e02a046cd83be0980db667afebe52391.ppt
- Количество слайдов: 17
 Security Operating System Concepts Essentials – 8 th Edition 13. 1 Silberschatz, Galvin and Gagne © 2011
Security Operating System Concepts Essentials – 8 th Edition 13. 1 Silberschatz, Galvin and Gagne © 2011
 Program Threats (Cont. ) n Logic Bomb l Program that initiates a security incident under certain circumstances n Stack and Buffer Overflow l Exploits a bug in a program (overflow either the stack or memory buffers) l Failure to check bounds on inputs, arguments l Write past arguments on the stack into the return address on stack l When routine returns from call, returns to hacked address 4 l Pointed to code loaded onto stack that executes malicious code Unauthorized user or privilege escalation Operating System Concepts Essentials – 8 th Edition 13. 2 Silberschatz, Galvin and Gagne © 2011
Program Threats (Cont. ) n Logic Bomb l Program that initiates a security incident under certain circumstances n Stack and Buffer Overflow l Exploits a bug in a program (overflow either the stack or memory buffers) l Failure to check bounds on inputs, arguments l Write past arguments on the stack into the return address on stack l When routine returns from call, returns to hacked address 4 l Pointed to code loaded onto stack that executes malicious code Unauthorized user or privilege escalation Operating System Concepts Essentials – 8 th Edition 13. 2 Silberschatz, Galvin and Gagne © 2011
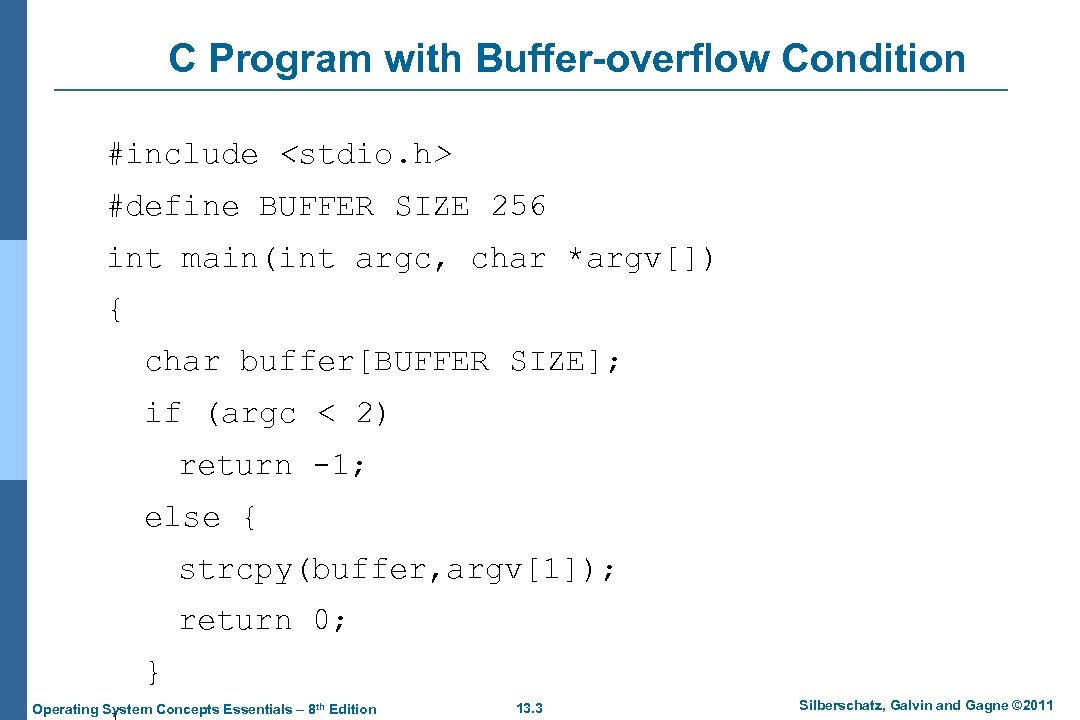 C Program with Buffer-overflow Condition #include
C Program with Buffer-overflow Condition #include
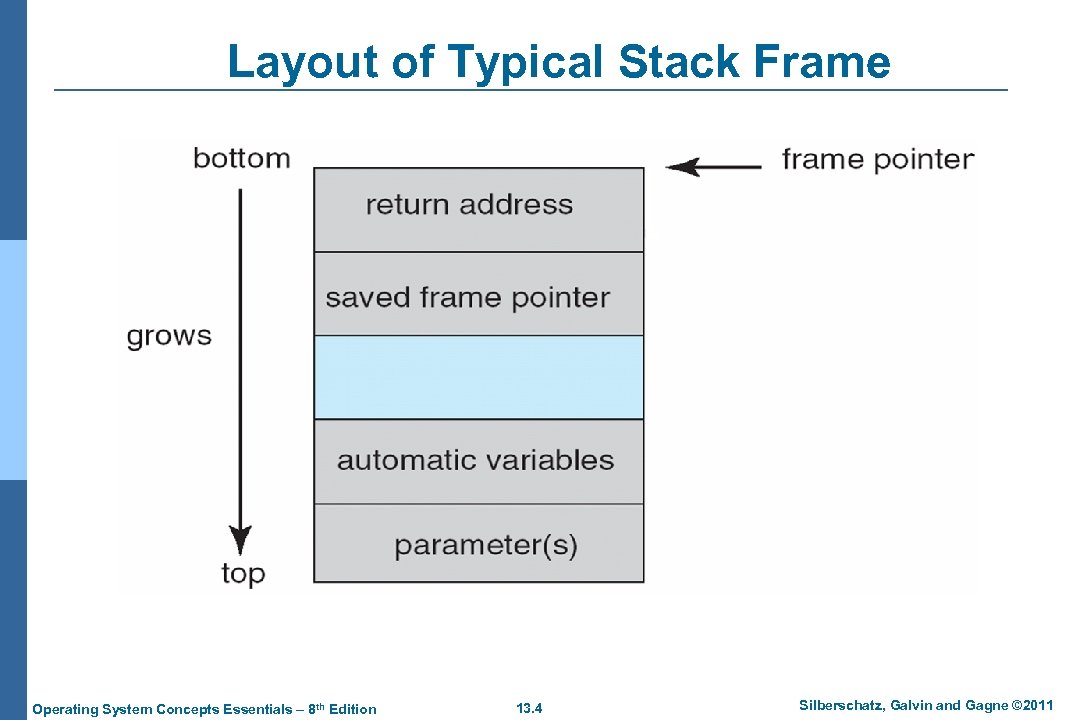 Layout of Typical Stack Frame Operating System Concepts Essentials – 8 th Edition 13. 4 Silberschatz, Galvin and Gagne © 2011
Layout of Typical Stack Frame Operating System Concepts Essentials – 8 th Edition 13. 4 Silberschatz, Galvin and Gagne © 2011
![Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp(‘‘binsh’’, ‘‘bin Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp(‘‘binsh’’, ‘‘bin](https://present5.com/presentation/e02a046cd83be0980db667afebe52391/image-5.jpg) Modified Shell Code #include
Modified Shell Code #include
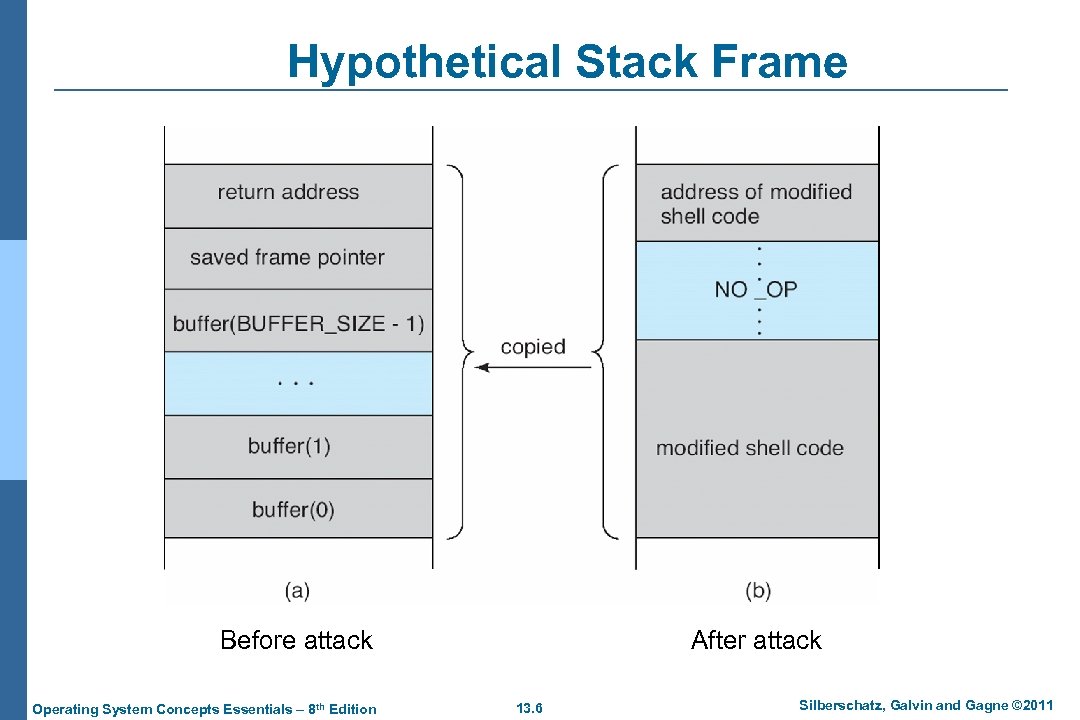 Hypothetical Stack Frame After attack Before attack Operating System Concepts Essentials – 8 th Edition 13. 6 Silberschatz, Galvin and Gagne © 2011
Hypothetical Stack Frame After attack Before attack Operating System Concepts Essentials – 8 th Edition 13. 6 Silberschatz, Galvin and Gagne © 2011
 Great Programming Required? n For the first step of determining the bug, and second step of writing exploit code, yes n Script kiddies can run pre-written exploit code to attack a given system n Attack code can get a shell with the processes’ owner’s permissions l Or open a network port, delete files, download a program, etc n Depending on bug, attack can be executed across a network using allowed connections, bypassing firewalls n Buffer overflow can be disabled by disabling stack execution or adding bit to page table to indicate “non-executable” state l Available in SPARC and x 86 l But still have security exploits 13. 7 Operating System Concepts Essentials – 8 th Edition Silberschatz, Galvin and Gagne © 2011
Great Programming Required? n For the first step of determining the bug, and second step of writing exploit code, yes n Script kiddies can run pre-written exploit code to attack a given system n Attack code can get a shell with the processes’ owner’s permissions l Or open a network port, delete files, download a program, etc n Depending on bug, attack can be executed across a network using allowed connections, bypassing firewalls n Buffer overflow can be disabled by disabling stack execution or adding bit to page table to indicate “non-executable” state l Available in SPARC and x 86 l But still have security exploits 13. 7 Operating System Concepts Essentials – 8 th Edition Silberschatz, Galvin and Gagne © 2011
 Program Threats (Cont. ) n Viruses l Code fragment embedded in legitimate program l Self-replicating, designed to infect other computers l Very specific to CPU architecture, operating system, applications l Usually borne via email or as a macro 4 Visual Basic Macro to reformat hard drive Sub Auto. Open() Dim o. FS Set o. FS = Create. Object(’’Scripting. File. System. Object’’) vs = Shell(’’c: command. com /k format c: ’’, vb. Hide) End Sub Operating System Concepts Essentials – 8 th Edition 13. 8 Silberschatz, Galvin and Gagne © 2011
Program Threats (Cont. ) n Viruses l Code fragment embedded in legitimate program l Self-replicating, designed to infect other computers l Very specific to CPU architecture, operating system, applications l Usually borne via email or as a macro 4 Visual Basic Macro to reformat hard drive Sub Auto. Open() Dim o. FS Set o. FS = Create. Object(’’Scripting. File. System. Object’’) vs = Shell(’’c: command. com /k format c: ’’, vb. Hide) End Sub Operating System Concepts Essentials – 8 th Edition 13. 8 Silberschatz, Galvin and Gagne © 2011
 Program Threats (Cont. ) n Virus dropper inserts virus onto the system n Many categories of viruses, literally many thousands of viruses l File / parasitic l Boot / memory l Macro l Source code l Polymorphic to avoid having a virus signature l Encrypted l Stealth l Tunneling l Multipartite l Armored Operating System Concepts Essentials – 8 th Edition 13. 9 Silberschatz, Galvin and Gagne © 2011
Program Threats (Cont. ) n Virus dropper inserts virus onto the system n Many categories of viruses, literally many thousands of viruses l File / parasitic l Boot / memory l Macro l Source code l Polymorphic to avoid having a virus signature l Encrypted l Stealth l Tunneling l Multipartite l Armored Operating System Concepts Essentials – 8 th Edition 13. 9 Silberschatz, Galvin and Gagne © 2011
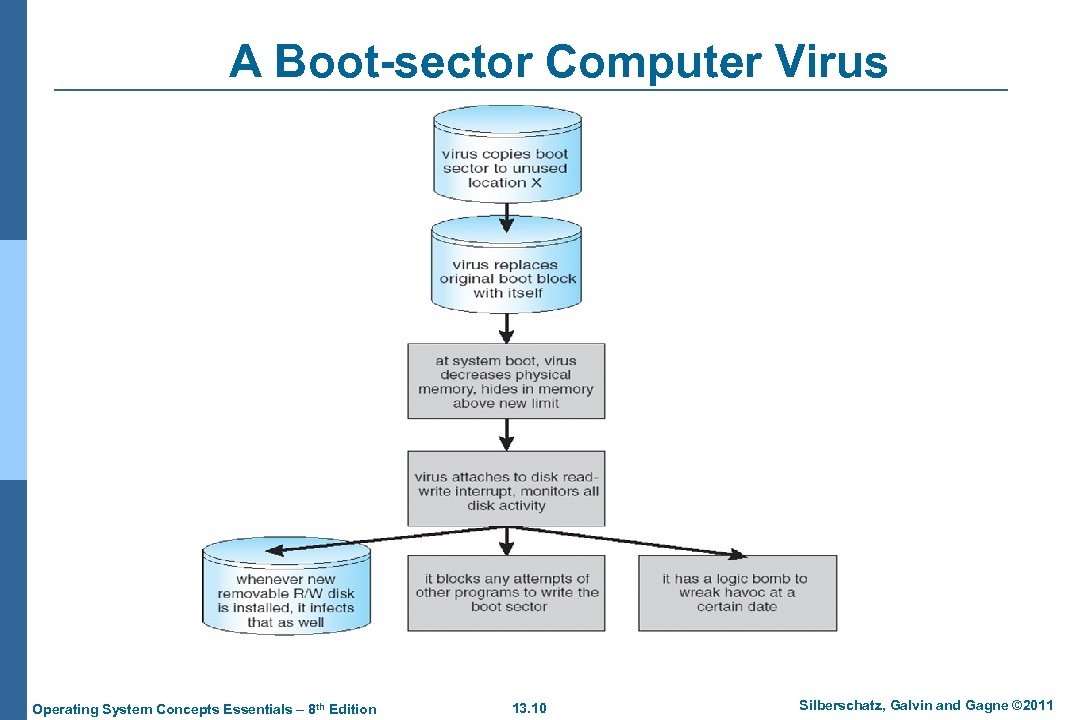 A Boot-sector Computer Virus Operating System Concepts Essentials – 8 th Edition 13. 10 Silberschatz, Galvin and Gagne © 2011
A Boot-sector Computer Virus Operating System Concepts Essentials – 8 th Edition 13. 10 Silberschatz, Galvin and Gagne © 2011
 The Threat Continues n Attacks still common, still occurring n Attacks moved over time from science experiments to tools of organized crime l Targeting specific companies l Creating botnets to use as tool for spam and DDOS delivery l Keystroke logger to grab passwords, credit card numbers n Why is Windows the target for most attacks? l Most common l Everyone is an administrator 4 l Licensing required? Monoculture considered harmful Operating System Concepts Essentials – 8 th Edition 13. 11 Silberschatz, Galvin and Gagne © 2011
The Threat Continues n Attacks still common, still occurring n Attacks moved over time from science experiments to tools of organized crime l Targeting specific companies l Creating botnets to use as tool for spam and DDOS delivery l Keystroke logger to grab passwords, credit card numbers n Why is Windows the target for most attacks? l Most common l Everyone is an administrator 4 l Licensing required? Monoculture considered harmful Operating System Concepts Essentials – 8 th Edition 13. 11 Silberschatz, Galvin and Gagne © 2011
 System and Network Threats n Some systems “open” rather than secure by default l Reduce attack surface l But harder to use, more knowledge needed to administer n Network threats harder to detect, prevent l Protection systems weaker l More difficult to have a shared secret on which to base access l No physical limits once system attached to internet 4 l Or on network with system attached to internet Even determining location of connecting system difficult 4 IP address is only knowledge Operating System Concepts Essentials – 8 th Edition 13. 12 Silberschatz, Galvin and Gagne © 2011
System and Network Threats n Some systems “open” rather than secure by default l Reduce attack surface l But harder to use, more knowledge needed to administer n Network threats harder to detect, prevent l Protection systems weaker l More difficult to have a shared secret on which to base access l No physical limits once system attached to internet 4 l Or on network with system attached to internet Even determining location of connecting system difficult 4 IP address is only knowledge Operating System Concepts Essentials – 8 th Edition 13. 12 Silberschatz, Galvin and Gagne © 2011
 System and Network Threats (Cont. ) n Worms – use spawn mechanism; standalone program n Internet worm l Exploited UNIX networking features (remote access) and bugs in finger and sendmail programs l Exploited trust-relationship mechanism used by rsh to access friendly systems without use of password l Grappling hook program uploaded main worm program 4 99 lines of C code l Hooked system then uploaded main code, tried to attack connected systems l Also tried to break into other users accounts on local system via password guessing l If target system already infected, abort, except for every 7 th time Operating System Concepts Essentials – 8 th Edition 13. 13 Silberschatz, Galvin and Gagne © 2011
System and Network Threats (Cont. ) n Worms – use spawn mechanism; standalone program n Internet worm l Exploited UNIX networking features (remote access) and bugs in finger and sendmail programs l Exploited trust-relationship mechanism used by rsh to access friendly systems without use of password l Grappling hook program uploaded main worm program 4 99 lines of C code l Hooked system then uploaded main code, tried to attack connected systems l Also tried to break into other users accounts on local system via password guessing l If target system already infected, abort, except for every 7 th time Operating System Concepts Essentials – 8 th Edition 13. 13 Silberschatz, Galvin and Gagne © 2011
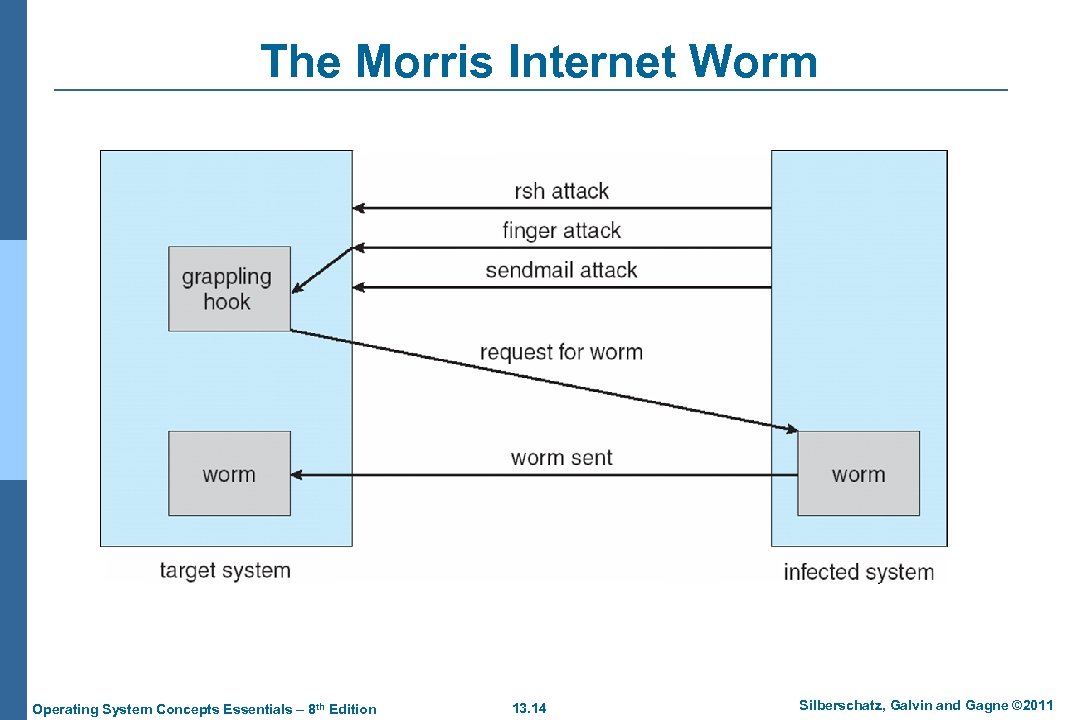 The Morris Internet Worm Operating System Concepts Essentials – 8 th Edition 13. 14 Silberschatz, Galvin and Gagne © 2011
The Morris Internet Worm Operating System Concepts Essentials – 8 th Edition 13. 14 Silberschatz, Galvin and Gagne © 2011
 System and Network Threats (Cont. ) n Port scanning l Automated attempt to connect to a range of ports on one or a range of IP addresses l Detection of answering service protocol l Detection of OS and version running on system l nmap scans all ports in a given IP range for a response l nessus has a database of protocols and bugs (and exploits) to apply against a system l Frequently launched from zombie systems 4 To decrease trace-ability Operating System Concepts Essentials – 8 th Edition 13. 15 Silberschatz, Galvin and Gagne © 2011
System and Network Threats (Cont. ) n Port scanning l Automated attempt to connect to a range of ports on one or a range of IP addresses l Detection of answering service protocol l Detection of OS and version running on system l nmap scans all ports in a given IP range for a response l nessus has a database of protocols and bugs (and exploits) to apply against a system l Frequently launched from zombie systems 4 To decrease trace-ability Operating System Concepts Essentials – 8 th Edition 13. 15 Silberschatz, Galvin and Gagne © 2011
 System and Network Threats (Cont. ) n Denial of Service l Overload the targeted computer preventing it from doing any useful work l Distributed denial-of-service (DDOS) come from multiple sites at once l Consider the start of the IP-connection handshake (SYN) 4 l How many started-connections can the OS handle? Consider traffic to a web site 4 How can you tell the difference between being a target and being really popular? l Accidental – CS students writing bad fork() code l Purposeful – extortion, punishment Operating System Concepts Essentials – 8 th Edition 13. 16 Silberschatz, Galvin and Gagne © 2011
System and Network Threats (Cont. ) n Denial of Service l Overload the targeted computer preventing it from doing any useful work l Distributed denial-of-service (DDOS) come from multiple sites at once l Consider the start of the IP-connection handshake (SYN) 4 l How many started-connections can the OS handle? Consider traffic to a web site 4 How can you tell the difference between being a target and being really popular? l Accidental – CS students writing bad fork() code l Purposeful – extortion, punishment Operating System Concepts Essentials – 8 th Edition 13. 16 Silberschatz, Galvin and Gagne © 2011
 Sobig. F Worm n More modern example n Disguised as a photo uploaded to adult newsgroup via account created with stolen credit card n Targeted Windows systems n Had own SMTP engine to mail itself as attachment to everyone in infect system’s address book n Disguised with innocuous subject lines, looking like it came from someone known Operating System Concepts Essentials – 8 th Edition 13. 17 Silberschatz, Galvin and Gagne © 2011
Sobig. F Worm n More modern example n Disguised as a photo uploaded to adult newsgroup via account created with stolen credit card n Targeted Windows systems n Had own SMTP engine to mail itself as attachment to everyone in infect system’s address book n Disguised with innocuous subject lines, looking like it came from someone known Operating System Concepts Essentials – 8 th Edition 13. 17 Silberschatz, Galvin and Gagne © 2011


