0d78d1ebb95308f3e65a064b6b2cf944.ppt
- Количество слайдов: 55
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems
 Objectives n n n Explain how to harden operating systems List ways to prevent attacks through a Web browser Define SQL injection and explain how to protect against it Explain how to protect systems from communications-based attacks Describe various software security applications Security+ Guide to Network Security Fundamentals, Third Edition 2
Objectives n n n Explain how to harden operating systems List ways to prevent attacks through a Web browser Define SQL injection and explain how to protect against it Explain how to protect systems from communications-based attacks Describe various software security applications Security+ Guide to Network Security Fundamentals, Third Edition 2
 Hardening the Operating System n Hardening the operating system to resist attacks is often a ________ approach that involves: q q q ________ to the operating system Protecting against ____________ operating system ______ Let’s take a look at each of these… Security+ Guide to Network Security Fundamentals, Third Edition 3
Hardening the Operating System n Hardening the operating system to resist attacks is often a ________ approach that involves: q q q ________ to the operating system Protecting against ____________ operating system ______ Let’s take a look at each of these… Security+ Guide to Network Security Fundamentals, Third Edition 3
 Managing Operating System Updates n n One of the most important steps in hardening an operating system is to ________ Due to the increased length and complexity of operating systems __________ were introduced q n Then these vulnerabilities were _________________ Software vendors deploy software “fixes” to address vulnerabilities Security+ Guide to Network Security Fundamentals, Third Edition 4
Managing Operating System Updates n n One of the most important steps in hardening an operating system is to ________ Due to the increased length and complexity of operating systems __________ were introduced q n Then these vulnerabilities were _________________ Software vendors deploy software “fixes” to address vulnerabilities Security+ Guide to Network Security Fundamentals, Third Edition 4
 Managing Operating System Updates (continued) n Update terminology q Security patch n q Hotfix addresses a ____________ n q A general software security update _____________________________ Often may not be distributed outside that customer’s organization Service pack n A _________________________________________ Security+ Guide to Network Security Fundamentals, Third Edition 5
Managing Operating System Updates (continued) n Update terminology q Security patch n q Hotfix addresses a ____________ n q A general software security update _____________________________ Often may not be distributed outside that customer’s organization Service pack n A _________________________________________ Security+ Guide to Network Security Fundamentals, Third Edition 5
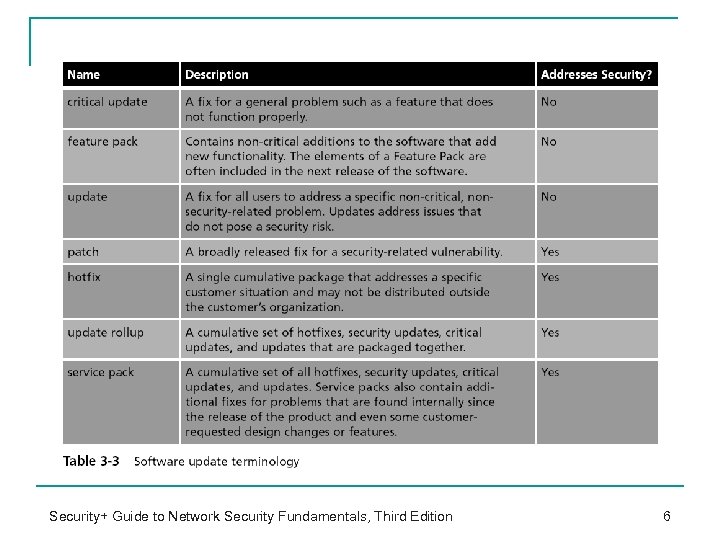 Security+ Guide to Network Security Fundamentals, Third Edition 6
Security+ Guide to Network Security Fundamentals, Third Edition 6
 Managing Operating System Updates (continued) n Patch management techniques- applies to all modern operating systems… 1. Install updates _____________ n Checks, downloads and installs regularly and automatically 2. Download updates automatically but ________________________ 3. Check for updates but ________________________________ 4. Never check for updates What is an incentive to using approach #2 or #3? Security+ Guide to Network Security Fundamentals, Third Edition 7
Managing Operating System Updates (continued) n Patch management techniques- applies to all modern operating systems… 1. Install updates _____________ n Checks, downloads and installs regularly and automatically 2. Download updates automatically but ________________________ 3. Check for updates but ________________________________ 4. Never check for updates What is an incentive to using approach #2 or #3? Security+ Guide to Network Security Fundamentals, Third Edition 7
 Managing Operating System Updates (continued) n Automated patch update service q n Used to ________________ instead of relying upon the vendor’s online update service Advantages to an automated patch update service include: q q q Can ____________ by downloading locally Computers that do not have Internet access can receive updates _______________________, and obtain reports on what updates each computer needs Security+ Guide to Network Security Fundamentals, Third Edition 8
Managing Operating System Updates (continued) n Automated patch update service q n Used to ________________ instead of relying upon the vendor’s online update service Advantages to an automated patch update service include: q q q Can ____________ by downloading locally Computers that do not have Internet access can receive updates _______________________, and obtain reports on what updates each computer needs Security+ Guide to Network Security Fundamentals, Third Edition 8
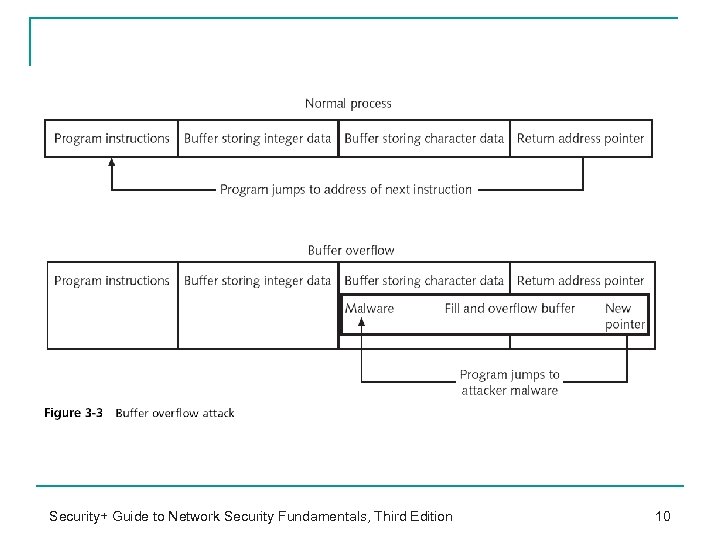
 Buffer Overflow Protection n What is Buffer overflow? q Occurs when a _______________ in random access memory (_____) ______________ n n Extra data overflows into the adjacent memory locations and under certain conditions may cause the computer to stop functioning or have unpredictable results ___________________ in order to compromise a computer q And point to a memory area that contains the attacker’s malware code See example to follow… Security+ Guide to Network Security Fundamentals, Third Edition 9
Buffer Overflow Protection n What is Buffer overflow? q Occurs when a _______________ in random access memory (_____) ______________ n n Extra data overflows into the adjacent memory locations and under certain conditions may cause the computer to stop functioning or have unpredictable results ___________________ in order to compromise a computer q And point to a memory area that contains the attacker’s malware code See example to follow… Security+ Guide to Network Security Fundamentals, Third Edition 9
 Security+ Guide to Network Security Fundamentals, Third Edition 10
Security+ Guide to Network Security Fundamentals, Third Edition 10
 Buffer Overflow Protection (continued) n Basic defenses against buffer overflows q q n ________________ that will protect against these attacks Use a _______________ that makes these attacks more difficult For Windows-based systems, there are two defenses against buffer overflows q q Data execution prevention (_____) Address space layout randomization (____) Security+ Guide to Network Security Fundamentals, Third Edition 11
Buffer Overflow Protection (continued) n Basic defenses against buffer overflows q q n ________________ that will protect against these attacks Use a _______________ that makes these attacks more difficult For Windows-based systems, there are two defenses against buffer overflows q q Data execution prevention (_____) Address space layout randomization (____) Security+ Guide to Network Security Fundamentals, Third Edition 11
 Buffer Overflow Protection (continued) n Data Execution Prevention (DEP) q q q Most modern CPUs support an ___ (No e. Xecute) bit to designate a _________________________________ Windows Vista allows software developers to enable NX hardware protection specifically for the application software that they develop Security+ Guide to Network Security Fundamentals, Third Edition 12
Buffer Overflow Protection (continued) n Data Execution Prevention (DEP) q q q Most modern CPUs support an ___ (No e. Xecute) bit to designate a _________________________________ Windows Vista allows software developers to enable NX hardware protection specifically for the application software that they develop Security+ Guide to Network Security Fundamentals, Third Edition 12
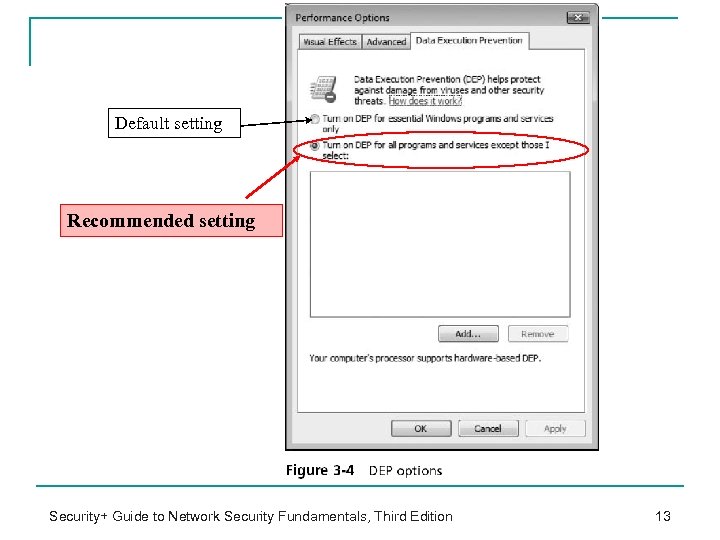 Default setting Recommended setting Security+ Guide to Network Security Fundamentals, Third Edition 13
Default setting Recommended setting Security+ Guide to Network Security Fundamentals, Third Edition 13
 Buffer Overflow Protection (continued) n Address Space Layout Randomization (ASLR) q q _____ assigns executable operating system code to ____________ in memory This makes it ______________ and take advantage of any functionality inside these executables n q Also makes it harder to predict where OS functionality resides in memory ASLR is _____________________________________ Security+ Guide to Network Security Fundamentals, Third Edition 14
Buffer Overflow Protection (continued) n Address Space Layout Randomization (ASLR) q q _____ assigns executable operating system code to ____________ in memory This makes it ______________ and take advantage of any functionality inside these executables n q Also makes it harder to predict where OS functionality resides in memory ASLR is _____________________________________ Security+ Guide to Network Security Fundamentals, Third Edition 14
 Configuring Operating System Protection n Most organizations take a _______ to configuring operating system protections: q q __________ a document that clearly ______________ an organization will employ to keep information secure ____________ - OS _____________ used for each computer ___________ – a way of configuring a group of baseline security settings at once ____________ of security template Security+ Guide to Network Security Fundamentals, Third Edition 15
Configuring Operating System Protection n Most organizations take a _______ to configuring operating system protections: q q __________ a document that clearly ______________ an organization will employ to keep information secure ____________ - OS _____________ used for each computer ___________ – a way of configuring a group of baseline security settings at once ____________ of security template Security+ Guide to Network Security Fundamentals, Third Edition 15
 Preventing Attacks That Come Through the Web Browser n These attacks involve using: q q q Cookies Java. Script Java Active. X Cross-site scripting Security+ Guide to Network Security Fundamentals, Third Edition 16
Preventing Attacks That Come Through the Web Browser n These attacks involve using: q q q Cookies Java. Script Java Active. X Cross-site scripting Security+ Guide to Network Security Fundamentals, Third Edition 16
 Cookies n Cookies are _____________________________________ q n Two types of cookies: q q n ______________ created by website ___________________ created by a ________ than the one which attempts to access the cookie Cookies can pose a _________ risk q n Info gathered based on shopping cart contents, info entered by user, preferences set etc. Cookies can be used to track the browsing or buying habits of a user Defenses against cookies include ______________________ them once they are created Security+ Guide to Network Security Fundamentals 17
Cookies n Cookies are _____________________________________ q n Two types of cookies: q q n ______________ created by website ___________________ created by a ________ than the one which attempts to access the cookie Cookies can pose a _________ risk q n Info gathered based on shopping cart contents, info entered by user, preferences set etc. Cookies can be used to track the browsing or buying habits of a user Defenses against cookies include ______________________ them once they are created Security+ Guide to Network Security Fundamentals 17
 Java. Script n A __________________ q q A computer programming language ________ and __________________________________ When a users access a website, the HTML document and script is downloaded to the user’s computer. n n Java. Script _______ used to create standalone applications q n Web browser extracts the script from HTML and runs it Executes using a Java interpreter Visiting a Web site that _________________________ to run on a local computer ______________ Security+ Guide to Network Security Fundamentals, Third Edition 18
Java. Script n A __________________ q q A computer programming language ________ and __________________________________ When a users access a website, the HTML document and script is downloaded to the user’s computer. n n Java. Script _______ used to create standalone applications q n Web browser extracts the script from HTML and runs it Executes using a Java interpreter Visiting a Web site that _________________________ to run on a local computer ______________ Security+ Guide to Network Security Fundamentals, Third Edition 18
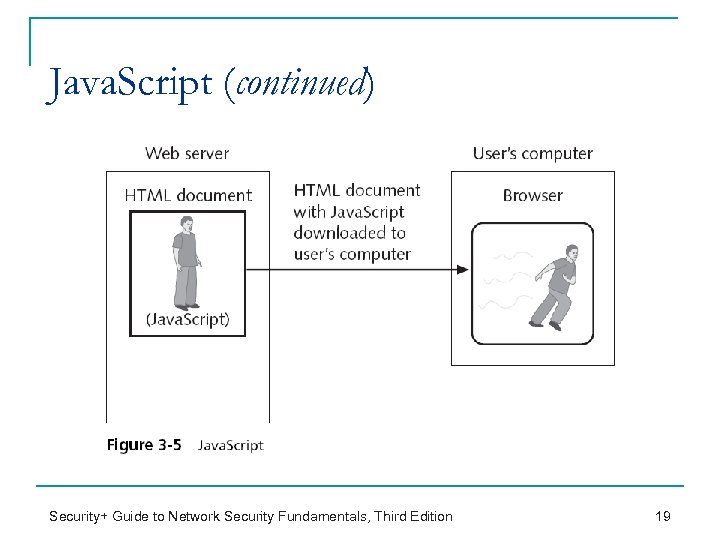 Java. Script (continued) Security+ Guide to Network Security Fundamentals, Third Edition 19
Java. Script (continued) Security+ Guide to Network Security Fundamentals, Third Edition 19
 Java. Script (continued) n Defense mechanisms in place to prevent Java. Script programs from causing serious harm: q Java. Script __________ capabilities such as _______________________ n q n Java. Script has _______________ Security concerns remain: q n But CAN access info available to a browser such as cookies Java. Script programs _____________________________ or authorization The defense against Java. Script is to ___________________ Security+ Guide to Network Security Fundamentals, Third Edition 20
Java. Script (continued) n Defense mechanisms in place to prevent Java. Script programs from causing serious harm: q Java. Script __________ capabilities such as _______________________ n q n Java. Script has _______________ Security concerns remain: q n But CAN access info available to a browser such as cookies Java. Script programs _____________________________ or authorization The defense against Java. Script is to ___________________ Security+ Guide to Network Security Fundamentals, Third Edition 20
 Java n Java q q n A __________________ _______ to create standalone applications Java applet q q A ________ stored on a Web server and __________________ along with HTML code Can also be made into hostile programs Security+ Guide to Network Security Fundamentals, Third Edition 21
Java n Java q q n A __________________ _______ to create standalone applications Java applet q q A ________ stored on a Web server and __________________ along with HTML code Can also be made into hostile programs Security+ Guide to Network Security Fundamentals, Third Edition 21
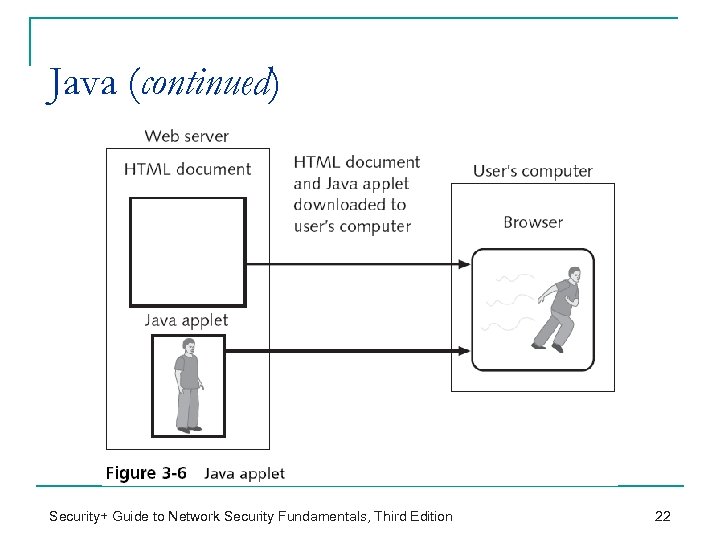 Java (continued) Security+ Guide to Network Security Fundamentals, Third Edition 22
Java (continued) Security+ Guide to Network Security Fundamentals, Third Edition 22
 Java (continued) n ________ is a safety mechanism and ____________________ q q n Surrounds program and __________________________ on a local computer ____________ allowing hostile applets access to sensitive data on the hard drive Two types of Java applets: q q _______ Java applet: program that ________________ and by default- run in a sandbox ______ Java applet: has information proving the program is _________ and has not been altered Security+ Guide to Network Security Fundamentals, Third Edition 23
Java (continued) n ________ is a safety mechanism and ____________________ q q n Surrounds program and __________________________ on a local computer ____________ allowing hostile applets access to sensitive data on the hard drive Two types of Java applets: q q _______ Java applet: program that ________________ and by default- run in a sandbox ______ Java applet: has information proving the program is _________ and has not been altered Security+ Guide to Network Security Fundamentals, Third Edition 23
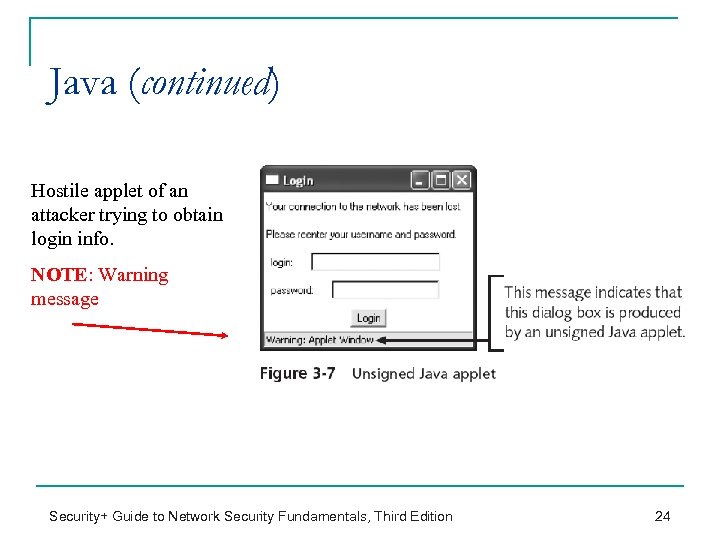 Java (continued) Hostile applet of an attacker trying to obtain login info. NOTE: Warning message Security+ Guide to Network Security Fundamentals, Third Edition 24
Java (continued) Hostile applet of an attacker trying to obtain login info. NOTE: Warning message Security+ Guide to Network Security Fundamentals, Third Edition 24
 Active. X n n n Set of technologies developed by _______ Not a programming language but a __________________________ Active. X controls q q n Also called ______________ Can perform many of the same functions of a Java applet, __________________ Have _____________________ Can be signed or unsigned but signing only verifies the signer, ____________________ Active. X poses a number of _________ Security+ Guide to Network Security Fundamentals, Third Edition 25
Active. X n n n Set of technologies developed by _______ Not a programming language but a __________________________ Active. X controls q q n Also called ______________ Can perform many of the same functions of a Java applet, __________________ Have _____________________ Can be signed or unsigned but signing only verifies the signer, ____________________ Active. X poses a number of _________ Security+ Guide to Network Security Fundamentals, Third Edition 25
 Active. X (continued) n If a computer is shared by multiple users, any user can download an Active. X control which would be available to all users q n n However, a ________________________________ that use Active. X technology _____________ mechanisms available in Internet Explorer The defense against Active. X is to _____ it within the Web browser Security+ Guide to Network Security Fundamentals, Third Edition 26
Active. X (continued) n If a computer is shared by multiple users, any user can download an Active. X control which would be available to all users q n n However, a ________________________________ that use Active. X technology _____________ mechanisms available in Internet Explorer The defense against Active. X is to _____ it within the Web browser Security+ Guide to Network Security Fundamentals, Third Edition 26
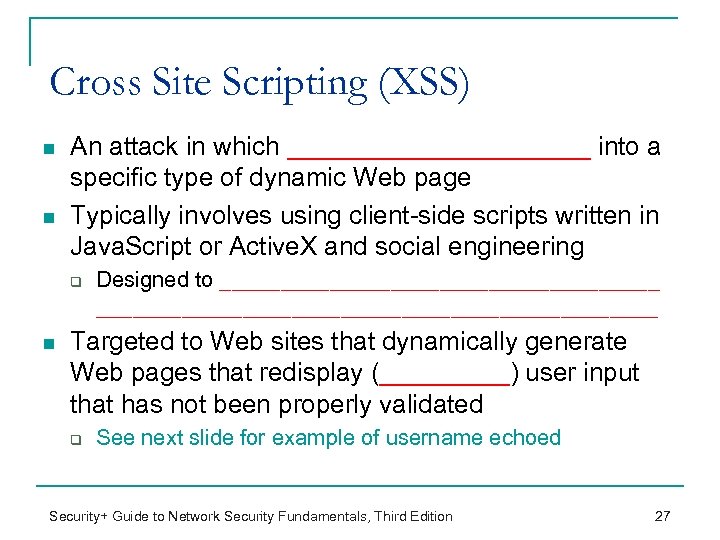 Cross Site Scripting (XSS) n n An attack in which ___________ into a specific type of dynamic Web page Typically involves using client-side scripts written in Java. Script or Active. X and social engineering q n Designed to _________________________________________ Targeted to Web sites that dynamically generate Web pages that redisplay (_____) user input that has not been properly validated q See next slide for example of username echoed Security+ Guide to Network Security Fundamentals, Third Edition 27
Cross Site Scripting (XSS) n n An attack in which ___________ into a specific type of dynamic Web page Typically involves using client-side scripts written in Java. Script or Active. X and social engineering q n Designed to _________________________________________ Targeted to Web sites that dynamically generate Web pages that redisplay (_____) user input that has not been properly validated q See next slide for example of username echoed Security+ Guide to Network Security Fundamentals, Third Edition 27
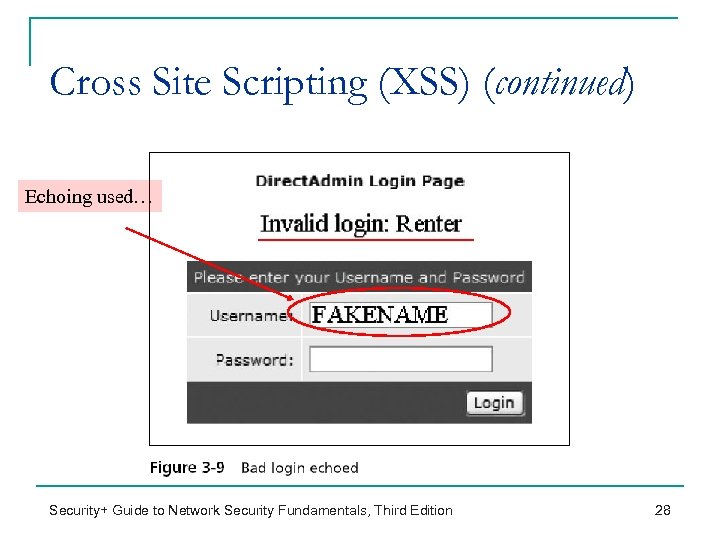 Cross Site Scripting (XSS) (continued) Echoing used… Security+ Guide to Network Security Fundamentals, Third Edition 28
Cross Site Scripting (XSS) (continued) Echoing used… Security+ Guide to Network Security Fundamentals, Third Edition 28
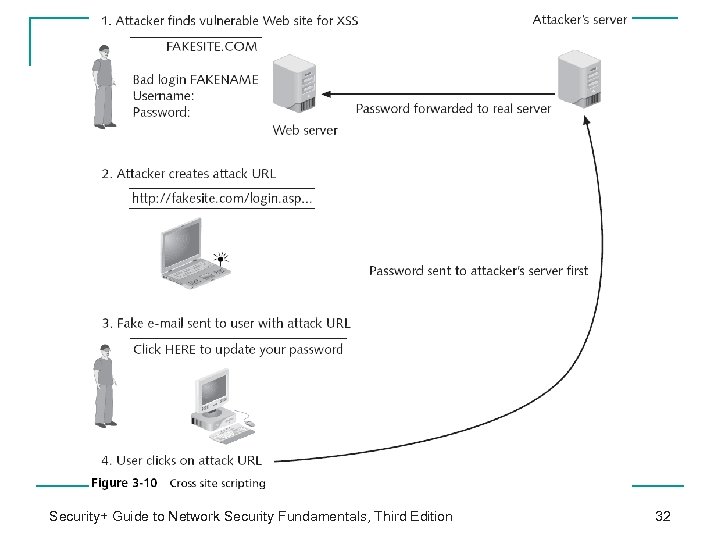
 Cross Site Scripting (XSS) (continued) Cross Site Scripting (XSS) attack steps:
Cross Site Scripting (XSS) (continued) Cross Site Scripting (XSS) attack steps:
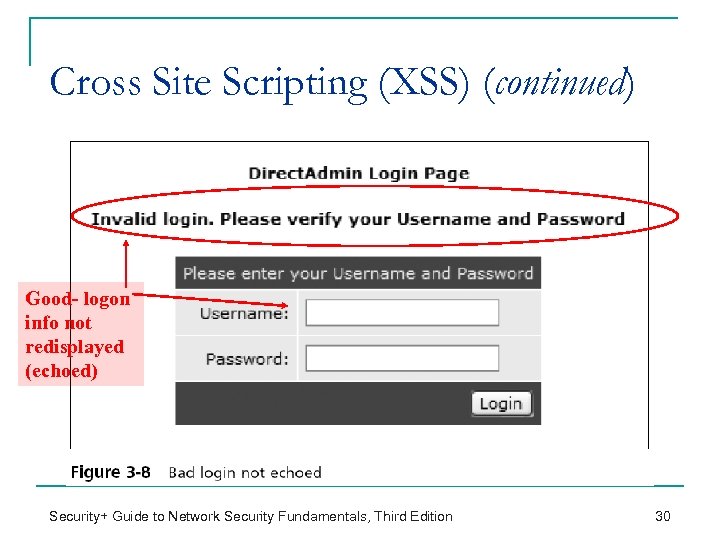 Cross Site Scripting (XSS) (continued) Good- logon info not redisplayed (echoed) Security+ Guide to Network Security Fundamentals, Third Edition 30
Cross Site Scripting (XSS) (continued) Good- logon info not redisplayed (echoed) Security+ Guide to Network Security Fundamentals, Third Edition 30
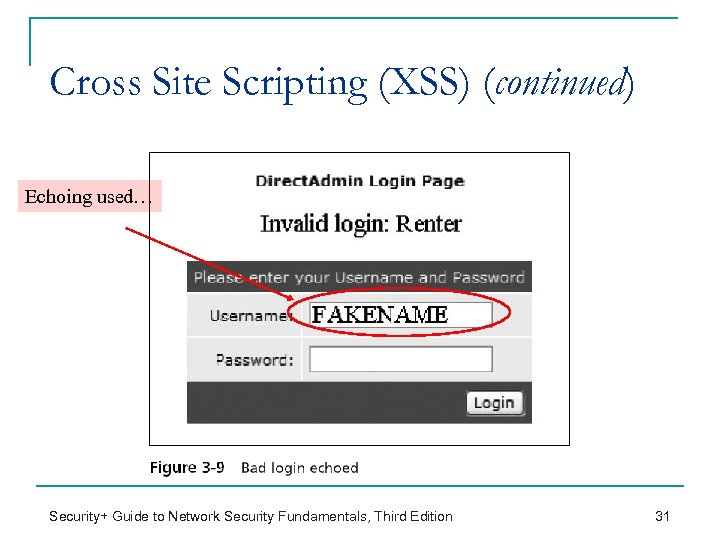 Cross Site Scripting (XSS) (continued) Echoing used… Security+ Guide to Network Security Fundamentals, Third Edition 31
Cross Site Scripting (XSS) (continued) Echoing used… Security+ Guide to Network Security Fundamentals, Third Edition 31
 Security+ Guide to Network Security Fundamentals, Third Edition 32
Security+ Guide to Network Security Fundamentals, Third Edition 32
 Cross Site Scripting (XSS) (continued) n Defenses against XSS _____________________ as well as ______ q Webmasters should check that all __________________________ n q They also should be sure that all Web services and database software is ______ to prevent XSS ____________________ Security+ Guide to Network Security Fundamentals, Third Edition 33
Cross Site Scripting (XSS) (continued) n Defenses against XSS _____________________ as well as ______ q Webmasters should check that all __________________________ n q They also should be sure that all Web services and database software is ______ to prevent XSS ____________________ Security+ Guide to Network Security Fundamentals, Third Edition 33
 Hardening Web Servers n n Because of their open exposure, ________________ for attackers ____ (structured query language) q n A language ____________ that is stored in a relational _________ SQL injection q q q One of the most ____________ Uses a form of injection like XSS Hinges on an _____________ into a dynamic Web page Security+ Guide to Network Security Fundamentals, Third Edition 34
Hardening Web Servers n n Because of their open exposure, ________________ for attackers ____ (structured query language) q n A language ____________ that is stored in a relational _________ SQL injection q q q One of the most ____________ Uses a form of injection like XSS Hinges on an _____________ into a dynamic Web page Security+ Guide to Network Security Fundamentals, Third Edition 34
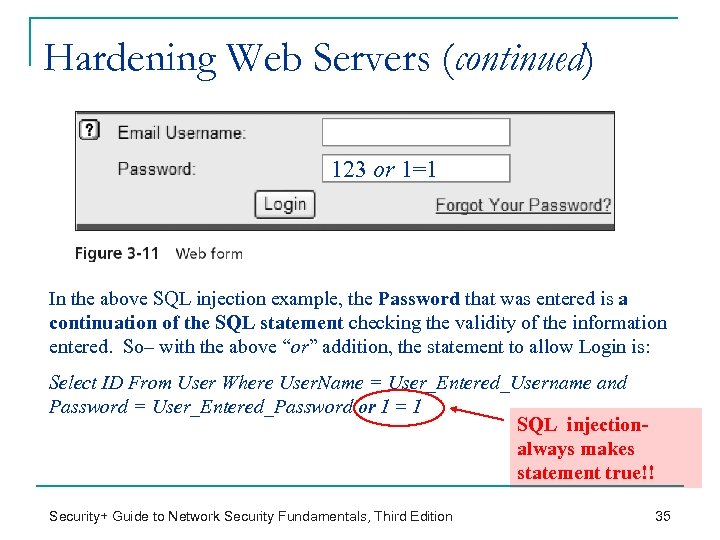 Hardening Web Servers (continued) 123 or 1=1 In the above SQL injection example, the Password that was entered is a continuation of the SQL statement checking the validity of the information entered. So– with the above “or” addition, the statement to allow Login is: Select ID From User Where User. Name = User_Entered_Username and Password = User_Entered_Password or 1 = 1 SQL injectionalways makes statement true!! Security+ Guide to Network Security Fundamentals, Third Edition 35
Hardening Web Servers (continued) 123 or 1=1 In the above SQL injection example, the Password that was entered is a continuation of the SQL statement checking the validity of the information entered. So– with the above “or” addition, the statement to allow Login is: Select ID From User Where User. Name = User_Entered_Username and Password = User_Entered_Password or 1 = 1 SQL injectionalways makes statement true!! Security+ Guide to Network Security Fundamentals, Third Edition 35
 Hardening Web Servers (continued) n Attacks in addition to the SQL injection attack q q q ________ from the database ______________ through function calls ________ a list of all usernames and passwords Security+ Guide to Network Security Fundamentals, Third Edition 36
Hardening Web Servers (continued) n Attacks in addition to the SQL injection attack q q q ________ from the database ______________ through function calls ________ a list of all usernames and passwords Security+ Guide to Network Security Fundamentals, Third Edition 36
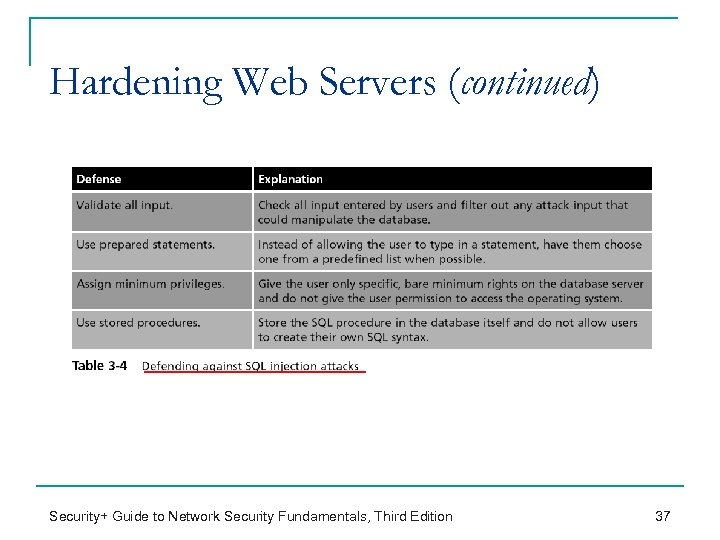 Hardening Web Servers (continued) Security+ Guide to Network Security Fundamentals, Third Edition 37
Hardening Web Servers (continued) Security+ Guide to Network Security Fundamentals, Third Edition 37
 Protecting Systems from Communications-Based Attacks n n Communications protocols and applications can also be vectors for attacks Some of the most common communicationsbased attacks are: q q q Security+ Guide to Network Security Fundamentals, Third Edition 38
Protecting Systems from Communications-Based Attacks n n Communications protocols and applications can also be vectors for attacks Some of the most common communicationsbased attacks are: q q q Security+ Guide to Network Security Fundamentals, Third Edition 38
 SMTP Open Relays n E-mail systems often use the following two TCP/IP protocols to send and receive messages q q n Simple Mail Transfer Protocol (____) handles ________ (sent) mail Post Office Protocol (______ for the current version) handles _______ (received) mail IMAP (Internet Mail Access Protocol- _______ is the current version) q q q A more advanced protocol than POP 3 for _________________ E-mail remains on the e-mail server Mail can be organized into folders and read from any computer Security+ Guide to Network Security Fundamentals, Third Edition 39
SMTP Open Relays n E-mail systems often use the following two TCP/IP protocols to send and receive messages q q n Simple Mail Transfer Protocol (____) handles ________ (sent) mail Post Office Protocol (______ for the current version) handles _______ (received) mail IMAP (Internet Mail Access Protocol- _______ is the current version) q q q A more advanced protocol than POP 3 for _________________ E-mail remains on the e-mail server Mail can be organized into folders and read from any computer Security+ Guide to Network Security Fundamentals, Third Edition 39
 SMTP Open Relays (continued) n SMTP relay q n SMTP open relay q n SMTP servers can _____________________________ If SMTP relay is not controlled, an __________________________ The _______ against SMTP open relay is to _________________ q So that all users ____________ or limit relays to only local users Security+ Guide to Network Security Fundamentals, Third Edition 40
SMTP Open Relays (continued) n SMTP relay q n SMTP open relay q n SMTP servers can _____________________________ If SMTP relay is not controlled, an __________________________ The _______ against SMTP open relay is to _________________ q So that all users ____________ or limit relays to only local users Security+ Guide to Network Security Fundamentals, Third Edition 40
 Instant Messaging n n n _____________________ Can also be used to chat between several users simultaneously, to send and receive files etc Basic IM has several ____________ q IM provides a __________________ n n q q Bypasses IM server Attackers can use this direct connection to _____________________ IM is _____________ by default so attackers could view the content of messages ________________ kept on IM server of the correspondence Security+ Guide to Network Security Fundamentals, Third Edition 41
Instant Messaging n n n _____________________ Can also be used to chat between several users simultaneously, to send and receive files etc Basic IM has several ____________ q IM provides a __________________ n n q q Bypasses IM server Attackers can use this direct connection to _____________________ IM is _____________ by default so attackers could view the content of messages ________________ kept on IM server of the correspondence Security+ Guide to Network Security Fundamentals, Third Edition 41
 Instant Messaging (continued) n Steps to secure IM include: q q Keep the IM server within the organization’s firewall and ________________________________ Enable ____________________________________ messages Security+ Guide to Network Security Fundamentals, Third Edition 42
Instant Messaging (continued) n Steps to secure IM include: q q Keep the IM server within the organization’s firewall and ________________________________ Enable ____________________________________ messages Security+ Guide to Network Security Fundamentals, Third Edition 42
 Peer-to-Peer (P 2 P) Networks n n Uses a _______________, so each device simultaneously functions as both a client and a server to all other devices connected to the network q q n For ______ of audio, video, and data, etc Downloads are entire files from one location __________________ using P 2 P Security+ Guide to Network Security Fundamentals, Third Edition 43
Peer-to-Peer (P 2 P) Networks n n Uses a _______________, so each device simultaneously functions as both a client and a server to all other devices connected to the network q q n For ______ of audio, video, and data, etc Downloads are entire files from one location __________________ using P 2 P Security+ Guide to Network Security Fundamentals, Third Edition 43
 Peer-to-Peer (P 2 P) Networks (continued) n n A new type of P 2 P network has emerged known as ______________ Torrents are ____________ that ________ available through a _____ n n n _______ program operated by the person or organization that wants to ____________ With _________________ Bit. Torrent ________________ like traditional P 2 P networks q Individual Bit. Torrent users _____________ so the entire file comes from a ___________ Security+ Guide to Network Security Fundamentals, Third Edition 44
Peer-to-Peer (P 2 P) Networks (continued) n n A new type of P 2 P network has emerged known as ______________ Torrents are ____________ that ________ available through a _____ n n n _______ program operated by the person or organization that wants to ____________ With _________________ Bit. Torrent ________________ like traditional P 2 P networks q Individual Bit. Torrent users _____________ so the entire file comes from a ___________ Security+ Guide to Network Security Fundamentals, Third Edition 44
 Applying Software Security Applications n Software security applications that are commonly installed on systems include: q q q Antivirus Anti-spam Popup blockers Personal software firewalls Host intrusion detection systems Security+ Guide to Network Security Fundamentals, Third Edition 45
Applying Software Security Applications n Software security applications that are commonly installed on systems include: q q q Antivirus Anti-spam Popup blockers Personal software firewalls Host intrusion detection systems Security+ Guide to Network Security Fundamentals, Third Edition 45
 Antivirus n Antivirus (AV) software q q q n ______________ as well as monitor computer activity and ____________, such as e-mail attachments, that might contain a virus If a virus is detected, options generally include cleaning the file of the virus, quarantining the infected file, or deleting the file Entire hard drive should be __________ The _________ of AV software is that it must be _______________ to recognize new viruses q AV updates known as ______________ Security+ Guide to Network Security Fundamentals, Third Edition 46
Antivirus n Antivirus (AV) software q q q n ______________ as well as monitor computer activity and ____________, such as e-mail attachments, that might contain a virus If a virus is detected, options generally include cleaning the file of the virus, quarantining the infected file, or deleting the file Entire hard drive should be __________ The _________ of AV software is that it must be _______________ to recognize new viruses q AV updates known as ______________ Security+ Guide to Network Security Fundamentals, Third Edition 46
 Popup Blockers n Popup q n Popup _______ q q n A ___________________ over the Web site that is being viewed Allows the ________________ Can be either a separate program or a feature incorporated within a browser As a separate program, popup blockers are often part of a package known as _________ q q ____________________ by different types of spyware Updates must be downloaded _________ Security+ Guide to Network Security Fundamentals, Third Edition 47
Popup Blockers n Popup q n Popup _______ q q n A ___________________ over the Web site that is being viewed Allows the ________________ Can be either a separate program or a feature incorporated within a browser As a separate program, popup blockers are often part of a package known as _________ q q ____________________ by different types of spyware Updates must be downloaded _________ Security+ Guide to Network Security Fundamentals, Third Edition 47
 Anti-Spam n Spam can be annoying but also pose a _________ q n Viruses can be spread through e-mails Four different options that corporations can use to prevent (reduce) spam from reaching the user 1. _____________________ A. Install the spam filter with the SMTP server n See Figure 3 -14 on next slide B. Install the spam filter with the POP 3 server n See Figure 3 -15 – two slides down… Security+ Guide to Network Security Fundamentals, Third Edition 48
Anti-Spam n Spam can be annoying but also pose a _________ q n Viruses can be spread through e-mails Four different options that corporations can use to prevent (reduce) spam from reaching the user 1. _____________________ A. Install the spam filter with the SMTP server n See Figure 3 -14 on next slide B. Install the spam filter with the POP 3 server n See Figure 3 -15 – two slides down… Security+ Guide to Network Security Fundamentals, Third Edition 48
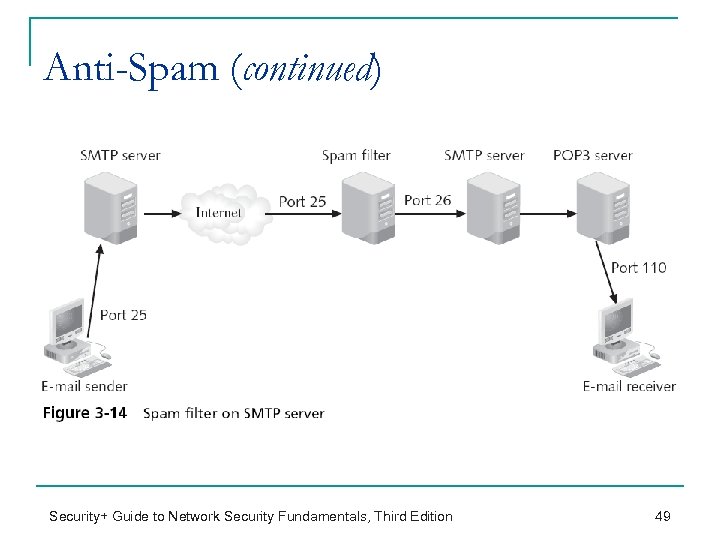 Anti-Spam (continued) Security+ Guide to Network Security Fundamentals, Third Edition 49
Anti-Spam (continued) Security+ Guide to Network Security Fundamentals, Third Edition 49
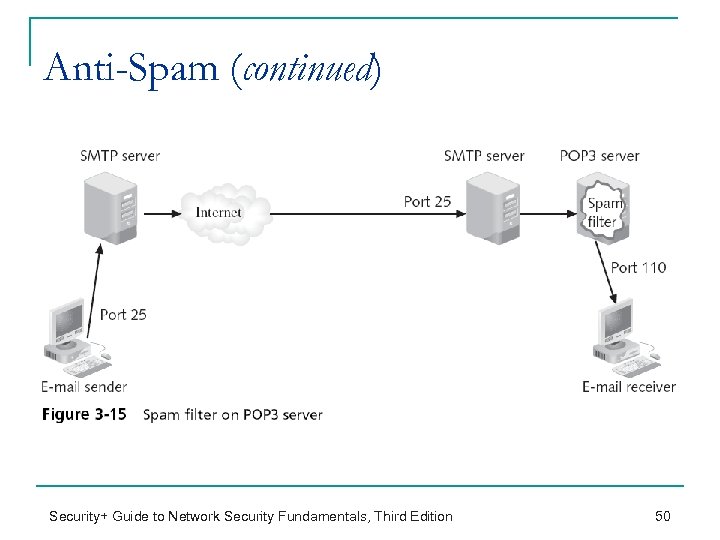 Anti-Spam (continued) Security+ Guide to Network Security Fundamentals, Third Edition 50
Anti-Spam (continued) Security+ Guide to Network Security Fundamentals, Third Edition 50
 Anti-Spam (continued) 2. Another way to filter spam is for the organization to _________________ q All e-mail is directed to the third-party’s remote spam filter where it is cleansed before it is redirected back to the organization 3. Third method is to _____________ q Configurations include setting the level of junk e-mail protection, specifying blocked or allowed senders etc. 4. A final method of spam filtering is to _____________________ that works with the e-mail client software Security+ Guide to Network Security Fundamentals, Third Edition 51
Anti-Spam (continued) 2. Another way to filter spam is for the organization to _________________ q All e-mail is directed to the third-party’s remote spam filter where it is cleansed before it is redirected back to the organization 3. Third method is to _____________ q Configurations include setting the level of junk e-mail protection, specifying blocked or allowed senders etc. 4. A final method of spam filtering is to _____________________ that works with the e-mail client software Security+ Guide to Network Security Fundamentals, Third Edition 51
 Personal Software Firewalls n Firewall, sometimes called a packet filter q q n _______ software firewall q n ________________________________________ Can be _________________ Runs as a ______________ to protect it against attacks Many operating systems now come with personal software firewalls Security+ Guide to Network Security Fundamentals, Third Edition 52
Personal Software Firewalls n Firewall, sometimes called a packet filter q q n _______ software firewall q n ________________________________________ Can be _________________ Runs as a ______________ to protect it against attacks Many operating systems now come with personal software firewalls Security+ Guide to Network Security Fundamentals, Third Edition 52
 Host Intrusion Detection Systems (_______) n n n Monitors _______________________________________IDS are software-based and __________________ These systems can be divided into four groups: q q n ______ monitors ___________ analyzers HIDS work on the ________________________________- Security+ Guide to Network Security Fundamentals, Third Edition 53
Host Intrusion Detection Systems (_______) n n n Monitors _______________________________________IDS are software-based and __________________ These systems can be divided into four groups: q q n ______ monitors ___________ analyzers HIDS work on the ________________________________- Security+ Guide to Network Security Fundamentals, Third Edition 53
 Summary n n Hardening the operating system is key in resisting attacks A buffer overflow occurs when a process attempts to store data in random access memory (RAM) beyond the boundaries of a fixed-length storage buffer Most organizations use a four-fold approach to protecting operating systems: security policies, configuration baselines, security templates, and deployment Systems must also be protected from attacks that attempt to enter through a Web browser Security+ Guide to Network Security Fundamentals, Third Edition 54
Summary n n Hardening the operating system is key in resisting attacks A buffer overflow occurs when a process attempts to store data in random access memory (RAM) beyond the boundaries of a fixed-length storage buffer Most organizations use a four-fold approach to protecting operating systems: security policies, configuration baselines, security templates, and deployment Systems must also be protected from attacks that attempt to enter through a Web browser Security+ Guide to Network Security Fundamentals, Third Edition 54
 Summary (continued) n n n Attacks can also be based on communications protocols and applications Additional security-based software, whose sole purpose is to fend off attacks, is another important layer of security A firewall is designed to prevent malicious packets from entering or leaving the computer Security+ Guide to Network Security Fundamentals, Third Edition 55
Summary (continued) n n n Attacks can also be based on communications protocols and applications Additional security-based software, whose sole purpose is to fend off attacks, is another important layer of security A firewall is designed to prevent malicious packets from entering or leaving the computer Security+ Guide to Network Security Fundamentals, Third Edition 55


