206e9b6e5b435024f1a6d4bb3669ebce.ppt
- Количество слайдов: 31

 Security History in San Antonio • In 1985 the Air Force consolidated their computer security missions at Kelly AFB, combining Computer, Communications, and Emanations security disciplines • The Air Force Computer Emergency Response Team (AFCERT) and the Air Force Information Warfare Center (AFIWC) created in the early ’ 90 s • Charted the course for the military services and private sector and has made San Antonio a hub of security activity. • National and local companies reside in S. A. supporting information and infrastructure security missions
Security History in San Antonio • In 1985 the Air Force consolidated their computer security missions at Kelly AFB, combining Computer, Communications, and Emanations security disciplines • The Air Force Computer Emergency Response Team (AFCERT) and the Air Force Information Warfare Center (AFIWC) created in the early ’ 90 s • Charted the course for the military services and private sector and has made San Antonio a hub of security activity. • National and local companies reside in S. A. supporting information and infrastructure security missions
 Others recognize our dependence on the different critical infrastructures “An adversary wishing to destroy the United States only has to mess up the computer systems of its banks by hi-tech means. This would disrupt and destroy the US economy. If we overlook this point and simply rely on the building of a costly standing army…. it is as good as building a contemporary Maginot Line. ” - Peoples Liberation Daily Peoples Republic of China
Others recognize our dependence on the different critical infrastructures “An adversary wishing to destroy the United States only has to mess up the computer systems of its banks by hi-tech means. This would disrupt and destroy the US economy. If we overlook this point and simply rely on the building of a costly standing army…. it is as good as building a contemporary Maginot Line. ” - Peoples Liberation Daily Peoples Republic of China
 Critical Infrastructures as identified by the President’s Critical Infrastructure Protection Board • • • • banking and finance information and telecommunications transportation postal and shipping emergency services continuity of government public health food energy water chemical industry and hazardous materials agriculture defense industrial base
Critical Infrastructures as identified by the President’s Critical Infrastructure Protection Board • • • • banking and finance information and telecommunications transportation postal and shipping emergency services continuity of government public health food energy water chemical industry and hazardous materials agriculture defense industrial base
 UTSA Center of Excellence for Bioprocessing Biotechnology Education and Research (CEBBER) Center for Response and Security Engineering & Technology (CRSET) Center for Infrastructure Assurance and Security (CIAS)
UTSA Center of Excellence for Bioprocessing Biotechnology Education and Research (CEBBER) Center for Response and Security Engineering & Technology (CRSET) Center for Infrastructure Assurance and Security (CIAS)
 “Terrorism Law is an emerging discipline critical to understanding the complex balance between global security and civil justice. ”
“Terrorism Law is an emerging discipline critical to understanding the complex balance between global security and civil justice. ”
 The Center for Infrastructure Assurance and Security (CIAS) • The CIAS Mission: – Develop and proliferate operationally based strategies, techniques and technologies – through training, education, economic development, partnerships, and research – to ensure the integrity and security of our nation’s infrastructure and organizations that are dependent upon complex information and control systems. • The CIAS Vision: – Propel the Infrastructure Security consciousness and readiness of our nation and its leaders through cutting edge and mission critical training, education, research, and industry-government-academia partnerships.
The Center for Infrastructure Assurance and Security (CIAS) • The CIAS Mission: – Develop and proliferate operationally based strategies, techniques and technologies – through training, education, economic development, partnerships, and research – to ensure the integrity and security of our nation’s infrastructure and organizations that are dependent upon complex information and control systems. • The CIAS Vision: – Propel the Infrastructure Security consciousness and readiness of our nation and its leaders through cutting edge and mission critical training, education, research, and industry-government-academia partnerships.
 The Center for Infrastructure Assurance and Security (CIAS) • The Goals of the CIAS are focused on four major areas: – Training and Education – Local and National Outreach – Exercises – Services and Assessments
The Center for Infrastructure Assurance and Security (CIAS) • The Goals of the CIAS are focused on four major areas: – Training and Education – Local and National Outreach – Exercises – Services and Assessments
 The Center for Infrastructure Assurance and Security (CIAS) Training and Education Voice and Data Security Cyber Forensics Intrusion Detection Incident Response Local and National Outreach Seminars/Conferences Collegiate Cyber Defense Competition Cyber First Respondertm Program K-12 programs ITSA 9/11 Memorial Services and Assessments UT-System Security Assessment Exercises Community Cyber Security Exercisestm Dark Screen Corpus Christi Del Rio Dayton Oklahoma City Hampton Roads State of Texas (Plano/Tyler/Austin) Sector-based exercises Financial Services Oil & Gas Chemical IT & Telecommunications State Exercises Texas
The Center for Infrastructure Assurance and Security (CIAS) Training and Education Voice and Data Security Cyber Forensics Intrusion Detection Incident Response Local and National Outreach Seminars/Conferences Collegiate Cyber Defense Competition Cyber First Respondertm Program K-12 programs ITSA 9/11 Memorial Services and Assessments UT-System Security Assessment Exercises Community Cyber Security Exercisestm Dark Screen Corpus Christi Del Rio Dayton Oklahoma City Hampton Roads State of Texas (Plano/Tyler/Austin) Sector-based exercises Financial Services Oil & Gas Chemical IT & Telecommunications State Exercises Texas
 The CIAS • Information Assurance Research Center supporting UTSA – One of 66 universities with the NSA COAE designation • Cooperative Effort – Air Intelligence Agency (AIA) – Local City/County Government – Academia – Private Sector
The CIAS • Information Assurance Research Center supporting UTSA – One of 66 universities with the NSA COAE designation • Cooperative Effort – Air Intelligence Agency (AIA) – Local City/County Government – Academia – Private Sector
 CIAS Original Research Areas • • • Steganography Data Mining Wireless Encryption Intrusion Detection Cyber Security Exercises (Dark Screen & ISACs) • Researchers from Colleges of Business (Information Systems), Engineering and Computer Science • Partnership with St. Mary’s University Law School and its Center for Terrorism Law to examine the many legal aspects relating to cyber security and information sharing among city/state/national level agencies
CIAS Original Research Areas • • • Steganography Data Mining Wireless Encryption Intrusion Detection Cyber Security Exercises (Dark Screen & ISACs) • Researchers from Colleges of Business (Information Systems), Engineering and Computer Science • Partnership with St. Mary’s University Law School and its Center for Terrorism Law to examine the many legal aspects relating to cyber security and information sharing among city/state/national level agencies
 New Research Areas • Examination of bi-modal techniques in biometrics • Spam detection and elimination • Detection of intrusive activity in mobile adhoc networks • Countering fast-spreading malicious worms • Privacy in database operations
New Research Areas • Examination of bi-modal techniques in biometrics • Spam detection and elimination • Detection of intrusive activity in mobile adhoc networks • Countering fast-spreading malicious worms • Privacy in database operations
 CIAS Competition and Exercise Program • • High School Collegiate Scenario-based Community © 2006 Center for Infrastructure Assurance and Security (CIAS)
CIAS Competition and Exercise Program • • High School Collegiate Scenario-based Community © 2006 Center for Infrastructure Assurance and Security (CIAS)
 © 2005 Center for Infrastructure Assurance and Security (CIAS)
© 2005 Center for Infrastructure Assurance and Security (CIAS)
 High School Cyber Defense Competition • Conducted with local high schools • Best paper, Individual, and Team components (only AFJROTC teams) • Sponsored by AFA, ISACA, and ISSA • Written and hands-on portions to the competition • Scholarships awarded to winners in various categories © 2006 Center for Infrastructure Assurance and Security (CIAS)
High School Cyber Defense Competition • Conducted with local high schools • Best paper, Individual, and Team components (only AFJROTC teams) • Sponsored by AFA, ISACA, and ISSA • Written and hands-on portions to the competition • Scholarships awarded to winners in various categories © 2006 Center for Infrastructure Assurance and Security (CIAS)
 © 2006 Center for Infrastructure Assurance and Security (CIAS)
© 2006 Center for Infrastructure Assurance and Security (CIAS)
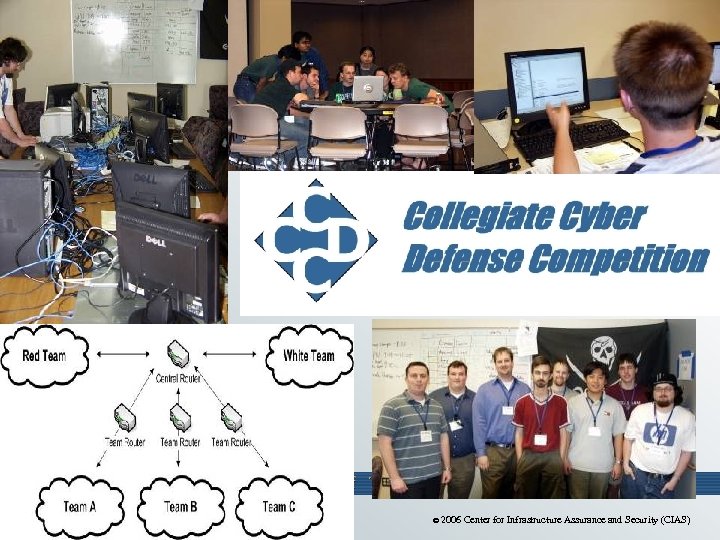
 CCDC • An information assurance/network security exercise at the regional and national level • Similar to the CDX the military academies have been conducting over the past several years • Competition focused on business processes and technology – DEFENSIVE ONLY • Not a hack and defend or capture the flag • Sponsors include DHS, ISSA, Cisco Systems, Acronis, Northrup Grumman, Tipping. Point, Internet Security Systems, Citadel, and O’Reilly © 2006 Center for Infrastructure Assurance and Security (CIAS)
CCDC • An information assurance/network security exercise at the regional and national level • Similar to the CDX the military academies have been conducting over the past several years • Competition focused on business processes and technology – DEFENSIVE ONLY • Not a hack and defend or capture the flag • Sponsors include DHS, ISSA, Cisco Systems, Acronis, Northrup Grumman, Tipping. Point, Internet Security Systems, Citadel, and O’Reilly © 2006 Center for Infrastructure Assurance and Security (CIAS)
 CCDC • Each team is given an identical “business” network to manage and defend • Business tasks are given to teams throughout the competition • Independent red team used to test networks during competition • Neutral white team runs and scores the competition • Teams are scored based on their ability to defend their networks against attack and complete the business tasks in a timely and secure manner © 2006 Center for Infrastructure Assurance and Security (CIAS)
CCDC • Each team is given an identical “business” network to manage and defend • Business tasks are given to teams throughout the competition • Independent red team used to test networks during competition • Neutral white team runs and scores the competition • Teams are scored based on their ability to defend their networks against attack and complete the business tasks in a timely and secure manner © 2006 Center for Infrastructure Assurance and Security (CIAS)
 CCDC • First competition held April 15 -17, 2005 at UTSA • 5 regionals and first national competition held in 2006 • 7 -10 regionals and second national competition will be held in 2007 © 2006 Center for Infrastructure Assurance and Security (CIAS)
CCDC • First competition held April 15 -17, 2005 at UTSA • 5 regionals and first national competition held in 2006 • 7 -10 regionals and second national competition will be held in 2007 © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Why run exercises • • • Promote awareness Provide Training Evaluate plans, procedures, and responses • Identify gaps • Test a community’s ability to prevent, detect, and respond to cyber security events © 2006 Center for Infrastructure Assurance and Security (CIAS)
Why run exercises • • • Promote awareness Provide Training Evaluate plans, procedures, and responses • Identify gaps • Test a community’s ability to prevent, detect, and respond to cyber security events © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Scenario-based Exercises • The CIAS conducts scenario-based tabletop exercises • Each exercise is built around a central idea • Exercises have multiple events designed to depict a plausible reality • Each exercise is researched, designed, and customized for that specific community • We focus on cyber elements in our exercises but don’t exclude physical © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • The CIAS conducts scenario-based tabletop exercises • Each exercise is built around a central idea • Exercises have multiple events designed to depict a plausible reality • Each exercise is researched, designed, and customized for that specific community • We focus on cyber elements in our exercises but don’t exclude physical © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Scenario-based Exercises • Our exercises have fallen into two major groupings: – Sector-based for the Information Sharing and Analysis Centers (ISACs) and Critical Infrastructures – City-based © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • Our exercises have fallen into two major groupings: – Sector-based for the Information Sharing and Analysis Centers (ISACs) and Critical Infrastructures – City-based © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Scenario-based Exercises • Sector Exercises – One to Two day events – Are highly technical – Multiple scenarios with multiple events – Have performed 7 exercises with the Financial, IT, Oil and Gas, and Chemical Sectors as well as the ISAC Congress – Conducted with USSS and DHS © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • Sector Exercises – One to Two day events – Are highly technical – Multiple scenarios with multiple events – Have performed 7 exercises with the Financial, IT, Oil and Gas, and Chemical Sectors as well as the ISAC Congress – Conducted with USSS and DHS © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Scenario-based Exercises • City Exercises – Generally half day events – Less technical, more awareness – Multiple scenarios with multiple events – Have been performed with San Antonio, Corpus Christi, Del Rio, Virginia Beach, Dayton, and the State of Texas – Future exercises with Omaha, Colorado Springs, and Honolulu © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • City Exercises – Generally half day events – Less technical, more awareness – Multiple scenarios with multiple events – Have been performed with San Antonio, Corpus Christi, Del Rio, Virginia Beach, Dayton, and the State of Texas – Future exercises with Omaha, Colorado Springs, and Honolulu © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Scenario-based Exercises • Each exercise is customized to the community • Participants are drawn from various organizations and grouped into tables – EOC – First Responders – Infrastructure – Military – Industry © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • Each exercise is customized to the community • Participants are drawn from various organizations and grouped into tables – EOC – First Responders – Infrastructure – Military – Industry © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Scenario-based Exercises • Events are presented in 3 modules (Preattack, Attack, and Post-attack) • Each event has additional “discoverable” details • Facilitators lead discussions at each table – Focuses participants on what capabilities currently exist – Helps identify gaps – Provides additional background and details © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • Events are presented in 3 modules (Preattack, Attack, and Post-attack) • Each event has additional “discoverable” details • Facilitators lead discussions at each table – Focuses participants on what capabilities currently exist – Helps identify gaps – Provides additional background and details © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Community Exercise Lessons • Cyber Security perceived as a nuisance and an overhead burden • Low level of awareness regarding interdependencies and vulnerabilities • Poorly defined communications procedures and channels • Lack of information sharing • Best role for government not clear • Helped participants learn what they didn’t know © 2006 Center for Infrastructure Assurance and Security (CIAS)
Community Exercise Lessons • Cyber Security perceived as a nuisance and an overhead burden • Low level of awareness regarding interdependencies and vulnerabilities • Poorly defined communications procedures and channels • Lack of information sharing • Best role for government not clear • Helped participants learn what they didn’t know © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Community Exercise Lessons • • Helps identify and fix the gaps Promotes information sharing and awareness Identifies opportunities for collaboration Facilitates development of response procedures and best practices • Provides mechanism to test/drill/exercise community responders • Communities not ready for hands-on technical exercises like Black Demon © 2006 Center for Infrastructure Assurance and Security (CIAS)
Community Exercise Lessons • • Helps identify and fix the gaps Promotes information sharing and awareness Identifies opportunities for collaboration Facilitates development of response procedures and best practices • Provides mechanism to test/drill/exercise community responders • Communities not ready for hands-on technical exercises like Black Demon © 2006 Center for Infrastructure Assurance and Security (CIAS)

 Scenario-based Exercises • Each table receives a unique set of events Aug 10, 11: 20 AM (EOC, First Responders) Concerned citizens are calling city hall and local police stations for more information regarding the contaminated water supply. Citizens claim to have received a phone call with an automated announcement informing them that the local water supply had been contaminated and they should immediately stop using it for any drinking or cooking needs. The message also informed them to call city hall or their local police station for more details. © 2006 Center for Infrastructure Assurance and Security (CIAS)
Scenario-based Exercises • Each table receives a unique set of events Aug 10, 11: 20 AM (EOC, First Responders) Concerned citizens are calling city hall and local police stations for more information regarding the contaminated water supply. Citizens claim to have received a phone call with an automated announcement informing them that the local water supply had been contaminated and they should immediately stop using it for any drinking or cooking needs. The message also informed them to call city hall or their local police station for more details. © 2006 Center for Infrastructure Assurance and Security (CIAS)
 Importance of Computer Systems “The United States possesses both the world’s strongest military and its largest national economy. Those two aspects of our power are mutually reinforcing and dependent. They are also increasingly reliant upon certain critical infrastructures and upon cyberbased information systems. ” “[N]ontraditional attacks on our infrastructure and information systems may be capable of significantly harming both our military power and our economy. ” Presidential Decision Directive (PDD) 63, dated May 22, 1998
Importance of Computer Systems “The United States possesses both the world’s strongest military and its largest national economy. Those two aspects of our power are mutually reinforcing and dependent. They are also increasingly reliant upon certain critical infrastructures and upon cyberbased information systems. ” “[N]ontraditional attacks on our infrastructure and information systems may be capable of significantly harming both our military power and our economy. ” Presidential Decision Directive (PDD) 63, dated May 22, 1998


