59c9c2459e37cd6ce533f4aae82afdd1.ppt
- Количество слайдов: 48


Security Objectives Internet Security - Farkas 2

Types of Attacks (1) Internet Security - Farkas 3

Types of Attacks (2) Internet Security - Farkas 4

Protection Internet Security - Farkas 5

Basic Defense Mechanisms Internet Security - Farkas 6

Attacks Against Communication Channels Internet Security - Farkas 7
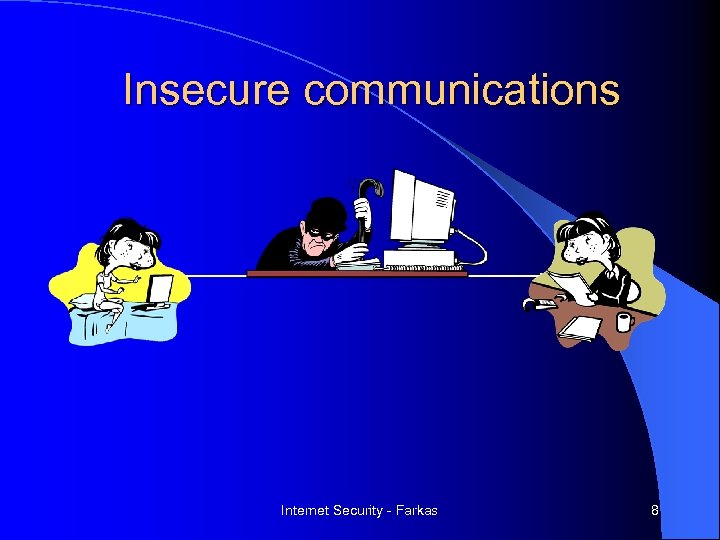
Insecure communications Internet Security - Farkas 8

Encryption Internet Security - Farkas 9

Internet Security - Farkas 10

Internet Security - Farkas 11

Internet Security - Farkas 12

Internet Security - Farkas 13
Internet Security - Farkas 14
Internet Security - Farkas 15

Internet Security - Farkas 16

Internet Security - Farkas 17

Internet Security - Farkas 18

Internet Security - Farkas 19

Internet Security - Farkas 20

Protocol Internet Security - Farkas 21

Internet Security - Farkas 22

Security Protocols Internet Security - Farkas 23

Internet Security - Farkas 24

Security Properties – Authentication of Origin Internet Security - Farkas 25

Security Properties – Entity Authentication Internet Security - Farkas 26

Security Properties – Integrity Internet Security - Farkas 27

Internet Security - Farkas 28

Security Properties – Nonrepudiation Internet Security - Farkas 29

Security Properties – Fairness Internet Security - Farkas 30

Security Properties – Anonymity Internet Security - Farkas 31

Internet Security - Farkas 32

More Examples of Crypto protocols Read on your own Internet Security - Farkas 33

Internet Security - Farkas 34

Internet Security - Farkas 35

Internet Security - Farkas 36
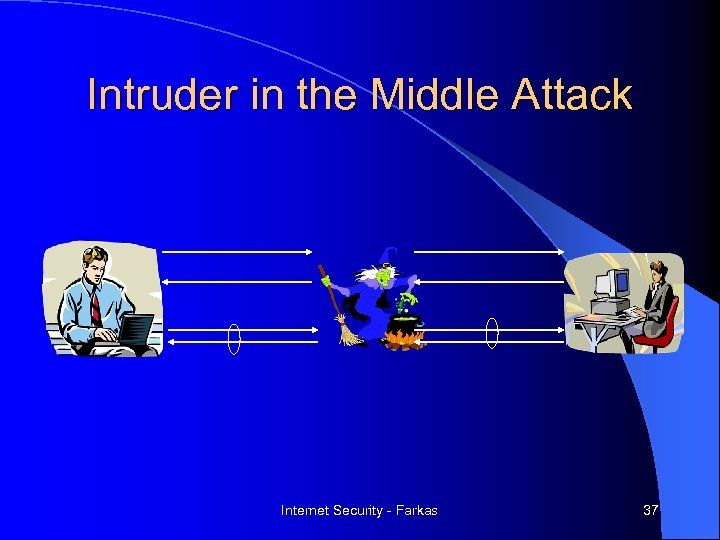
Intruder in the Middle Attack Internet Security - Farkas 37

Internet Security - Farkas 38
Internet Security - Farkas 39

Internet Security - Farkas 40
Internet Security - Farkas 41
Internet Security - Farkas 42

Internet Security - Farkas 43

Internet Security - Farkas 44

Internet Security - Farkas 45

Internet Security - Farkas 46

Internet Security - Farkas 47

Internet Security - Farkas 48
59c9c2459e37cd6ce533f4aae82afdd1.ppt