12a756db9b9ae05fab073fc3626b6070.ppt
- Количество слайдов: 72

Security Protection Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
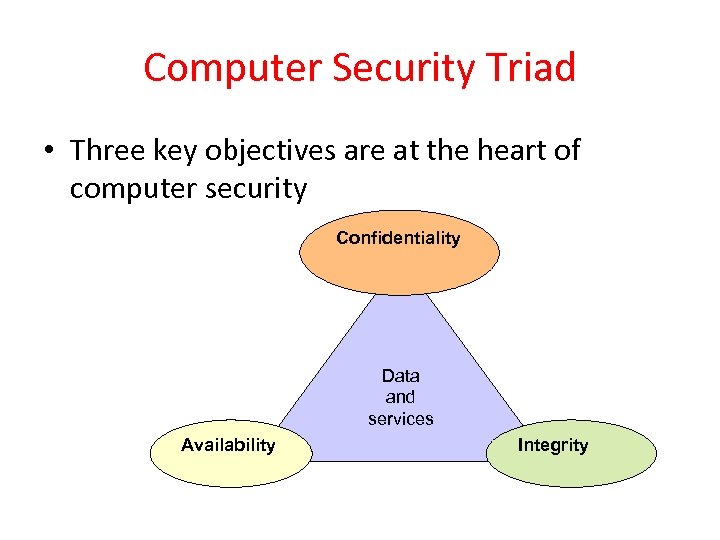
Computer Security Triad • Three key objectives are at the heart of computer security Confidentiality Data and services Availability Integrity
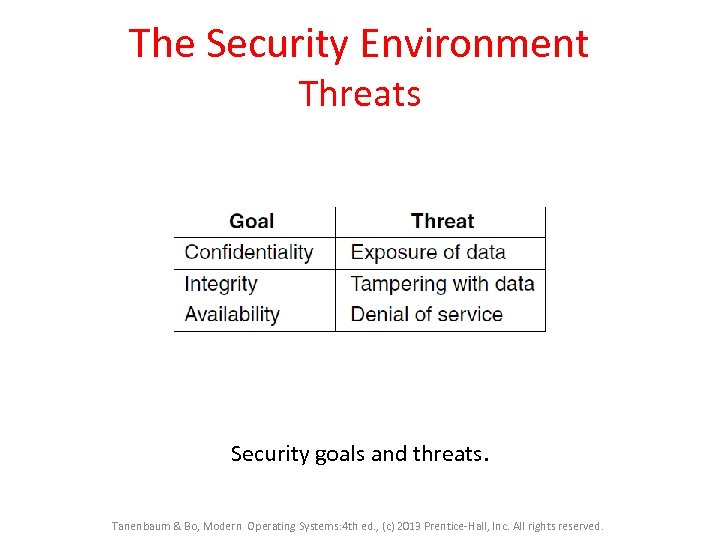
The Security Environment Threats Security goals and threats. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Can We Build Secure Systems? Two questions concerning security: 1. Is it possible to build a secure computer system? 2. If so, why is it not done? Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
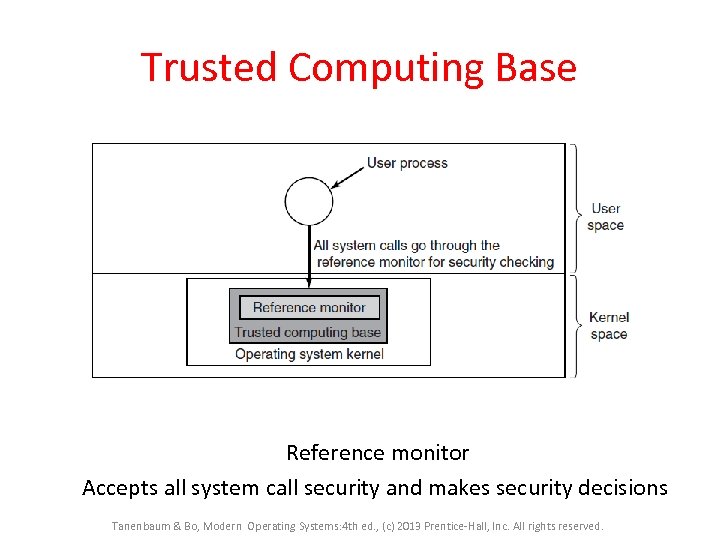
Trusted Computing Base Reference monitor Accepts all system call security and makes security decisions Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Protection Domains • Resources to be protected • Domain is a set of (object, rights)pairs. – Each pair specifies an object and some operation that can be preformed on it. – Right, in this context, means the permission to perform one of the operations. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
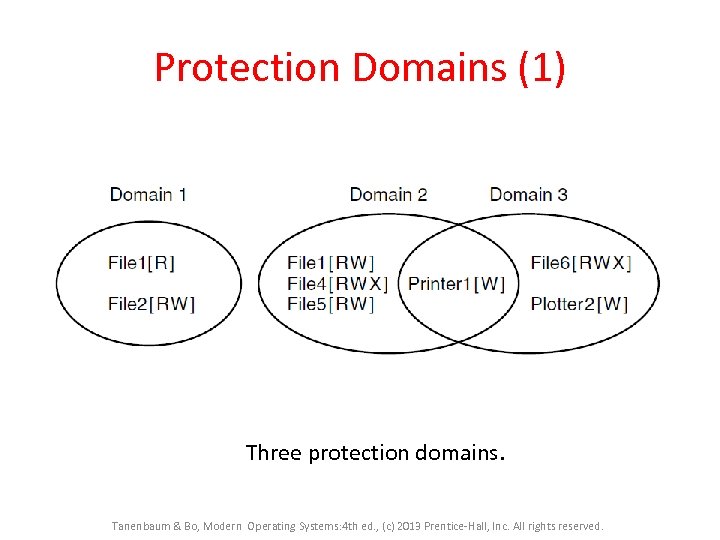
Protection Domains (1) Three protection domains. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Principle of Least Authority In general, Security works best when each domain has the minimum objects and privileges to do its work and no more. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
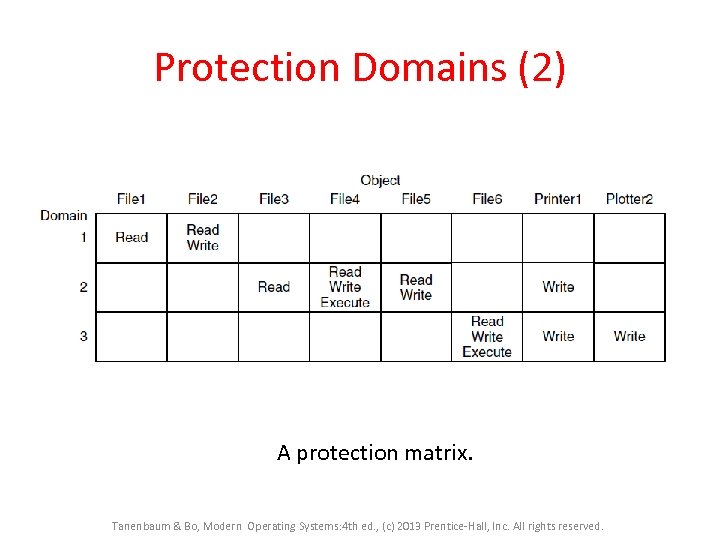
Protection Domains (2) A protection matrix. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
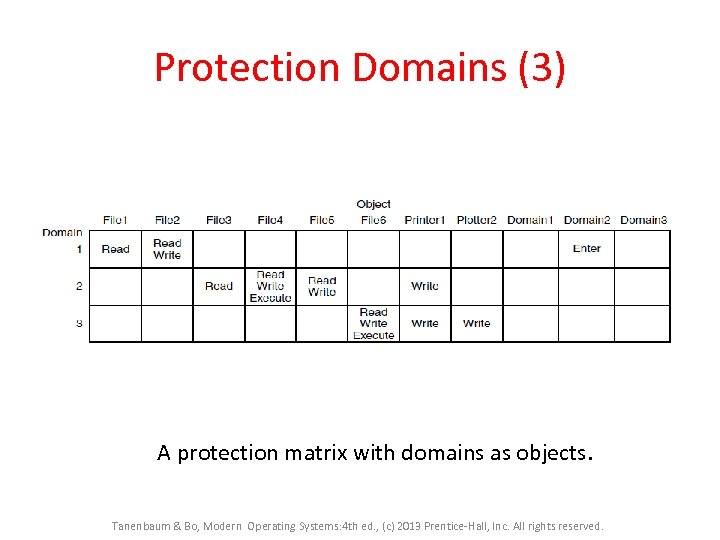
Protection Domains (3) A protection matrix with domains as objects. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
Two methods of implementation • Access Control lists • Capabilities list Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
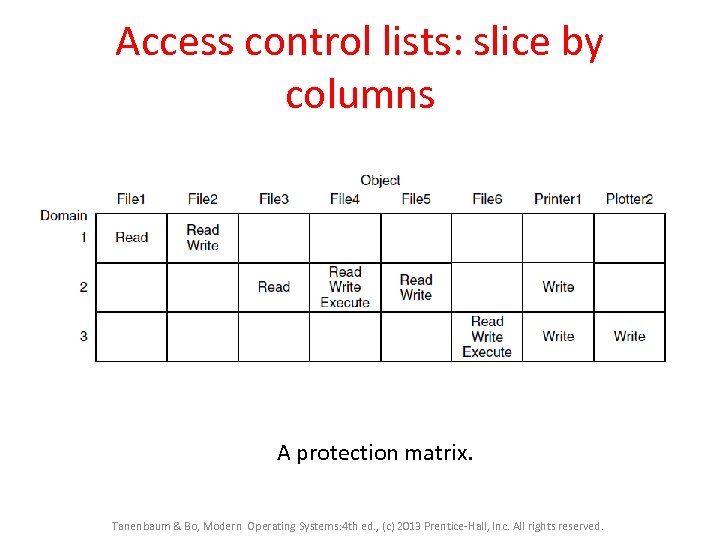
Access control lists: slice by columns A protection matrix. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
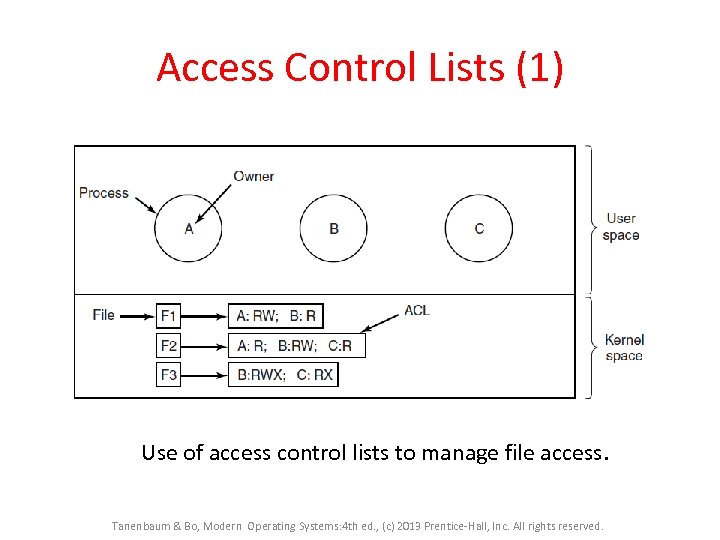
Access Control Lists (1) Use of access control lists to manage file access. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
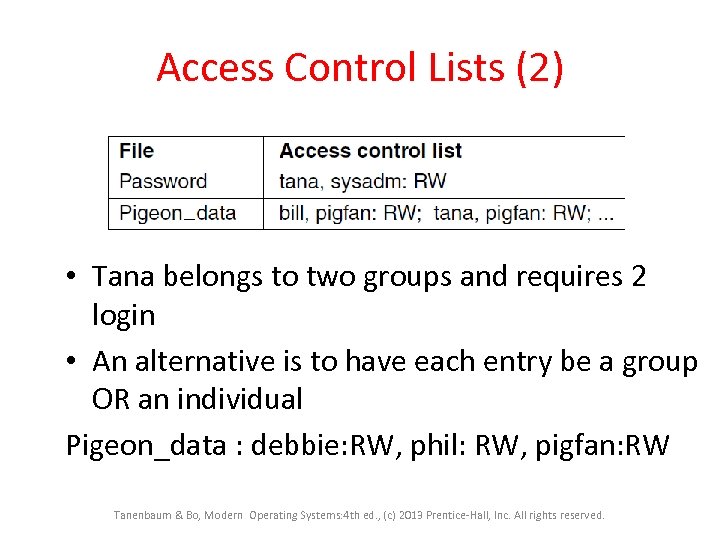
Access Control Lists (2) • Tana belongs to two groups and requires 2 login • An alternative is to have each entry be a group OR an individual Pigeon_data : debbie: RW, phil: RW, pigfan: RW Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Access Control Lists (2) • Easy to change permissions with respect to file • Only check at file open. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
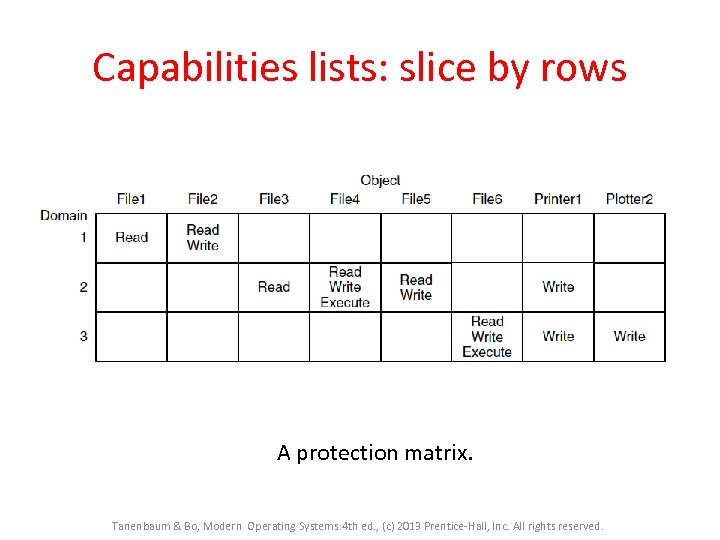
Capabilities lists: slice by rows A protection matrix. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
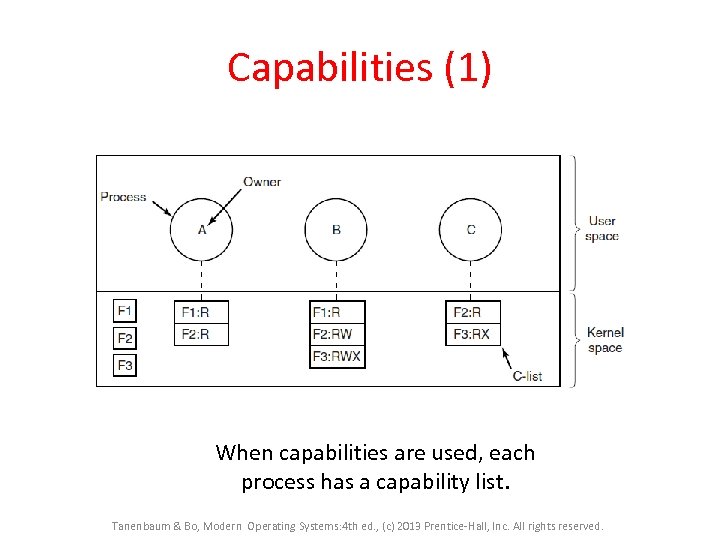
Capabilities (1) When capabilities are used, each process has a capability list. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Capabilities (2) • Protect the list from tampering: • A cryptographically protected capability. • Suited for distributed files Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Cryptographically protected capability list • Client sends a message to remote serve to create a file object. • Server creates the object and generates a long random number ‘check field’ • Slot on the server’s table (inode) is reserved • It is not sent back to the user and never put on the network Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Cryptographically protected capability list • Sent to the user is the capability entry in the form: • Run object, rights, and check through a oneway function (f). • User sends the capability entry when it wants to access the file. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
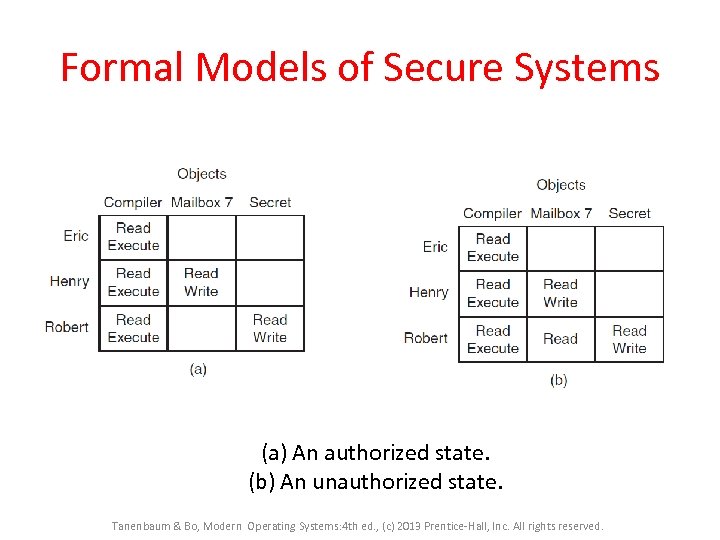
Formal Models of Secure Systems (a) An authorized state. (b) An unauthorized state. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
Multilevel Security • Discretionary Access Control – Operating systems allow individual to determine who may read and write their files • Mandatory Access Control – Organizational rules state who can see and modify what. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
Multilevel Security Bell-La. Padula Model rules for information flow: 1. The simple security property – Process running at security level k can read only objects at its level or lower 2. The * property – Process running at security level k can write only objects at its level or higher Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
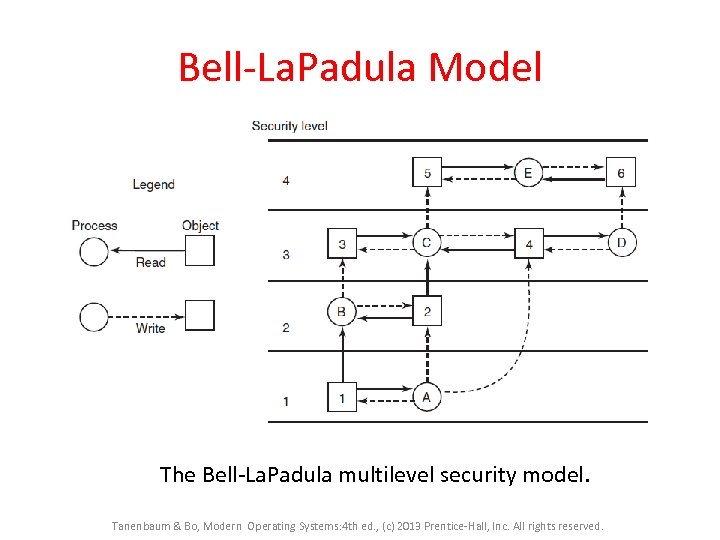
Bell-La. Padula Model The Bell-La. Padula multilevel security model. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Bell-La. Padula Model • The Bell-La. Padula multilevel security model was devised to keep secrets, not guarantee the integrity of data. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
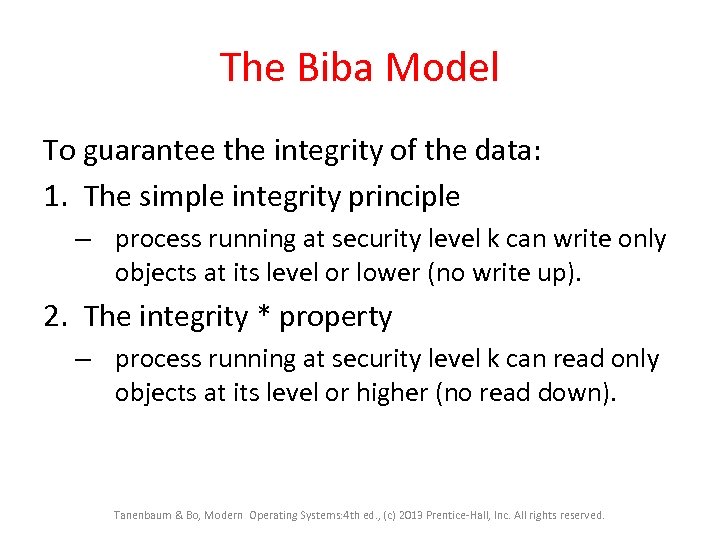
The Biba Model To guarantee the integrity of the data: 1. The simple integrity principle – process running at security level k can write only objects at its level or lower (no write up). 2. The integrity * property – process running at security level k can read only objects at its level or higher (no read down). Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

• BUT… security leaks still can occur Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
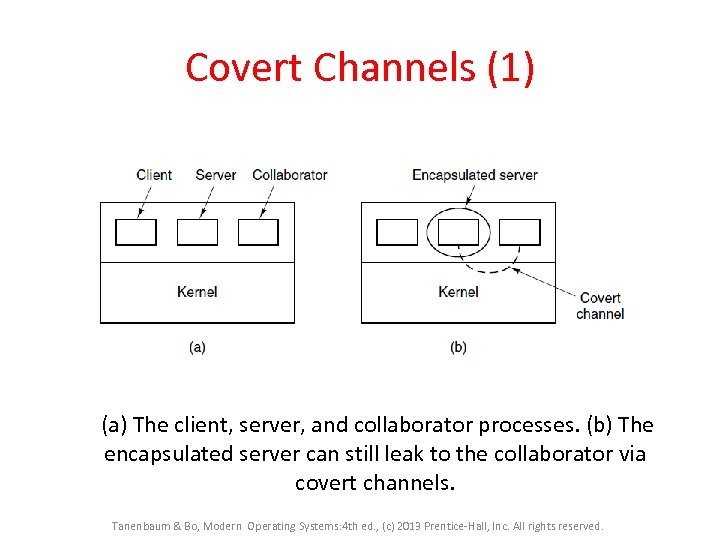
Covert Channels (1) (a) The client, server, and collaborator processes. (b) The encapsulated server can still leak to the collaborator via covert channels. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
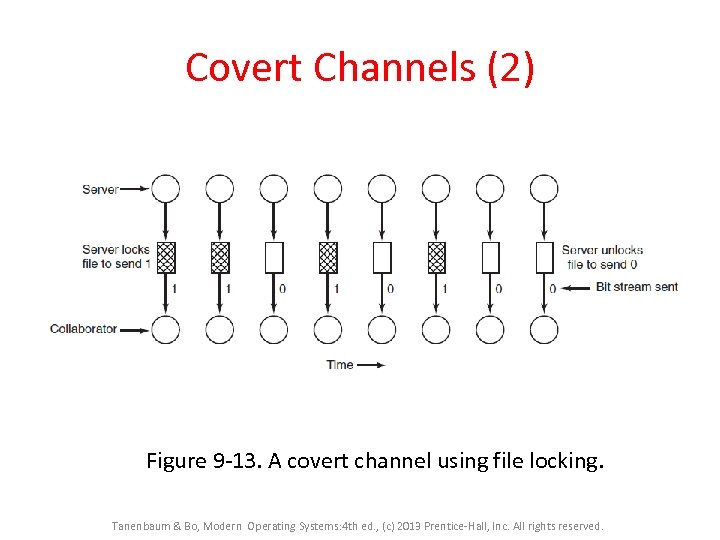
Covert Channels (2) Figure 9 -13. A covert channel using file locking. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Steganography • Concealing secrets in plain site – Hiding secret information in paintings, jpegs, MP 3 files… or messages… or the network Network Security

Steganography example • The German Embassy in Washington, DC, sent these messages in telegrams to their headquarters in Berlin during World War I (Kahn 1996). PRESIDENT'S EMBARGO RULING SHOULD HAVE IMMEDIATE NOTICE. GRAVE SITUATION AFFECTING INTERNATIONAL LAW. STATEMENT FORESHADOWS RUIN OF MANY NEUTRALS. YELLOW JOURNALS UNIFYING NATIONAL EXCITEMENT IMMENSELY. • PERSHING SAILS FROM N. Y. JUNE 1 Network Security
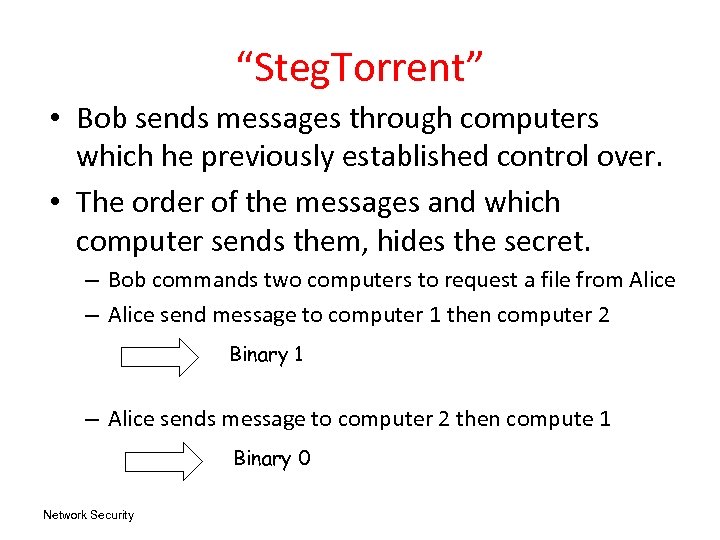
“Steg. Torrent” • Bob sends messages through computers which he previously established control over. • The order of the messages and which computer sends them, hides the secret. – Bob commands two computers to request a file from Alice – Alice send message to computer 1 then computer 2 Binary 1 – Alice sends message to computer 2 then compute 1 Binary 0 Network Security

Skyde (Skype Hide) • Skype packs data into audio packets while Alice is talking • Skype continues to send audio packets when Alice is silent. – This improves the quality of the call and helps data continue to clear firewalls • ‘Silent’ packets are hijacked contents are replaced with encrypted data – Receiver application just assumes the original silent packets were lost • 30% of silent packets can be compromised with out notice Network Security
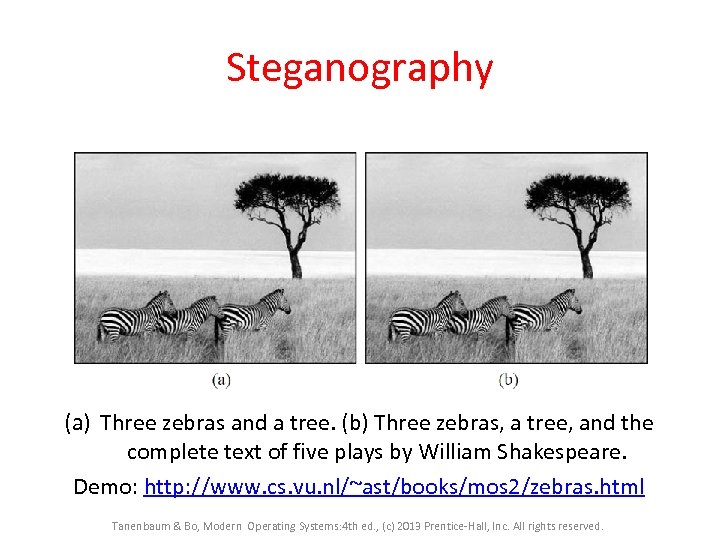
Steganography (a) Three zebras and a tree. (b) Three zebras, a tree, and the complete text of five plays by William Shakespeare. Demo: http: //www. cs. vu. nl/~ast/books/mos 2/zebras. html Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
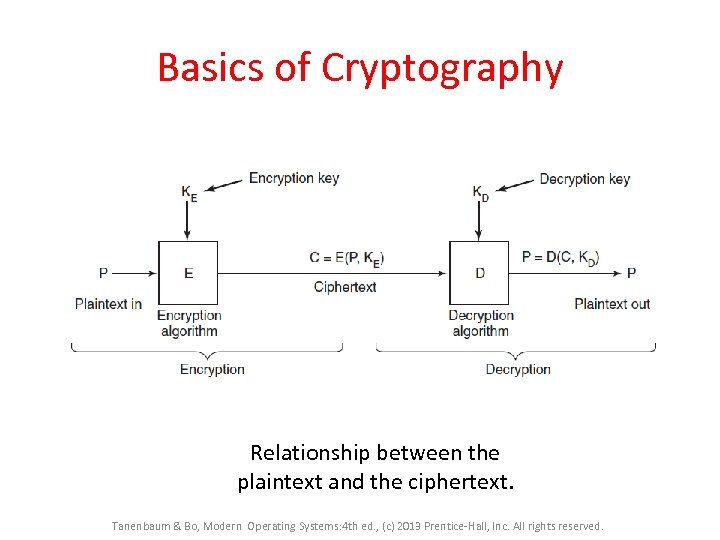
Basics of Cryptography Relationship between the plaintext and the ciphertext. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Secret-Key Cryptography An encryption algorithm in which each letter is replaced by a different letter. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
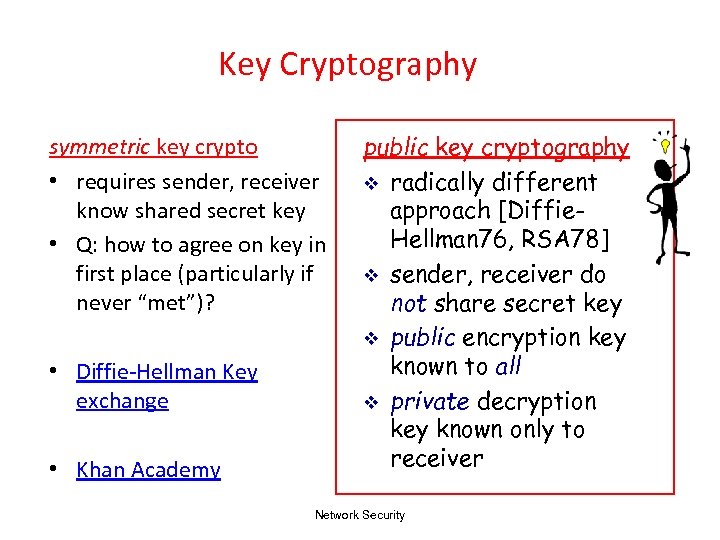
Key Cryptography symmetric key crypto • requires sender, receiver know shared secret key • Q: how to agree on key in first place (particularly if never “met”)? • Diffie-Hellman Key exchange • Khan Academy public key cryptography v radically different approach [Diffie. Hellman 76, RSA 78] v sender, receiver do not share secret key v public encryption key known to all v private decryption key known only to receiver Network Security
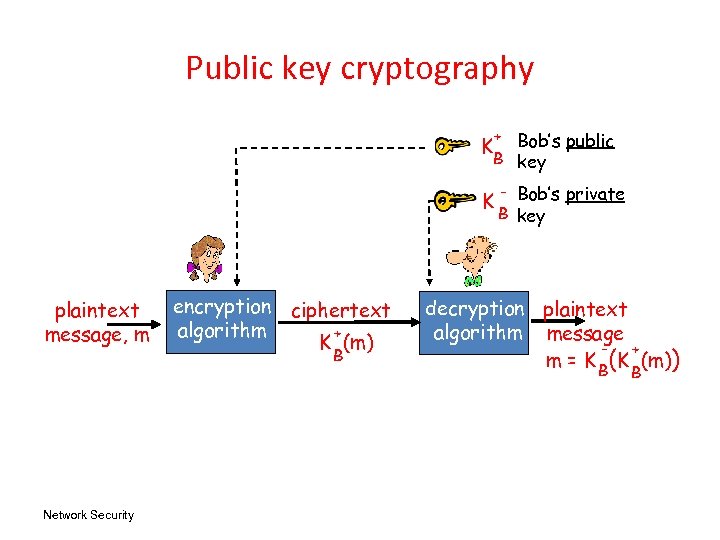
Public key cryptography + Bob’s public B key K K plaintext message, m Network Security encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B
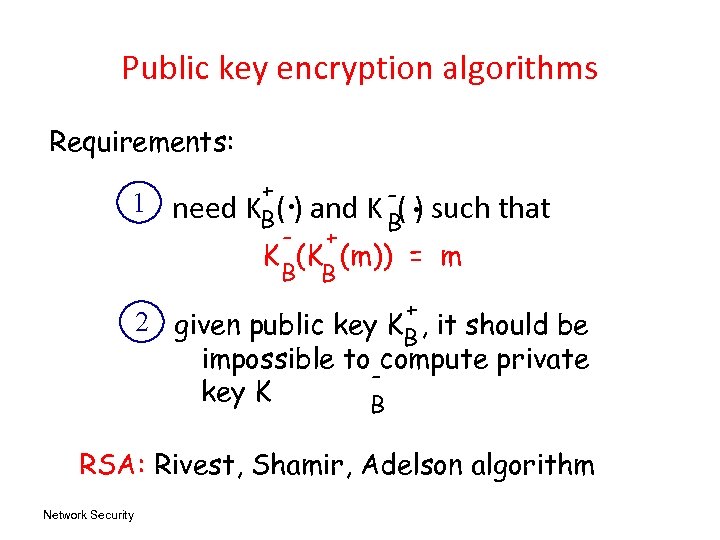
Public key encryption algorithms Requirements: 1 need . . + KB( ) and K B( ) such - + K (K (m)) = m B B that 2 given public key K + , it should be B impossible to compute private key K B RSA: Rivest, Shamir, Adelson algorithm Network Security
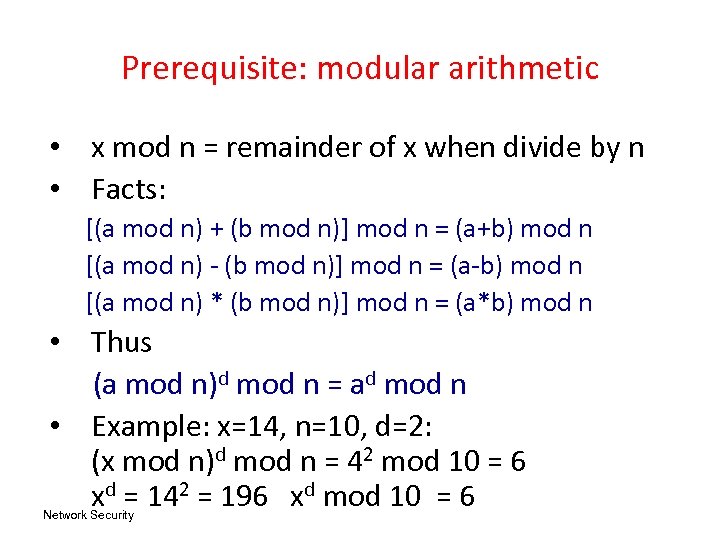
Prerequisite: modular arithmetic • x mod n = remainder of x when divide by n • Facts: [(a mod n) + (b mod n)] mod n = (a+b) mod n [(a mod n) - (b mod n)] mod n = (a-b) mod n [(a mod n) * (b mod n)] mod n = (a*b) mod n • Thus (a mod n)d mod n = ad mod n • Example: x=14, n=10, d=2: (x mod n)d mod n = 42 mod 10 = 6 xd = 142 = 196 xd mod 10 = 6 Network Security

RSA: getting ready • A message is a bit pattern. • A bit pattern can be uniquely represented by an integer number. • Thus encrypting a message is equivalent to encrypting a number. Example • m= 10010001. This message is uniquely represented by the decimal number 145. • To encrypt m, we encrypt the corresponding number, which gives a new number (the ciphertext). Network Security
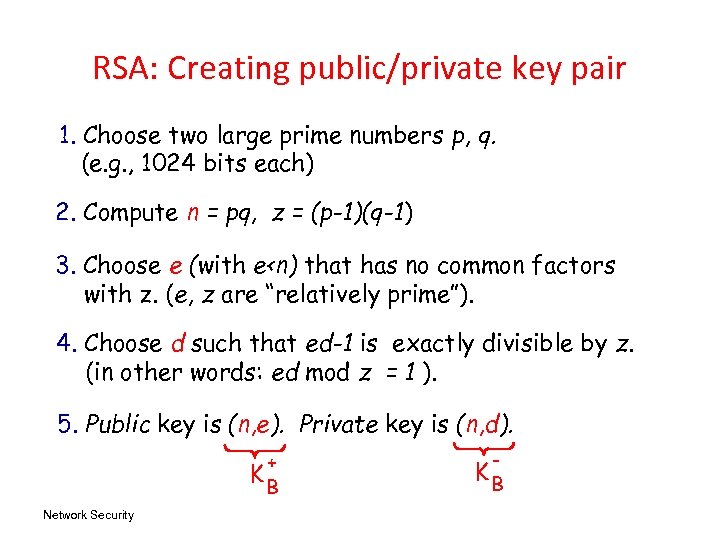
RSA: Creating public/private key pair 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e<n) that has no common factors with z. (e, z are “relatively prime”). 4. Choose d such that ed-1 is exactly divisible by z. (in other words: ed mod z = 1 ). 5. Public key is (n, e). Private key is (n, d). + KB Network Security - KB
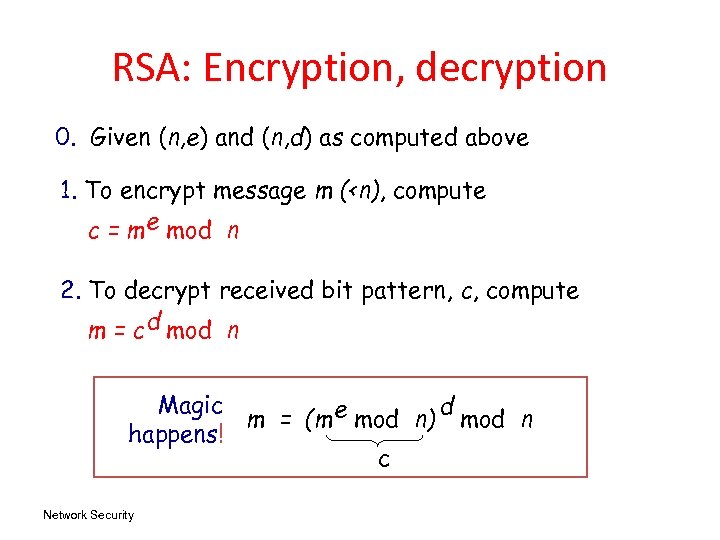
RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt message m (<n), compute c = m e mod n 2. To decrypt received bit pattern, c, compute m = c d mod n Magic d m = (m e mod n) mod n happens! c Network Security
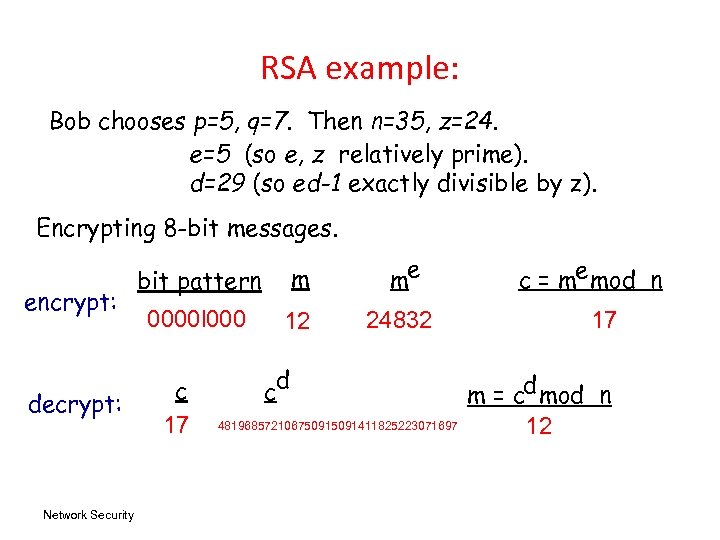
RSA example: Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z). Encrypting 8 -bit messages. encrypt: decrypt: Network Security bit pattern m me 0000 l 000 12 24832 c 17 d c 48196857210675091411825223071697 c = me mod n 17 m = cd mod n 12
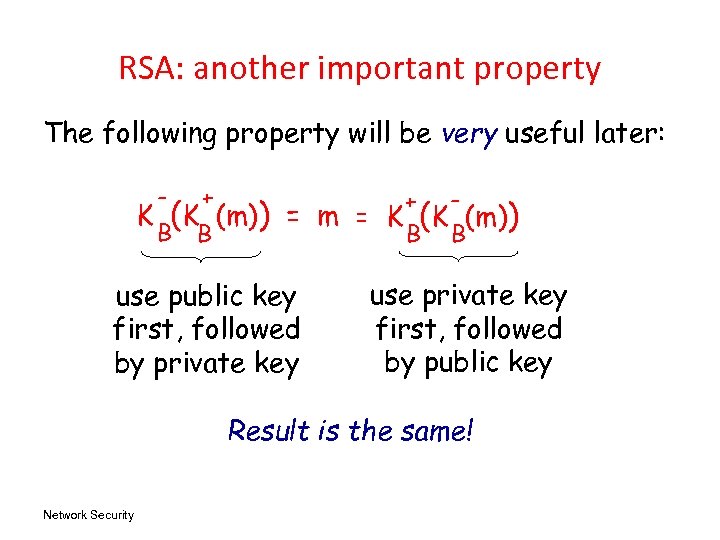
RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! Network Security

Why is RSA Secure? • suppose you know Bob’s public key (n, e). How hard is it to determine d? • essentially need to find factors of n without knowing the two factors p and q. • fact: factoring a big number is hard. Generating RSA keys have to find big primes p and q v approach: make good guess then apply testing rules (see Kaufman) v Network Security

Ensuring Networked Message Integrity • allows communicating parties to verify that received messages are authentic. – Content is not read by anyone other than intended recipient – Content of message has not been altered – Source of message is who/what you think it is: – Message has not been replayed Network Security

Ensuring Networked Message Integrity • Goal: Allow communicating parties to verify that received messages are authentic. – Content is not read by anyone other than intended recipient Encryption – Content of message has not been altered – Source of message is who/what you think it is – Message has not been replayed Network Security

Ensuring Network Message Integrity • allows communicating parties to verify that received messages are authentic. – Content is not read by anyone other than intended recipient Encryption – Content of message has not been altered Message Digests – Source of message is who/what you think it is – Message has not been replayed Network Security
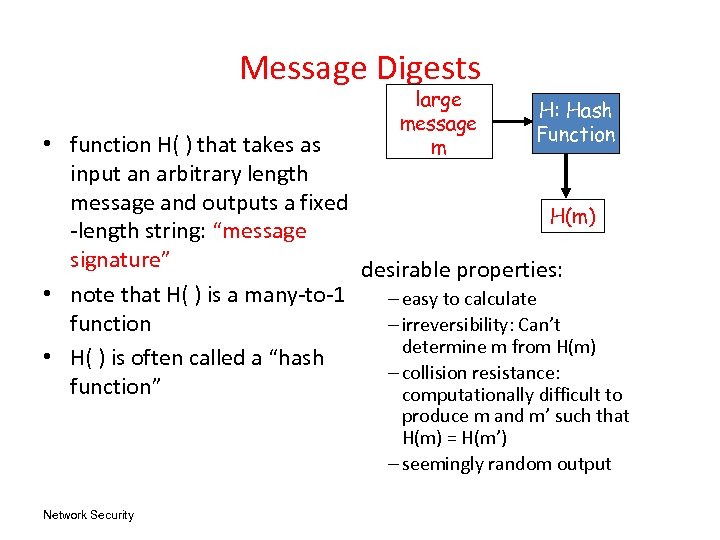
Message Digests large message m H: Hash Function • function H( ) that takes as input an arbitrary length message and outputs a fixed H(m) -length string: “message signature” desirable properties: • note that H( ) is a many-to-1 – easy to calculate function – irreversibility: Can’t determine m from H(m) • H( ) is often called a “hash – collision resistance: function” computationally difficult to produce m and m’ such that H(m) = H(m’) – seemingly random output Network Security

Hashed Message Digest • MD 5 hash function widely used (RFC 1321) – computes 128 -bit message digest in 4 -step process. • SHA-1 is also used. – US standard [NIST, FIPS PUB 180 -1] – 160 -bit message digest Network Security
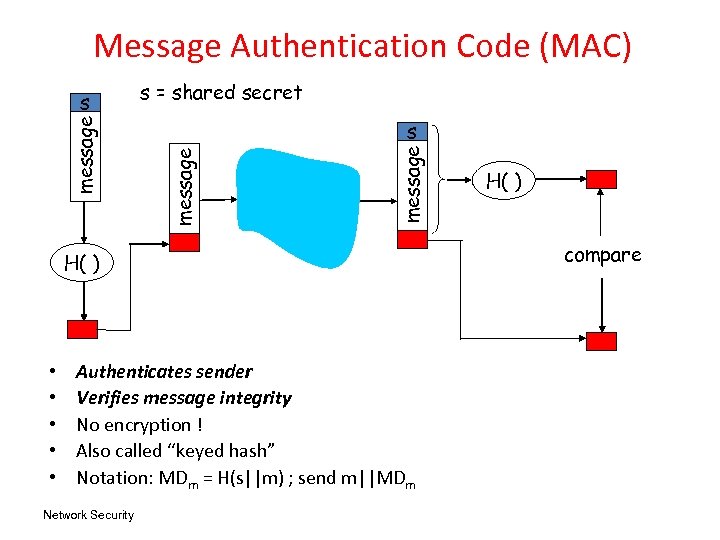
Message Authentication Code (MAC) s = shared secret message s H( ) • • • Authenticates sender Verifies message integrity No encryption ! Also called “keyed hash” Notation: MDm = H(s||m) ; send m||MDm Network Security H( ) compare

Message Integrity • allows communicating parties to verify that received messages are authentic. – Content is not read by anyone other than intended recipient – Content of message has not been altered : Message Digests – Source of message is who/what you think it is: • Digital Signatures • Certification Authority – Message has not been replayed Network Security
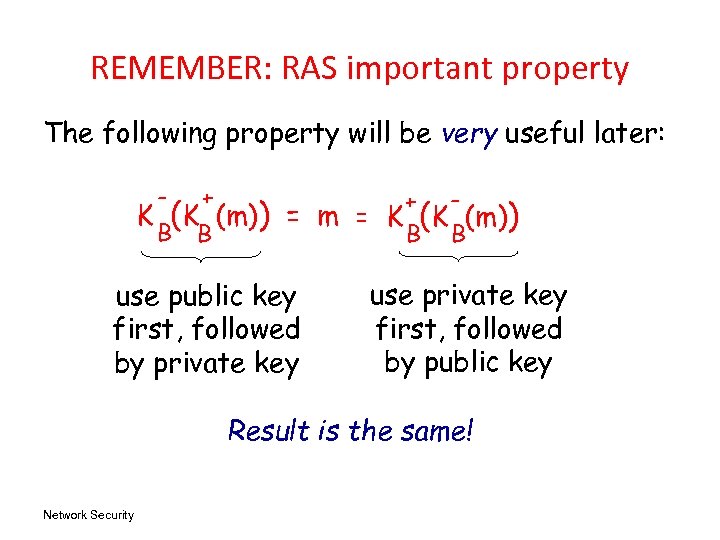
REMEMBER: RAS important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! Network Security

Digital Signatures cryptographic technique analogous to hand-written signatures. • sender (Bob) digitally signs document, establishing he is document owner/creator. • goal is similar to that of MAC, except now use public-key cryptography verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document (Non-repudiation: Alice can take m, and signature KB(m) to court and prove that Bob signed m. ) Network Security
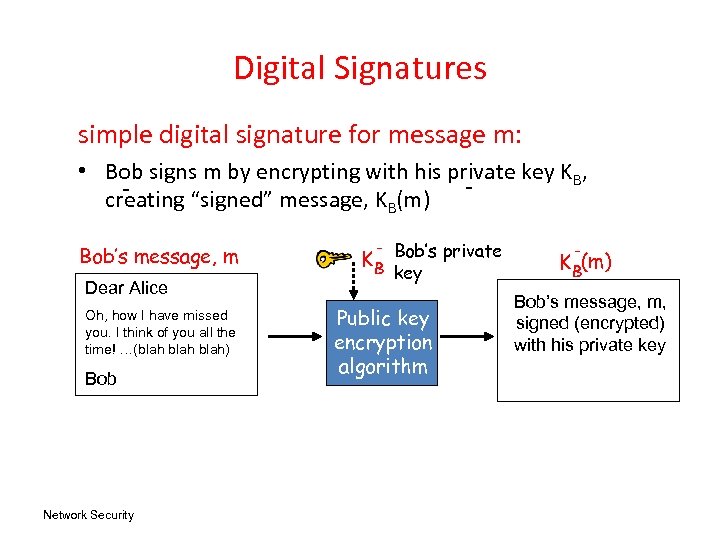
Digital Signatures simple digital signature for message m: • Bob signs m by encrypting with his private key KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob Network Security K B Bob’s private key Public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key
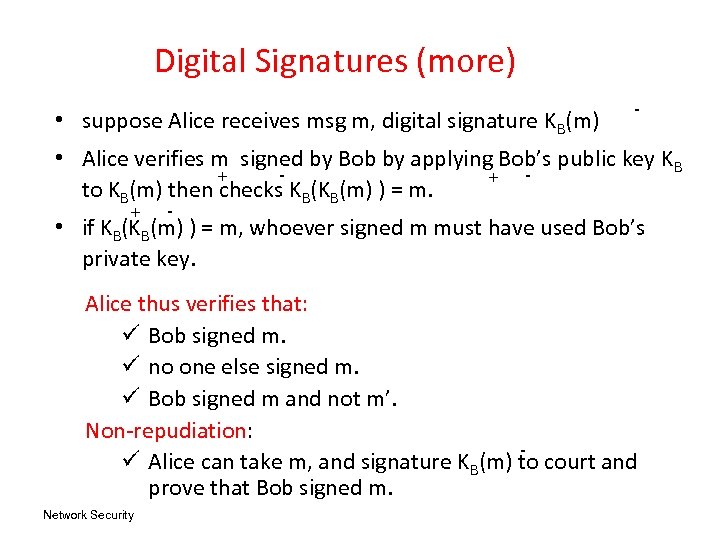
Digital Signatures (more) • suppose Alice receives msg m, digital signature KB(m) - • Alice verifies m signed by Bob by applying Bob’s public key KB + + to KB(m) then checks KB(KB(m) ) = m. + - • if KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü no one else signed m. ü Bob signed m and not m’. Non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. Network Security

Ensuring Message Integrity – Content is not read by anyone other than intended recipient Encryption – Content of message has not been altered Message Digests – Source of message is who/what you think it is Digital Signatures Certification Authority – Message has not been replayed Network Security

Public-key certification • motivation: Trudy plays pizza prank on Bob – Trudy creates e-mail order: Dear Pizza Store, Please deliver to me four pepperoni pizzas. Thank you, Bob – Trudy signs order with her private key – Trudy sends order to Pizza Store – Trudy sends to Pizza Store her public key, but says it’s Bob’s public key. – Pizza Store verifies signature; then delivers four pizzas to Bob. – Bob doesn’t even like Pepperoni Network Security
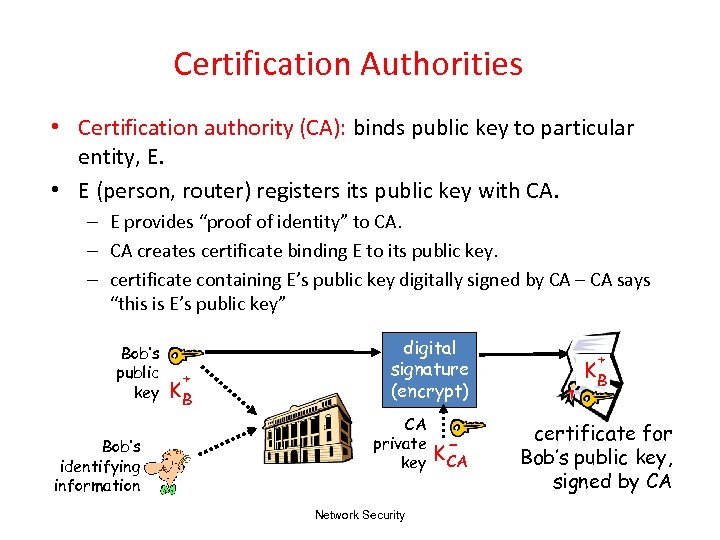
Certification Authorities • Certification authority (CA): binds public key to particular entity, E. • E (person, router) registers its public key with CA. – E provides “proof of identity” to CA. – CA creates certificate binding E to its public key. – certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key Network Security K- CA + KB certificate for Bob’s public key, signed by CA
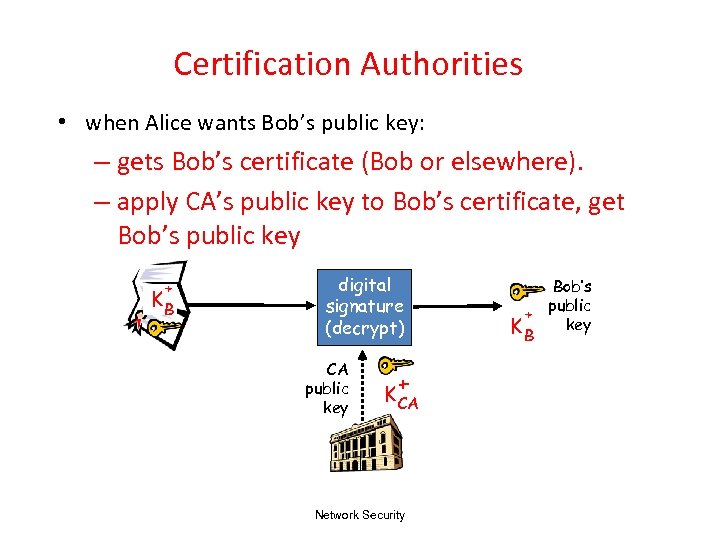
Certification Authorities • when Alice wants Bob’s public key: – gets Bob’s certificate (Bob or elsewhere). – apply CA’s public key to Bob’s certificate, get Bob’s public key + KB digital signature (decrypt) CA public key + K CA Network Security Bob’s public + key KB
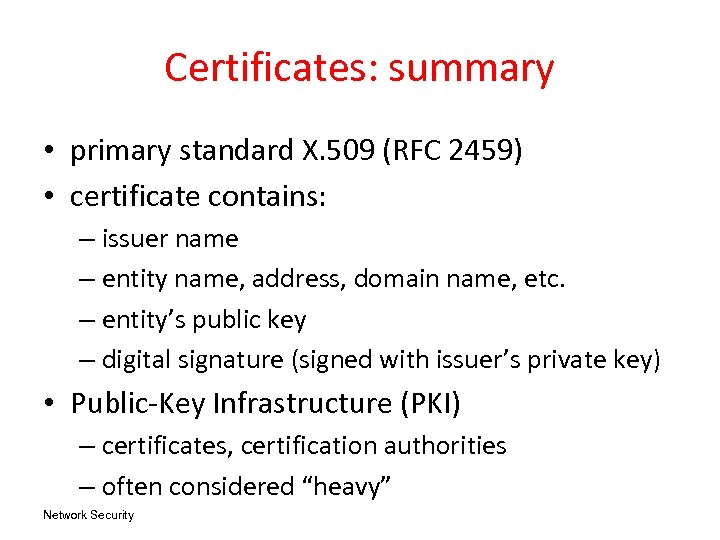
Certificates: summary • primary standard X. 509 (RFC 2459) • certificate contains: – issuer name – entity name, address, domain name, etc. – entity’s public key – digital signature (signed with issuer’s private key) • Public-Key Infrastructure (PKI) – certificates, certification authorities – often considered “heavy” Network Security

Ensuring Message Integrity – Content is not read by anyone other than intended recipient Encryption – Content of message has not been altered Message Digests – Source of message is who/what you think it is Digital Signatures Certification Authority – Message has not been replayed Nonce Network Security

End-point authentication • want to be sure of the originator of the message – end-point authentication • assuming Alice and Bob have a shared secret, will MAC provide end-point authentication? – we do know that Alice created message. – … but did she send it? Network Security
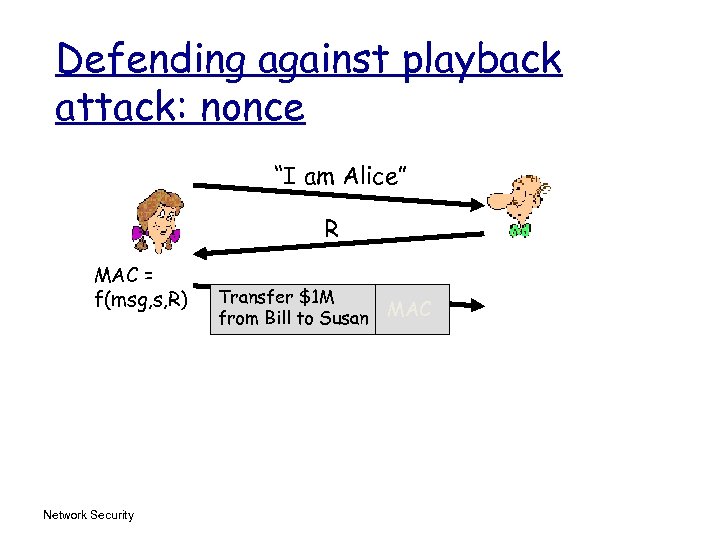
Defending against playback attack: nonce “I am Alice” R MAC = f(msg, s, R) Network Security Transfer $1 M from Bill to Susan MAC

Authentication (1) Methods of authenticating users when they attempt to log in based on one of three general principles: 1. Something the user knows. 2. Something the user has. 3. Something the user is. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Authentication (2) (a) A successful login. (b) Login rejected after name is entered. (c) Login rejected after name and password are typed. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

UNIX Password Security The use of salt to defeat precomputation of encrypted passwords. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

Challenge-Response Authentication Questions should be chosen so that the user does not need to write them down. Examples: 1. On what street was your elementary school? 2. What did Mrs. Ellis teach? Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
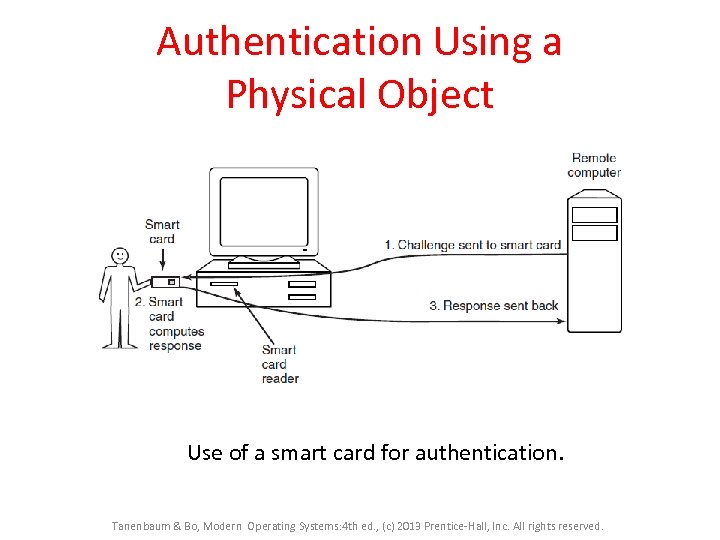
Authentication Using a Physical Object Use of a smart card for authentication. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
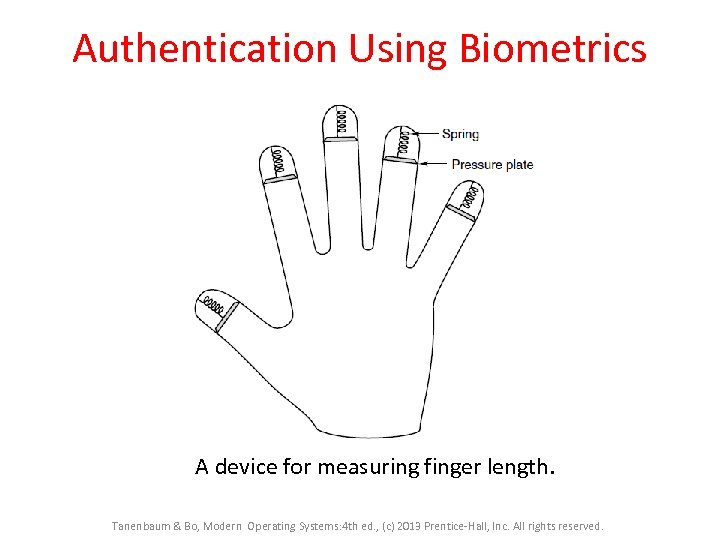
Authentication Using Biometrics A device for measuring finger length. Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.

End of part 1 Tanenbaum & Bo, Modern Operating Systems: 4 th ed. , (c) 2013 Prentice-Hall, Inc. All rights reserved.
12a756db9b9ae05fab073fc3626b6070.ppt