0393d07398d527f97582494c9c1b56f5.ppt
- Количество слайдов: 17
 Security in Computational Grid Seonho Kim Oct 18 th 2002
Security in Computational Grid Seonho Kim Oct 18 th 2002
 Content • • • Computational Grid Security Requirements in Grid Terminology Security Policy in Grid Globus overview Grid Security Architecture
Content • • • Computational Grid Security Requirements in Grid Terminology Security Policy in Grid Globus overview Grid Security Architecture
 What is Grid? • A computational grid is a hardware and software infrastructure that provides dependable, consistent, pervasive, and inexpensive access to high-end computational capabilities • A Computational Grids is a wide area distributed and parallel computing environment consisting of heterogenous platforms spanning multiple administrative domains – coordinated resource sharing and problem solving in dynamic, multi-institutional virtual organizations – Checklists • Coordinates resources that are not subject to centralized control • Using standard, open, general-purpose protocols and interfaces • Deliver nontrivial qualities of services
What is Grid? • A computational grid is a hardware and software infrastructure that provides dependable, consistent, pervasive, and inexpensive access to high-end computational capabilities • A Computational Grids is a wide area distributed and parallel computing environment consisting of heterogenous platforms spanning multiple administrative domains – coordinated resource sharing and problem solving in dynamic, multi-institutional virtual organizations – Checklists • Coordinates resources that are not subject to centralized control • Using standard, open, general-purpose protocols and interfaces • Deliver nontrivial qualities of services
 Security? • Protecting the system from its users • Preventing the unauthorized disclosure or modification of data Security in Computational Grid • Characteristics of the Grid computing environment • • Large & dynamic user population and resource pool Dynamic resource acquisition and release Dynamic creation and destruction of a variety of network connections Heterogenous local authentication and authorization mechanisms and policies (e. g. Kerboros, plaintext passwords, SSL, SSH etc) • An individual user will be associated with different local name spaces, credentials, or accounts at different sites.
Security? • Protecting the system from its users • Preventing the unauthorized disclosure or modification of data Security in Computational Grid • Characteristics of the Grid computing environment • • Large & dynamic user population and resource pool Dynamic resource acquisition and release Dynamic creation and destruction of a variety of network connections Heterogenous local authentication and authorization mechanisms and policies (e. g. Kerboros, plaintext passwords, SSL, SSH etc) • An individual user will be associated with different local name spaces, credentials, or accounts at different sites.
 Security Requirements • Authentication solution for verifying identities among a user, the processes, and the resources during the computation • Support for Local Heterogeneity – Various authentication/authorization mechanism, polices • Several Constraints to meet – Single sign-on & delegation – Protection of Credentials – Interoperability with local security solutions: Inter-domain access mechanism – Uniform certification infrastructure – Support for secure group communication – Support for multiple implementations
Security Requirements • Authentication solution for verifying identities among a user, the processes, and the resources during the computation • Support for Local Heterogeneity – Various authentication/authorization mechanism, polices • Several Constraints to meet – Single sign-on & delegation – Protection of Credentials – Interoperability with local security solutions: Inter-domain access mechanism – Uniform certification infrastructure – Support for secure group communication – Support for multiple implementations
 Security Requirements - Delegation • The context initiator gives the context acceptor the ability to initiate additional security contexts as an agent of the context initiator – Remote creation of a proxy credential – Allows remote process to authenticate on behalf of the user • Delegation in Globus – New key pair generated remotely on server – Proxy certificate and public key sent to client – Clients signs proxy certificate with its private key and returns it – Server puts proxy in /tmp
Security Requirements - Delegation • The context initiator gives the context acceptor the ability to initiate additional security contexts as an agent of the context initiator – Remote creation of a proxy credential – Allows remote process to authenticate on behalf of the user • Delegation in Globus – New key pair generated remotely on server – Proxy certificate and public key sent to client – Clients signs proxy certificate with its private key and returns it – Server puts proxy in /tmp
 Terminology • • Authentication Authorization Integrity and Confidentiality Security Policy – A set of rules that define the security subjects, security objects, and relationships(security operations) among them. • CA(Certificate Authority) – The third party that does certification(the binding) and issuing certificate • Trust Domain – A logical, administrative structure where a single, consistent local security policy holds
Terminology • • Authentication Authorization Integrity and Confidentiality Security Policy – A set of rules that define the security subjects, security objects, and relationships(security operations) among them. • CA(Certificate Authority) – The third party that does certification(the binding) and issuing certificate • Trust Domain – A logical, administrative structure where a single, consistent local security policy holds
 Security Policy in Grid • Multiple trust domains – Inter-domain interactions + mapping of inter-domain operations into local security policy • Operations within a single trust domain are subject to local security policy only • Mapping from global subjects to local subjects – Authenticated global subject is considered authenticated locally • Mutual authentication between entities in different trust domains • Local access control decisions by local system administrators • The execution of programs without additional user interaction during the computation • Processes running on behalf of the same subject within the same trust domain may share a single set of credentials
Security Policy in Grid • Multiple trust domains – Inter-domain interactions + mapping of inter-domain operations into local security policy • Operations within a single trust domain are subject to local security policy only • Mapping from global subjects to local subjects – Authenticated global subject is considered authenticated locally • Mutual authentication between entities in different trust domains • Local access control decisions by local system administrators • The execution of programs without additional user interaction during the computation • Processes running on behalf of the same subject within the same trust domain may share a single set of credentials
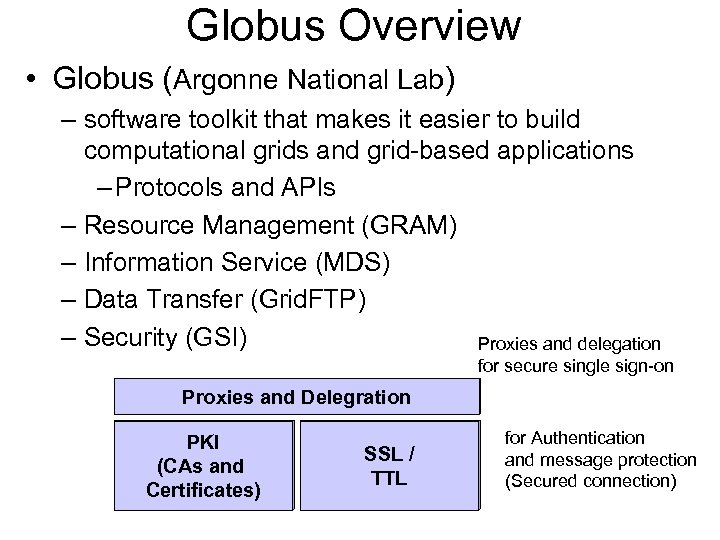 Globus Overview • Globus (Argonne National Lab) – software toolkit that makes it easier to build computational grids and grid-based applications – Protocols and APIs – Resource Management (GRAM) – Information Service (MDS) – Data Transfer (Grid. FTP) – Security (GSI) Proxies and delegation for secure single sign-on Proxies and Delegration PKI (CAs and Certificates) SSL / TTL for Authentication and message protection (Secured connection)
Globus Overview • Globus (Argonne National Lab) – software toolkit that makes it easier to build computational grids and grid-based applications – Protocols and APIs – Resource Management (GRAM) – Information Service (MDS) – Data Transfer (Grid. FTP) – Security (GSI) Proxies and delegation for secure single sign-on Proxies and Delegration PKI (CAs and Certificates) SSL / TTL for Authentication and message protection (Secured connection)
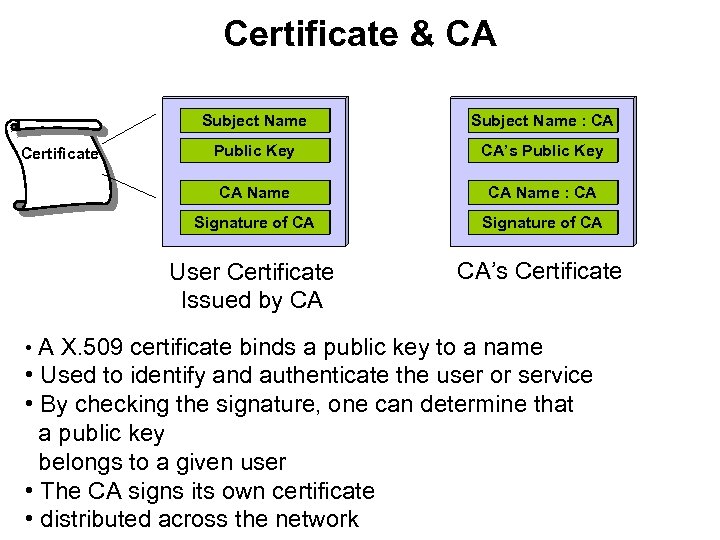 Certificate & CA Subject Name Public Key CA’s Public Key CA Name : CA Signature of CA User Certificate Issued by CA Certificate Subject Name : CA CA’s Certificate • A X. 509 certificate binds a public key to a name • Used to identify and authenticate the user or service • By checking the signature, one can determine that a public key belongs to a given user • The CA signs its own certificate • distributed across the network
Certificate & CA Subject Name Public Key CA’s Public Key CA Name : CA Signature of CA User Certificate Issued by CA Certificate Subject Name : CA CA’s Certificate • A X. 509 certificate binds a public key to a name • Used to identify and authenticate the user or service • By checking the signature, one can determine that a public key belongs to a given user • The CA signs its own certificate • distributed across the network
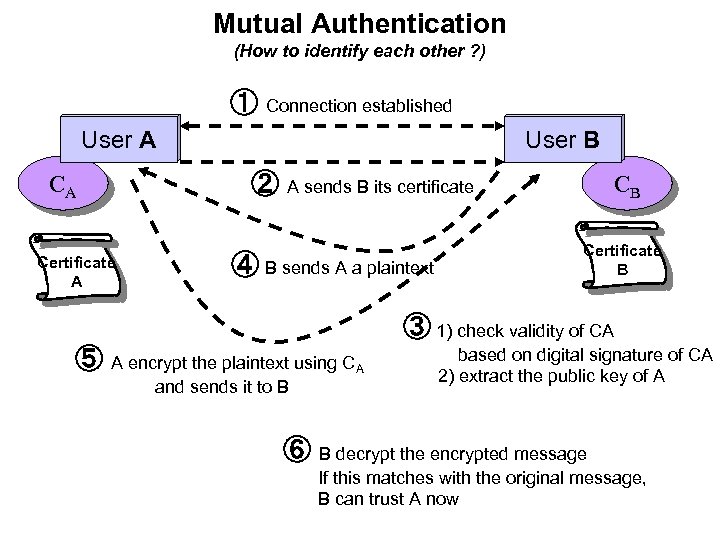 Mutual Authentication (How to identify each other ? ) ① Connection established User A CA Certificate A User B ② A sends B its certificate ④ B sends A a plaintext CB Certificate B ③ 1) check validity of CA ⑤ A encrypt the plaintext using CA and sends it to B based on digital signature of CA 2) extract the public key of A ⑥ B decrypt the encrypted message If this matches with the original message, B can trust A now
Mutual Authentication (How to identify each other ? ) ① Connection established User A CA Certificate A User B ② A sends B its certificate ④ B sends A a plaintext CB Certificate B ③ 1) check validity of CA ⑤ A encrypt the plaintext using CA and sends it to B based on digital signature of CA 2) extract the public key of A ⑥ B decrypt the encrypted message If this matches with the original message, B can trust A now
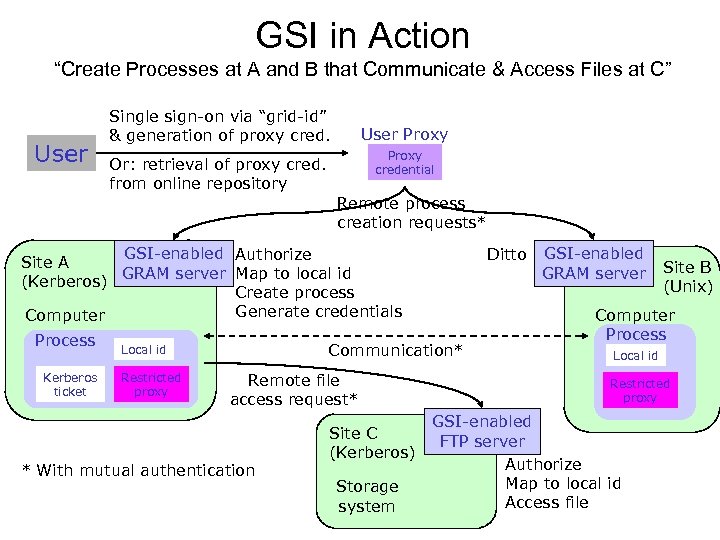 GSI in Action “Create Processes at A and B that Communicate & Access Files at C” User Single sign-on via “grid-id” & generation of proxy cred. User Proxy credential Or: retrieval of proxy cred. from online repository Remote process creation requests* GSI-enabled Authorize Site A GRAM server Map to local id (Kerberos) Create process Generate credentials Computer Process Kerberos ticket Communication* Local id Restricted proxy Ditto Remote file access request* * With mutual authentication Site C (Kerberos) Storage system GSI-enabled GRAM server Site B (Unix) Computer Process Local id Restricted proxy GSI-enabled FTP server Authorize Map to local id Access file
GSI in Action “Create Processes at A and B that Communicate & Access Files at C” User Single sign-on via “grid-id” & generation of proxy cred. User Proxy credential Or: retrieval of proxy cred. from online repository Remote process creation requests* GSI-enabled Authorize Site A GRAM server Map to local id (Kerberos) Create process Generate credentials Computer Process Kerberos ticket Communication* Local id Restricted proxy Ditto Remote file access request* * With mutual authentication Site C (Kerberos) Storage system GSI-enabled GRAM server Site B (Unix) Computer Process Local id Restricted proxy GSI-enabled FTP server Authorize Map to local id Access file
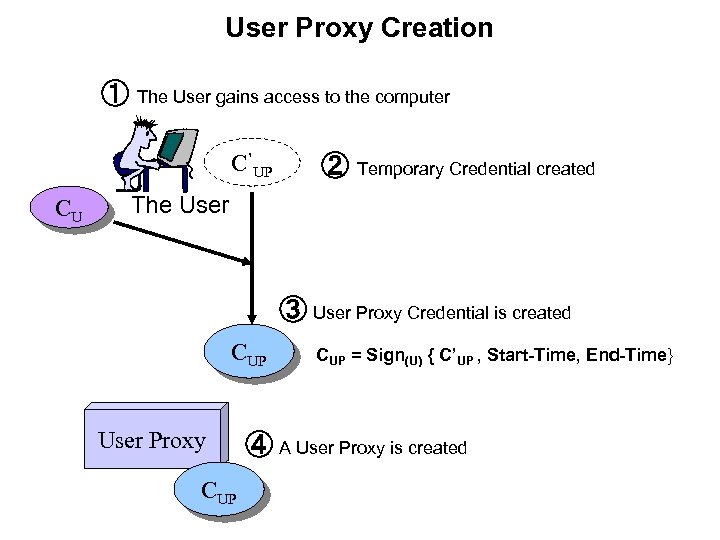 User Proxy Creation ① The User gains access to the computer C’UP CU ② Temporary Credential created The User ③ User Proxy Credential is created CUP User Proxy CUP = Sign(U) { C’UP , Start-Time, End-Time} ④ A User Proxy is created
User Proxy Creation ① The User gains access to the computer C’UP CU ② Temporary Credential created The User ③ User Proxy Credential is created CUP User Proxy CUP = Sign(U) { C’UP , Start-Time, End-Time} ④ A User Proxy is created
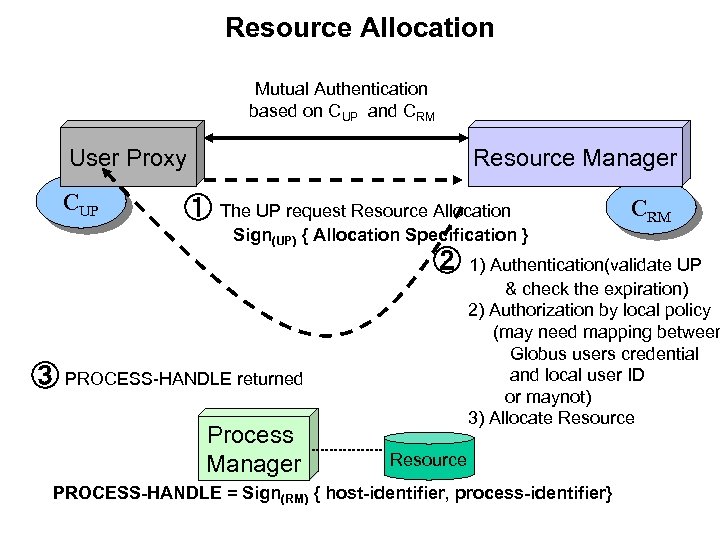 Resource Allocation Mutual Authentication based on CUP and CRM User Proxy CUP Resource Manager ① The UP request Resource Allocation Sign(UP) { Allocation Specification } CRM ② 1) Authentication(validate UP & check the expiration) 2) Authorization by local policy (may need mapping between Globus users credential and local user ID or maynot) 3) Allocate Resource ③ PROCESS-HANDLE returned Process Manager Resource PROCESS-HANDLE = Sign(RM) { host-identifier, process-identifier}
Resource Allocation Mutual Authentication based on CUP and CRM User Proxy CUP Resource Manager ① The UP request Resource Allocation Sign(UP) { Allocation Specification } CRM ② 1) Authentication(validate UP & check the expiration) 2) Authorization by local policy (may need mapping between Globus users credential and local user ID or maynot) 3) Allocate Resource ③ PROCESS-HANDLE returned Process Manager Resource PROCESS-HANDLE = Sign(RM) { host-identifier, process-identifier}
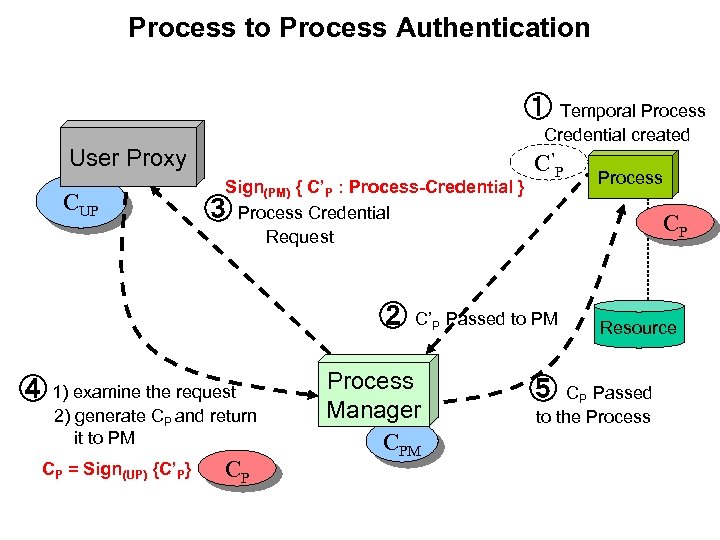 Process to Process Authentication ① Temporal Process Credential created User Proxy CUP Sign(PM) { C’P : Process-Credential } ③ Process Credential Request C ’P CP ② C’P Passed to PM ④ 1) examine the request 2) generate CP and return it to PM CP = Sign(UP) {C’P} CP Process Manager CPM Process Resource ⑤ CP Passed to the Process
Process to Process Authentication ① Temporal Process Credential created User Proxy CUP Sign(PM) { C’P : Process-Credential } ③ Process Credential Request C ’P CP ② C’P Passed to PM ④ 1) examine the request 2) generate CP and return it to PM CP = Sign(UP) {C’P} CP Process Manager CPM Process Resource ⑤ CP Passed to the Process
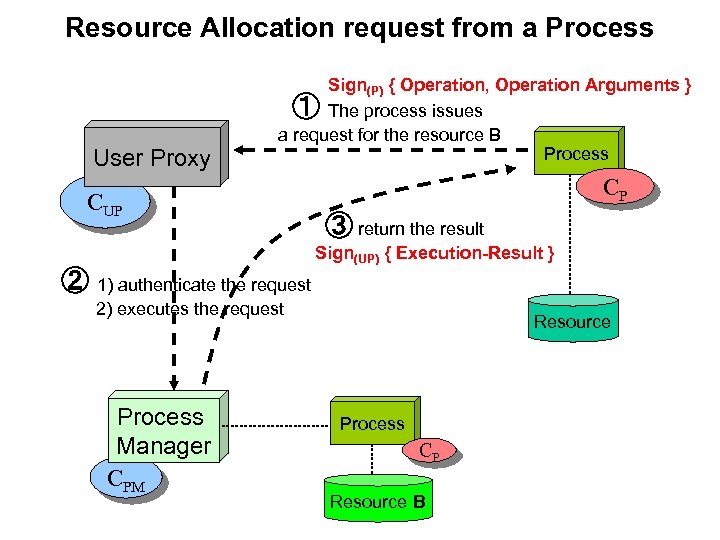 Resource Allocation request from a Process User Proxy Sign(P) { Operation, Operation Arguments } ① The process issues a request for the resource B Process CUP CP ③ return the result Sign(UP) { Execution-Result } ② 1) authenticate the request 2) executes the request Process Manager CPM Resource Process CP Resource B
Resource Allocation request from a Process User Proxy Sign(P) { Operation, Operation Arguments } ① The process issues a request for the resource B Process CUP CP ③ return the result Sign(UP) { Execution-Result } ② 1) authenticate the request 2) executes the request Process Manager CPM Resource Process CP Resource B
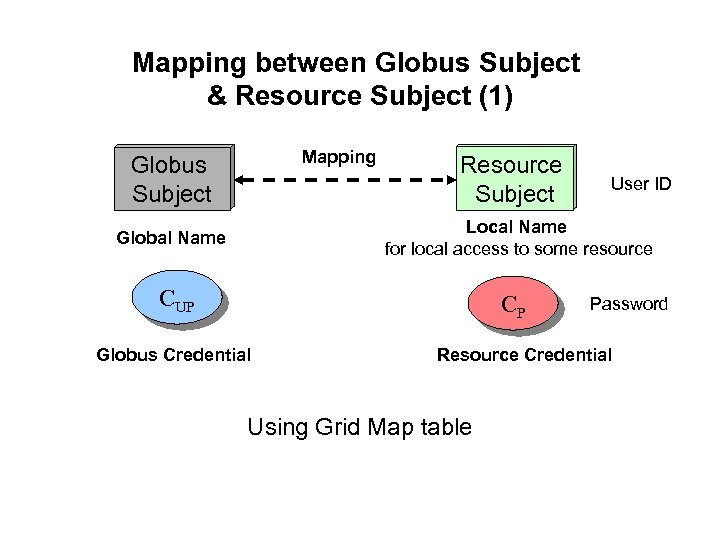 Mapping between Globus Subject & Resource Subject (1) Mapping Globus Subject Resource Subject User ID Local Name for local access to some resource Global Name CUP CP Globus Credential Password Resource Credential Using Grid Map table
Mapping between Globus Subject & Resource Subject (1) Mapping Globus Subject Resource Subject User ID Local Name for local access to some resource Global Name CUP CP Globus Credential Password Resource Credential Using Grid Map table


