane = routing, signaling and control protocols that assign lables to IP routes/prefixes u Existing protocols: Label Distribution Protocol (LDP) or RSVP-TE u Think of an LDP as being an official way for one LSR to say to another "let's use this label to get stuff to this destination really fast". 20
MPLS: Multi. Protocol Label Switching u MPLS is not a routing protocol; it works with layer 3 routing protocols (BGP, IS-IS, OSPF) to integrate network layer routing with label switching. u Not just Qo. S: A way to set up connections and treat the connection in a certain way v Traffic Engineering – steer it this way v Qo. S is another “way this connection should be treated” u Establish a Forwarding Equivalence Class (FEC) at the ingress, and map the IP packets to the FEC v An FEC represents a group of packets that share the same requirements for their transport (Delay, Jitter, Packet Loss, etc…) u The FEC has a label value – a fixed value, no mask (like IP destinations) u Once the label is assigned, packets are forwarded (switched) according to the label and not the destination IP address v Faster lookups on fixed-length values than on variable-length values v Very similar to ATM and Frame Relay switching u Runs over layer 2 vs RSVP which runs over layer 3 v More secure u MPLS Operating Planes v Data Plane = label swapping and forwarding labeled packets v Control Plane = routing, signaling and control protocols that assign lables to IP routes/prefixes u Existing protocols: Label Distribution Protocol (LDP) or RSVP-TE u Think of an LDP as being an official way for one LSR to say to another "let's use this label to get stuff to this destination really fast". 20
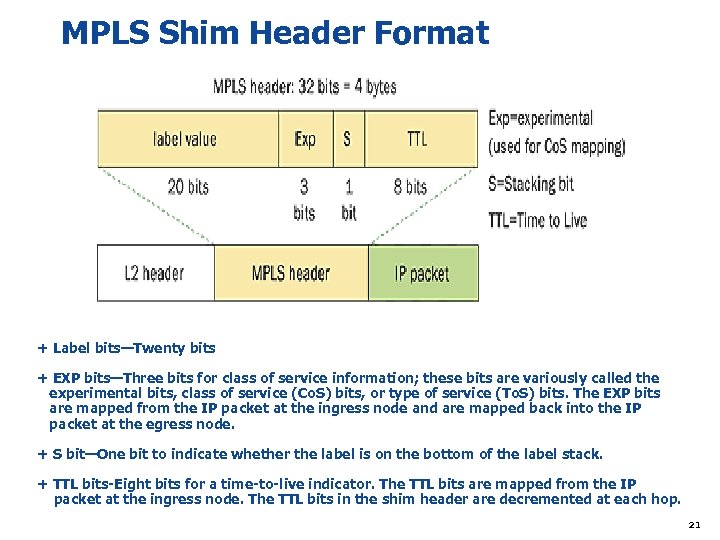 MPLS Shim Header Format + Label bits—Twenty bits + EXP bits—Three bits for class of service information; these bits are variously called the experimental bits, class of service (Co. S) bits, or type of service (To. S) bits. The EXP bits are mapped from the IP packet at the ingress node and are mapped back into the IP packet at the egress node. + S bit—One bit to indicate whether the label is on the bottom of the label stack. + TTL bits-Eight bits for a time-to-live indicator. The TTL bits are mapped from the IP packet at the ingress node. The TTL bits in the shim header are decremented at each hop. 21
MPLS Shim Header Format + Label bits—Twenty bits + EXP bits—Three bits for class of service information; these bits are variously called the experimental bits, class of service (Co. S) bits, or type of service (To. S) bits. The EXP bits are mapped from the IP packet at the ingress node and are mapped back into the IP packet at the egress node. + S bit—One bit to indicate whether the label is on the bottom of the label stack. + TTL bits-Eight bits for a time-to-live indicator. The TTL bits are mapped from the IP packet at the ingress node. The TTL bits in the shim header are decremented at each hop. 21
 Data Flow In An MPLS Network 22
Data Flow In An MPLS Network 22
 MPLS Architecture u As packets enter the MPLS network, they are mapped to labels based on their destination IP addresses u Routers that run MPLS are known as Label Switching Routers (LSRs) u The MLPS connection is called a Label. Switched Path (LSP) u All packets going to a single destination with similar characteristics (e. g. , Qo. S) belong to the same Forwarding Equivalence Class (FEC) 23
MPLS Architecture u As packets enter the MPLS network, they are mapped to labels based on their destination IP addresses u Routers that run MPLS are known as Label Switching Routers (LSRs) u The MLPS connection is called a Label. Switched Path (LSP) u All packets going to a single destination with similar characteristics (e. g. , Qo. S) belong to the same Forwarding Equivalence Class (FEC) 23
 Forward Equivalent Class (FEC) – What it means u A Forwarding Equivalence Class (FEC) is a class of packets that should be forwarded in the same manner (i. e. over the same path). u A FEC is not a packet, nor is it a label. A FEC is a logical entity created by the router to represent a class (category) of packets. When a packet arrives at the ingress router of an MPLS domain, the router parses the packet's headers, and checks to see if the packet matches a known FEC (class). Once the matching FEC is determined, the path and outgoing label assigned to that FEC are used to forward the packet. u FECs are typically created based on the IP destinations known to the router, so for each different destination a router might create a different FEC, or if a router is doing aggregation, it might represent multiple destinations with a single FEC (for example, if those destinations are reachable through the same immediate next hop anyway). The MPLS framework, however, allows for the creation of FECs using advanced criteria like source and destination address pairs, destination address and TOS, etc. 24
Forward Equivalent Class (FEC) – What it means u A Forwarding Equivalence Class (FEC) is a class of packets that should be forwarded in the same manner (i. e. over the same path). u A FEC is not a packet, nor is it a label. A FEC is a logical entity created by the router to represent a class (category) of packets. When a packet arrives at the ingress router of an MPLS domain, the router parses the packet's headers, and checks to see if the packet matches a known FEC (class). Once the matching FEC is determined, the path and outgoing label assigned to that FEC are used to forward the packet. u FECs are typically created based on the IP destinations known to the router, so for each different destination a router might create a different FEC, or if a router is doing aggregation, it might represent multiple destinations with a single FEC (for example, if those destinations are reachable through the same immediate next hop anyway). The MPLS framework, however, allows for the creation of FECs using advanced criteria like source and destination address pairs, destination address and TOS, etc. 24
 Forwarding Equivalence Class (FEC) u Introduced in MPLS standards to denote packet forwarding classes u Comprises traffic v to a particular destination v to destination with distinct service requirements u Why FEC? v To precisely specify which IP packets are mapped to each LSP v Done by providing a FEC specification for each LSP 25
Forwarding Equivalence Class (FEC) u Introduced in MPLS standards to denote packet forwarding classes u Comprises traffic v to a particular destination v to destination with distinct service requirements u Why FEC? v To precisely specify which IP packets are mapped to each LSP v Done by providing a FEC specification for each LSP 25
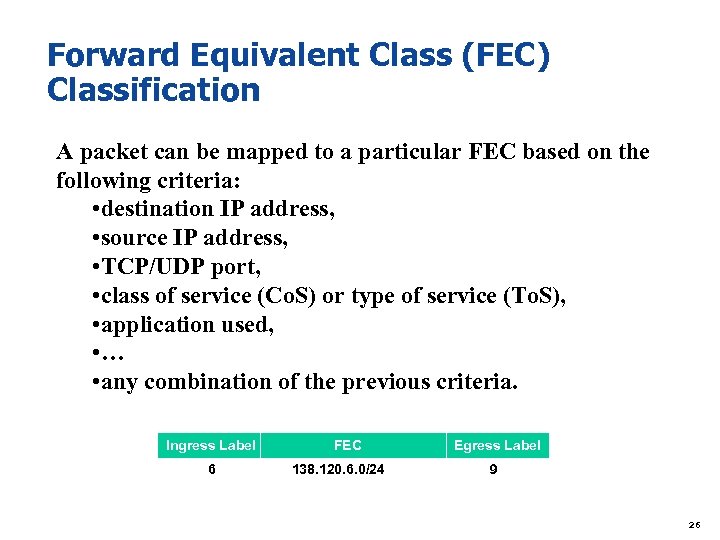 Forward Equivalent Class (FEC) Classification A packet can be mapped to a particular FEC based on the following criteria: • destination IP address, • source IP address, • TCP/UDP port, • class of service (Co. S) or type of service (To. S), • application used, • … • any combination of the previous criteria. Ingress Label 6 FEC 138. 120. 6. 0/24 Egress Label 9 26
Forward Equivalent Class (FEC) Classification A packet can be mapped to a particular FEC based on the following criteria: • destination IP address, • source IP address, • TCP/UDP port, • class of service (Co. S) or type of service (To. S), • application used, • … • any combination of the previous criteria. Ingress Label 6 FEC 138. 120. 6. 0/24 Egress Label 9 26
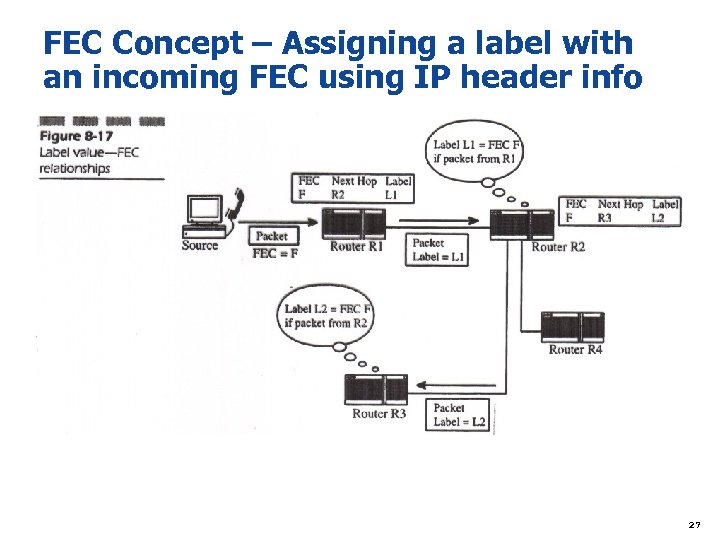 FEC Concept – Assigning a label with an incoming FEC using IP header info 27
FEC Concept – Assigning a label with an incoming FEC using IP header info 27
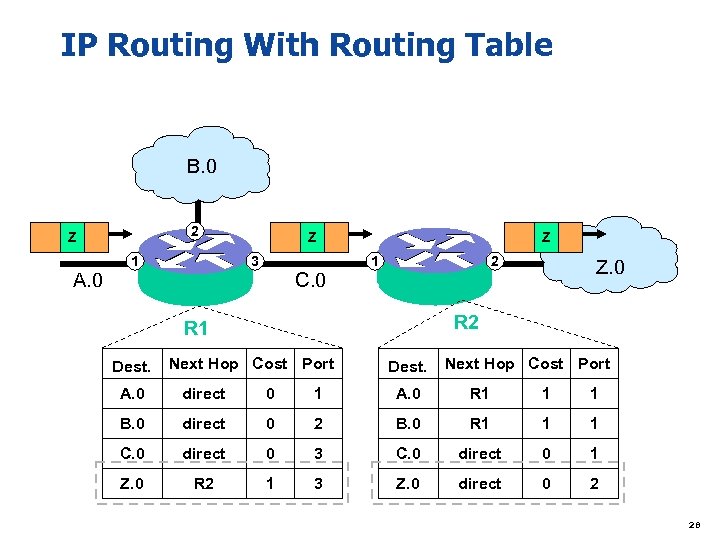 IP Routing With Routing Table B. 0 2 Z A. 0 1 Z 3 C. 0 Z 1 2 R 1 Dest. Z. 0 Next Hop Cost Port Dest. Next Hop Cost Port A. 0 direct 0 1 A. 0 R 1 1 1 B. 0 direct 0 2 B. 0 R 1 1 1 C. 0 direct 0 3 C. 0 direct 0 1 Z. 0 R 2 1 3 Z. 0 direct 0 2 28
IP Routing With Routing Table B. 0 2 Z A. 0 1 Z 3 C. 0 Z 1 2 R 1 Dest. Z. 0 Next Hop Cost Port Dest. Next Hop Cost Port A. 0 direct 0 1 A. 0 R 1 1 1 B. 0 direct 0 2 B. 0 R 1 1 1 C. 0 direct 0 3 C. 0 direct 0 1 Z. 0 R 2 1 3 Z. 0 direct 0 2 28
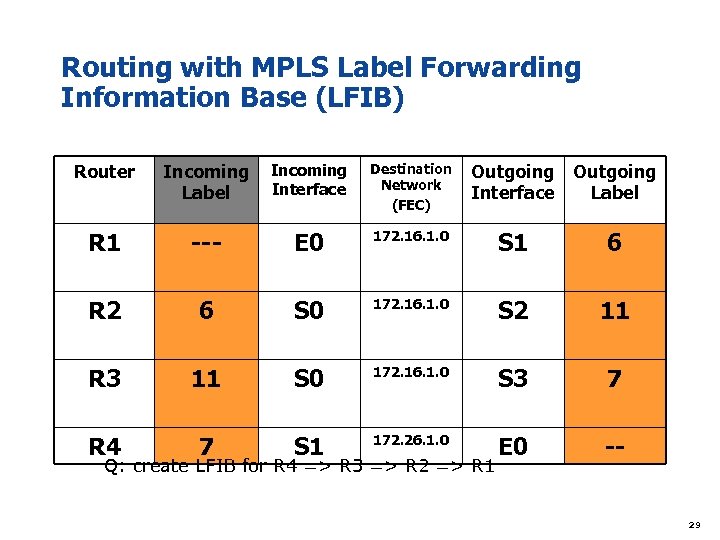 Routing with MPLS Label Forwarding Information Base (LFIB) Router Incoming Interface Label Destination Network (FEC) Outgoing Interface Label R 1 --- E 0 172. 16. 1. 0 S 1 6 R 2 6 S 0 172. 16. 1. 0 S 2 11 R 3 11 S 0 172. 16. 1. 0 S 3 7 R 4 7 S 1 172. 26. 1. 0 E 0 -- Q: create LFIB for R 4 => R 3 => R 2 => R 1 29
Routing with MPLS Label Forwarding Information Base (LFIB) Router Incoming Interface Label Destination Network (FEC) Outgoing Interface Label R 1 --- E 0 172. 16. 1. 0 S 1 6 R 2 6 S 0 172. 16. 1. 0 S 2 11 R 3 11 S 0 172. 16. 1. 0 S 3 7 R 4 7 S 1 172. 26. 1. 0 E 0 -- Q: create LFIB for R 4 => R 3 => R 2 => R 1 29
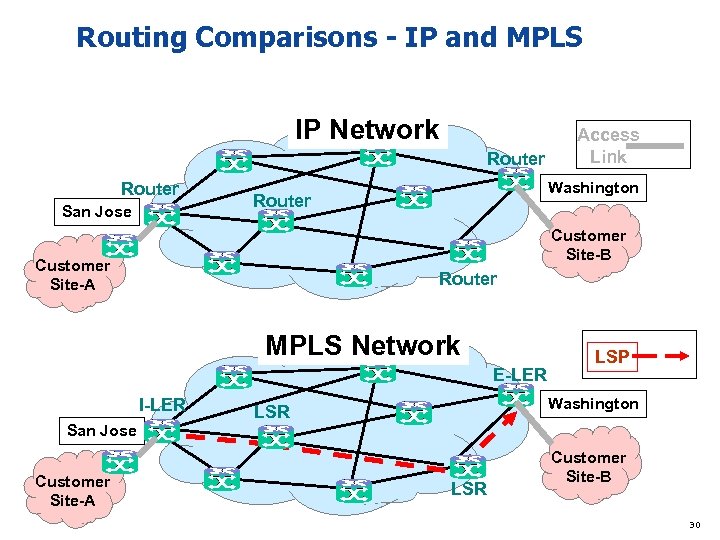 Routing Comparisons - IP and MPLS IP Network Router San Jose Access Link Washington Router Customer Site-B Customer Site-A Router MPLS Network E-LER I-LER LSP Washington LSR San Jose Customer Site-A LSR Customer Site-B 30
Routing Comparisons - IP and MPLS IP Network Router San Jose Access Link Washington Router Customer Site-B Customer Site-A Router MPLS Network E-LER I-LER LSP Washington LSR San Jose Customer Site-A LSR Customer Site-B 30
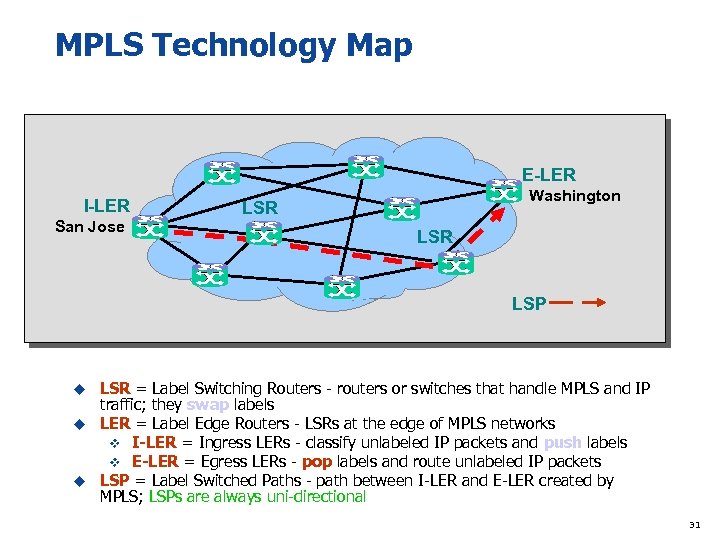 MPLS Technology Map E-LER I-LER San Jose Washington LSR LSP LSR = Label Switching Routers - routers or switches that handle MPLS and IP traffic; they swap labels u LER = Label Edge Routers - LSRs at the edge of MPLS networks v I-LER = Ingress LERs - classify unlabeled IP packets and push labels v E-LER = Egress LERs - pop labels and route unlabeled IP packets u LSP = Label Switched Paths - path between I-LER and E-LER created by MPLS; LSPs are always uni-directional u 31
MPLS Technology Map E-LER I-LER San Jose Washington LSR LSP LSR = Label Switching Routers - routers or switches that handle MPLS and IP traffic; they swap labels u LER = Label Edge Routers - LSRs at the edge of MPLS networks v I-LER = Ingress LERs - classify unlabeled IP packets and push labels v E-LER = Egress LERs - pop labels and route unlabeled IP packets u LSP = Label Switched Paths - path between I-LER and E-LER created by MPLS; LSPs are always uni-directional u 31
 Actions at LERs and LSRs u Ingress @ I-LER v u PUSH the label: assign the traffic to an LSP or “get on” the LSP here Transit @ LSRs SWAP the label: switch the packet according to label info v Exact-match versus longest-match v u Egress @ E-LER v u POP the label at the end of the LSP, strip the label Penultimate Hop Popping “Cheat”: strip the label at the second-to-last router v This is done by the E-LSR send a label value of 3 to the penultimate Router v Helps offload the processing done by the E-LER v 32
Actions at LERs and LSRs u Ingress @ I-LER v u PUSH the label: assign the traffic to an LSP or “get on” the LSP here Transit @ LSRs SWAP the label: switch the packet according to label info v Exact-match versus longest-match v u Egress @ E-LER v u POP the label at the end of the LSP, strip the label Penultimate Hop Popping “Cheat”: strip the label at the second-to-last router v This is done by the E-LSR send a label value of 3 to the penultimate Router v Helps offload the processing done by the E-LER v 32
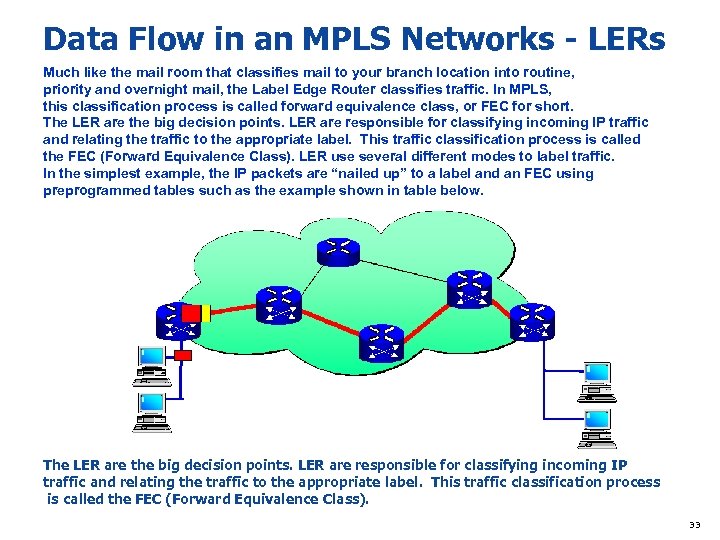 Data Flow in an MPLS Networks - LERs Much like the mail room that classifies mail to your branch location into routine, priority and overnight mail, the Label Edge Router classifies traffic. In MPLS, this classification process is called forward equivalence class, or FEC for short. The LER are the big decision points. LER are responsible for classifying incoming IP traffic and relating the traffic to the appropriate label. This traffic classification process is called the FEC (Forward Equivalence Class). LER use several different modes to label traffic. In the simplest example, the IP packets are “nailed up” to a label and an FEC using preprogrammed tables such as the example shown in table below. The LER are the big decision points. LER are responsible for classifying incoming IP traffic and relating the traffic to the appropriate label. This traffic classification process is called the FEC (Forward Equivalence Class). 33
Data Flow in an MPLS Networks - LERs Much like the mail room that classifies mail to your branch location into routine, priority and overnight mail, the Label Edge Router classifies traffic. In MPLS, this classification process is called forward equivalence class, or FEC for short. The LER are the big decision points. LER are responsible for classifying incoming IP traffic and relating the traffic to the appropriate label. This traffic classification process is called the FEC (Forward Equivalence Class). LER use several different modes to label traffic. In the simplest example, the IP packets are “nailed up” to a label and an FEC using preprogrammed tables such as the example shown in table below. The LER are the big decision points. LER are responsible for classifying incoming IP traffic and relating the traffic to the appropriate label. This traffic classification process is called the FEC (Forward Equivalence Class). 33
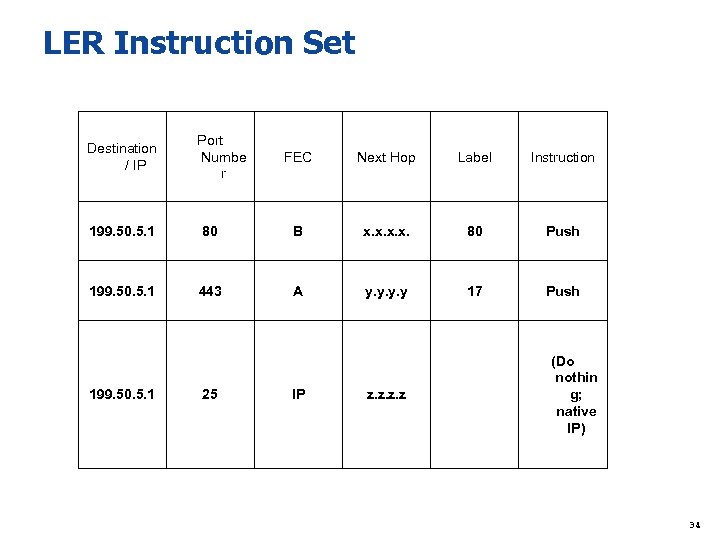 LER Instruction Set Destination / IP Port Numbe r FEC Next Hop Label Instruction 199. 50. 5. 1 80 B x. x. 80 Push 199. 50. 5. 1 443 A y. y 17 Push 199. 50. 5. 1 25 IP z. z (Do nothin g; native IP) 34
LER Instruction Set Destination / IP Port Numbe r FEC Next Hop Label Instruction 199. 50. 5. 1 80 B x. x. 80 Push 199. 50. 5. 1 443 A y. y 17 Push 199. 50. 5. 1 25 IP z. z (Do nothin g; native IP) 34
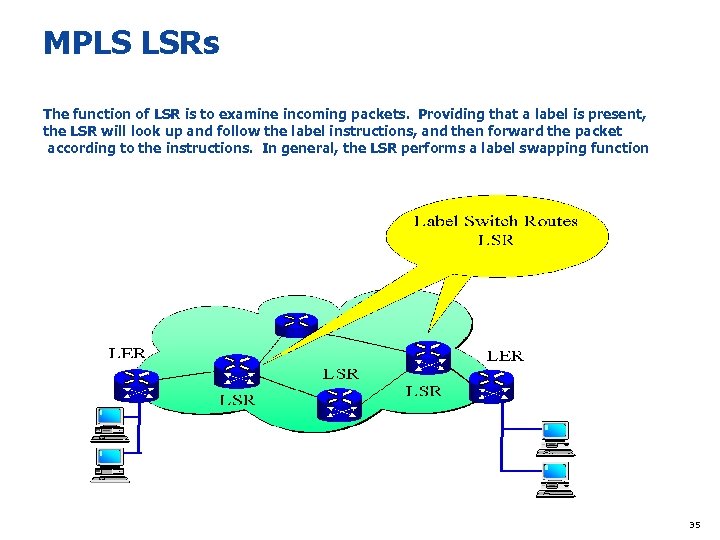 MPLS LSRs The function of LSR is to examine incoming packets. Providing that a label is present, the LSR will look up and follow the label instructions, and then forward the packet according to the instructions. In general, the LSR performs a label swapping function 35
MPLS LSRs The function of LSR is to examine incoming packets. Providing that a label is present, the LSR will look up and follow the label instructions, and then forward the packet according to the instructions. In general, the LSR performs a label swapping function 35
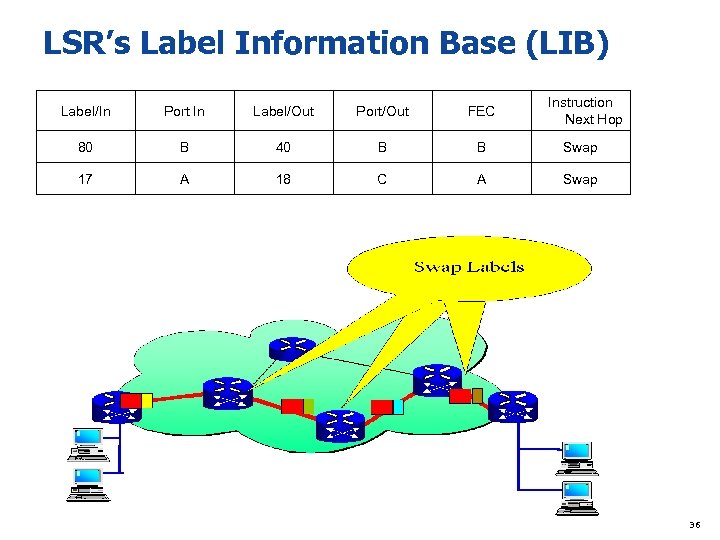 LSR’s Label Information Base (LIB) Instruction Next Hop Label/In Port In Label/Out Port/Out FEC 80 B 40 B B Swap 17 A 18 C A Swap 36
LSR’s Label Information Base (LIB) Instruction Next Hop Label/In Port In Label/Out Port/Out FEC 80 B 40 B B Swap 17 A 18 C A Swap 36
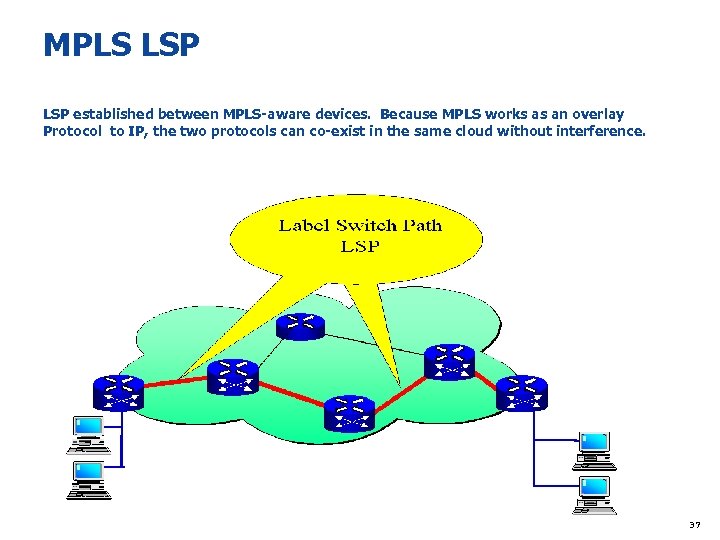 MPLS LSP established between MPLS-aware devices. Because MPLS works as an overlay Protocol to IP, the two protocols can co-exist in the same cloud without interference. 37
MPLS LSP established between MPLS-aware devices. Because MPLS works as an overlay Protocol to IP, the two protocols can co-exist in the same cloud without interference. 37
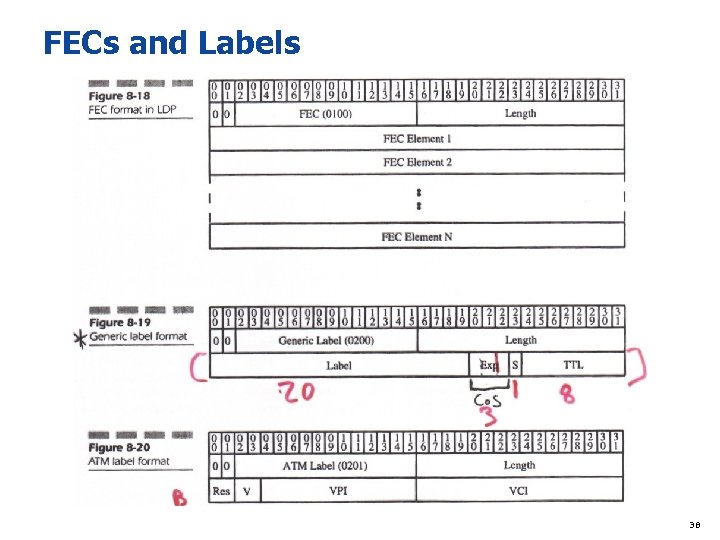 FECs and Labels 38
FECs and Labels 38
 Label Assignment and Distribution u Labels are locally significant; can be switched at each leg of the connection u Downstream router assigns label to upstream router u Header and label formats: Figure 8 -19 v Header is 32 bits, including 20 bits of label, 3 bits of Co. S u Protocols to distribute labels between routers: RSVP and LDP u Multiple labels in a Label Stack 39
Label Assignment and Distribution u Labels are locally significant; can be switched at each leg of the connection u Downstream router assigns label to upstream router u Header and label formats: Figure 8 -19 v Header is 32 bits, including 20 bits of label, 3 bits of Co. S u Protocols to distribute labels between routers: RSVP and LDP u Multiple labels in a Label Stack 39
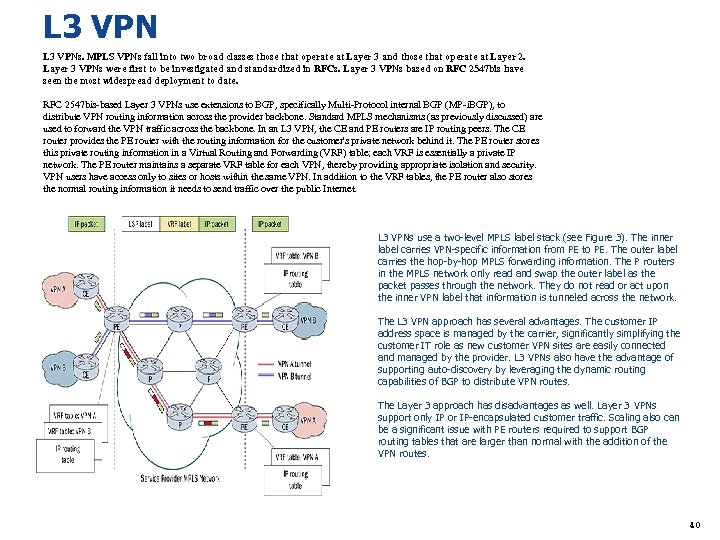 L 3 VPNs. MPLS VPNs fall into two broad classes those that operate at Layer 3 and those that operate at Layer 2. Layer 3 VPNs were first to be investigated and standardized in RFCs. Layer 3 VPNs based on RFC 2547 bis have seen the most widespread deployment to date. RFC 2547 bis-based Layer 3 VPNs use extensions to BGP, specifically Multi-Protocol internal BGP (MP-i. BGP), to distribute VPN routing information across the provider backbone. Standard MPLS mechanisms (as previously discussed) are used to forward the VPN traffic across the backbone. In an L 3 VPN, the CE and PE routers are IP routing peers. The CE router provides the PE router with the routing information for the customer's private network behind it. The PE router stores this private routing information in a Virtual Routing and Forwarding (VRF) table; each VRF is essentially a private IP network. The PE router maintains a separate VRF table for each VPN, thereby providing appropriate isolation and security. VPN users have access only to sites or hosts within the same VPN. In addition to the VRF tables, the PE router also stores the normal routing information it needs to send traffic over the public Internet. L 3 VPNs use a two-level MPLS label stack (see Figure 3). The inner label carries VPN-specific information from PE to PE. The outer label carries the hop-by-hop MPLS forwarding information. The P routers in the MPLS network only read and swap the outer label as the packet passes through the network. They do not read or act upon the inner VPN label that information is tunneled across the network. The L 3 VPN approach has several advantages. The customer IP address space is managed by the carrier, significantly simplifying the customer IT role as new customer VPN sites are easily connected and managed by the provider. L 3 VPNs also have the advantage of supporting auto-discovery by leveraging the dynamic routing capabilities of BGP to distribute VPN routes. The Layer 3 approach has disadvantages as well. Layer 3 VPNs support only IP or IP-encapsulated customer traffic. Scaling also can be a significant issue with PE routers required to support BGP routing tables that are larger than normal with the addition of the VPN routes. 40
L 3 VPNs. MPLS VPNs fall into two broad classes those that operate at Layer 3 and those that operate at Layer 2. Layer 3 VPNs were first to be investigated and standardized in RFCs. Layer 3 VPNs based on RFC 2547 bis have seen the most widespread deployment to date. RFC 2547 bis-based Layer 3 VPNs use extensions to BGP, specifically Multi-Protocol internal BGP (MP-i. BGP), to distribute VPN routing information across the provider backbone. Standard MPLS mechanisms (as previously discussed) are used to forward the VPN traffic across the backbone. In an L 3 VPN, the CE and PE routers are IP routing peers. The CE router provides the PE router with the routing information for the customer's private network behind it. The PE router stores this private routing information in a Virtual Routing and Forwarding (VRF) table; each VRF is essentially a private IP network. The PE router maintains a separate VRF table for each VPN, thereby providing appropriate isolation and security. VPN users have access only to sites or hosts within the same VPN. In addition to the VRF tables, the PE router also stores the normal routing information it needs to send traffic over the public Internet. L 3 VPNs use a two-level MPLS label stack (see Figure 3). The inner label carries VPN-specific information from PE to PE. The outer label carries the hop-by-hop MPLS forwarding information. The P routers in the MPLS network only read and swap the outer label as the packet passes through the network. They do not read or act upon the inner VPN label that information is tunneled across the network. The L 3 VPN approach has several advantages. The customer IP address space is managed by the carrier, significantly simplifying the customer IT role as new customer VPN sites are easily connected and managed by the provider. L 3 VPNs also have the advantage of supporting auto-discovery by leveraging the dynamic routing capabilities of BGP to distribute VPN routes. The Layer 3 approach has disadvantages as well. Layer 3 VPNs support only IP or IP-encapsulated customer traffic. Scaling also can be a significant issue with PE routers required to support BGP routing tables that are larger than normal with the addition of the VPN routes. 40
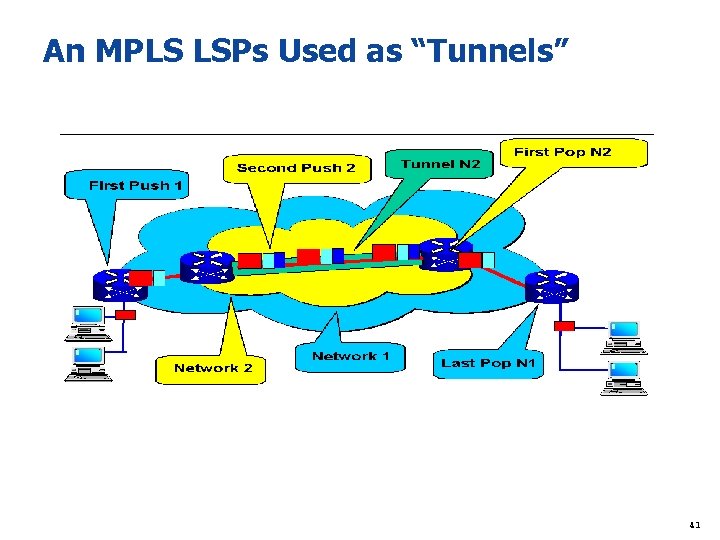 An MPLS LSPs Used as “Tunnels” 41
An MPLS LSPs Used as “Tunnels” 41
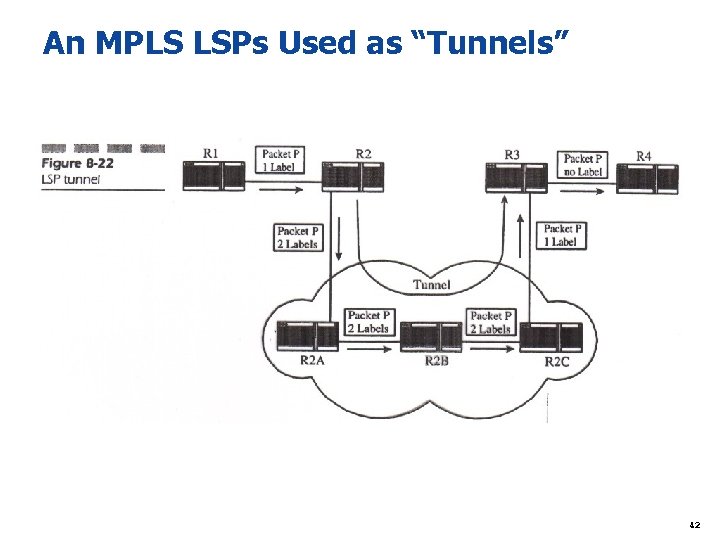 An MPLS LSPs Used as “Tunnels” 42
An MPLS LSPs Used as “Tunnels” 42
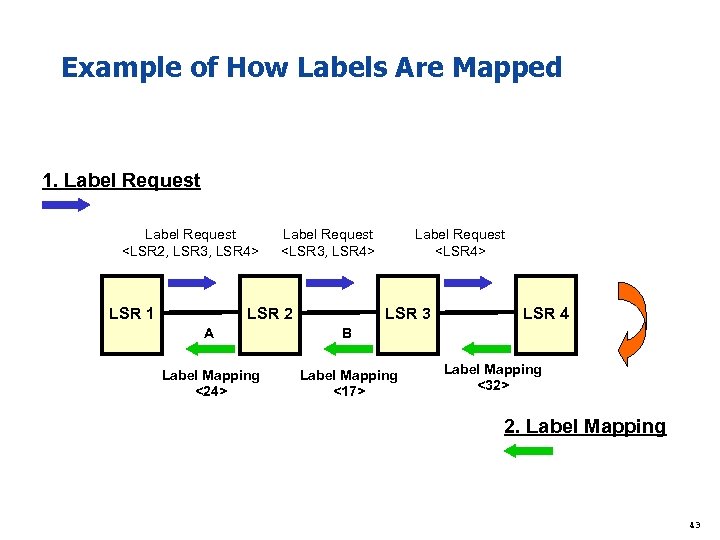 Example of How Labels Are Mapped 1. Label Request
Example of How Labels Are Mapped 1. Label Request
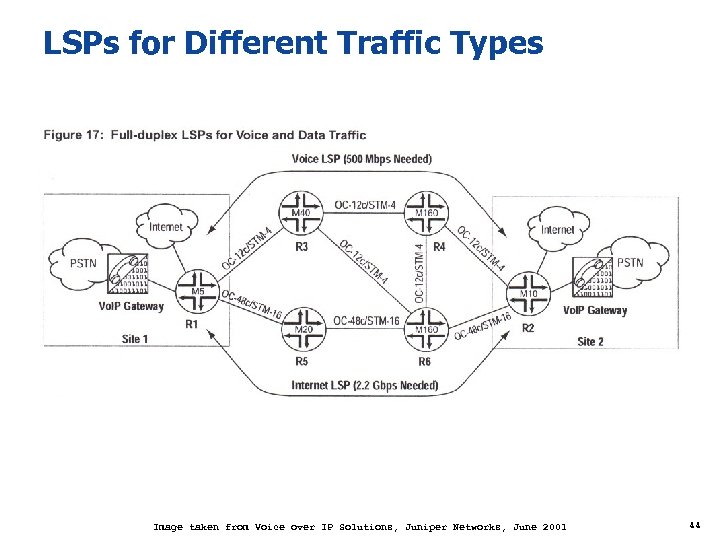 LSPs for Different Traffic Types Image taken from Voice over IP Solutions, Juniper Networks, June 2001 44
LSPs for Different Traffic Types Image taken from Voice over IP Solutions, Juniper Networks, June 2001 44
 Advanced Topic IP Sec 45
Advanced Topic IP Sec 45
 Network Security 101 u Integrity : Received = Sent u Availability: Legal users should be able to use system. Ping u Confidentiality: No wiretapping and snooping u Authentication: You are who you say you are u Authorization: Access Control 46
Network Security 101 u Integrity : Received = Sent u Availability: Legal users should be able to use system. Ping u Confidentiality: No wiretapping and snooping u Authentication: You are who you say you are u Authorization: Access Control 46
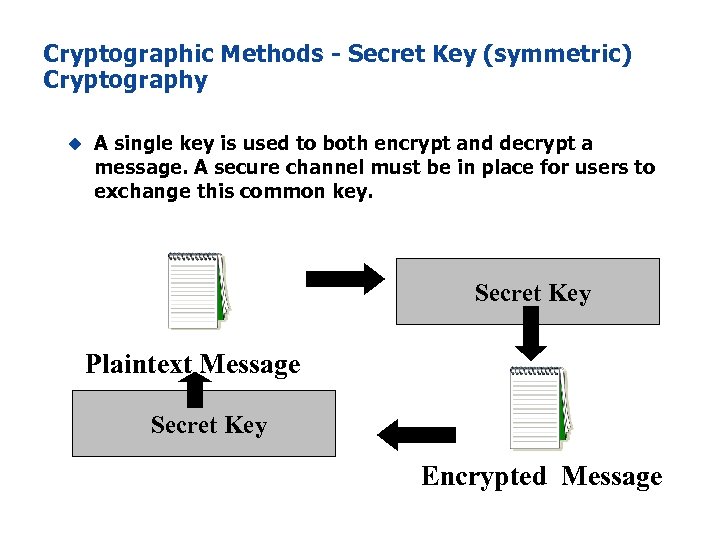 Cryptographic Methods - Secret Key (symmetric) Cryptography u A single key is used to both encrypt and decrypt a message. A secure channel must be in place for users to exchange this common key. Secret Key Plaintext Message Secret Key Encrypted Message
Cryptographic Methods - Secret Key (symmetric) Cryptography u A single key is used to both encrypt and decrypt a message. A secure channel must be in place for users to exchange this common key. Secret Key Plaintext Message Secret Key Encrypted Message
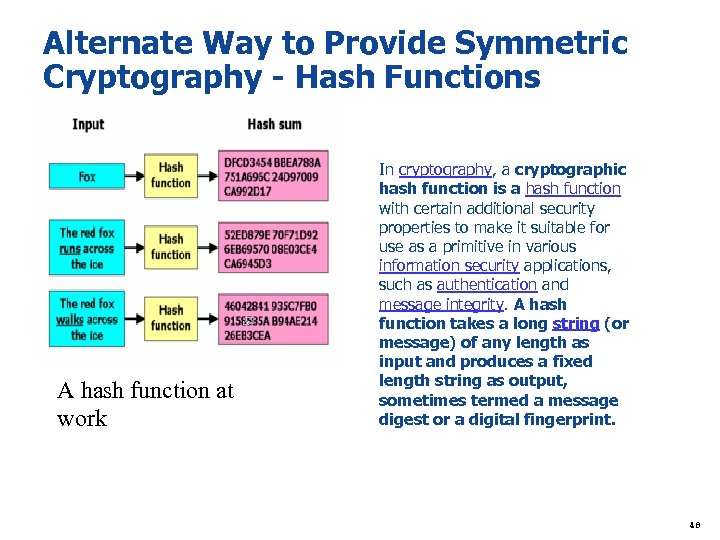 Alternate Way to Provide Symmetric Cryptography - Hash Functions A hash function at work In cryptography, a cryptographic hash function is a hash function with certain additional security properties to make it suitable for use as a primitive in various information security applications, such as authentication and message integrity. A hash function takes a long string (or message) of any length as input and produces a fixed length string as output, sometimes termed a message digest or a digital fingerprint. 48
Alternate Way to Provide Symmetric Cryptography - Hash Functions A hash function at work In cryptography, a cryptographic hash function is a hash function with certain additional security properties to make it suitable for use as a primitive in various information security applications, such as authentication and message integrity. A hash function takes a long string (or message) of any length as input and produces a fixed length string as output, sometimes termed a message digest or a digital fingerprint. 48
 Authentication Using Hash Functions 49
Authentication Using Hash Functions 49
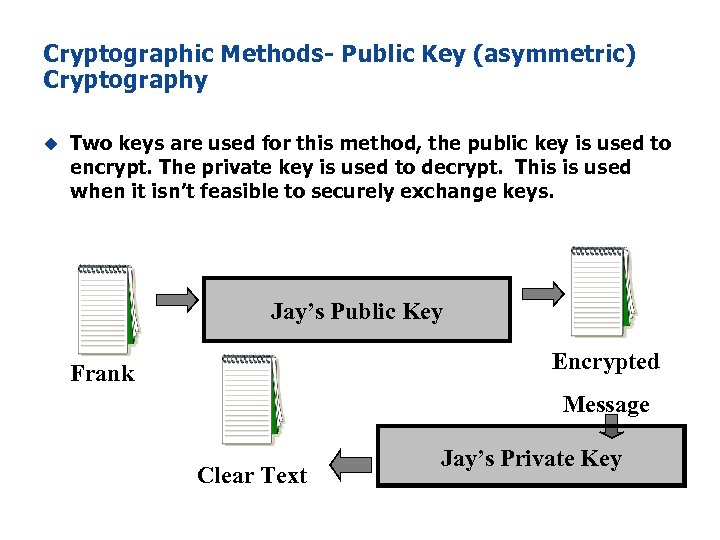 Cryptographic Methods- Public Key (asymmetric) Cryptography u Two keys are used for this method, the public key is used to encrypt. The private key is used to decrypt. This is used when it isn’t feasible to securely exchange keys. Jay’s Public Key Encrypted Frank Message Clear Text Jay’s Private Key
Cryptographic Methods- Public Key (asymmetric) Cryptography u Two keys are used for this method, the public key is used to encrypt. The private key is used to decrypt. This is used when it isn’t feasible to securely exchange keys. Jay’s Public Key Encrypted Frank Message Clear Text Jay’s Private Key
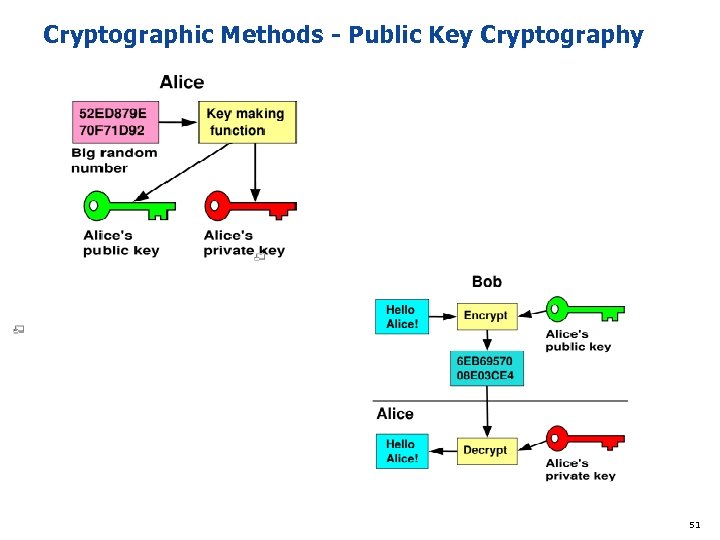 Cryptographic Methods - Public Key Cryptography 51
Cryptographic Methods - Public Key Cryptography 51
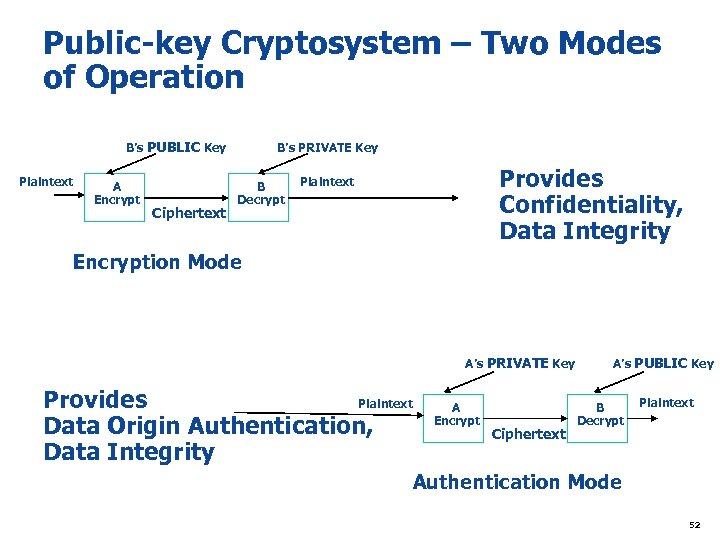 Public-key Cryptosystem – Two Modes of Operation B’s PUBLIC Key Plaintext A Encrypt Ciphertext B’s PRIVATE Key B Decrypt Provides Confidentiality, Data Integrity Plaintext Encryption Mode A’s PRIVATE Key Plaintext Provides Data Origin Authentication, Data Integrity A Encrypt Ciphertext A’s PUBLIC Key B Decrypt Plaintext Authentication Mode 52
Public-key Cryptosystem – Two Modes of Operation B’s PUBLIC Key Plaintext A Encrypt Ciphertext B’s PRIVATE Key B Decrypt Provides Confidentiality, Data Integrity Plaintext Encryption Mode A’s PRIVATE Key Plaintext Provides Data Origin Authentication, Data Integrity A Encrypt Ciphertext A’s PUBLIC Key B Decrypt Plaintext Authentication Mode 52
 Purpose of IPSec u IPSec provides a secured mechanism to send data over unsecured infrastructure – using secure tunnels between two peers, such as two routers. You define which packets are considered sensitive and should be sent through these secure tunnels, and you define the parameters which should be used to protect these sensitive packets, by specifying characteristics of these tunnels. Then, when the IPSec peer sees such a sensitive packet, it sets up the appropriate secure tunnel and sends the packet through the tunnel to the remote peer. u Provides security for transmission of sensitive information over UNPROTECTED networks such as the Internet v Acts at the network layer, protecting and authenticating IP packets between IPSec devises (peers) u Services provided by IPSec v Data Confidentiality u Encrypts packets before sendint them across a network v Data Integrity/Authentication u The IPSec receiver can authenticate packets sent by the IPSec sender to ensure that the data has not been altered during transmission v Data origin Authentication u The IPSec receiver can authenticate the source of the IPSec packets sent. This service is dependent upon the data intergrity service v Anti-Replay u The IPSec receiver can detect and reject replayed packets 53
Purpose of IPSec u IPSec provides a secured mechanism to send data over unsecured infrastructure – using secure tunnels between two peers, such as two routers. You define which packets are considered sensitive and should be sent through these secure tunnels, and you define the parameters which should be used to protect these sensitive packets, by specifying characteristics of these tunnels. Then, when the IPSec peer sees such a sensitive packet, it sets up the appropriate secure tunnel and sends the packet through the tunnel to the remote peer. u Provides security for transmission of sensitive information over UNPROTECTED networks such as the Internet v Acts at the network layer, protecting and authenticating IP packets between IPSec devises (peers) u Services provided by IPSec v Data Confidentiality u Encrypts packets before sendint them across a network v Data Integrity/Authentication u The IPSec receiver can authenticate packets sent by the IPSec sender to ensure that the data has not been altered during transmission v Data origin Authentication u The IPSec receiver can authenticate the source of the IPSec packets sent. This service is dependent upon the data intergrity service v Anti-Replay u The IPSec receiver can detect and reject replayed packets 53
 Concept of IPSec u IPsec is a set of extensions to the IP protocol family. It provides cryptographic security services. These services allow for: v authentication, integrity, access control, and confidentiality. v IPsec provides similar services as SSL, but at the network layer, in a way that is completely transparent to your applications, and much more powerful. We say this because your applications do not have to have any knowledge of IPsec to be able to use it. You can use any IP protocol over IPsec. You can create encrypted tunnels (VPNs), or just do encryption between computers. Since you have so many options, IPsec is rather complex (much more so than SSL!) u IPsec works in any of these three ways: v Host-to-Host ( VPNs) v Host-to-Network (VPNs) v Network-to-Network (Tunneling) 54
Concept of IPSec u IPsec is a set of extensions to the IP protocol family. It provides cryptographic security services. These services allow for: v authentication, integrity, access control, and confidentiality. v IPsec provides similar services as SSL, but at the network layer, in a way that is completely transparent to your applications, and much more powerful. We say this because your applications do not have to have any knowledge of IPsec to be able to use it. You can use any IP protocol over IPsec. You can create encrypted tunnels (VPNs), or just do encryption between computers. Since you have so many options, IPsec is rather complex (much more so than SSL!) u IPsec works in any of these three ways: v Host-to-Host ( VPNs) v Host-to-Network (VPNs) v Network-to-Network (Tunneling) 54
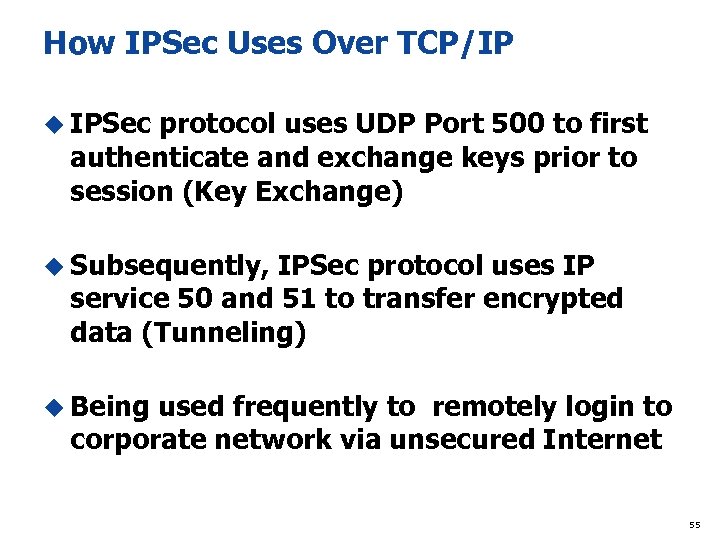 How IPSec Uses Over TCP/IP u IPSec protocol uses UDP Port 500 to first authenticate and exchange keys prior to session (Key Exchange) u Subsequently, IPSec protocol uses IP service 50 and 51 to transfer encrypted data (Tunneling) u Being used frequently to remotely login to corporate network via unsecured Internet 55
How IPSec Uses Over TCP/IP u IPSec protocol uses UDP Port 500 to first authenticate and exchange keys prior to session (Key Exchange) u Subsequently, IPSec protocol uses IP service 50 and 51 to transfer encrypted data (Tunneling) u Being used frequently to remotely login to corporate network via unsecured Internet 55
 What are the protocols behind IPsec? u IPsec = IKE + AH + ESP u IKE: AH and ESP need shared secret key between peers. For communication between distant location, we need to provide ways to negotiate keys in secrecy. IKE will make it possible. u IPsec provides confidentiality, integrity, authenticity, and replay protection through two new protocols. These protocols are called Authentication Header (AH), and Encapsulating Security Payload (ESP). u AH provides authentication, integrity, and replay protection (but not confidentiality). The main difference between the authentication features of AH and ESP is that AH also authenticates portions of the IP header of the packet (such as the source/destination addresses). ESP authenticates only the packet payload. u ESP can provide authentication, integrity, replay protection, and confidentiality of the data (it secures everything in the packet that follows the header). Replay protection requires authentication and integrity (these two go always together). Confidentiality (encryption) can be used with or without authentication/integrity. Similarly, one could use authentication/integrity with or without confidentiality. In practice, it is recommended that ESP be used for most applications. 56
What are the protocols behind IPsec? u IPsec = IKE + AH + ESP u IKE: AH and ESP need shared secret key between peers. For communication between distant location, we need to provide ways to negotiate keys in secrecy. IKE will make it possible. u IPsec provides confidentiality, integrity, authenticity, and replay protection through two new protocols. These protocols are called Authentication Header (AH), and Encapsulating Security Payload (ESP). u AH provides authentication, integrity, and replay protection (but not confidentiality). The main difference between the authentication features of AH and ESP is that AH also authenticates portions of the IP header of the packet (such as the source/destination addresses). ESP authenticates only the packet payload. u ESP can provide authentication, integrity, replay protection, and confidentiality of the data (it secures everything in the packet that follows the header). Replay protection requires authentication and integrity (these two go always together). Confidentiality (encryption) can be used with or without authentication/integrity. Similarly, one could use authentication/integrity with or without confidentiality. In practice, it is recommended that ESP be used for most applications. 56
 IKE – Internet Key Exchange in IPSec u IPsec uses the concept of point-to-point peers. These peers share Transform Sets (TS) with each other during the Security Association negotiation process, and these Transform Sets determine the character of the IPsec session that they share. A Transform Set consists of the following information: v The IPsec security protocol (AH or ESP) v Integrity/Authority algorithm (MD 5, SHA-1) v Encryption Algorithm (DES, 3 -DES) u There are basically 3 steps involved: v Specific algorithms and hashes used to actually secure the communications are agreed upon v A Diffie-Hellman exchange takes place, which is used to generate shared secret keys. This is used to verify the identity of both end points in step three. v Based upon the IP address of both end points the identity of each other is verified. The earlier noted key exchange is now used to decrypt the IP addresses thereby verifying them. u Peers may be from different manufacturers, so they use this negotiation process to work out the lowest common denominator with regards to the features that the peers have been configured to use. Bear in mind that these transform sets are configurable and operate on a session by session basis and they do not necessarily represent the full capabilities of the device. You may for instance configure a different transform set for one connection compared to a transform set for another connection. 57
IKE – Internet Key Exchange in IPSec u IPsec uses the concept of point-to-point peers. These peers share Transform Sets (TS) with each other during the Security Association negotiation process, and these Transform Sets determine the character of the IPsec session that they share. A Transform Set consists of the following information: v The IPsec security protocol (AH or ESP) v Integrity/Authority algorithm (MD 5, SHA-1) v Encryption Algorithm (DES, 3 -DES) u There are basically 3 steps involved: v Specific algorithms and hashes used to actually secure the communications are agreed upon v A Diffie-Hellman exchange takes place, which is used to generate shared secret keys. This is used to verify the identity of both end points in step three. v Based upon the IP address of both end points the identity of each other is verified. The earlier noted key exchange is now used to decrypt the IP addresses thereby verifying them. u Peers may be from different manufacturers, so they use this negotiation process to work out the lowest common denominator with regards to the features that the peers have been configured to use. Bear in mind that these transform sets are configurable and operate on a session by session basis and they do not necessarily represent the full capabilities of the device. You may for instance configure a different transform set for one connection compared to a transform set for another connection. 57
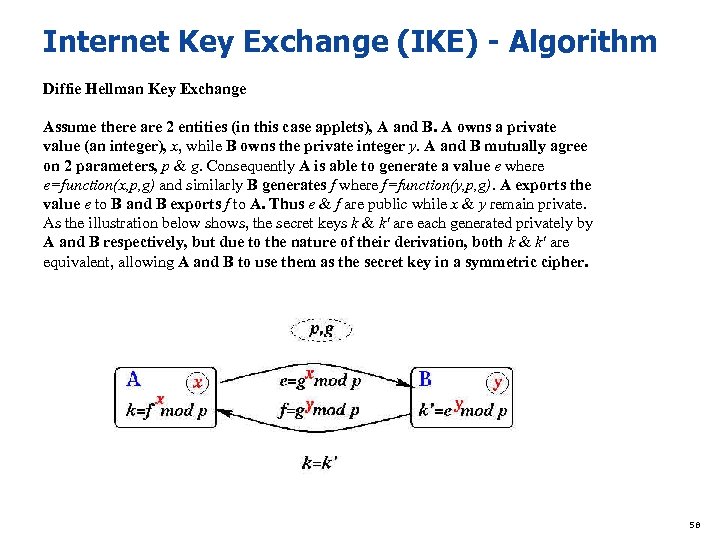 Internet Key Exchange (IKE) - Algorithm Diffie Hellman Key Exchange Assume there are 2 entities (in this case applets), A and B. A owns a private value (an integer), x, while B owns the private integer y. A and B mutually agree on 2 parameters, p & g. Consequently A is able to generate a value e where e=function(x, p, g) and similarly B generates f where f=function(y, p, g). A exports the value e to B and B exports f to A. Thus e & f are public while x & y remain private. As the illustration below shows, the secret keys k & k' are each generated privately by A and B respectively, but due to the nature of their derivation, both k & k' are equivalent, allowing A and B to use them as the secret key in a symmetric cipher. 58
Internet Key Exchange (IKE) - Algorithm Diffie Hellman Key Exchange Assume there are 2 entities (in this case applets), A and B. A owns a private value (an integer), x, while B owns the private integer y. A and B mutually agree on 2 parameters, p & g. Consequently A is able to generate a value e where e=function(x, p, g) and similarly B generates f where f=function(y, p, g). A exports the value e to B and B exports f to A. Thus e & f are public while x & y remain private. As the illustration below shows, the secret keys k & k' are each generated privately by A and B respectively, but due to the nature of their derivation, both k & k' are equivalent, allowing A and B to use them as the secret key in a symmetric cipher. 58
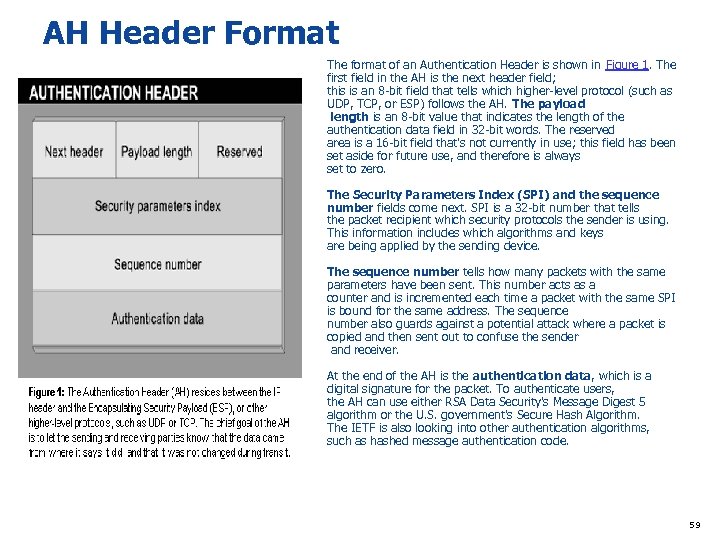 AH Header Format The format of an Authentication Header is shown in Figure 1. The first field in the AH is the next header field; this is an 8 -bit field that tells which higher-level protocol (such as UDP, TCP, or ESP) follows the AH. The payload length is an 8 -bit value that indicates the length of the authentication data field in 32 -bit words. The reserved area is a 16 -bit field that's not currently in use; this field has been set aside for future use, and therefore is always set to zero. The Security Parameters Index (SPI) and the sequence number fields come next. SPI is a 32 -bit number that tells the packet recipient which security protocols the sender is using. This information includes which algorithms and keys are being applied by the sending device. The sequence number tells how many packets with the same parameters have been sent. This number acts as a counter and is incremented each time a packet with the same SPI is bound for the same address. The sequence number also guards against a potential attack where a packet is copied and then sent out to confuse the sender and receiver. At the end of the AH is the authentication data, which is a digital signature for the packet. To authenticate users, the AH can use either RSA Data Security's Message Digest 5 algorithm or the U. S. government's Secure Hash Algorithm. The IETF is also looking into other authentication algorithms, such as hashed message authentication code. 59
AH Header Format The format of an Authentication Header is shown in Figure 1. The first field in the AH is the next header field; this is an 8 -bit field that tells which higher-level protocol (such as UDP, TCP, or ESP) follows the AH. The payload length is an 8 -bit value that indicates the length of the authentication data field in 32 -bit words. The reserved area is a 16 -bit field that's not currently in use; this field has been set aside for future use, and therefore is always set to zero. The Security Parameters Index (SPI) and the sequence number fields come next. SPI is a 32 -bit number that tells the packet recipient which security protocols the sender is using. This information includes which algorithms and keys are being applied by the sending device. The sequence number tells how many packets with the same parameters have been sent. This number acts as a counter and is incremented each time a packet with the same SPI is bound for the same address. The sequence number also guards against a potential attack where a packet is copied and then sent out to confuse the sender and receiver. At the end of the AH is the authentication data, which is a digital signature for the packet. To authenticate users, the AH can use either RSA Data Security's Message Digest 5 algorithm or the U. S. government's Secure Hash Algorithm. The IETF is also looking into other authentication algorithms, such as hashed message authentication code. 59
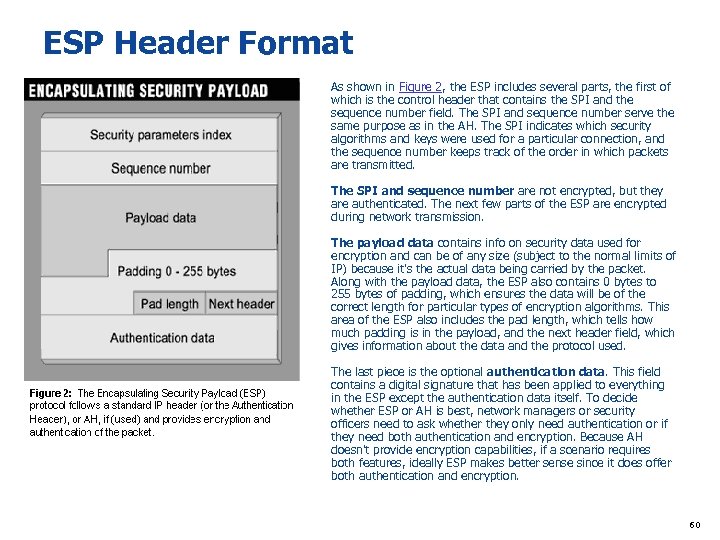 ESP Header Format As shown in Figure 2, the ESP includes several parts, the first of which is the control header that contains the SPI and the sequence number field. The SPI and sequence number serve the same purpose as in the AH. The SPI indicates which security algorithms and keys were used for a particular connection, and the sequence number keeps track of the order in which packets are transmitted. The SPI and sequence number are not encrypted, but they are authenticated. The next few parts of the ESP are encrypted during network transmission. The payload data contains info on security data used for encryption and can be of any size (subject to the normal limits of IP) because it's the actual data being carried by the packet. Along with the payload data, the ESP also contains 0 bytes to 255 bytes of padding, which ensures the data will be of the correct length for particular types of encryption algorithms. This area of the ESP also includes the pad length, which tells how much padding is in the payload, and the next header field, which gives information about the data and the protocol used. The last piece is the optional authentication data. This field contains a digital signature that has been applied to everything in the ESP except the authentication data itself. To decide whether ESP or AH is best, network managers or security officers need to ask whether they only need authentication or if they need both authentication and encryption. Because AH doesn't provide encryption capabilities, if a scenario requires both features, ideally ESP makes better sense since it does offer both authentication and encryption. 60
ESP Header Format As shown in Figure 2, the ESP includes several parts, the first of which is the control header that contains the SPI and the sequence number field. The SPI and sequence number serve the same purpose as in the AH. The SPI indicates which security algorithms and keys were used for a particular connection, and the sequence number keeps track of the order in which packets are transmitted. The SPI and sequence number are not encrypted, but they are authenticated. The next few parts of the ESP are encrypted during network transmission. The payload data contains info on security data used for encryption and can be of any size (subject to the normal limits of IP) because it's the actual data being carried by the packet. Along with the payload data, the ESP also contains 0 bytes to 255 bytes of padding, which ensures the data will be of the correct length for particular types of encryption algorithms. This area of the ESP also includes the pad length, which tells how much padding is in the payload, and the next header field, which gives information about the data and the protocol used. The last piece is the optional authentication data. This field contains a digital signature that has been applied to everything in the ESP except the authentication data itself. To decide whether ESP or AH is best, network managers or security officers need to ask whether they only need authentication or if they need both authentication and encryption. Because AH doesn't provide encryption capabilities, if a scenario requires both features, ideally ESP makes better sense since it does offer both authentication and encryption. 60
 ESP Header - Example ESP(spi=0 x 14579 c 09, seq=0 x 4926) (ttl 243, id 9712, len 1072) 0 x 0000 4500 0430 25 f 0 0000 f 332 94 e 8 c 0 a 8 0164 E. . 0%. . 2. . . {. . 0 x 0010 c 0 a 8 01 c 8 1457 9 c 09 0000 4926 67 f 3 2 e 95 . . . W. . I&g. . . 0 x 0020 6804 f 49 a a 7 e 6 e 6 c 5 4 fd 8 7 b 7 a c 2 b 0 1575 h. . . . O. {z. . . u 0 x 0030 dbdd a 425 2 d 73 9565 0 b 13 0273 53 dc c 6 b 3 . . . %-s. e. . . s. S. . . 0 x 0040 9301 eb 2 b 3 d 29 f 85 e 2 b 81 799 c ec 07 1 e 80 . . . +=). ^+. y. . . 0 x 0050 08 fb cf 16 9 cea 3263 3 d 46 55 f 6 f 070 a 6 f 0 . . . 2 c=FU. . p. 0 x 0060 4029 0453 4707 19 cc 0212 5 d 33 36 fa 134 a @). SG. . . ]36. . J 0 x 0070 d 640 690 c 01 f 6 ac 9 c 3818 1 da 5 becb 2 baa . @i. . . 8. . . +. 61
ESP Header - Example ESP(spi=0 x 14579 c 09, seq=0 x 4926) (ttl 243, id 9712, len 1072) 0 x 0000 4500 0430 25 f 0 0000 f 332 94 e 8 c 0 a 8 0164 E. . 0%. . 2. . . {. . 0 x 0010 c 0 a 8 01 c 8 1457 9 c 09 0000 4926 67 f 3 2 e 95 . . . W. . I&g. . . 0 x 0020 6804 f 49 a a 7 e 6 e 6 c 5 4 fd 8 7 b 7 a c 2 b 0 1575 h. . . . O. {z. . . u 0 x 0030 dbdd a 425 2 d 73 9565 0 b 13 0273 53 dc c 6 b 3 . . . %-s. e. . . s. S. . . 0 x 0040 9301 eb 2 b 3 d 29 f 85 e 2 b 81 799 c ec 07 1 e 80 . . . +=). ^+. y. . . 0 x 0050 08 fb cf 16 9 cea 3263 3 d 46 55 f 6 f 070 a 6 f 0 . . . 2 c=FU. . p. 0 x 0060 4029 0453 4707 19 cc 0212 5 d 33 36 fa 134 a @). SG. . . ]36. . J 0 x 0070 d 640 690 c 01 f 6 ac 9 c 3818 1 da 5 becb 2 baa . @i. . . 8. . . +. 61
 IPSec Modes of Operation u Transport Mode (Less secured) – Encrypts normal communication between peers with routing info untouched (IP Address) v only the payload (data) of the original IP packet is protected (encrypted, authenticated, or both) and not the end-to-end header. The payload is encapsulated by the IPSec headers and trailers (an ESP header and trailer, an AH header, or both). The original IP headers remain intact and are not protected by IPSec. v Use transport mode only when the IP traffic to be protected has IPSec peers as both the source and destination. For example, you could use transport mode to protect router management traffic. Specifying transport mode allows the router to negotiate with the remote peer whether to use transport or tunnel mode. u Tunnel Mode (More secured) - encapsulate packet into new IPv 4 header v the entire original IP packet is protected (encrypted, authenticated, or both) and is encapsulated by the IPSec headers and trailers (an ESP header and trailer, an AH header, or both). Then a new IP header is prefixed to the packet, specifying the IPSec endpoints as the source and destination. v Tunnel mode can be used with any IP traffic. Tunnel mode must be used if IPSec is protecting traffic from hosts behind the IPSec peers. For example, tunnel mode is used with virtual private networks (VPNs) where hosts on one protected network send packets to hosts on a different protected network via a pair of IPSec peers. With VPNs, the IPSec peers "tunnel" the protected traffic between the peers while the hosts on their protected networks are the session endpoints. 62
IPSec Modes of Operation u Transport Mode (Less secured) – Encrypts normal communication between peers with routing info untouched (IP Address) v only the payload (data) of the original IP packet is protected (encrypted, authenticated, or both) and not the end-to-end header. The payload is encapsulated by the IPSec headers and trailers (an ESP header and trailer, an AH header, or both). The original IP headers remain intact and are not protected by IPSec. v Use transport mode only when the IP traffic to be protected has IPSec peers as both the source and destination. For example, you could use transport mode to protect router management traffic. Specifying transport mode allows the router to negotiate with the remote peer whether to use transport or tunnel mode. u Tunnel Mode (More secured) - encapsulate packet into new IPv 4 header v the entire original IP packet is protected (encrypted, authenticated, or both) and is encapsulated by the IPSec headers and trailers (an ESP header and trailer, an AH header, or both). Then a new IP header is prefixed to the packet, specifying the IPSec endpoints as the source and destination. v Tunnel mode can be used with any IP traffic. Tunnel mode must be used if IPSec is protecting traffic from hosts behind the IPSec peers. For example, tunnel mode is used with virtual private networks (VPNs) where hosts on one protected network send packets to hosts on a different protected network via a pair of IPSec peers. With VPNs, the IPSec peers "tunnel" the protected traffic between the peers while the hosts on their protected networks are the session endpoints. 62
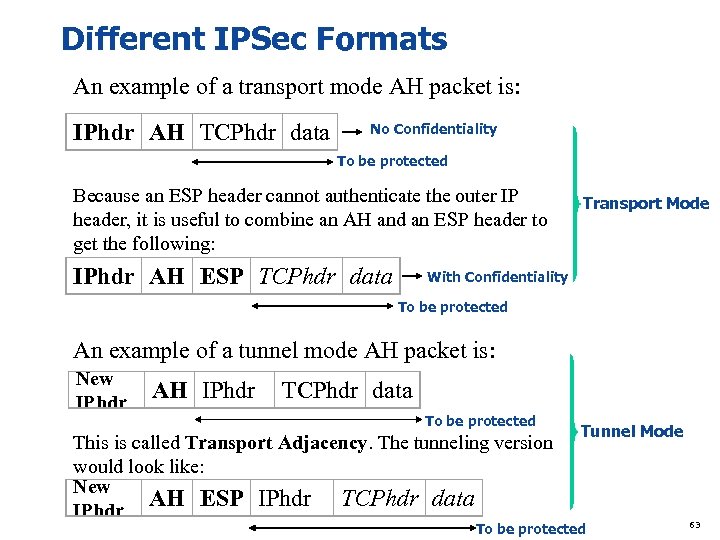 Different IPSec Formats An example of a transport mode AH packet is: IPhdr AH TCPhdr data No Confidentiality To be protected Because an ESP header cannot authenticate the outer IP header, it is useful to combine an AH and an ESP header to get the following: IPhdr AH ESP TCPhdr data Transport Mode With Confidentiality To be protected An example of a tunnel mode AH packet is: New IPhdr AH IPhdr TCPhdr data To be protected This is called Transport Adjacency. The tunneling version would look like: New AH ESP IPhdr TCPhdr data IPhdr Tunnel Mode To be protected 63
Different IPSec Formats An example of a transport mode AH packet is: IPhdr AH TCPhdr data No Confidentiality To be protected Because an ESP header cannot authenticate the outer IP header, it is useful to combine an AH and an ESP header to get the following: IPhdr AH ESP TCPhdr data Transport Mode With Confidentiality To be protected An example of a tunnel mode AH packet is: New IPhdr AH IPhdr TCPhdr data To be protected This is called Transport Adjacency. The tunneling version would look like: New AH ESP IPhdr TCPhdr data IPhdr Tunnel Mode To be protected 63
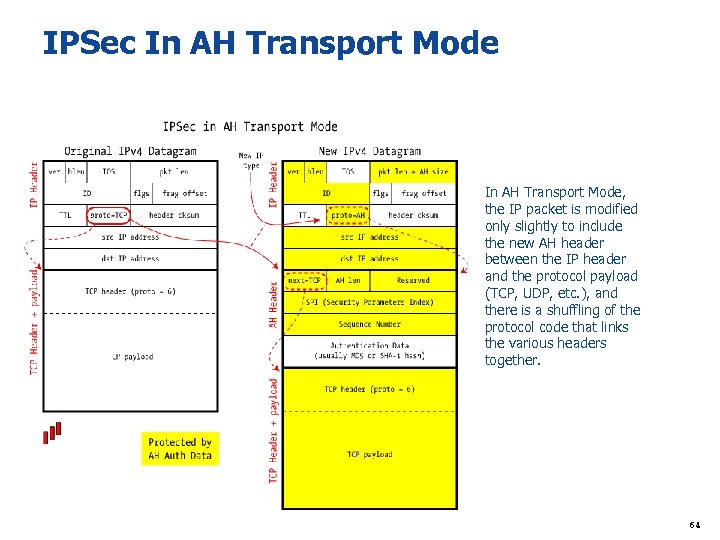 IPSec In AH Transport Mode In AH Transport Mode, the IP packet is modified only slightly to include the new AH header between the IP header and the protocol payload (TCP, UDP, etc. ), and there is a shuffling of the protocol code that links the various headers together. 64
IPSec In AH Transport Mode In AH Transport Mode, the IP packet is modified only slightly to include the new AH header between the IP header and the protocol payload (TCP, UDP, etc. ), and there is a shuffling of the protocol code that links the various headers together. 64
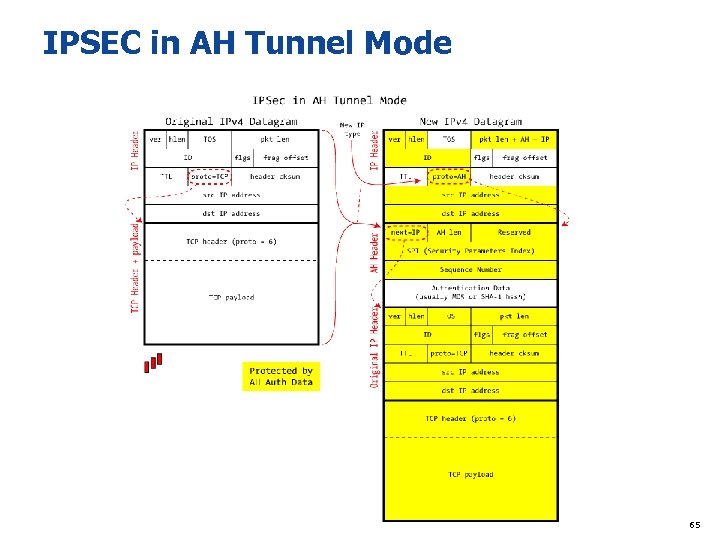 IPSEC in AH Tunnel Mode 65
IPSEC in AH Tunnel Mode 65
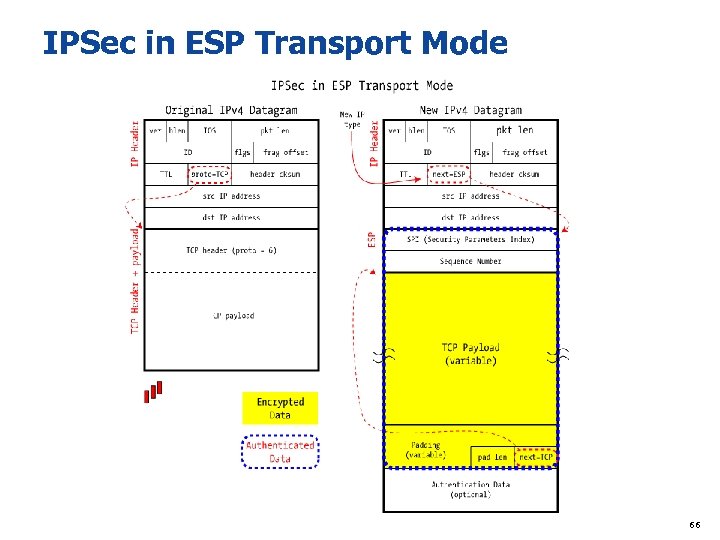 IPSec in ESP Transport Mode 66
IPSec in ESP Transport Mode 66
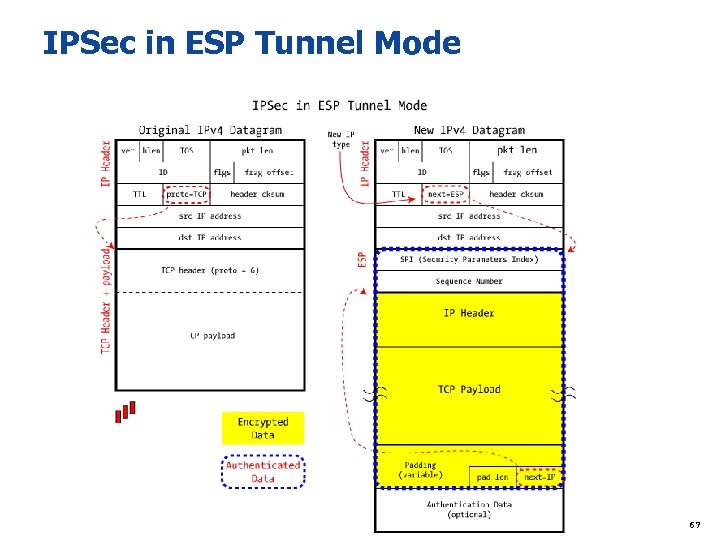 IPSec in ESP Tunnel Mode 67
IPSec in ESP Tunnel Mode 67
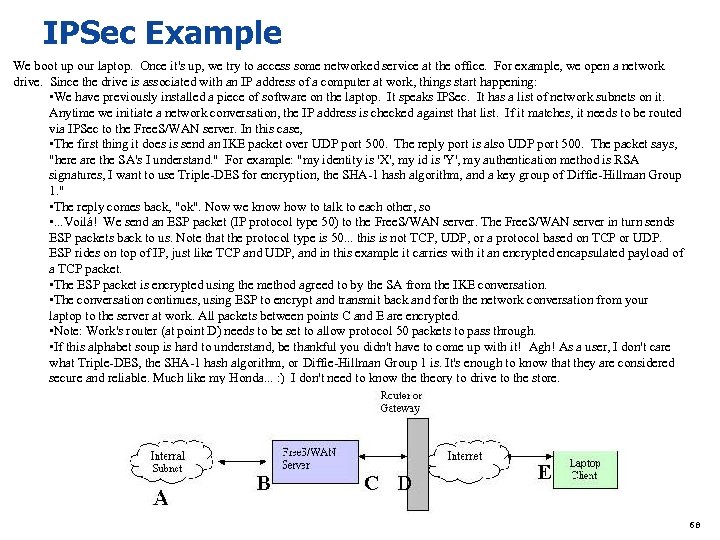 IPSec Example We boot up our laptop. Once it's up, we try to access some networked service at the office. For example, we open a network drive. Since the drive is associated with an IP address of a computer at work, things start happening: • We have previously installed a piece of software on the laptop. It speaks IPSec. It has a list of network subnets on it. Anytime we initiate a network conversation, the IP address is checked against that list. If it matches, it needs to be routed via IPSec to the Free. S/WAN server. In this case, • The first thing it does is send an IKE packet over UDP port 500. The reply port is also UDP port 500. The packet says, "here are the SA's I understand. " For example: "my identity is 'X', my id is 'Y', my authentication method is RSA signatures, I want to use Triple-DES for encryption, the SHA-1 hash algorithm, and a key group of Diffie-Hillman Group 1. " • The reply comes back, "ok". Now we know how to talk to each other, so • . . . Voilá! We send an ESP packet (IP protocol type 50) to the Free. S/WAN server. The Free. S/WAN server in turn sends ESP packets back to us. Note that the protocol type is 50. . . this is not TCP, UDP, or a protocol based on TCP or UDP. ESP rides on top of IP, just like TCP and UDP, and in this example it carries with it an encrypted encapsulated payload of a TCP packet. • The ESP packet is encrypted using the method agreed to by the SA from the IKE conversation. • The conversation continues, using ESP to encrypt and transmit back and forth the network conversation from your laptop to the server at work. All packets between points C and E are encrypted. • Note: Work's router (at point D) needs to be set to allow protocol 50 packets to pass through. • If this alphabet soup is hard to understand, be thankful you didn't have to come up with it! Agh! As a user, I don't care what Triple-DES, the SHA-1 hash algorithm, or Diffie-Hillman Group 1 is. It's enough to know that they are considered secure and reliable. Much like my Honda. . . : ) I don't need to know theory to drive to the store. 68
IPSec Example We boot up our laptop. Once it's up, we try to access some networked service at the office. For example, we open a network drive. Since the drive is associated with an IP address of a computer at work, things start happening: • We have previously installed a piece of software on the laptop. It speaks IPSec. It has a list of network subnets on it. Anytime we initiate a network conversation, the IP address is checked against that list. If it matches, it needs to be routed via IPSec to the Free. S/WAN server. In this case, • The first thing it does is send an IKE packet over UDP port 500. The reply port is also UDP port 500. The packet says, "here are the SA's I understand. " For example: "my identity is 'X', my id is 'Y', my authentication method is RSA signatures, I want to use Triple-DES for encryption, the SHA-1 hash algorithm, and a key group of Diffie-Hillman Group 1. " • The reply comes back, "ok". Now we know how to talk to each other, so • . . . Voilá! We send an ESP packet (IP protocol type 50) to the Free. S/WAN server. The Free. S/WAN server in turn sends ESP packets back to us. Note that the protocol type is 50. . . this is not TCP, UDP, or a protocol based on TCP or UDP. ESP rides on top of IP, just like TCP and UDP, and in this example it carries with it an encrypted encapsulated payload of a TCP packet. • The ESP packet is encrypted using the method agreed to by the SA from the IKE conversation. • The conversation continues, using ESP to encrypt and transmit back and forth the network conversation from your laptop to the server at work. All packets between points C and E are encrypted. • Note: Work's router (at point D) needs to be set to allow protocol 50 packets to pass through. • If this alphabet soup is hard to understand, be thankful you didn't have to come up with it! Agh! As a user, I don't care what Triple-DES, the SHA-1 hash algorithm, or Diffie-Hillman Group 1 is. It's enough to know that they are considered secure and reliable. Much like my Honda. . . : ) I don't need to know theory to drive to the store. 68
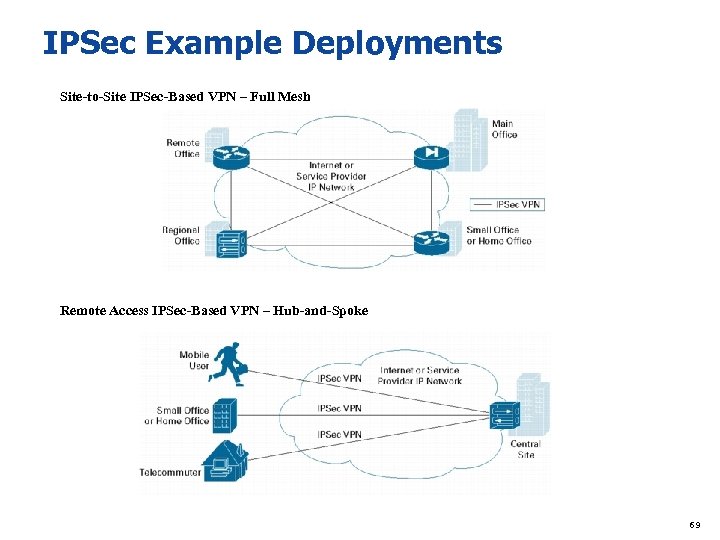 IPSec Example Deployments Site-to-Site IPSec-Based VPN – Full Mesh Remote Access IPSec-Based VPN – Hub-and-Spoke 69
IPSec Example Deployments Site-to-Site IPSec-Based VPN – Full Mesh Remote Access IPSec-Based VPN – Hub-and-Spoke 69
 Good Reasons For Deploying IPSec u u u The enterprise needs security measures like data encryption or user and device authentication. IPSec provides strong security beyond the traffic separation inherent to MPLS, Frame Relay, or ATM networks. Enterprises that choose the MPLS VPN architecture because of its scalability and Qo. S support sometimes augment it with IPSec when they need additional security functions such as data encryption. Cost considerations are important. An IPSec VPN can be deployed across any existing IP network, avoiding the capital and operational expense of building a new network. The enterprise needs to extend their corporate network resources to geographically dispersed teleworkers and mobile workers. Rapid deployment is important because the business can quickly add a new site or expand to a new location. IPSec saves time because it requires little or no change to the existing IP network infrastructure. Traffic flow follows a hub-and-spoke topology. 70
Good Reasons For Deploying IPSec u u u The enterprise needs security measures like data encryption or user and device authentication. IPSec provides strong security beyond the traffic separation inherent to MPLS, Frame Relay, or ATM networks. Enterprises that choose the MPLS VPN architecture because of its scalability and Qo. S support sometimes augment it with IPSec when they need additional security functions such as data encryption. Cost considerations are important. An IPSec VPN can be deployed across any existing IP network, avoiding the capital and operational expense of building a new network. The enterprise needs to extend their corporate network resources to geographically dispersed teleworkers and mobile workers. Rapid deployment is important because the business can quickly add a new site or expand to a new location. IPSec saves time because it requires little or no change to the existing IP network infrastructure. Traffic flow follows a hub-and-spoke topology. 70
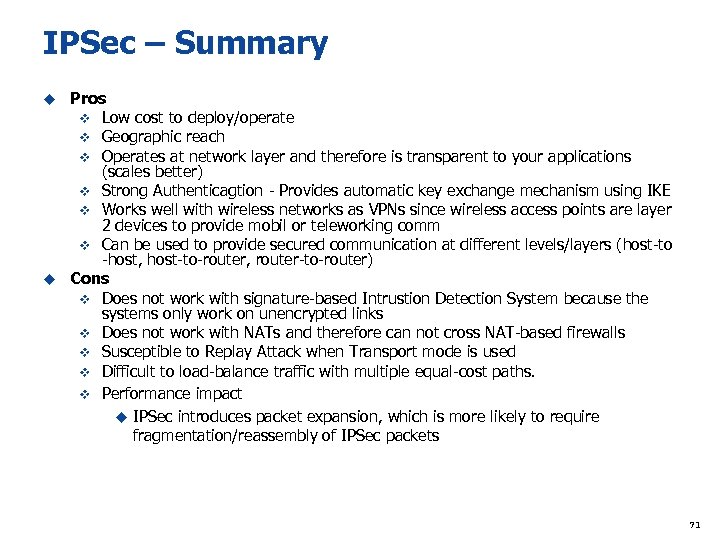 IPSec – Summary Pros v Low cost to deploy/operate v Geographic reach v Operates at network layer and therefore is transparent to your applications (scales better) v Strong Authenticagtion - Provides automatic key exchange mechanism using IKE v Works well with wireless networks as VPNs since wireless access points are layer 2 devices to provide mobil or teleworking comm v Can be used to provide secured communication at different levels/layers (host-to -host, host-to-router, router-to-router) u Cons v Does not work with signature-based Intrustion Detection System because the systems only work on unencrypted links v Does not work with NATs and therefore can not cross NAT-based firewalls v Susceptible to Replay Attack when Transport mode is used v Difficult to load-balance traffic with multiple equal-cost paths. v Performance impact u IPSec introduces packet expansion, which is more likely to require fragmentation/reassembly of IPSec packets u 71
IPSec – Summary Pros v Low cost to deploy/operate v Geographic reach v Operates at network layer and therefore is transparent to your applications (scales better) v Strong Authenticagtion - Provides automatic key exchange mechanism using IKE v Works well with wireless networks as VPNs since wireless access points are layer 2 devices to provide mobil or teleworking comm v Can be used to provide secured communication at different levels/layers (host-to -host, host-to-router, router-to-router) u Cons v Does not work with signature-based Intrustion Detection System because the systems only work on unencrypted links v Does not work with NATs and therefore can not cross NAT-based firewalls v Susceptible to Replay Attack when Transport mode is used v Difficult to load-balance traffic with multiple equal-cost paths. v Performance impact u IPSec introduces packet expansion, which is more likely to require fragmentation/reassembly of IPSec packets u 71
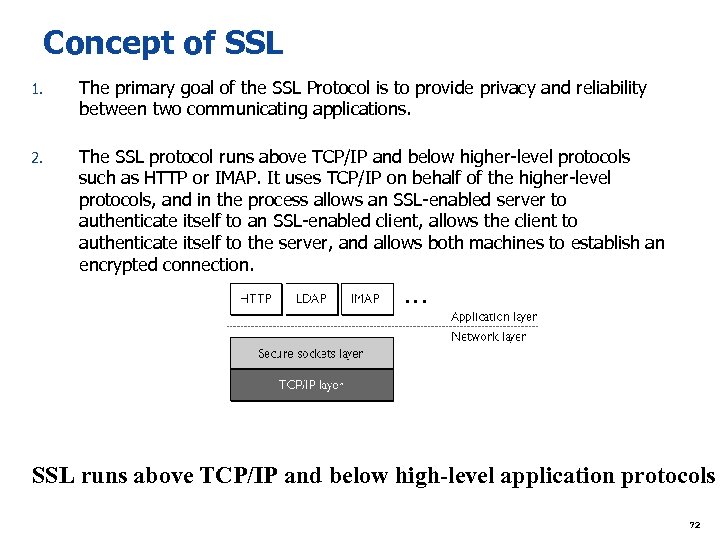 Concept of SSL 1. The primary goal of the SSL Protocol is to provide privacy and reliability between two communicating applications. 2. The SSL protocol runs above TCP/IP and below higher-level protocols such as HTTP or IMAP. It uses TCP/IP on behalf of the higher-level protocols, and in the process allows an SSL-enabled server to authenticate itself to an SSL-enabled client, allows the client to authenticate itself to the server, and allows both machines to establish an encrypted connection. SSL runs above TCP/IP and below high-level application protocols 72
Concept of SSL 1. The primary goal of the SSL Protocol is to provide privacy and reliability between two communicating applications. 2. The SSL protocol runs above TCP/IP and below higher-level protocols such as HTTP or IMAP. It uses TCP/IP on behalf of the higher-level protocols, and in the process allows an SSL-enabled server to authenticate itself to an SSL-enabled client, allows the client to authenticate itself to the server, and allows both machines to establish an encrypted connection. SSL runs above TCP/IP and below high-level application protocols 72
 SSL Functions • SSL server authentication allows a user to confirm a server's identity. SSL-enabled client software can use standard techniques of public-key cryptography to check that a server's certificate and public ID are valid and have been issued by a certificate authority (CA) listed in the client's list of trusted CAs. This confirmation might be important if the user, for example, is sending a credit card number over the network and wants to check the receiving server's identity. • SSL client authentication allows a server to confirm a user's identity. Using the same techniques as those used for server authentication, SSL-enabled server software can check that a client's certificate and public ID are valid and have been issued by a certificate authority (CA) listed in the server's list of trusted CAs. This confirmation might be important if the server, for example, is a bank sending confidential financial information to a customer and wants to check the recipient's identity. • An encrypted SSL connection requires all information sent between a client and a server to be encrypted by the sending software and decrypted by the receiving software, thus providing a high degree of confidentiality. Confidentiality is important for both parties to any private transaction. In addition, all data sent over an encrypted SSL connection is protected with a mechanism for detecting tampering--that is, for automatically determining whether the data has been altered in transit. 73
SSL Functions • SSL server authentication allows a user to confirm a server's identity. SSL-enabled client software can use standard techniques of public-key cryptography to check that a server's certificate and public ID are valid and have been issued by a certificate authority (CA) listed in the client's list of trusted CAs. This confirmation might be important if the user, for example, is sending a credit card number over the network and wants to check the receiving server's identity. • SSL client authentication allows a server to confirm a user's identity. Using the same techniques as those used for server authentication, SSL-enabled server software can check that a client's certificate and public ID are valid and have been issued by a certificate authority (CA) listed in the server's list of trusted CAs. This confirmation might be important if the server, for example, is a bank sending confidential financial information to a customer and wants to check the recipient's identity. • An encrypted SSL connection requires all information sent between a client and a server to be encrypted by the sending software and decrypted by the receiving software, thus providing a high degree of confidentiality. Confidentiality is important for both parties to any private transaction. In addition, all data sent over an encrypted SSL connection is protected with a mechanism for detecting tampering--that is, for automatically determining whether the data has been altered in transit. 73
 Advanced Topic IPv 6 74
Advanced Topic IPv 6 74
 Agenda u Justification for IPv 6 u Key Differences between IPv 4 and IPv 6 v Protocol/header format/fields u Implications of IPv 6 v IPv 4 and IPv 6 Transition v Security v Business u Current state of IPv 6 75
Agenda u Justification for IPv 6 u Key Differences between IPv 4 and IPv 6 v Protocol/header format/fields u Implications of IPv 6 v IPv 4 and IPv 6 Transition v Security v Business u Current state of IPv 6 75
 Justification for IPv 6 u Theoretical address exhaustion u Different Types of Addresses u But NAT will save us! 76
Justification for IPv 6 u Theoretical address exhaustion u Different Types of Addresses u But NAT will save us! 76
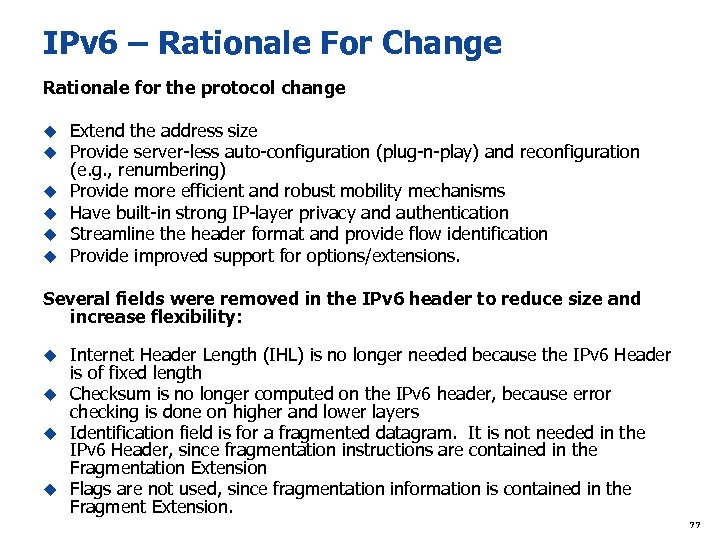 IPv 6 – Rationale For Change Rationale for the protocol change u Extend the address size u Provide server-less auto-configuration (plug-n-play) and reconfiguration (e. g. , renumbering) u Provide more efficient and robust mobility mechanisms u Have built-in strong IP-layer privacy and authentication u Streamline the header format and provide flow identification u Provide improved support for options/extensions. Several fields were removed in the IPv 6 header to reduce size and increase flexibility: Internet Header Length (IHL) is no longer needed because the IPv 6 Header is of fixed length u Checksum is no longer computed on the IPv 6 header, because error checking is done on higher and lower layers u Identification field is for a fragmented datagram. It is not needed in the IPv 6 Header, since fragmentation instructions are contained in the Fragmentation Extension u Flags are not used, since fragmentation information is contained in the Fragment Extension. u 77
IPv 6 – Rationale For Change Rationale for the protocol change u Extend the address size u Provide server-less auto-configuration (plug-n-play) and reconfiguration (e. g. , renumbering) u Provide more efficient and robust mobility mechanisms u Have built-in strong IP-layer privacy and authentication u Streamline the header format and provide flow identification u Provide improved support for options/extensions. Several fields were removed in the IPv 6 header to reduce size and increase flexibility: Internet Header Length (IHL) is no longer needed because the IPv 6 Header is of fixed length u Checksum is no longer computed on the IPv 6 header, because error checking is done on higher and lower layers u Identification field is for a fragmented datagram. It is not needed in the IPv 6 Header, since fragmentation instructions are contained in the Fragmentation Extension u Flags are not used, since fragmentation information is contained in the Fragment Extension. u 77
 What are the implications of increased address space in the network? Vastly expanded routing and addressing capabilities v The network and the nodes it supports can now scale effectively to any conceivable size. u Network Transparency v In IPv 6, any node has the potential to directly communicate with any other node v Enables effective deployment of peer-to-peer applications. Peer to peer apps are more resilient to network changes since they only need a communication path – no “state” information about the application is maintained in the network or in a central server. v Removes single nodes of failure like NATs, enables cleaner network architecture v Changes the security paradigm of the network, as “security through obscurity” with NAT will not exist. A layered security infrastructure, using firewalls, end-node security, and intelligent network security is needed. u 78
What are the implications of increased address space in the network? Vastly expanded routing and addressing capabilities v The network and the nodes it supports can now scale effectively to any conceivable size. u Network Transparency v In IPv 6, any node has the potential to directly communicate with any other node v Enables effective deployment of peer-to-peer applications. Peer to peer apps are more resilient to network changes since they only need a communication path – no “state” information about the application is maintained in the network or in a central server. v Removes single nodes of failure like NATs, enables cleaner network architecture v Changes the security paradigm of the network, as “security through obscurity” with NAT will not exist. A layered security infrastructure, using firewalls, end-node security, and intelligent network security is needed. u 78
 IPv 6 - the Technology u Impetus for design in early 90’s was looming address shortage, major benefit of IPv 6 is resolving this shortage and the implications to network scalability, transparency, and flexibility. u Along the way seen as an opportunity to fix every other shortcoming of IPv 4 u As IPv 6 was being designed, many v 4 shortcomings fixed with stopgap measures – examples: v Classless Interdomain Routing (CIDR) : helped extend the lifetime of the IPv 4 address space, but caused vast increase in core network routing table v Network Address Translation (NAT) : again helped extend the usefulness of the IPv 4 address space, at the cost of new single nodes of failure and breaking the original peer-to-peer capability of the Internet. u In the long term the vastly increased scalability and transparency IPv 6 provides is needed to provide for future anticipated network requirements 79
IPv 6 - the Technology u Impetus for design in early 90’s was looming address shortage, major benefit of IPv 6 is resolving this shortage and the implications to network scalability, transparency, and flexibility. u Along the way seen as an opportunity to fix every other shortcoming of IPv 4 u As IPv 6 was being designed, many v 4 shortcomings fixed with stopgap measures – examples: v Classless Interdomain Routing (CIDR) : helped extend the lifetime of the IPv 4 address space, but caused vast increase in core network routing table v Network Address Translation (NAT) : again helped extend the usefulness of the IPv 4 address space, at the cost of new single nodes of failure and breaking the original peer-to-peer capability of the Internet. u In the long term the vastly increased scalability and transparency IPv 6 provides is needed to provide for future anticipated network requirements 79
 Theoretical Address Exhaustion Size of IP range u IPv 4 addresses v u 2^32 = 4 x 10^9 = 4, 294, 967, 296 IPv 6 addresses 2^128 = 3 x 10^38 = 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 v 340 undecillion –US, 340 sextillion-UK v 79, 228, 162, 514, 264, 337, 593, 543, 950, 336 times more v 6 addresses than v 4 v 80
Theoretical Address Exhaustion Size of IP range u IPv 4 addresses v u 2^32 = 4 x 10^9 = 4, 294, 967, 296 IPv 6 addresses 2^128 = 3 x 10^38 = 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 v 340 undecillion –US, 340 sextillion-UK v 79, 228, 162, 514, 264, 337, 593, 543, 950, 336 times more v 6 addresses than v 4 v 80
 But NAT will save us! What is NAT? u Network Address Translation Advantage u Interim solution to combat IPv 4 address depletion u NAT maps IP addresses from one realm to another v v v Used to obscure private network topology u v u Mapping private IPs to public IPs. Provides one-to-one mapping May be defined between public and private IP addresses Security through obscurity has never succeeded long term NAT is for network administration and not for security 81
But NAT will save us! What is NAT? u Network Address Translation Advantage u Interim solution to combat IPv 4 address depletion u NAT maps IP addresses from one realm to another v v v Used to obscure private network topology u v u Mapping private IPs to public IPs. Provides one-to-one mapping May be defined between public and private IP addresses Security through obscurity has never succeeded long term NAT is for network administration and not for security 81
 But NAT will save us! Disadvantages u NAT eliminates end to end connectivity and can’t participate in some protocols u Higher-layer protocols (such as FTP, Quake, Net. Bios and SIP) send layer-3 information inside IP datagram payloads u Some protocols such as FTP in active mode, use separate ports for control traffic (commands) and for data traffic (file transfers) 82
But NAT will save us! Disadvantages u NAT eliminates end to end connectivity and can’t participate in some protocols u Higher-layer protocols (such as FTP, Quake, Net. Bios and SIP) send layer-3 information inside IP datagram payloads u Some protocols such as FTP in active mode, use separate ports for control traffic (commands) and for data traffic (file transfers) 82
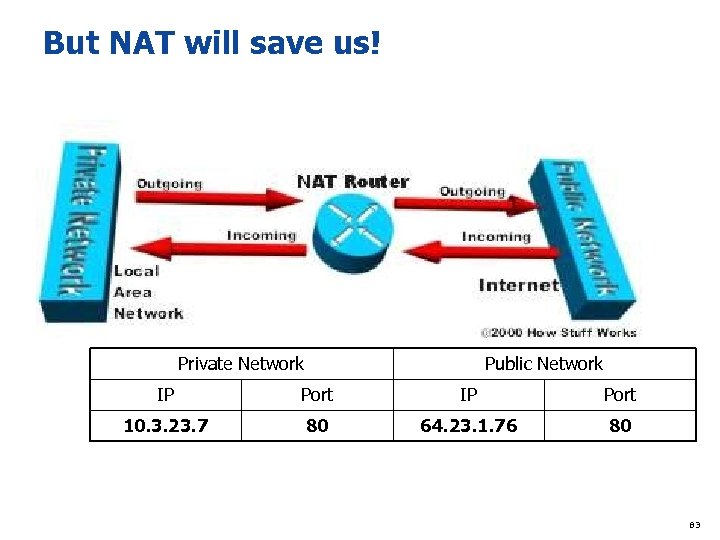 But NAT will save us! Private Network Public Network IP Port 10. 3. 23. 7 80 64. 23. 1. 76 80 83
But NAT will save us! Private Network Public Network IP Port 10. 3. 23. 7 80 64. 23. 1. 76 80 83
 But NAT will save us! Not! u NAT adds complexity to v v v u u u Firewall code Application code Network/security administration Techniques exist to bypass NAT Requires more intelligence in Network IDS/IPS systems Creates bottlenecks in networks 84
But NAT will save us! Not! u NAT adds complexity to v v v u u u Firewall code Application code Network/security administration Techniques exist to bypass NAT Requires more intelligence in Network IDS/IPS systems Creates bottlenecks in networks 84
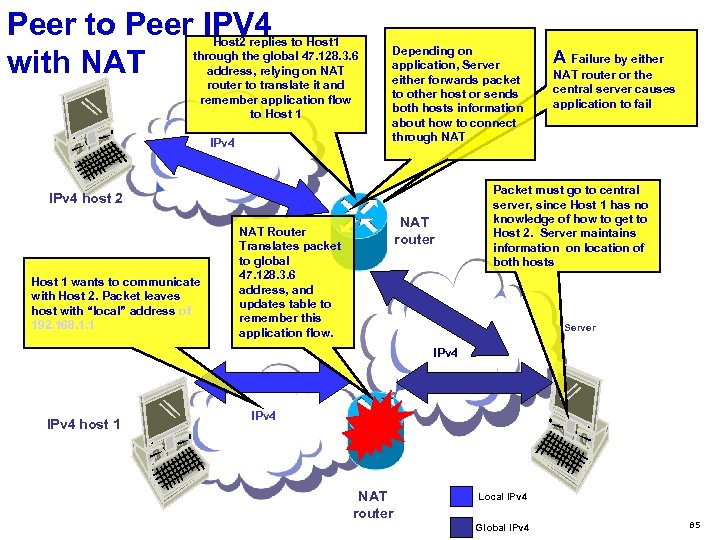 Peer to Peer IPV 4 with NAT Host 2 replies to Host 1 through the global 47. 128. 3. 6 address, relying on NAT router to translate it and remember application flow to Host 1 IPv 4 Depending on application, Server either forwards packet to other host or sends both hosts information about how to connect through NAT IPv 4 host 2 Host 1 wants to communicate with Host 2. Packet leaves host with “local” address of 192. 168. 1. 1 NAT router NAT Router Translates packet to global 47. 128. 3. 6 address, and updates table to remember this application flow. A Failure by either NAT router or the central server causes application to fail Packet must go to central server, since Host 1 has no knowledge of how to get to Host 2. Server maintains information on location of both hosts Server IPv 4 host 1 IPv 4 NAT router Local IPv 4 Global IPv 4 85
Peer to Peer IPV 4 with NAT Host 2 replies to Host 1 through the global 47. 128. 3. 6 address, relying on NAT router to translate it and remember application flow to Host 1 IPv 4 Depending on application, Server either forwards packet to other host or sends both hosts information about how to connect through NAT IPv 4 host 2 Host 1 wants to communicate with Host 2. Packet leaves host with “local” address of 192. 168. 1. 1 NAT router NAT Router Translates packet to global 47. 128. 3. 6 address, and updates table to remember this application flow. A Failure by either NAT router or the central server causes application to fail Packet must go to central server, since Host 1 has no knowledge of how to get to Host 2. Server maintains information on location of both hosts Server IPv 4 host 1 IPv 4 NAT router Local IPv 4 Global IPv 4 85
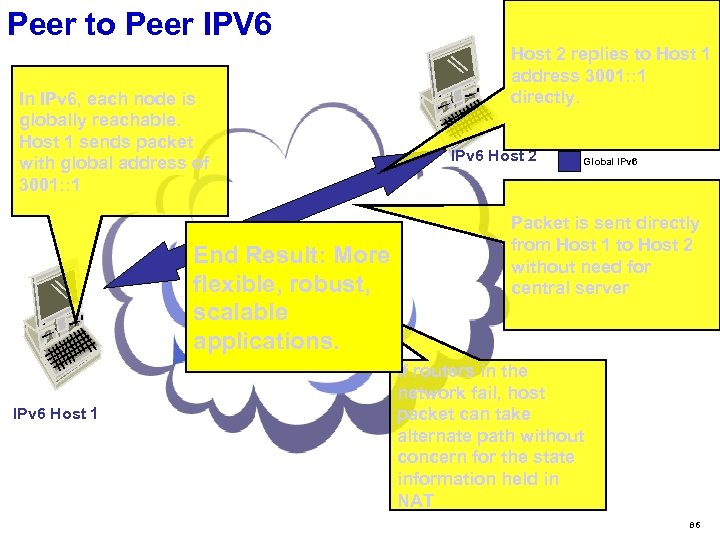 Peer to Peer IPV 6 In IPv 6, each node is globally reachable. Host 1 sends packet with global address of 3001: : 1 End Result: More IPv 6 flexible, robust, scalable applications. IPv 6 Host 1 Host 2 replies to Host 1 address 3001: : 1 directly. IPv 6 Host 2 Global IPv 6 Packet is sent directly from Host 1 to Host 2 without need for central server If routers in the network fail, host packet can take alternate path without concern for the state information held in NAT 86
Peer to Peer IPV 6 In IPv 6, each node is globally reachable. Host 1 sends packet with global address of 3001: : 1 End Result: More IPv 6 flexible, robust, scalable applications. IPv 6 Host 1 Host 2 replies to Host 1 address 3001: : 1 directly. IPv 6 Host 2 Global IPv 6 Packet is sent directly from Host 1 to Host 2 without need for central server If routers in the network fail, host packet can take alternate path without concern for the state information held in NAT 86
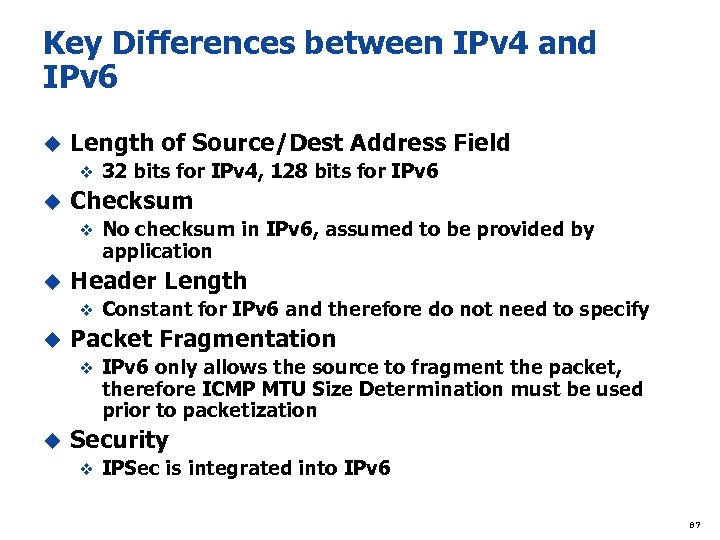 Key Differences between IPv 4 and IPv 6 u Length of Source/Dest Address Field v u Checksum v u Constant for IPv 6 and therefore do not need to specify Packet Fragmentation v u No checksum in IPv 6, assumed to be provided by application Header Length v u 32 bits for IPv 4, 128 bits for IPv 6 only allows the source to fragment the packet, therefore ICMP MTU Size Determination must be used prior to packetization Security v IPSec is integrated into IPv 6 87
Key Differences between IPv 4 and IPv 6 u Length of Source/Dest Address Field v u Checksum v u Constant for IPv 6 and therefore do not need to specify Packet Fragmentation v u No checksum in IPv 6, assumed to be provided by application Header Length v u 32 bits for IPv 4, 128 bits for IPv 6 only allows the source to fragment the packet, therefore ICMP MTU Size Determination must be used prior to packetization Security v IPSec is integrated into IPv 6 87
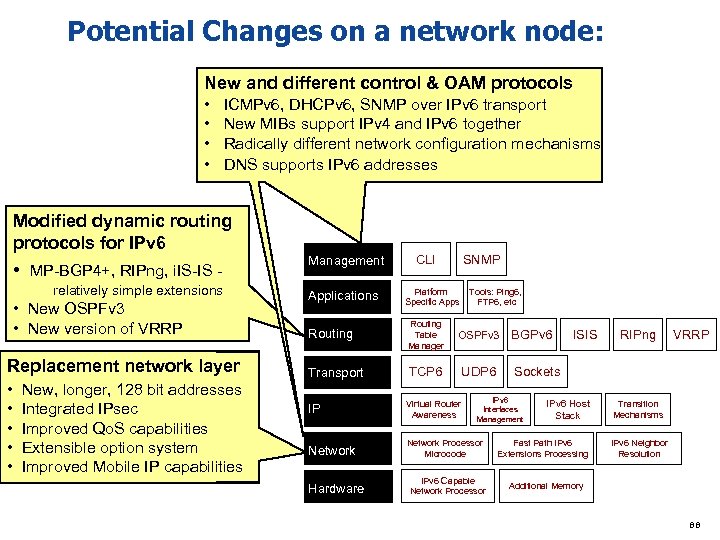 Potential Changes on a network node: New and different control & OAM protocols • ICMPv 6, DHCPv 6, SNMP over IPv 6 transport • New MIBs support IPv 4 and IPv 6 together • Radically different network configuration mechanisms • DNS supports IPv 6 addresses Modified dynamic routing protocols for IPv 6 • MP-BGP 4+, RIPng, i. IS-IS relatively simple extensions • New OSPFv 3 • New version of VRRP Replacement network layer • New, longer, 128 bit addresses • Integrated IPsec • Improved Qo. S capabilities • Extensible option system • Improved Mobile IP capabilities Management Applications CLI SNMP Platform Specific Apps Tools: Ping 6, FTP 6, etc Routing Table Manager OSPFv 3 Transport TCP 6 UDP 6 Virtual Router Awareness Network Processor Microcode IPv 6 Capable Network Processor ISIS RIPng VRRP Sockets IPv 6 Interfaces Management IP Hardware BGPv 6 IPv 6 Host Stack Fast Path IPv 6 Extensions Processing Transition Mechanisms IPv 6 Neighbor Resolution Additional Memory 88
Potential Changes on a network node: New and different control & OAM protocols • ICMPv 6, DHCPv 6, SNMP over IPv 6 transport • New MIBs support IPv 4 and IPv 6 together • Radically different network configuration mechanisms • DNS supports IPv 6 addresses Modified dynamic routing protocols for IPv 6 • MP-BGP 4+, RIPng, i. IS-IS relatively simple extensions • New OSPFv 3 • New version of VRRP Replacement network layer • New, longer, 128 bit addresses • Integrated IPsec • Improved Qo. S capabilities • Extensible option system • Improved Mobile IP capabilities Management Applications CLI SNMP Platform Specific Apps Tools: Ping 6, FTP 6, etc Routing Table Manager OSPFv 3 Transport TCP 6 UDP 6 Virtual Router Awareness Network Processor Microcode IPv 6 Capable Network Processor ISIS RIPng VRRP Sockets IPv 6 Interfaces Management IP Hardware BGPv 6 IPv 6 Host Stack Fast Path IPv 6 Extensions Processing Transition Mechanisms IPv 6 Neighbor Resolution Additional Memory 88
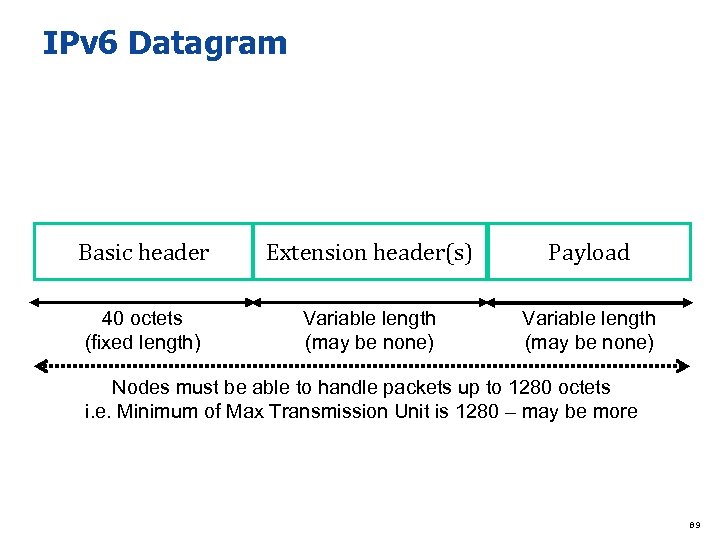 IPv 6 Datagram Basic header Extension header(s) Payload 40 octets (fixed length) Variable length (may be none) Nodes must be able to handle packets up to 1280 octets i. e. Minimum of Max Transmission Unit is 1280 – may be more 89
IPv 6 Datagram Basic header Extension header(s) Payload 40 octets (fixed length) Variable length (may be none) Nodes must be able to handle packets up to 1280 octets i. e. Minimum of Max Transmission Unit is 1280 – may be more 89
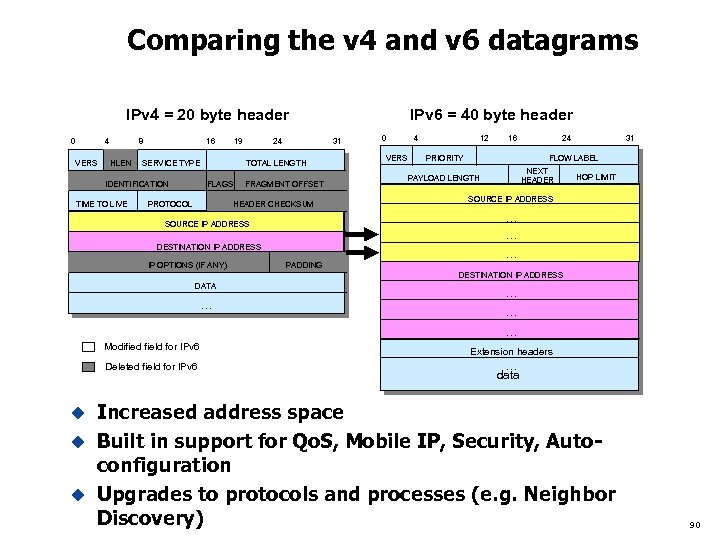 Comparing the v 4 and v 6 datagrams IPv 4 = 20 byte header 0 4 VERS 8 HLEN 16 SERVICE TYPE IDENTIFICATION TIME TO LIVE 19 24 31 TOTAL LENGTH FLAGS PROTOCOL IPv 6 = 40 byte header FRAGMENT OFFSET HEADER CHECKSUM 0 VERS 4 12 16 PRIORITY 24 31 FLOW LABEL NEXT HEADER PAYLOAD LENGTH HOP LIMIT SOURCE IP ADDRESS. . . SOURCE IP ADDRESS . . . DESTINATION IP ADDRESS IP OPTIONS (IF ANY) . . . PADDING DESTINATION IP ADDRESS DATA. . . Modified field for IPv 6 Deleted field for IPv 6 Extension headers. . . data Increased address space u Built in support for Qo. S, Mobile IP, Security, Autoconfiguration u Upgrades to protocols and processes (e. g. Neighbor Discovery) u 90
Comparing the v 4 and v 6 datagrams IPv 4 = 20 byte header 0 4 VERS 8 HLEN 16 SERVICE TYPE IDENTIFICATION TIME TO LIVE 19 24 31 TOTAL LENGTH FLAGS PROTOCOL IPv 6 = 40 byte header FRAGMENT OFFSET HEADER CHECKSUM 0 VERS 4 12 16 PRIORITY 24 31 FLOW LABEL NEXT HEADER PAYLOAD LENGTH HOP LIMIT SOURCE IP ADDRESS. . . SOURCE IP ADDRESS . . . DESTINATION IP ADDRESS IP OPTIONS (IF ANY) . . . PADDING DESTINATION IP ADDRESS DATA. . . Modified field for IPv 6 Deleted field for IPv 6 Extension headers. . . data Increased address space u Built in support for Qo. S, Mobile IP, Security, Autoconfiguration u Upgrades to protocols and processes (e. g. Neighbor Discovery) u 90
 IPv 6 Header Fields • Version: IP version number (4 bits). This field's value is 6 for IPv 6 (and 4 for IPv 4). Note that this field is in the same location as the Version field in the IPv 4 header, making it simple for an IP node to quickly distinguish an IPv 4 packet from an IPv 6 packet. Priority: Enables a source to identify the desired delivery priority of this packet (4 bits). The 4 -bit Priority field in the IPv 6 header enables a source to identify the desired delivery priority of its packets, relative to other packets from the same source. The Priority values are divided into two ranges: Values 0 through 7 are used to specify the priority of traffic for which the source is providing congestion control, i. e. , traffic that "backs off" in response to congestion, such as TCP traffic. Values 8 through 15 are used to specify the priority of traffic that does not back off in response to congestion, e. g. , "real-time" packets being sent at a constant rate. For congestion-controlled traffic, the following Priority values are recommended for particular application categories: 0 Uncharacterized traffic 1 "Filler" traffic (e. g. , netnews) 2 Unattended data transfer (e. g. , email) 3 (Reserved) 4 Attended bulk transfer (e. g. , FTP, HTTP, NFS) 5 (Reserved) 6 Interactive traffic (e. g. , telnet, X) 7 Internet control traffic (e. g. , routing protocols, SNMP) Flow Label: Used by a source to identify associated packets needing the same type of special handling, such as a real -time service between a pair of hosts (24 bits). The 24 -bit Flow Label field in the IPv 6 header may be used by a source to label those packets for which it requests special handling by the IPv 6 routers, such as non-default quality of service or "real-time" service. A flow label is assigned to a flow by the flow's source node. New flow labels must be chosen (pseudo-)randomly and uniformly from the range 1 to FFFFFF hex. The purpose of the random allocation is to make any set of bits within the Flow Label field suitable for use as a hash key by routers, for looking up the state associated with the flow. All packets belonging to the same flow must be sent with the same source address, same destination address, and same non-zero flow label. 91
IPv 6 Header Fields • Version: IP version number (4 bits). This field's value is 6 for IPv 6 (and 4 for IPv 4). Note that this field is in the same location as the Version field in the IPv 4 header, making it simple for an IP node to quickly distinguish an IPv 4 packet from an IPv 6 packet. Priority: Enables a source to identify the desired delivery priority of this packet (4 bits). The 4 -bit Priority field in the IPv 6 header enables a source to identify the desired delivery priority of its packets, relative to other packets from the same source. The Priority values are divided into two ranges: Values 0 through 7 are used to specify the priority of traffic for which the source is providing congestion control, i. e. , traffic that "backs off" in response to congestion, such as TCP traffic. Values 8 through 15 are used to specify the priority of traffic that does not back off in response to congestion, e. g. , "real-time" packets being sent at a constant rate. For congestion-controlled traffic, the following Priority values are recommended for particular application categories: 0 Uncharacterized traffic 1 "Filler" traffic (e. g. , netnews) 2 Unattended data transfer (e. g. , email) 3 (Reserved) 4 Attended bulk transfer (e. g. , FTP, HTTP, NFS) 5 (Reserved) 6 Interactive traffic (e. g. , telnet, X) 7 Internet control traffic (e. g. , routing protocols, SNMP) Flow Label: Used by a source to identify associated packets needing the same type of special handling, such as a real -time service between a pair of hosts (24 bits). The 24 -bit Flow Label field in the IPv 6 header may be used by a source to label those packets for which it requests special handling by the IPv 6 routers, such as non-default quality of service or "real-time" service. A flow label is assigned to a flow by the flow's source node. New flow labels must be chosen (pseudo-)randomly and uniformly from the range 1 to FFFFFF hex. The purpose of the random allocation is to make any set of bits within the Flow Label field suitable for use as a hash key by routers, for looking up the state associated with the flow. All packets belonging to the same flow must be sent with the same source address, same destination address, and same non-zero flow label. 91
 IPv 6 Header Fields (Cont’d) u Payload Length: Length of the payload (the portion of the packet following the u Next Header: Identifies the type of header immediately following the IPv 6 header; u Hop Limit: Specifies the maximum number of hops that a packet may take before it u Source Address: IPv 6 address of the originator of the packet (128 bits). u Destination Address: IPv 6 address of the intended recipient(s) of the packet (128 header), in octets (16 bits). The maximum value in this field is 65, 535; if this field contains zero, it means that the packet contains a payload larger than 64 KB and the actual payload length value is carried in a Jumbo Payload hop-by-hop option. uses the same values as the IPv 4 Protocol field, where applicable (8 bits). The Next Header field can indicate an options header, higher layer protocol, or no protocol above IP. Sample values are listed in next table. is discarded (8 bits). This value is set by the source and decremented by 1 by each node that forwards the packet; the packet is discarded if the Hop Limit reaches zero. The comparable field in IPv 4 is the Time to Live (TTL) field; it was renamed for IPv 6 because the value limits the number of hops, not the amount of time that a packet can stay in the network. bits). 92
IPv 6 Header Fields (Cont’d) u Payload Length: Length of the payload (the portion of the packet following the u Next Header: Identifies the type of header immediately following the IPv 6 header; u Hop Limit: Specifies the maximum number of hops that a packet may take before it u Source Address: IPv 6 address of the originator of the packet (128 bits). u Destination Address: IPv 6 address of the intended recipient(s) of the packet (128 header), in octets (16 bits). The maximum value in this field is 65, 535; if this field contains zero, it means that the packet contains a payload larger than 64 KB and the actual payload length value is carried in a Jumbo Payload hop-by-hop option. uses the same values as the IPv 4 Protocol field, where applicable (8 bits). The Next Header field can indicate an options header, higher layer protocol, or no protocol above IP. Sample values are listed in next table. is discarded (8 bits). This value is set by the source and decremented by 1 by each node that forwards the packet; the packet is discarded if the Hop Limit reaches zero. The comparable field in IPv 4 is the Time to Live (TTL) field; it was renamed for IPv 6 because the value limits the number of hops, not the amount of time that a packet can stay in the network. bits). 92
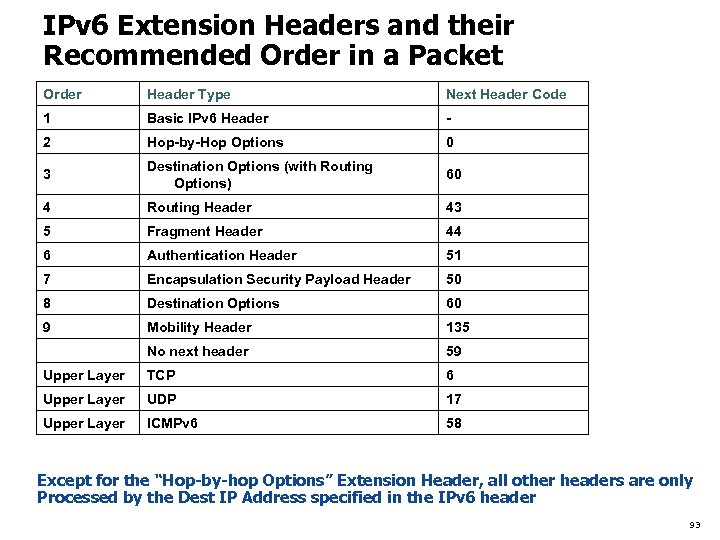 IPv 6 Extension Headers and their Recommended Order in a Packet Order Header Type Next Header Code 1 Basic IPv 6 Header - 2 Hop-by-Hop Options 0 3 Destination Options (with Routing Options) 60 4 Routing Header 43 5 Fragment Header 44 6 Authentication Header 51 7 Encapsulation Security Payload Header 50 8 Destination Options 60 9 Mobility Header 135 No next header 59 Upper Layer TCP 6 Upper Layer UDP 17 Upper Layer ICMPv 6 58 Except for the “Hop-by-hop Options” Extension Header, all other headers are only Processed by the Dest IP Address specified in the IPv 6 header 93
IPv 6 Extension Headers and their Recommended Order in a Packet Order Header Type Next Header Code 1 Basic IPv 6 Header - 2 Hop-by-Hop Options 0 3 Destination Options (with Routing Options) 60 4 Routing Header 43 5 Fragment Header 44 6 Authentication Header 51 7 Encapsulation Security Payload Header 50 8 Destination Options 60 9 Mobility Header 135 No next header 59 Upper Layer TCP 6 Upper Layer UDP 17 Upper Layer ICMPv 6 58 Except for the “Hop-by-hop Options” Extension Header, all other headers are only Processed by the Dest IP Address specified in the IPv 6 header 93
 IPv 6 Extension Headers – Their meanings u Each extension header typically occurs only once within a given packet, except for the destination header, as explained on the following page. u Hop-by-Hop Options Header When present, this header carries options that are examined by intermediate nodes along the forwarding path. It must be the first extension header after the initial IPv 6 header. Since this header is read by all routers along the path, it is useful for transmitting management information or debugging commands to routers. One currently defined application of the hop-by-hop extension header is the Router Alert option, which informs routers that the packet should be processed completely by a router before it is forwarded to the next hop. An example of such a packet is an RSVP's resource reservation message. u Destination Options Headers There are two variations of this header, each with a different position in the packet. The first incidence of this field is for carrying information to the first destination listed in the IPv 6 address field. This header can also be read by a subsequent destination listed in the source routing header address fields. The second incidence of this header is used for optional information that is only to be read by the final destination. For efficiency, the first variation is typically located towards the front of the header chain, directly after the hop-by-hop header (if any). The second variation is relegated to a position at the end of the extension header chain, which is typically the last IPv 6 optional header before transport and payload. u Source Routing Header The IPv 6 routing extension header is an incarnation of the source routing function supported currently by IPv 4. This optional header allows a source node to specify a list of IP addresses that dictate what path a packet will traverse. IETF RFC 1883 defines a version of this routing header called "Type 0, " which gives a sending node a great deal of control over each packet's route. Type 0 routing headers contain a 24 -bit field that indicates how intermediate nodes may forward a packet to the next address in the routing header. Each bit in the 24 -bit field indicates whether the next corresponding destination address must be a neighbor of the preceding address (1 = strict, must be a neighbor; 0 = loose, need not be a neighbor). u Fragmentation Header The IPv 6 fragmentation header contains fields that identify a group of fragments as a packet and assigns them sequence numbers. Because IPv 6 routers do not fragment packets between end nodes, the responsibility for sending the correct size packet is with the source node, which needs to determine the Maximum Transmission Unit (MTU) of the links in the end-to-end path. For instance, if two FDDI networks with 4500 -byte MTUs are connected by an Ethernet with an MTU of 1500, then the source station must send packets that are no larger than 1500. 94
IPv 6 Extension Headers – Their meanings u Each extension header typically occurs only once within a given packet, except for the destination header, as explained on the following page. u Hop-by-Hop Options Header When present, this header carries options that are examined by intermediate nodes along the forwarding path. It must be the first extension header after the initial IPv 6 header. Since this header is read by all routers along the path, it is useful for transmitting management information or debugging commands to routers. One currently defined application of the hop-by-hop extension header is the Router Alert option, which informs routers that the packet should be processed completely by a router before it is forwarded to the next hop. An example of such a packet is an RSVP's resource reservation message. u Destination Options Headers There are two variations of this header, each with a different position in the packet. The first incidence of this field is for carrying information to the first destination listed in the IPv 6 address field. This header can also be read by a subsequent destination listed in the source routing header address fields. The second incidence of this header is used for optional information that is only to be read by the final destination. For efficiency, the first variation is typically located towards the front of the header chain, directly after the hop-by-hop header (if any). The second variation is relegated to a position at the end of the extension header chain, which is typically the last IPv 6 optional header before transport and payload. u Source Routing Header The IPv 6 routing extension header is an incarnation of the source routing function supported currently by IPv 4. This optional header allows a source node to specify a list of IP addresses that dictate what path a packet will traverse. IETF RFC 1883 defines a version of this routing header called "Type 0, " which gives a sending node a great deal of control over each packet's route. Type 0 routing headers contain a 24 -bit field that indicates how intermediate nodes may forward a packet to the next address in the routing header. Each bit in the 24 -bit field indicates whether the next corresponding destination address must be a neighbor of the preceding address (1 = strict, must be a neighbor; 0 = loose, need not be a neighbor). u Fragmentation Header The IPv 6 fragmentation header contains fields that identify a group of fragments as a packet and assigns them sequence numbers. Because IPv 6 routers do not fragment packets between end nodes, the responsibility for sending the correct size packet is with the source node, which needs to determine the Maximum Transmission Unit (MTU) of the links in the end-to-end path. For instance, if two FDDI networks with 4500 -byte MTUs are connected by an Ethernet with an MTU of 1500, then the source station must send packets that are no larger than 1500. 94
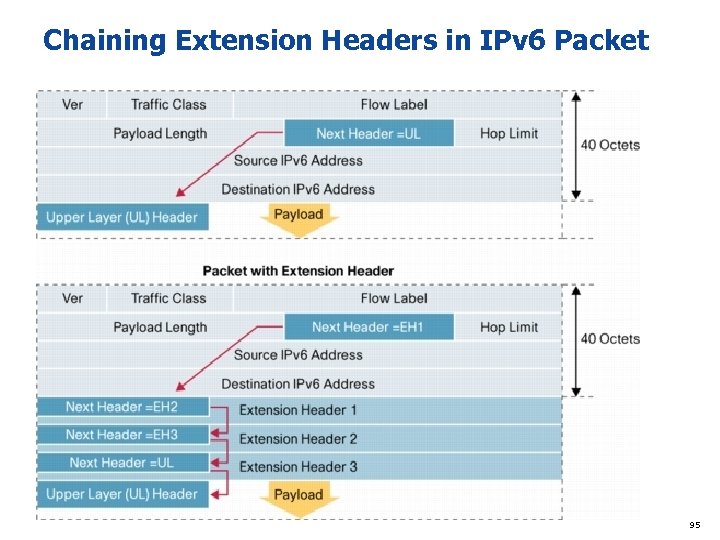 Chaining Extension Headers in IPv 6 Packet Figure 2. Chaining Extension Headers in IPv 6 Packets 95
Chaining Extension Headers in IPv 6 Packet Figure 2. Chaining Extension Headers in IPv 6 Packets 95
 IPv 6 Number Allocation ARIN (ww. arin. net) is the authority for issuing IP Addresses u IPv 4 Model v v Everyone and their brother 'owns' IP ranges Too Many Routes Big Routing Tables Complex Routes - Multipath 96
IPv 6 Number Allocation ARIN (ww. arin. net) is the authority for issuing IP Addresses u IPv 4 Model v v Everyone and their brother 'owns' IP ranges Too Many Routes Big Routing Tables Complex Routes - Multipath 96
 IPv 6 Number Allocation ARIN (ww. arin. net) is the authority for issuing IP Addresses u IPv 6 Model v Addresses “leased” from the ISP. No longer 'owned' u v Global => Regional => Local => You Forces good summarization u u v Smaller number of routes = smaller routing tables Site Multihoming in IPv 6 http: //www. ietf. org/html. charters/multi 6 -charter. html Has renumbering implications making it easer to change numbers Multihoming has created some challenges for but is currently being addressed This is a major shift in IP addressing paradigms! 97
IPv 6 Number Allocation ARIN (ww. arin. net) is the authority for issuing IP Addresses u IPv 6 Model v Addresses “leased” from the ISP. No longer 'owned' u v Global => Regional => Local => You Forces good summarization u u v Smaller number of routes = smaller routing tables Site Multihoming in IPv 6 http: //www. ietf. org/html. charters/multi 6 -charter. html Has renumbering implications making it easer to change numbers Multihoming has created some challenges for but is currently being addressed This is a major shift in IP addressing paradigms! 97
 What does an IPv 6 address look like? FEDC: BA 98: 7654: 3210: FEDC: BA 98: 7654: 3210 u Representation v x: x: x u u x = 0000 to FFFF (x: x = The Entire IPv 4 Internet) 0000: 0000: 0000 v v Suppress leading zeros u v That is 40 Character to type 1080: 0: 8: 800: 200 C: 417 A Suppress multiple zeros u 1080: : 8: 800: 200 C: 417 A 98
What does an IPv 6 address look like? FEDC: BA 98: 7654: 3210: FEDC: BA 98: 7654: 3210 u Representation v x: x: x u u x = 0000 to FFFF (x: x = The Entire IPv 4 Internet) 0000: 0000: 0000 v v Suppress leading zeros u v That is 40 Character to type 1080: 0: 8: 800: 200 C: 417 A Suppress multiple zeros u 1080: : 8: 800: 200 C: 417 A 98
 What does an IPv 6 address look like? The Extreme Case v v 0: 0: 0 : : What does not work v v u 1080: 0: 8: 0: 0: 417 A 1080: : 8: : 417 A Instead v v 1080: : 8: 0: 0: 417 A 1080: 0: 8: : 417 A 99
What does an IPv 6 address look like? The Extreme Case v v 0: 0: 0 : : What does not work v v u 1080: 0: 8: 0: 0: 417 A 1080: : 8: : 417 A Instead v v 1080: : 8: 0: 0: 417 A 1080: 0: 8: : 417 A 99
 How do you use an IPv 6 address in a URL? u Use the Domain Name! v u www. google. com But if you can't then. . . v v v v Use [ ] http: //[FEDC: BA 98: 7654: 3210: FEDC: BA 98: 7654: 3210]: http: //[1080: 0: 8: 800: 200 C: 417 A]/index. html http: //[3 ffe: 2 a 00: 100: 7031: : 1] http: //[1080: : 8: 800: 200 C: 417 A]/foo http: //[: : 192. 9. 5. 5]/ipng http: //[: : FFFF: 129. 144. 52. 38]: 80/index. html http: //[2010: 836 B: 4179: : 836 B: 4179] 100
How do you use an IPv 6 address in a URL? u Use the Domain Name! v u www. google. com But if you can't then. . . v v v v Use [ ] http: //[FEDC: BA 98: 7654: 3210: FEDC: BA 98: 7654: 3210]: http: //[1080: 0: 8: 800: 200 C: 417 A]/index. html http: //[3 ffe: 2 a 00: 100: 7031: : 1] http: //[1080: : 8: 800: 200 C: 417 A]/foo http: //[: : 192. 9. 5. 5]/ipng http: //[: : FFFF: 129. 144. 52. 38]: 80/index. html http: //[2010: 836 B: 4179: : 836 B: 4179] 100
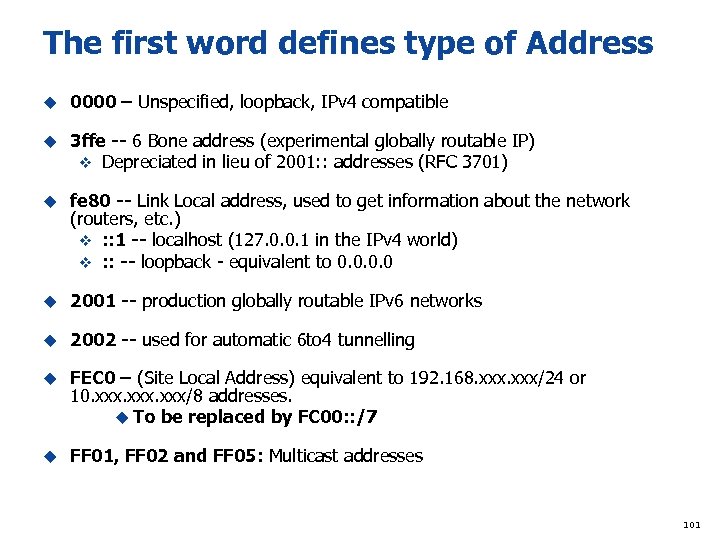 The first word defines type of Address u 0000 – Unspecified, loopback, IPv 4 compatible u 3 ffe -- 6 Bone address (experimental globally routable IP) v Depreciated in lieu of 2001: : addresses (RFC 3701) u fe 80 -- Link Local address, used to get information about the network (routers, etc. ) v : : 1 -- localhost (127. 0. 0. 1 in the IPv 4 world) v : : -- loopback - equivalent to 0. 0 u 2001 -- production globally routable IPv 6 networks u 2002 -- used for automatic 6 to 4 tunnelling u FEC 0 – (Site Local Address) equivalent to 192. 168. xxx/24 or 10. xxx/8 addresses. u To be replaced by FC 00: : /7 u FF 01, FF 02 and FF 05: Multicast addresses 101
The first word defines type of Address u 0000 – Unspecified, loopback, IPv 4 compatible u 3 ffe -- 6 Bone address (experimental globally routable IP) v Depreciated in lieu of 2001: : addresses (RFC 3701) u fe 80 -- Link Local address, used to get information about the network (routers, etc. ) v : : 1 -- localhost (127. 0. 0. 1 in the IPv 4 world) v : : -- loopback - equivalent to 0. 0 u 2001 -- production globally routable IPv 6 networks u 2002 -- used for automatic 6 to 4 tunnelling u FEC 0 – (Site Local Address) equivalent to 192. 168. xxx/24 or 10. xxx/8 addresses. u To be replaced by FC 00: : /7 u FF 01, FF 02 and FF 05: Multicast addresses 101
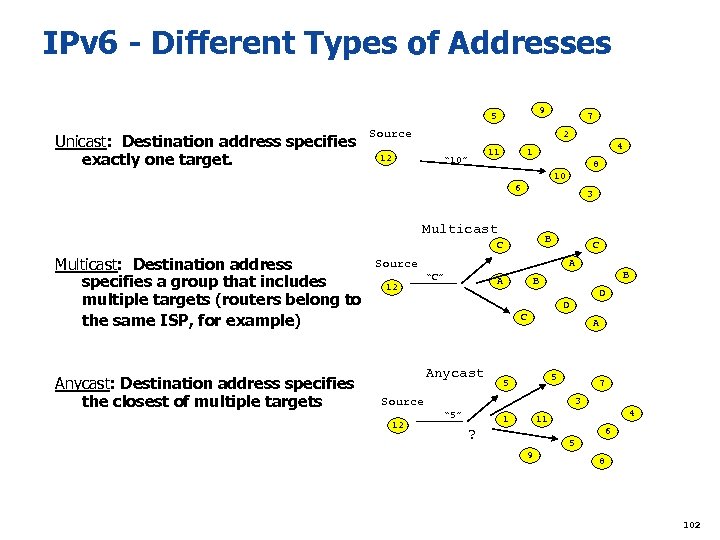 IPv 6 - Different Types of Addresses 9 5 Unicast: Destination address specifies exactly one target. 7 Source 2 12 “ 10” 11 4 1 8 10 6 3 Multicast B C Multicast: Destination address specifies a group that includes multiple targets (routers belong to the same ISP, for example) Anycast: Destination address specifies the closest of multiple targets C Source 12 A “C” A B B D D C Anycast A 5 5 7 Source 12 3 “ 5” 1 4 11 ? 6 5 9 8 102
IPv 6 - Different Types of Addresses 9 5 Unicast: Destination address specifies exactly one target. 7 Source 2 12 “ 10” 11 4 1 8 10 6 3 Multicast B C Multicast: Destination address specifies a group that includes multiple targets (routers belong to the same ISP, for example) Anycast: Destination address specifies the closest of multiple targets C Source 12 A “C” A B B D D C Anycast A 5 5 7 Source 12 3 “ 5” 1 4 11 ? 6 5 9 8 102
 IPv 6 Unicast Address Types u These are the global provider based unicast address, u the neutral-interconnect unicast address, the NSAP address, u the IPX hierarchical address, u the site-local-use address, u the link-local-use address, a u And the IPv 4 -capable host address. 103
IPv 6 Unicast Address Types u These are the global provider based unicast address, u the neutral-interconnect unicast address, the NSAP address, u the IPX hierarchical address, u the site-local-use address, u the link-local-use address, a u And the IPv 4 -capable host address. 103
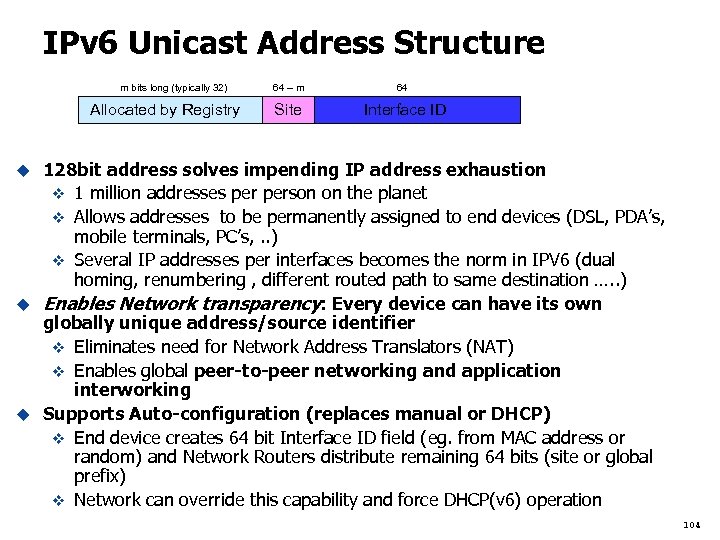 IPv 6 Unicast Address Structure m bits long (typically 32) Allocated by Registry 64 – m 64 Site Interface ID 128 bit address solves impending IP address exhaustion v 1 million addresses person on the planet v Allows addresses to be permanently assigned to end devices (DSL, PDA’s, mobile terminals, PC’s, . . ) v Several IP addresses per interfaces becomes the norm in IPV 6 (dual homing, renumbering , different routed path to same destination …. . ) u Enables Network transparency: Every device can have its own globally unique address/source identifier v Eliminates need for Network Address Translators (NAT) v Enables global peer-to-peer networking and application interworking u Supports Auto-configuration (replaces manual or DHCP) v End device creates 64 bit Interface ID field (eg. from MAC address or random) and Network Routers distribute remaining 64 bits (site or global prefix) v Network can override this capability and force DHCP(v 6) operation u 104
IPv 6 Unicast Address Structure m bits long (typically 32) Allocated by Registry 64 – m 64 Site Interface ID 128 bit address solves impending IP address exhaustion v 1 million addresses person on the planet v Allows addresses to be permanently assigned to end devices (DSL, PDA’s, mobile terminals, PC’s, . . ) v Several IP addresses per interfaces becomes the norm in IPV 6 (dual homing, renumbering , different routed path to same destination …. . ) u Enables Network transparency: Every device can have its own globally unique address/source identifier v Eliminates need for Network Address Translators (NAT) v Enables global peer-to-peer networking and application interworking u Supports Auto-configuration (replaces manual or DHCP) v End device creates 64 bit Interface ID field (eg. from MAC address or random) and Network Routers distribute remaining 64 bits (site or global prefix) v Network can override this capability and force DHCP(v 6) operation u 104
 IPv 6 Address – Provider-based Unicast Address Scheme One of the goals of the IPv 6 address format is to accommodate many different types of addresses. The beginning of an address contains a three- to ten-bit Format Prefix defining the general address type (Table 2); the remaining bits contain the actual host address, in a format specific to the indicated address type. | 3 | 5 bits | n bits | 56 -n bits | 64 bits | +------------+--------+---------+ |010| Registry. ID | Provider. ID | Subscriber. ID | Intra-Subscriber | +------------+---------+---------+ FIGURE 2. Provider-Based Unicast Address Format (from RFC 1884). For example, the Provider-Based Unicast Address is an IPv 6 address that might be assigned by an Internet service provider (ISP) to a customer. This type of address contains a number of subfields, including (Figure 2): • Format Prefix: Indicates type of address as Provider-Based Unicast. Always 3 bits, coded "010. " • Registry Identifier: Identifies the Internet address registry from which this ISP obtains addresses. A 5 -bit value indicating the IANA Internet Assigned Number Authority or one of the three Regional Registries, namely the Internet Network Information Center (Inter. NIC), Rèseaux IP Europèens Network Coordination Center (RIPE NCC), or Asia-Pacific Network Information Center (APNIC). In the future, national registries may also be accommodated. • Provider Identifier: Identifies the ISP; this field contains the address block assigned to this ISP by the address registry authority. • Subscriber Identifier: Identifies the ISP's subscriber; this field contains the address assigned to this subscriber by the ISP. The Provider. ID and Subscriber. ID fields together are 56 bits in length. • Intra-Subscriber: Contains the portion of the address assigned and managed by the subscriber. A 64 -bit value, suggested to comprise a 16 -bit subnetwork identifier and a 48 -bit interface identifier (such as an IEEE MAC address). 105
IPv 6 Address – Provider-based Unicast Address Scheme One of the goals of the IPv 6 address format is to accommodate many different types of addresses. The beginning of an address contains a three- to ten-bit Format Prefix defining the general address type (Table 2); the remaining bits contain the actual host address, in a format specific to the indicated address type. | 3 | 5 bits | n bits | 56 -n bits | 64 bits | +------------+--------+---------+ |010| Registry. ID | Provider. ID | Subscriber. ID | Intra-Subscriber | +------------+---------+---------+ FIGURE 2. Provider-Based Unicast Address Format (from RFC 1884). For example, the Provider-Based Unicast Address is an IPv 6 address that might be assigned by an Internet service provider (ISP) to a customer. This type of address contains a number of subfields, including (Figure 2): • Format Prefix: Indicates type of address as Provider-Based Unicast. Always 3 bits, coded "010. " • Registry Identifier: Identifies the Internet address registry from which this ISP obtains addresses. A 5 -bit value indicating the IANA Internet Assigned Number Authority or one of the three Regional Registries, namely the Internet Network Information Center (Inter. NIC), Rèseaux IP Europèens Network Coordination Center (RIPE NCC), or Asia-Pacific Network Information Center (APNIC). In the future, national registries may also be accommodated. • Provider Identifier: Identifies the ISP; this field contains the address block assigned to this ISP by the address registry authority. • Subscriber Identifier: Identifies the ISP's subscriber; this field contains the address assigned to this subscriber by the ISP. The Provider. ID and Subscriber. ID fields together are 56 bits in length. • Intra-Subscriber: Contains the portion of the address assigned and managed by the subscriber. A 64 -bit value, suggested to comprise a 16 -bit subnetwork identifier and a 48 -bit interface identifier (such as an IEEE MAC address). 105
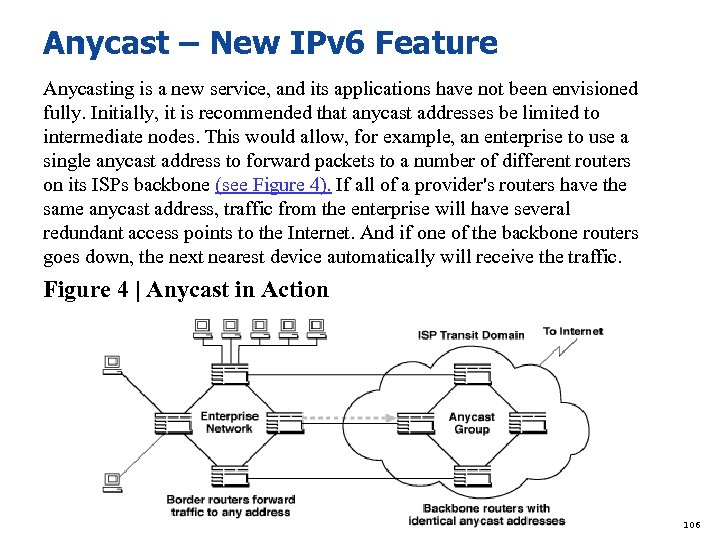 Anycast – New IPv 6 Feature Anycasting is a new service, and its applications have not been envisioned fully. Initially, it is recommended that anycast addresses be limited to intermediate nodes. This would allow, for example, an enterprise to use a single anycast address to forward packets to a number of different routers on its ISPs backbone (see Figure 4). If all of a provider's routers have the same anycast address, traffic from the enterprise will have several redundant access points to the Internet. And if one of the backbone routers goes down, the next nearest device automatically will receive the traffic. Figure 4 | Anycast in Action 106
Anycast – New IPv 6 Feature Anycasting is a new service, and its applications have not been envisioned fully. Initially, it is recommended that anycast addresses be limited to intermediate nodes. This would allow, for example, an enterprise to use a single anycast address to forward packets to a number of different routers on its ISPs backbone (see Figure 4). If all of a provider's routers have the same anycast address, traffic from the enterprise will have several redundant access points to the Internet. And if one of the backbone routers goes down, the next nearest device automatically will receive the traffic. Figure 4 | Anycast in Action 106
 IPv 4 -compatible IPv 6 Address u Another particularly important address type is the one that indicates an IPv 4 address. With over sixteen million hosts using 32 -bit addresses, the public Internet must continue to accommodate IPv 4 addresses even as it slowly migrates to IPv 6 and IPv 6 addressing, u IPv 4 addresses are carried in a 128 -bit IPv 6 address that begins with 80 zeros (0: 0: 0). The next 16 -bit block contains the compatibility bits, which indicate the way in which the host/router handles IPv 4 and IPv 6 addresses. If the device can handle either IPv 4 or IPv 6 addresses, the compatibility bits are all set to zero (0) and this is termed an IPv 4 -compatible IPv 6 address; if the address represents an IPv 4 -only node, the compatibility bits are all set to one (0 x. FFFF) and the address is termed an IPv 4 -mapped IPv 6 address. The final 32 bits contain a 32 -bit IPv 4 address in dotted decimal form. 107
IPv 4 -compatible IPv 6 Address u Another particularly important address type is the one that indicates an IPv 4 address. With over sixteen million hosts using 32 -bit addresses, the public Internet must continue to accommodate IPv 4 addresses even as it slowly migrates to IPv 6 and IPv 6 addressing, u IPv 4 addresses are carried in a 128 -bit IPv 6 address that begins with 80 zeros (0: 0: 0). The next 16 -bit block contains the compatibility bits, which indicate the way in which the host/router handles IPv 4 and IPv 6 addresses. If the device can handle either IPv 4 or IPv 6 addresses, the compatibility bits are all set to zero (0) and this is termed an IPv 4 -compatible IPv 6 address; if the address represents an IPv 4 -only node, the compatibility bits are all set to one (0 x. FFFF) and the address is termed an IPv 4 -mapped IPv 6 address. The final 32 bits contain a 32 -bit IPv 4 address in dotted decimal form. 107
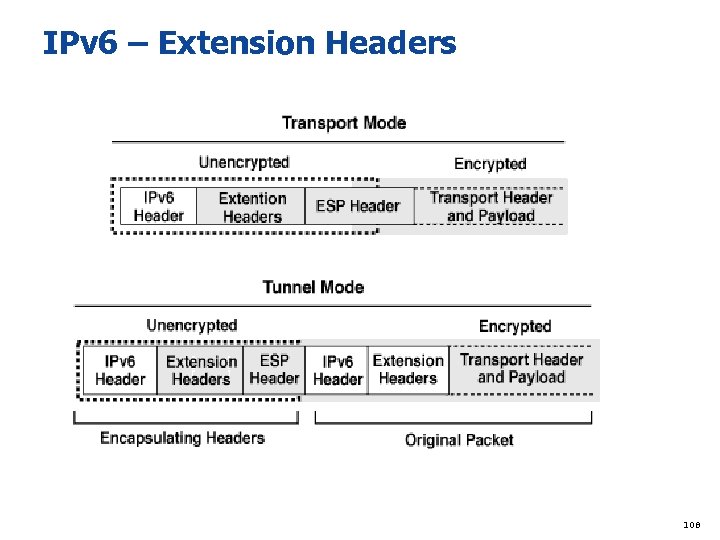 IPv 6 – Extension Headers 108
IPv 6 – Extension Headers 108
 IPv 6 Transition Mechanisms u It is generally accepted that IPv 4 and IPv 6 will co-exist for many years u IPv 6 transition mechanisms designed to enable a functional co-existence of IPv 4 and IPv 6 u Can add complexity and new security implications 109
IPv 6 Transition Mechanisms u It is generally accepted that IPv 4 and IPv 6 will co-exist for many years u IPv 6 transition mechanisms designed to enable a functional co-existence of IPv 4 and IPv 6 u Can add complexity and new security implications 109
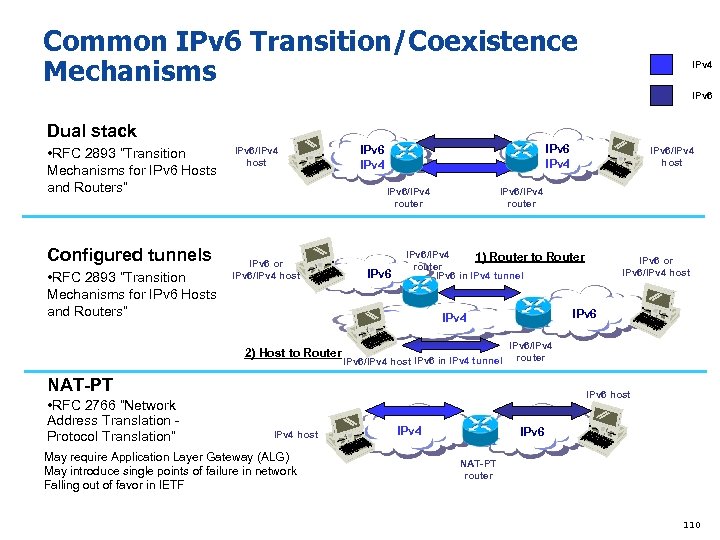 Common IPv 6 Transition/Coexistence Mechanisms IPv 4 IPv 6 Dual stack • RFC 2893 “Transition Mechanisms for IPv 6 Hosts and Routers” Configured tunnels • RFC 2893 “Transition Mechanisms for IPv 6 Hosts and Routers” IPv 6/IPv 4 host IPv 6 IPv 4 IPv 6/IPv 4 router IPv 6 or IPv 6/IPv 4 host IPv 6/IPv 4 router IPv 6/IPv 4 1) Router to Router router IPv 6 in IPv 4 tunnel IPv 6/IPv 4 host IPv 6 in IPv 4 tunnel IPv 6/IPv 4 router NAT-PT • RFC 2766 “Network Address Translation - Protocol Translation” IPv 6 or IPv 6/IPv 4 host IPv 6 IPv 4 2) Host to Router IPv 6/IPv 4 host IPv 6 host IPv 4 host May require Application Layer Gateway (ALG) May introduce single points of failure in network Falling out of favor in IETF IPv 4 IPv 6 NAT-PT router 110
Common IPv 6 Transition/Coexistence Mechanisms IPv 4 IPv 6 Dual stack • RFC 2893 “Transition Mechanisms for IPv 6 Hosts and Routers” Configured tunnels • RFC 2893 “Transition Mechanisms for IPv 6 Hosts and Routers” IPv 6/IPv 4 host IPv 6 IPv 4 IPv 6/IPv 4 router IPv 6 or IPv 6/IPv 4 host IPv 6/IPv 4 router IPv 6/IPv 4 1) Router to Router router IPv 6 in IPv 4 tunnel IPv 6/IPv 4 host IPv 6 in IPv 4 tunnel IPv 6/IPv 4 router NAT-PT • RFC 2766 “Network Address Translation - Protocol Translation” IPv 6 or IPv 6/IPv 4 host IPv 6 IPv 4 2) Host to Router IPv 6/IPv 4 host IPv 6 host IPv 4 host May require Application Layer Gateway (ALG) May introduce single points of failure in network Falling out of favor in IETF IPv 4 IPv 6 NAT-PT router 110
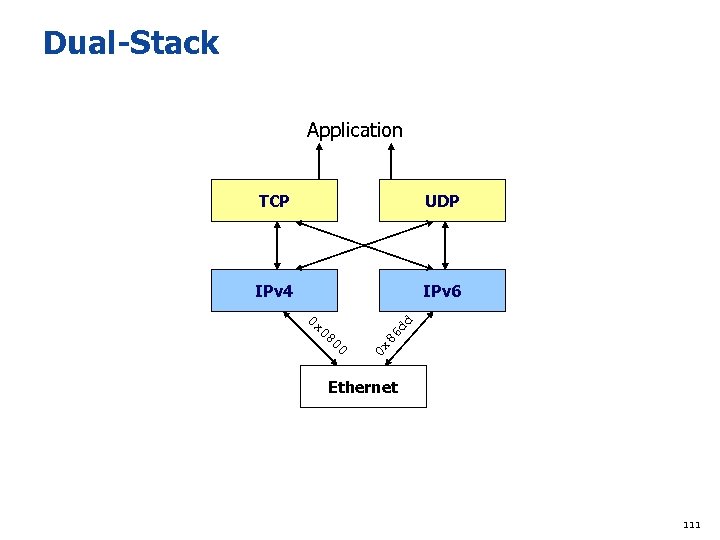 Dual-Stack Application TCP UDP IPv 4 IPv 6 0 x 00 86 dd 0 x 08 Ethernet 111
Dual-Stack Application TCP UDP IPv 4 IPv 6 0 x 00 86 dd 0 x 08 Ethernet 111
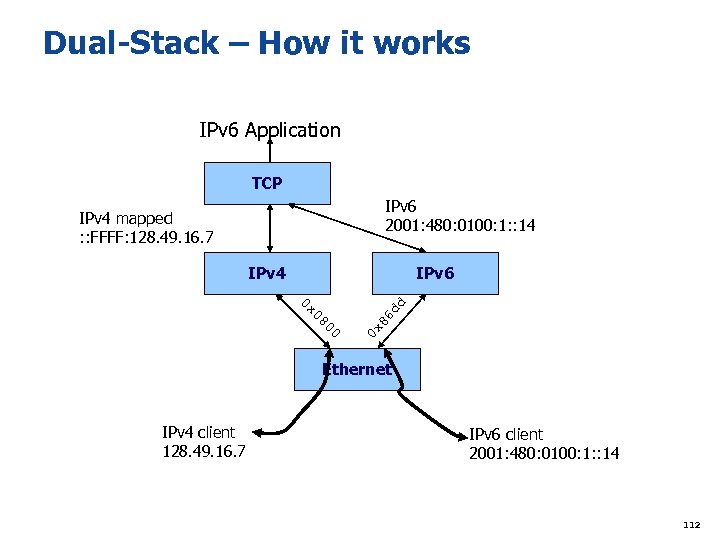 Dual-Stack – How it works IPv 6 Application TCP IPv 6 2001: 480: 0100: 1: : 14 IPv 4 mapped : : FFFF: 128. 49. 16. 7 IPv 4 IPv 6 0 x 00 86 dd 0 x 08 Ethernet IPv 4 client 128. 49. 16. 7 IPv 6 client 2001: 480: 0100: 1: : 14 112
Dual-Stack – How it works IPv 6 Application TCP IPv 6 2001: 480: 0100: 1: : 14 IPv 4 mapped : : FFFF: 128. 49. 16. 7 IPv 4 IPv 6 0 x 00 86 dd 0 x 08 Ethernet IPv 4 client 128. 49. 16. 7 IPv 6 client 2001: 480: 0100: 1: : 14 112
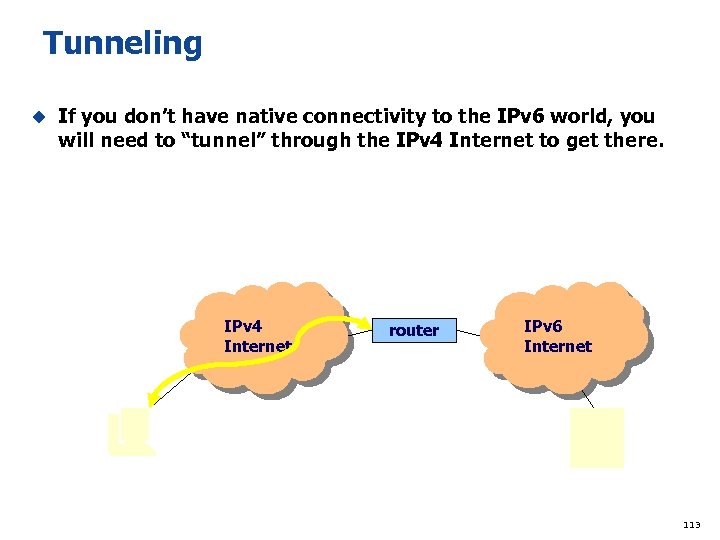 Tunneling u If you don’t have native connectivity to the IPv 6 world, you will need to “tunnel” through the IPv 4 Internet to get there. IPv 4 Internet router IPv 6 Internet 113
Tunneling u If you don’t have native connectivity to the IPv 6 world, you will need to “tunnel” through the IPv 4 Internet to get there. IPv 4 Internet router IPv 6 Internet 113
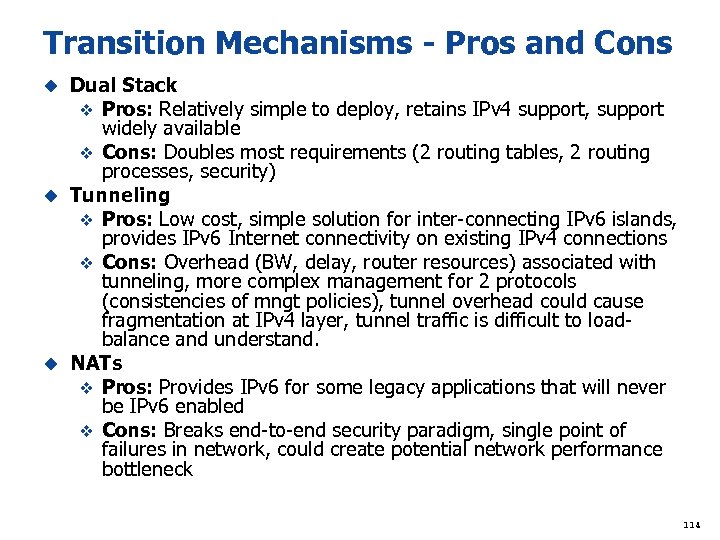 Transition Mechanisms - Pros and Cons Dual Stack v Pros: Relatively simple to deploy, retains IPv 4 support, support widely available v Cons: Doubles most requirements (2 routing tables, 2 routing processes, security) u Tunneling v Pros: Low cost, simple solution for inter-connecting IPv 6 islands, provides IPv 6 Internet connectivity on existing IPv 4 connections v Cons: Overhead (BW, delay, router resources) associated with tunneling, more complex management for 2 protocols (consistencies of mngt policies), tunnel overhead could cause fragmentation at IPv 4 layer, tunnel traffic is difficult to loadbalance and understand. u NATs v Pros: Provides IPv 6 for some legacy applications that will never be IPv 6 enabled v Cons: Breaks end-to-end security paradigm, single point of failures in network, could create potential network performance bottleneck u 114
Transition Mechanisms - Pros and Cons Dual Stack v Pros: Relatively simple to deploy, retains IPv 4 support, support widely available v Cons: Doubles most requirements (2 routing tables, 2 routing processes, security) u Tunneling v Pros: Low cost, simple solution for inter-connecting IPv 6 islands, provides IPv 6 Internet connectivity on existing IPv 4 connections v Cons: Overhead (BW, delay, router resources) associated with tunneling, more complex management for 2 protocols (consistencies of mngt policies), tunnel overhead could cause fragmentation at IPv 4 layer, tunnel traffic is difficult to loadbalance and understand. u NATs v Pros: Provides IPv 6 for some legacy applications that will never be IPv 6 enabled v Cons: Breaks end-to-end security paradigm, single point of failures in network, could create potential network performance bottleneck u 114
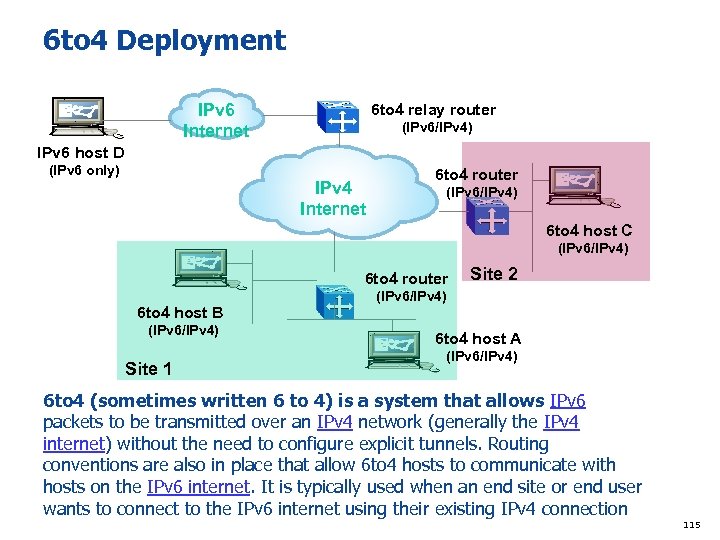 6 to 4 Deployment IPv 6 Internet 6 to 4 relay router (IPv 6/IPv 4) IPv 6 host D (IPv 6 only) IPv 4 Internet 6 to 4 router (IPv 6/IPv 4) 6 to 4 host C (IPv 6/IPv 4) 6 to 4 router 6 to 4 host B (IPv 6/IPv 4) Site 1 Site 2 (IPv 6/IPv 4) 6 to 4 host A (IPv 6/IPv 4) 6 to 4 (sometimes written 6 to 4) is a system that allows IPv 6 packets to be transmitted over an IPv 4 network (generally the IPv 4 internet) without the need to configure explicit tunnels. Routing conventions are also in place that allow 6 to 4 hosts to communicate with hosts on the IPv 6 internet. It is typically used when an end site or end user wants to connect to the IPv 6 internet using their existing IPv 4 connection 115
6 to 4 Deployment IPv 6 Internet 6 to 4 relay router (IPv 6/IPv 4) IPv 6 host D (IPv 6 only) IPv 4 Internet 6 to 4 router (IPv 6/IPv 4) 6 to 4 host C (IPv 6/IPv 4) 6 to 4 router 6 to 4 host B (IPv 6/IPv 4) Site 1 Site 2 (IPv 6/IPv 4) 6 to 4 host A (IPv 6/IPv 4) 6 to 4 (sometimes written 6 to 4) is a system that allows IPv 6 packets to be transmitted over an IPv 4 network (generally the IPv 4 internet) without the need to configure explicit tunnels. Routing conventions are also in place that allow 6 to 4 hosts to communicate with hosts on the IPv 6 internet. It is typically used when an end site or end user wants to connect to the IPv 6 internet using their existing IPv 4 connection 115
 6 to 4 Functions u 6 to 4 performs three functions: u Assigns a block of IPv 6 address space to any host or network that has a global IPv 4 address. u Encapsulates IPv 6 packets inside IPv 4 packets for transmission over an IPv 4 network. u Routes traffic between 6 to 4 and "native" IPv 6 networks. 116
6 to 4 Functions u 6 to 4 performs three functions: u Assigns a block of IPv 6 address space to any host or network that has a global IPv 4 address. u Encapsulates IPv 6 packets inside IPv 4 packets for transmission over an IPv 4 network. u Routes traffic between 6 to 4 and "native" IPv 6 networks. 116
 6 to 4 Address Block Allocation u For any 32 -bit global IPv 4 address that is assigned to a host, a 48 -bit 6 to 4 IPv 6 prefix can be constructed for use by that host (and if applicable the network behind it) by prepending 2002 (hex) to the IPv 4 address. u IPv 4 addresses use dot-decimal notation while IPv 6 addresses use hexadecimal notation. Thus for the global IPv 4 address 207. 142. 131. 202, the corresponding 6 to 4 prefix would be 2002: CF 8 E: 83 CA: : /48. This gives a total prefix length of 48 bits, which is the same as an end site is the amount allocated under normal IPv 6 address allocation leaving room for a 16 -bit subnet field and a 64 -bit address within the subnet. u Any IPv 6 address that begins with the 2002: : /16 prefix is known of as a 6 to 4 address, as opposed to a native IPv 6 address which does not use that prefix. 117
6 to 4 Address Block Allocation u For any 32 -bit global IPv 4 address that is assigned to a host, a 48 -bit 6 to 4 IPv 6 prefix can be constructed for use by that host (and if applicable the network behind it) by prepending 2002 (hex) to the IPv 4 address. u IPv 4 addresses use dot-decimal notation while IPv 6 addresses use hexadecimal notation. Thus for the global IPv 4 address 207. 142. 131. 202, the corresponding 6 to 4 prefix would be 2002: CF 8 E: 83 CA: : /48. This gives a total prefix length of 48 bits, which is the same as an end site is the amount allocated under normal IPv 6 address allocation leaving room for a 16 -bit subnet field and a 64 -bit address within the subnet. u Any IPv 6 address that begins with the 2002: : /16 prefix is known of as a 6 to 4 address, as opposed to a native IPv 6 address which does not use that prefix. 117
 6 to 4 Encapsulation and Transmission u 6 to 4 embeds an IPv 6 packet in the payload portion of an IPv 4 packet with protocol type 41. To send an IPv 6 packet over an IPv 4 network to a 6 to 4 destination address, an IPv 4 header with protocol type 41 is pre-pended to the IPv 6 packet. The IPv 4 destination address for the pre-pended packet header is derived from the IPv 6 destination address of the inner packet, by extracting the 32 bits immediately following the IPv 6 destination address's 2002: : prefix. The IPv 4 source address in the prepended packet header is the IPv 4 address of the host or router which is sending the packet over IPv 4. The resulting IPv 4 packet is then routed to its IPv 4 destination address just like any other IPv 4 packet. 118
6 to 4 Encapsulation and Transmission u 6 to 4 embeds an IPv 6 packet in the payload portion of an IPv 4 packet with protocol type 41. To send an IPv 6 packet over an IPv 4 network to a 6 to 4 destination address, an IPv 4 header with protocol type 41 is pre-pended to the IPv 6 packet. The IPv 4 destination address for the pre-pended packet header is derived from the IPv 6 destination address of the inner packet, by extracting the 32 bits immediately following the IPv 6 destination address's 2002: : prefix. The IPv 4 source address in the prepended packet header is the IPv 4 address of the host or router which is sending the packet over IPv 4. The resulting IPv 4 packet is then routed to its IPv 4 destination address just like any other IPv 4 packet. 118
 Routing Between 6 to 4 and Native IPv 6 u To allow hosts and networks using 6 to 4 addresses to exchange traffic with hosts using "native" IPv 6 addresses, "relay routers" have been established. A relay router connects to an IPv 4 network and an IPv 6 network. 6 to 4 packets arriving on an IPv 4 interface will have their IPv 6 payloads routed to the IPv 6 network, while packets arriving on the IPv 6 interface with a destination address prefix of 2002: : /16 will be encapsulated and forwarded over the IPv 4 network. u To allow a 6 to 4 router to communicate with the native IPv 6 Internet, it must have its IPv 6 default gateway set to a 6 to 4 address which contains the IPv 4 address of a 6 to 4 relay router. To avoid the need for users to set this up manually, the 6 to 4 relay anycast address of 192. 88. 99. 1 (which when wrapped in 6 to 4 with the subnet and hosts fields zero becomes 2002: c 058: 6301: : ) has been allocated for the purpose of sending packets to a relay router. For routing reasons the whole of 192. 88. 99. 0/24 has been allocated for routes pointed at 6 to 4 relay routers that use the anycast IP. Providers willing to provide 6 to 4 service to their clients or peers should advertise the anycast prefix like any other IP prefix, and route the prefix to their 6 to 4 relay. u Packets from the IPv 6 Internet to 6 to 4 systems must be sent to a 6 to 4 relay router by normal IPv 6 routing methods. The specification states that such relay routers must only advertise 2002: : /16 and not subdivisions of it to prevent IPv 4 routes polluting the routing tables of IPv 6 routers. From here they can then be sent over the IPv 4 Internet to the destination. 119
Routing Between 6 to 4 and Native IPv 6 u To allow hosts and networks using 6 to 4 addresses to exchange traffic with hosts using "native" IPv 6 addresses, "relay routers" have been established. A relay router connects to an IPv 4 network and an IPv 6 network. 6 to 4 packets arriving on an IPv 4 interface will have their IPv 6 payloads routed to the IPv 6 network, while packets arriving on the IPv 6 interface with a destination address prefix of 2002: : /16 will be encapsulated and forwarded over the IPv 4 network. u To allow a 6 to 4 router to communicate with the native IPv 6 Internet, it must have its IPv 6 default gateway set to a 6 to 4 address which contains the IPv 4 address of a 6 to 4 relay router. To avoid the need for users to set this up manually, the 6 to 4 relay anycast address of 192. 88. 99. 1 (which when wrapped in 6 to 4 with the subnet and hosts fields zero becomes 2002: c 058: 6301: : ) has been allocated for the purpose of sending packets to a relay router. For routing reasons the whole of 192. 88. 99. 0/24 has been allocated for routes pointed at 6 to 4 relay routers that use the anycast IP. Providers willing to provide 6 to 4 service to their clients or peers should advertise the anycast prefix like any other IP prefix, and route the prefix to their 6 to 4 relay. u Packets from the IPv 6 Internet to 6 to 4 systems must be sent to a 6 to 4 relay router by normal IPv 6 routing methods. The specification states that such relay routers must only advertise 2002: : /16 and not subdivisions of it to prevent IPv 4 routes polluting the routing tables of IPv 6 routers. From here they can then be sent over the IPv 4 Internet to the destination. 119
 Connecting to the network u Configure System for IPv 6 u Native Connectivity (IPv 6) v The Provider v Dual Stack u Tunnel u Applications 120
Connecting to the network u Configure System for IPv 6 u Native Connectivity (IPv 6) v The Provider v Dual Stack u Tunnel u Applications 120
 Configure system for IPv 6 Current Linux, Unix, Solaris v http: //www. ipv 6. org/impl/unix. html u Microsoft 2000, Microsoft XP v http: //www. microsoft. com/technet/prodtechnol/windo wsserver 2003/library/Server. Help/8 edb 1 f 35 -3 aae-44 f 4 aab 8 -eb 005 fcef 59 d. mspx u Microsoft 2003 v http: //www. microsoft. com/windowsserver 2003/techno logies/ipv 6/default. mspx u All Others v http: //www. ipv 6. org/impl/index. html u 121
Configure system for IPv 6 Current Linux, Unix, Solaris v http: //www. ipv 6. org/impl/unix. html u Microsoft 2000, Microsoft XP v http: //www. microsoft. com/technet/prodtechnol/windo wsserver 2003/library/Server. Help/8 edb 1 f 35 -3 aae-44 f 4 aab 8 -eb 005 fcef 59 d. mspx u Microsoft 2003 v http: //www. microsoft. com/windowsserver 2003/techno logies/ipv 6/default. mspx u All Others v http: //www. ipv 6. org/impl/index. html u 121
 Implications of IPv 6 u IPv 4 and IPv 6 Transition u Security u Business 122
Implications of IPv 6 u IPv 4 and IPv 6 Transition u Security u Business 122
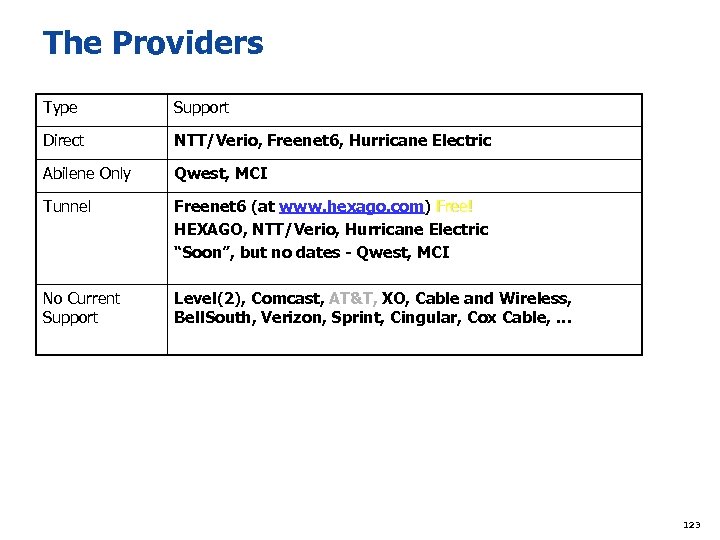 The Providers Type Support Direct NTT/Verio, Freenet 6, Hurricane Electric Abilene Only Qwest, MCI Tunnel Freenet 6 (at www. hexago. com) Free! HEXAGO, NTT/Verio, Hurricane Electric “Soon”, but no dates - Qwest, MCI No Current Support Level(2), Comcast, AT&T, XO, Cable and Wireless, Bell. South, Verizon, Sprint, Cingular, Cox Cable, … 123
The Providers Type Support Direct NTT/Verio, Freenet 6, Hurricane Electric Abilene Only Qwest, MCI Tunnel Freenet 6 (at www. hexago. com) Free! HEXAGO, NTT/Verio, Hurricane Electric “Soon”, but no dates - Qwest, MCI No Current Support Level(2), Comcast, AT&T, XO, Cable and Wireless, Bell. South, Verizon, Sprint, Cingular, Cox Cable, … 123
 How do Businesses Identify IPv 6 compatible products? IPv 6 Ready Logo Program u IPv 6 Ready Logo database contains the names of companies who have qualified to use the IPv 6 Ready Logo and those products for which samples have been evaluated. u http: //www. ipv 6 ready. org/frames. html 124
How do Businesses Identify IPv 6 compatible products? IPv 6 Ready Logo Program u IPv 6 Ready Logo database contains the names of companies who have qualified to use the IPv 6 Ready Logo and those products for which samples have been evaluated. u http: //www. ipv 6 ready. org/frames. html 124
 Current IPv 6 -enabled Applications u End User Application v E-Mail, Web server, Chat v And… 125
Current IPv 6 -enabled Applications u End User Application v E-Mail, Web server, Chat v And… 125
 IPsec and IPv 6 u IPsec provides security at network (Internet) layer v All IP datagrams covered v No re-engineering of applications v Transparent to users u Mandatory for next-generation IPv 6, Optional for current-generation (IPv 4) 126
IPsec and IPv 6 u IPsec provides security at network (Internet) layer v All IP datagrams covered v No re-engineering of applications v Transparent to users u Mandatory for next-generation IPv 6, Optional for current-generation (IPv 4) 126
 IPsec features Two basic modes of use: v “transport” mode: for IPsec-aware hosts as endpoints u Mostly unused in IPv 4 – likely to be used end to end in IPv 6 v “tunnel” mode: for IPsec-unaware hosts, established by intermediate gateways or host OS. u Provides authentication and/or confidentiality v AH and ESP protocols Implemented as extension headers in IPv 6 u Dynamic key establishment via IKEv 2 u IPsec more generally applicable in an IPv 6 world v Removal of NATs makes end to end security a real possibility v But end to end IPsec makes firewalling more difficult u 127
IPsec features Two basic modes of use: v “transport” mode: for IPsec-aware hosts as endpoints u Mostly unused in IPv 4 – likely to be used end to end in IPv 6 v “tunnel” mode: for IPsec-unaware hosts, established by intermediate gateways or host OS. u Provides authentication and/or confidentiality v AH and ESP protocols Implemented as extension headers in IPv 6 u Dynamic key establishment via IKEv 2 u IPsec more generally applicable in an IPv 6 world v Removal of NATs makes end to end security a real possibility v But end to end IPsec makes firewalling more difficult u 127
 IT Manager/Business View u Impact to business 128
IT Manager/Business View u Impact to business 128
 Justification u u u Improve Confidently and Integrity of your network v Peer-to-Peer Encryption available on all devices Easier Deployment of new systems v No NAT, no need for waiting for support of new audio, video and file sharing protocols Scalable v Ability to add many system to a single network Do business with China, Korea, Japan or the Do. D? v These partners and customers are already doing it. The Future v IPv 6 is like the web was in 1994 --- take advantage of it now before a competitor does 129
Justification u u u Improve Confidently and Integrity of your network v Peer-to-Peer Encryption available on all devices Easier Deployment of new systems v No NAT, no need for waiting for support of new audio, video and file sharing protocols Scalable v Ability to add many system to a single network Do business with China, Korea, Japan or the Do. D? v These partners and customers are already doing it. The Future v IPv 6 is like the web was in 1994 --- take advantage of it now before a competitor does 129
 What does it mean? Business Applications not currently supported v CRM, ERP, MRP, Vo. IP u Network Devices v Most new routers are IPv 6 capable v A mix of dual-stack and transition is the most common approach u Operating System v IPv 6 support in Windows 2000, XP, 2003 and Vista, Free. BSD 4. 0 (KAME) and above, Linux (Usagi) since 2000, Solaris 7, Mac OS X 10. 2. v No support for legacy applications --- will require an upgrade, a using transition mechanism or end of Life application u 130
What does it mean? Business Applications not currently supported v CRM, ERP, MRP, Vo. IP u Network Devices v Most new routers are IPv 6 capable v A mix of dual-stack and transition is the most common approach u Operating System v IPv 6 support in Windows 2000, XP, 2003 and Vista, Free. BSD 4. 0 (KAME) and above, Linux (Usagi) since 2000, Solaris 7, Mac OS X 10. 2. v No support for legacy applications --- will require an upgrade, a using transition mechanism or end of Life application u 130
 What does it mean? Network Connections v IPv 6 will increase bytes transmitted across connections u u IPv 4 - Header = 20 -60 bytes IPv 6 - Header = 40 bytes May require increasing your WAN and LAN connections 131
What does it mean? Network Connections v IPv 6 will increase bytes transmitted across connections u u IPv 4 - Header = 20 -60 bytes IPv 6 - Header = 40 bytes May require increasing your WAN and LAN connections 131


