f32638372f62476f2e8adf91815c1ddc.ppt
- Количество слайдов: 13
 Security in Wireless Networks: The Flexi. NET Approach G. Kostopoulos 1, C. Kavadias 2, C. Chrysoulas 3, S. Denazis 4, O. Koufopavlou 5 Electrical and Computer Engineering Department, University of Patras, GREECE {gkostop 1, cchrys 3, sdena 4, odysseas 5}@ee. upatras. gr TELETEL S. A, 124, Kifisias Avenue, Athens, GREECE, E-mail: C. Kavadias@TELETEL. gr 2 COMMUNICATION SYSTEMS, NETWORKS AND DIGITAL SIGNAL PROCESSING Fifth International Symposium 19 -21 July, 2006, Patras, Greece
Security in Wireless Networks: The Flexi. NET Approach G. Kostopoulos 1, C. Kavadias 2, C. Chrysoulas 3, S. Denazis 4, O. Koufopavlou 5 Electrical and Computer Engineering Department, University of Patras, GREECE {gkostop 1, cchrys 3, sdena 4, odysseas 5}@ee. upatras. gr TELETEL S. A, 124, Kifisias Avenue, Athens, GREECE, E-mail: C. Kavadias@TELETEL. gr 2 COMMUNICATION SYSTEMS, NETWORKS AND DIGITAL SIGNAL PROCESSING Fifth International Symposium 19 -21 July, 2006, Patras, Greece
 Outline l l l Flexi. NET Architecture Security Overview User Case Scenario AAA Proxy Module Authentication Scenarios 21/07/2006, Patras, Greece CSNDSP 2006
Outline l l l Flexi. NET Architecture Security Overview User Case Scenario AAA Proxy Module Authentication Scenarios 21/07/2006, Patras, Greece CSNDSP 2006
 Flexi. NET Architecture l l l The Flexi. NET network architecture consists mainly of node instances, communication buses and data repositories. The Flexi. NET UMTS Access Node (FUAN) provides to the Flexi. NET interfaces, functions such as switching/routing control, access to applications data & service logic, etc. The FUAN complements existing access nodes (RNC, BSC) of UMTS networks. The Flexi. NET WLAN Access Node (FWAN) acts as both a services access gateway (user authentication, service authorization, service discovery, etc. ), and connection gateway between WLAN infrastructures and the Flexi. NET WAN. The Flexi. NET Data Gateway Node (DGWN) acts as the Gateway between the generic SAN infrastructures and the Flexi. NET Network Architecture allowing for the realisation of the data-centric Flexi. NET services approach. The Generic Applications Interface Bus is the central and most important mechanism for the interconnection of the Flexi. NET instances. The Flexi. NET Applications Server (FLAS) is the physical entity, which hosts the logic of the applications that the Flexi. NET network architecture provides. 21/07/2006, Patras, Greece CSNDSP 2006
Flexi. NET Architecture l l l The Flexi. NET network architecture consists mainly of node instances, communication buses and data repositories. The Flexi. NET UMTS Access Node (FUAN) provides to the Flexi. NET interfaces, functions such as switching/routing control, access to applications data & service logic, etc. The FUAN complements existing access nodes (RNC, BSC) of UMTS networks. The Flexi. NET WLAN Access Node (FWAN) acts as both a services access gateway (user authentication, service authorization, service discovery, etc. ), and connection gateway between WLAN infrastructures and the Flexi. NET WAN. The Flexi. NET Data Gateway Node (DGWN) acts as the Gateway between the generic SAN infrastructures and the Flexi. NET Network Architecture allowing for the realisation of the data-centric Flexi. NET services approach. The Generic Applications Interface Bus is the central and most important mechanism for the interconnection of the Flexi. NET instances. The Flexi. NET Applications Server (FLAS) is the physical entity, which hosts the logic of the applications that the Flexi. NET network architecture provides. 21/07/2006, Patras, Greece CSNDSP 2006
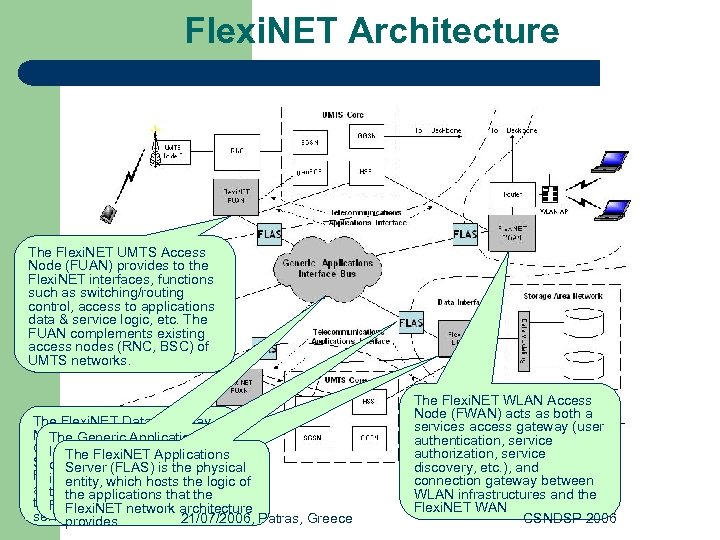 Flexi. NET Architecture The Flexi. NET UMTS Access Node (FUAN) provides to the Flexi. NET interfaces, functions such as switching/routing control, access to applications data & service logic, etc. The FUAN complements existing access nodes (RNC, BSC) of UMTS networks. The Flexi. NET Data Gateway Node (DGWN) acts as the The Generic Applications Gateway between the generic Interface Bus is Applications The Flexi. NET SAN Server (FLAS) and the infrastructures central and most is the physical Flexi. NET Network hosts the logic of importantwhich Architecture entity, mechanism for allowing for the realisationthe interconnectionthat of the applications of the data-centricnetwork architecture Flexi. NET instances Flexi. NET services approach 21/07/2006, Patras, Greece provides The Flexi. NET WLAN Access Node (FWAN) acts as both a services access gateway (user authentication, service authorization, service discovery, etc. ), and connection gateway between WLAN infrastructures and the Flexi. NET WAN CSNDSP 2006
Flexi. NET Architecture The Flexi. NET UMTS Access Node (FUAN) provides to the Flexi. NET interfaces, functions such as switching/routing control, access to applications data & service logic, etc. The FUAN complements existing access nodes (RNC, BSC) of UMTS networks. The Flexi. NET Data Gateway Node (DGWN) acts as the The Generic Applications Gateway between the generic Interface Bus is Applications The Flexi. NET SAN Server (FLAS) and the infrastructures central and most is the physical Flexi. NET Network hosts the logic of importantwhich Architecture entity, mechanism for allowing for the realisationthe interconnectionthat of the applications of the data-centricnetwork architecture Flexi. NET instances Flexi. NET services approach 21/07/2006, Patras, Greece provides The Flexi. NET WLAN Access Node (FWAN) acts as both a services access gateway (user authentication, service authorization, service discovery, etc. ), and connection gateway between WLAN infrastructures and the Flexi. NET WAN CSNDSP 2006
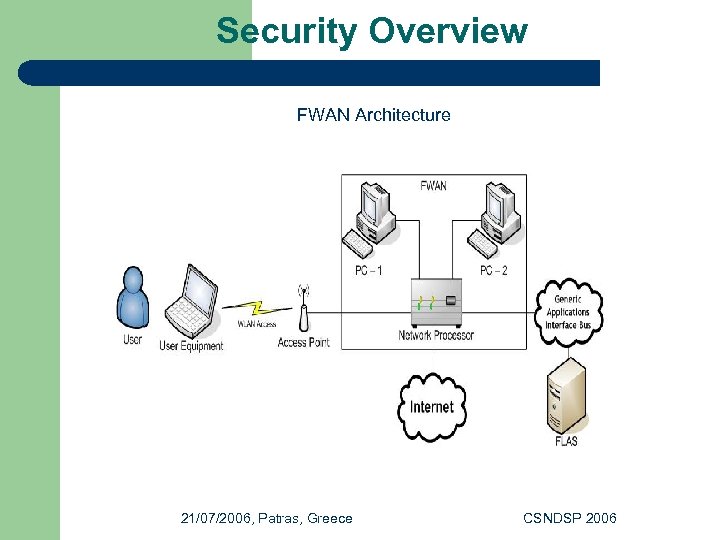 Security Overview FWAN Architecture 21/07/2006, Patras, Greece CSNDSP 2006
Security Overview FWAN Architecture 21/07/2006, Patras, Greece CSNDSP 2006
 Security Overview l l l l The necessary entities that are responsible for the security in Flexi. NET’s Wireless LAN node are the FWAN module and the FLAS Server. A user will access the FWAN through an access point using either a laptop or a mobile phone. The FWAN is responsible for authenticating native and roaming users through the FLAS using the AAA proxy module. The Dynamic Service Deployment module must be deployed on the FWAN before boot-up. The bootstrap process is responsible for booting up the FWAN with the AAA proxy module. FLAS is the physical entity, which hosts the logic of the services that the Flexi. NET network architecture provides. These services are called from other entities remotely and executed locally. FLAS provides services either to the other Flexi. NET node instances or to Third Party applications servers. These services are exposed as Web Services via the Generic Applications Interface Bus 21/07/2006, Patras, Greece CSNDSP 2006
Security Overview l l l l The necessary entities that are responsible for the security in Flexi. NET’s Wireless LAN node are the FWAN module and the FLAS Server. A user will access the FWAN through an access point using either a laptop or a mobile phone. The FWAN is responsible for authenticating native and roaming users through the FLAS using the AAA proxy module. The Dynamic Service Deployment module must be deployed on the FWAN before boot-up. The bootstrap process is responsible for booting up the FWAN with the AAA proxy module. FLAS is the physical entity, which hosts the logic of the services that the Flexi. NET network architecture provides. These services are called from other entities remotely and executed locally. FLAS provides services either to the other Flexi. NET node instances or to Third Party applications servers. These services are exposed as Web Services via the Generic Applications Interface Bus 21/07/2006, Patras, Greece CSNDSP 2006
 User Case Scenario l l l The Flexi. NET Wireless Access Node supports two different kinds of authentication scenarios. The Login/Password scenario and the SIM based authentication scenario. Both scenarios have been deployed upon EAP and RADIUS protocols. The entities that are involved in the Authentication Scenarios are the following: – – Client Authenticator AAA Proxy FLAS 21/07/2006, Patras, Greece CSNDSP 2006
User Case Scenario l l l The Flexi. NET Wireless Access Node supports two different kinds of authentication scenarios. The Login/Password scenario and the SIM based authentication scenario. Both scenarios have been deployed upon EAP and RADIUS protocols. The entities that are involved in the Authentication Scenarios are the following: – – Client Authenticator AAA Proxy FLAS 21/07/2006, Patras, Greece CSNDSP 2006
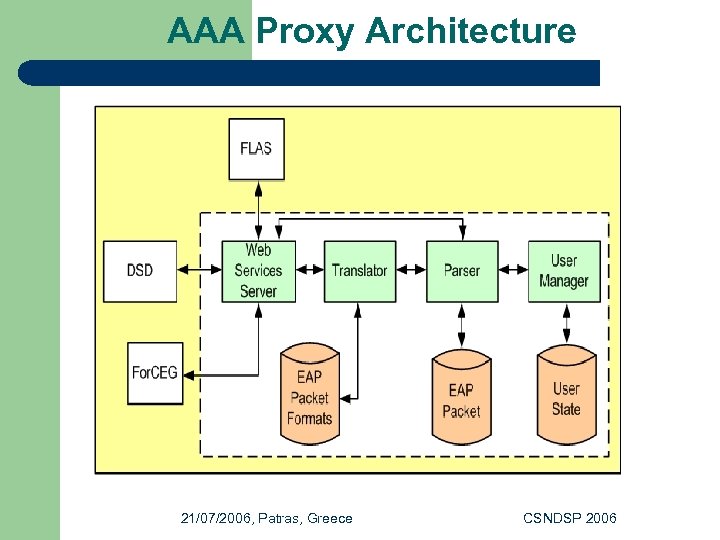 AAA Proxy Architecture 21/07/2006, Patras, Greece CSNDSP 2006
AAA Proxy Architecture 21/07/2006, Patras, Greece CSNDSP 2006
 AAA Proxy Module l The AAA Proxy is comprised of the following components: – – l l the Web Services Server, the Translator, the Parser and the User Manager. The Data Holders which the AAA Module includes are the EAP Packet Formats holder, the EAP Packet holder and the User State holder The AAA proxy module: – – forwards the authentication packets to the FLAS Server, encapsulates the EAP packets into XML messages that are passed over Web services and vice versa, to authenticate and authorize the user 21/07/2006, Patras, Greece CSNDSP 2006
AAA Proxy Module l The AAA Proxy is comprised of the following components: – – l l the Web Services Server, the Translator, the Parser and the User Manager. The Data Holders which the AAA Module includes are the EAP Packet Formats holder, the EAP Packet holder and the User State holder The AAA proxy module: – – forwards the authentication packets to the FLAS Server, encapsulates the EAP packets into XML messages that are passed over Web services and vice versa, to authenticate and authorize the user 21/07/2006, Patras, Greece CSNDSP 2006
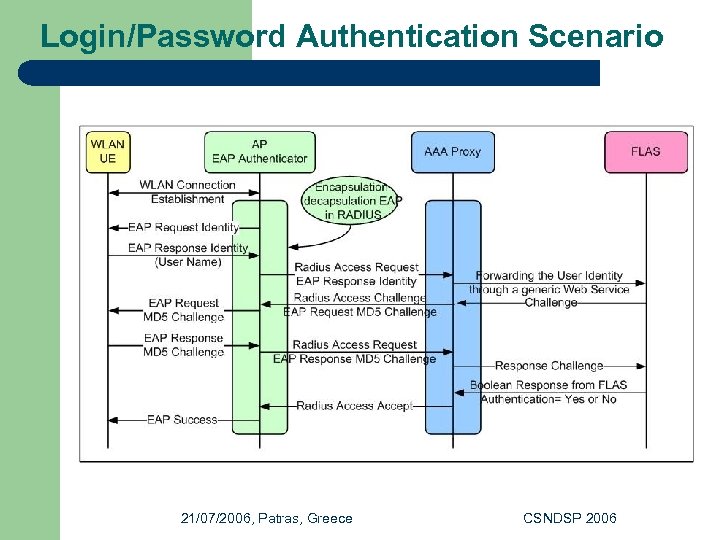 Login/Password Authentication Scenario 21/07/2006, Patras, Greece CSNDSP 2006
Login/Password Authentication Scenario 21/07/2006, Patras, Greece CSNDSP 2006
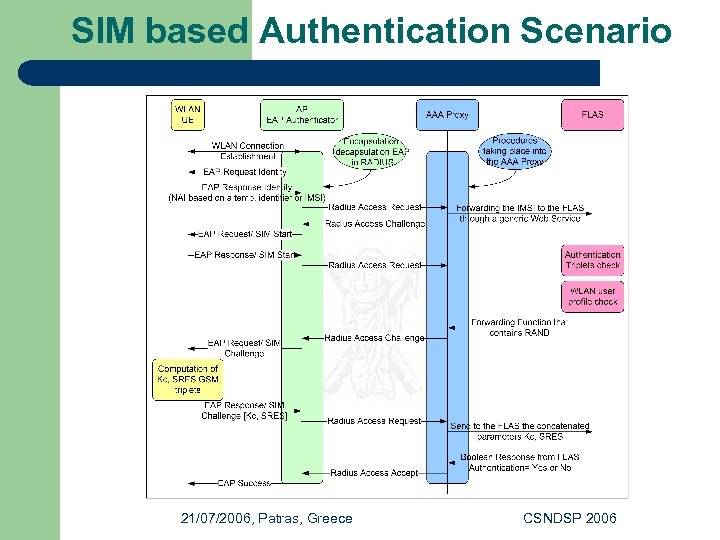 SIM based Authentication Scenario 21/07/2006, Patras, Greece CSNDSP 2006
SIM based Authentication Scenario 21/07/2006, Patras, Greece CSNDSP 2006
 Conclusions l l l In this paper we present an alternative architecture providing authentication using Web Services for the exchange of authentication material. Using the proposed method we achieve to authenticate the user independently of its type. The user does not have to choose the authentication method. The system by itself, through the AAA Proxy, controls the security mechanism that has to be used for each user using the same infrastructure for each case. 21/07/2006, Patras, Greece CSNDSP 2006
Conclusions l l l In this paper we present an alternative architecture providing authentication using Web Services for the exchange of authentication material. Using the proposed method we achieve to authenticate the user independently of its type. The user does not have to choose the authentication method. The system by itself, through the AAA Proxy, controls the security mechanism that has to be used for each user using the same infrastructure for each case. 21/07/2006, Patras, Greece CSNDSP 2006
 Thank You for Your Attention ! 21/07/2006, Patras, Greece CSNDSP 2006
Thank You for Your Attention ! 21/07/2006, Patras, Greece CSNDSP 2006


