93468dc88831ecc113db9c33d818d83e.ppt
- Количество слайдов: 43
Security of Web Applications Ladislav Hudec Faculty of Electrical Engineering and Information Technology Slovak University of Technology, Bratislava prepared for SOFSEM 2001, November 26, 2001, Piešťany http: //www. dcs. elf. stuba. sk/~lhudec/ Doc. Ing. Ladislav Hudec, CSc. , CISA

Agenda 1. Security services and technologies 2. Web security considerations 3. Network security 4. IPSec - IP Secure protocol 5. SSL - Secure Socket Layer Protocol 6. Firewalls 7. References Doc. Ing. Ladislav Hudec, CSc. , CISA

An organization faces numerous challenges in implementing appropriate security controls to secure its systems and information. The basic challenges are as : • security is not built into IT • security is always an afterbought • lack of management commitment • immaturity of software processes. Doc. Ing. Ladislav Hudec, CSc. , CISA

Security services and technologies New IT systems have incorporated a defined set of controls to ensure their security. Web applications (e. g. e-commerce) are no different in that regard and require the same set of security controls. The primary security controls are: • Confidentiality • Access control (autentication and authorization) • Integrity • Availability • Nonrepudiation. Doc. Ing. Ladislav Hudec, CSc. , CISA

Confidentiality refers to the protection of information from unauthorized disclosure to a person or computing entity. Cryptography enables confidentiality and protects data. Access control (autentication and authorization) autenticates the identity of the entity trying to access a computing resource, and controls the use of computing resource per predetermined levels of entitlement. Authentication by static password, token, one time password, biometrics autentication, public and private key autentication. Integrity controls protect the data/or computing resource from any intentional or unintentional tampering. It is ensured by cryptography, hash function and proper access control. (antivirus software, signing the mobile code). Doc. Ing. Ladislav Hudec, CSc. , CISA

Availability refers to the continuity of IT processing and the availability of information. Adequate configuration of the system and controlled processes and procedures guards against denial of services attack. Nonrepudiation controls ensure that users cannot deny actions they undertook. Other organizations require their users to read and agree to business agreements that hold users aaccountable to their authentication tokens. Transactions entered through those passwords are thus a user‘s sole responsibility. Doc. Ing. Ladislav Hudec, CSc. , CISA

Web security considerations Web presents new challenges (not generally appreciated) in the context of computer and network security: • the Internet is two way • the web is increasingly serving as a highly visible outlet • although web browsers are very easy to use, web servers are relatively easy to configure and manage, the web content is increasingly easy to develop, the underlying software is extraordinarily complex • a web server can be exploited as a launching pad for attack on corporation’s internal network • causual and untrained (in security matters) users are common clients for web based services. Doc. Ing. Ladislav Hudec, CSc. , CISA
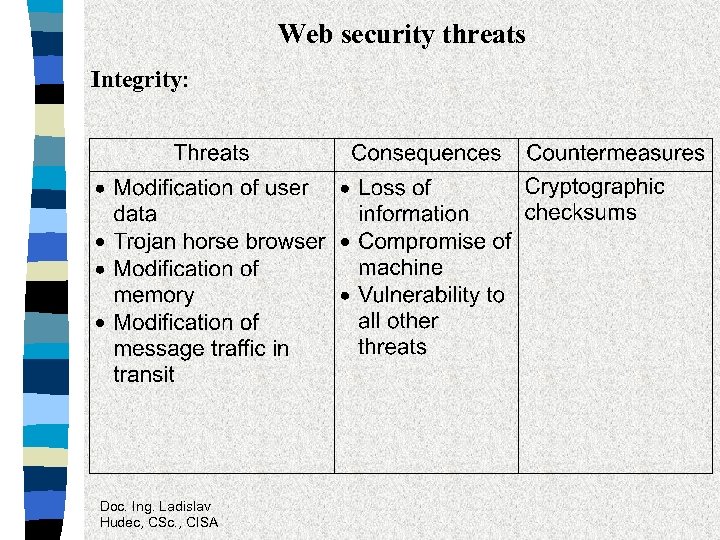
Web security threats Integrity: Doc. Ing. Ladislav Hudec, CSc. , CISA

Web security threats Confidentiality: Doc. Ing. Ladislav Hudec, CSc. , CISA
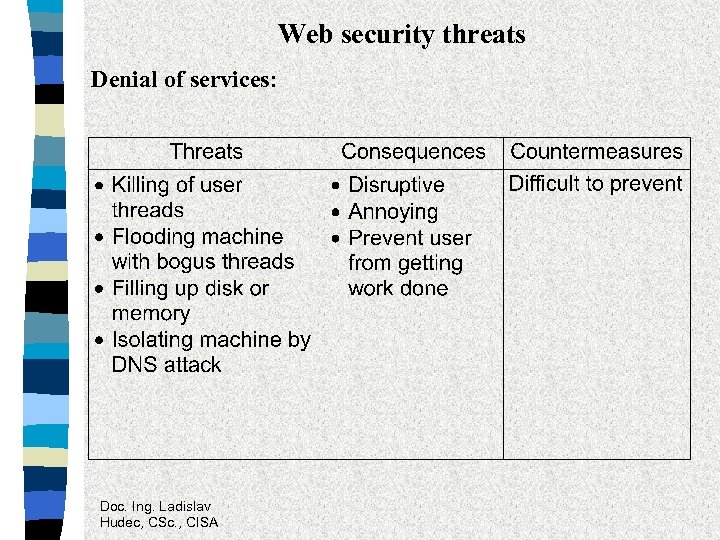
Web security threats Denial of services: Doc. Ing. Ladislav Hudec, CSc. , CISA
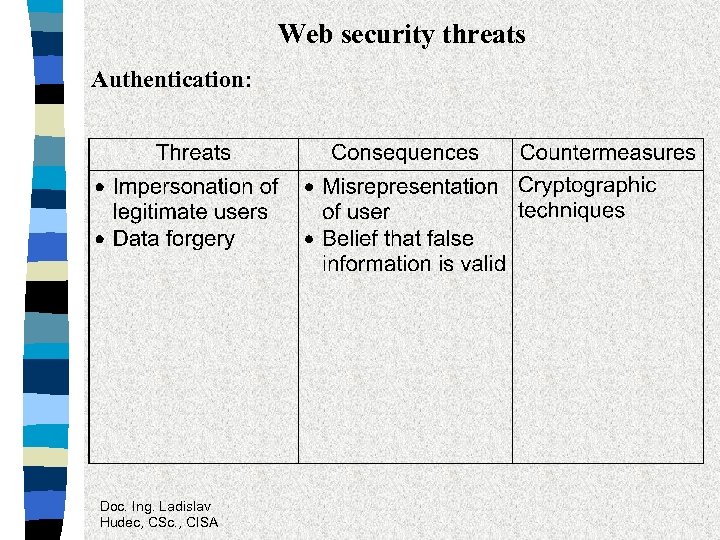
Web security threats Authentication: Doc. Ing. Ladislav Hudec, CSc. , CISA

Network security Another way to classify web security threats is in terms of the location of the threat: • web server • web browser • network traffic between browser and server. Issues of server and browser security fall into the category of computer system security. Issues of network traffic between server and browser fall into the category network security. Doc. Ing. Ladislav Hudec, CSc. , CISA
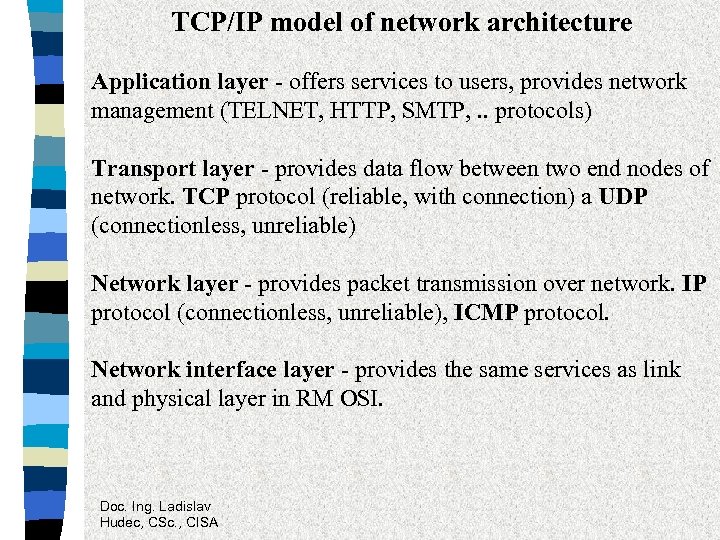
TCP/IP model of network architecture Application layer - offers services to users, provides network management (TELNET, HTTP, SMTP, . . protocols) Transport layer - provides data flow between two end nodes of network. TCP protocol (reliable, with connection) a UDP (connectionless, unreliable) Network layer - provides packet transmission over network. IP protocol (connectionless, unreliable), ICMP protocol. Network interface layer - provides the same services as link and physical layer in RM OSI. Doc. Ing. Ladislav Hudec, CSc. , CISA
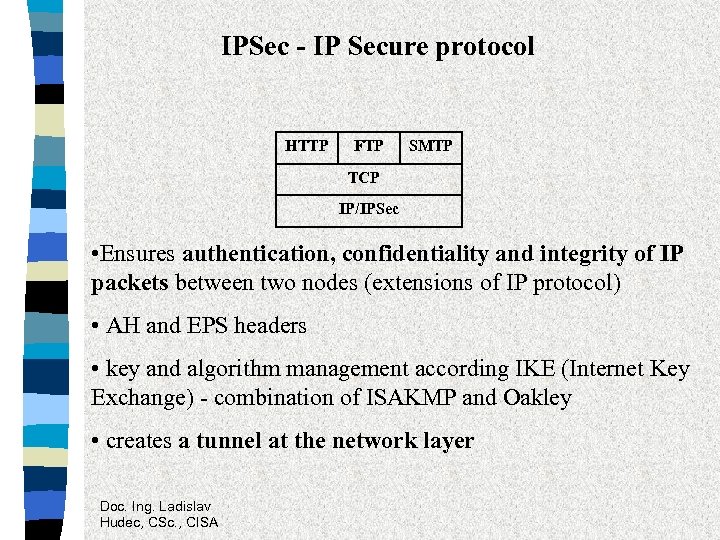
IPSec - IP Secure protocol HTTP FTP SMTP TCP IP/IPSec • Ensures authentication, confidentiality and integrity of IP packets between two nodes (extensions of IP protocol) • AH and EPS headers • key and algorithm management according IKE (Internet Key Exchange) - combination of ISAKMP and Oakley • creates a tunnel at the network layer Doc. Ing. Ladislav Hudec, CSc. , CISA
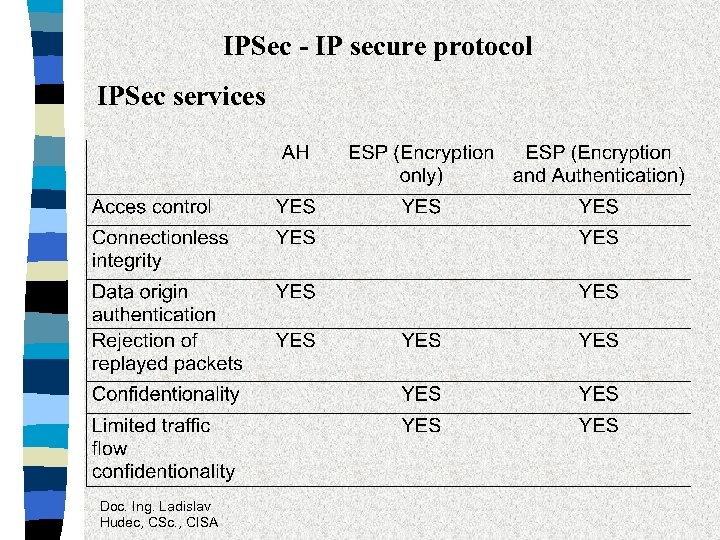
IPSec - IP secure protocol IPSec services Doc. Ing. Ladislav Hudec, CSc. , CISA

SSL - Secure Socket Layer Protocol SSL Handshake SSL Change Cip. Protocol Spec Protocol SSL Alert Protocol HTTP SSL Record Protocol TCP IP SSL connection - is a transport (RM OSI) that provides suitable type of services. Every connection is associated with one session. SSL session - is an association between a client and a server. Sessions are created by the Handshake protocol (defines set of cryptographic security parameters, that can be shared among multiple connections). Doc. Ing. Ladislav Hudec, CSc. , CISA

SSL - Secure Socket Layer Protocol SSL Record Protocol - provides two services for SSL connections • confidentiality - handshake protocol defines shared secret key for encryption of SSL payloads • integrity - handshake protocol defines shared secret key to form message authentication code MAC Operations of SSL Record Protocol • fragment • compress • add MAC • encryption Doc. Ing. Ladislav Hudec, CSc. , CISA

SSL - Secure Socket Layer Protocol Change Cipher Spec Protocol • uses the SSL Record protocol • is the simplest of SSL protocols • only single byte message with value 1 and causes the pending state to be copied into the current state (updates cipher suite to be used in this connection). Doc. Ing. Ladislav Hudec, CSc. , CISA

SSL - Secure Socket Layer Protocol Alert Protocol • used to convey SSL-related alerts to the peer entity • two types of alerts: warning and fatal • in the case of fatal alert SSL immediately terminates the connection (the other connections of the session can continue but no new one is established) Doc. Ing. Ladislav Hudec, CSc. , CISA

SSL - Secure Socket Layer Protocol Handshake Protocol • the most complex part of SSL • allows server and client to authenticate each other • negotiates an encryption and MAC algorithm and cryptographic keys to be used to protect data sent in an SSL • is used before any application data are transmitted • consists of four phases Doc. Ing. Ladislav Hudec, CSc. , CISA
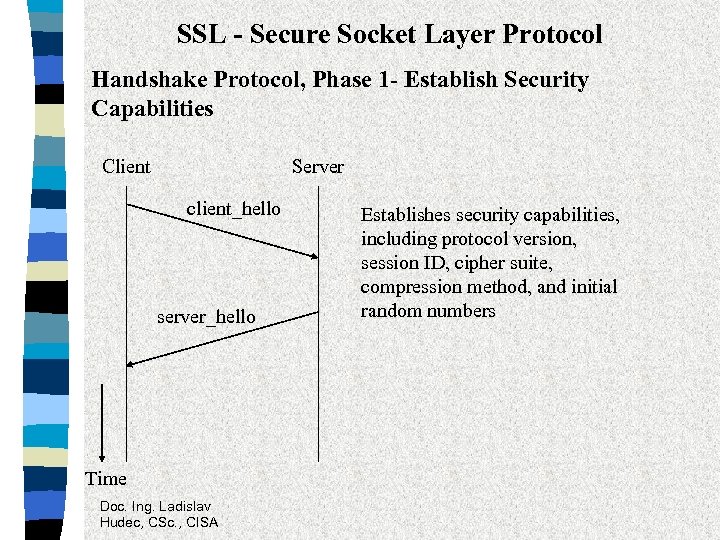
SSL - Secure Socket Layer Protocol Handshake Protocol, Phase 1 - Establish Security Capabilities Client Server client_hello server_hello Time Doc. Ing. Ladislav Hudec, CSc. , CISA Establishes security capabilities, including protocol version, session ID, cipher suite, compression method, and initial random numbers
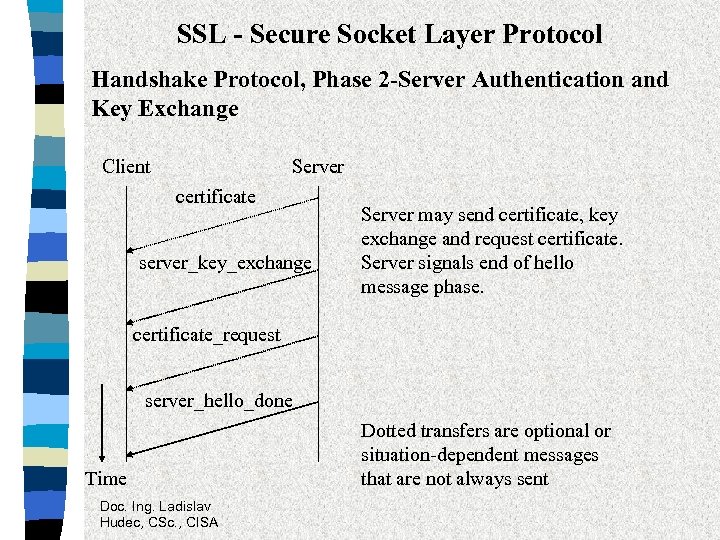
SSL - Secure Socket Layer Protocol Handshake Protocol, Phase 2 -Server Authentication and Key Exchange Client Server certificate server_key_exchange Server may send certificate, key exchange and request certificate. Server signals end of hello message phase. certificate_request server_hello_done Time Doc. Ing. Ladislav Hudec, CSc. , CISA Dotted transfers are optional or situation-dependent messages that are not always sent
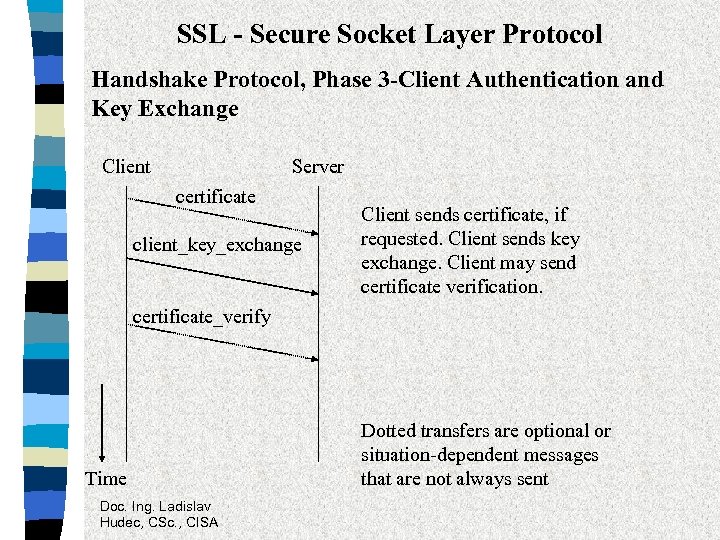
SSL - Secure Socket Layer Protocol Handshake Protocol, Phase 3 -Client Authentication and Key Exchange Client Server certificate client_key_exchange Client sends certificate, if requested. Client sends key exchange. Client may send certificate verification. certificate_verify Time Doc. Ing. Ladislav Hudec, CSc. , CISA Dotted transfers are optional or situation-dependent messages that are not always sent
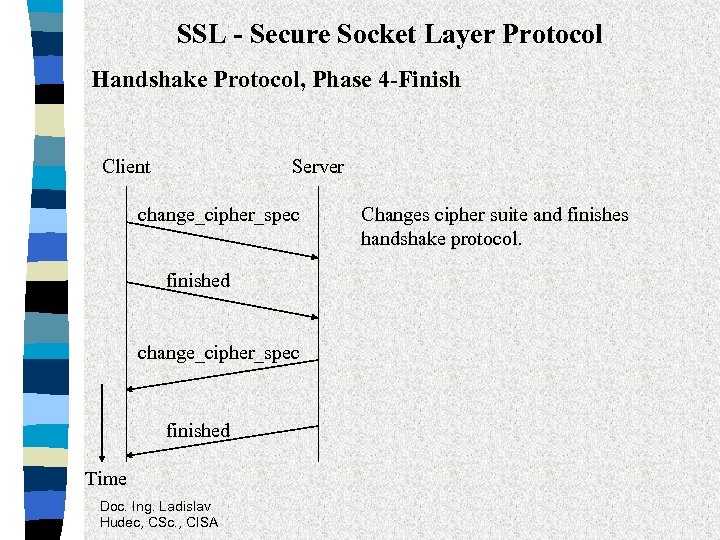
SSL - Secure Socket Layer Protocol Handshake Protocol, Phase 4 -Finish Client Server change_cipher_spec finished Time Doc. Ing. Ladislav Hudec, CSc. , CISA Changes cipher suite and finishes handshake protocol.

SSL - Secure Socket Layer Protocol Supported key exchange methods: • RSA - secret key is encrypted with the receiver’s RSA public key (receiver’s certificate available) • fixed Diffie-Hellman - server’s certificate contains the D-H public parameters • ephemeral Diffie-Hellman - the D-H public keys are exchanged, signed using the sender’s private RSA or DSS key • anonymous Diffie-Hellman - base D-H algorithm is used with no authentication • Fortezza Doc. Ing. Ladislav Hudec, CSc. , CISA
SSL - Secure Socket Layer Protocol Supported cipher algorithms: • RC 4, RC 2, DES, 3 DES, DES 40, IDEA, Fortezza Supported MAC algorithms: • MD 5, SHA-1 Transport Layer Security (TLS) is an IETF standardisation initiative for producing an Internet standard version of SSL. (Current version of TLS is very similar to SSLv 3. ) Doc. Ing. Ladislav Hudec, CSc. , CISA
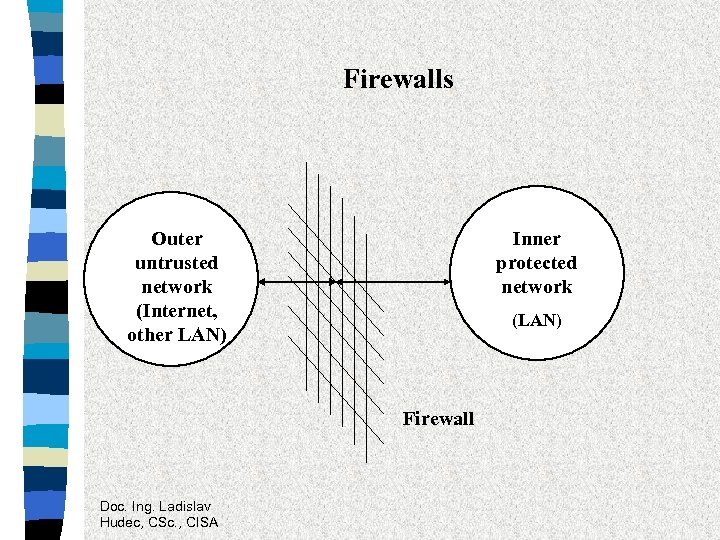
Firewalls Outer untrusted network (Internet, other LAN) Inner protected network (LAN) Firewall Doc. Ing. Ladislav Hudec, CSc. , CISA

Definition of firewall Firewall is a collection of components placed between two networks that collectively have the following properties: • all traffic from inside to outside, and vice versa, must pass through the firewall • only authorised traffic, as defined by the local security policy, will be allowed to pass • the firewall itself is immune to penetration. Doc. Ing. Ladislav Hudec, CSc. , CISA
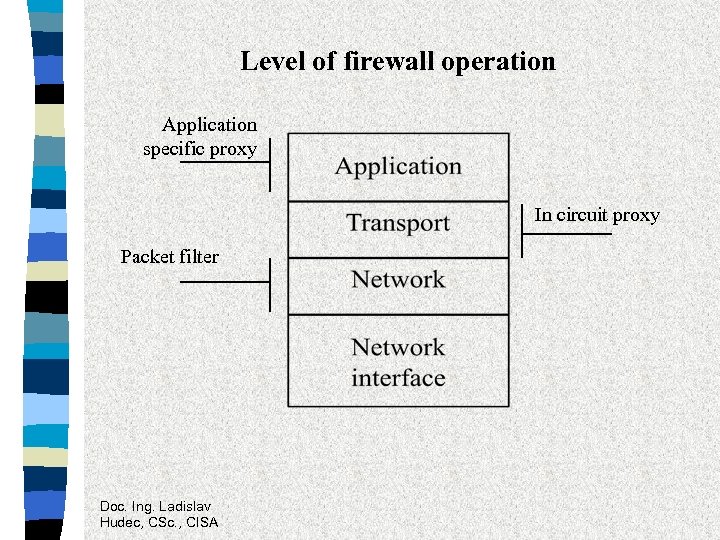
Level of firewall operation Application specific proxy In circuit proxy Packet filter Doc. Ing. Ladislav Hudec, CSc. , CISA

Packet filter • is a multiported internetworking device applying a set of rules to each incoming IP packet for deciding whether it will be forwarded or dropped • filtering is based on information found in packet headers (protocol numbers, source and destination IP addresses, source and destination port numbers, TCP connection flags, other options) • routers supporting packet filtering - screening routers • static packet filtering - stateless inspection (FTP session) • dynamic packet filtering - stateful inspection • implementation of high level security policy to filtering rules? Doc. Ing. Ladislav Hudec, CSc. , CISA
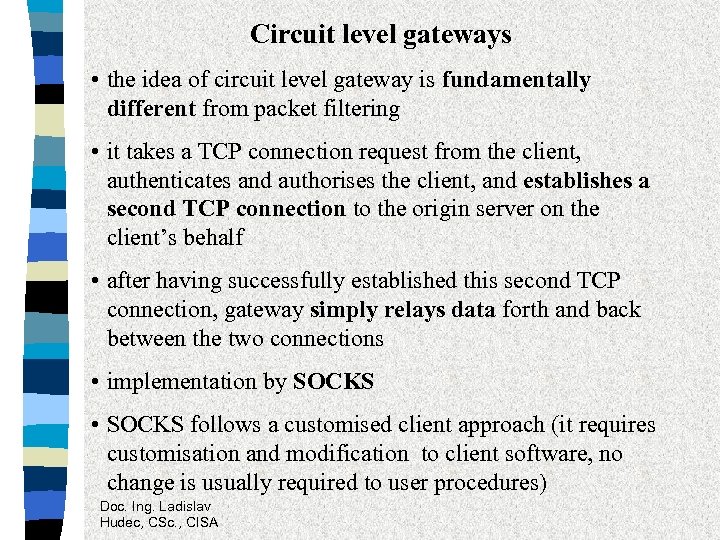
Circuit level gateways • the idea of circuit level gateway is fundamentally different from packet filtering • it takes a TCP connection request from the client, authenticates and authorises the client, and establishes a second TCP connection to the origin server on the client’s behalf • after having successfully established this second TCP connection, gateway simply relays data forth and back between the two connections • implementation by SOCKS • SOCKS follows a customised client approach (it requires customisation and modification to client software, no change is usually required to user procedures) Doc. Ing. Ladislav Hudec, CSc. , CISA
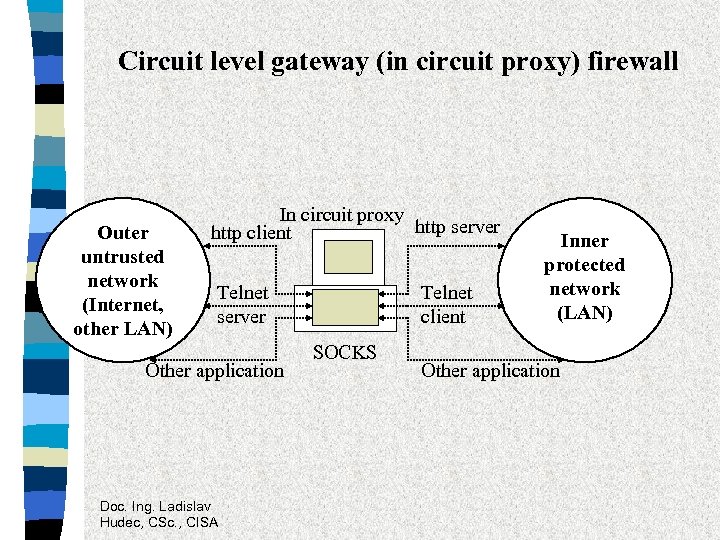
Circuit level gateway (in circuit proxy) firewall Outer untrusted network (Internet, other LAN) In circuit proxy http server http client Telnet server Other application Doc. Ing. Ladislav Hudec, CSc. , CISA Telnet client SOCKS Inner protected network (LAN) Other application
Application level gateways • is conceptually similar to a circuit level gateway (application level gateway understands the application protocol being relayed, whereas the second is generic and not application specific) • when a client contacts gateway using some application protocol (Telnet, FTP, HTTP, . . ), the gateway asks for some valid user authentication and authorisation information • for valid users gateway either connects itself to a preconfigured remote system (SMTP server) or asks the user to enter the name of a remote system to be accessed on the user’s behalf • after having established the second TCP connection, gateway fully controls data stream that is relayed between the two connections Doc. Ing. Ladislav Hudec, CSc. , CISA
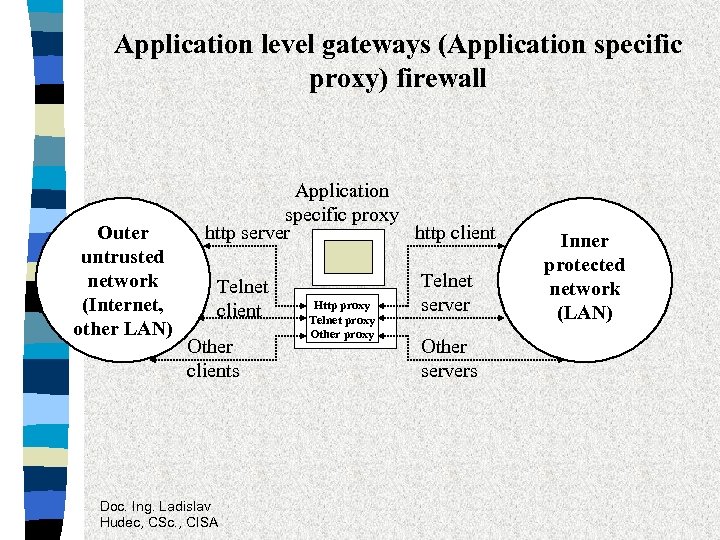
Application level gateways (Application specific proxy) firewall Outer untrusted network (Internet, other LAN) Application specific proxy http server http client Telnet client Other clients Doc. Ing. Ladislav Hudec, CSc. , CISA Http proxy Telnet proxy Other proxy Telnet server Other servers Inner protected network (LAN)

Firewalls configurations • firewall system consists of packet filters and application gateways (circuit or application level) There are many possibilities to combine these components in firewall configurations. The most commonly used configurations in practise today • dual homed firewalls • screened subnet firewalls. Doc. Ing. Ladislav Hudec, CSc. , CISA

Dual homed firewalls • bastion host with two network interfaces • IP forwarding and routing capabilities are disabled, IP packets can no longer be routed between the two networks segments • screening router is typically placed between bastion host and Internet (ensuring that any IP packets arriving from Internet is correctly addressed to the bastion host) • outer network segment can host specialised systems (information and network access servers) • this configuration can be replicated for performance reason parallel dual homed firewall • simple and secure configuration Doc. Ing. Ladislav Hudec, CSc. , CISA
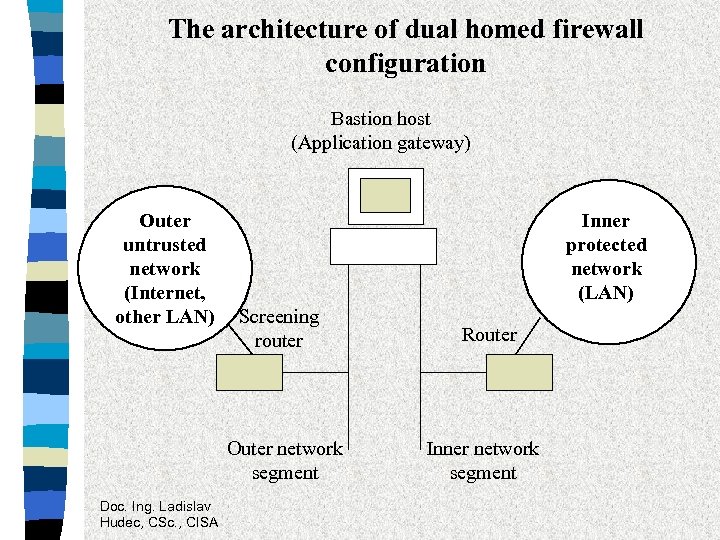
The architecture of dual homed firewall configuration Bastion host (Application gateway) Outer untrusted network (Internet, other LAN) Inner protected network (LAN) Screening router Outer network segment Doc. Ing. Ladislav Hudec, CSc. , CISA Router Inner network segment

Screened subnet firewalls • bastion host with one network interfaces on outer network segment • two screening routers used to create outer network segment called screened subnet or demilitarised zone • outer network segment can host application gateways running on one or more bastion hosts, as well as some additional servers that require carefully controlled Internet access • two screening routers provide redundancy (attacker should subvert two routers in order to reach internal machines) Doc. Ing. Ladislav Hudec, CSc. , CISA
Screened subnet firewalls • servers on the outer network segment could be the only systems seen from the Internet (no other system name would be known to DNS database) • some services could passed around the bastion host and the corresponding application gateways Doc. Ing. Ladislav Hudec, CSc. , CISA
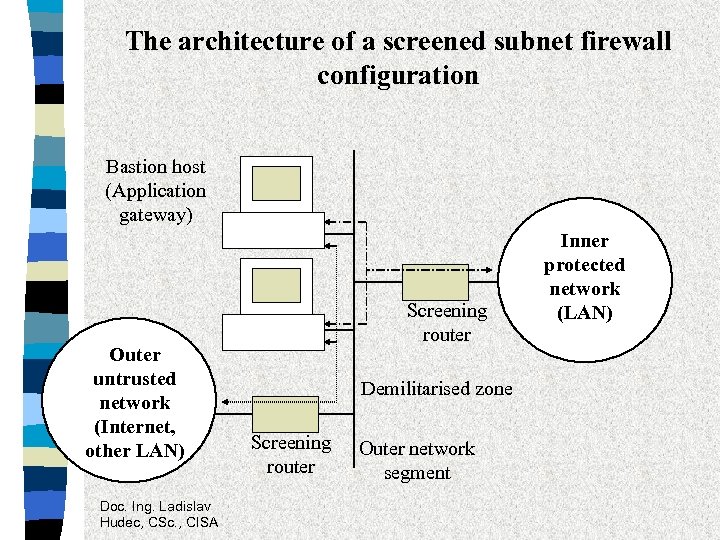
The architecture of a screened subnet firewall configuration Bastion host (Application gateway) Outer untrusted network (Internet, other LAN) Doc. Ing. Ladislav Hudec, CSc. , CISA Screening router Demilitarised zone Screening router Outer network segment Inner protected network (LAN)

References OPPLIGER, R. : Security Technologies for the World Wide Web. Artech House, 2000, ISBN 1 58053 045 1 OPPLIGER, R. : Internet and Intranet Security. Artech House, 1998 STEIN, L. D. : Web Security: A Step by Step Reference. Addison-Wesley, Reading, MA, 1998 TANENBAUM, A. S. : Computer Networks. 3 rd Edition, Prentice Hall, 1996 CHESWICK, W. R. , BELLOWIN, S. M. : Firewalls and Internet Security: Repelling the Wili Hacker, Addison-Wesley, Reading, MA, 1994, 2000 SCHUBA, C. L. : On The Modeling, Design, and Implementation of Firewall Technology. Ph. D Thesis, Purdue University, December 1997 Doc. Ing. Ladislav Hudec, CSc. , CISA

References Request For Comments – RFC 2316, Report of the IAB Security Architecture Workshop, April 1998 RFC 2068, Hypertext Transfer Protocol – HTTP/1. 1, January 1997 RFC 2069, Extension to HTTP: Digest Access Authentication, January 1997 RFC 1929, Username/Password Authentication for SOCKS V 5, June 1996 RFC 2138, Remote Authentication Dial In User Service (RADIUS), April 1997 RFC 2401, Security Architecture for the Internet Protocol, November 1998 RFC 2402, IP Authentication Header, November 1998 RFC 2406, IP Encapsulating Security Payload (ESP), November 1998 RFC 2408, Internet Security Association and Key Management Protocol (ISAKMP), November 1998 RFC 2409, The Internet Key Exchange (IKE), November 1998 RFC 2246, The TLS Protocol Version 1. 0, January 1999 Doc. Ing. Ladislav Hudec, CSc. , CISA

THANK YOU FOR YOUR ATTENTION Doc. Ing. Ladislav Hudec, CSc. , CISA
93468dc88831ecc113db9c33d818d83e.ppt