bac62d3fcc7432288523d66cc8765a65.ppt
- Количество слайдов: 12
 Security in a Pervasive Computing Environment Mike Chen CS Division, UC Berkeley mikechen@cs. berkeley. edu
Security in a Pervasive Computing Environment Mike Chen CS Division, UC Berkeley mikechen@cs. berkeley. edu
 Security in a Connected World n We want access anytime, anywhere – use pager to trade stock – use Pilot to open doors + buy coke n n Sensitive data and control information flowing across the network. Already have lots of security tools and standards – PGP, SSL, SET, etc. n ? How to scale down to fit small devices?
Security in a Connected World n We want access anytime, anywhere – use pager to trade stock – use Pilot to open doors + buy coke n n Sensitive data and control information flowing across the network. Already have lots of security tools and standards – PGP, SSL, SET, etc. n ? How to scale down to fit small devices?
 Authentication n Who are you? What you have and what you know. Device – knowledge of keys – eg. battlefield sensors w/ hardcoded keys n User – username/passwords – eg. Unix/NT accounts, online stock trading n Device + User – ownership of the device + passwords – eg. ATM cards + PIN
Authentication n Who are you? What you have and what you know. Device – knowledge of keys – eg. battlefield sensors w/ hardcoded keys n User – username/passwords – eg. Unix/NT accounts, online stock trading n Device + User – ownership of the device + passwords – eg. ATM cards + PIN
 Integrity n n What I say is what you hear. Man-in-the-middle attack Alice “Don’t fire!” n Bob “Fire!” Solutions – Checksum? No! Easy to forge. – Message Digest • one-way hash function. eg. MD 5 – Message Authentication Code (MAC) • key-dependent one-way hash function. eg. HMAC
Integrity n n What I say is what you hear. Man-in-the-middle attack Alice “Don’t fire!” n Bob “Fire!” Solutions – Checksum? No! Easy to forge. – Message Digest • one-way hash function. eg. MD 5 – Message Authentication Code (MAC) • key-dependent one-way hash function. eg. HMAC
 Encryption n n Keeping the conversation private. Public keys – advantage: simple key management – disadvantage: slow (20 s on Work. Pad) n Shared keys – advantage: much faster (<1 s on Work. Pad) – disadvantage: key distribution n Lesson: – use shared keys when possible – use a hybrid/proxy design • pub keys between proxy/service and shared keys between device/proxy.
Encryption n n Keeping the conversation private. Public keys – advantage: simple key management – disadvantage: slow (20 s on Work. Pad) n Shared keys – advantage: much faster (<1 s on Work. Pad) – disadvantage: key distribution n Lesson: – use shared keys when possible – use a hybrid/proxy design • pub keys between proxy/service and shared keys between device/proxy.
 Shared Key Secure Sockets n n secure socket layer Java/C implementations, Open Source 1 128 -bit shared authentication key (Ka) 4 Session Keys – one 128 -bit encryption key and one 160 -bit MAC key for each direction – generated using the shared key + the 2 random numbers generated by the device and the service
Shared Key Secure Sockets n n secure socket layer Java/C implementations, Open Source 1 128 -bit shared authentication key (Ka) 4 Session Keys – one 128 -bit encryption key and one 160 -bit MAC key for each direction – generated using the shared key + the 2 random numbers generated by the device and the service
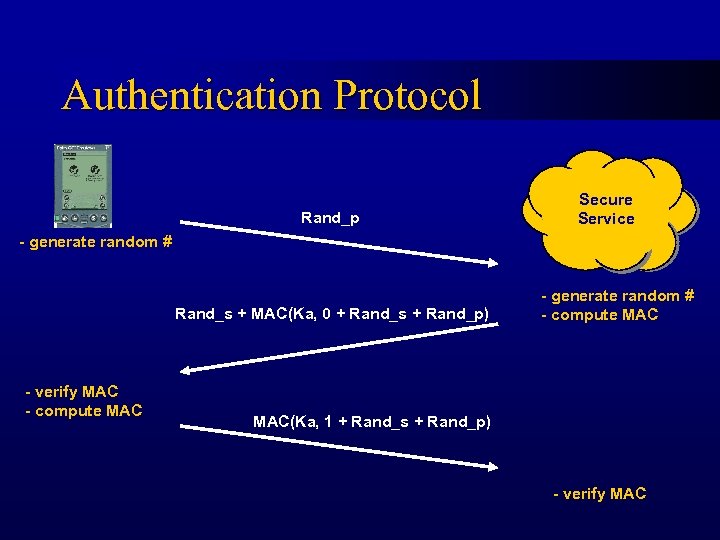 Authentication Protocol Rand_p Secure Service - generate random # Rand_s + MAC(Ka, 0 + Rand_s + Rand_p) - verify MAC - compute MAC - generate random # - compute MAC(Ka, 1 + Rand_s + Rand_p) - verify MAC
Authentication Protocol Rand_p Secure Service - generate random # Rand_s + MAC(Ka, 0 + Rand_s + Rand_p) - verify MAC - compute MAC - generate random # - compute MAC(Ka, 1 + Rand_s + Rand_p) - verify MAC
 Encrypted/MAC’d Transport n MAC – algorithm: HMAC-SHA-1 – HMAC: Keyed-Hashing for Message Authentication – MAC(key, prev. MAC + data) • prevents splicing/replay attacks n Encryption: – algorithm: Blowfish in CBC mode – 2 -3 times faster than 3 DES. (faster than the serial port on Work. Pad!)
Encrypted/MAC’d Transport n MAC – algorithm: HMAC-SHA-1 – HMAC: Keyed-Hashing for Message Authentication – MAC(key, prev. MAC + data) • prevents splicing/replay attacks n Encryption: – algorithm: Blowfish in CBC mode – 2 -3 times faster than 3 DES. (faster than the serial port on Work. Pad!)
 Key Management n 2 128 -bit keys – Authentication Key (Ka): two-way authentication – Encryption Key (Ke): optional encrypted storage n User management – Public Key Infrastructure – Certificate Authority (CA) n Bootstrapping – Use a trusted workstation w/ certificates to setup Authentication key – PDAs fail often => re-generate Authentication Key if necessary
Key Management n 2 128 -bit keys – Authentication Key (Ka): two-way authentication – Encryption Key (Ke): optional encrypted storage n User management – Public Key Infrastructure – Certificate Authority (CA) n Bootstrapping – Use a trusted workstation w/ certificates to setup Authentication key – PDAs fail often => re-generate Authentication Key if necessary
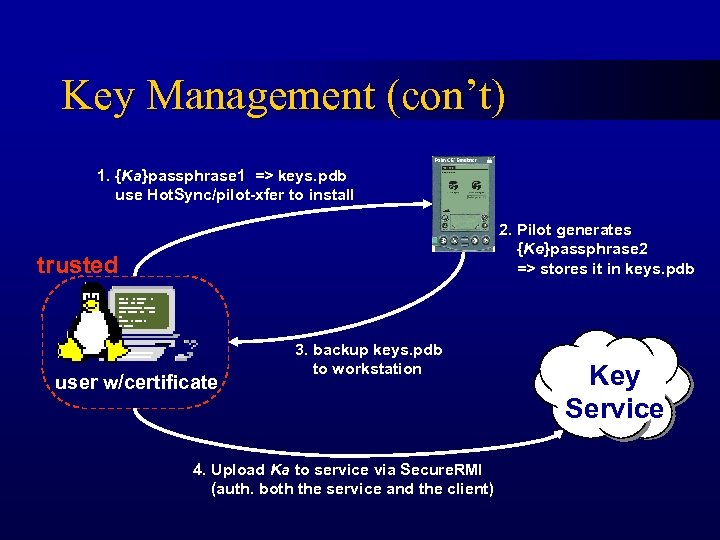 Key Management (con’t) 1. {Ka}passphrase 1 => keys. pdb use Hot. Sync/pilot-xfer to install 2. Pilot generates {Ke}passphrase 2 => stores it in keys. pdb trusted user w/certificate 3. backup keys. pdb to workstation 4. Upload Ka to service via Secure. RMI (auth. both the service and the client) Key Service
Key Management (con’t) 1. {Ka}passphrase 1 => keys. pdb use Hot. Sync/pilot-xfer to install 2. Pilot generates {Ke}passphrase 2 => stores it in keys. pdb trusted user w/certificate 3. backup keys. pdb to workstation 4. Upload Ka to service via Secure. RMI (auth. both the service and the client) Key Service
 Security in the Proxy World n The Trusted Computing Base (TCB) is the smallest part of your computer/network that you need to trust for the system to be “secure” AP n The TCB now includes the proxy.
Security in the Proxy World n The Trusted Computing Base (TCB) is the smallest part of your computer/network that you need to trust for the system to be “secure” AP n The TCB now includes the proxy.
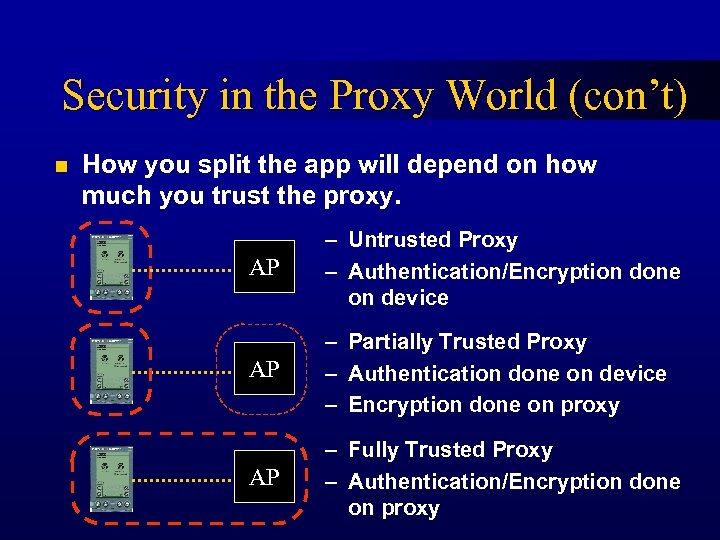 Security in the Proxy World (con’t) n How you split the app will depend on how much you trust the proxy. AP – Untrusted Proxy – Authentication/Encryption done on device AP – Partially Trusted Proxy – Authentication done on device – Encryption done on proxy AP – Fully Trusted Proxy – Authentication/Encryption done on proxy
Security in the Proxy World (con’t) n How you split the app will depend on how much you trust the proxy. AP – Untrusted Proxy – Authentication/Encryption done on device AP – Partially Trusted Proxy – Authentication done on device – Encryption done on proxy AP – Fully Trusted Proxy – Authentication/Encryption done on proxy


