dd90070075d2c8e9e651248ddba03dde.ppt
- Количество слайдов: 31
 Security in Wireless LAN 802. 11 i Open System Authentication Security n. Wired Equivalent Privacy (WEP) n. Robust Security Network (RSN) n n n Temporal Key Integrity protocol (TKIP) Counter Mode with CBC-MAC (CCMP) Key Management and Establishment Authentication Protocols CN 8816: Network Security 1
Security in Wireless LAN 802. 11 i Open System Authentication Security n. Wired Equivalent Privacy (WEP) n. Robust Security Network (RSN) n n n Temporal Key Integrity protocol (TKIP) Counter Mode with CBC-MAC (CCMP) Key Management and Establishment Authentication Protocols CN 8816: Network Security 1
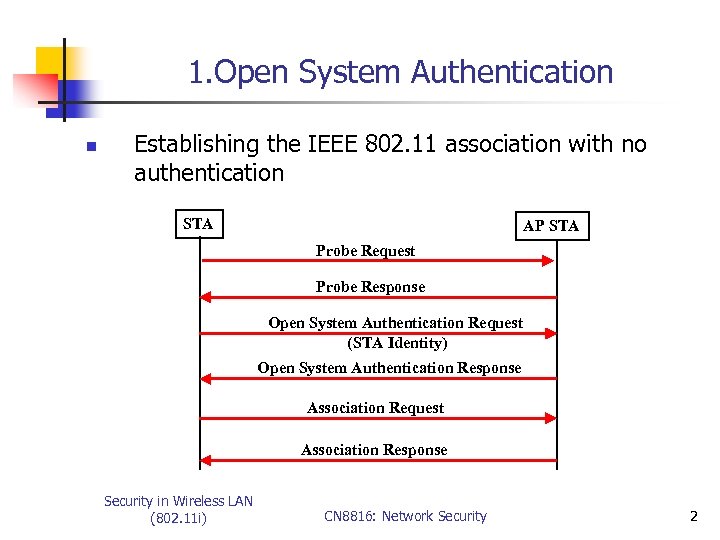 1. Open System Authentication n Establishing the IEEE 802. 11 association with no authentication STA AP STA Probe Request Probe Response Open System Authentication Request (STA Identity) Open System Authentication Response Association Request Association Response Security in Wireless LAN (802. 11 i) CN 8816: Network Security 2
1. Open System Authentication n Establishing the IEEE 802. 11 association with no authentication STA AP STA Probe Request Probe Response Open System Authentication Request (STA Identity) Open System Authentication Response Association Request Association Response Security in Wireless LAN (802. 11 i) CN 8816: Network Security 2
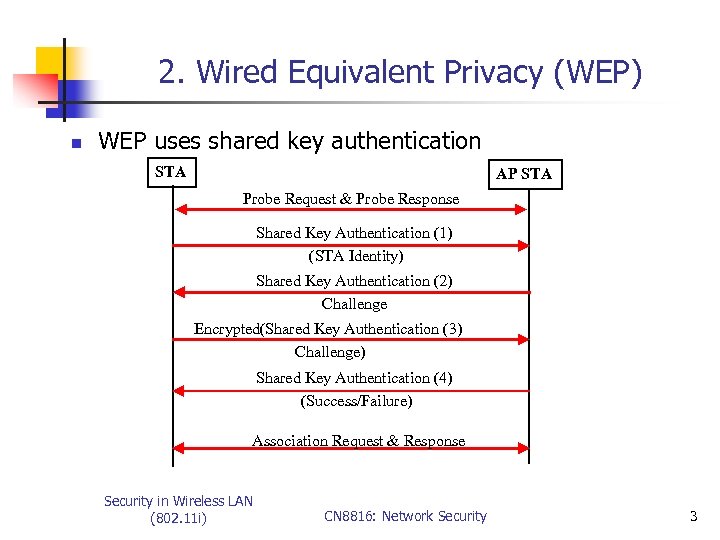 2. Wired Equivalent Privacy (WEP) n WEP uses shared key authentication STA AP STA Probe Request & Probe Response Shared Key Authentication (1) (STA Identity) Shared Key Authentication (2) Challenge Encrypted(Shared Key Authentication (3) Challenge) Shared Key Authentication (4) (Success/Failure) Association Request & Response Security in Wireless LAN (802. 11 i) CN 8816: Network Security 3
2. Wired Equivalent Privacy (WEP) n WEP uses shared key authentication STA AP STA Probe Request & Probe Response Shared Key Authentication (1) (STA Identity) Shared Key Authentication (2) Challenge Encrypted(Shared Key Authentication (3) Challenge) Shared Key Authentication (4) (Success/Failure) Association Request & Response Security in Wireless LAN (802. 11 i) CN 8816: Network Security 3
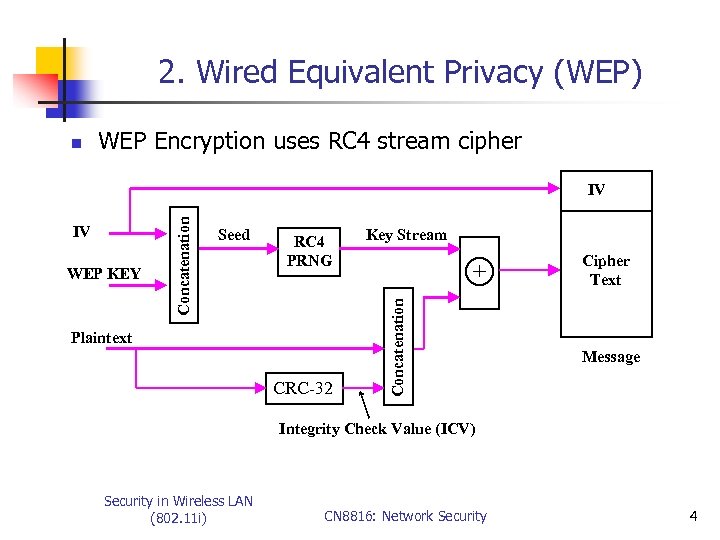 2. Wired Equivalent Privacy (WEP) n WEP Encryption uses RC 4 stream cipher WEP KEY Seed RC 4 PRNG Plaintext CRC-32 Key Stream + Concatenation IV Cipher Text Message Integrity Check Value (ICV) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 4
2. Wired Equivalent Privacy (WEP) n WEP Encryption uses RC 4 stream cipher WEP KEY Seed RC 4 PRNG Plaintext CRC-32 Key Stream + Concatenation IV Cipher Text Message Integrity Check Value (ICV) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 4
 2. Wired Equivalent Privacy (WEP) n Several major problems in WEP security n n The IV used to produce the RC 4 stream is only 24 -bit long n The short IV field means that the same RC 4 stream will be used to encrypt different texts – IV collision n Statistical attacks can be used to recover the plaintexts due to IV collision The CRC-32 checksum can be easily manipulated to produce a valid integrity check value (ICV) for a false message Security in Wireless LAN (802. 11 i) CN 8816: Network Security 5
2. Wired Equivalent Privacy (WEP) n Several major problems in WEP security n n The IV used to produce the RC 4 stream is only 24 -bit long n The short IV field means that the same RC 4 stream will be used to encrypt different texts – IV collision n Statistical attacks can be used to recover the plaintexts due to IV collision The CRC-32 checksum can be easily manipulated to produce a valid integrity check value (ICV) for a false message Security in Wireless LAN (802. 11 i) CN 8816: Network Security 5
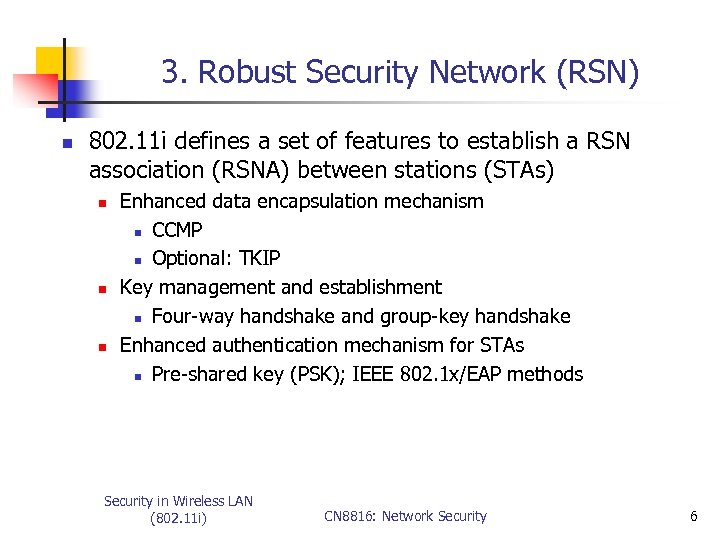 3. Robust Security Network (RSN) n 802. 11 i defines a set of features to establish a RSN association (RSNA) between stations (STAs) n n n Enhanced data encapsulation mechanism n CCMP n Optional: TKIP Key management and establishment n Four-way handshake and group-key handshake Enhanced authentication mechanism for STAs n Pre-shared key (PSK); IEEE 802. 1 x/EAP methods Security in Wireless LAN (802. 11 i) CN 8816: Network Security 6
3. Robust Security Network (RSN) n 802. 11 i defines a set of features to establish a RSN association (RSNA) between stations (STAs) n n n Enhanced data encapsulation mechanism n CCMP n Optional: TKIP Key management and establishment n Four-way handshake and group-key handshake Enhanced authentication mechanism for STAs n Pre-shared key (PSK); IEEE 802. 1 x/EAP methods Security in Wireless LAN (802. 11 i) CN 8816: Network Security 6
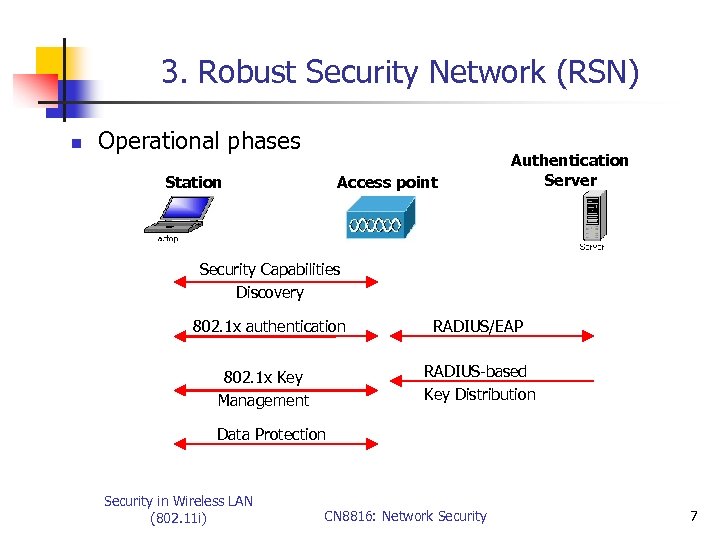 3. Robust Security Network (RSN) n Operational phases Station Access point Authentication Server Security Capabilities Discovery 802. 1 x authentication RADIUS/EAP RADIUS-based Key Distribution 802. 1 x Key Management Data Protection Security in Wireless LAN (802. 11 i) CN 8816: Network Security 7
3. Robust Security Network (RSN) n Operational phases Station Access point Authentication Server Security Capabilities Discovery 802. 1 x authentication RADIUS/EAP RADIUS-based Key Distribution 802. 1 x Key Management Data Protection Security in Wireless LAN (802. 11 i) CN 8816: Network Security 7
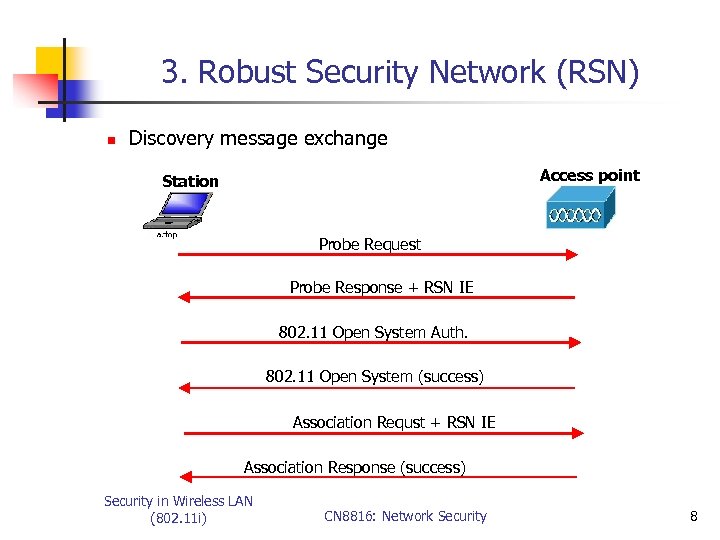 3. Robust Security Network (RSN) n Discovery message exchange Access point Station Probe Request Probe Response + RSN IE 802. 11 Open System Auth. 802. 11 Open System (success) Association Requst + RSN IE Association Response (success) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 8
3. Robust Security Network (RSN) n Discovery message exchange Access point Station Probe Request Probe Response + RSN IE 802. 11 Open System Auth. 802. 11 Open System (success) Association Requst + RSN IE Association Response (success) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 8
 3. Robust Security Network (RSN) n Authentication n n Mutual authentication The AS and station derive a Master Key (MK) A Pairwise Master Key (PMK) is derived from MK The AS distributed PMK to the AP In PSK authentication, the authentication phase is skipped n PMK = PSK Security in Wireless LAN (802. 11 i) CN 8816: Network Security 9
3. Robust Security Network (RSN) n Authentication n n Mutual authentication The AS and station derive a Master Key (MK) A Pairwise Master Key (PMK) is derived from MK The AS distributed PMK to the AP In PSK authentication, the authentication phase is skipped n PMK = PSK Security in Wireless LAN (802. 11 i) CN 8816: Network Security 9
 3. Robust Security Network (RSN) n Key management and establishment n n PMK is sent to AP by AS Key management is performed between AP and the peer – four-way handshake n The four-way handshake can also be used for mutual authentication between AP and the peer in PSK mode A set of keys are derived from PMK to protect group key exchange and data Group key exchange allows AP to distribute group key (for multicast) to the peer Security in Wireless LAN (802. 11 i) CN 8816: Network Security 10
3. Robust Security Network (RSN) n Key management and establishment n n PMK is sent to AP by AS Key management is performed between AP and the peer – four-way handshake n The four-way handshake can also be used for mutual authentication between AP and the peer in PSK mode A set of keys are derived from PMK to protect group key exchange and data Group key exchange allows AP to distribute group key (for multicast) to the peer Security in Wireless LAN (802. 11 i) CN 8816: Network Security 10
 4. Temporal Key Integrity Protocol (TKIP) n Optional IEEE 802. 11 i protocol for data confidentiality and integrity n n TKIP is designed explicitly for implementation on WEP legacy hardware TKIP three new features: n n n A cryptographic message integrity code (MIC) A new IV sequencing discipline n The transmitter increments the sequence number with each packet it sends A per-packet key mixing function Security in Wireless LAN (802. 11 i) CN 8816: Network Security 11
4. Temporal Key Integrity Protocol (TKIP) n Optional IEEE 802. 11 i protocol for data confidentiality and integrity n n TKIP is designed explicitly for implementation on WEP legacy hardware TKIP three new features: n n n A cryptographic message integrity code (MIC) A new IV sequencing discipline n The transmitter increments the sequence number with each packet it sends A per-packet key mixing function Security in Wireless LAN (802. 11 i) CN 8816: Network Security 11
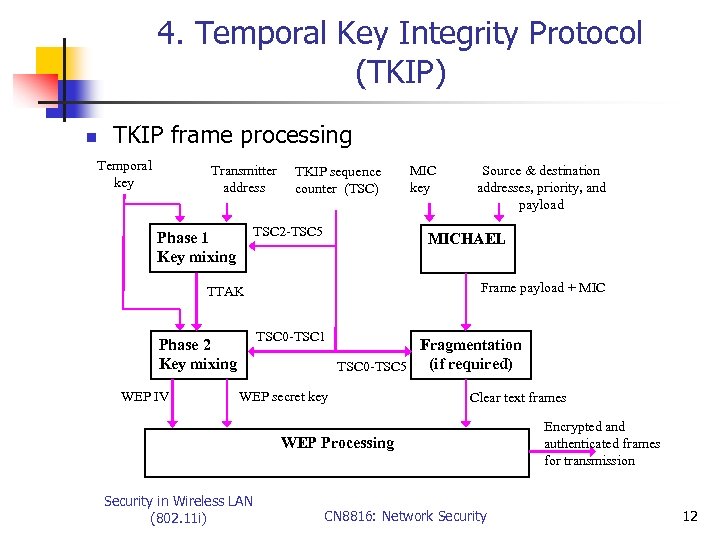 4. Temporal Key Integrity Protocol (TKIP) n TKIP frame processing Temporal key Transmitter address TKIP sequence counter (TSC) TSC 2 -TSC 5 Phase 1 Key mixing WEP IV Source & destination addresses, priority, and payload MICHAEL Frame payload + MIC TTAK TSC 0 -TSC 1 Phase 2 Key mixing MIC key Fragmentation (if required) TSC 0 -TSC 5 WEP secret key Clear text frames WEP Processing Security in Wireless LAN (802. 11 i) CN 8816: Network Security Encrypted and authenticated frames for transmission 12
4. Temporal Key Integrity Protocol (TKIP) n TKIP frame processing Temporal key Transmitter address TKIP sequence counter (TSC) TSC 2 -TSC 5 Phase 1 Key mixing WEP IV Source & destination addresses, priority, and payload MICHAEL Frame payload + MIC TTAK TSC 0 -TSC 1 Phase 2 Key mixing MIC key Fragmentation (if required) TSC 0 -TSC 5 WEP secret key Clear text frames WEP Processing Security in Wireless LAN (802. 11 i) CN 8816: Network Security Encrypted and authenticated frames for transmission 12
 4. Temporal Key Integrity Protocol (TKIP) n Defeating weak key attacks: key mixing n n Transforms a temporal key and packet sequence number into a per packet key and IV The key mixing function operates in two phases n Phase 1: Different keys used by different links n Phase 1 needs to be recomputed only once every 216 frames Phase 2: Different WEP key and IV per packet Phases 1 and 2 can be pre-computed n n Security in Wireless LAN (802. 11 i) CN 8816: Network Security 13
4. Temporal Key Integrity Protocol (TKIP) n Defeating weak key attacks: key mixing n n Transforms a temporal key and packet sequence number into a per packet key and IV The key mixing function operates in two phases n Phase 1: Different keys used by different links n Phase 1 needs to be recomputed only once every 216 frames Phase 2: Different WEP key and IV per packet Phases 1 and 2 can be pre-computed n n Security in Wireless LAN (802. 11 i) CN 8816: Network Security 13
 3. Temporal Key Integrity Protocol (TKIP) n Defeating replays: IV sequence enforcement n n TKIP uses the IV field as a packet sequence number The transmitter increments the sequence number with each packet it send A packet will be discarded if it arrives out of order n A packet is out-of-order if its IV is the same or smaller than a previous correctly received packet Defeating forgeries: New MIC (Michael) n MIC key is 64 -bits n security level of 20 bits Security in Wireless LAN (802. 11 i) CN 8816: Network Security 14
3. Temporal Key Integrity Protocol (TKIP) n Defeating replays: IV sequence enforcement n n TKIP uses the IV field as a packet sequence number The transmitter increments the sequence number with each packet it send A packet will be discarded if it arrives out of order n A packet is out-of-order if its IV is the same or smaller than a previous correctly received packet Defeating forgeries: New MIC (Michael) n MIC key is 64 -bits n security level of 20 bits Security in Wireless LAN (802. 11 i) CN 8816: Network Security 14
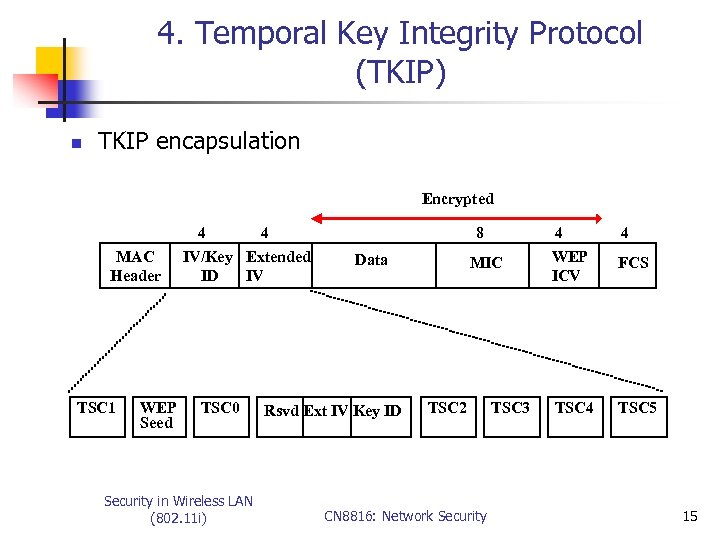 4. Temporal Key Integrity Protocol (TKIP) n TKIP encapsulation Encrypted 4 MAC Header TSC 1 WEP Seed 4 IV/Key Extended ID IV TSC 0 Security in Wireless LAN (802. 11 i) 8 Data Rsvd Ext IV Key ID 4 MIC TSC 2 CN 8816: Network Security TSC 3 4 WEP ICV FCS TSC 4 TSC 5 15
4. Temporal Key Integrity Protocol (TKIP) n TKIP encapsulation Encrypted 4 MAC Header TSC 1 WEP Seed 4 IV/Key Extended ID IV TSC 0 Security in Wireless LAN (802. 11 i) 8 Data Rsvd Ext IV Key ID 4 MIC TSC 2 CN 8816: Network Security TSC 3 4 WEP ICV FCS TSC 4 TSC 5 15
 5. Counter Mode with CBC-MAC (CCMP) n Both encryption and MIC use AES n n n Uses counter Mode (CTR) to encrypt the payload and MIC Uses CBC-MAC to compute a MIC on the plaintext header and the payload Both encryption and authentication use the same key Encryption Header Payload MIC Authenticated Security in Wireless LAN (802. 11 i) CN 8816: Network Security 16
5. Counter Mode with CBC-MAC (CCMP) n Both encryption and MIC use AES n n n Uses counter Mode (CTR) to encrypt the payload and MIC Uses CBC-MAC to compute a MIC on the plaintext header and the payload Both encryption and authentication use the same key Encryption Header Payload MIC Authenticated Security in Wireless LAN (802. 11 i) CN 8816: Network Security 16
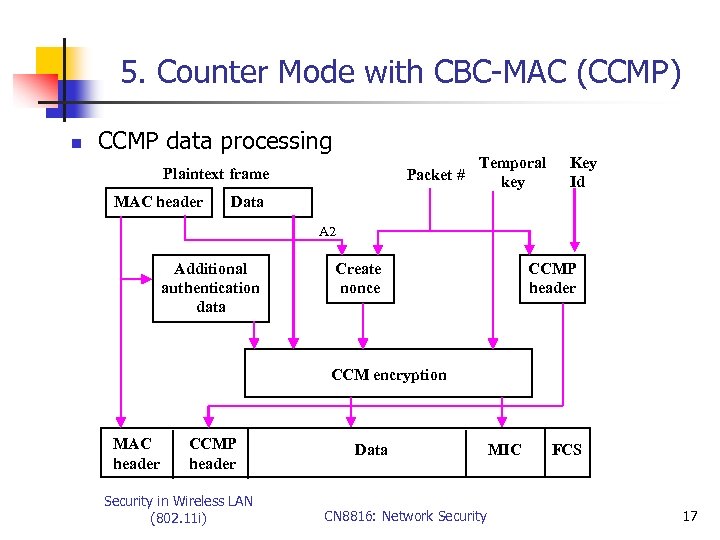 5. Counter Mode with CBC-MAC (CCMP) n CCMP data processing Plaintext frame MAC header Packet # Temporal key Key Id Data A 2 Additional authentication data Create nonce CCMP header CCM encryption MAC header CCMP header Security in Wireless LAN (802. 11 i) Data CN 8816: Network Security MIC FCS 17
5. Counter Mode with CBC-MAC (CCMP) n CCMP data processing Plaintext frame MAC header Packet # Temporal key Key Id Data A 2 Additional authentication data Create nonce CCMP header CCM encryption MAC header CCMP header Security in Wireless LAN (802. 11 i) Data CN 8816: Network Security MIC FCS 17
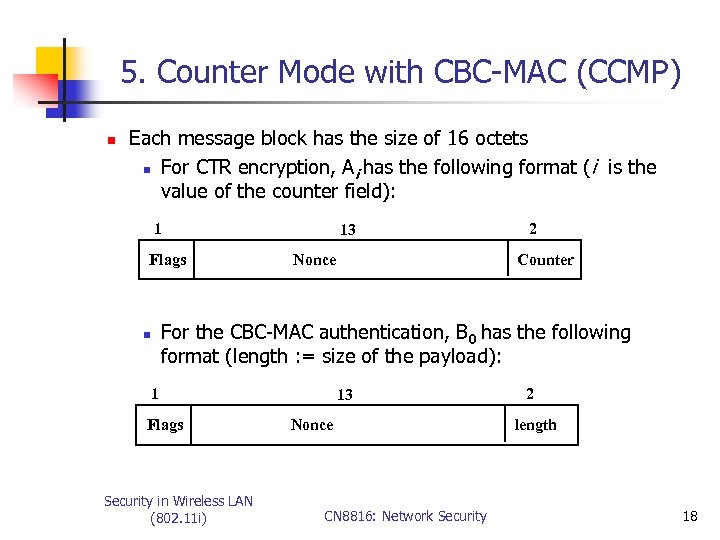 5. Counter Mode with CBC-MAC (CCMP) n Each message block has the size of 16 octets n For CTR encryption, Ai has the following format (i is the value of the counter field): 1 Flags 13 Nonce 2 Counter For the CBC-MAC authentication, B 0 has the following format (length : = size of the payload): n 1 Flags Security in Wireless LAN (802. 11 i) 13 Nonce CN 8816: Network Security 2 length 18
5. Counter Mode with CBC-MAC (CCMP) n Each message block has the size of 16 octets n For CTR encryption, Ai has the following format (i is the value of the counter field): 1 Flags 13 Nonce 2 Counter For the CBC-MAC authentication, B 0 has the following format (length : = size of the payload): n 1 Flags Security in Wireless LAN (802. 11 i) 13 Nonce CN 8816: Network Security 2 length 18
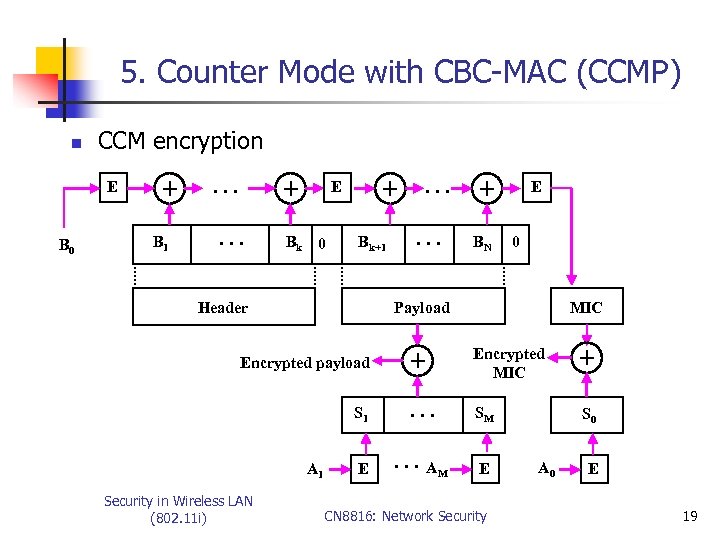 5. Counter Mode with CBC-MAC (CCMP) n CCM encryption E B 0 + B 1 + . . . + E Bk 0 Bk+1 Header . . . + BN E 0 Payload Encrypted payload S 1 A 1 Security in Wireless LAN (802. 11 i) . . . E MIC + Encrypted MIC + . . . SM S 0 . . . AM E CN 8816: Network Security A 0 E 19
5. Counter Mode with CBC-MAC (CCMP) n CCM encryption E B 0 + B 1 + . . . + E Bk 0 Bk+1 Header . . . + BN E 0 Payload Encrypted payload S 1 A 1 Security in Wireless LAN (802. 11 i) . . . E MIC + Encrypted MIC + . . . SM S 0 . . . AM E CN 8816: Network Security A 0 E 19
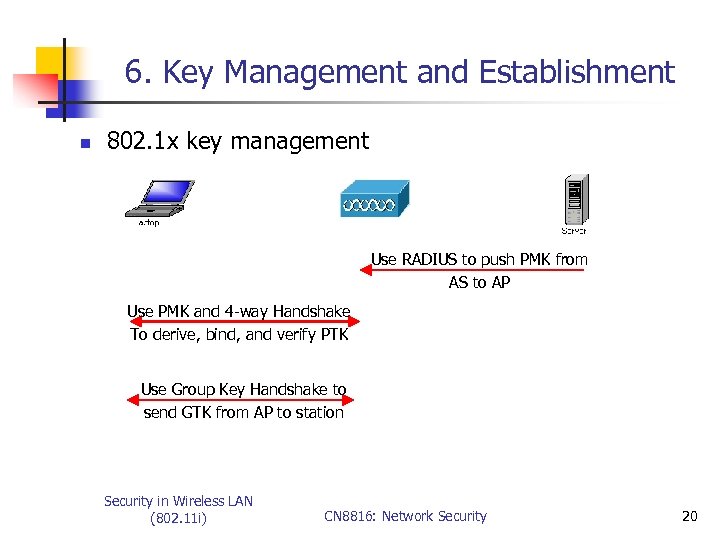 6. Key Management and Establishment n 802. 1 x key management Use RADIUS to push PMK from AS to AP Use PMK and 4 -way Handshake To derive, bind, and verify PTK Use Group Key Handshake to send GTK from AP to station Security in Wireless LAN (802. 11 i) CN 8816: Network Security 20
6. Key Management and Establishment n 802. 1 x key management Use RADIUS to push PMK from AS to AP Use PMK and 4 -way Handshake To derive, bind, and verify PTK Use Group Key Handshake to send GTK from AP to station Security in Wireless LAN (802. 11 i) CN 8816: Network Security 20
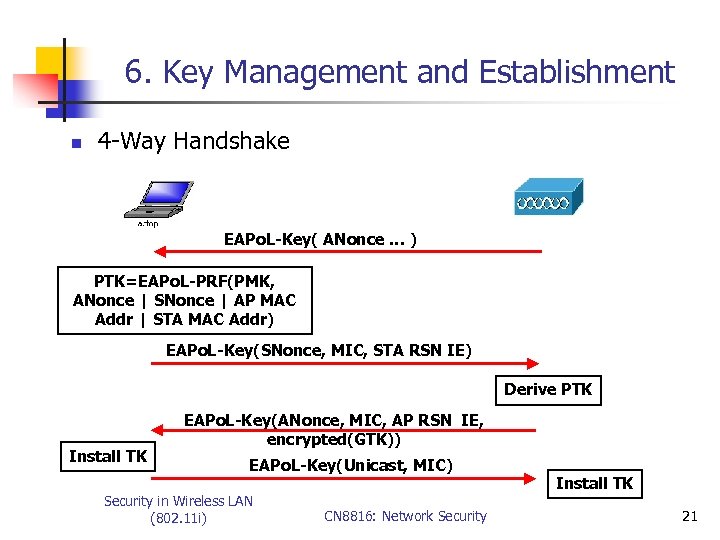 6. Key Management and Establishment n 4 -Way Handshake EAPo. L-Key( ANonce … ) PTK=EAPo. L-PRF(PMK, ANonce | SNonce | AP MAC Addr | STA MAC Addr) EAPo. L-Key(SNonce, MIC, STA RSN IE) Derive PTK Install TK EAPo. L-Key(ANonce, MIC, AP RSN IE, encrypted(GTK)) EAPo. L-Key(Unicast, MIC) Security in Wireless LAN (802. 11 i) CN 8816: Network Security Install TK 21
6. Key Management and Establishment n 4 -Way Handshake EAPo. L-Key( ANonce … ) PTK=EAPo. L-PRF(PMK, ANonce | SNonce | AP MAC Addr | STA MAC Addr) EAPo. L-Key(SNonce, MIC, STA RSN IE) Derive PTK Install TK EAPo. L-Key(ANonce, MIC, AP RSN IE, encrypted(GTK)) EAPo. L-Key(Unicast, MIC) Security in Wireless LAN (802. 11 i) CN 8816: Network Security Install TK 21
 6. Key Management and Establishment n n n PTK : = KCK | KEK | TK n KCK used to authenticate Messages 2, 3, and 4 n KEK unused by 4 -way handshake – used for the encryption of group key n TK installed after Message 4 – used for data encryption The discovery RSN IE exchange from alteration protected by the MIC in Messages 2 and 3 The MIC carried in the messages are also used for mutual authentication Security in Wireless LAN (802. 11 i) CN 8816: Network Security 22
6. Key Management and Establishment n n n PTK : = KCK | KEK | TK n KCK used to authenticate Messages 2, 3, and 4 n KEK unused by 4 -way handshake – used for the encryption of group key n TK installed after Message 4 – used for data encryption The discovery RSN IE exchange from alteration protected by the MIC in Messages 2 and 3 The MIC carried in the messages are also used for mutual authentication Security in Wireless LAN (802. 11 i) CN 8816: Network Security 22
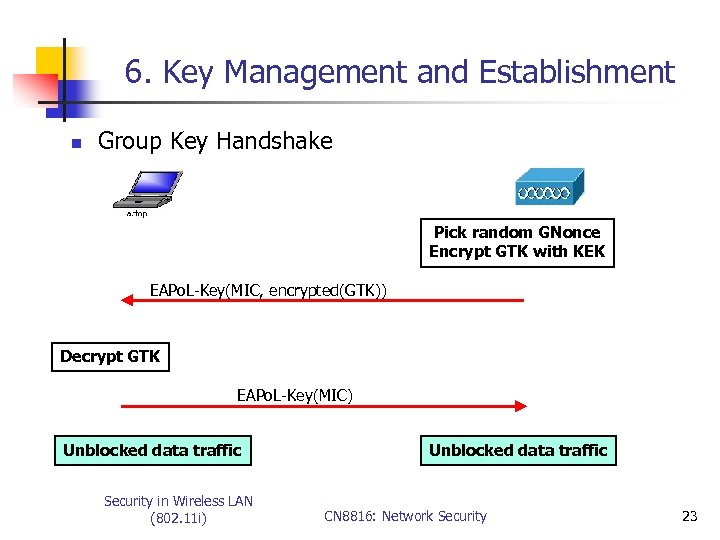 6. Key Management and Establishment n Group Key Handshake Pick random GNonce Encrypt GTK with KEK EAPo. L-Key(MIC, encrypted(GTK)) Decrypt GTK EAPo. L-Key(MIC) Unblocked data traffic Security in Wireless LAN (802. 11 i) Unblocked data traffic CN 8816: Network Security 23
6. Key Management and Establishment n Group Key Handshake Pick random GNonce Encrypt GTK with KEK EAPo. L-Key(MIC, encrypted(GTK)) Decrypt GTK EAPo. L-Key(MIC) Unblocked data traffic Security in Wireless LAN (802. 11 i) Unblocked data traffic CN 8816: Network Security 23
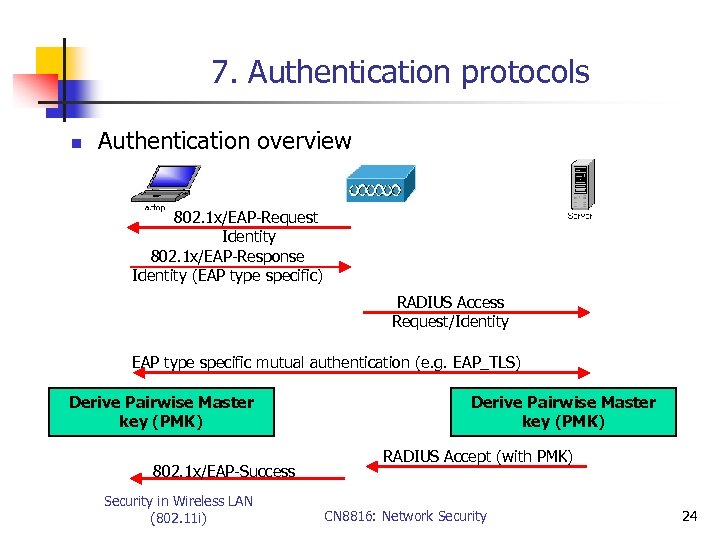 7. Authentication protocols n Authentication overview 802. 1 x/EAP-Request Identity 802. 1 x/EAP-Response Identity (EAP type specific) RADIUS Access Request/Identity EAP type specific mutual authentication (e. g. EAP_TLS) Derive Pairwise Master key (PMK) 802. 1 x/EAP-Success Security in Wireless LAN (802. 11 i) Derive Pairwise Master key (PMK) RADIUS Accept (with PMK) CN 8816: Network Security 24
7. Authentication protocols n Authentication overview 802. 1 x/EAP-Request Identity 802. 1 x/EAP-Response Identity (EAP type specific) RADIUS Access Request/Identity EAP type specific mutual authentication (e. g. EAP_TLS) Derive Pairwise Master key (PMK) 802. 1 x/EAP-Success Security in Wireless LAN (802. 11 i) Derive Pairwise Master key (PMK) RADIUS Accept (with PMK) CN 8816: Network Security 24
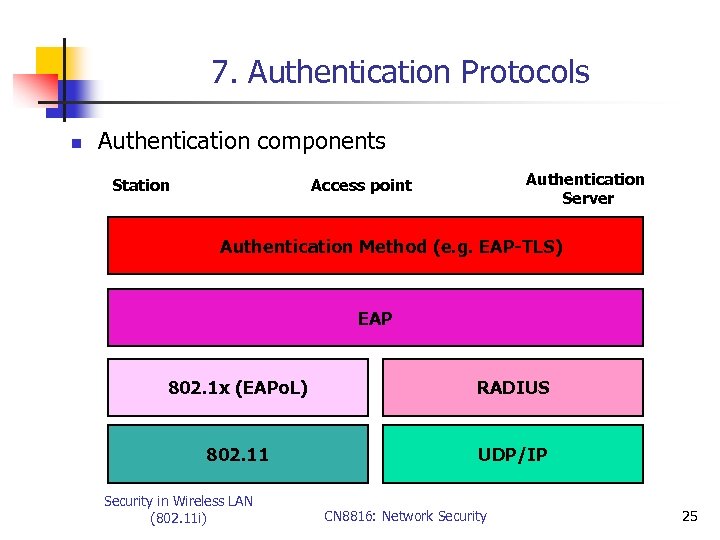 7. Authentication Protocols n Authentication components Station Authentication Server Access point Authentication Method (e. g. EAP-TLS) EAP 802. 1 x (EAPo. L) RADIUS 802. 11 UDP/IP Security in Wireless LAN (802. 11 i) CN 8816: Network Security 25
7. Authentication Protocols n Authentication components Station Authentication Server Access point Authentication Method (e. g. EAP-TLS) EAP 802. 1 x (EAPo. L) RADIUS 802. 11 UDP/IP Security in Wireless LAN (802. 11 i) CN 8816: Network Security 25
 7. Authentication Protocols n LEAP n n Simple – neither server certificate or peer certificates is required CHAP is used for mutual authentication n The user’s password is the shared secret Session key is derived from the shared secret , the challenges and the challenge responses Susceptible to the dictionary attack Security in Wireless LAN (802. 11 i) CN 8816: Network Security 26
7. Authentication Protocols n LEAP n n Simple – neither server certificate or peer certificates is required CHAP is used for mutual authentication n The user’s password is the shared secret Session key is derived from the shared secret , the challenges and the challenge responses Susceptible to the dictionary attack Security in Wireless LAN (802. 11 i) CN 8816: Network Security 26
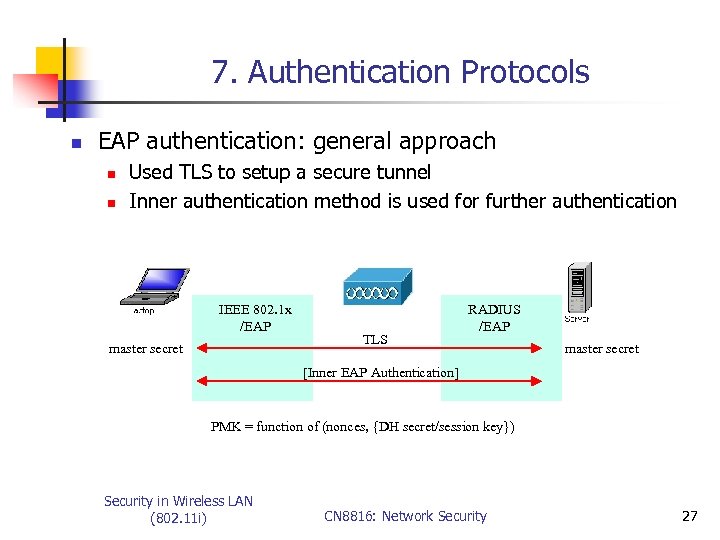 7. Authentication Protocols n EAP authentication: general approach n n Used TLS to setup a secure tunnel Inner authentication method is used for further authentication IEEE 802. 1 x /EAP master secret TLS RADIUS /EAP master secret [Inner EAP Authentication] PMK = function of (nonces, {DH secret/session key}) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 27
7. Authentication Protocols n EAP authentication: general approach n n Used TLS to setup a secure tunnel Inner authentication method is used for further authentication IEEE 802. 1 x /EAP master secret TLS RADIUS /EAP master secret [Inner EAP Authentication] PMK = function of (nonces, {DH secret/session key}) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 27
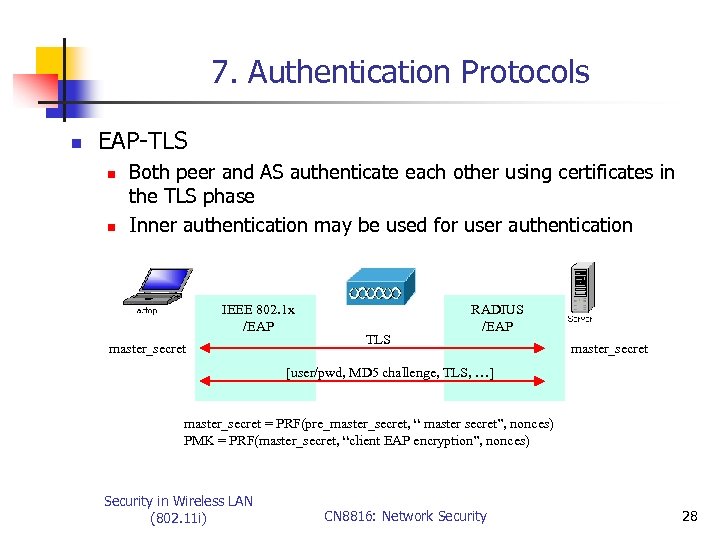 7. Authentication Protocols n EAP-TLS n n Both peer and AS authenticate each other using certificates in the TLS phase Inner authentication may be used for user authentication IEEE 802. 1 x /EAP master_secret TLS RADIUS /EAP master_secret [user/pwd, MD 5 challenge, TLS, …] master_secret = PRF(pre_master_secret, “ master secret”, nonces) PMK = PRF(master_secret, “client EAP encryption”, nonces) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 28
7. Authentication Protocols n EAP-TLS n n Both peer and AS authenticate each other using certificates in the TLS phase Inner authentication may be used for user authentication IEEE 802. 1 x /EAP master_secret TLS RADIUS /EAP master_secret [user/pwd, MD 5 challenge, TLS, …] master_secret = PRF(pre_master_secret, “ master secret”, nonces) PMK = PRF(master_secret, “client EAP encryption”, nonces) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 28
 7. Authentication Protocols n PEAP n n n At the TLS phase, server is authenticated based on the server’s certificate – no peer authentication Peer authentication is done at the inner authentication n EAP-MS-CHAPV 2 is the most popular inner authentication method – it provides mutual authentication plus key generation The PMK generated is based on both the TLS master_secret and the master_session_key (MSK) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 29
7. Authentication Protocols n PEAP n n n At the TLS phase, server is authenticated based on the server’s certificate – no peer authentication Peer authentication is done at the inner authentication n EAP-MS-CHAPV 2 is the most popular inner authentication method – it provides mutual authentication plus key generation The PMK generated is based on both the TLS master_secret and the master_session_key (MSK) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 29
 7. Authentication Protocols n EAP-FAST n n Two methods for setting up TLS tunnel n Server certificate n Protected Access Credential (PAC) PAC components: n Shared secret – used to derive TLS master secret n opaque element – presented by the peer to the AS n n n Contains shared secret and peer identity Protected with cryptographic keys and algorithm other information – identity of the PAC issuer, secret lifetime … Security in Wireless LAN (802. 11 i) CN 8816: Network Security 30
7. Authentication Protocols n EAP-FAST n n Two methods for setting up TLS tunnel n Server certificate n Protected Access Credential (PAC) PAC components: n Shared secret – used to derive TLS master secret n opaque element – presented by the peer to the AS n n n Contains shared secret and peer identity Protected with cryptographic keys and algorithm other information – identity of the PAC issuer, secret lifetime … Security in Wireless LAN (802. 11 i) CN 8816: Network Security 30
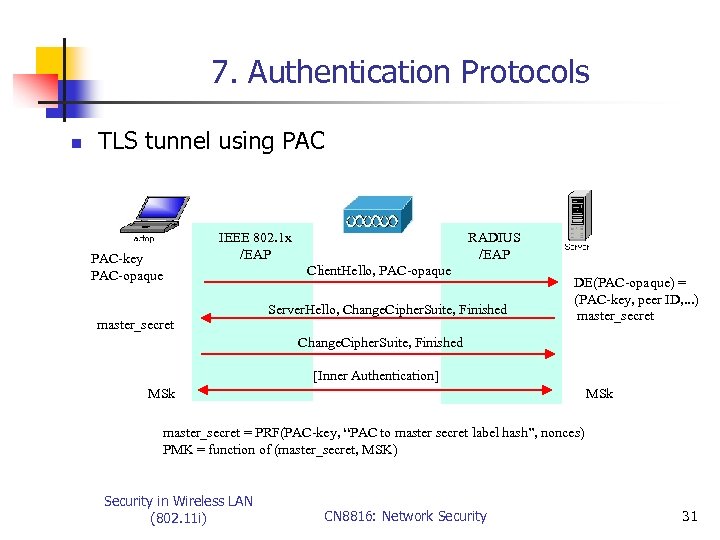 7. Authentication Protocols n TLS tunnel using PAC-key PAC-opaque IEEE 802. 1 x /EAP master_secret RADIUS /EAP Client. Hello, PAC-opaque Server. Hello, Change. Cipher. Suite, Finished DE(PAC-opaque) = (PAC-key, peer ID, . . . ) master_secret Change. Cipher. Suite, Finished [Inner Authentication] MSk master_secret = PRF(PAC-key, “PAC to master secret label hash”, nonces) PMK = function of (master_secret, MSK) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 31
7. Authentication Protocols n TLS tunnel using PAC-key PAC-opaque IEEE 802. 1 x /EAP master_secret RADIUS /EAP Client. Hello, PAC-opaque Server. Hello, Change. Cipher. Suite, Finished DE(PAC-opaque) = (PAC-key, peer ID, . . . ) master_secret Change. Cipher. Suite, Finished [Inner Authentication] MSk master_secret = PRF(PAC-key, “PAC to master secret label hash”, nonces) PMK = function of (master_secret, MSK) Security in Wireless LAN (802. 11 i) CN 8816: Network Security 31


