ef8453d4fb16254fe3a82da0522ee7a3.ppt
- Количество слайдов: 49
 Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls 1
Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls 1
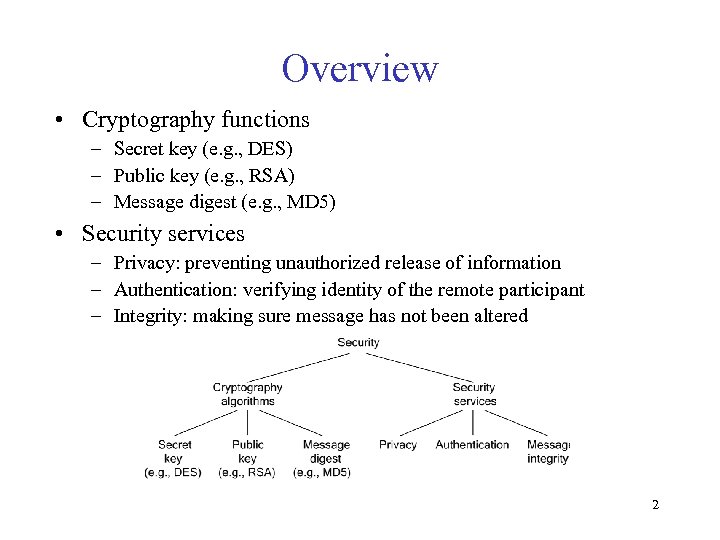 Overview • Cryptography functions – Secret key (e. g. , DES) – Public key (e. g. , RSA) – Message digest (e. g. , MD 5) • Security services – Privacy: preventing unauthorized release of information – Authentication: verifying identity of the remote participant – Integrity: making sure message has not been altered 2
Overview • Cryptography functions – Secret key (e. g. , DES) – Public key (e. g. , RSA) – Message digest (e. g. , MD 5) • Security services – Privacy: preventing unauthorized release of information – Authentication: verifying identity of the remote participant – Integrity: making sure message has not been altered 2
 Secret Key • DES (data encryption standard) • AES (advanced encryption standard) • Both standardized by NIST (US national inst. of standards & technology), both considered secure, with AES permitting fast implementation and less memory and suitable for small mobile devices. 3
Secret Key • DES (data encryption standard) • AES (advanced encryption standard) • Both standardized by NIST (US national inst. of standards & technology), both considered secure, with AES permitting fast implementation and less memory and suitable for small mobile devices. 3
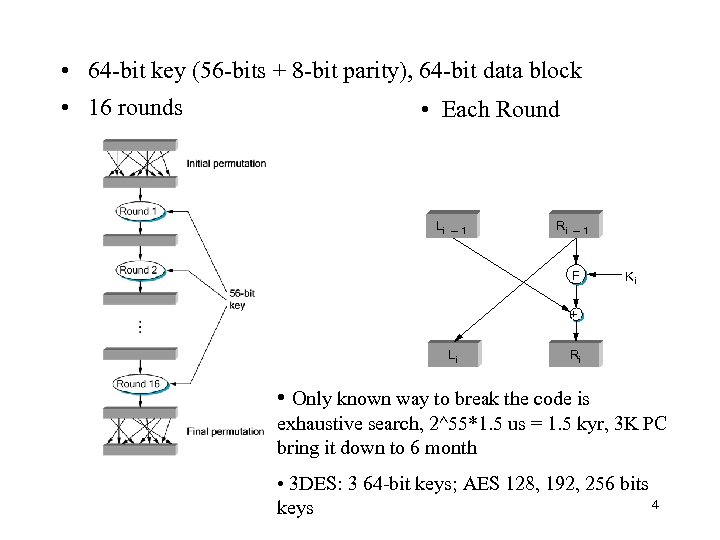 • 64 -bit key (56 -bits + 8 -bit parity), 64 -bit data block • 16 rounds • Each Round Li ─1 Ri ─1 F Ki + Li Ri • Only known way to break the code is exhaustive search, 2^55*1. 5 us = 1. 5 kyr, 3 K PC bring it down to 6 month • 3 DES: 3 64 -bit keys; AES 128, 192, 256 bits 4 keys
• 64 -bit key (56 -bits + 8 -bit parity), 64 -bit data block • 16 rounds • Each Round Li ─1 Ri ─1 F Ki + Li Ri • Only known way to break the code is exhaustive search, 2^55*1. 5 us = 1. 5 kyr, 3 K PC bring it down to 6 month • 3 DES: 3 64 -bit keys; AES 128, 192, 256 bits 4 keys
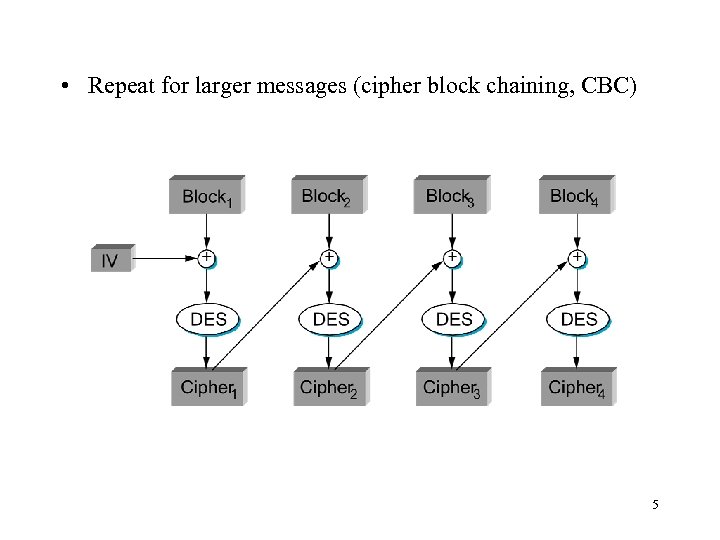 • Repeat for larger messages (cipher block chaining, CBC) 5
• Repeat for larger messages (cipher block chaining, CBC) 5
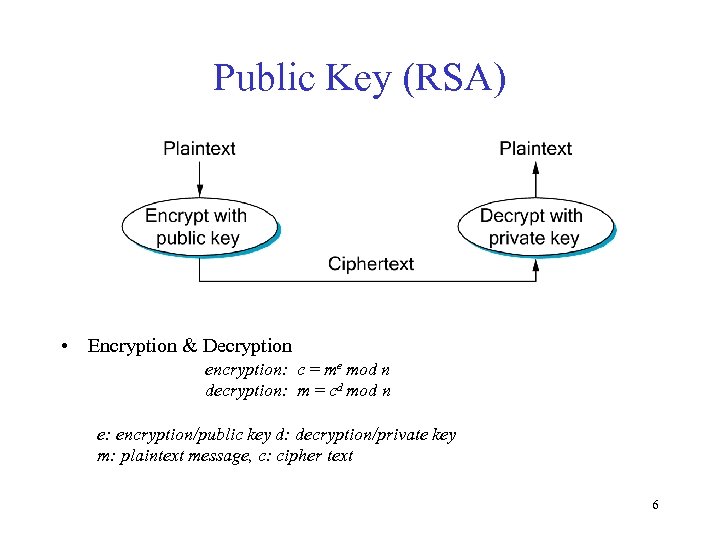 Public Key (RSA) • Encryption & Decryption encryption: c = me mod n decryption: m = cd mod n e: encryption/public key d: decryption/private key m: plaintext message, c: cipher text 6
Public Key (RSA) • Encryption & Decryption encryption: c = me mod n decryption: m = cd mod n e: encryption/public key d: decryption/private key m: plaintext message, c: cipher text 6
 RSA (cont) • Choose two large prime numbers p and q (each 256 bits) – Multiply p and q together to get n • Choose the encryption key e, such that e and (p - 1) x (q - 1) are relatively prime. – Two numbers are relatively prime if they have no common factor greater than one • Compute decryption key d such that d x e= 1 mod ((p - 1) x (q - 1)) • Construct public key as (e, n) • Construct private key as (d, n) • Discard (do not disclose) original primes p and q 7
RSA (cont) • Choose two large prime numbers p and q (each 256 bits) – Multiply p and q together to get n • Choose the encryption key e, such that e and (p - 1) x (q - 1) are relatively prime. – Two numbers are relatively prime if they have no common factor greater than one • Compute decryption key d such that d x e= 1 mod ((p - 1) x (q - 1)) • Construct public key as (e, n) • Construct private key as (d, n) • Discard (do not disclose) original primes p and q 7
 RSA: Example • Let p = 7 and q = 11 – n = 7 x 11 = 77 • Choose e = 7 – relatively prime to (7 - 1) x (11 - 1) = 60 • Select d = 43, which satisfies – d x e= 1 mod ((p - 1) x (q - 1)) • Let m = 9, then – c = 9^7 mod 77 = 37 – m = 37^43 mod 77 = 9 • RSA is based on the premise that factoring large numbers is hard – if n (public) can be factored to p and q, d is easy to compute – 512 -bit number factorable in the next few years, now 1024 -bit or higher considered secure. 8
RSA: Example • Let p = 7 and q = 11 – n = 7 x 11 = 77 • Choose e = 7 – relatively prime to (7 - 1) x (11 - 1) = 60 • Select d = 43, which satisfies – d x e= 1 mod ((p - 1) x (q - 1)) • Let m = 9, then – c = 9^7 mod 77 = 37 – m = 37^43 mod 77 = 9 • RSA is based on the premise that factoring large numbers is hard – if n (public) can be factored to p and q, d is easy to compute – 512 -bit number factorable in the next few years, now 1024 -bit or higher considered secure. 8
 Message Digest • Cryptographic checksum – just as a regular checksum protects the receiver from accidental changes to the message, a cryptographic checksum protects the receiver from malicious changes to the message. • One-way function – given a cryptographic checksum for a message, it is virtually impossible to figure out what message produced that checksum; it is not computationally feasible to find two messages that hash to the same cryptographic checksum. • Relevance – if you are given a checksum for a message and you are able to compute exactly the same checksum for that message, then it is highly likely this message produced the checksum you were given. 9
Message Digest • Cryptographic checksum – just as a regular checksum protects the receiver from accidental changes to the message, a cryptographic checksum protects the receiver from malicious changes to the message. • One-way function – given a cryptographic checksum for a message, it is virtually impossible to figure out what message produced that checksum; it is not computationally feasible to find two messages that hash to the same cryptographic checksum. • Relevance – if you are given a checksum for a message and you are able to compute exactly the same checksum for that message, then it is highly likely this message produced the checksum you were given. 9
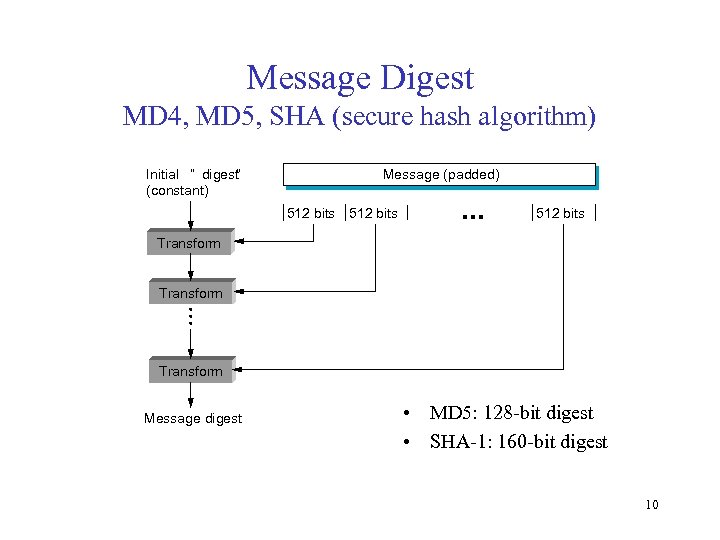 Message Digest MD 4, MD 5, SHA (secure hash algorithm) Initial “ digest“ (constant) Message (padded) 512 bits ■■■ 512 bits Transform Message digest • MD 5: 128 -bit digest • SHA-1: 160 -bit digest 10
Message Digest MD 4, MD 5, SHA (secure hash algorithm) Initial “ digest“ (constant) Message (padded) 512 bits ■■■ 512 bits Transform Message digest • MD 5: 128 -bit digest • SHA-1: 160 -bit digest 10
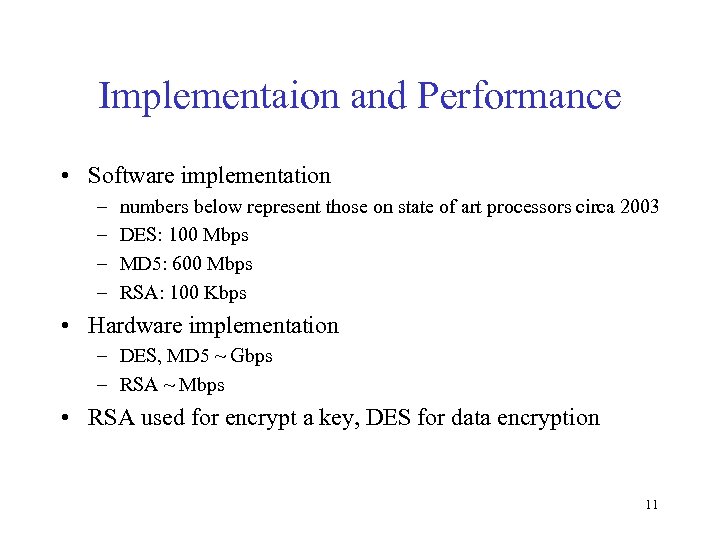 Implementaion and Performance • Software implementation – – numbers below represent those on state of art processors circa 2003 DES: 100 Mbps MD 5: 600 Mbps RSA: 100 Kbps • Hardware implementation – DES, MD 5 ~ Gbps – RSA ~ Mbps • RSA used for encrypt a key, DES for data encryption 11
Implementaion and Performance • Software implementation – – numbers below represent those on state of art processors circa 2003 DES: 100 Mbps MD 5: 600 Mbps RSA: 100 Kbps • Hardware implementation – DES, MD 5 ~ Gbps – RSA ~ Mbps • RSA used for encrypt a key, DES for data encryption 11
 Security Services • A security system is composed of a collection of security services, which use cryptographic algorithms. • Key Distribution • Message Integrity Protocols – Ascertain the message has not be altered by a third party • Authentication Protocols – Ascertain you (the corresponding partner) are who you claim to be 12
Security Services • A security system is composed of a collection of security services, which use cryptographic algorithms. • Key Distribution • Message Integrity Protocols – Ascertain the message has not be altered by a third party • Authentication Protocols – Ascertain you (the corresponding partner) are who you claim to be 12
 Key Distribution • Issues: – In secret key cipher, how does the two communicating parties obtain the shared key? – In public key cipher, how does one know what public key belongs to a certain participant? • Types of keys – Session key: valid for one session only, using secret key cipher – Pre-distribution key: used to generate session key, typically using public key cipher. 13
Key Distribution • Issues: – In secret key cipher, how does the two communicating parties obtain the shared key? – In public key cipher, how does one know what public key belongs to a certain participant? • Types of keys – Session key: valid for one session only, using secret key cipher – Pre-distribution key: used to generate session key, typically using public key cipher. 13
 Public Key Distribution • Certificate (standardized in X. 509) – special type of digitally signed document: “I certify that the public key in this document belongs to the entity named in this document, signed X. ” – the name of the entity being certified can be: • John Smith (jsmith@nmsu. edu) • www. citibank. com – components: • the public key of the entity • the name of the certified authority • a digital signature 14
Public Key Distribution • Certificate (standardized in X. 509) – special type of digitally signed document: “I certify that the public key in this document belongs to the entity named in this document, signed X. ” – the name of the entity being certified can be: • John Smith (jsmith@nmsu. edu) • www. citibank. com – components: • the public key of the entity • the name of the certified authority • a digital signature 14
 Public Key Distribution (cont) • Certified Authority (CA) – administrative entity that issues certificates – useful only to someone that already holds the CA’s public key. • Chain of Trust – if X certifies that a certain public key belongs to Y, and Y certifies that another public key belongs to Z, then there exists a chain of certificates from X to Z – someone that wants to verify Z’s public key has to know X’s public key and follow the chain • Certificate Revocation List (CRL) – A user of a certificate will first check with CRL – CRL do not keep certificates which have expired 15
Public Key Distribution (cont) • Certified Authority (CA) – administrative entity that issues certificates – useful only to someone that already holds the CA’s public key. • Chain of Trust – if X certifies that a certain public key belongs to Y, and Y certifies that another public key belongs to Z, then there exists a chain of certificates from X to Z – someone that wants to verify Z’s public key has to know X’s public key and follow the chain • Certificate Revocation List (CRL) – A user of a certificate will first check with CRL – CRL do not keep certificates which have expired 15
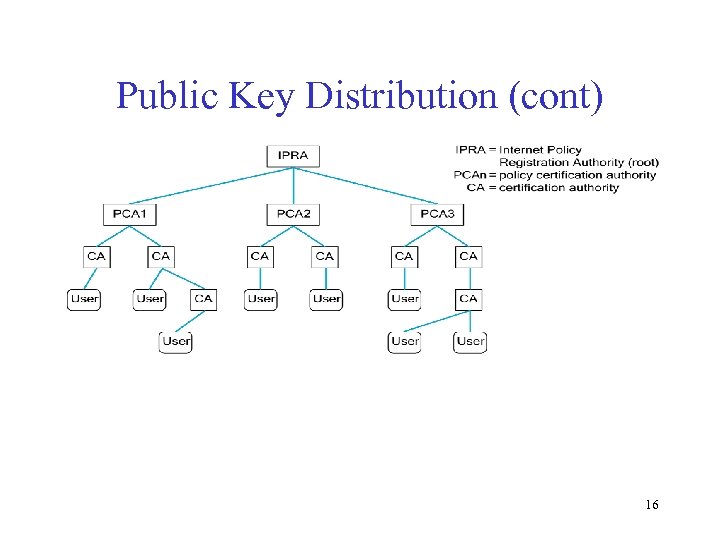 Public Key Distribution (cont) 16
Public Key Distribution (cont) 16
 Secret Key Distribution • Harder than public key distribution – For n parties, need n(n-1) secret keys, one for each pair, rather than n public keys, one for each party. – Keys must be kept secret in contrast to public keys. • A common solution: key distribution center (KDC, used in Kerberos). – KDC shares a secret key with each party, needs only n 1 keys, can be distributed using out-of-band method. – When A talks with B, both contact KDC using their keys, which generates a session key. 17
Secret Key Distribution • Harder than public key distribution – For n parties, need n(n-1) secret keys, one for each pair, rather than n public keys, one for each party. – Keys must be kept secret in contrast to public keys. • A common solution: key distribution center (KDC, used in Kerberos). – KDC shares a secret key with each party, needs only n 1 keys, can be distributed using out-of-band method. – When A talks with B, both contact KDC using their keys, which generates a session key. 17
 Message Integrity Protocols • MD is not enough, anyone can produce a valid MD with an altered message – Needs to ascertain the message is generated by true sender – Has to involve a secret privy to the sender (private key, secret key). – Such message digest is called authenticator. 18
Message Integrity Protocols • MD is not enough, anyone can produce a valid MD with an altered message – Needs to ascertain the message is generated by true sender – Has to involve a secret privy to the sender (private key, secret key). – Such message digest is called authenticator. 18
 Message Integrity Protocols Using public key • Digital signature standard (DSS) – Compute signature (encrypted MD) with private key and verify with public key – Standardized by NIST 19
Message Integrity Protocols Using public key • Digital signature standard (DSS) – Compute signature (encrypted MD) with private key and verify with public key – Standardized by NIST 19
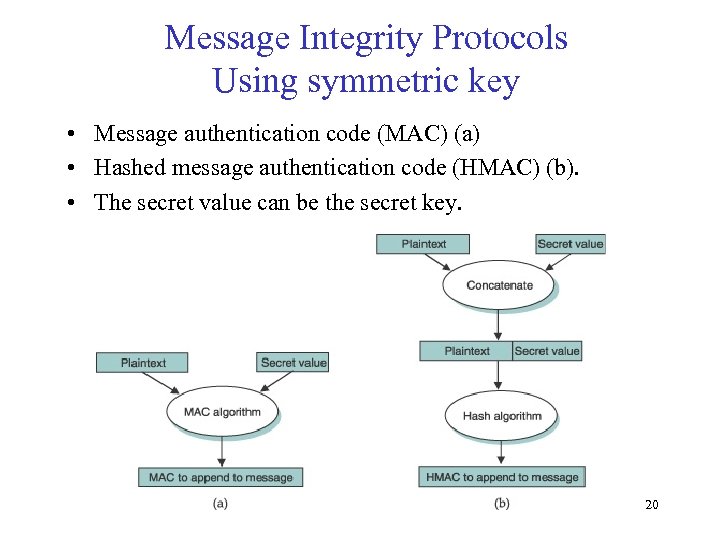 Message Integrity Protocols Using symmetric key • Message authentication code (MAC) (a) • Hashed message authentication code (HMAC) (b). • The secret value can be the secret key. 20
Message Integrity Protocols Using symmetric key • Message authentication code (MAC) (a) • Hashed message authentication code (HMAC) (b). • The secret value can be the secret key. 20
 Authentication Protocols • Objectives are to ascertain: – Originality: you are who you claim to be. – Timeliness: the message is truly sent at this moment • Relay attack: delayed playback of an original message (e. g. replay a bank transaction). – Also establishing a session key in the process 21
Authentication Protocols • Objectives are to ascertain: – Originality: you are who you claim to be. – Timeliness: the message is truly sent at this moment • Relay attack: delayed playback of an original message (e. g. replay a bank transaction). – Also establishing a session key in the process 21
 Methods to provide timeliness • Timestamp (tamper-proof). – Deficiency: clock synchronization accuracy, protecting against clock tampering • Nonce: a random number used only once – Can check if a nonce has been used before – Nonce + timestamp to reduce the amount of previous nonces to be remembered. 22
Methods to provide timeliness • Timestamp (tamper-proof). – Deficiency: clock synchronization accuracy, protecting against clock tampering • Nonce: a random number used only once – Can check if a nonce has been used before – Nonce + timestamp to reduce the amount of previous nonces to be remembered. 22
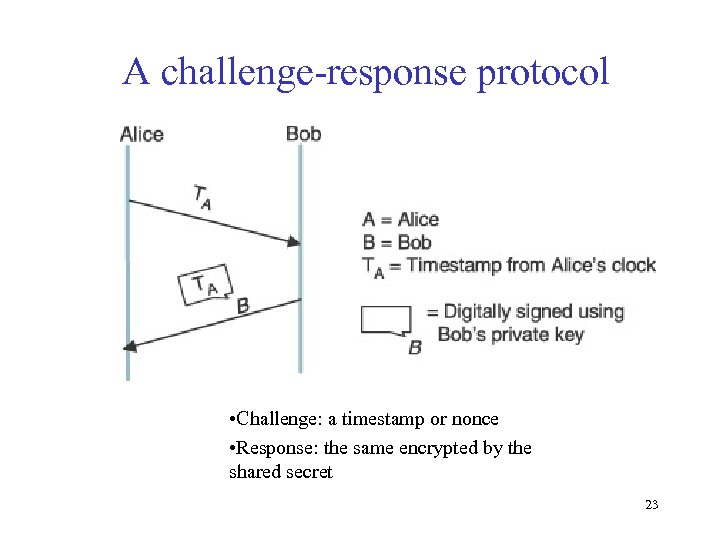 A challenge-response protocol • Challenge: a timestamp or nonce • Response: the same encrypted by the shared secret 23
A challenge-response protocol • Challenge: a timestamp or nonce • Response: the same encrypted by the shared secret 23
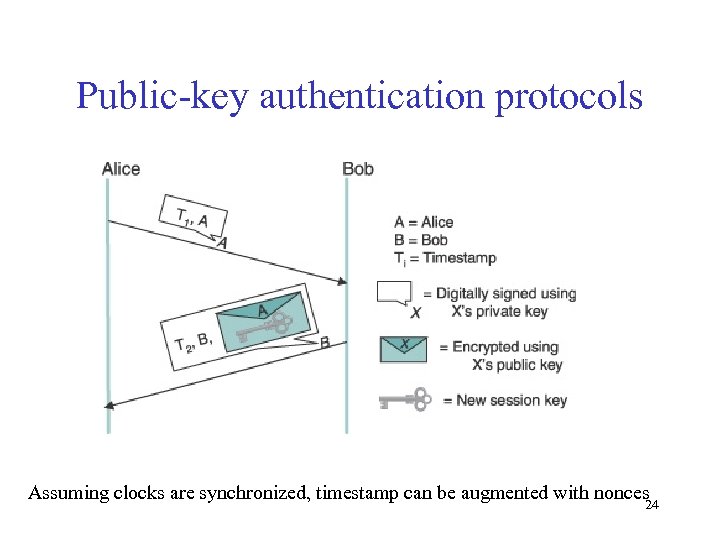 Public-key authentication protocols Assuming clocks are synchronized, timestamp can be augmented with nonces 24
Public-key authentication protocols Assuming clocks are synchronized, timestamp can be augmented with nonces 24
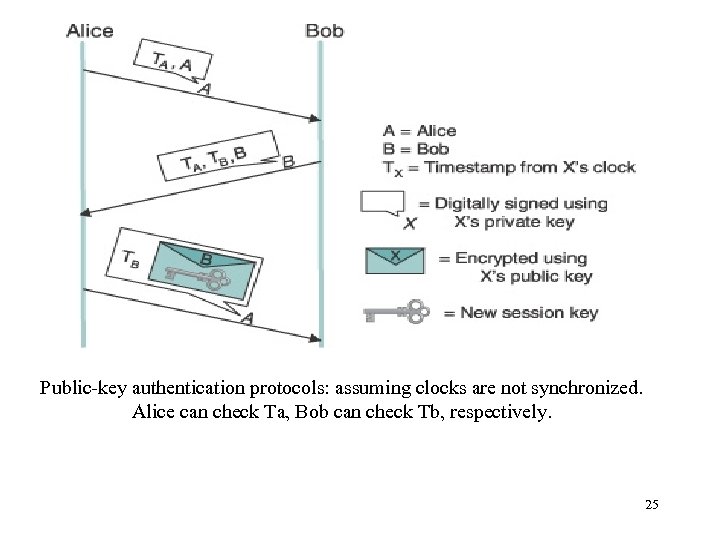 Public-key authentication protocols: assuming clocks are not synchronized. Alice can check Ta, Bob can check Tb, respectively. 25
Public-key authentication protocols: assuming clocks are not synchronized. Alice can check Ta, Bob can check Tb, respectively. 25
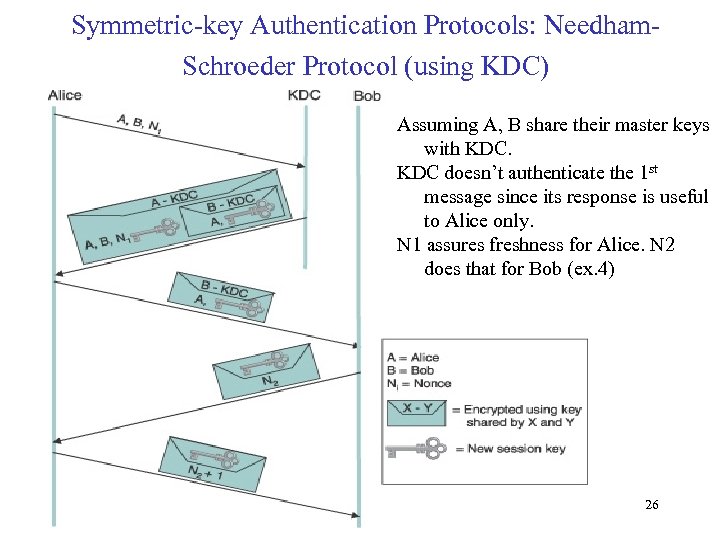 Symmetric-key Authentication Protocols: Needham. Schroeder Protocol (using KDC) Assuming A, B share their master keys with KDC doesn’t authenticate the 1 st message since its response is useful to Alice only. N 1 assures freshness for Alice. N 2 does that for Bob (ex. 4) 26
Symmetric-key Authentication Protocols: Needham. Schroeder Protocol (using KDC) Assuming A, B share their master keys with KDC doesn’t authenticate the 1 st message since its response is useful to Alice only. N 1 assures freshness for Alice. N 2 does that for Bob (ex. 4) 26
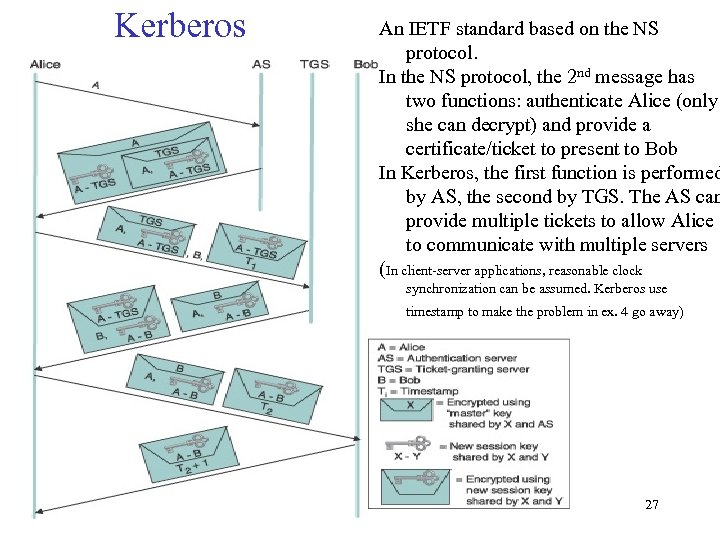 Kerberos An IETF standard based on the NS protocol. In the NS protocol, the 2 nd message has two functions: authenticate Alice (only she can decrypt) and provide a certificate/ticket to present to Bob In Kerberos, the first function is performed by AS, the second by TGS. The AS can provide multiple tickets to allow Alice to communicate with multiple servers (In client-server applications, reasonable clock synchronization can be assumed. Kerberos use timestamp to make the problem in ex. 4 go away) 27
Kerberos An IETF standard based on the NS protocol. In the NS protocol, the 2 nd message has two functions: authenticate Alice (only she can decrypt) and provide a certificate/ticket to present to Bob In Kerberos, the first function is performed by AS, the second by TGS. The AS can provide multiple tickets to allow Alice to communicate with multiple servers (In client-server applications, reasonable clock synchronization can be assumed. Kerberos use timestamp to make the problem in ex. 4 go away) 27
 Diffie-Hellman Key Management • Features: – Establishes a session key without using any predistributed keys. – Messages are open to the public. – But does not provide authentication (thus needs to be augmented to be useful) 28
Diffie-Hellman Key Management • Features: – Establishes a session key without using any predistributed keys. – Messages are open to the public. – But does not provide authentication (thus needs to be augmented to be useful) 28
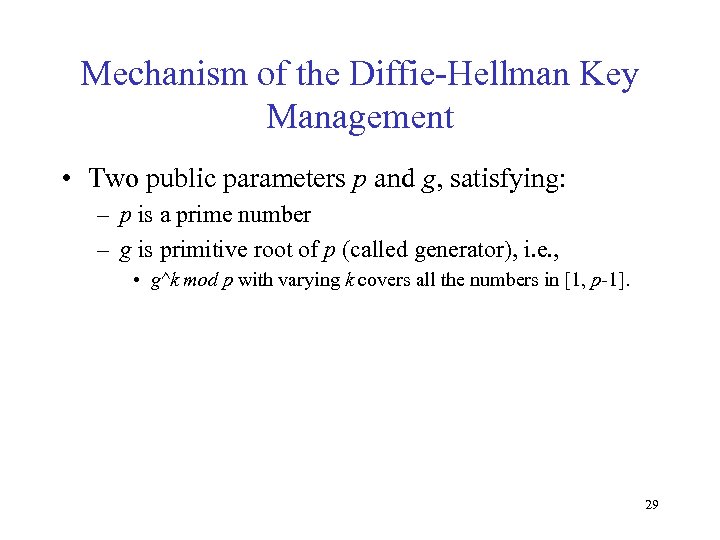 Mechanism of the Diffie-Hellman Key Management • Two public parameters p and g, satisfying: – p is a prime number – g is primitive root of p (called generator), i. e. , • g^k mod p with varying k covers all the numbers in [1, p-1]. 29
Mechanism of the Diffie-Hellman Key Management • Two public parameters p and g, satisfying: – p is a prime number – g is primitive root of p (called generator), i. e. , • g^k mod p with varying k covers all the numbers in [1, p-1]. 29
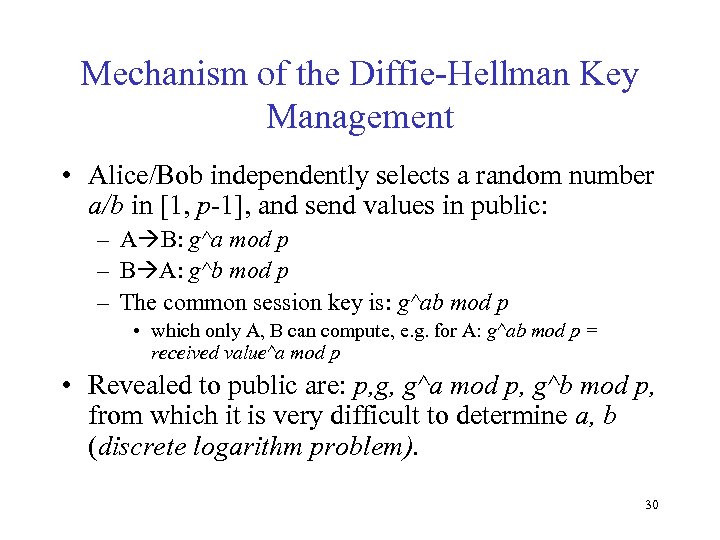 Mechanism of the Diffie-Hellman Key Management • Alice/Bob independently selects a random number a/b in [1, p-1], and send values in public: – A B: g^a mod p – B A: g^b mod p – The common session key is: g^ab mod p • which only A, B can compute, e. g. for A: g^ab mod p = received value^a mod p • Revealed to public are: p, g, g^a mod p, g^b mod p, from which it is very difficult to determine a, b (discrete logarithm problem). 30
Mechanism of the Diffie-Hellman Key Management • Alice/Bob independently selects a random number a/b in [1, p-1], and send values in public: – A B: g^a mod p – B A: g^b mod p – The common session key is: g^ab mod p • which only A, B can compute, e. g. for A: g^ab mod p = received value^a mod p • Revealed to public are: p, g, g^a mod p, g^b mod p, from which it is very difficult to determine a, b (discrete logarithm problem). 30
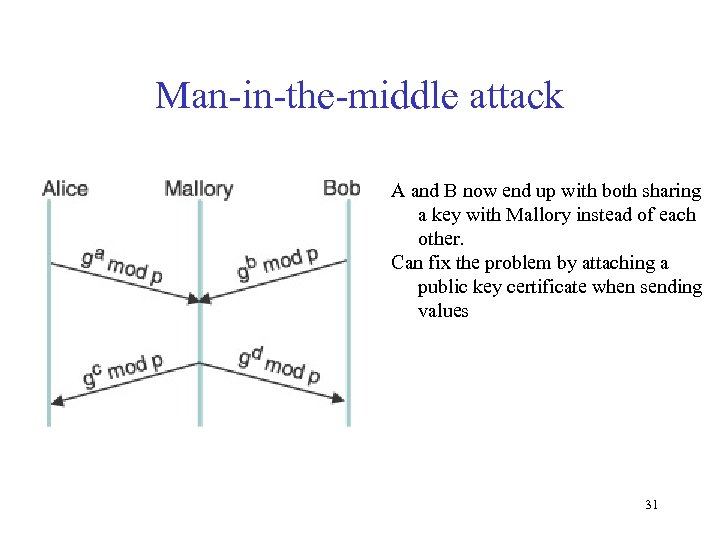 Man-in-the-middle attack A and B now end up with both sharing a key with Mallory instead of each other. Can fix the problem by attaching a public key certificate when sending values 31
Man-in-the-middle attack A and B now end up with both sharing a key with Mallory instead of each other. Can fix the problem by attaching a public key certificate when sending values 31
 Example Security Systems • Can be grouped by the main protocol layer at which they operate – L 3: IP Security (IPSEC) – L 4: Transport Layer Security (TLS), Secure Socket Layer (SSL) – Application: Pretty Good Privacy (PGP, email), Secure Shell (SSH, telnet) 32
Example Security Systems • Can be grouped by the main protocol layer at which they operate – L 3: IP Security (IPSEC) – L 4: Transport Layer Security (TLS), Secure Socket Layer (SSL) – Application: Pretty Good Privacy (PGP, email), Secure Shell (SSH, telnet) 32
 Pretty Good Privacy (PGP) • Provide for encryption and authentication of emails • Authentication – Mesh structured trust relationship – Anyone can assign anyone else’s certificate, the more certificate signatures the more trust • Encryption – Sender selects a random secret key k, sends E[m, k] + E[k, receiver’s public key] • Allow different cryptographic algorithms (specified in the email header) 33
Pretty Good Privacy (PGP) • Provide for encryption and authentication of emails • Authentication – Mesh structured trust relationship – Anyone can assign anyone else’s certificate, the more certificate signatures the more trust • Encryption – Sender selects a random secret key k, sends E[m, k] + E[k, receiver’s public key] • Allow different cryptographic algorithms (specified in the email header) 33
 Secure Shell (SSH) • Problem with telnet – password and messages are sent in the clear • SSH v. 2 – Client connects to the server, the server provides its public key • doubtful value for the key, alternative: out-of-band mechanism – Client authenticates the server using public key algorithm, sets up a session key • a encrypted channel is established – Transmission of password and messages can start now – The secure channel provided by SSH is often used by other applications, e. g. X-windows, IMAP mail readers, etc. 34
Secure Shell (SSH) • Problem with telnet – password and messages are sent in the clear • SSH v. 2 – Client connects to the server, the server provides its public key • doubtful value for the key, alternative: out-of-band mechanism – Client authenticates the server using public key algorithm, sets up a session key • a encrypted channel is established – Transmission of password and messages can start now – The secure channel provided by SSH is often used by other applications, e. g. X-windows, IMAP mail readers, etc. 34
 Transport Layer Security (TLS, SSL, HTTPS) • TLS (SSL: older version) – Motivated by the need to conduct secure transactions over the web – Provided secure transport layer to the application layer • HTTPS = TLS/(SSL, older) + HTTP – assigned #port, 443. 35
Transport Layer Security (TLS, SSL, HTTPS) • TLS (SSL: older version) – Motivated by the need to conduct secure transactions over the web – Provided secure transport layer to the application layer • HTTPS = TLS/(SSL, older) + HTTP – assigned #port, 443. 35
 TLS Components • A handshake protocol that authenticate and establishes a secure channel – Through exchange of certificates, keys • A “record” protocol for data transfer – Handles encryption, message integrity, even compression – Maintains persistent session state through session ID • Avoid a security handshake for downloading each item (e. g. picture) 36
TLS Components • A handshake protocol that authenticate and establishes a secure channel – Through exchange of certificates, keys • A “record” protocol for data transfer – Handles encryption, message integrity, even compression – Maintains persistent session state through session ID • Avoid a security handshake for downloading each item (e. g. picture) 36
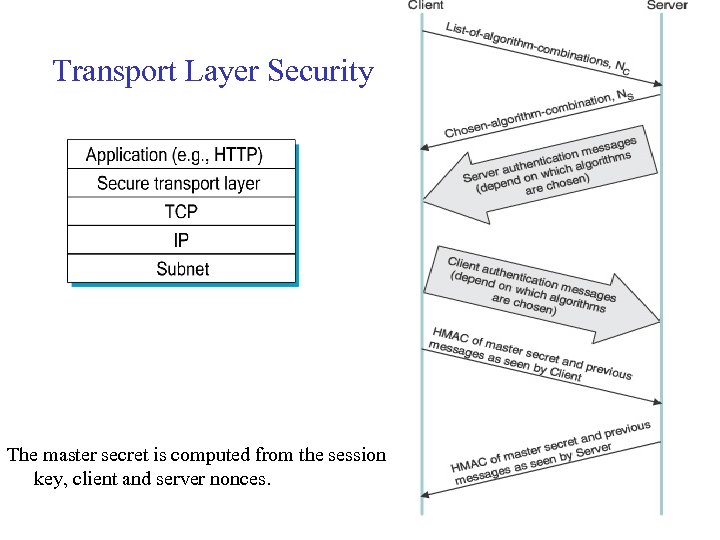 Transport Layer Security The master secret is computed from the session key, client and server nonces. 37
Transport Layer Security The master secret is computed from the session key, client and server nonces. 37
 IP Security (IPSEC) • An ambitious framework to provide all security services at the IP level – Modular, allow users to select security algorithms, services, granularity (per connection btw. hosts, per trunk btw. routers) • Two components – Security protocol • Authentication header (AH) (rarely used) • Encapsulation security payload (ESP) – implement authentication, encryption, etc. – Key management protocol (ISAKMP: internet security and association and key management protocol) 38
IP Security (IPSEC) • An ambitious framework to provide all security services at the IP level – Modular, allow users to select security algorithms, services, granularity (per connection btw. hosts, per trunk btw. routers) • Two components – Security protocol • Authentication header (AH) (rarely used) • Encapsulation security payload (ESP) – implement authentication, encryption, etc. – Key management protocol (ISAKMP: internet security and association and key management protocol) 38
 IP Security (IPSEC) • A secure connection consists of two simplex security associations (SA) – SA is identifiable by the destination IP address and a security parameters index (SPI: id of the SA). – SA is established, modified, and deleted by ISAKMP. – SA defines packet format for exchanging key generation and authentication data. 39
IP Security (IPSEC) • A secure connection consists of two simplex security associations (SA) – SA is identifiable by the destination IP address and a security parameters index (SPI: id of the SA). – SA is established, modified, and deleted by ISAKMP. – SA defines packet format for exchanging key generation and authentication data. 39
 IP Security (IPSEC) • Encapsulating security payload (ESP) provides a secure L 3 channel – ESP head • With IPv 4, it follows IP header, plus a trailer • With IPv 6, it is an IP extension header – Fields • • SPI identifies the SA Seq. Num protects against replay attack Payload. Data is the data sent, can be encrypted. Padlength described how much padding was added (for aligning along block boundaries) • Next. Hdr describes data • Authentication. Data carries authenticator 40
IP Security (IPSEC) • Encapsulating security payload (ESP) provides a secure L 3 channel – ESP head • With IPv 4, it follows IP header, plus a trailer • With IPv 6, it is an IP extension header – Fields • • SPI identifies the SA Seq. Num protects against replay attack Payload. Data is the data sent, can be encrypted. Padlength described how much padding was added (for aligning along block boundaries) • Next. Hdr describes data • Authentication. Data carries authenticator 40
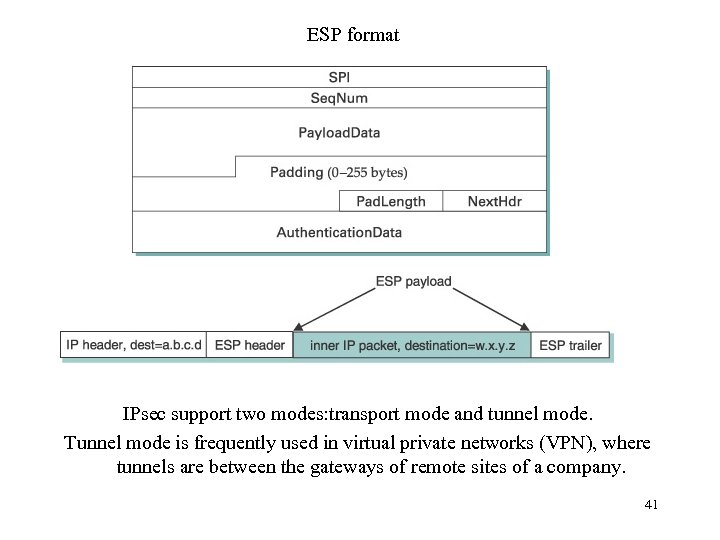 ESP format IPsec support two modes: transport mode and tunnel mode. Tunnel mode is frequently used in virtual private networks (VPN), where tunnels are between the gateways of remote sites of a company. 41
ESP format IPsec support two modes: transport mode and tunnel mode. Tunnel mode is frequently used in virtual private networks (VPN), where tunnels are between the gateways of remote sites of a company. 41
 Wireless Security (802. 11 i) • Wireless links are particularly exposed to security threats because of lack of physical security. • IEEE 802. 11 i/Wi-Fi Protected Access 2 (WPA 2) – Provides authentication, message integrity and confidentiality to 802. 11/Wi. Fi networks – Backward compatible to WEP (wired equivalent privacy, the first-generation Wi. Fi security protocol which has serious flaws). 42
Wireless Security (802. 11 i) • Wireless links are particularly exposed to security threats because of lack of physical security. • IEEE 802. 11 i/Wi-Fi Protected Access 2 (WPA 2) – Provides authentication, message integrity and confidentiality to 802. 11/Wi. Fi networks – Backward compatible to WEP (wired equivalent privacy, the first-generation Wi. Fi security protocol which has serious flaws). 42
 Wireless Security (802. 11 i) • Two authentication modes – Personal/pre-shared key (PSK) mode: • Provides weaker security, more convenient, suitable for home networks. • The secret key between a wireless device and AP is derived from a preconfigured passphrase 43
Wireless Security (802. 11 i) • Two authentication modes – Personal/pre-shared key (PSK) mode: • Provides weaker security, more convenient, suitable for home networks. • The secret key between a wireless device and AP is derived from a preconfigured passphrase 43
 Wireless Security (802. 11 i) – Strong mode • Suitable for enterprise networks. • Involves authentication server (AS) • Uses EAP (extensible authentication protocol) which supports multiple authentication methods (Kerberos, public-key authentication, smart cards, one-time passwords, etc. ) • Mutual authentication between wireless device and AP • Establishes a pair-wise master key, which generates session keys 44
Wireless Security (802. 11 i) – Strong mode • Suitable for enterprise networks. • Involves authentication server (AS) • Uses EAP (extensible authentication protocol) which supports multiple authentication methods (Kerberos, public-key authentication, smart cards, one-time passwords, etc. ) • Mutual authentication between wireless device and AP • Establishes a pair-wise master key, which generates session keys 44
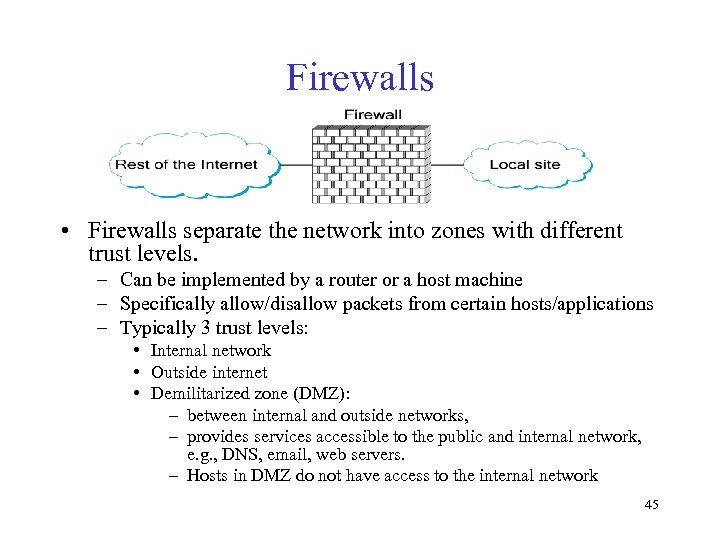 Firewalls • Firewalls separate the network into zones with different trust levels. – Can be implemented by a router or a host machine – Specifically allow/disallow packets from certain hosts/applications – Typically 3 trust levels: • Internal network • Outside internet • Demilitarized zone (DMZ): – between internal and outside networks, – provides services accessible to the public and internal network, e. g. , DNS, email, web servers. – Hosts in DMZ do not have access to the internal network 45
Firewalls • Firewalls separate the network into zones with different trust levels. – Can be implemented by a router or a host machine – Specifically allow/disallow packets from certain hosts/applications – Typically 3 trust levels: • Internal network • Outside internet • Demilitarized zone (DMZ): – between internal and outside networks, – provides services accessible to the public and internal network, e. g. , DNS, email, web servers. – Hosts in DMZ do not have access to the internal network 45
 Firewalls • Using filter to allow/disallow application traffic – Lists of 4 -tuples to allow/disallow • Example (prevent web traffic to 128. 7. 6. 5) ( 192. 13. 14, 1234, 128. 7. 6. 5, 80 ) (*, *, 128. 7. 6. 5, 80 ) – Can Filter based on application header contents • Example: disallow packets containing certain URL in the HTTP header. – Default: allow or disallow? • Disallow is more secure, but involves tradeoff between security and convenience. – Dynamic port selection • In some application, the port number is determined at run time. Need stateful firewall to remember session state. 46
Firewalls • Using filter to allow/disallow application traffic – Lists of 4 -tuples to allow/disallow • Example (prevent web traffic to 128. 7. 6. 5) ( 192. 13. 14, 1234, 128. 7. 6. 5, 80 ) (*, *, 128. 7. 6. 5, 80 ) – Can Filter based on application header contents • Example: disallow packets containing certain URL in the HTTP header. – Default: allow or disallow? • Disallow is more secure, but involves tradeoff between security and convenience. – Dynamic port selection • In some application, the port number is determined at run time. Need stateful firewall to remember session state. 46
 Firewalls • What firewalls do not protect – Internal adversaries (disgruntled employee, visitors, etc) – Services allowed by firewalls can later turn out to be unsafe. – Limited capability to filter out Malware (virusse, worms, spyware) 47
Firewalls • What firewalls do not protect – Internal adversaries (disgruntled employee, visitors, etc) – Services allowed by firewalls can later turn out to be unsafe. – Limited capability to filter out Malware (virusse, worms, spyware) 47
 Denial of Service • Attacks that exhaust system resources – bandwidth, processing power, memory space, etc. • Attacks on end hosts – SYN attack • more effective than data packets due to more processing/states incurred • Attacks on routers – Christmas tree packets • Send packets with all IP options turned on, exhausting processing capability – Pollute route cache • Send serial sequence of IP packets, blowing away 1 st level route cache and making router spend all its time build new forwarding table 48
Denial of Service • Attacks that exhaust system resources – bandwidth, processing power, memory space, etc. • Attacks on end hosts – SYN attack • more effective than data packets due to more processing/states incurred • Attacks on routers – Christmas tree packets • Send packets with all IP options turned on, exhausting processing capability – Pollute route cache • Send serial sequence of IP packets, blowing away 1 st level route cache and making router spend all its time build new forwarding table 48
 Denial of Service • Counter attack – Detect resource usage anomaly • Account for resource usage • Discover if some users/connections are consuming disproportionate amount of resource – Restrict resource usage by misbehaving users/connecitons • Distributed Do. S attacks – Makes distinguishing legitimate heavy load and DDOS hard 49
Denial of Service • Counter attack – Detect resource usage anomaly • Account for resource usage • Discover if some users/connections are consuming disproportionate amount of resource – Restrict resource usage by misbehaving users/connecitons • Distributed Do. S attacks – Makes distinguishing legitimate heavy load and DDOS hard 49


