ef4b56e60e6d8f484a9a859568e5c70b.ppt
- Количество слайдов: 27
 Security Outsourcing Melissa Karolewski
Security Outsourcing Melissa Karolewski
 Overview • Introduction • Definitions • Offshoring • MSSP • Outsourcing Advice • Vendors • MSSPs • Benefits & Risks • • • Security Audits Cyberinsurance Some Popular MSSPs Graphs & Charts Conclusion References
Overview • Introduction • Definitions • Offshoring • MSSP • Outsourcing Advice • Vendors • MSSPs • Benefits & Risks • • • Security Audits Cyberinsurance Some Popular MSSPs Graphs & Charts Conclusion References
 Introduction • Outsourcing can sometimes be critical for a business in order to maintain company objectives. • Many pros and cons to outsourcing security. • Can cost up to 50% less than in-house security. • Still is not known whether outsourcing security is beneficial or hazardous.
Introduction • Outsourcing can sometimes be critical for a business in order to maintain company objectives. • Many pros and cons to outsourcing security. • Can cost up to 50% less than in-house security. • Still is not known whether outsourcing security is beneficial or hazardous.
 What is outsourcing? • Delegation of non-core operations or jobs from internal production within a business to an external entity (such as a subcontractor) that specializes in that operation. Outsourcing is a business decision that is often made to lower costs or focus on competencies. • (Wikipedia, 2006)
What is outsourcing? • Delegation of non-core operations or jobs from internal production within a business to an external entity (such as a subcontractor) that specializes in that operation. Outsourcing is a business decision that is often made to lower costs or focus on competencies. • (Wikipedia, 2006)
 Other Definitions • Offshoring: transferring work to another country, often overseas is also a type of outsourcing. • Common type of outsourcing vendor is Managed Security Service Providers (MSSP)
Other Definitions • Offshoring: transferring work to another country, often overseas is also a type of outsourcing. • Common type of outsourcing vendor is Managed Security Service Providers (MSSP)
 Why Outsource? • Cost • Lack of Qualified Individuals • Reliability
Why Outsource? • Cost • Lack of Qualified Individuals • Reliability
 Security Areas that are Outsourced • Intrusion Detection (IDS’s) • Firewalls • VPNs • Security monitoring • Incident management • Emergency response and forensic analysis • Vulnerability assessment • Penetration testing • Anti-virus • Content filtering services • Information security risk assessments • Data archiving and restoration • On-site consulting • http: //www. cert. org/security-improvement/modules/omss/c. html
Security Areas that are Outsourced • Intrusion Detection (IDS’s) • Firewalls • VPNs • Security monitoring • Incident management • Emergency response and forensic analysis • Vulnerability assessment • Penetration testing • Anti-virus • Content filtering services • Information security risk assessments • Data archiving and restoration • On-site consulting • http: //www. cert. org/security-improvement/modules/omss/c. html
 Outsourcing Advice • Involve department staff in application outsourcing decisions. • Compare variable in-house costs with fixed outsourcing costs. • Evaluate multiple vendor quotes for security, reliability and problem resolution. • Prepare to work with emerging companies and have contingency plans. • Consider the social dynamics of outsourcing a workforce vs. a company-career model. • Evaluate global vs. national outsourcing for cost and business process. • Consider application outsourcing for upgrading platforms and adding new capability. • Use tools to standardize and manage outsourcing. • http: //www. networkworld. com/careers/2002/0527 man. html
Outsourcing Advice • Involve department staff in application outsourcing decisions. • Compare variable in-house costs with fixed outsourcing costs. • Evaluate multiple vendor quotes for security, reliability and problem resolution. • Prepare to work with emerging companies and have contingency plans. • Consider the social dynamics of outsourcing a workforce vs. a company-career model. • Evaluate global vs. national outsourcing for cost and business process. • Consider application outsourcing for upgrading platforms and adding new capability. • Use tools to standardize and manage outsourcing. • http: //www. networkworld. com/careers/2002/0527 man. html
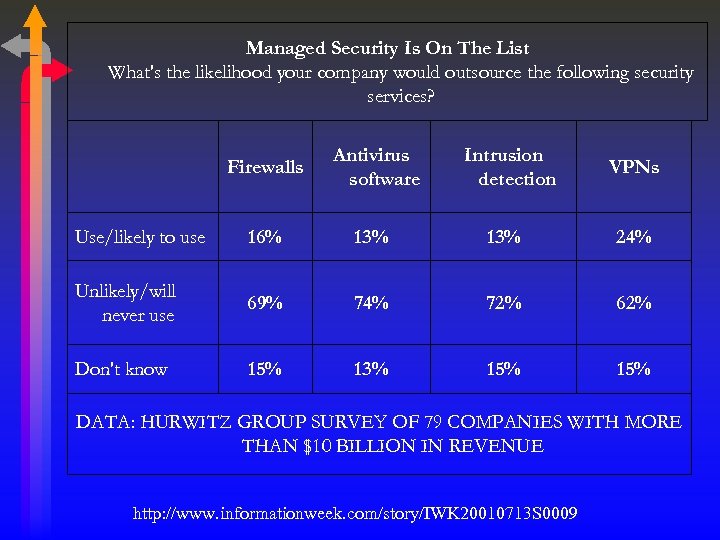 Managed Security Is On The List What's the likelihood your company would outsource the following security services? Firewalls Antivirus software Use/likely to use 16% 13% Unlikely/will never use 69% Don't know 15% Intrusion detection VPNs 13% 24% 72% 62% 13% 15% DATA: HURWITZ GROUP SURVEY OF 79 COMPANIES WITH MORE THAN $10 BILLION IN REVENUE http: //www. informationweek. com/story/IWK 20010713 S 0009
Managed Security Is On The List What's the likelihood your company would outsource the following security services? Firewalls Antivirus software Use/likely to use 16% 13% Unlikely/will never use 69% Don't know 15% Intrusion detection VPNs 13% 24% 72% 62% 13% 15% DATA: HURWITZ GROUP SURVEY OF 79 COMPANIES WITH MORE THAN $10 BILLION IN REVENUE http: //www. informationweek. com/story/IWK 20010713 S 0009
 Benefits of Security Outsourcing • Cost • Can cost up to 1/2 as much. • Recent data points to only a 15% savings. • “Establishing a solid cyber incident response team means hiring approximately 18 employees and making an initial investment of almost $6 million, according to statistics from Gartner, an international IT research firm. ”(Lawson, 2000) • Vendor can provide: • • • Adequate Staffing Well Trained Individuals Better facilities Connection with law enforcement. 24/7 Monitoring • Focused Objective and Plan • Security Awareness
Benefits of Security Outsourcing • Cost • Can cost up to 1/2 as much. • Recent data points to only a 15% savings. • “Establishing a solid cyber incident response team means hiring approximately 18 employees and making an initial investment of almost $6 million, according to statistics from Gartner, an international IT research firm. ”(Lawson, 2000) • Vendor can provide: • • • Adequate Staffing Well Trained Individuals Better facilities Connection with law enforcement. 24/7 Monitoring • Focused Objective and Plan • Security Awareness
 Risks of Security Outsourcing • Possibility of dependence • Partnership Failure • Lack of communication • Legal Issues • Trust • Must have trust in company • Signed Confidentiality Agreements
Risks of Security Outsourcing • Possibility of dependence • Partnership Failure • Lack of communication • Legal Issues • Trust • Must have trust in company • Signed Confidentiality Agreements
 Choosing a Good Vendor • Choose a vendor that requires top-secret clearance. • If they work for the government, then they are probably reputable. • Background Checks • Research the Company • Other companies experiences
Choosing a Good Vendor • Choose a vendor that requires top-secret clearance. • If they work for the government, then they are probably reputable. • Background Checks • Research the Company • Other companies experiences
 Security Vendors • Charge an average of $300 an hour. • Some are just reformed hackers • MSSP Managed Security Service Providers • • Symantec AT&T Secure. Works ISS. net
Security Vendors • Charge an average of $300 an hour. • Some are just reformed hackers • MSSP Managed Security Service Providers • • Symantec AT&T Secure. Works ISS. net
 MSSP • a company that handles network security services (such as intrusion detection and prevention, spam blocking and firewall capabilities) for its clients. MSSPs are outsourcing providers. • http: //www. csoonline. com/glossary/term. cfm? ID=3331. • Provides services in areas that companies wish to outsource security. • Benefits and Risks, listed above.
MSSP • a company that handles network security services (such as intrusion detection and prevention, spam blocking and firewall capabilities) for its clients. MSSPs are outsourcing providers. • http: //www. csoonline. com/glossary/term. cfm? ID=3331. • Provides services in areas that companies wish to outsource security. • Benefits and Risks, listed above.
 Continued Evaluation of a MSSP • Security Audits • systematic evaluation of the security of a company's information system by measuring how well it conforms to a set of established criteria. • often used to determine regulatory compliance, in the wake of legislation • HIPAA, the Sarbanes-Oxley Act, and the California Security Breach Information Act • (Security Audit, n. d. )
Continued Evaluation of a MSSP • Security Audits • systematic evaluation of the security of a company's information system by measuring how well it conforms to a set of established criteria. • often used to determine regulatory compliance, in the wake of legislation • HIPAA, the Sarbanes-Oxley Act, and the California Security Breach Information Act • (Security Audit, n. d. )
 Cyberinsruance • Covers a number of areas not normally spelled out in traditional policies. • Can be thought as a means of outsourcing, since it is a “written” protection from an outside vendor. • Further protect security. • Insurance discounts. • Can cover insider attacks.
Cyberinsruance • Covers a number of areas not normally spelled out in traditional policies. • Can be thought as a means of outsourcing, since it is a “written” protection from an outside vendor. • Further protect security. • Insurance discounts. • Can cover insider attacks.
 Popular MSSPs • Symantec • Offers security packages for all computer users, from personal use to small business and enterprise use. • MSS services offered: • Firewall/VPN • Intrusion Detection • Integrated Security Appliance • http: //www. symantec. com. • Secure. Works • Offers many types of protection. • SC Magazines “Best Intrusion Protection Award” • NSS approved award • http: //www. secureworks. com • ISS. net • Offers many services • Has been around since 1995 • Sys. Trust
Popular MSSPs • Symantec • Offers security packages for all computer users, from personal use to small business and enterprise use. • MSS services offered: • Firewall/VPN • Intrusion Detection • Integrated Security Appliance • http: //www. symantec. com. • Secure. Works • Offers many types of protection. • SC Magazines “Best Intrusion Protection Award” • NSS approved award • http: //www. secureworks. com • ISS. net • Offers many services • Has been around since 1995 • Sys. Trust
 Symantec
Symantec
 Secure. Works
Secure. Works
 ISS. net
ISS. net
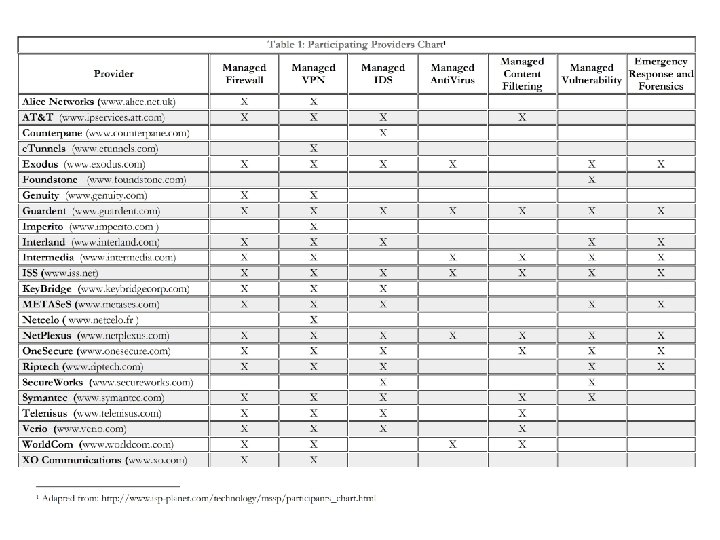
 The KPMG Global Information Security Survey 2002 http: //www. cisco. com/warp/public/cc/so/neso/sqso/mnsqss/prodlit/sosfm_ov/sosfm_o 4. jpg
The KPMG Global Information Security Survey 2002 http: //www. cisco. com/warp/public/cc/so/neso/sqso/mnsqss/prodlit/sosfm_ov/sosfm_o 4. jpg
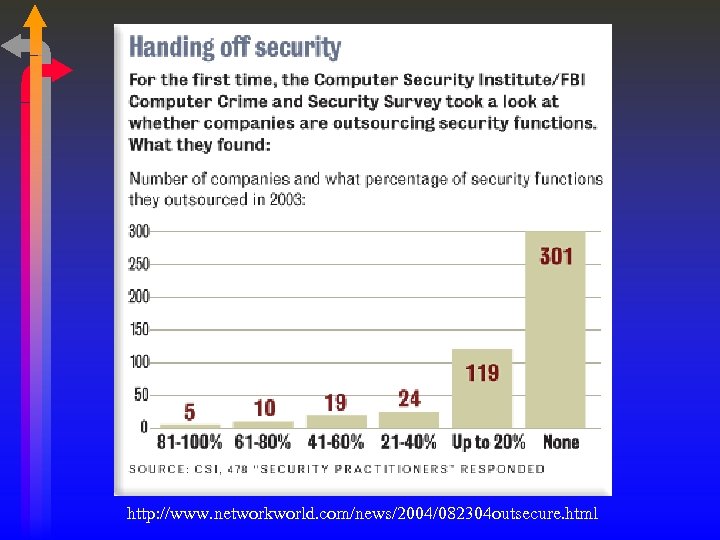 http: //www. networkworld. com/news/2004/082304 outsecure. html
http: //www. networkworld. com/news/2004/082304 outsecure. html
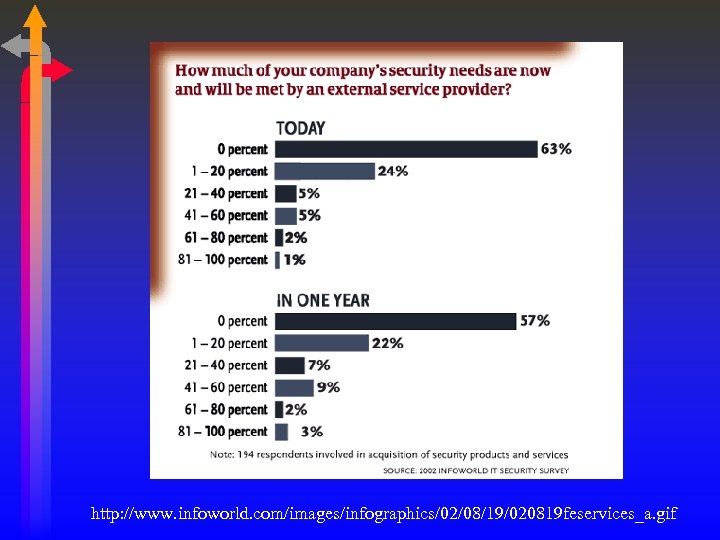 http: //www. infoworld. com/images/infographics/02/08/19/020819 feservices_a. gif
http: //www. infoworld. com/images/infographics/02/08/19/020819 feservices_a. gif
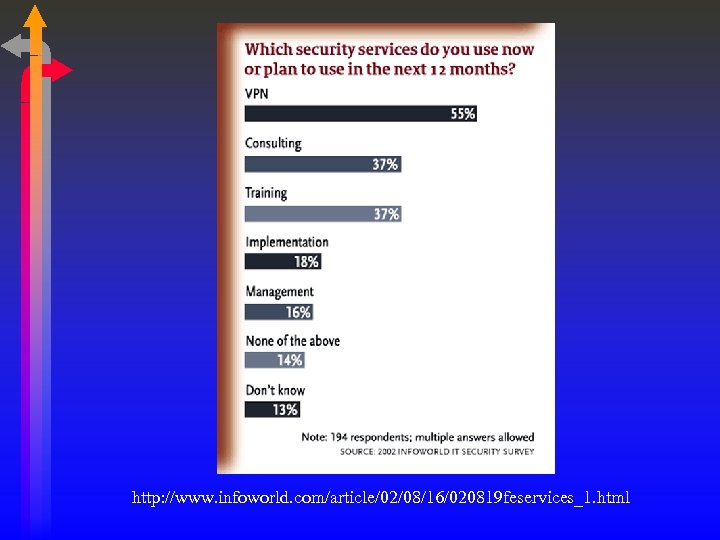 http: //www. infoworld. com/article/02/08/16/020819 feservices_1. html
http: //www. infoworld. com/article/02/08/16/020819 feservices_1. html
 Conclusion • Security outsourcing is still a developing field. • It is still unknown if the benefits outweigh the risks. • A way to ensure a vendor is reputable is to look for clearances. • Security outsourcing will continue to be an importance to the industry.
Conclusion • Security outsourcing is still a developing field. • It is still unknown if the benefits outweigh the risks. • A way to ensure a vendor is reputable is to look for clearances. • Security outsourcing will continue to be an importance to the industry.
 References • • • • http: //www. cert. org/security-improvement/modules/omss/index. html http: //www. infoworld. com/article/02/08/16/020819 feservices_1. html http: //www. csoonline. com/glossary/term. cfm? ID=975 http: //www. cio. com/archive/120101/et_article. html http: //www. networkworld. com/careers/2002/0527 man. html http: //www. informationweek. com/story/IWK 20010713 S 0009 http: //www. microsoft. com/smallbusiness/resources/management/recruiting_staffing/tips_for _outsourcing_your_small_business_needs. mspx http: //techrepublic. com/5100 -10878 -1033997. html# http: //searchsecurity. techtarget. com/s. Definition/0, , sid 14_gci 912633, 00. html) http: //www. csoonline. com/glossary/term. cfm? ID=3331 http: //www. darwinmag. com/read/080101/blunders. html. http: //www. isp-planet. com/technology/mssp_survey. html http: //www. washingtonpost. com/wp-yn/content/article/2006/04/13/AR 2006041300261. html http: //searchcio. techtarget. com/s. Definition/0, , sid 19_gci 955099, 00. html http: //www. cisco. com/warp/public/cc/so/neso/sqso/mnsqss/prodlit/sosfm_ov. pdf http: //www. securitypipeline. com/show. Article. jhtml? article. Id=15306149&pgno=4.
References • • • • http: //www. cert. org/security-improvement/modules/omss/index. html http: //www. infoworld. com/article/02/08/16/020819 feservices_1. html http: //www. csoonline. com/glossary/term. cfm? ID=975 http: //www. cio. com/archive/120101/et_article. html http: //www. networkworld. com/careers/2002/0527 man. html http: //www. informationweek. com/story/IWK 20010713 S 0009 http: //www. microsoft. com/smallbusiness/resources/management/recruiting_staffing/tips_for _outsourcing_your_small_business_needs. mspx http: //techrepublic. com/5100 -10878 -1033997. html# http: //searchsecurity. techtarget. com/s. Definition/0, , sid 14_gci 912633, 00. html) http: //www. csoonline. com/glossary/term. cfm? ID=3331 http: //www. darwinmag. com/read/080101/blunders. html. http: //www. isp-planet. com/technology/mssp_survey. html http: //www. washingtonpost. com/wp-yn/content/article/2006/04/13/AR 2006041300261. html http: //searchcio. techtarget. com/s. Definition/0, , sid 19_gci 955099, 00. html http: //www. cisco. com/warp/public/cc/so/neso/sqso/mnsqss/prodlit/sosfm_ov. pdf http: //www. securitypipeline. com/show. Article. jhtml? article. Id=15306149&pgno=4.


