4276f870d637c1268ffd2a9ba37aada6.ppt
- Количество слайдов: 73
Security II – Grid Computing Security and Globus Security

Aspects Grid computing involves setting up a virtual organization for the project: – Setting up the resources that will be used. – Identifying the users – Creating a security policy across sites

Virtual Organization Security Issues Need to establish and enforce terms of sharing. • VO-wide identification of users and services • Authentication across administrative domains • Authorization policy across administrative domains • Trust across administrative domains

• Dynamics – Changing community roles, members • Scaling – Support for large numbers of resources and users • Policy – VO and stakeholder control of priorities Modified form a slide by Ian Foster

Grid security must define mechanisms for identity, policy, and trust across autonomous domains with minimal arrangements. Modified form a slide by Ian Foster
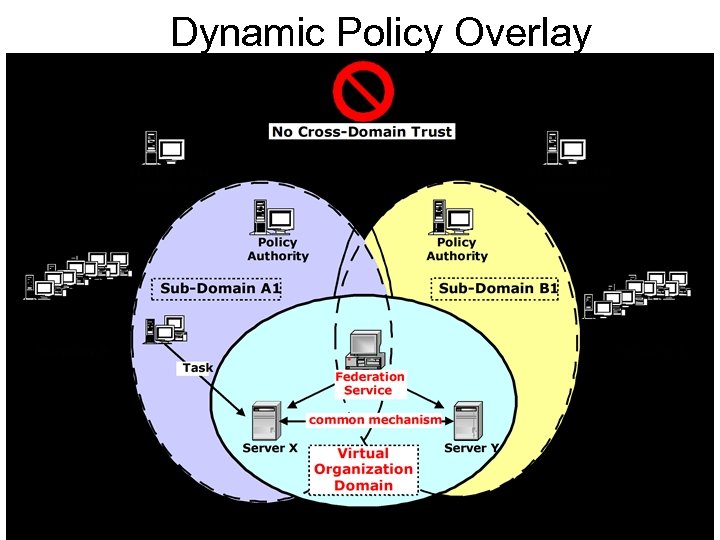
Dynamic Policy Overlay Slide by Ian Foster

Globus Grid Security Infrastructure (GSI) • A set of tools, libraries, and protocols to allow users and applications to access resources securely in a grid computing environment.

Globus Grid Security Infrastructure (GSI) • Based upon public key infrastructure with certificate authorities and X 509 certificates. • GT 2 components use SSL for authentication and message protection. • GT 4 can use WS-Security protocols – extensions to SOAP messaging for security
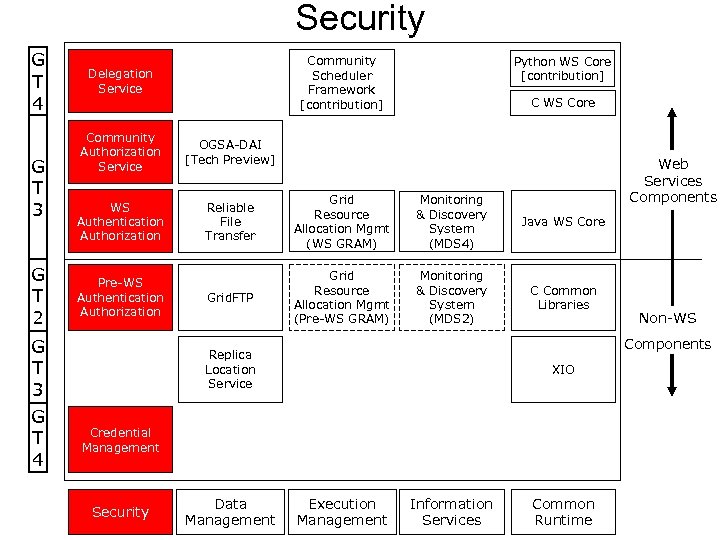
Security G T 4 G T 3 G T 2 G T 3 G T 4 Community Scheduler Framework [contribution] Delegation Service Python WS Core [contribution] C WS Core Community Authorization Service OGSA-DAI [Tech Preview] WS Authentication Authorization Reliable File Transfer Grid Resource Allocation Mgmt (WS GRAM) Monitoring & Discovery System (MDS 4) Java WS Core Grid. FTP Grid Resource Allocation Mgmt (Pre-WS GRAM) Monitoring & Discovery System (MDS 2) C Common Libraries Pre-WS Authentication Authorization Web Services Components Replica Location Service XIO Credential Management Security Data Management Non-WS Execution Management Information Services Common Runtime

Three important factors in grid computing are: • Authorization – Process of deciding whether a particular identity can access a particular resource • Authentication – Process of deciding whether a particular identity is who he says he is (applies to humans and systems) • Delegation (somewhat specific to grid computing) – Process of giving authority to another identity (usually a computer/process) to act on your behalf.
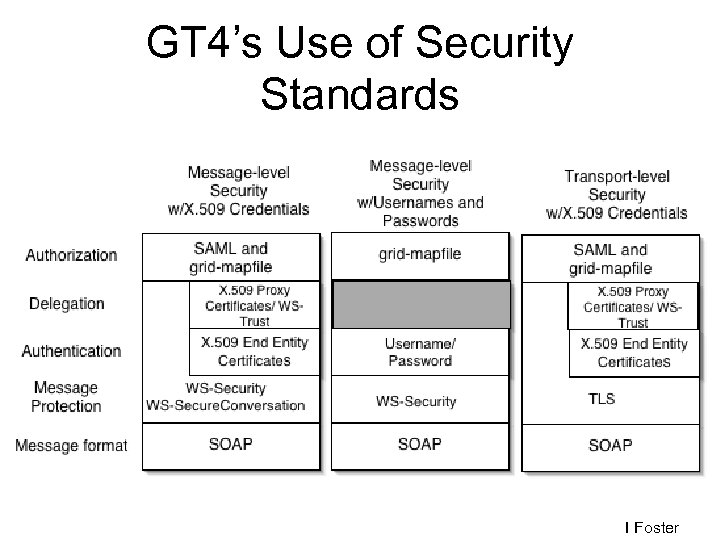
GT 4’s Use of Security Standards I Foster

Authentication Process of deciding whether a particular identity is who he says he is (applies to humans and systems)

GSI Authentication Each user has set of credentials they use to prove their identity on the grid. Consists of: – X 509 certificate and – private key • Long-term private key kept encrypted with a pass phrase – Good for security, inconvenient for repeated usage

Certificate Authorities • Grid computing group (virtual organization) requires one or more CAs to control access to their grid. • Generally set up CA’s specifically for grid computing virtual organization.

Certificate Authority for Grid Computing • Usually a certificate authority is created for the specific grid computing environment. • Globus has “simple” implementation called simple. CA.

Grid Users • After Certificate Authority established for grid, users have to register with grid CA. • Users joining a grid from geographically dispersed locations must communicate with the CA system administrator to verify their identity and to get a certificate. • Communication often done by email!

Setting up a CA • Globus Simple. CA – For use with small projects with simple requirements. • Globus Certificate Service – For testing only (example use in sticky note assignment exercise 10). • Design your own CA or use existing one.
Single CA • Some grids have established a single CA for the virtual organization. Example • UK e-Science grid has a centralized CA.

Trans-European Research and Education Networking Association Provides a list of CAs with access to their certificates: http: //www. terena. nl/tech/task-forces/ tf-aace/tacar/certs. html
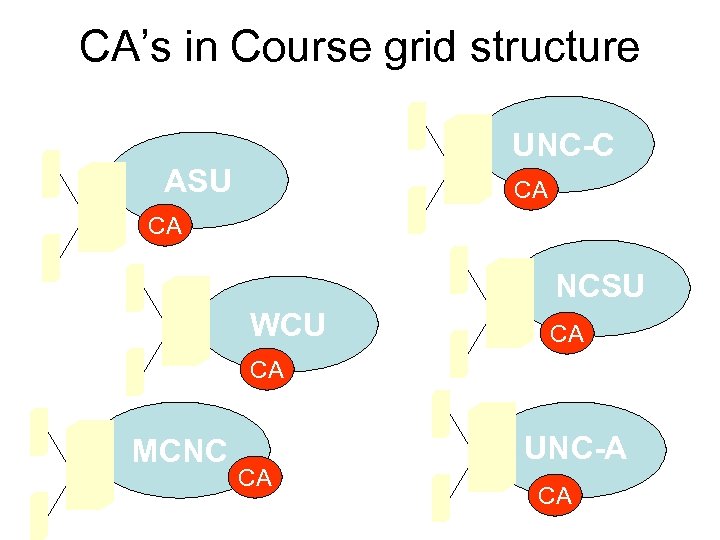
CA’s in Course grid structure UNC-C ASU CA CA NCSU WCU CA CA MCNC CA UNC-A CA
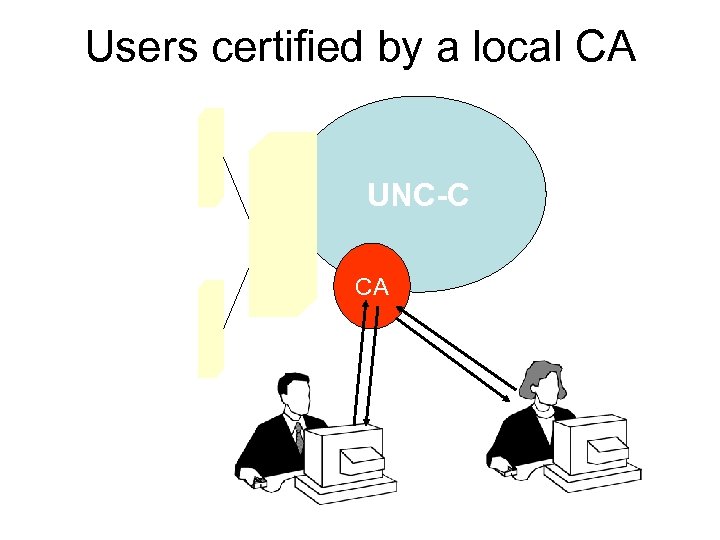
Users certified by a local CA UNC-C CA

Configuring GT 4 to Trust a Particular Certificate Authority GT 4 can be configured to accept certificates from multiple CAs. • Needs to know the CA’s to accept. • Consists of loading two files describing each CA: – cert_hash. 0 The trusted CA certificate – cert_hash. signing_policy A configuration file defining the distinguished names of certificates signed by the CA
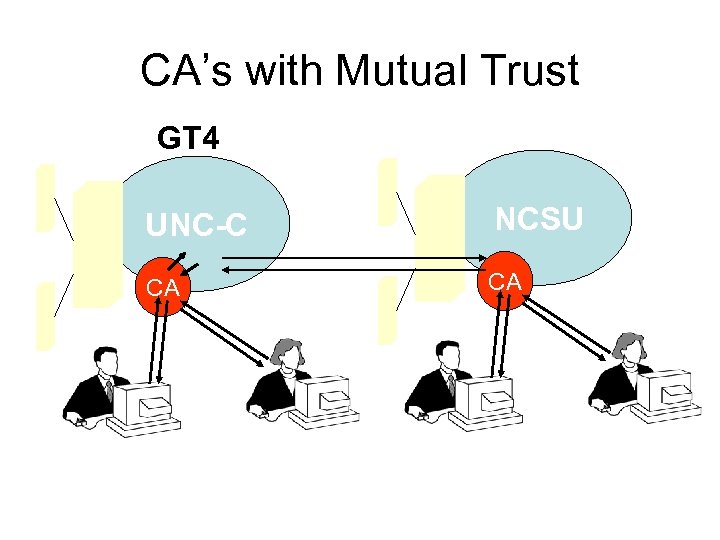
CA’s with Mutual Trust GT 4 UNC-C NCSU CA CA
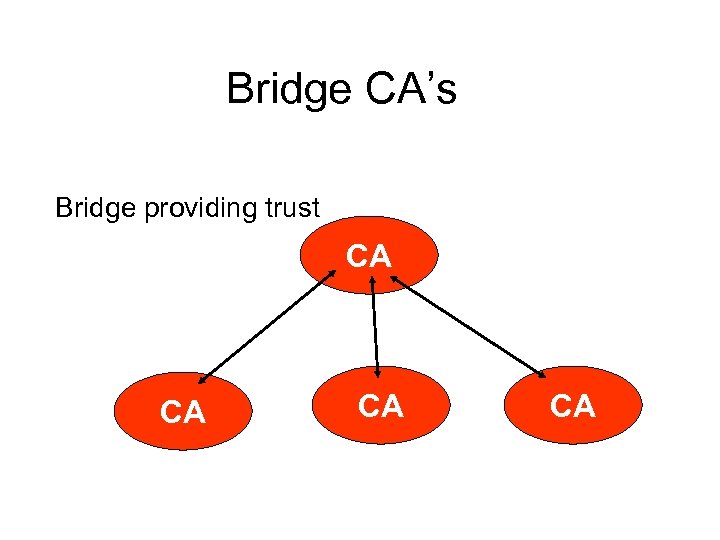
Bridge CA’s Bridge providing trust CA CA
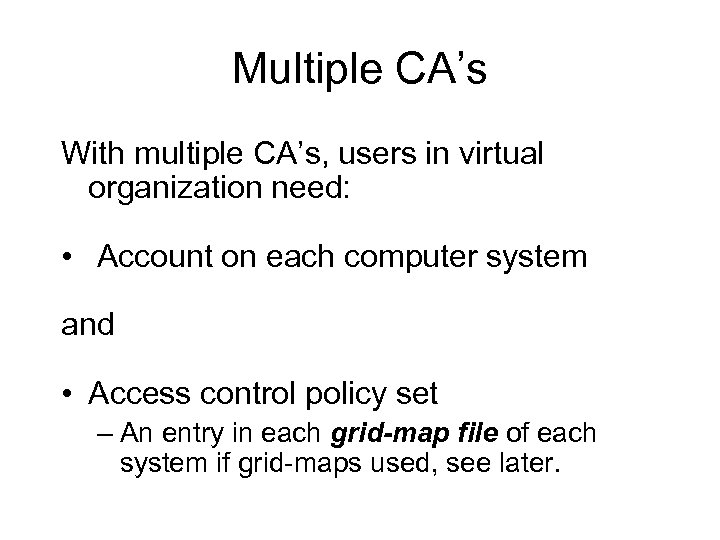
Multiple CA’s With multiple CA’s, users in virtual organization need: • Account on each computer system and • Access control policy set – An entry in each grid-map file of each system if grid-maps used, see later.

Need to specify polices and how to establish subject’s identity.
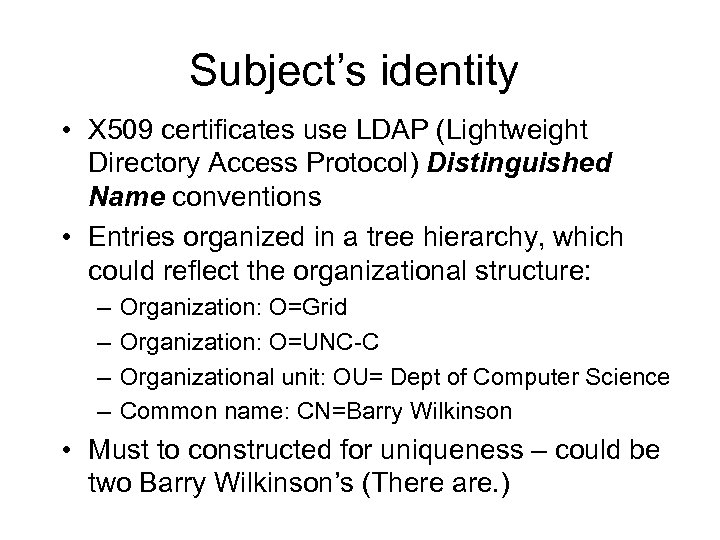
Subject’s identity • X 509 certificates use LDAP (Lightweight Directory Access Protocol) Distinguished Name conventions • Entries organized in a tree hierarchy, which could reflect the organizational structure: – – Organization: O=Grid Organization: O=UNC-C Organizational unit: OU= Dept of Computer Science Common name: CN=Barry Wilkinson • Must to constructed for uniqueness – could be two Barry Wilkinson’s (There are. )

Sample Distinguishing Name used at NCSU /O=NCSU/OU=HPC/OU=unity. ncsu. edu/C N=Barry Wilkinson
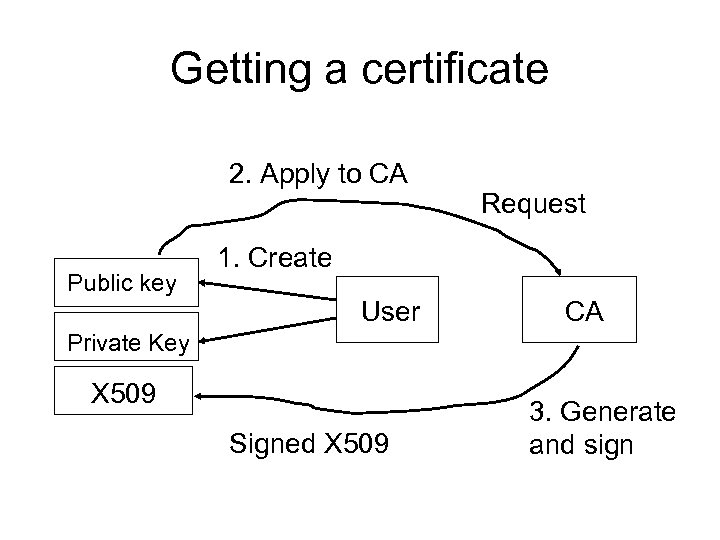
Getting a certificate 2. Apply to CA Public key Request 1. Create User CA Private Key X 509 Signed X 509 3. Generate and sign
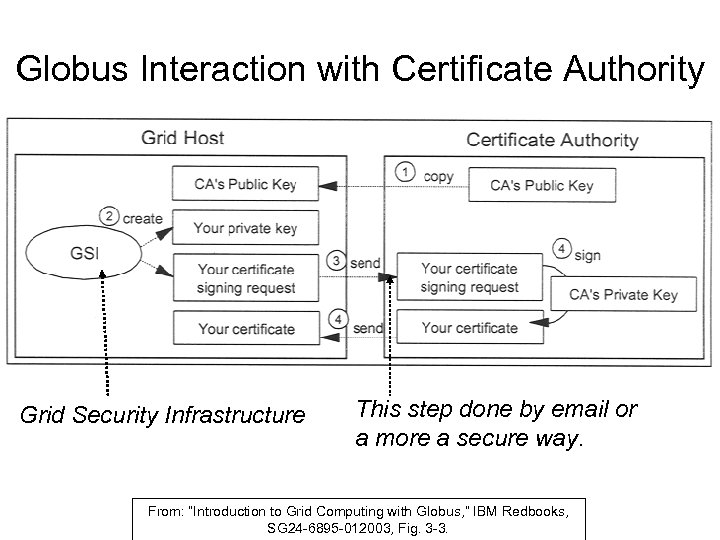
Globus Interaction with Certificate Authority Grid Security Infrastructure This step done by email or a more a secure way. From: “Introduction to Grid Computing with Globus, ” IBM Redbooks, SG 24 -6895 -012003, Fig. 3 -3.

grid-cert-request • Globus command to run to get certificate. • Requests a pass phrase. • Can be used to get user certificates, host certificates and CA’s own certificate (chosen with grid-cert-request flags).
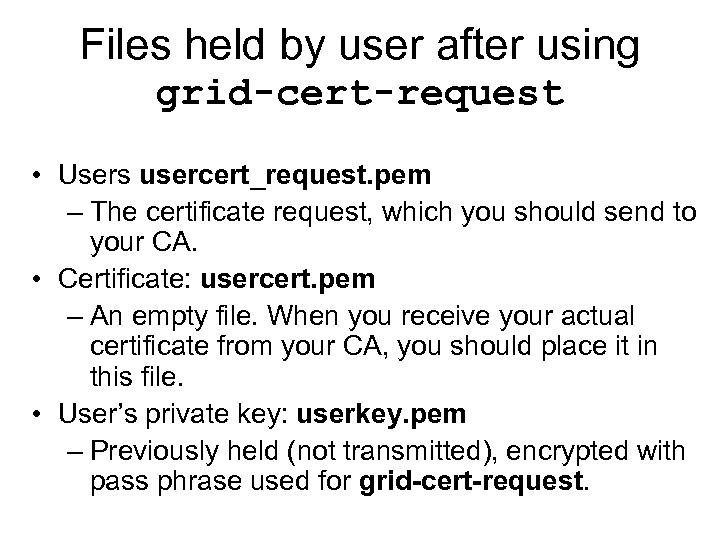
Files held by user after using grid-cert-request • Users usercert_request. pem – The certificate request, which you should send to your CA. • Certificate: usercert. pem – An empty file. When you receive your actual certificate from your CA, you should place it in this file. • User’s private key: userkey. pem – Previously held (not transmitted), encrypted with pass phrase used for grid-cert-request.
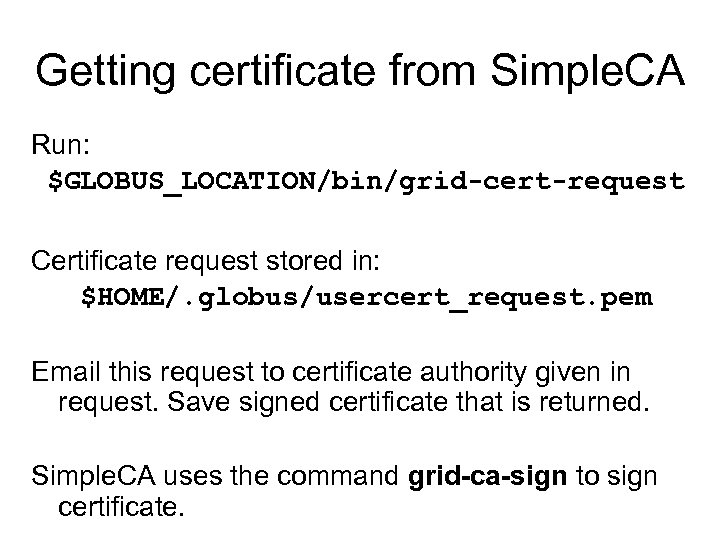
Getting certificate from Simple. CA Run: $GLOBUS_LOCATION/bin/grid-cert-request Certificate request stored in: $HOME/. globus/usercert_request. pem Email this request to certificate authority given in request. Save signed certificate that is returned. Simple. CA uses the command grid-ca-sign to sign certificate.
Grid Computers • Computers added to a grid (donors) preferably need their identity verified in a similar fashion. • Computers registered with certificate authority - only those machines will be allowed to participate in the grid activities. • Computers might be used under a certain access rights.

GSI Authentication Originally based on SSL protocol where one passes an encrypted random number between parties

B authenticating host A’s certificate • Host A send its certificate to Host B. • Host B gets Host A’s public key and name using CA’s public key. • Host B creates a random number and sends it to Host A. • Host A encrypts random number with its private key and sends it to host B. • Host B decrypts number and checks number. If correct, Host B authenticates host A’s certificate.
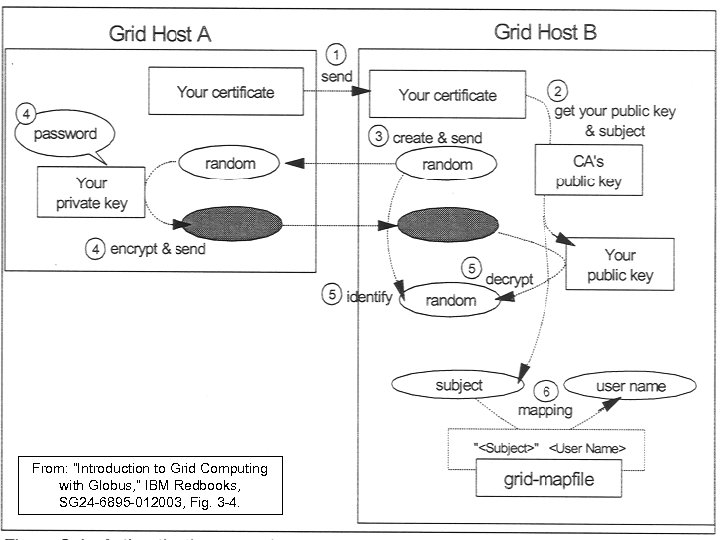
From: “Introduction to Grid Computing with Globus, ” IBM Redbooks, SG 24 -6895 -012003, Fig. 3 -4.

Mutual Authentication Two parties proving to each other that they are who they say they are. Mutual authentication involves the previous process done both ways. Both parties need to trust CAs that signed each other's certificates.

GSI Mutual Authentication • Before mutual authentication can occur, parties involved must first trust CAs that signed each other's certificates. – In practice, this means that they must have copies of the CAs' certificate, which contain the CAs' public keys, and that they trust that these certificates really belong to the CAs.

Mutual Authentication cont. To start the authentication process, : • A gives B his certificate. • B will first make sure that certificate valid by checking CA's digital signature to make sure that the CA actually signed the certificate and that the certificate hasn't been tampered with. (This is where B must trust the CA that signed A's certificate. ) Once B has checked out A's certificate, B must make sure that A really is the person identified in the certificate.
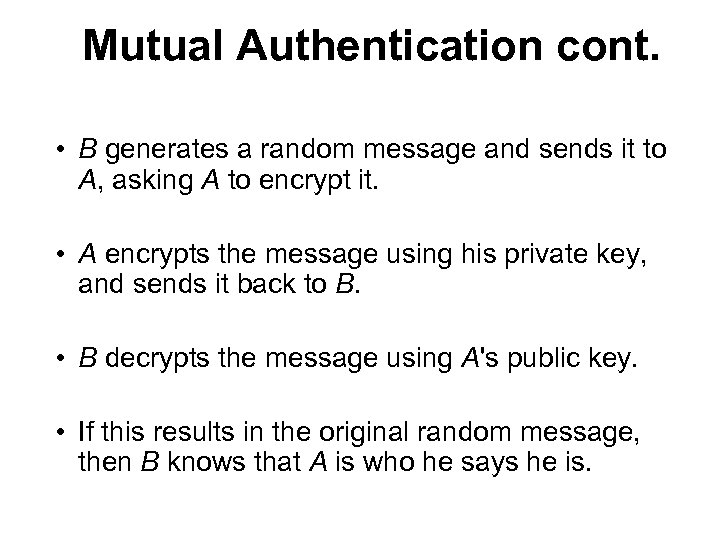
Mutual Authentication cont. • B generates a random message and sends it to A, asking A to encrypt it. • A encrypts the message using his private key, and sends it back to B. • B decrypts the message using A's public key. • If this results in the original random message, then B knows that A is who he says he is.

Mutual Authentication cont. • Now that B trusts A's identity, the same operation must happen in reverse. • B sends A her certificate, A validates the certificate and sends a challenge message to be encrypted. • B encrypts the message and sends it back to A, and A decrypts it and compares it with the original. • If it matches, then A knows that B is who she says she is. At this point, A and B have established a connection to each other and are certain that they know each others' identities.

Confidential Communication after Mutual Authentication By default, GSI does not establish confidential (encrypted) communication between parties. Communication can occur without the overhead of constant encryption and decryption. GSI can easily be used to establish a shared key for encryption if confidential communication is desired.

Communication integrity Means that an eavesdropper may be able to read communication between two parties but is not able to modify the communication in any way. GSI provides communication integrity by default. (It can be turned off if desired). Communication integrity introduces some overhead in communication, but not as large as encryption.

Authorization Process of deciding whether a particular identity can access a particular resource and what fashion.

GSI Authorization Classical way of doing authorization is an access control list, listing the identities of those allowed and the type of access allowed. • A grid could use a similar approach, using a grid-map file
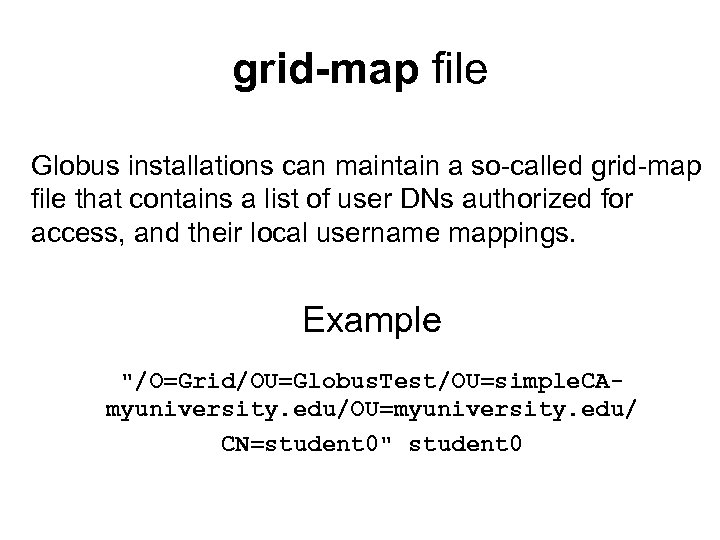
grid-map file Globus installations can maintain a so-called grid-map file that contains a list of user DNs authorized for access, and their local username mappings. Example "/O=Grid/OU=Globus. Test/OU=simple. CAmyuniversity. edu/OU=myuniversity. edu/ CN=student 0" student 0

Other ways of doing authorization Grid-map file a very primitive way which does not scale well. Other ways • SAML – Security Assertions Markup Language, a OASIS standard – Allows to communicate user authentication, authorization and attribute information • Communication Authorization Service (CAS)

Community Authorization Service CAS To handle the situation of many users and many resources. If each resource were to maintain access policies for each user, will not scale. Delegate authorization to CAS to handle authorization for resources.
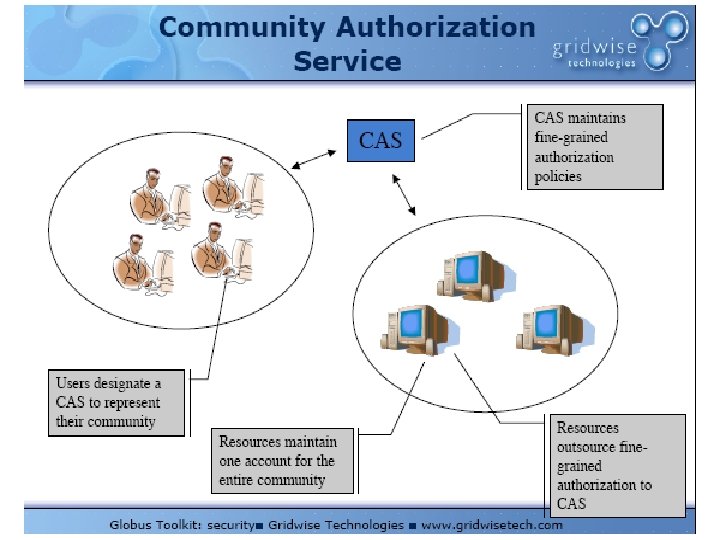
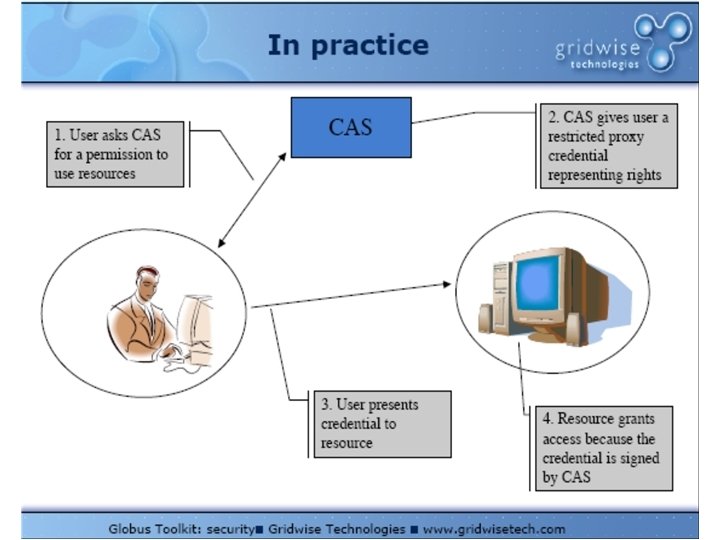
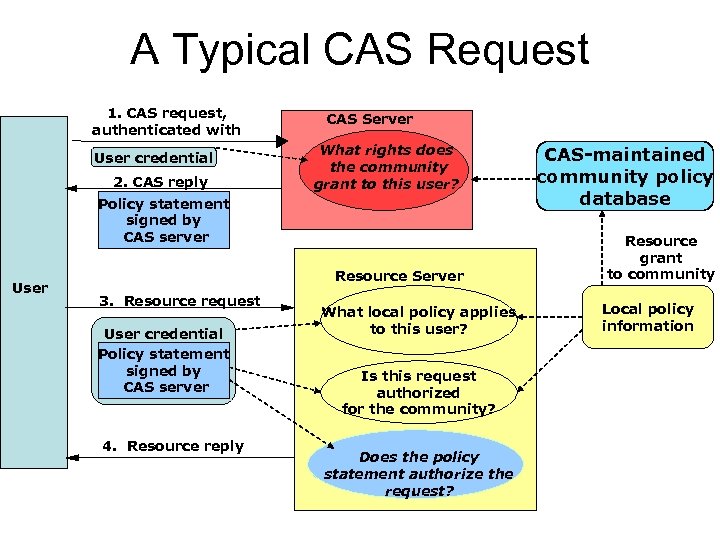
A Typical CAS Request 1. CAS request, authenticated with User credential 2. CAS reply CAS Server What rights does the community grant to this user? Policy statement signed by CAS server User Resource Server 3. Resource request User credential Policy statement signed by CAS server 4. Resource reply What local policy applies to this user? Is this request authorized for the community? Does the policy statement authorize the request? CAS-maintained community policy database Resource grant to community Local policy information

Delegation • Process of giving authority to another identity (usually a computer/process) to act on your behalf. • Single sign-on -- to enable user and it’s agents to acquire additional resources without repeated authentication (passwords).

GSI Delegation • Uses additional certificates passed between intermediate parties. • Certificates called proxies. • An extension to the standard SSL/TLS protocol.

Proxy • Consists of a new certificate with new public, private keys, and owner’s identify (/CN=proxy added to name). • Certificate signed by owner (not CA) • Proxy given limited lifetimes • Proxy’s private key does not need to be kept as secure as owner’s private key - setting file permissions usually sufficient

Use of proxy certificates • Single sign-on • Create local proxy with say 12 hours lifetime. – Use proxy instead of your certificate – Password typing only once. – No password down wire. • Delegation – Allows a remote entity to perform tasks on your behalf, and access to your resources • Mutual trust domains – All entities with proxies from same issuer will trust each other
• Proxies used to authenticate users and run user programs on grid. • Proxy created with grid-proxy-int command. • We shall see a use of this in assignment 3.

Proxy Certificate • Commands: – Grid-proxy-init – Grid-proxy-info – Grid-proxy-destroy • In GT: – User cert is password protected – Proxy cert is filesystem protected (/tmp)
Delegation authority to another host • Suppose host A wishes to delegate authority to host B to act on its behalf with host C. • Rather a large number of internal steps.
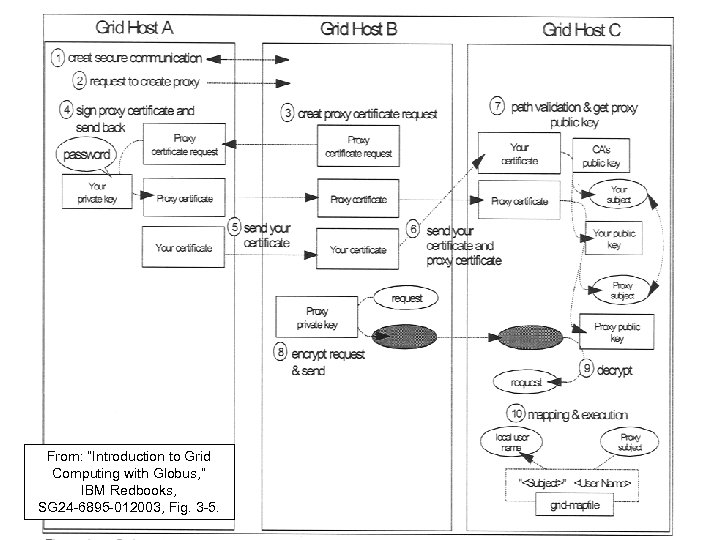
From: “Introduction to Grid Computing with Globus, ” IBM Redbooks, SG 24 -6895 -012003, Fig. 3 -5.

Chain of trust Continuing this process can have host B delegate authority to host C, host C delegate to host D, etc.
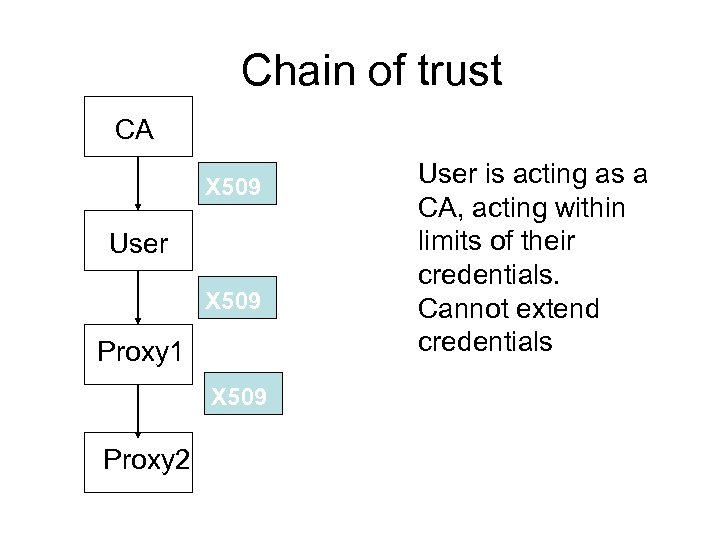
Chain of trust CA X 509 User X 509 Proxy 1 X 509 Proxy 2 User is acting as a CA, acting within limits of their credentials. Cannot extend credentials
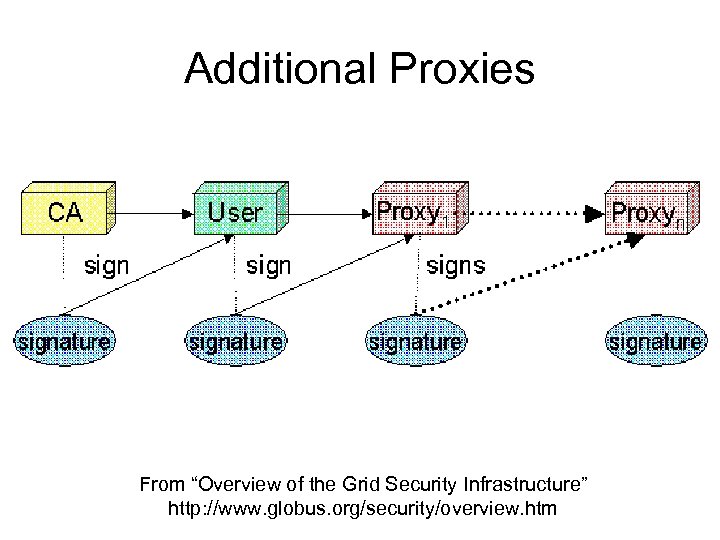
Additional Proxies From “Overview of the Grid Security Infrastructure” http: //www. globus. org/security/overview. htm

Mutual Authentication with Proxies • Remote party receives owner’s certificate and owner’s proxy certificate. Chain of trust • Owner’s public key from owner’s certificate used to validate proxy signature on proxy certificate. • Certificate authority (CA) public key used to validate owner’s signature on owner’s certificate

• On grid, each party identifies itself with credentials. • Credentials vulnerable to theft. • No easy way of canceling stolen credentials.

My. Proxy • My. Proxy is a Grid credential repository. • Reduces risk of management of many copies of credentials.

Summary

GT 4 Grid Security Components (from GT 4 documentation) • Basic Security Mechanisms • Components for Credential Generation • Components for Credential Management • Components for Access Control and Authorization

Basic Security Mechanisms • Pre-Web Services Authentication and Authorization - A non-Web services implementation of GSI, containing core libraries and tools needed to secure applications. • Web Services Authentication and Authorization - A Web services implementation of GSI, containing core libraries and tools needed to secure applications.

Components for Credential Generation • Globus Certificate Service - An online service that issues low-quality GSI certificates to users who want to experiment with Grid software but don't have any other means to acquire certificates • Simple CA - A convenient method of issuing certificates for users and services that work with GSI and WS-Security
Components for Credential Management • My. Proxy - A network service that stores user credentials so they can be accessed from other systems on the network Also: • KX. 509 and KCA - A system for providing Kerberos users with Grid credentials without operating a conventional Certificate Authority • PKINIT - A mechanism that allows a Kerberos ticket to be obtained using a Grid credential rather than a Kerberos passphrase.

Components for Access Control and Authorization • Community Authorization Service (CAS) - A service that allows resource providers to specify course-grained access control policies in terms of communities as a whole, delegating fine-grained access control policy management to the community itself.

Components for Access Control and Authorization Also: • Shibboleth - A set of services that leverage existing user authentication and authorization systems at "home institutions" to give remote services the information they need to make authorization decisions. • VOMS - A database-driven mechanism for central management of user role and capability data
4276f870d637c1268ffd2a9ba37aada6.ppt