b7dc1dc8e507bb69b1d13767d58ad076.ppt
- Количество слайдов: 17
 Security proofs for practical encryption schemes Yiannis Tsiounis, GTE Labs Moti Yung, Cert. Co LLC
Security proofs for practical encryption schemes Yiannis Tsiounis, GTE Labs Moti Yung, Cert. Co LLC
![Secure encryption z. Semantic Security [GM 84, Gol 89] y. Hide all partial information Secure encryption z. Semantic Security [GM 84, Gol 89] y. Hide all partial information](https://present5.com/presentation/b7dc1dc8e507bb69b1d13767d58ad076/image-2.jpg) Secure encryption z. Semantic Security [GM 84, Gol 89] y. Hide all partial information y. Immune against a-priori knowledge “Security”: Semantic security:
Secure encryption z. Semantic Security [GM 84, Gol 89] y. Hide all partial information y. Immune against a-priori knowledge “Security”: Semantic security:
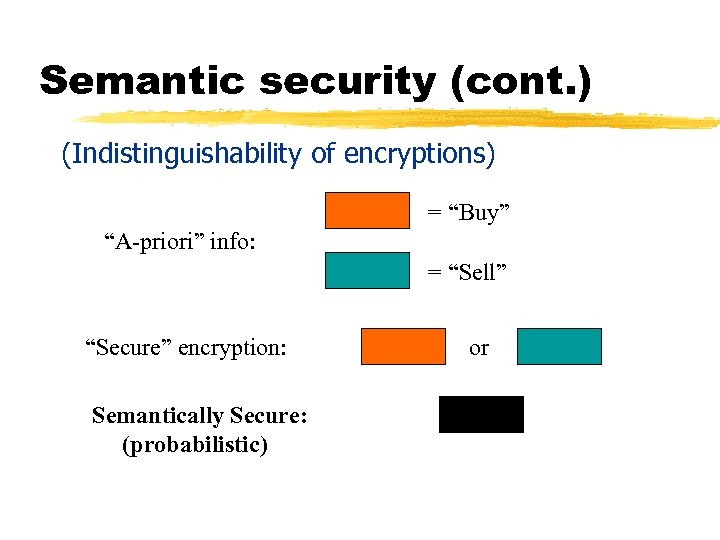 Semantic security (cont. ) (Indistinguishability of encryptions) = “Buy” “A-priori” info: = “Sell” “Secure” encryption: Semantically Secure: (probabilistic) or
Semantic security (cont. ) (Indistinguishability of encryptions) = “Buy” “A-priori” info: = “Sell” “Secure” encryption: Semantically Secure: (probabilistic) or
![Beyond semantic security z. Chosen ciphertext security [NY 90] y“Lunch-time” attack [NY 90] y. Beyond semantic security z. Chosen ciphertext security [NY 90] y“Lunch-time” attack [NY 90] y.](https://present5.com/presentation/b7dc1dc8e507bb69b1d13767d58ad076/image-4.jpg) Beyond semantic security z. Chosen ciphertext security [NY 90] y“Lunch-time” attack [NY 90] y. Rackoff-Simon attack (adaptive) [RS 91] z. Non-malleability [DDN 91] y. Infeasible to create a “related” ciphertext y. Message & sender cannot be altered by manin-the-middle
Beyond semantic security z. Chosen ciphertext security [NY 90] y“Lunch-time” attack [NY 90] y. Rackoff-Simon attack (adaptive) [RS 91] z. Non-malleability [DDN 91] y. Infeasible to create a “related” ciphertext y. Message & sender cannot be altered by manin-the-middle
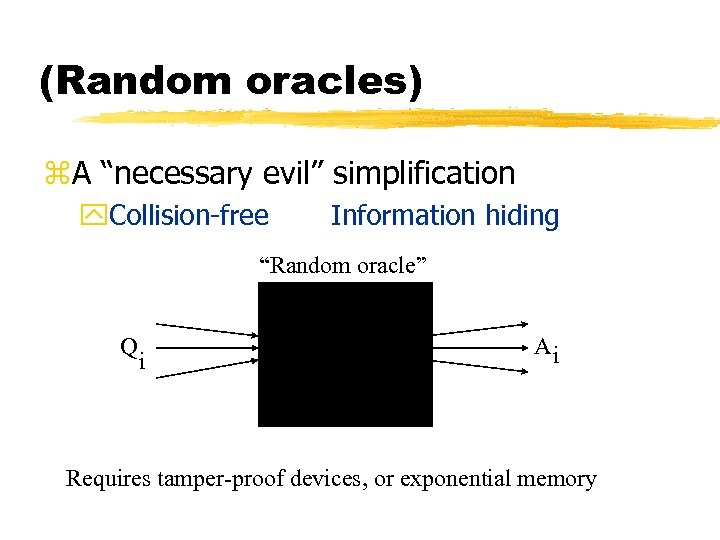 (Random oracles) z. A “necessary evil” simplification y. Collision-free Information hiding “Random oracle” Q i Ai Requires tamper-proof devices, or exponential memory
(Random oracles) z. A “necessary evil” simplification y. Collision-free Information hiding “Random oracle” Q i Ai Requires tamper-proof devices, or exponential memory
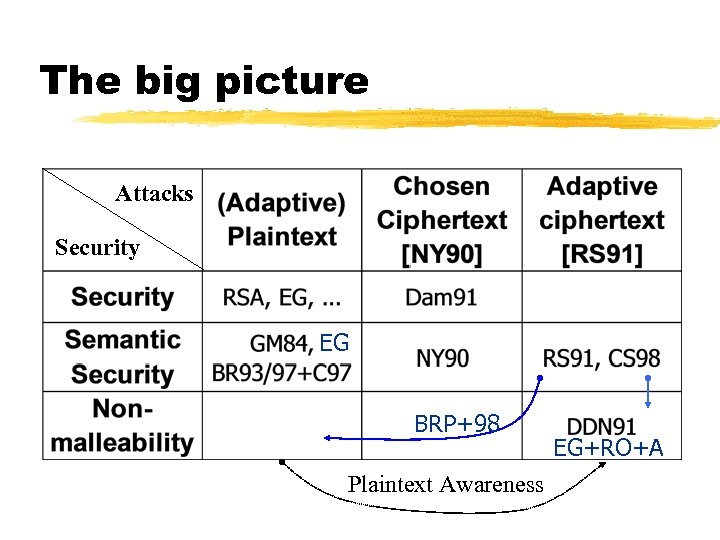 The big picture Attacks Security EG BRP+98 Plaintext Awareness EG+RO+A
The big picture Attacks Security EG BRP+98 Plaintext Awareness EG+RO+A
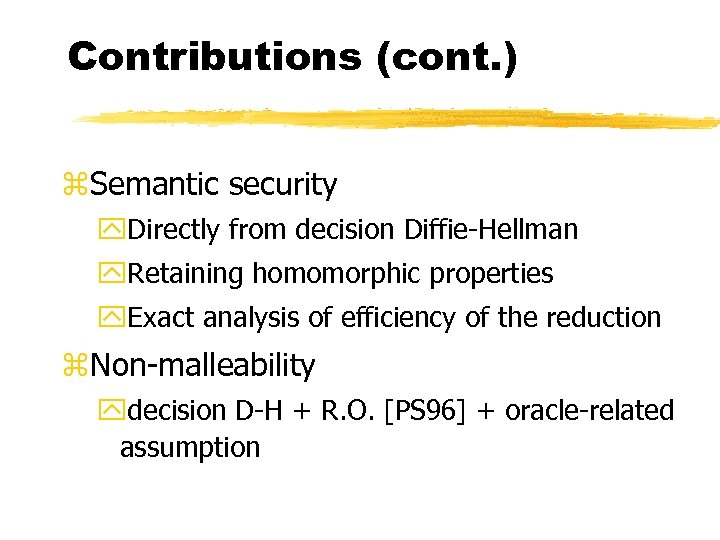 Contributions (cont. ) z. Semantic security y. Directly from decision Diffie-Hellman y. Retaining homomorphic properties y. Exact analysis of efficiency of the reduction z. Non-malleability ydecision D-H + R. O. [PS 96] + oracle-related assumption
Contributions (cont. ) z. Semantic security y. Directly from decision Diffie-Hellman y. Retaining homomorphic properties y. Exact analysis of efficiency of the reduction z. Non-malleability ydecision D-H + R. O. [PS 96] + oracle-related assumption
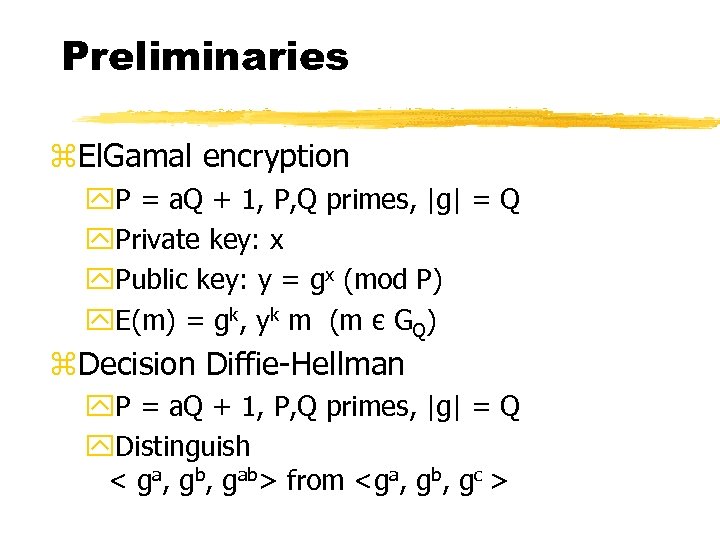 Preliminaries z. El. Gamal encryption y. P = a. Q + 1, P, Q primes, |g| = Q y. Private key: x y. Public key: y = gx (mod P) y. E(m) = gk, yk m (m є GQ) z. Decision Diffie-Hellman y. P = a. Q + 1, P, Q primes, |g| = Q y. Distinguish < ga, gb, gab> from
Preliminaries z. El. Gamal encryption y. P = a. Q + 1, P, Q primes, |g| = Q y. Private key: x y. Public key: y = gx (mod P) y. E(m) = gk, yk m (m є GQ) z. Decision Diffie-Hellman y. P = a. Q + 1, P, Q primes, |g| = Q y. Distinguish < ga, gb, gab> from
 Preliminaries (cont. ) z. Semantic security = indistinguishability of encryptions: It is infeasible to find 2 messages whose encryptions can be distinguished (nonnegl. better than random guessing)
Preliminaries (cont. ) z. Semantic security = indistinguishability of encryptions: It is infeasible to find 2 messages whose encryptions can be distinguished (nonnegl. better than random guessing)
 El. Gamal => decision D-H z. Assume we have El. Gamal oracle z. Given a triplet
El. Gamal => decision D-H z. Assume we have El. Gamal oracle z. Given a triplet
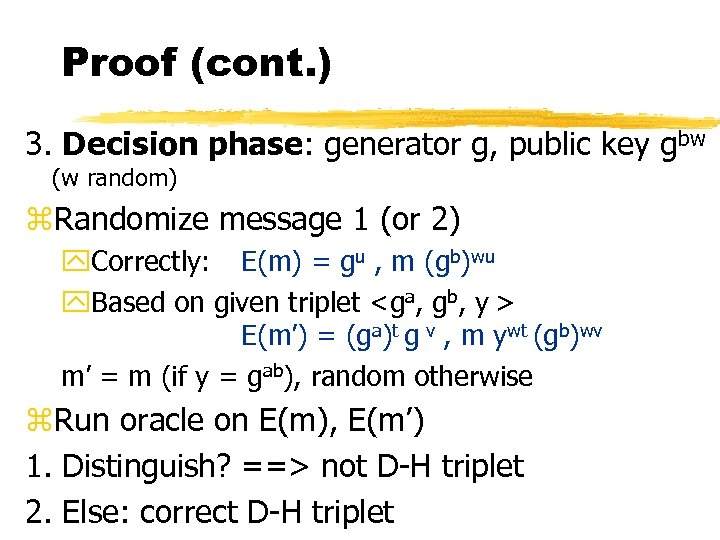 Proof (cont. ) 3. Decision phase: generator g, public key gbw (w random) z. Randomize message 1 (or 2) y. Correctly: E(m) = gu , m (gb)wu y. Based on given triplet
Proof (cont. ) 3. Decision phase: generator g, public key gbw (w random) z. Randomize message 1 (or 2) y. Correctly: E(m) = gu , m (gb)wu y. Based on given triplet
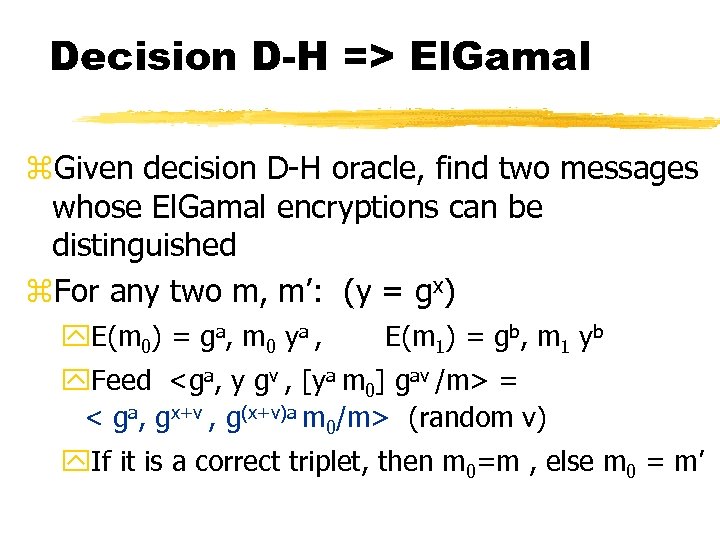 Decision D-H => El. Gamal z. Given decision D-H oracle, find two messages whose El. Gamal encryptions can be distinguished z. For any two m, m’: (y = gx) y. E(m 0) = ga, m 0 ya , E(m 1) = gb, m 1 yb y. Feed
Decision D-H => El. Gamal z. Given decision D-H oracle, find two messages whose El. Gamal encryptions can be distinguished z. For any two m, m’: (y = gx) y. E(m 0) = ga, m 0 ya , E(m 1) = gb, m 1 yb y. Feed
 Non-malleability z. Given ciphertext C, cannot construct ciphertext C’ such that the plaintexts are related z. All we need is a proof of knowledge of the plaintext y. I. e. , a proof of knowledge of k in E(m) = gk, yk m y. But, it must be a non-malleable ZK proof: it must be bound to the prover
Non-malleability z. Given ciphertext C, cannot construct ciphertext C’ such that the plaintexts are related z. All we need is a proof of knowledge of the plaintext y. I. e. , a proof of knowledge of k in E(m) = gk, yk m y. But, it must be a non-malleable ZK proof: it must be bound to the prover
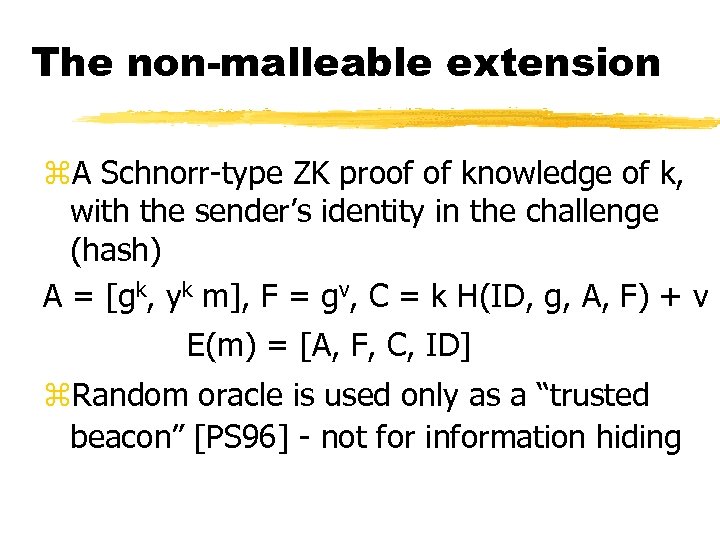 The non-malleable extension z. A Schnorr-type ZK proof of knowledge of k, with the sender’s identity in the challenge (hash) A = [gk, yk m], F = gv, C = k H(ID, g, A, F) + v E(m) = [A, F, C, ID] z. Random oracle is used only as a “trusted beacon” [PS 96] - not for information hiding
The non-malleable extension z. A Schnorr-type ZK proof of knowledge of k, with the sender’s identity in the challenge (hash) A = [gk, yk m], F = gv, C = k H(ID, g, A, F) + v E(m) = [A, F, C, ID] z. Random oracle is used only as a “trusted beacon” [PS 96] - not for information hiding
 Security proof 1. We need to verify that semantic security still holds (the knowledge proof does not leak information) 2. Knowledge of k: provided from Schnorr proof 3. Sender-bound: the addition forms a Schnorr signature of ID based on k, which is existentially unforgeable [PS 96]
Security proof 1. We need to verify that semantic security still holds (the knowledge proof does not leak information) 2. Knowledge of k: provided from Schnorr proof 3. Sender-bound: the addition forms a Schnorr signature of ID based on k, which is existentially unforgeable [PS 96]
![Practical implications: Encryption z. El. Gamal is as secure as [BR 94+Can 97] z. Practical implications: Encryption z. El. Gamal is as secure as [BR 94+Can 97] z.](https://present5.com/presentation/b7dc1dc8e507bb69b1d13767d58ad076/image-16.jpg) Practical implications: Encryption z. El. Gamal is as secure as [BR 94+Can 97] z. Non-malleability can be added at minimal efficiency costs z. In applications a signature is still needed y. Otherwise senders can be impersonated y. Signatures using Schnorr-proofs is a smooth addition
Practical implications: Encryption z. El. Gamal is as secure as [BR 94+Can 97] z. Non-malleability can be added at minimal efficiency costs z. In applications a signature is still needed y. Otherwise senders can be impersonated y. Signatures using Schnorr-proofs is a smooth addition
 Implications: protocols z. First encryption scheme with homomorphic properties that is semantically secure z. Anonymous e-cash: escrowing can be performed based on decision D-H
Implications: protocols z. First encryption scheme with homomorphic properties that is semantically secure z. Anonymous e-cash: escrowing can be performed based on decision D-H


