1dfaee1f2a364007451a48758a24edd2.ppt
- Количество слайдов: 27
 Security WP 7: Security Coordination Group (SCG) David Kelsey (CCLRC-RAL, UK) d. p. kelsey@rl. ac. uk Data. Grid is a project funded by the European Commission under contract IST-2000 -25182 3 rd EU Review – 19 -20/02/2004
Security WP 7: Security Coordination Group (SCG) David Kelsey (CCLRC-RAL, UK) d. p. kelsey@rl. ac. uk Data. Grid is a project funded by the European Commission under contract IST-2000 -25182 3 rd EU Review – 19 -20/02/2004
 Outline u SCG Objectives u SCG Achievements n Overview n Authentication n Authorization n Requirements analysis u Lessons learned u Future u Exploitation u Summary David Kelsey - Security - n° 2
Outline u SCG Objectives u SCG Achievements n Overview n Authentication n Authorization n Requirements analysis u Lessons learned u Future u Exploitation u Summary David Kelsey - Security - n° 2
 SCG Objectives u No n single work-package to tackle Grid security But WP 2 has a security task and team u Security n Coordination Group (SCG) was formed in late 2001 Task 7. 4 (TA) in WP 7 started in month 13 u Mandate of SCG (sub-group of WP 7) n To produce the Deliverables of WP 7 on Security (task 7. 4) n To help coordinate security activities in WPs 1 to 7 n To liaise with WP 6 CA & Authorization groups (and others) n To contribute to the architecture of the EU Data. Grid (ATF) u SCG has larger scope than foreseen in TA task 7. 4 n At least one representative per middleware WP n Collaboration with Data. TAG and national Grid projects David Kelsey - Security - n° 3
SCG Objectives u No n single work-package to tackle Grid security But WP 2 has a security task and team u Security n Coordination Group (SCG) was formed in late 2001 Task 7. 4 (TA) in WP 7 started in month 13 u Mandate of SCG (sub-group of WP 7) n To produce the Deliverables of WP 7 on Security (task 7. 4) n To help coordinate security activities in WPs 1 to 7 n To liaise with WP 6 CA & Authorization groups (and others) n To contribute to the architecture of the EU Data. Grid (ATF) u SCG has larger scope than foreseen in TA task 7. 4 n At least one representative per middleware WP n Collaboration with Data. TAG and national Grid projects David Kelsey - Security - n° 3
 SCG Achievements - overview u Authentication: n WP 6 Certificate Authorities Coordination Group u Data. Grid n n Certification Authorities (CAs) for EDG and others Security Requirements (D 7. 5, May 2002) 112 requirements in many areas… Authentication, Authorization, Auditing, Non-repudiation, Delegation, Confidentiality, Integrity, Network, Manageability, Usability, Interoperability, Scalability, Performance, Robustness u Several joint meetings with WP 8, 9 and 10 for VO use cases u Security Design (D 7. 6, March 2003) u Successful implementation, integration and deployment of many security components u Final n Security Report (D 7. 7, January 2004) includes comparison with initial requirements David Kelsey - Security - n° 4
SCG Achievements - overview u Authentication: n WP 6 Certificate Authorities Coordination Group u Data. Grid n n Certification Authorities (CAs) for EDG and others Security Requirements (D 7. 5, May 2002) 112 requirements in many areas… Authentication, Authorization, Auditing, Non-repudiation, Delegation, Confidentiality, Integrity, Network, Manageability, Usability, Interoperability, Scalability, Performance, Robustness u Several joint meetings with WP 8, 9 and 10 for VO use cases u Security Design (D 7. 6, March 2003) u Successful implementation, integration and deployment of many security components u Final n Security Report (D 7. 7, January 2004) includes comparison with initial requirements David Kelsey - Security - n° 4
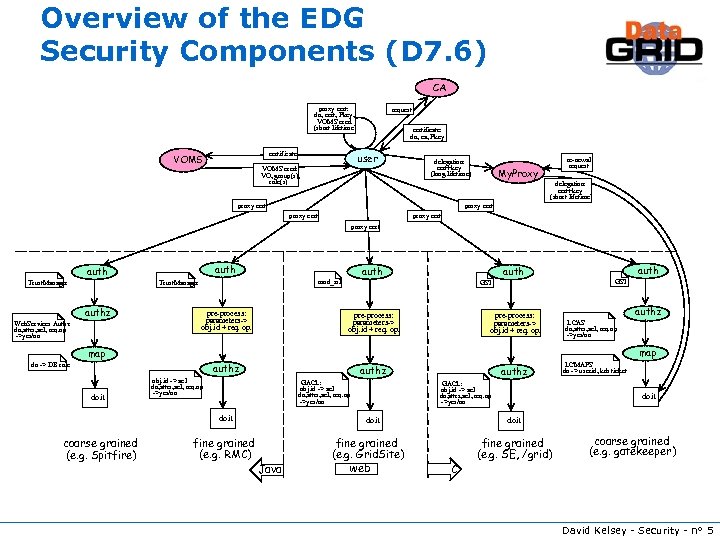 Overview of the EDG Security Components (D 7. 6) CA proxy cert: dn, cert, Pkey, VOMS cred. (short lifetime) certificate VOMS request certificate: dn, ca, Pkey user VOMS cred: VO, group(s), role(s) delegation: cert+key (long lifetime) re-newal request My. Proxy delegation: cert+key (short lifetime) proxy cert proxy cert auth Trust. Manager authz Web. Services Authz dn, attrs, acl, req. op ->yes/no auth mod_ssl Trust. Manager pre-process: parameters-> obj. id + req. op. GSI pre-process: parameters-> obj. id + req. op. auth GSI authz LCAS dn, attrs, acl, req. op ->yes/no map dn -> DB role authz doit authz obj. id -> acl dn, attrs, acl, req. op ->yes/no GACL: obj. id -> acl dn, attrs, acl, req. op ->yes/no doit coarse grained (e. g. Spitfire) authz GACL: obj. id -> acl dn, attrs, acl, req. op ->yes/no doit fine grained (e. g. RMC) Java fine grained (e. g. Grid. Site) web LCMAPS dn -> userid, krb ticket doit C fine grained (e. g. SE, /grid) coarse grained (e. g. gatekeeper) David Kelsey - Security - n° 5
Overview of the EDG Security Components (D 7. 6) CA proxy cert: dn, cert, Pkey, VOMS cred. (short lifetime) certificate VOMS request certificate: dn, ca, Pkey user VOMS cred: VO, group(s), role(s) delegation: cert+key (long lifetime) re-newal request My. Proxy delegation: cert+key (short lifetime) proxy cert proxy cert auth Trust. Manager authz Web. Services Authz dn, attrs, acl, req. op ->yes/no auth mod_ssl Trust. Manager pre-process: parameters-> obj. id + req. op. GSI pre-process: parameters-> obj. id + req. op. auth GSI authz LCAS dn, attrs, acl, req. op ->yes/no map dn -> DB role authz doit authz obj. id -> acl dn, attrs, acl, req. op ->yes/no GACL: obj. id -> acl dn, attrs, acl, req. op ->yes/no doit coarse grained (e. g. Spitfire) authz GACL: obj. id -> acl dn, attrs, acl, req. op ->yes/no doit fine grained (e. g. RMC) Java fine grained (e. g. Grid. Site) web LCMAPS dn -> userid, krb ticket doit C fine grained (e. g. SE, /grid) coarse grained (e. g. gatekeeper) David Kelsey - Security - n° 5
 Authentication A PKI with Certification Authorities (CAs) for u EU Data. Grid u EU Data. TAG u EU Cross. Grid u LHC Computing Grid project (LCG) n Global service for particle physics n Includes North America and Asia u The n same CA’s also used by many national projects France, Italy, Netherlands, Nordic countries, Spain, UK, … u This PKI is used for cross-authentication by applications spanning several Grids David Kelsey - Security - n° 6
Authentication A PKI with Certification Authorities (CAs) for u EU Data. Grid u EU Data. TAG u EU Cross. Grid u LHC Computing Grid project (LCG) n Global service for particle physics n Includes North America and Asia u The n same CA’s also used by many national projects France, Italy, Netherlands, Nordic countries, Spain, UK, … u This PKI is used for cross-authentication by applications spanning several Grids David Kelsey - Security - n° 6
 Data. Grid PKI History u Started n planning the PKI in Autumn 2000 First meeting of WP 6 CA group in December 2000 u Requirements n Use Globus Toolkit and GSI (X. 509 PKI) n Users – require single sign-on n One identity certificate for use in many different Grids n Only support Grid Authentication s No long-term encryption, digital signing, … u Pre-existing Certification Authorities in some countries n For other purposes and/or larger communities n Czech Republic, France, Italy, Portugal, UK, … David Kelsey - Security - n° 7
Data. Grid PKI History u Started n planning the PKI in Autumn 2000 First meeting of WP 6 CA group in December 2000 u Requirements n Use Globus Toolkit and GSI (X. 509 PKI) n Users – require single sign-on n One identity certificate for use in many different Grids n Only support Grid Authentication s No long-term encryption, digital signing, … u Pre-existing Certification Authorities in some countries n For other purposes and/or larger communities n Czech Republic, France, Italy, Portugal, UK, … David Kelsey - Security - n° 7
 Early PKI Decisions u Keep n Authorization and Authentication separate Authorization not stable enough and too VO-specific u One Grid electronic identity n For use in many Grid projects (EU and national) n For user convenience u Would one CA be enough? u Hierarchy u What n or cross-signing? NO NO is the most appropriate scale? One CA per country u Define “minimum requirements” for EDG-approved CA’s David Kelsey - Security - n° 8
Early PKI Decisions u Keep n Authorization and Authentication separate Authorization not stable enough and too VO-specific u One Grid electronic identity n For use in many Grid projects (EU and national) n For user convenience u Would one CA be enough? u Hierarchy u What n or cross-signing? NO NO is the most appropriate scale? One CA per country u Define “minimum requirements” for EDG-approved CA’s David Kelsey - Security - n° 8
 CA Approval process u “Minimum requirements” document http: //marianne. in 2 p 3. fr/datagrid/ca/ u Evaluation of policy and procedures (CP/CPS) and presentation to WP 6 CA meeting n no physical audit u Concentrate on n Registration Authority procedures n Operational procedures of the CA n Unique Distinguished Names within the whole PKI u Concerns about scalability n Regional PMAs n CAs could be run by NRENs David Kelsey - Security - n° 9
CA Approval process u “Minimum requirements” document http: //marianne. in 2 p 3. fr/datagrid/ca/ u Evaluation of policy and procedures (CP/CPS) and presentation to WP 6 CA meeting n no physical audit u Concentrate on n Registration Authority procedures n Operational procedures of the CA n Unique Distinguished Names within the whole PKI u Concerns about scalability n Regional PMAs n CAs could be run by NRENs David Kelsey - Security - n° 9
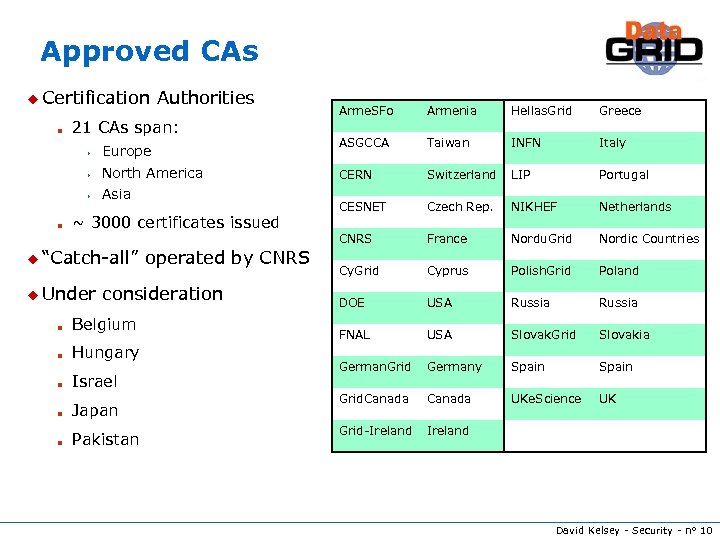 Approved CAs u Certification n Authorities 21 CAs span: s s North America s n Europe Asia ~ 3000 certificates issued u “Catch-all” u Under operated by CNRS consideration n Belgium n Hungary n Israel n Japan n Pakistan Arme. SFo Armenia Hellas. Grid Greece ASGCCA Taiwan INFN Italy CERN Switzerland LIP Portugal CESNET Czech Rep. NIKHEF Netherlands CNRS France Nordu. Grid Nordic Countries Cy. Grid Cyprus Polish. Grid Poland DOE USA Russia FNAL USA Slovak. Grid Slovakia German. Grid Germany Spain Grid. Canada UKe. Science UK Grid-Ireland David Kelsey - Security - n° 10
Approved CAs u Certification n Authorities 21 CAs span: s s North America s n Europe Asia ~ 3000 certificates issued u “Catch-all” u Under operated by CNRS consideration n Belgium n Hungary n Israel n Japan n Pakistan Arme. SFo Armenia Hellas. Grid Greece ASGCCA Taiwan INFN Italy CERN Switzerland LIP Portugal CESNET Czech Rep. NIKHEF Netherlands CNRS France Nordu. Grid Nordic Countries Cy. Grid Cyprus Polish. Grid Poland DOE USA Russia FNAL USA Slovak. Grid Slovakia German. Grid Germany Spain Grid. Canada UKe. Science UK Grid-Ireland David Kelsey - Security - n° 10
 Authorization (Auth. Z) overview u The Authorization model n Build on the GSI-based authentication n Global Auth. Z by one or more VOs n Local site/resource-based Auth. Z u Early Data. Grid VO management system: “VO-LDAP” u New Auth. Z system: VOMS u policy or ACL based local access control n u coarse and fine grained solutions Data. Grid security components: n GSI/LCAS/LCMAPS for C/C++ services n edg-java-security for Java web services n mod_ssl/GACL for Apache based web services u Services can either use the grid-mapfile or use VOMS credentials u Modified My. Proxy service for credential renewal (incl Auth. Z) David Kelsey - Security - n° 11
Authorization (Auth. Z) overview u The Authorization model n Build on the GSI-based authentication n Global Auth. Z by one or more VOs n Local site/resource-based Auth. Z u Early Data. Grid VO management system: “VO-LDAP” u New Auth. Z system: VOMS u policy or ACL based local access control n u coarse and fine grained solutions Data. Grid security components: n GSI/LCAS/LCMAPS for C/C++ services n edg-java-security for Java web services n mod_ssl/GACL for Apache based web services u Services can either use the grid-mapfile or use VOMS credentials u Modified My. Proxy service for credential renewal (incl Auth. Z) David Kelsey - Security - n° 11
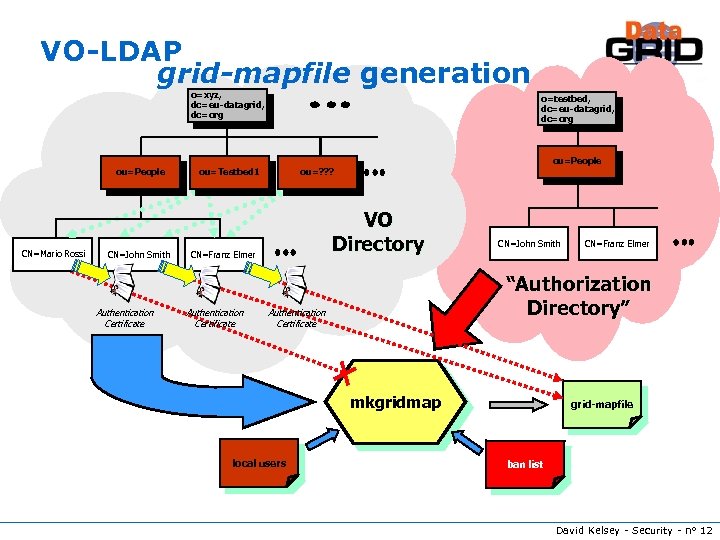 VO-LDAP grid-mapfile generation o=xyz, dc=eu-datagrid, dc=org ou=People CN=Mario Rossi CN=John Smith Authentication Certificate o=testbed, dc=eu-datagrid, dc=org ou=Testbed 1 VO Directory CN=Franz Elmer Authentication Certificate ou=People ou=? ? ? CN=John Smith “Authorization Directory” Authentication Certificate mkgridmap local users CN=Franz Elmer grid-mapfile ban list David Kelsey - Security - n° 12
VO-LDAP grid-mapfile generation o=xyz, dc=eu-datagrid, dc=org ou=People CN=Mario Rossi CN=John Smith Authentication Certificate o=testbed, dc=eu-datagrid, dc=org ou=Testbed 1 VO Directory CN=Franz Elmer Authentication Certificate ou=People ou=? ? ? CN=John Smith “Authorization Directory” Authentication Certificate mkgridmap local users CN=Franz Elmer grid-mapfile ban list David Kelsey - Security - n° 12
 Virtual Organization Membership Service (VOMS) u Joint development with Data. TAG u Issues n signed credentials to prove group/role/VO membership Moved to standard RFC 3281 Attribute Certificate format u The AC is included as a non-critical extension of the user’s proxy certificate n Backwards compatible u Core n service: standalone daemon for the “login” Administered by the VO manager u Administrative service: web service with API, command line and web user interface n for administration and registration u VOMS migration tools for grid-mapfiles and VO-LDAP servers David Kelsey - Security - n° 13
Virtual Organization Membership Service (VOMS) u Joint development with Data. TAG u Issues n signed credentials to prove group/role/VO membership Moved to standard RFC 3281 Attribute Certificate format u The AC is included as a non-critical extension of the user’s proxy certificate n Backwards compatible u Core n service: standalone daemon for the “login” Administered by the VO manager u Administrative service: web service with API, command line and web user interface n for administration and registration u VOMS migration tools for grid-mapfiles and VO-LDAP servers David Kelsey - Security - n° 13
 Local Site Authorization (WP 4) u Local n Centre Authorization Service (LCAS) Handles authorization requests to local fabric s s n decisions based on user proxy certificate and job specification supports grid-mapfile mechanism. Plug-in framework (hooks for external authorization plugins) s allowed users, banned users, available timeslots, GACL s plugin for VOMS (to process authorization data) u Local Credential Mapping Service (LCMAPS) n provides local credentials needed for jobs in fabric n mapping based on user identity, VO affiliation, local site policy n plug-ins for local systems (Kerberos/AFS, LDAP nss) David Kelsey - Security - n° 14
Local Site Authorization (WP 4) u Local n Centre Authorization Service (LCAS) Handles authorization requests to local fabric s s n decisions based on user proxy certificate and job specification supports grid-mapfile mechanism. Plug-in framework (hooks for external authorization plugins) s allowed users, banned users, available timeslots, GACL s plugin for VOMS (to process authorization data) u Local Credential Mapping Service (LCMAPS) n provides local credentials needed for jobs in fabric n mapping based on user identity, VO affiliation, local site policy n plug-ins for local systems (Kerberos/AFS, LDAP nss) David Kelsey - Security - n° 14
 edg-java-security (WP 2) u Trust manager n GSI compatible authentication (supporting proxy chain) n Adapters to HTTP and SOAP n Currently deployed for Tomcat 4 n VOMS credential verification u Authorization n Manager Authorization and mapping for Java services Plug-in framework for maps: database, XML file and for backward compatibility: grid-mapfile Handles VOMS attributes David Kelsey - Security - n° 15
edg-java-security (WP 2) u Trust manager n GSI compatible authentication (supporting proxy chain) n Adapters to HTTP and SOAP n Currently deployed for Tomcat 4 n VOMS credential verification u Authorization n Manager Authorization and mapping for Java services Plug-in framework for maps: database, XML file and for backward compatibility: grid-mapfile Handles VOMS attributes David Kelsey - Security - n° 15
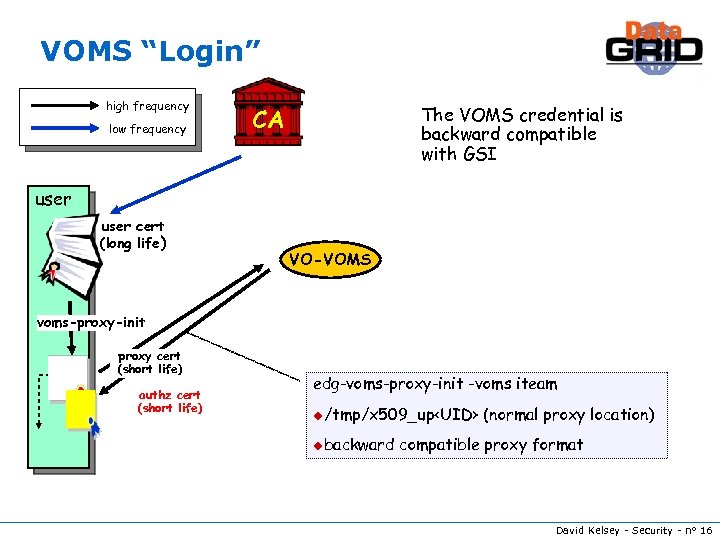 VOMS “Login” high frequency low frequency The VOMS credential is backward compatible with GSI CA user cert (long life) VO-VOMS voms-proxy-init proxy cert (short life) authz cert (short life) edg-voms-proxy-init -voms iteam u/tmp/x 509_up
VOMS “Login” high frequency low frequency The VOMS credential is backward compatible with GSI CA user cert (long life) VO-VOMS voms-proxy-init proxy cert (short life) authz cert (short life) edg-voms-proxy-init -voms iteam u/tmp/x 509_up
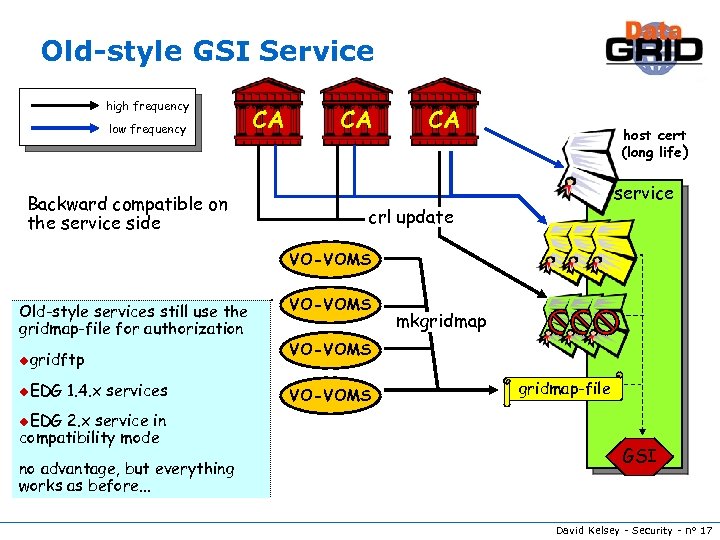 Old-style GSI Service high frequency low frequency Backward compatible on the service side CA CA CA host cert (long life) service crl update VO-VOMS Old-style services still use the gridmap-file for authorization ugridftp u. EDG 1. 4. x services 2. x service in compatibility mode VO-VOMS mkgridmap VO-VOMS gridmap-file u. EDG no advantage, but everything works as before. . . GSI David Kelsey - Security - n° 17
Old-style GSI Service high frequency low frequency Backward compatible on the service side CA CA CA host cert (long life) service crl update VO-VOMS Old-style services still use the gridmap-file for authorization ugridftp u. EDG 1. 4. x services 2. x service in compatibility mode VO-VOMS mkgridmap VO-VOMS gridmap-file u. EDG no advantage, but everything works as before. . . GSI David Kelsey - Security - n° 17
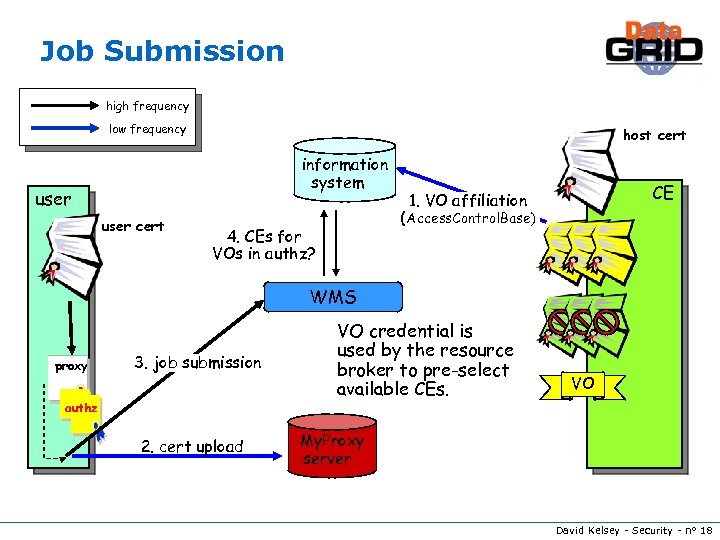 Job Submission high frequency low frequency host cert information system user cert CE 1. VO affiliation (Access. Control. Base) 4. CEs for VOs in authz? WMS proxy 3. job submission authz 2. cert upload VO credential is used by the resource broker to pre-select available CEs. VO My. Proxy server David Kelsey - Security - n° 18
Job Submission high frequency low frequency host cert information system user cert CE 1. VO affiliation (Access. Control. Base) 4. CEs for VOs in authz? WMS proxy 3. job submission authz 2. cert upload VO credential is used by the resource broker to pre-select available CEs. VO My. Proxy server David Kelsey - Security - n° 18
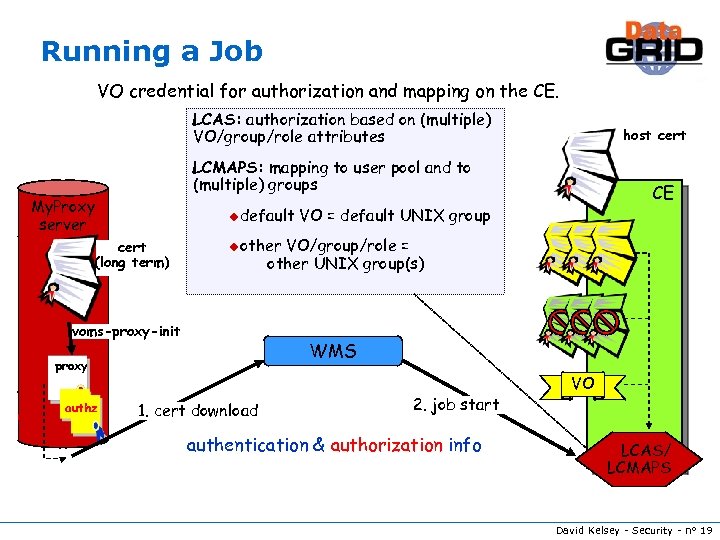 Running a Job VO credential for authorization and mapping on the CE. LCAS: authorization based on (multiple) VO/group/role attributes LCMAPS: mapping to user pool and to (multiple) groups My. Proxy server udefault cert (long term) CE VO = default UNIX group uother VO/group/role = other UNIX group(s) voms-proxy-init WMS proxy authz host cert 1. cert download 2. job start authentication & authorization info VO LCAS/ LCMAPS David Kelsey - Security - n° 19
Running a Job VO credential for authorization and mapping on the CE. LCAS: authorization based on (multiple) VO/group/role attributes LCMAPS: mapping to user pool and to (multiple) groups My. Proxy server udefault cert (long term) CE VO = default UNIX group uother VO/group/role = other UNIX group(s) voms-proxy-init WMS proxy authz host cert 1. cert download 2. job start authentication & authorization info VO LCAS/ LCMAPS David Kelsey - Security - n° 19
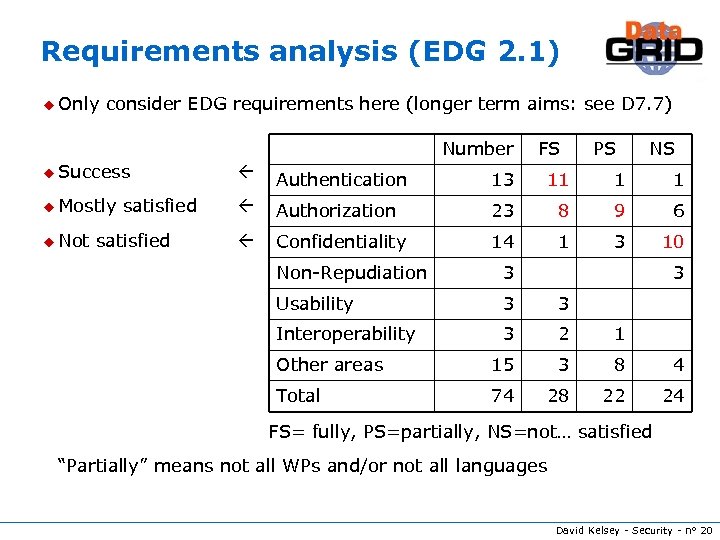 Requirements analysis (EDG 2. 1) u Only consider EDG requirements here (longer term aims: see D 7. 7) Number FS PS NS u Success Authentication 13 11 1 1 u Mostly Authorization 23 8 9 6 Confidentiality 14 1 3 10 u Not satisfied Non-Repudiation 3 3 Usability 3 3 Interoperability 3 2 1 Other areas 15 3 8 4 Total 74 28 22 24 FS= fully, PS=partially, NS=not… satisfied “Partially” means not all WPs and/or not all languages David Kelsey - Security - n° 20
Requirements analysis (EDG 2. 1) u Only consider EDG requirements here (longer term aims: see D 7. 7) Number FS PS NS u Success Authentication 13 11 1 1 u Mostly Authorization 23 8 9 6 Confidentiality 14 1 3 10 u Not satisfied Non-Repudiation 3 3 Usability 3 3 Interoperability 3 2 1 Other areas 15 3 8 4 Total 74 28 22 24 FS= fully, PS=partially, NS=not… satisfied “Partially” means not all WPs and/or not all languages David Kelsey - Security - n° 20
 Requirements - comments u Authentication n The EDG PKI is a major success s Except for 1 “NS” (revocation in < 10 minutes) u Authorization n Another major success of the project s n But not all components are fully deployed and/or configured “NS” requirements are related to s s Assigning job priorities and pre-checking fine-grained access (WP 1) Authorization of resources rather than users (WP 10) u Confidentiality n “NS” requirements are related to (mainly WP 10) s s Encryption/decryption and fine-grained access control to files/keys Concealing information about users and audit data u The Data. Grid design and implementation is aimed at meeting all requirements and prototyping secure services n towards industrial strength David Kelsey - Security - n° 21
Requirements - comments u Authentication n The EDG PKI is a major success s Except for 1 “NS” (revocation in < 10 minutes) u Authorization n Another major success of the project s n But not all components are fully deployed and/or configured “NS” requirements are related to s s Assigning job priorities and pre-checking fine-grained access (WP 1) Authorization of resources rather than users (WP 10) u Confidentiality n “NS” requirements are related to (mainly WP 10) s s Encryption/decryption and fine-grained access control to files/keys Concealing information about users and audit data u The Data. Grid design and implementation is aimed at meeting all requirements and prototyping secure services n towards industrial strength David Kelsey - Security - n° 21
 Bio-medical confidentiality u Requires n fine-grained Auth. Z on files and encryption keys (in RMC) A solution is described in D 7. 6 design document u Many components implemented and deployed n Shown to work independently n Sufficient to fulfil some application requirements u Only partial integration into EDG release 2. 1 was possible n Difficult to integrate security into existing systems n Difficult priority decisions were taken by the project management n Stability more important than functionality u We n have successfully integrated fine-grained Auth. Z in Job submission fine-grained Auth. Z on SE and RM not yet deployed/configured u Medium-grained u But Auth. Z (group level) on files is achievable fine-grained Auth. Z requires more development and integration David Kelsey - Security - n° 22
Bio-medical confidentiality u Requires n fine-grained Auth. Z on files and encryption keys (in RMC) A solution is described in D 7. 6 design document u Many components implemented and deployed n Shown to work independently n Sufficient to fulfil some application requirements u Only partial integration into EDG release 2. 1 was possible n Difficult to integrate security into existing systems n Difficult priority decisions were taken by the project management n Stability more important than functionality u We n have successfully integrated fine-grained Auth. Z in Job submission fine-grained Auth. Z on SE and RM not yet deployed/configured u Medium-grained u But Auth. Z (group level) on files is achievable fine-grained Auth. Z requires more development and integration David Kelsey - Security - n° 22
 Lessons learned u Be n n careful collecting requirements In hindsight, the D 7. 5 requirements were rather ambitious The expectations of the applications were documented but there was not sufficient analysis of the difficulty of integration u Security must be an integral part of all development n from the start n Larger scope SCG started late (but as defined in the TA) u Building and maintaining “trust” between projects and continents takes time u Integration of security into existing systems is complex u There must be a dedicated activity dealing with security u EGEE planning has already benefited from our experience David Kelsey - Security - n° 23
Lessons learned u Be n n careful collecting requirements In hindsight, the D 7. 5 requirements were rather ambitious The expectations of the applications were documented but there was not sufficient analysis of the difficulty of integration u Security must be an integral part of all development n from the start n Larger scope SCG started late (but as defined in the TA) u Building and maintaining “trust” between projects and continents takes time u Integration of security into existing systems is complex u There must be a dedicated activity dealing with security u EGEE planning has already benefited from our experience David Kelsey - Security - n° 23
 Future work u Authentication n Continue and expand the EDG PKI n Secure credential management: online services, Smart. Cards n Faster and more robust certificate revocation, e. g. OCSP u Authorization n Fuller use of VOMS Auth. Z credentials n Mutual Auth. Z: VOs should approve resources and services n Convergence with GGF standards (XACML, SAML, …) u Restricted delegation u Confidentiality n Integrate and deploy the proposed solution for WP 10 u Build n on Data. Grid design and components for industrial strength PKI/SSL authentication, standards-based authorization, ws-security, … David Kelsey - Security - n° 24
Future work u Authentication n Continue and expand the EDG PKI n Secure credential management: online services, Smart. Cards n Faster and more robust certificate revocation, e. g. OCSP u Authorization n Fuller use of VOMS Auth. Z credentials n Mutual Auth. Z: VOs should approve resources and services n Convergence with GGF standards (XACML, SAML, …) u Restricted delegation u Confidentiality n Integrate and deploy the proposed solution for WP 10 u Build n on Data. Grid design and components for industrial strength PKI/SSL authentication, standards-based authorization, ws-security, … David Kelsey - Security - n° 24
 Exploitation u Authentication n The CA infrastructure will continue s Discussions started with DEISA and SEEGRID n EGEE will manage the EDG PKI in a new EU PMA n LCG driving the requirements for global physics authentication n Grid CAs to be registered in new TERENA CA repository (TACAR) n e. Infrastructure and e. IRG meetings (Ireland) to consider this topic s n A general EU Grid PKI infrastructure? Data. Grid people will continue in EGEE and GGF u Security n n Policy issues Data. Grid people already active in defining LCG policy and procedures Important input to EGEE and e. IRG David Kelsey - Security - n° 25
Exploitation u Authentication n The CA infrastructure will continue s Discussions started with DEISA and SEEGRID n EGEE will manage the EDG PKI in a new EU PMA n LCG driving the requirements for global physics authentication n Grid CAs to be registered in new TERENA CA repository (TACAR) n e. Infrastructure and e. IRG meetings (Ireland) to consider this topic s n A general EU Grid PKI infrastructure? Data. Grid people will continue in EGEE and GGF u Security n n Policy issues Data. Grid people already active in defining LCG policy and procedures Important input to EGEE and e. IRG David Kelsey - Security - n° 25
 Exploitation (2) u Authorization n n EDG components and people will continue in EGEE, LCG and other projects VOMS is part of LCG-2 s n Integration with Slash. Grid, ACLs (GACL) and Grid. Site s n The HEP applications need roles and groups Joint work with UK Grid. PP, using VOMS and working with PERMIS team Work in GGF security area groups will continue s EDG providing reference implementations in OGSA-Auth. Z s WS-security, VOMS, LCAS, Grid. Site, Slash. Grid etc s XML policy, XACML, VOMS Attribute Certificates, SAML s Will continue to drive and track standards u Publication of the work is ongoing David Kelsey - Security - n° 26
Exploitation (2) u Authorization n n EDG components and people will continue in EGEE, LCG and other projects VOMS is part of LCG-2 s n Integration with Slash. Grid, ACLs (GACL) and Grid. Site s n The HEP applications need roles and groups Joint work with UK Grid. PP, using VOMS and working with PERMIS team Work in GGF security area groups will continue s EDG providing reference implementations in OGSA-Auth. Z s WS-security, VOMS, LCAS, Grid. Site, Slash. Grid etc s XML policy, XACML, VOMS Attribute Certificates, SAML s Will continue to drive and track standards u Publication of the work is ongoing David Kelsey - Security - n° 26
 Summary u Authentication n We have built a large Grid PKI used by many EU projects n strong links to North America and Asia n support for global applications u Authorization n Data. Grid has made major contributions in this area n Established the VO as an important security domain u Future n Much still to be done s n n work & exploitation For example in bio-medical confidentiality The people will continue in EGEE and elsewhere Data. Grid security architecture, design and components will be used David Kelsey - Security - n° 27
Summary u Authentication n We have built a large Grid PKI used by many EU projects n strong links to North America and Asia n support for global applications u Authorization n Data. Grid has made major contributions in this area n Established the VO as an important security domain u Future n Much still to be done s n n work & exploitation For example in bio-medical confidentiality The people will continue in EGEE and elsewhere Data. Grid security architecture, design and components will be used David Kelsey - Security - n° 27


