40bf73a26ca47436b3c51e63802f25cc.ppt
- Количество слайдов: 88
 Security Issues and Challenges in Wireless Networks Kishore Kothapalli Bruhadeshwar Bezawada Center for Security, Theory, and Algorithmic Research (CSTAR) International Institute of Information Technology Hyderabad, INDIA
Security Issues and Challenges in Wireless Networks Kishore Kothapalli Bruhadeshwar Bezawada Center for Security, Theory, and Algorithmic Research (CSTAR) International Institute of Information Technology Hyderabad, INDIA
 Introduction Wireless stations, or nodes, communicate over a wireless medium Networks operating under infrastructure mode e. g. , 802. 11, 802. 16, Cellular networks Networks operating with limited or no infrastructural support e. g. , ad hoc networks in AODV mode Security threats are imminent due to the open nature of communication Two main issues: authentication and privacy Other serious issues: denial-of-service A categorization is required to understand the issues in each situation.
Introduction Wireless stations, or nodes, communicate over a wireless medium Networks operating under infrastructure mode e. g. , 802. 11, 802. 16, Cellular networks Networks operating with limited or no infrastructural support e. g. , ad hoc networks in AODV mode Security threats are imminent due to the open nature of communication Two main issues: authentication and privacy Other serious issues: denial-of-service A categorization is required to understand the issues in each situation.
 Introduction – Wireless Technologies Different technologies have been developed for different scenarios and requirements Wi. Fi is technology for Wireless LANs and short range mobile access networks Wi. MAX is technology for last mile broadband connectivity Wireless USB is technology for Internet connectivity on the go Other technologies like Infrared (TV remotes etc), Bluetooth (soon to be obsolete) etc are short range Extreme bandwidth but short range technologies are Gigabit wireless etc
Introduction – Wireless Technologies Different technologies have been developed for different scenarios and requirements Wi. Fi is technology for Wireless LANs and short range mobile access networks Wi. MAX is technology for last mile broadband connectivity Wireless USB is technology for Internet connectivity on the go Other technologies like Infrared (TV remotes etc), Bluetooth (soon to be obsolete) etc are short range Extreme bandwidth but short range technologies are Gigabit wireless etc
 Introduction Fixed Infrastructure Base stations that are typically not resource constrained. Examples: sensor networks, and cellular networks. Mobility of nodes but not of base stations.
Introduction Fixed Infrastructure Base stations that are typically not resource constrained. Examples: sensor networks, and cellular networks. Mobility of nodes but not of base stations.
 Introduction Ad hoc wireless networks Image from www. microsoft. com No infrastructural support. Nodes also double up as routers. Mobility of nodes. Examples laptops/cellphones operating in ad hoc mode.
Introduction Ad hoc wireless networks Image from www. microsoft. com No infrastructural support. Nodes also double up as routers. Mobility of nodes. Examples laptops/cellphones operating in ad hoc mode.
 Introduction Mixed mode In between the two modes. Some nodes exhibit ad hoc capability.
Introduction Mixed mode In between the two modes. Some nodes exhibit ad hoc capability.
 Introduction To formalize study and solutions, need good models for these networks. Formal model to characterize the properties and solutions Models that are close to reality Still allow for solution design and analysis.
Introduction To formalize study and solutions, need good models for these networks. Formal model to characterize the properties and solutions Models that are close to reality Still allow for solution design and analysis.
 Introduction Solution properties Light-weight Have to use battery power wisely. Other resources, such as storage, are also limited. Local control Many cases, only neighbours are known. Any additional information gathering is expensive.
Introduction Solution properties Light-weight Have to use battery power wisely. Other resources, such as storage, are also limited. Local control Many cases, only neighbours are known. Any additional information gathering is expensive.
 Introduction Difficulty of modeling wireless networks as opposed to wired networks: Transmission Interference Resource constraints Mobility Physical carrier sensing
Introduction Difficulty of modeling wireless networks as opposed to wired networks: Transmission Interference Resource constraints Mobility Physical carrier sensing
 Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
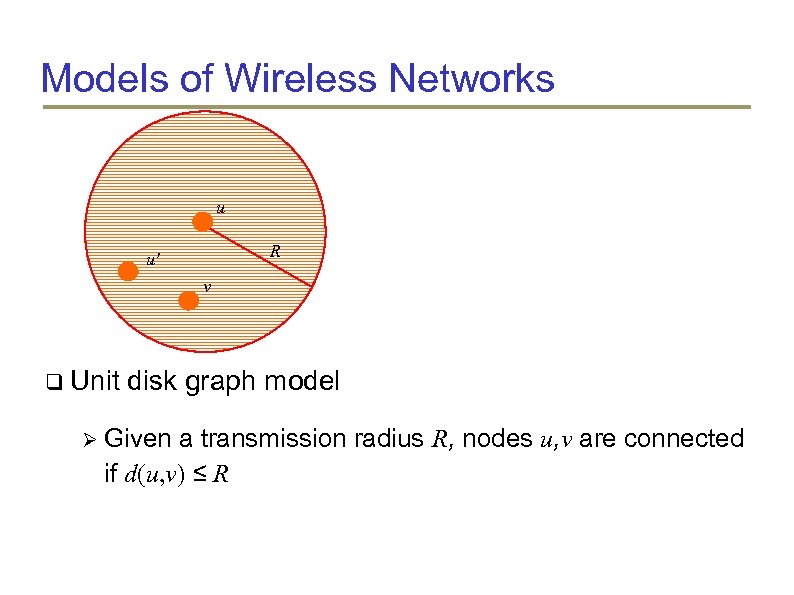 Models of Wireless Networks u R u' v Unit disk graph model Given a transmission radius R, nodes u, v are connected if d(u, v) ≤ R
Models of Wireless Networks u R u' v Unit disk graph model Given a transmission radius R, nodes u, v are connected if d(u, v) ≤ R
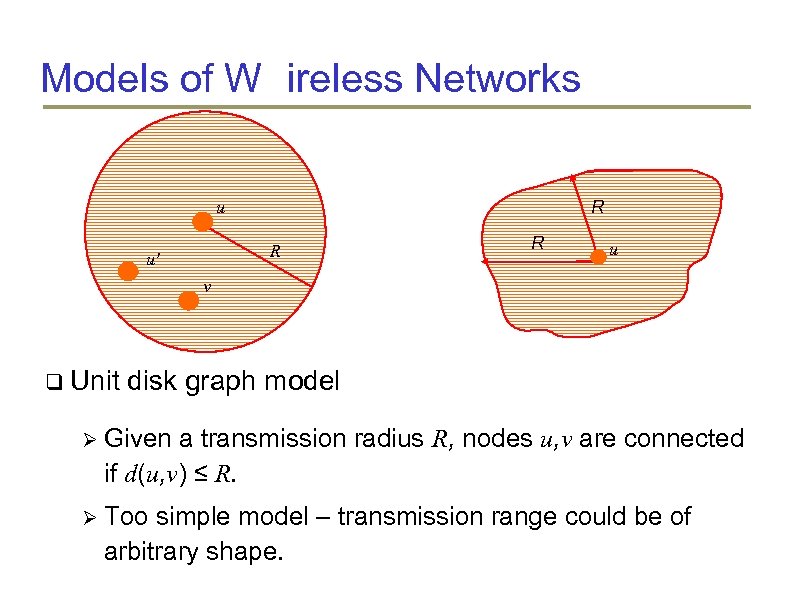 Models of W ireless Networks R u' R u v Unit disk graph model Given a transmission radius R, nodes u, v are connected if d(u, v) ≤ R. Too simple model – transmission range could be of arbitrary shape.
Models of W ireless Networks R u' R u v Unit disk graph model Given a transmission radius R, nodes u, v are connected if d(u, v) ≤ R. Too simple model – transmission range could be of arbitrary shape.
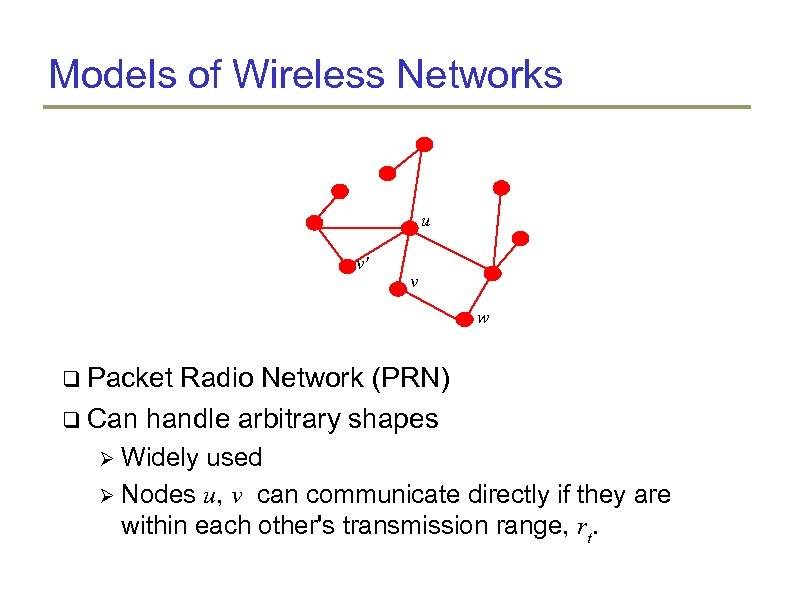 Models of Wireless Networks u v' v w Packet Radio Network (PRN) Can handle arbitrary shapes Widely used Nodes u, v can communicate directly if they are within each other's transmission range, rt.
Models of Wireless Networks u v' v w Packet Radio Network (PRN) Can handle arbitrary shapes Widely used Nodes u, v can communicate directly if they are within each other's transmission range, rt.
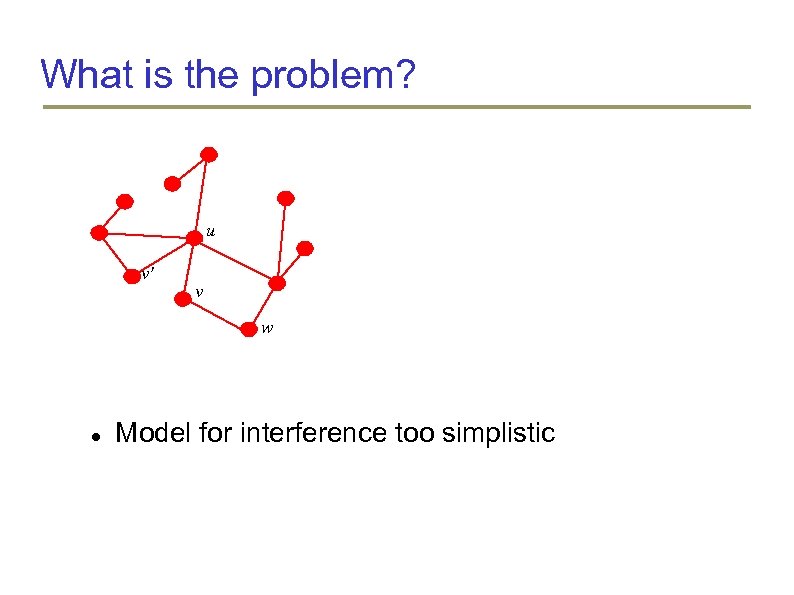 What is the problem? u v' v w Model for interference too simplistic
What is the problem? u v' v w Model for interference too simplistic
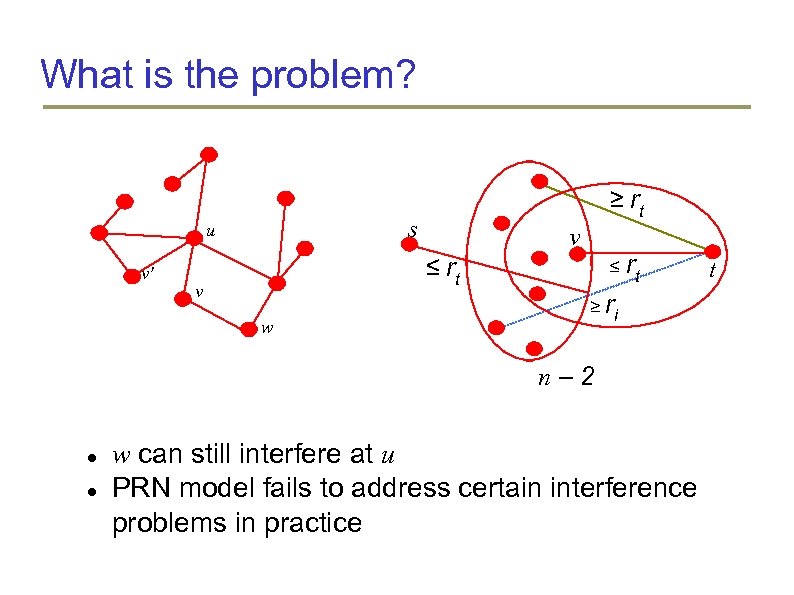 What is the problem? s u v' ≥ rt v ≤ rt v w ≥ ri n– 2 w can still interfere at u PRN model fails to address certain interference problems in practice t
What is the problem? s u v' ≥ rt v ≤ rt v w ≥ ri n– 2 w can still interfere at u PRN model fails to address certain interference problems in practice t
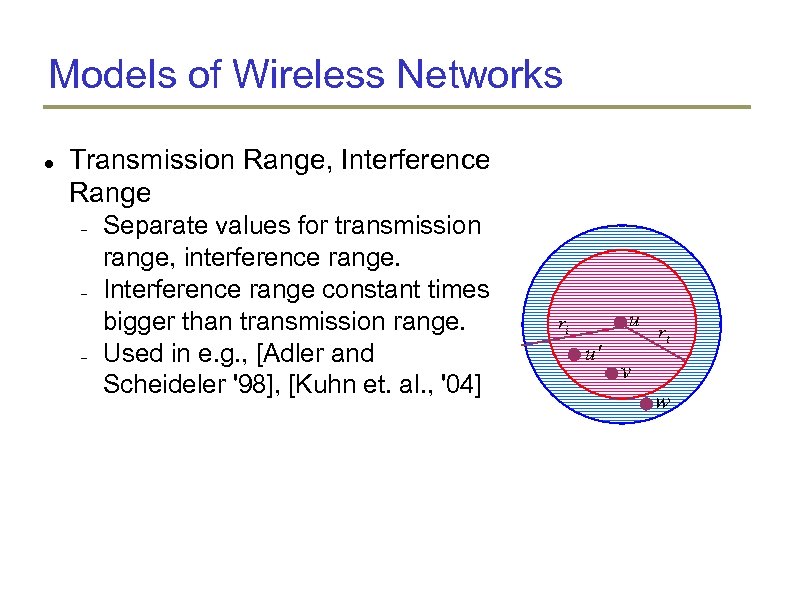 Models of Wireless Networks Transmission Range, Interference Range Separate values for transmission range, interference range. Interference range constant times bigger than transmission range. Used in e. g. , [Adler and Scheideler '98], [Kuhn et. al. , '04] u ri u' rt v w
Models of Wireless Networks Transmission Range, Interference Range Separate values for transmission range, interference range. Interference range constant times bigger than transmission range. Used in e. g. , [Adler and Scheideler '98], [Kuhn et. al. , '04] u ri u' rt v w
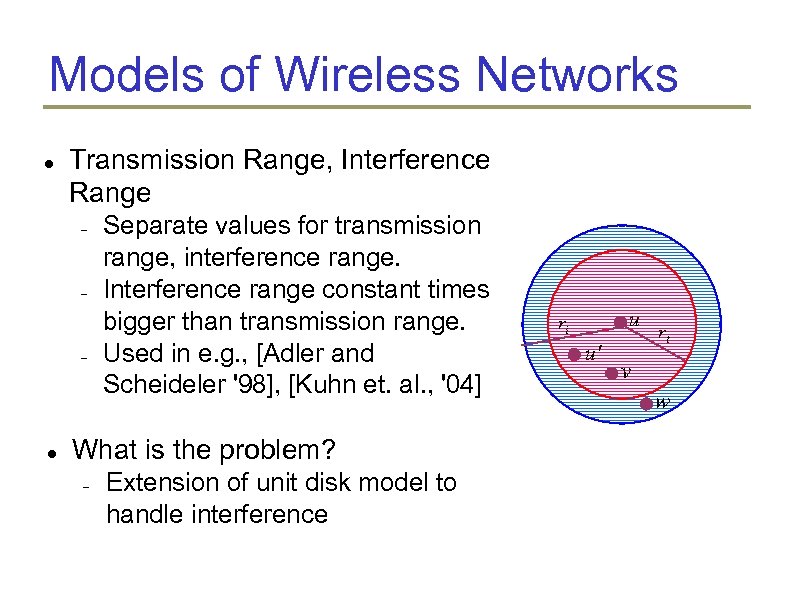 Models of Wireless Networks Transmission Range, Interference Range Separate values for transmission range, interference range. Interference range constant times bigger than transmission range. Used in e. g. , [Adler and Scheideler '98], [Kuhn et. al. , '04] What is the problem? Extension of unit disk model to handle interference u ri u' rt v w
Models of Wireless Networks Transmission Range, Interference Range Separate values for transmission range, interference range. Interference range constant times bigger than transmission range. Used in e. g. , [Adler and Scheideler '98], [Kuhn et. al. , '04] What is the problem? Extension of unit disk model to handle interference u ri u' rt v w
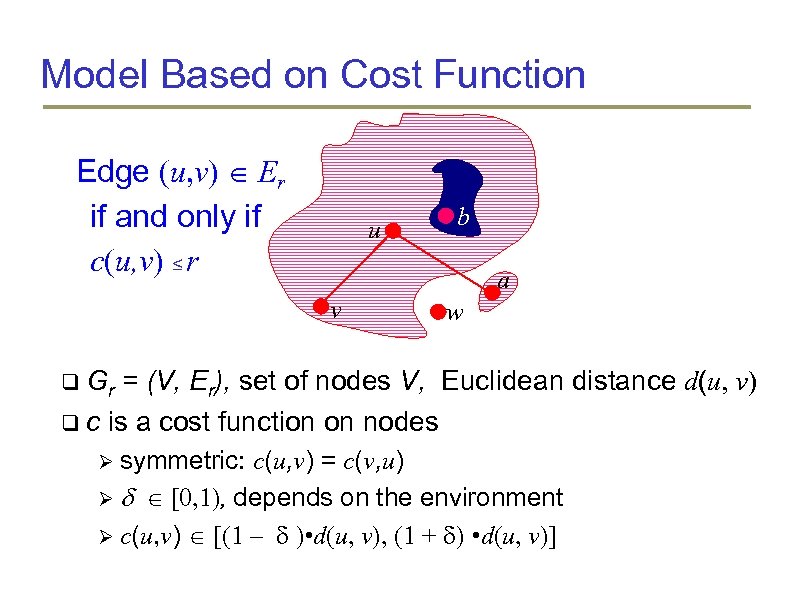 Model Based on Cost Function Edge (u, v) Er if and only if c(u, v) ≤ r u b a v w Gr = (V, Er), set of nodes V, Euclidean distance d(u, v) c is a cost function on nodes symmetric: c(u, v) = c(v, u) [0, 1), depends on the environment c(u, v) [(1 – ) • d(u, v), (1 + ) • d(u, v)]
Model Based on Cost Function Edge (u, v) Er if and only if c(u, v) ≤ r u b a v w Gr = (V, Er), set of nodes V, Euclidean distance d(u, v) c is a cost function on nodes symmetric: c(u, v) = c(v, u) [0, 1), depends on the environment c(u, v) [(1 – ) • d(u, v), (1 + ) • d(u, v)]
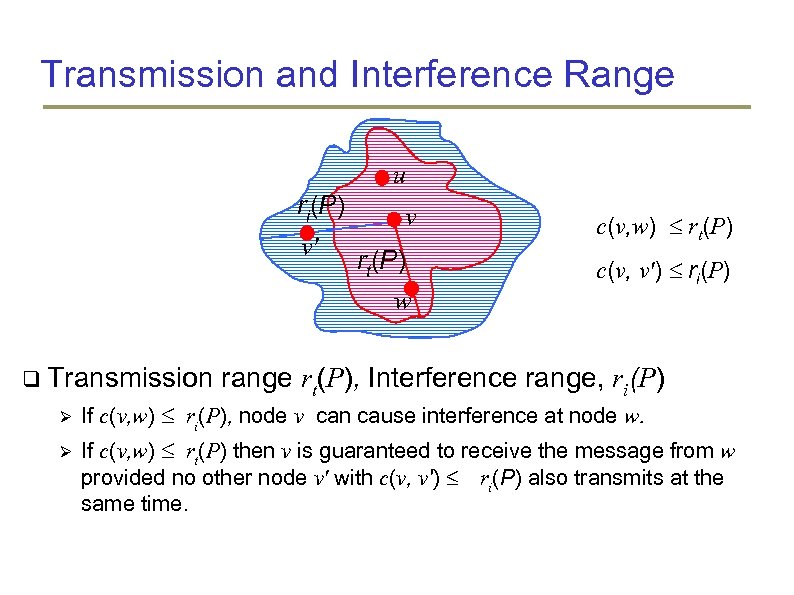 Transmission and Interference Range u ri(P) v' v rt(P) w Transmission c(v, w) rt(P) c(v, v') ri(P) range rt(P), Interference range, ri(P) If c(v, w) ri(P), node v can cause interference at node w. If c(v, w) rt(P) then v is guaranteed to receive the message from w provided no other node v' with c(v, v') ≤ ri(P) also transmits at the same time.
Transmission and Interference Range u ri(P) v' v rt(P) w Transmission c(v, w) rt(P) c(v, v') ri(P) range rt(P), Interference range, ri(P) If c(v, w) ri(P), node v can cause interference at node w. If c(v, w) rt(P) then v is guaranteed to receive the message from w provided no other node v' with c(v, v') ≤ ri(P) also transmits at the same time.
 Carrier Sensing Virtual carrier sensing using RTS/CTS. Physical Carrier Sensing Provided by Clear Channel Assessment (CCA) circuit. Monitor the medium as a function of Received Signal Strength Indicator (RSSI) Energy Detection (ED) bit set to 1 if RSSI exceeds a certain threshold Has a register to set the threshold in d. B
Carrier Sensing Virtual carrier sensing using RTS/CTS. Physical Carrier Sensing Provided by Clear Channel Assessment (CCA) circuit. Monitor the medium as a function of Received Signal Strength Indicator (RSSI) Energy Detection (ED) bit set to 1 if RSSI exceeds a certain threshold Has a register to set the threshold in d. B
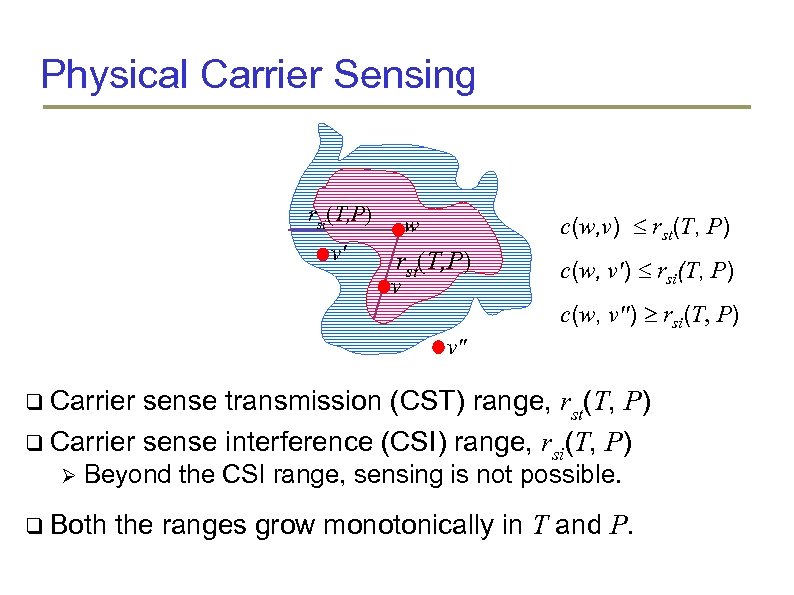 Physical Carrier Sensing rsi(T, P) v' c(w, v) rst(T, P) w rst(T, P) v c(w, v') rsi(T, P) c(w, v'') rsi(T, P) v'' Carrier sense transmission (CST) range, rst(T, P) Carrier sense interference (CSI) range, rsi(T, P) Beyond the CSI range, sensing is not possible. Both the ranges grow monotonically in T and P.
Physical Carrier Sensing rsi(T, P) v' c(w, v) rst(T, P) w rst(T, P) v c(w, v') rsi(T, P) c(w, v'') rsi(T, P) v'' Carrier sense transmission (CST) range, rst(T, P) Carrier sense interference (CSI) range, rsi(T, P) Beyond the CSI range, sensing is not possible. Both the ranges grow monotonically in T and P.
 Outline Introduction Models of Wireless Networks Various Layers and Current Solutions at each layer Security Issues and Threats at each Layer Security Solutions Open Problems
Outline Introduction Models of Wireless Networks Various Layers and Current Solutions at each layer Security Issues and Threats at each Layer Security Solutions Open Problems
 Various Layers of Interest – Physical Layer 802. 11 standard supports several data rates between 11 Mbps and 54 Mbps 802. 16 support multiple data rates from 2 Mbps to 300 Mbps Several modulation schemes in use and support different conditions and data rates AM, FM, PSK, BPSK, QPSK, FDM, OFDMA, . . .
Various Layers of Interest – Physical Layer 802. 11 standard supports several data rates between 11 Mbps and 54 Mbps 802. 16 support multiple data rates from 2 Mbps to 300 Mbps Several modulation schemes in use and support different conditions and data rates AM, FM, PSK, BPSK, QPSK, FDM, OFDMA, . . .
 Physical Layer – Wi. Fi Stands for Wireless Fidelity Range of Technologies Technology that uses IEEE 802. 11 protocol standards 802. 11 b operates at 2. 4 Ghz using DSSS 802. 11 g operates at 2. 4 Ghz resp, with 20 Mhz, OFDM Has three non-overlapping channels with 11 mbps max Achieves 54 Mbps and inter-operable to 802. 11 b 802. 11 a operates at 5 GHz using OFDM About 4 -8 (depending on country) non-overlapping channels Bandwidth achieved is 54 Mbps
Physical Layer – Wi. Fi Stands for Wireless Fidelity Range of Technologies Technology that uses IEEE 802. 11 protocol standards 802. 11 b operates at 2. 4 Ghz using DSSS 802. 11 g operates at 2. 4 Ghz resp, with 20 Mhz, OFDM Has three non-overlapping channels with 11 mbps max Achieves 54 Mbps and inter-operable to 802. 11 b 802. 11 a operates at 5 GHz using OFDM About 4 -8 (depending on country) non-overlapping channels Bandwidth achieved is 54 Mbps
 Various Layers of Interest – MAC Layer Medium access control is an important requirement. Collision detection (CSMA/CD) not possible unlike wired networks. Hence using Collision avoidance (CSMA/CA) Functions of MAC Scanning, Authentication, Association, WEP, RTS/CTS, Power Save options, Fragmentation
Various Layers of Interest – MAC Layer Medium access control is an important requirement. Collision detection (CSMA/CD) not possible unlike wired networks. Hence using Collision avoidance (CSMA/CA) Functions of MAC Scanning, Authentication, Association, WEP, RTS/CTS, Power Save options, Fragmentation
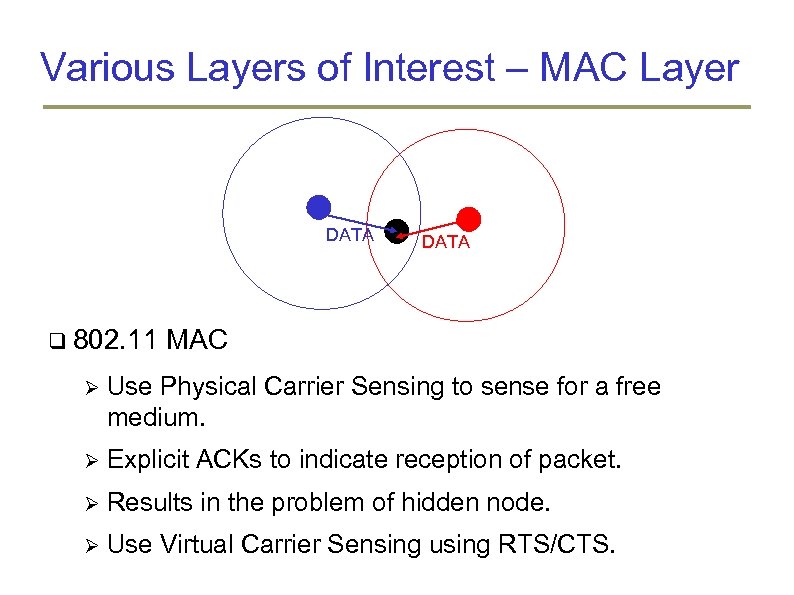 Various Layers of Interest – MAC Layer DATA 802. 11 DATA MAC Use Physical Carrier Sensing to sense for a free medium. Explicit ACKs to indicate reception of packet. Results in the problem of hidden node. Use Virtual Carrier Sensing using RTS/CTS.
Various Layers of Interest – MAC Layer DATA 802. 11 DATA MAC Use Physical Carrier Sensing to sense for a free medium. Explicit ACKs to indicate reception of packet. Results in the problem of hidden node. Use Virtual Carrier Sensing using RTS/CTS.
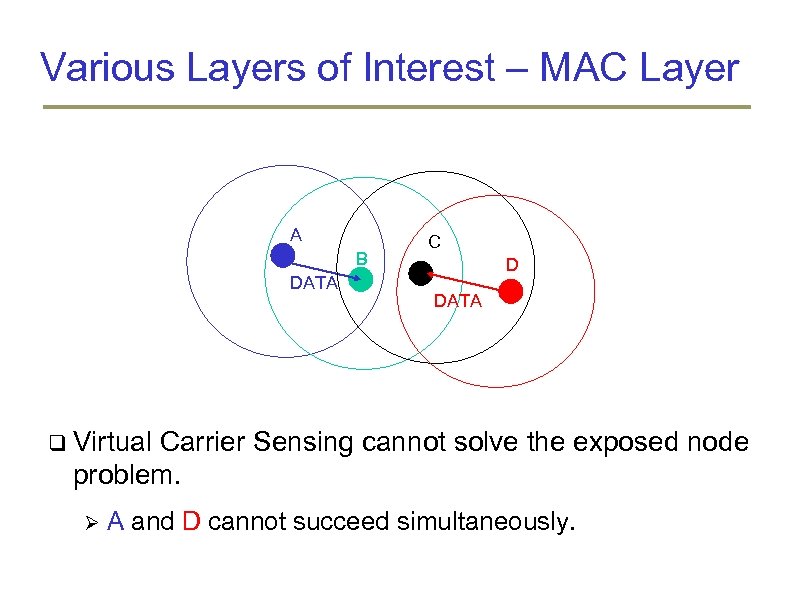 Various Layers of Interest – MAC Layer A B DATA C D DATA Virtual Carrier Sensing cannot solve the exposed node problem. A and D cannot succeed simultaneously.
Various Layers of Interest – MAC Layer A B DATA C D DATA Virtual Carrier Sensing cannot solve the exposed node problem. A and D cannot succeed simultaneously.
 Other MAC Techniques Cell phone networks Node to base station and vice-versa. Fixed frequency for communication pair (FDD). Separate frequencies for each pair. Different technologies Analog/CDMA/GSM support different number of simultaneous communications per band. 802. 16 has a Receive/Grant model which is basically TDD (Time-Division Duplexing) More efficient than FDD.
Other MAC Techniques Cell phone networks Node to base station and vice-versa. Fixed frequency for communication pair (FDD). Separate frequencies for each pair. Different technologies Analog/CDMA/GSM support different number of simultaneous communications per band. 802. 16 has a Receive/Grant model which is basically TDD (Time-Division Duplexing) More efficient than FDD.
 MAC Layer More recent solutions address issues such as, especially with respect to ad hoc networks self-stabilization Dynamism Efficiency Fairness
MAC Layer More recent solutions address issues such as, especially with respect to ad hoc networks self-stabilization Dynamism Efficiency Fairness
 Various Layers – Network Layer Route packets in the network. Routing in infrastructure based networks is similar to IP routing All the base stations have a wired IP interface which is used by the routers/switches to forward data Issues like handoffs are handled through techniques like Mobile IP or Cellular Handoffs or Soft-handoffs as done in Mobile Wi. MAX Now, for network without infrastructure the problem is difficult as the routes are transient
Various Layers – Network Layer Route packets in the network. Routing in infrastructure based networks is similar to IP routing All the base stations have a wired IP interface which is used by the routers/switches to forward data Issues like handoffs are handled through techniques like Mobile IP or Cellular Handoffs or Soft-handoffs as done in Mobile Wi. MAX Now, for network without infrastructure the problem is difficult as the routes are transient
 Various Layers – Network Layer Ad hoc networks No easy solutions but different proposals exist. Two kinds: proactive and reactive Proactive: Maintain lot of state, proactive updates. Example: DSDV, DSR Reactive: Minimal state, react to changes. Example: AODV
Various Layers – Network Layer Ad hoc networks No easy solutions but different proposals exist. Two kinds: proactive and reactive Proactive: Maintain lot of state, proactive updates. Example: DSDV, DSR Reactive: Minimal state, react to changes. Example: AODV
 Other Important Layers Transport layer This is important layer especially since the wireless medium suffers from high bit-error rate and collisions. To offset this wireless technologies rely less on TCP’s reliability mechanism This is mostly handled at physical layer through techniques like FEC and other error correcting codes Application Layer Notion of an application layer protocol Email/Web/Games/SMS/MMS
Other Important Layers Transport layer This is important layer especially since the wireless medium suffers from high bit-error rate and collisions. To offset this wireless technologies rely less on TCP’s reliability mechanism This is mostly handled at physical layer through techniques like FEC and other error correcting codes Application Layer Notion of an application layer protocol Email/Web/Games/SMS/MMS
 Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
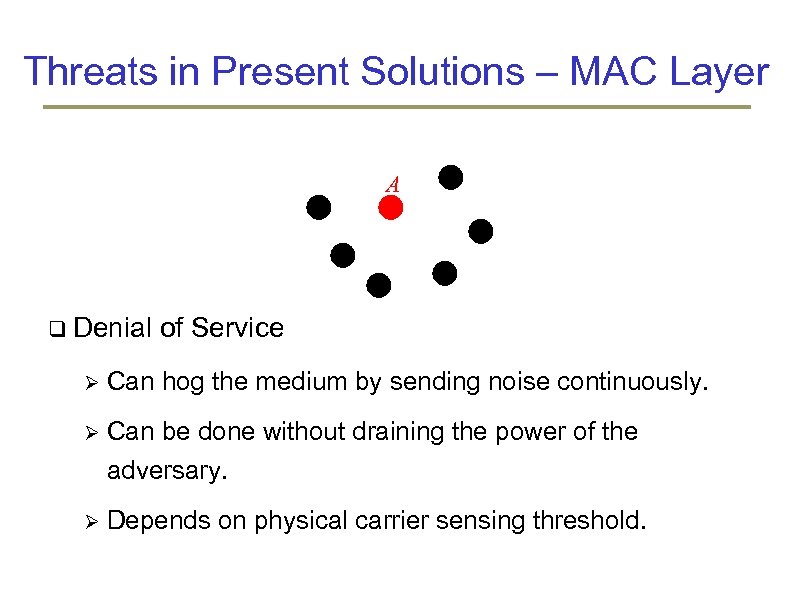 Threats in Present Solutions – MAC Layer A z Denial of Service Can hog the medium by sending noise continuously. Can be done without draining the power of the adversary. Depends on physical carrier sensing threshold.
Threats in Present Solutions – MAC Layer A z Denial of Service Can hog the medium by sending noise continuously. Can be done without draining the power of the adversary. Depends on physical carrier sensing threshold.
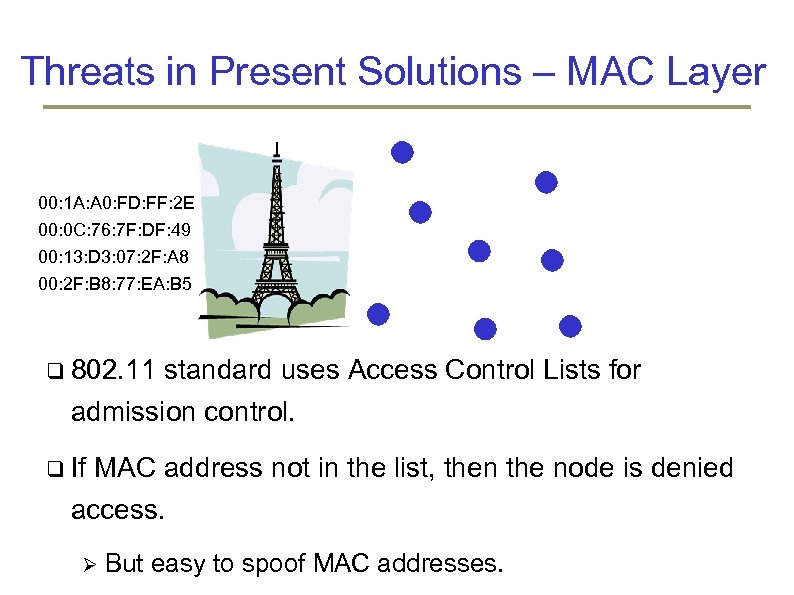 Threats in Present Solutions – MAC Layer 00: 1 A: A 0: FD: FF: 2 E 00: 0 C: 76: 7 F: DF: 49 00: 13: D 3: 07: 2 F: A 8 00: 2 F: B 8: 77: EA: B 5 802. 11 standard uses Access Control Lists for admission control. If MAC address not in the list, then the node is denied access. But easy to spoof MAC addresses.
Threats in Present Solutions – MAC Layer 00: 1 A: A 0: FD: FF: 2 E 00: 0 C: 76: 7 F: DF: 49 00: 13: D 3: 07: 2 F: A 8 00: 2 F: B 8: 77: EA: B 5 802. 11 standard uses Access Control Lists for admission control. If MAC address not in the list, then the node is denied access. But easy to spoof MAC addresses.
 Threats in Present Solutions – Network Layer Ad hoc networks Network layer Denial-of-service attacks Broadcast nature of communication Packet dropping Route discovery failure in ad hoc network Packet rerouting
Threats in Present Solutions – Network Layer Ad hoc networks Network layer Denial-of-service attacks Broadcast nature of communication Packet dropping Route discovery failure in ad hoc network Packet rerouting
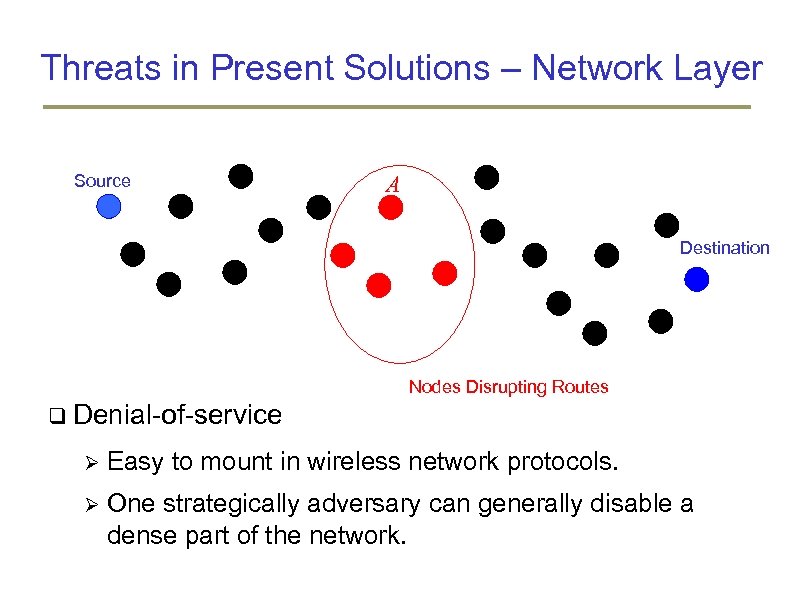 Threats in Present Solutions – Network Layer Source A z Destination Nodes Disrupting Routes Denial-of-service Easy to mount in wireless network protocols. One strategically adversary can generally disable a dense part of the network.
Threats in Present Solutions – Network Layer Source A z Destination Nodes Disrupting Routes Denial-of-service Easy to mount in wireless network protocols. One strategically adversary can generally disable a dense part of the network.
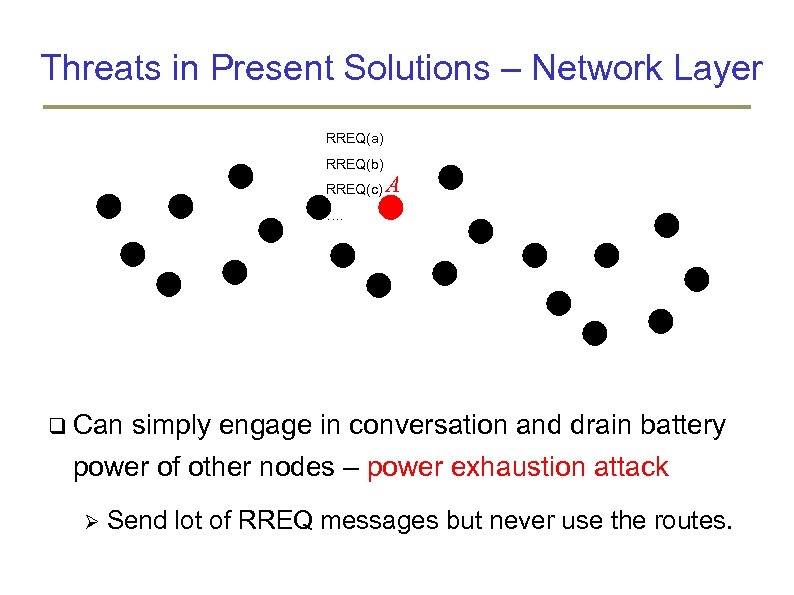 Threats in Present Solutions – Network Layer RREQ(a) RREQ(b) RREQ(c) A …. z Can simply engage in conversation and drain battery power of other nodes – power exhaustion attack Send lot of RREQ messages but never use the routes.
Threats in Present Solutions – Network Layer RREQ(a) RREQ(b) RREQ(c) A …. z Can simply engage in conversation and drain battery power of other nodes – power exhaustion attack Send lot of RREQ messages but never use the routes.
 Threats in Present Solutions – Network Layer s t Broadcast A nature of communication Each message can be received by all nodes in the transmission range Packet sniffing is a lot easier than in wired networks. Poses a data privacy issue
Threats in Present Solutions – Network Layer s t Broadcast A nature of communication Each message can be received by all nodes in the transmission range Packet sniffing is a lot easier than in wired networks. Poses a data privacy issue
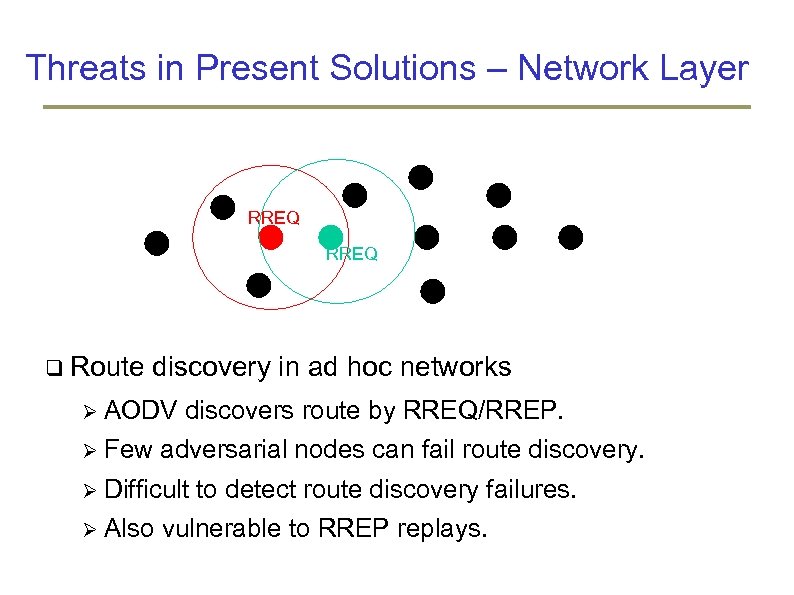 Threats in Present Solutions – Network Layer RREQ Route discovery in ad hoc networks AODV discovers route by RREQ/RREP. Few adversarial nodes can fail route discovery. Difficult to detect route discovery failures. Also vulnerable to RREP replays.
Threats in Present Solutions – Network Layer RREQ Route discovery in ad hoc networks AODV discovers route by RREQ/RREP. Few adversarial nodes can fail route discovery. Difficult to detect route discovery failures. Also vulnerable to RREP replays.
 Threats in Present Solutions – Network Layer Packet dropping Wired networks can monitor packet drops reasonably Such mechanisms are resource intensive for wireless networks AODV has timeouts but no theoretical solutions Difficult to distinguish packet drops, say RREQs, from non-existence of route itself Nodes some times behave selfishly to preserve resources
Threats in Present Solutions – Network Layer Packet dropping Wired networks can monitor packet drops reasonably Such mechanisms are resource intensive for wireless networks AODV has timeouts but no theoretical solutions Difficult to distinguish packet drops, say RREQs, from non-existence of route itself Nodes some times behave selfishly to preserve resources
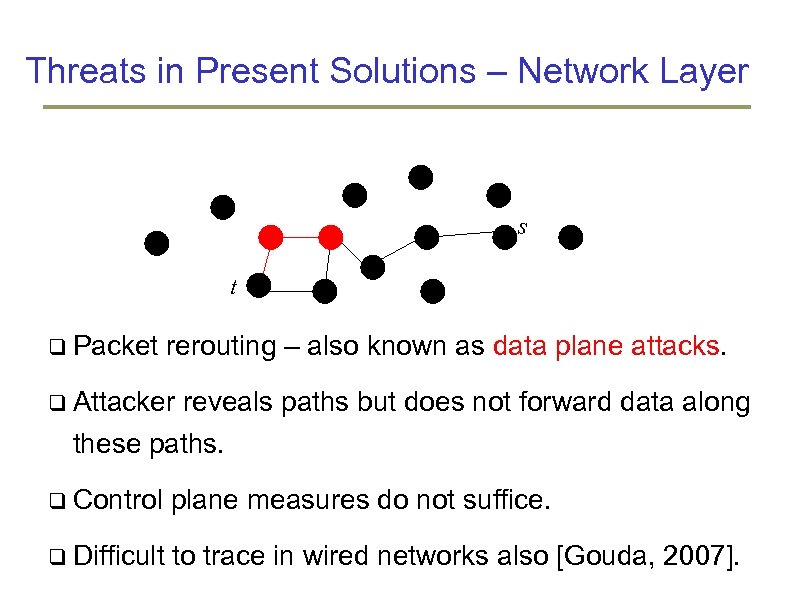 Threats in Present Solutions – Network Layer s t Packet rerouting – also known as data plane attacks. Attacker reveals paths but does not forward data along these paths. Control plane measures do not suffice. Difficult to trace in wired networks also [Gouda, 2007].
Threats in Present Solutions – Network Layer s t Packet rerouting – also known as data plane attacks. Attacker reveals paths but does not forward data along these paths. Control plane measures do not suffice. Difficult to trace in wired networks also [Gouda, 2007].
 Threats in Present Solutions – Network Layer Application Layer Easy to infect mobile devices. Rerouting content through the base station poses privacy issues. Bluetooth networks and ad hoc networks do not have a base station facility. Contrast with wired networks with firewalls, filters, sandboxes.
Threats in Present Solutions – Network Layer Application Layer Easy to infect mobile devices. Rerouting content through the base station poses privacy issues. Bluetooth networks and ad hoc networks do not have a base station facility. Contrast with wired networks with firewalls, filters, sandboxes.
 Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
 Security Solutions Requirements Need solutions that do not add any perceivable burden Cryptography can help Public key solutions Public key operations about 1000 times slow compared to symmetric key operations. Cost of SHA-1 = 2 microseconds Cost of RSA signature verification = order of millisec Symmetric key solutions for privacy and authentication Issue: How to distribute and manage keys?
Security Solutions Requirements Need solutions that do not add any perceivable burden Cryptography can help Public key solutions Public key operations about 1000 times slow compared to symmetric key operations. Cost of SHA-1 = 2 microseconds Cost of RSA signature verification = order of millisec Symmetric key solutions for privacy and authentication Issue: How to distribute and manage keys?
 Security Solutions for 802. 11 Networks Previous WEP (Wired Equivalent Privacy) based on RC 4 is prone to attacks Privacy is not guaranteed as the key streams could be easily recovered Weaknesses in RC 4 are well documented Authentication is weak as well due to weak encryption technique Challenge-response using pre-shared keys is prone to attacks if encryption is weak
Security Solutions for 802. 11 Networks Previous WEP (Wired Equivalent Privacy) based on RC 4 is prone to attacks Privacy is not guaranteed as the key streams could be easily recovered Weaknesses in RC 4 are well documented Authentication is weak as well due to weak encryption technique Challenge-response using pre-shared keys is prone to attacks if encryption is weak
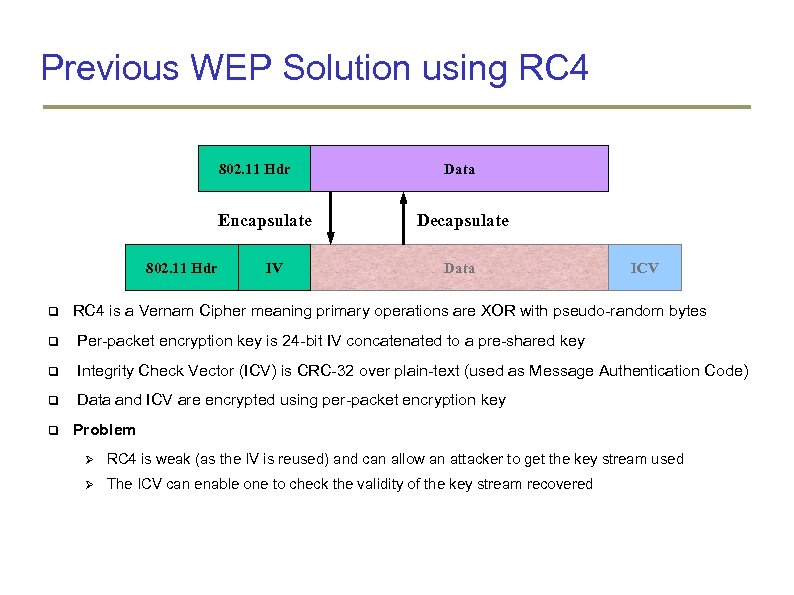 Previous WEP Solution using RC 4 802. 11 Hdr Encapsulate 802. 11 Hdr IV Data Decapsulate Data ICV RC 4 is a Vernam Cipher meaning primary operations are XOR with pseudo-random bytes Per-packet encryption key is 24 -bit IV concatenated to a pre-shared key Integrity Check Vector (ICV) is CRC-32 over plain-text (used as Message Authentication Code) Data and ICV are encrypted using per-packet encryption key Problem RC 4 is weak (as the IV is reused) and can allow an attacker to get the key stream used The ICV can enable one to check the validity of the key stream recovered
Previous WEP Solution using RC 4 802. 11 Hdr Encapsulate 802. 11 Hdr IV Data Decapsulate Data ICV RC 4 is a Vernam Cipher meaning primary operations are XOR with pseudo-random bytes Per-packet encryption key is 24 -bit IV concatenated to a pre-shared key Integrity Check Vector (ICV) is CRC-32 over plain-text (used as Message Authentication Code) Data and ICV are encrypted using per-packet encryption key Problem RC 4 is weak (as the IV is reused) and can allow an attacker to get the key stream used The ICV can enable one to check the validity of the key stream recovered
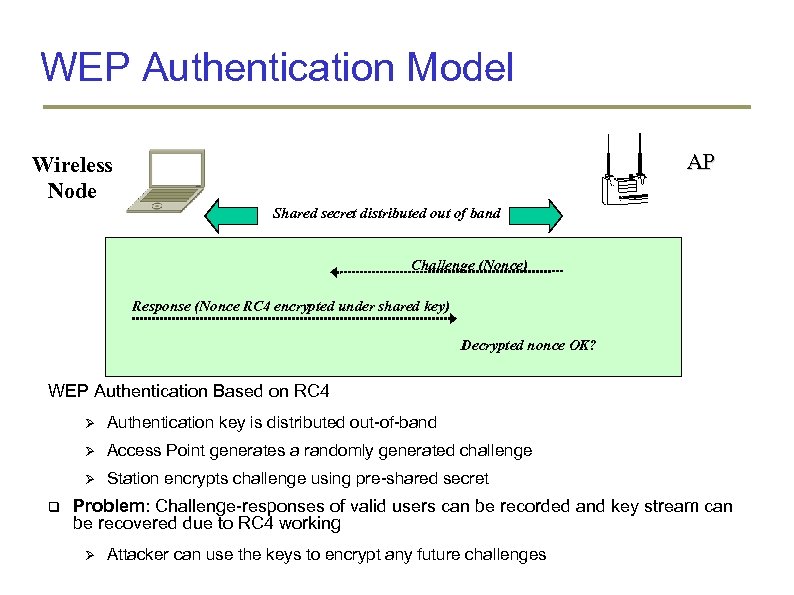 WEP Authentication Model AP Wireless Node Shared secret distributed out of band Challenge (Nonce) Response (Nonce RC 4 encrypted under shared key) Decrypted nonce OK? WEP Authentication Based on RC 4 Access Point generates a randomly generated challenge Authentication key is distributed out-of-band Station encrypts challenge using pre-shared secret Problem: Challenge-responses of valid users can be recorded and key stream can be recovered due to RC 4 working Attacker can use the keys to encrypt any future challenges
WEP Authentication Model AP Wireless Node Shared secret distributed out of band Challenge (Nonce) Response (Nonce RC 4 encrypted under shared key) Decrypted nonce OK? WEP Authentication Based on RC 4 Access Point generates a randomly generated challenge Authentication key is distributed out-of-band Station encrypts challenge using pre-shared secret Problem: Challenge-responses of valid users can be recorded and key stream can be recovered due to RC 4 working Attacker can use the keys to encrypt any future challenges
 Security Solution for 802. 11 Networks: 802. 11 i Model Solution Requirements Mutual authentication Scalable key management for large networks Central authorization and accounting Support for extended authentication like smart cards Key Management Issues Need to dynamically manage keys to avoid manual reconfiguration difficulties especially for large networks
Security Solution for 802. 11 Networks: 802. 11 i Model Solution Requirements Mutual authentication Scalable key management for large networks Central authorization and accounting Support for extended authentication like smart cards Key Management Issues Need to dynamically manage keys to avoid manual reconfiguration difficulties especially for large networks
 Current Standard: 802. 11 i or WPA 2 802. 1 X for Authentication Based on EAP (Extensible Authentication Protocol) Port based authentication Access denied if port authentication fails CCMP (Counter Mode CBC-MAC Protocol) using AES for confidentiality, integrity and origin authentication Dynamic Key Management
Current Standard: 802. 11 i or WPA 2 802. 1 X for Authentication Based on EAP (Extensible Authentication Protocol) Port based authentication Access denied if port authentication fails CCMP (Counter Mode CBC-MAC Protocol) using AES for confidentiality, integrity and origin authentication Dynamic Key Management
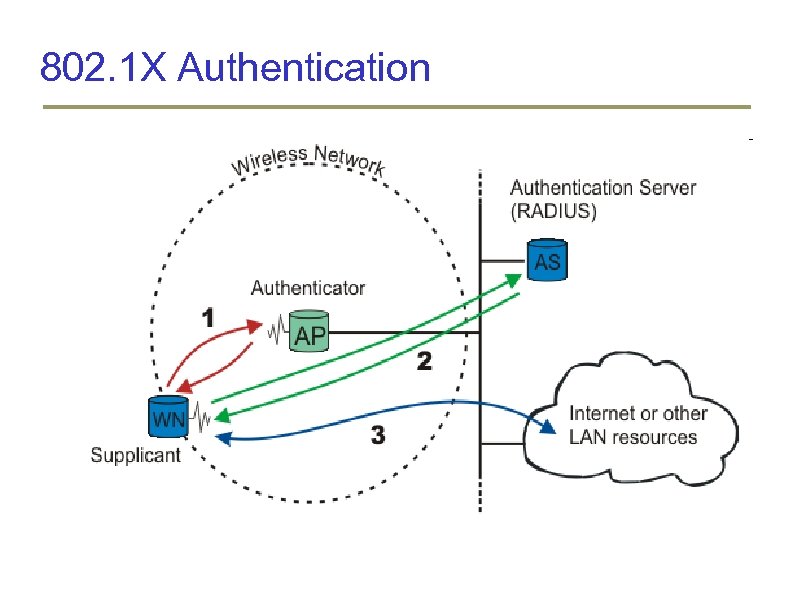 802. 1 X Authentication
802. 1 X Authentication
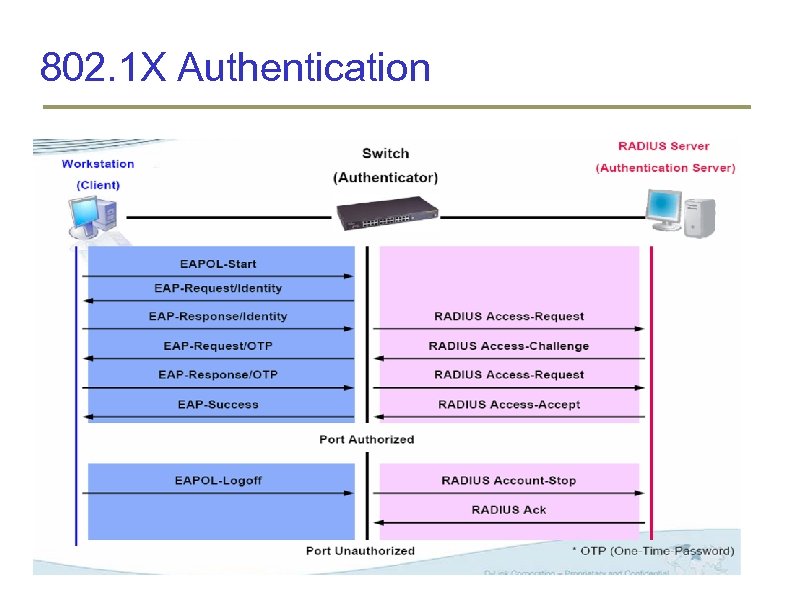 802. 1 X Authentication
802. 1 X Authentication
 802. 1 X Key Management LEAP use dynamically generated WEP keys to secure authentication data EAP-TLS –Station and Access Point use public-key certificates through a TLS tunnel Session key can be exchanged Mutual-authentication as both parties have digital certificates EAP-TTLS and PEAP –Only server-side certificate is needed Simplifies implementation where certificate management is difficult EAP-GSS where the authenticator is required to be in contact with a KDC
802. 1 X Key Management LEAP use dynamically generated WEP keys to secure authentication data EAP-TLS –Station and Access Point use public-key certificates through a TLS tunnel Session key can be exchanged Mutual-authentication as both parties have digital certificates EAP-TTLS and PEAP –Only server-side certificate is needed Simplifies implementation where certificate management is difficult EAP-GSS where the authenticator is required to be in contact with a KDC
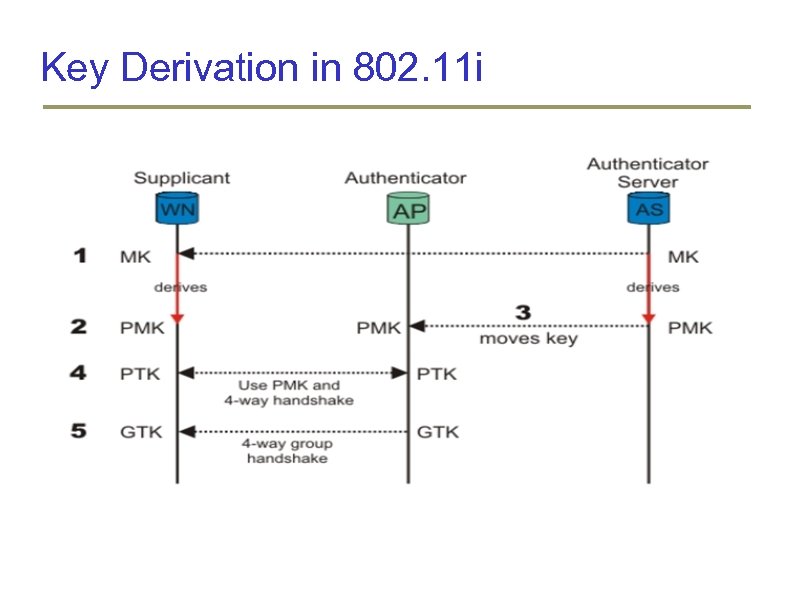 Key Derivation in 802. 11 i
Key Derivation in 802. 11 i
 Key Derivation in 802. 11 i At the end of EAPOL: Station and Server share a Master Key: MK (E. g. , Using EAPTLS) Both the Station and the AP derive a new key, called the Pairwise Master Key (PMK), from the Master Key. Radius Server moves PMK to AP A 4−way handshake between the station and the AP to derive, bind, and verify a Pairwise Transient Key (PTK). Key Encryption Key (KEK) is used to distributed the Group Transient Key (GTK) Key Confirmation Key (KCK), as the name implies, is used to prove the posession of the PMK Temporal Key 1 & 2 (TK 1/TK 2) are used for encryption. The KEK is used to send the Group Transient Key (GTK) from AP to the station The GTK is a shared key among all stations connected to the same authenticator (AP), to secure multicast/broadcast traffic
Key Derivation in 802. 11 i At the end of EAPOL: Station and Server share a Master Key: MK (E. g. , Using EAPTLS) Both the Station and the AP derive a new key, called the Pairwise Master Key (PMK), from the Master Key. Radius Server moves PMK to AP A 4−way handshake between the station and the AP to derive, bind, and verify a Pairwise Transient Key (PTK). Key Encryption Key (KEK) is used to distributed the Group Transient Key (GTK) Key Confirmation Key (KCK), as the name implies, is used to prove the posession of the PMK Temporal Key 1 & 2 (TK 1/TK 2) are used for encryption. The KEK is used to send the Group Transient Key (GTK) from AP to the station The GTK is a shared key among all stations connected to the same authenticator (AP), to secure multicast/broadcast traffic
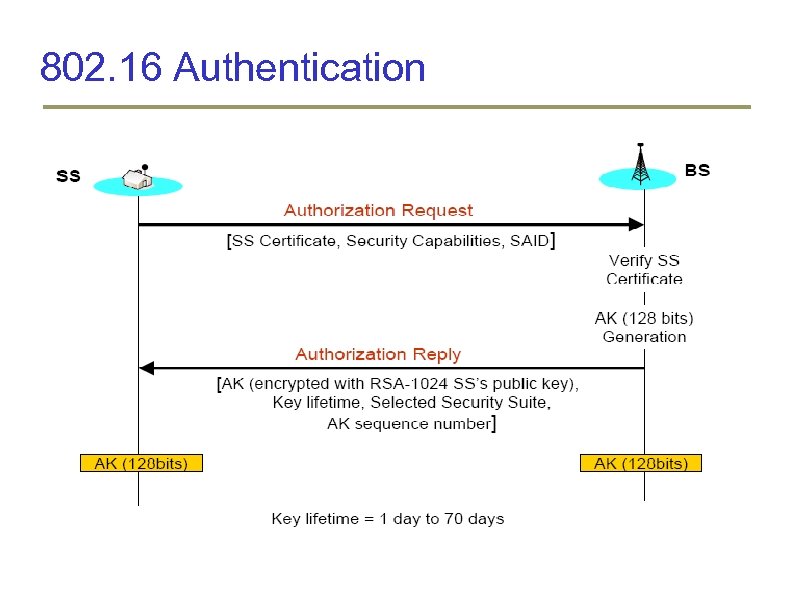 802. 16 Authentication
802. 16 Authentication
 Security Solutions for 802. 16 Networks 802. 16 or popularly Wi. MAX use X. 509 certificates for authentication Establish security association (SAID) Authentication Key (AK) exchange AK is encrypted using public key of SS Subscriber Station authentication using X. 509 certificate Authentication is completed when both SS and BS verify possession AK AK is used to exchange the TEK (Traffic encryption key) Base station generates TEK randomly and encrypts using KEK generated from AK 802. 16 uses AES in CCM mode for privacy Mutual authentication is possible through EAP-TLS etc (802. 16 e)
Security Solutions for 802. 16 Networks 802. 16 or popularly Wi. MAX use X. 509 certificates for authentication Establish security association (SAID) Authentication Key (AK) exchange AK is encrypted using public key of SS Subscriber Station authentication using X. 509 certificate Authentication is completed when both SS and BS verify possession AK AK is used to exchange the TEK (Traffic encryption key) Base station generates TEK randomly and encrypts using KEK generated from AK 802. 16 uses AES in CCM mode for privacy Mutual authentication is possible through EAP-TLS etc (802. 16 e)
 Security in Ad Hoc Mode Ad hoc networks cannot use RADIUS type authentication Problem: if RADIUS type authentication is used, every station will need to store every other station’s credentials Moreover, authentication will have to be using EAP-TLS which is computationally intensive Problem: mutual authentication is trouble some Other Security Requirements Cryptographic mechanisms for confidentiality Public-key management to prevent replacement of keys Key establishment for confidentiality Symmetric key management to protect from compromise Denial-of-service resistance in contention mechanisms at MAC layer
Security in Ad Hoc Mode Ad hoc networks cannot use RADIUS type authentication Problem: if RADIUS type authentication is used, every station will need to store every other station’s credentials Moreover, authentication will have to be using EAP-TLS which is computationally intensive Problem: mutual authentication is trouble some Other Security Requirements Cryptographic mechanisms for confidentiality Public-key management to prevent replacement of keys Key establishment for confidentiality Symmetric key management to protect from compromise Denial-of-service resistance in contention mechanisms at MAC layer
 Security in Ad Hoc Networks Security Mechanisms Pro-active : Prevents an attacker from launching an attack say by using cryptographic mechanisms Requirement is establishment of necessary cryptographic material E. g. , Routing Attacks Reactive : Relies on detection and mitigation of attacks Benign behaviour is defined and behaviour analysis is done to detect malicious behaviour E. g. , Packet Forwarding attacks
Security in Ad Hoc Networks Security Mechanisms Pro-active : Prevents an attacker from launching an attack say by using cryptographic mechanisms Requirement is establishment of necessary cryptographic material E. g. , Routing Attacks Reactive : Relies on detection and mitigation of attacks Benign behaviour is defined and behaviour analysis is done to detect malicious behaviour E. g. , Packet Forwarding attacks
 Key Management in Ad Hoc Networks- An Overview Key management – Manage a set of secure communication channels so that Avoid centralized infrastructure during sessions Minimal cryptographic/message overhead Use as few keys as possible Ensure “reasonable” security Two scenarios Broadcast security Peer-to-peer security
Key Management in Ad Hoc Networks- An Overview Key management – Manage a set of secure communication channels so that Avoid centralized infrastructure during sessions Minimal cryptographic/message overhead Use as few keys as possible Ensure “reasonable” security Two scenarios Broadcast security Peer-to-peer security
 Security Solutions – Broadcast Security Base station and a set of nodes. Base station sends updates to all the nodes using broadcast. N = number of satellite nodes Authentication and privacy is required
Security Solutions – Broadcast Security Base station and a set of nodes. Base station sends updates to all the nodes using broadcast. N = number of satellite nodes Authentication and privacy is required
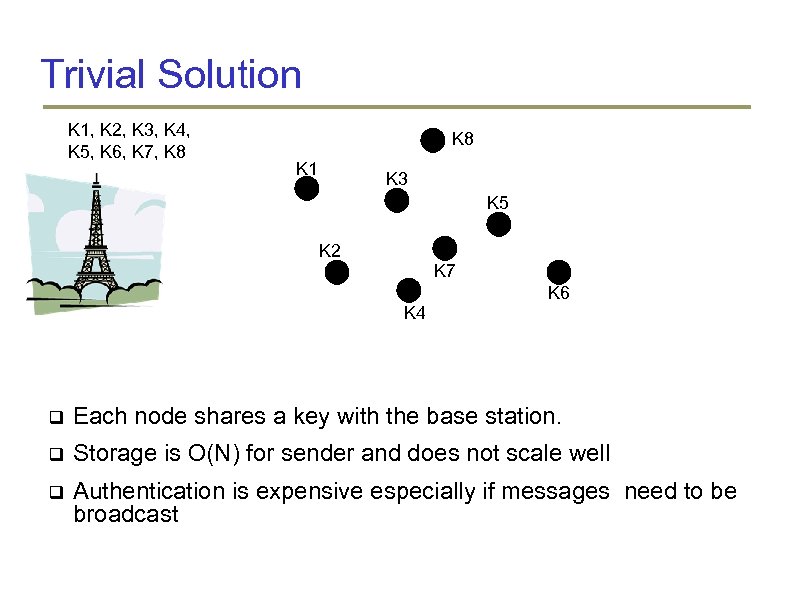 Trivial Solution K 1, K 2, K 3, K 4, K 5, K 6, K 7, K 8 K 1 K 3 K 5 K 2 K 7 K 4 K 6 Each node shares a key with the base station. Storage is O(N) for sender and does not scale well Authentication is expensive especially if messages need to be broadcast
Trivial Solution K 1, K 2, K 3, K 4, K 5, K 6, K 7, K 8 K 1 K 3 K 5 K 2 K 7 K 4 K 6 Each node shares a key with the base station. Storage is O(N) for sender and does not scale well Authentication is expensive especially if messages need to be broadcast
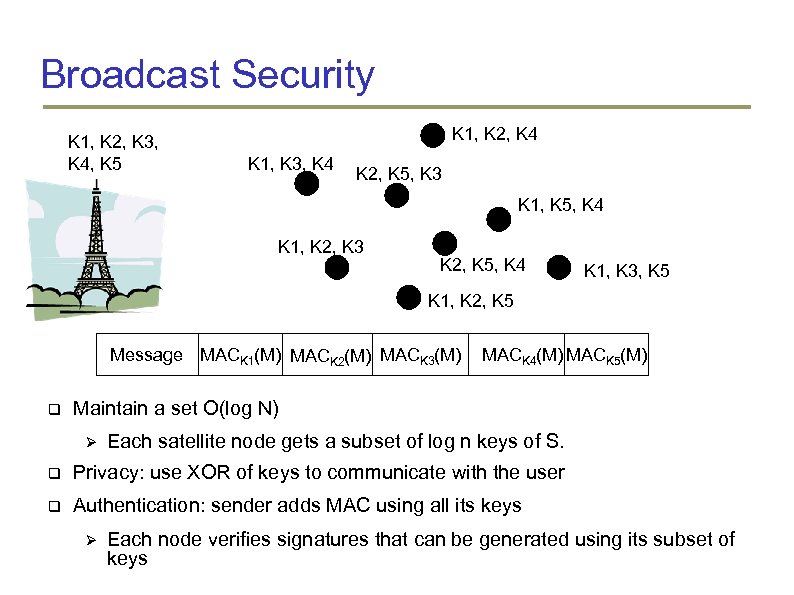 Broadcast Security K 1, K 2, K 3, K 4, K 5 K 1, K 2, K 4 K 1, K 3, K 4 K 2, K 5, K 3 K 1, K 5, K 4 K 1, K 2, K 3 K 2, K 5, K 4 K 1, K 3, K 5 K 1, K 2, K 5 Message MACK 1(M) MACK 2(M) MACK 3(M) MACK 4(M) MACK 5(M) Maintain a set O(log N) Each satellite node gets a subset of log n keys of S. Privacy: use XOR of keys to communicate with the user Authentication: sender adds MAC using all its keys Each node verifies signatures that can be generated using its subset of keys
Broadcast Security K 1, K 2, K 3, K 4, K 5 K 1, K 2, K 4 K 1, K 3, K 4 K 2, K 5, K 3 K 1, K 5, K 4 K 1, K 2, K 3 K 2, K 5, K 4 K 1, K 3, K 5 K 1, K 2, K 5 Message MACK 1(M) MACK 2(M) MACK 3(M) MACK 4(M) MACK 5(M) Maintain a set O(log N) Each satellite node gets a subset of log n keys of S. Privacy: use XOR of keys to communicate with the user Authentication: sender adds MAC using all its keys Each node verifies signatures that can be generated using its subset of keys
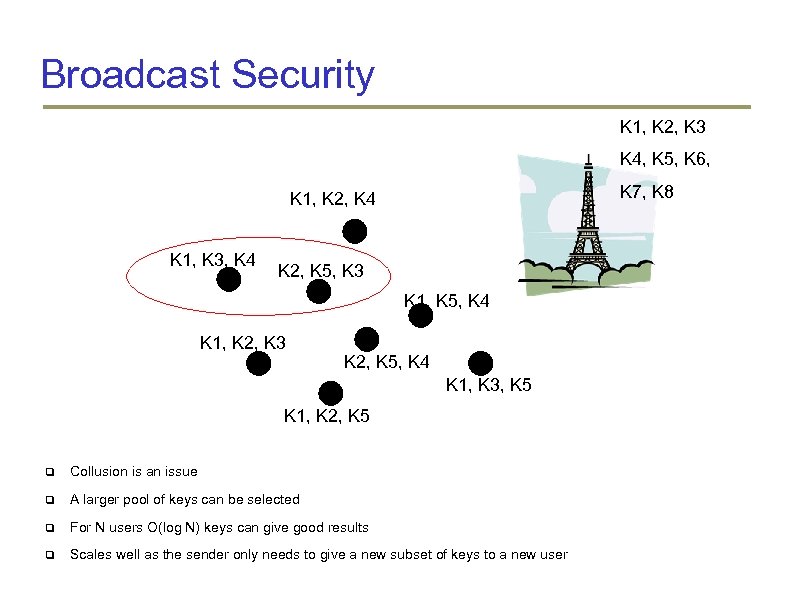 Broadcast Security K 1, K 2, K 3 K 4, K 5, K 6, K 7, K 8 K 1, K 2, K 4 K 1, K 3, K 4 K 2, K 5, K 3 K 1, K 5, K 4 K 1, K 2, K 3 K 2, K 5, K 4 K 1, K 3, K 5 K 1, K 2, K 5 Collusion is an issue A larger pool of keys can be selected For N users O(log N) keys can give good results Scales well as the sender only needs to give a new subset of keys to a new user
Broadcast Security K 1, K 2, K 3 K 4, K 5, K 6, K 7, K 8 K 1, K 2, K 4 K 1, K 3, K 4 K 2, K 5, K 3 K 1, K 5, K 4 K 1, K 2, K 3 K 2, K 5, K 4 K 1, K 3, K 5 K 1, K 2, K 5 Collusion is an issue A larger pool of keys can be selected For N users O(log N) keys can give good results Scales well as the sender only needs to give a new subset of keys to a new user
 Security Solutions Privacy in a Peer-to-peer situation Public-key cryptography can be of use but expensive Key distribution is a major hurdle given that communicating parties are not known in advance Anyone can communicate with any one Trivial Solution: one unique key per pair of users work Not scalable if new user gets added Expensive Revocation is little more tricky Scalable approach : key pre-distribution
Security Solutions Privacy in a Peer-to-peer situation Public-key cryptography can be of use but expensive Key distribution is a major hurdle given that communicating parties are not known in advance Anyone can communicate with any one Trivial Solution: one unique key per pair of users work Not scalable if new user gets added Expensive Revocation is little more tricky Scalable approach : key pre-distribution
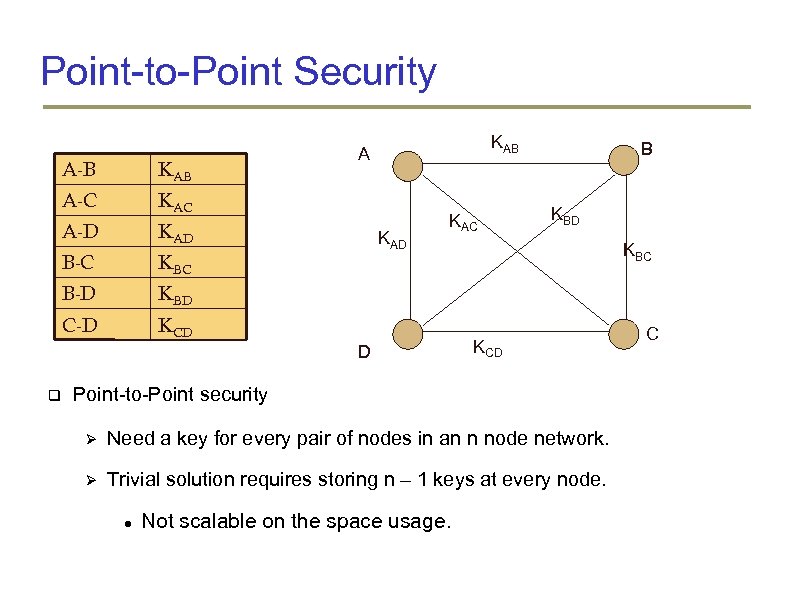 Point-to-Point Security A-B KAB A-C KAC A-D KAD B-C KBC B-D KCD B KBD C-D KAB A KAD KAC D KBD KBC KCD Point-to-Point security Need a key for every pair of nodes in an n node network. Trivial solution requires storing n – 1 keys at every node. Not scalable on the space usage. C
Point-to-Point Security A-B KAB A-C KAC A-D KAD B-C KBC B-D KCD B KBD C-D KAB A KAD KAC D KBD KBC KCD Point-to-Point security Need a key for every pair of nodes in an n node network. Trivial solution requires storing n – 1 keys at every node. Not scalable on the space usage. C
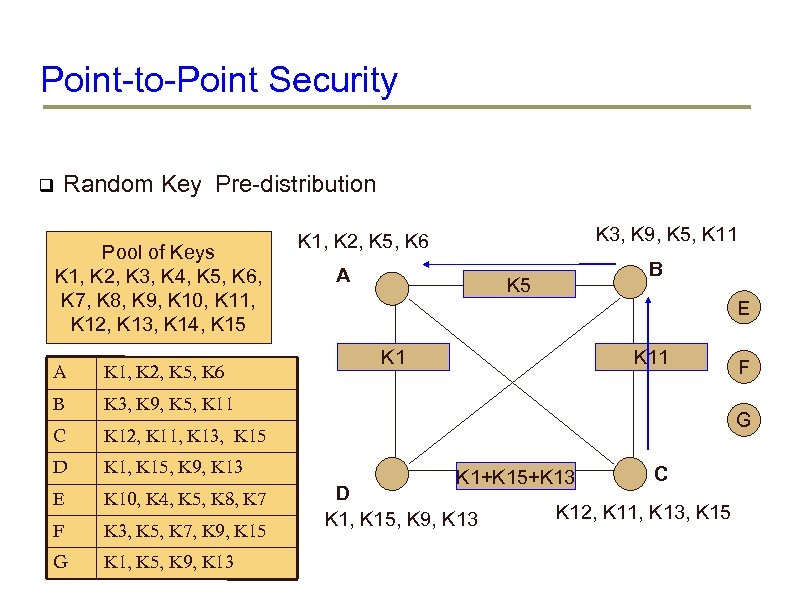 Point-to-Point Security Random Key Pre-distribution Pool of Keys K 1, K 2, K 3, K 4, K 5, K 6, K 7, K 8, K 9, K 10, K 11, K 12, K 13, K 14, K 15 A K 1, K 2, K 5, K 6 B K 1, K 15, K 9, K 13 E K 10, K 4, K 5, K 8, K 7 F K 3, K 5, K 7, K 9, K 15 G K 1, K 5, K 9, K 13 B K 5 E K 11 K 12, K 11, K 13, K 15 D A K 3, K 9, K 5, K 11 C K 3, K 9, K 5, K 11 K 1, K 2, K 5, K 6 F G K 1+K 15+K 13 D K 1, K 15, K 9, K 13 C K 12, K 11, K 13, K 15
Point-to-Point Security Random Key Pre-distribution Pool of Keys K 1, K 2, K 3, K 4, K 5, K 6, K 7, K 8, K 9, K 10, K 11, K 12, K 13, K 14, K 15 A K 1, K 2, K 5, K 6 B K 1, K 15, K 9, K 13 E K 10, K 4, K 5, K 8, K 7 F K 3, K 5, K 7, K 9, K 15 G K 1, K 5, K 9, K 13 B K 5 E K 11 K 12, K 11, K 13, K 15 D A K 3, K 9, K 5, K 11 C K 3, K 9, K 5, K 11 K 1, K 2, K 5, K 6 F G K 1+K 15+K 13 D K 1, K 15, K 9, K 13 C K 12, K 11, K 13, K 15
 Point-to-Point Security Issues in Random Key Pre-Distribution May need Intermediaries for key establishment Storage is High Experimental: 250 keys out of 10, 000 keys may be necessary An active adversary is dangerous Collusion effect is unknown due to the randomness of key distribution Might require privacy mechanisms to hide key sharing patterns Revocation issues exist Probabilistic arguments for size of key storage and connectivity possible Practice proves otherwise, especially for sparse graphs
Point-to-Point Security Issues in Random Key Pre-Distribution May need Intermediaries for key establishment Storage is High Experimental: 250 keys out of 10, 000 keys may be necessary An active adversary is dangerous Collusion effect is unknown due to the randomness of key distribution Might require privacy mechanisms to hide key sharing patterns Revocation issues exist Probabilistic arguments for size of key storage and connectivity possible Practice proves otherwise, especially for sparse graphs
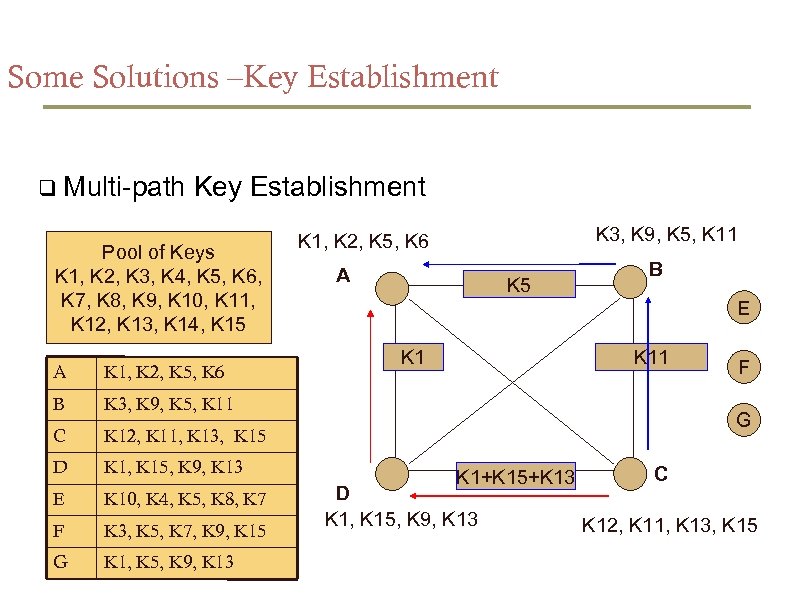 Some Solutions –Key Establishment Multi-path Key Establishment Pool of Keys K 1, K 2, K 3, K 4, K 5, K 6, K 7, K 8, K 9, K 10, K 11, K 12, K 13, K 14, K 15 A K 1, K 2, K 5, K 6 B K 1, K 15, K 9, K 13 E K 10, K 4, K 5, K 8, K 7 F K 3, K 5, K 7, K 9, K 15 G K 1, K 5, K 9, K 13 K 5 B E K 11 K 12, K 11, K 13, K 15 D A K 3, K 9, K 5, K 11 C K 3, K 9, K 5, K 11 K 1, K 2, K 5, K 6 F G K 1+K 15+K 13 D K 1, K 15, K 9, K 13 C K 12, K 11, K 13, K 15
Some Solutions –Key Establishment Multi-path Key Establishment Pool of Keys K 1, K 2, K 3, K 4, K 5, K 6, K 7, K 8, K 9, K 10, K 11, K 12, K 13, K 14, K 15 A K 1, K 2, K 5, K 6 B K 1, K 15, K 9, K 13 E K 10, K 4, K 5, K 8, K 7 F K 3, K 5, K 7, K 9, K 15 G K 1, K 5, K 9, K 13 K 5 B E K 11 K 12, K 11, K 13, K 15 D A K 3, K 9, K 5, K 11 C K 3, K 9, K 5, K 11 K 1, K 2, K 5, K 6 F G K 1+K 15+K 13 D K 1, K 15, K 9, K 13 C K 12, K 11, K 13, K 15
![Some Solutions –Key Establishment Deterministic [0, 0] Solution –Square Grid [Ref. 4] [0, 1] Some Solutions –Key Establishment Deterministic [0, 0] Solution –Square Grid [Ref. 4] [0, 1]](https://present5.com/presentation/40bf73a26ca47436b3c51e63802f25cc/image-70.jpg) Some Solutions –Key Establishment Deterministic [0, 0] Solution –Square Grid [Ref. 4] [0, 1] [0, 2] [1, 0] [1, 1] [1, 2] [2, 0] [2, 1] [2, 2] [3, 0] [3, 1] [3, 2] [0, 3] [1, 3] [2, 3] [3, 3] User Placement
Some Solutions –Key Establishment Deterministic [0, 0] Solution –Square Grid [Ref. 4] [0, 1] [0, 2] [1, 0] [1, 1] [1, 2] [2, 0] [2, 1] [2, 2] [3, 0] [3, 1] [3, 2] [0, 3] [1, 3] [2, 3] [3, 3] User Placement
![Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] Kg(0, 0) [0, 1] Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] Kg(0, 0) [0, 1]](https://present5.com/presentation/40bf73a26ca47436b3c51e63802f25cc/image-71.jpg) Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] Kg(0, 0) [0, 1] [1, 0] [0, 2] [0, 3] [1, 2] Grid Secrets [2, 0] [3, 0] [2, 1] [2, 2] Kg(2, 2) [3, 2] [2, 3]
Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] Kg(0, 0) [0, 1] [1, 0] [0, 2] [0, 3] [1, 2] Grid Secrets [2, 0] [3, 0] [2, 1] [2, 2] Kg(2, 2) [3, 2] [2, 3]
![Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [1, 0] [2, 0] Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [1, 0] [2, 0]](https://present5.com/presentation/40bf73a26ca47436b3c51e63802f25cc/image-72.jpg) Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [1, 0] [2, 0] [3, 0] [0, 1] [0, 2] [0, 3] Direct Secrets
Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [1, 0] [2, 0] [3, 0] [0, 1] [0, 2] [0, 3] Direct Secrets
![Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2] Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2]](https://present5.com/presentation/40bf73a26ca47436b3c51e63802f25cc/image-73.jpg) Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2] [0, 3] Communication [1, 0] [2, 0] [3, 0] [1, 2] [2, 1] [2, 2] [3, 2] Along Same Row/Column [2, 3]
Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2] [0, 3] Communication [1, 0] [2, 0] [3, 0] [1, 2] [2, 1] [2, 2] [3, 2] Along Same Row/Column [2, 3]
![Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2] Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2]](https://present5.com/presentation/40bf73a26ca47436b3c51e63802f25cc/image-74.jpg) Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2] [0, 3] Kg(0, 2) [1, 0] Kg(2, 0) [2, 0] [3, 0] Communication Among Users of Different Rows/Columns [1, 2] [2, 1] [2, 2] [3, 2] [2, 3]
Some Solutions –Key Establishment Deterministic Solution –Square Grid [0, 0] [0, 1] [0, 2] [0, 3] Kg(0, 2) [1, 0] Kg(2, 0) [2, 0] [3, 0] Communication Among Users of Different Rows/Columns [1, 2] [2, 1] [2, 2] [3, 2] [2, 3]
 Some Solutions –Key Establishment Square Grid Features and Issues Mobility has no effect on key establishment –always guaranteed by design Failure tolerant –failure of links hardly matters Storage is high, but comparable to random KPS Collusion resistance is slightly weak Two users are sufficient to compromise session key Scalability is weak as the grid size is fixed before hand Optimizations possible, by choosing higher grid size and allowing for some additional users
Some Solutions –Key Establishment Square Grid Features and Issues Mobility has no effect on key establishment –always guaranteed by design Failure tolerant –failure of links hardly matters Storage is high, but comparable to random KPS Collusion resistance is slightly weak Two users are sufficient to compromise session key Scalability is weak as the grid size is fixed before hand Optimizations possible, by choosing higher grid size and allowing for some additional users
 Security Solutions Can reduce storage further by considering a k – dimensional grid User belongs to multiple grids with lower dimension: n 1/k number of keys stored per node decreases to kn 1/k. At k = log n, this reduces to log n. But collusion resistance decreases with increasing k Best case storage is around: 12 log 2 n Lower values are possible but multiplication constant is higher
Security Solutions Can reduce storage further by considering a k – dimensional grid User belongs to multiple grids with lower dimension: n 1/k number of keys stored per node decreases to kn 1/k. At k = log n, this reduces to log n. But collusion resistance decreases with increasing k Best case storage is around: 12 log 2 n Lower values are possible but multiplication constant is higher
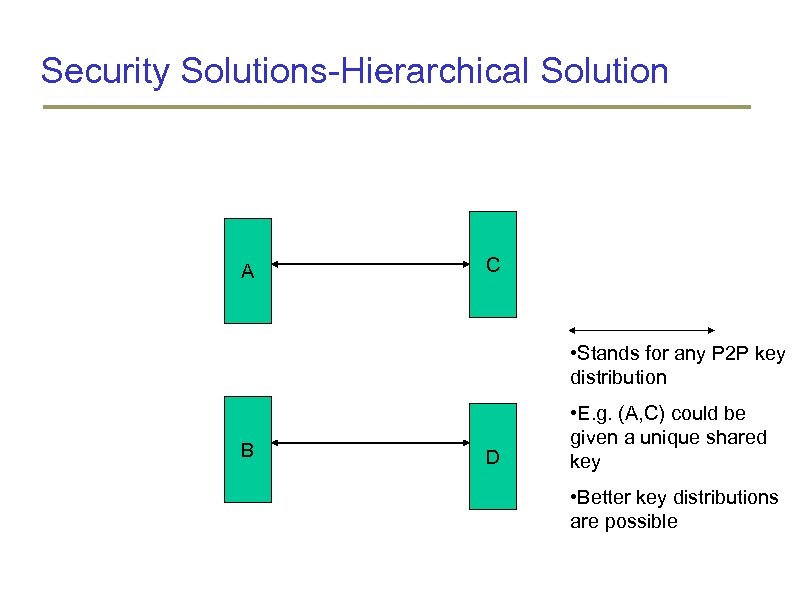 Security Solutions-Hierarchical Solution A C • Stands for any P 2 P key distribution B D • E. g. (A, C) could be given a unique shared key • Better key distributions are possible
Security Solutions-Hierarchical Solution A C • Stands for any P 2 P key distribution B D • E. g. (A, C) could be given a unique shared key • Better key distributions are possible
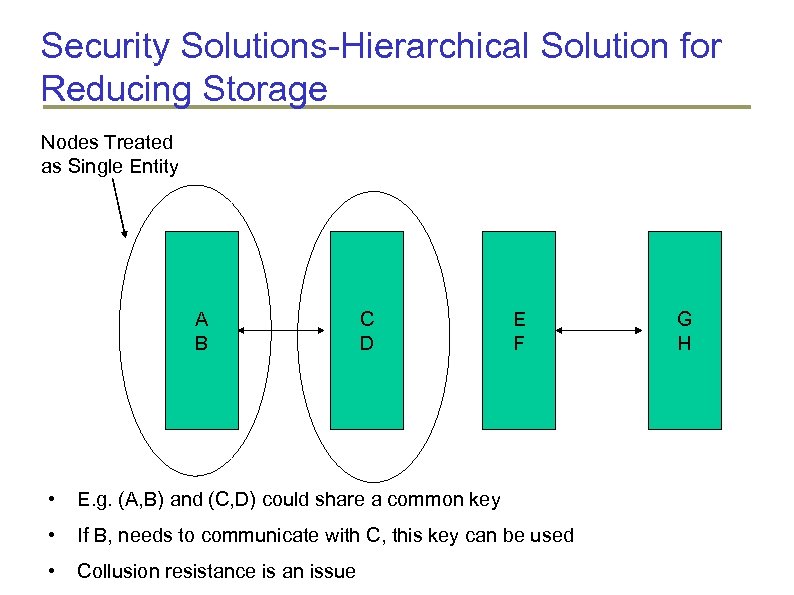 Security Solutions-Hierarchical Solution for Reducing Storage Nodes Treated as Single Entity A B C D E F • E. g. (A, B) and (C, D) could share a common key • If B, needs to communicate with C, this key can be used • Collusion resistance is an issue G H
Security Solutions-Hierarchical Solution for Reducing Storage Nodes Treated as Single Entity A B C D E F • E. g. (A, B) and (C, D) could share a common key • If B, needs to communicate with C, this key can be used • Collusion resistance is an issue G H
 Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
Outline Introduction Models of Wireless Networks Various Layers and Current Solutions for each Layer Security Issues and Threats at each Layer Security Solutions Open Problems
 Open Problems Problem 1: Secure Admission Control For fixed infrastructure networks, how to decide admitting a new node into the network? EAP-TLS, EAP-TTLS are expensive in terms of computation and do not work well in ad hoc mode Access points should be able to handle more decisions to enable easy roaming Need for a scalable but practical solution for admission control especially for roaming accessibility If key management is used dynamics and storage become issues
Open Problems Problem 1: Secure Admission Control For fixed infrastructure networks, how to decide admitting a new node into the network? EAP-TLS, EAP-TTLS are expensive in terms of computation and do not work well in ad hoc mode Access points should be able to handle more decisions to enable easy roaming Need for a scalable but practical solution for admission control especially for roaming accessibility If key management is used dynamics and storage become issues
 Open Problems Problem 2 : Application Layer Security for fixed infrastructure networks Equivalent notions of wired networks. Require Light-weight sand boxing mechanisms Privacy-preserving light-weight content filtering techniques Existing solutions: J 2 ME KVM, Download. Fun, Qual. Comm BREW
Open Problems Problem 2 : Application Layer Security for fixed infrastructure networks Equivalent notions of wired networks. Require Light-weight sand boxing mechanisms Privacy-preserving light-weight content filtering techniques Existing solutions: J 2 ME KVM, Download. Fun, Qual. Comm BREW
 Open Problems Problem 3: Real-time Cell Communication Security Key management solutions may not work due to realtime voice data Hacking/tapping cell phones is possible depending on the encoding scheme used
Open Problems Problem 3: Real-time Cell Communication Security Key management solutions may not work due to realtime voice data Hacking/tapping cell phones is possible depending on the encoding scheme used
 Open Problems 4 Certificate mechanisms for nodes Certificates in wired networks are well understood. Users typically have better user interfaces e. g. , PC Monitor, allowing them to examine things like certificates Certificate verification/validation is tolerable on desktops and even laptops.
Open Problems 4 Certificate mechanisms for nodes Certificates in wired networks are well understood. Users typically have better user interfaces e. g. , PC Monitor, allowing them to examine things like certificates Certificate verification/validation is tolerable on desktops and even laptops.
 Open Problem 4 Problem: Not the same for mobile users say, cell phones Integrating such features into a cell-phone is difficult Expensive to verify certificates due long certification path. Solution more difficult for devices with no display or limited display or regular monitoring of the device, such as sensors. Need a different way of handling certificates.
Open Problem 4 Problem: Not the same for mobile users say, cell phones Integrating such features into a cell-phone is difficult Expensive to verify certificates due long certification path. Solution more difficult for devices with no display or limited display or regular monitoring of the device, such as sensors. Need a different way of handling certificates.
 Conclusions Situations are more complex in wireless networks, even with infrastructural support. Threats exist at various layers of operation. Present solutions to address these threats are not scalable or not strong enough. Simple key management solutions can help. But not always. Still, lots of interesting and open issues to be solved.
Conclusions Situations are more complex in wireless networks, even with infrastructural support. Threats exist at various layers of operation. Present solutions to address these threats are not scalable or not strong enough. Simple key management solutions can help. But not always. Still, lots of interesting and open issues to be solved.
 Thank You!
Thank You!
 References Jean-Pierre Hubaux, Levente, Buttyan and Srdan Capkun “The Quest for Security in Mobile Ad Hoc Networks”, ACM Mobi. HOC 2001 Laurent Eschenauer and Virgil D. Gligor “A Key Management Scheme for Distributed Sensor Networks” ACM CCS 2002 Haowen Chan, Adrian Perrig and Dawn Song “Random Key Predistribution Schemes for Sensor Networks” IEEE Symposium on Security and Privacy 2003 S. S. Kulkarni, M. G. Gouda and A. Arora “Secret Instantiation in Ad Hoc Networks” Special Issue of Elsevier Journal of Computer Communication on Dependable Wireless Sensor Networks, 2006 Amitanand S. Aiyer, Lorenzo Alvisi, Mohamed G. Gouda “Key Grids: A Protocol Family for Assigning Symmetric Keys” IEEE International Conference on Network Protocols, 2006 B. Bruhadeshwar and Sandeep Kulkarni “An Optimal Symmetric Secret Distribution for Secure Communication” Michigan State University Technical Report 2008 MSU -TR-08 -196
References Jean-Pierre Hubaux, Levente, Buttyan and Srdan Capkun “The Quest for Security in Mobile Ad Hoc Networks”, ACM Mobi. HOC 2001 Laurent Eschenauer and Virgil D. Gligor “A Key Management Scheme for Distributed Sensor Networks” ACM CCS 2002 Haowen Chan, Adrian Perrig and Dawn Song “Random Key Predistribution Schemes for Sensor Networks” IEEE Symposium on Security and Privacy 2003 S. S. Kulkarni, M. G. Gouda and A. Arora “Secret Instantiation in Ad Hoc Networks” Special Issue of Elsevier Journal of Computer Communication on Dependable Wireless Sensor Networks, 2006 Amitanand S. Aiyer, Lorenzo Alvisi, Mohamed G. Gouda “Key Grids: A Protocol Family for Assigning Symmetric Keys” IEEE International Conference on Network Protocols, 2006 B. Bruhadeshwar and Sandeep Kulkarni “An Optimal Symmetric Secret Distribution for Secure Communication” Michigan State University Technical Report 2008 MSU -TR-08 -196
 References Bezawada Bruhadeshwar, Kishore Kothapalli: A Family of Collusion Resistant Symmetric Key Protocols for Authentication. ICDCN 2008: 387 -392 Kishore Kothapalli, Christian Scheideler, Melih Onus, Andréa W. Richa: Constant density spanners for wireless ad-hoc networks. SPAA 2005: 116 -125 Edmund L. Wong, Praveen Balasubramanian, Lorenzo Alvisi, Mohamed G. Gouda, Vitaly Shmatikov: Truth in advertising: lightweight verification of route integrity. PODC 2007: 147 -156 Ran Canetti, Adrian Perrig, Dawn Song and Doug Tygar “The TESLA Broadcast Authenitcation Protocol” RSA Cryptobytes 2002 Chalermek Intanagonwiwat, Ramesh Govindan, Deborah Estrin, John S. Heidemann, Fabio Silva: Directed diffusion for wireless sensor networking. IEEE/ACM Trans. Netw. 11(1): 216 (2003) Arshad Jhumka, Sandeep S. Kulkarni: On the Design of Mobility-Tolerant TDMA-Based Media Access Control (MAC) Protocol for Mobile Sensor Networks. ICDCIT 2007: General: Wikipedia, Wi. Fi Forum, Wi. MAX Forum, IETF Website
References Bezawada Bruhadeshwar, Kishore Kothapalli: A Family of Collusion Resistant Symmetric Key Protocols for Authentication. ICDCN 2008: 387 -392 Kishore Kothapalli, Christian Scheideler, Melih Onus, Andréa W. Richa: Constant density spanners for wireless ad-hoc networks. SPAA 2005: 116 -125 Edmund L. Wong, Praveen Balasubramanian, Lorenzo Alvisi, Mohamed G. Gouda, Vitaly Shmatikov: Truth in advertising: lightweight verification of route integrity. PODC 2007: 147 -156 Ran Canetti, Adrian Perrig, Dawn Song and Doug Tygar “The TESLA Broadcast Authenitcation Protocol” RSA Cryptobytes 2002 Chalermek Intanagonwiwat, Ramesh Govindan, Deborah Estrin, John S. Heidemann, Fabio Silva: Directed diffusion for wireless sensor networking. IEEE/ACM Trans. Netw. 11(1): 216 (2003) Arshad Jhumka, Sandeep S. Kulkarni: On the Design of Mobility-Tolerant TDMA-Based Media Access Control (MAC) Protocol for Mobile Sensor Networks. ICDCIT 2007: General: Wikipedia, Wi. Fi Forum, Wi. MAX Forum, IETF Website


