82bf32e92eb9737e83bc419ab303c818.ppt
- Количество слайдов: 74
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 4 Application, Data, and Host Security
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 4 Application, Data, and Host Security
 Objectives • List the steps for securing a host computer • Define application security • Explain how to secure data Security+ Guide to Network Security Fundamentals, Fifth Edition 2
Objectives • List the steps for securing a host computer • Define application security • Explain how to secure data Security+ Guide to Network Security Fundamentals, Fifth Edition 2
 Application, Data, and Host Security • Basic security starts with protecting host, applications, and data • Host, which can be either a server or a client on a network, runs applications that process, save, or transport data • Securing the host involves: – Protecting the physical device itself – Securing the operating system (OS) – Using antimalware software Security+ Guide to Network Security Fundamentals, Fifth Edition 3
Application, Data, and Host Security • Basic security starts with protecting host, applications, and data • Host, which can be either a server or a client on a network, runs applications that process, save, or transport data • Securing the host involves: – Protecting the physical device itself – Securing the operating system (OS) – Using antimalware software Security+ Guide to Network Security Fundamentals, Fifth Edition 3
 Securing Devices • Security control - Any device or process used to reduce risk • Two levels of security controls: – Administrative controls - Processes for developing and ensuring that policies and procedures are carried out – Technical controls – Processes carried out or managed by devices Security+ Guide to Network Security Fundamentals, Fifth Edition 4
Securing Devices • Security control - Any device or process used to reduce risk • Two levels of security controls: – Administrative controls - Processes for developing and ensuring that policies and procedures are carried out – Technical controls – Processes carried out or managed by devices Security+ Guide to Network Security Fundamentals, Fifth Edition 4
 Activity Phase Controls • Deterrent control - Attempts to discourage security violations before they occur • Preventive controls - Works to prevent the threat from coming into contact with the vulnerability • Detective controls - Designed to identify any threat that has reached the system • Compensating controls - Controls that provide alternative to normal controls that for some reason cannot be used Security+ Guide to Network Security Fundamentals, Fifth Edition 5
Activity Phase Controls • Deterrent control - Attempts to discourage security violations before they occur • Preventive controls - Works to prevent the threat from coming into contact with the vulnerability • Detective controls - Designed to identify any threat that has reached the system • Compensating controls - Controls that provide alternative to normal controls that for some reason cannot be used Security+ Guide to Network Security Fundamentals, Fifth Edition 5
 Activity Phase Controls: Corrective Controls • Corrective controls - Controls intended to mitigate or lessen the damage caused by the incident Security+ Guide to Network Security Fundamentals, Fifth Edition 6
Activity Phase Controls: Corrective Controls • Corrective controls - Controls intended to mitigate or lessen the damage caused by the incident Security+ Guide to Network Security Fundamentals, Fifth Edition 6
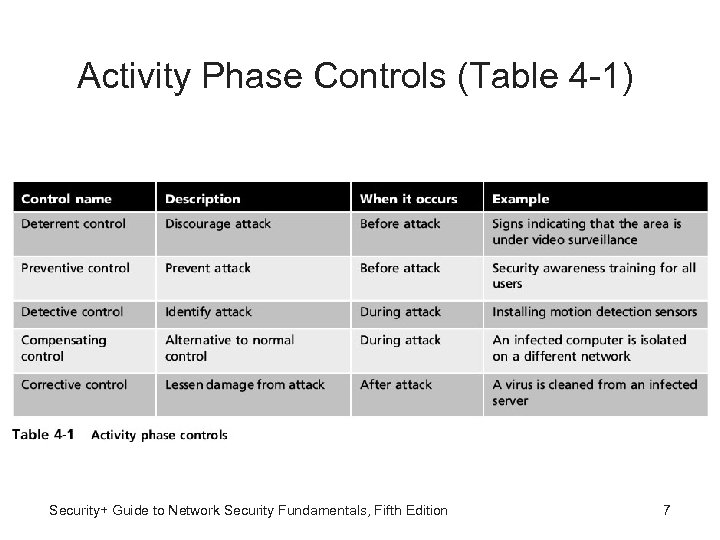 Activity Phase Controls (Table 4 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 7
Activity Phase Controls (Table 4 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 7
 External Perimeter Defenses • External perimeter defenses are designed to restrict access to areas equipment is located • Examples: – Barriers – Guards – Motion detection devices Security+ Guide to Network Security Fundamentals, Fifth Edition 8
External Perimeter Defenses • External perimeter defenses are designed to restrict access to areas equipment is located • Examples: – Barriers – Guards – Motion detection devices Security+ Guide to Network Security Fundamentals, Fifth Edition 8
 Barriers • Different types of passive barriers can be used to restrict unwanted individuals or vehicles from entering secure area • Fencing - Tall, permanent structure to keep out individuals for maintaining security • Sign - Explains the area is restricted • Lighting - Area can be viewed after dark • Modern perimeter security consists of fence equipped with other deterrents Security+ Guide to Network Security Fundamentals, Fifth Edition 9
Barriers • Different types of passive barriers can be used to restrict unwanted individuals or vehicles from entering secure area • Fencing - Tall, permanent structure to keep out individuals for maintaining security • Sign - Explains the area is restricted • Lighting - Area can be viewed after dark • Modern perimeter security consists of fence equipped with other deterrents Security+ Guide to Network Security Fundamentals, Fifth Edition 9
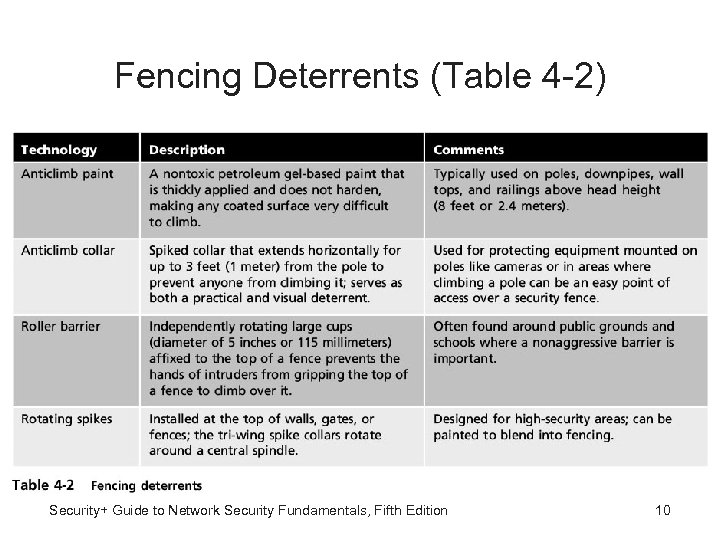 Fencing Deterrents (Table 4 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 10
Fencing Deterrents (Table 4 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 10
 Barricade • Barricade - Generally designed to block passage of traffic • Most often used for directing large crowds or restricting vehicular traffic and are generally not designed to keep out individuals • Barricades are usually not as tall as fences and can more easily be circumvented by climbing over them • Temporary vehicular traffic barricades are frequently used in construction areas Security+ Guide to Network Security Fundamentals, Fifth Edition 11
Barricade • Barricade - Generally designed to block passage of traffic • Most often used for directing large crowds or restricting vehicular traffic and are generally not designed to keep out individuals • Barricades are usually not as tall as fences and can more easily be circumvented by climbing over them • Temporary vehicular traffic barricades are frequently used in construction areas Security+ Guide to Network Security Fundamentals, Fifth Edition 11
 Guards • Guards - Active security elements • Unlike passive devices, guard can differentiate between an intruder and non-intruder • Can also make split-second decisions about when necessary to take appropriate action Security+ Guide to Network Security Fundamentals, Fifth Edition 12
Guards • Guards - Active security elements • Unlike passive devices, guard can differentiate between an intruder and non-intruder • Can also make split-second decisions about when necessary to take appropriate action Security+ Guide to Network Security Fundamentals, Fifth Edition 12
 Closed Circuit Television (CCTV) • Some guards responsible for monitoring activity captured by video camera • Video surveillance - Uses video cameras to transmit a signal • Closed circuit television (CCTV) – Video signal to a specific and limited set of receivers • CCTV options: – Fixed in single position (pointed at door or hallway) – Moveable in 360 degrees for a full panoramic view – Motion-tracking Security+ Guide to Network Security Fundamentals, Fifth Edition 13
Closed Circuit Television (CCTV) • Some guards responsible for monitoring activity captured by video camera • Video surveillance - Uses video cameras to transmit a signal • Closed circuit television (CCTV) – Video signal to a specific and limited set of receivers • CCTV options: – Fixed in single position (pointed at door or hallway) – Moveable in 360 degrees for a full panoramic view – Motion-tracking Security+ Guide to Network Security Fundamentals, Fifth Edition 13
 Motion Detection • Motion detection - Determining object’s change in position in relation to surroundings • Movement usually generates an audible alarm to warn guard of an intruder Security+ Guide to Network Security Fundamentals, Fifth Edition 14
Motion Detection • Motion detection - Determining object’s change in position in relation to surroundings • Movement usually generates an audible alarm to warn guard of an intruder Security+ Guide to Network Security Fundamentals, Fifth Edition 14
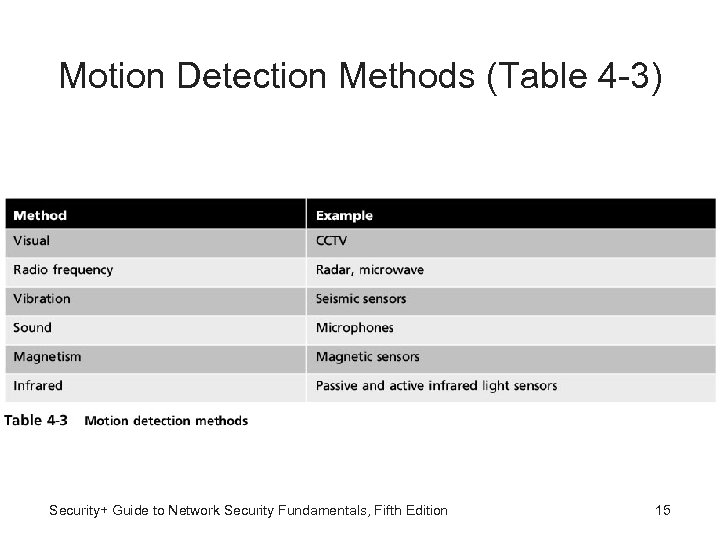 Motion Detection Methods (Table 4 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 15
Motion Detection Methods (Table 4 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 15
 Internal Physical Access Security • External perimeter defenses designed to keep intruder from entering area • Yet if intruder successful then must face internal physical access security (focused on interior) • Examples: – – – Hardware locks Proximity readers Access lists Mantraps Protected distribution systems for cabling Security+ Guide to Network Security Fundamentals, Fifth Edition 16
Internal Physical Access Security • External perimeter defenses designed to keep intruder from entering area • Yet if intruder successful then must face internal physical access security (focused on interior) • Examples: – – – Hardware locks Proximity readers Access lists Mantraps Protected distribution systems for cabling Security+ Guide to Network Security Fundamentals, Fifth Edition 16
 Hardware Locks • Door locks in commercial buildings different from residential door locks • Deadbolt lock - Extends solid metal bar into door frame for extra security • Much more difficult to defeat than keyed entry locks: – Cannot be broken from the outside like a preset lock – Extension of bar prevents credit card from being inserted to “jimmy” it open – Requires key be used to both open and lock door Security+ Guide to Network Security Fundamentals, Fifth Edition 17
Hardware Locks • Door locks in commercial buildings different from residential door locks • Deadbolt lock - Extends solid metal bar into door frame for extra security • Much more difficult to defeat than keyed entry locks: – Cannot be broken from the outside like a preset lock – Extension of bar prevents credit card from being inserted to “jimmy” it open – Requires key be used to both open and lock door Security+ Guide to Network Security Fundamentals, Fifth Edition 17
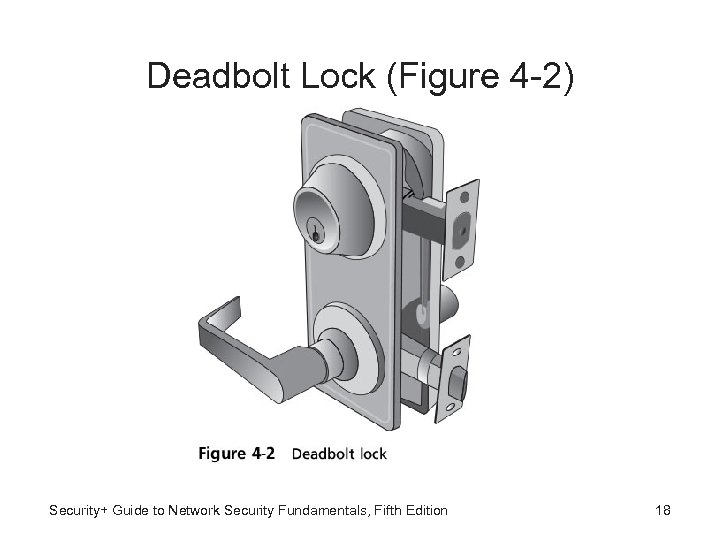 Deadbolt Lock (Figure 4 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 18
Deadbolt Lock (Figure 4 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 18
 Key Management • Inspect all locks on regular basis to identify physical damage or signs of tampering • Receive approval of supervisor or other appropriate person before issuing keys • Keep track of keys issued, to whom, and date • Require users to sign name when receiving keys • Master keys not have any marks identifying them as masters • Secure unused keys in locked safe • Establish procedure to monitor use locks and keys Security+ Guide to Network Security Fundamentals, Fifth Edition 19
Key Management • Inspect all locks on regular basis to identify physical damage or signs of tampering • Receive approval of supervisor or other appropriate person before issuing keys • Keep track of keys issued, to whom, and date • Require users to sign name when receiving keys • Master keys not have any marks identifying them as masters • Secure unused keys in locked safe • Establish procedure to monitor use locks and keys Security+ Guide to Network Security Fundamentals, Fifth Edition 19
 Key Management: Duplicates • When making duplicates master keys: – Mark “Do Not Duplicate” – Wipe out manufacturer’s serial numbers to keep duplicates from being ordered Security+ Guide to Network Security Fundamentals, Fifth Edition 20
Key Management: Duplicates • When making duplicates master keys: – Mark “Do Not Duplicate” – Wipe out manufacturer’s serial numbers to keep duplicates from being ordered Security+ Guide to Network Security Fundamentals, Fifth Edition 20
 Cipher Lock • Cipher lock more sophisticated alternative to key lock • Combination sequence necessary to open door • Can be programmed to allow individual’s code to give access at only certain days or times • Records when door is opened and by which code • Can be vulnerable to shoulder surfing Security+ Guide to Network Security Fundamentals, Fifth Edition 21
Cipher Lock • Cipher lock more sophisticated alternative to key lock • Combination sequence necessary to open door • Can be programmed to allow individual’s code to give access at only certain days or times • Records when door is opened and by which code • Can be vulnerable to shoulder surfing Security+ Guide to Network Security Fundamentals, Fifth Edition 21
 Cipher Lock (Figure 4 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 22
Cipher Lock (Figure 4 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 22
 ID Badge • Instead of using key or entering a code to open door user can use an object (physical token) for identification • ID badge - Originally contained photograph of bearer and were visually screened by security guards • Later ID badges were magnetic stripe cards that were “swiped” or contained barcode identifier “scanned” to identify user Security+ Guide to Network Security Fundamentals, Fifth Edition 23
ID Badge • Instead of using key or entering a code to open door user can use an object (physical token) for identification • ID badge - Originally contained photograph of bearer and were visually screened by security guards • Later ID badges were magnetic stripe cards that were “swiped” or contained barcode identifier “scanned” to identify user Security+ Guide to Network Security Fundamentals, Fifth Edition 23
 Magnetic Stripe vs. Strip • Although “magnetic stripe card” and “magnetic strip card” often used interchangeably that is incorrect • Strip is long narrow piece of something, usually of uniform width, like a “strip of paper” • Stripe is a strip of material (like magnetic tape) • Technically magnetic stripe card contains a magnetic strip Security+ Guide to Network Security Fundamentals, Fifth Edition 24
Magnetic Stripe vs. Strip • Although “magnetic stripe card” and “magnetic strip card” often used interchangeably that is incorrect • Strip is long narrow piece of something, usually of uniform width, like a “strip of paper” • Stripe is a strip of material (like magnetic tape) • Technically magnetic stripe card contains a magnetic strip Security+ Guide to Network Security Fundamentals, Fifth Edition 24
 Proximity Readers • New technologies not require ID badge be visually exposed • Badge emits signal identifying owner to then be detected • Proximity reader – Device that receives the badge signal • Sometimes even unnecessary for bearer to remove badge from pocket or purse Security+ Guide to Network Security Fundamentals, Fifth Edition 25
Proximity Readers • New technologies not require ID badge be visually exposed • Badge emits signal identifying owner to then be detected • Proximity reader – Device that receives the badge signal • Sometimes even unnecessary for bearer to remove badge from pocket or purse Security+ Guide to Network Security Fundamentals, Fifth Edition 25
 Radio Frequency Identification (RFID) • ID badges detected by proximity reader often fitted with tiny radio frequency identification (RFID) tags • RFID tags easily be affixed to inside of ID badge • Can be read by an RFID proximity reader as user walks through turnstile with badge in pocket Security+ Guide to Network Security Fundamentals, Fifth Edition 26
Radio Frequency Identification (RFID) • ID badges detected by proximity reader often fitted with tiny radio frequency identification (RFID) tags • RFID tags easily be affixed to inside of ID badge • Can be read by an RFID proximity reader as user walks through turnstile with badge in pocket Security+ Guide to Network Security Fundamentals, Fifth Edition 26
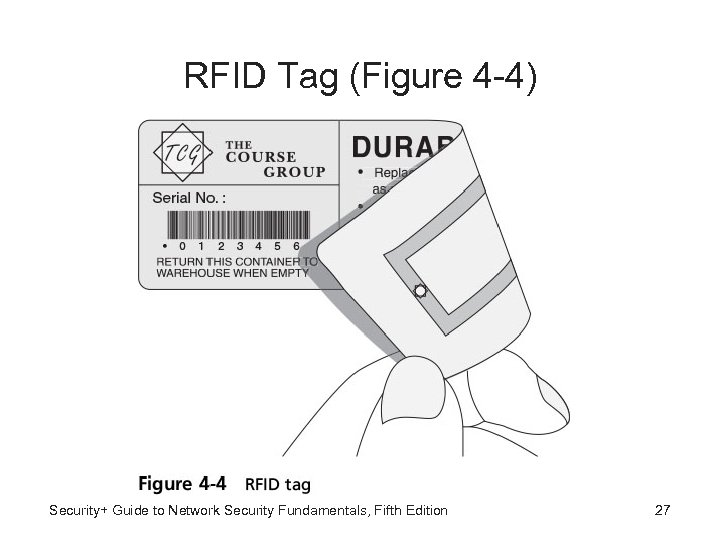 RFID Tag (Figure 4 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 27
RFID Tag (Figure 4 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 27
 Access List & Mantraps • Access list - Record of individuals who have permission to enter secure area • Records time they entered and left • Mantrap - Separates a secured from a nonsecured area • Device monitors and controls two interlocking doors so only one door may open at any time Security+ Guide to Network Security Fundamentals, Fifth Edition 28
Access List & Mantraps • Access list - Record of individuals who have permission to enter secure area • Records time they entered and left • Mantrap - Separates a secured from a nonsecured area • Device monitors and controls two interlocking doors so only one door may open at any time Security+ Guide to Network Security Fundamentals, Fifth Edition 28
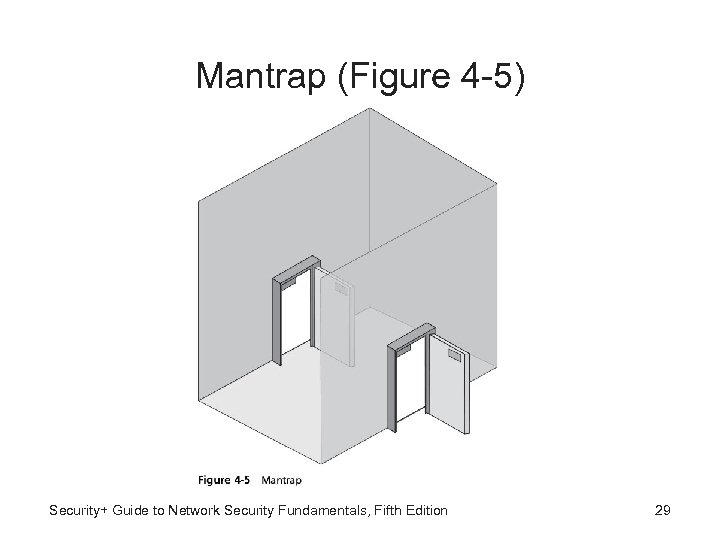 Mantrap (Figure 4 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 29
Mantrap (Figure 4 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 29
 Protected Distribution Systems (PDS) • Cable conduits made up of hollow tubes that carry copper wire or fiber-optic cables • Protected distribution system (PDS) - System of cable conduits used to protect classified information being transmitted between two secure areas • PDS is a standard created by U. S. Department of Defense (DOD) Security+ Guide to Network Security Fundamentals, Fifth Edition 30
Protected Distribution Systems (PDS) • Cable conduits made up of hollow tubes that carry copper wire or fiber-optic cables • Protected distribution system (PDS) - System of cable conduits used to protect classified information being transmitted between two secure areas • PDS is a standard created by U. S. Department of Defense (DOD) Security+ Guide to Network Security Fundamentals, Fifth Edition 30
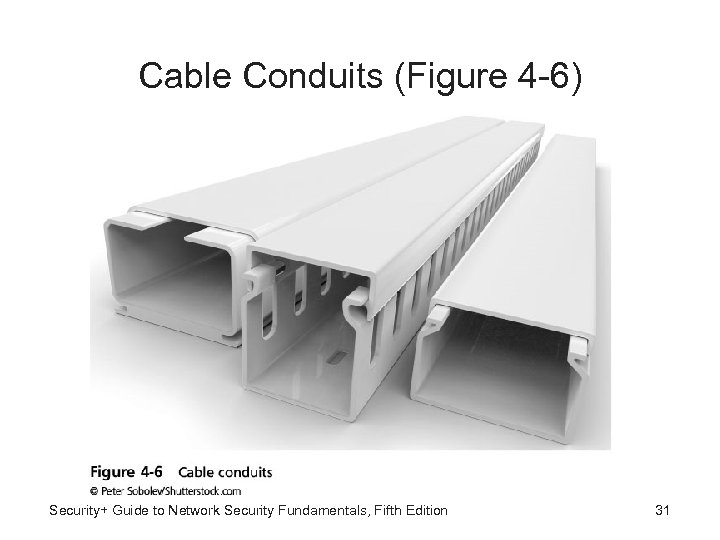 Cable Conduits (Figure 4 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 31
Cable Conduits (Figure 4 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 31
 Hardened Carrier PDS • Hardened carrier PDS - Data cables installed in conduit constructed of special electrical metallic tubing or similar material • All of connections between the different segments are permanently sealed with welds or special sealants • If hardened carrier PDS buried underground the carrier containing cables must be encased in concrete and manhole covers that give access must be locked down • Must be visually inspected on a regular basis Security+ Guide to Network Security Fundamentals, Fifth Edition 32
Hardened Carrier PDS • Hardened carrier PDS - Data cables installed in conduit constructed of special electrical metallic tubing or similar material • All of connections between the different segments are permanently sealed with welds or special sealants • If hardened carrier PDS buried underground the carrier containing cables must be encased in concrete and manhole covers that give access must be locked down • Must be visually inspected on a regular basis Security+ Guide to Network Security Fundamentals, Fifth Edition 32
 Alarmed Carrier PDS • Alarmed carrier PDS - Carrier system deployed with specialized optical fibers in the conduit • Can sense acoustic vibrations and trigger alarm when intruder attempts to gain access • Advantages: – Provides continuous monitoring – Eliminates need for periodic visual inspections – Allows carrier to be hidden above ceiling or below floor – Eliminates need for welding or sealing connections Security+ Guide to Network Security Fundamentals, Fifth Edition 33
Alarmed Carrier PDS • Alarmed carrier PDS - Carrier system deployed with specialized optical fibers in the conduit • Can sense acoustic vibrations and trigger alarm when intruder attempts to gain access • Advantages: – Provides continuous monitoring – Eliminates need for periodic visual inspections – Allows carrier to be hidden above ceiling or below floor – Eliminates need for welding or sealing connections Security+ Guide to Network Security Fundamentals, Fifth Edition 33
 Hardware Security • Hardware security - Physical security protecting host system hardware • Portable devices have steel bracket security slot • Cable lock inserted into slot and secured to device • Laptops may be placed in safe or locking cabinets • Can be prewired for power and network connections to allow devices to charge while stored Security+ Guide to Network Security Fundamentals, Fifth Edition 34
Hardware Security • Hardware security - Physical security protecting host system hardware • Portable devices have steel bracket security slot • Cable lock inserted into slot and secured to device • Laptops may be placed in safe or locking cabinets • Can be prewired for power and network connections to allow devices to charge while stored Security+ Guide to Network Security Fundamentals, Fifth Edition 34
 Cable Lock (Figure 4 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 35
Cable Lock (Figure 4 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 35
 Securing the Operating System Software • Two approaches to securing operating system – Properly configure operating system after it has been installed to “fortify” it – Tighten security during initial design and coding of operating system. • Five-step process for protecting operating system 1. Develop the security policy 2. Perform host software baselining 3. Configure operating system security and settings 4. Deploy the settings 5. Implement patch management Security+ Guide to Network Security Fundamentals, Fifth Edition 36
Securing the Operating System Software • Two approaches to securing operating system – Properly configure operating system after it has been installed to “fortify” it – Tighten security during initial design and coding of operating system. • Five-step process for protecting operating system 1. Develop the security policy 2. Perform host software baselining 3. Configure operating system security and settings 4. Deploy the settings 5. Implement patch management Security+ Guide to Network Security Fundamentals, Fifth Edition 36
 Securing the Operating System Software – Steps 1 & 2 • Security policy - Document(s) that clearly define organization’s defense mechanisms • Perform host software baselining (standard or checklist against which systems can be evaluated) • Configuration settings that are used for each computer in the organization Security+ Guide to Network Security Fundamentals, Fifth Edition 37
Securing the Operating System Software – Steps 1 & 2 • Security policy - Document(s) that clearly define organization’s defense mechanisms • Perform host software baselining (standard or checklist against which systems can be evaluated) • Configuration settings that are used for each computer in the organization Security+ Guide to Network Security Fundamentals, Fifth Edition 37
 Securing the Operating System Software – Step 3 • Configure operating system security and settings • Hundreds of different security settings can be manipulated • Typical configuration baseline: – Changing insecure default settings – Eliminating unnecessary software, services, protocols – Enabling security features such as a firewall Security+ Guide to Network Security Fundamentals, Fifth Edition 38
Securing the Operating System Software – Step 3 • Configure operating system security and settings • Hundreds of different security settings can be manipulated • Typical configuration baseline: – Changing insecure default settings – Eliminating unnecessary software, services, protocols – Enabling security features such as a firewall Security+ Guide to Network Security Fundamentals, Fifth Edition 38
 Securing the Operating System Software – Step 4 • Deploy settings through security template (collections of security configuration settings) • Group policy - Windows feature providing centralized computer management • A single configuration may be deployed to many users Security+ Guide to Network Security Fundamentals, Fifth Edition 39
Securing the Operating System Software – Step 4 • Deploy settings through security template (collections of security configuration settings) • Group policy - Windows feature providing centralized computer management • A single configuration may be deployed to many users Security+ Guide to Network Security Fundamentals, Fifth Edition 39
 Securing the Operating System Software – Step 5 • Operating systems have increased in size and complexity • New attack tools have made secure functions vulnerable • Security patch - General software update to cover discovered vulnerabilities • Hotfix - Addresses specific customer situation • Service pack - Accumulates security updates and additional features Security+ Guide to Network Security Fundamentals, Fifth Edition 40
Securing the Operating System Software – Step 5 • Operating systems have increased in size and complexity • New attack tools have made secure functions vulnerable • Security patch - General software update to cover discovered vulnerabilities • Hotfix - Addresses specific customer situation • Service pack - Accumulates security updates and additional features Security+ Guide to Network Security Fundamentals, Fifth Edition 40
 Securing the Operating System Software – 5: Updates • Modern operating systems can perform automatic updates • OS interacts with vendor’s online update service to automatically download and install patches (depending upon configuration option chosen) • Patches can sometimes create new problems • Vendor should thoroughly test before deploying Security+ Guide to Network Security Fundamentals, Fifth Edition 41
Securing the Operating System Software – 5: Updates • Modern operating systems can perform automatic updates • OS interacts with vendor’s online update service to automatically download and install patches (depending upon configuration option chosen) • Patches can sometimes create new problems • Vendor should thoroughly test before deploying Security+ Guide to Network Security Fundamentals, Fifth Edition 41
 Securing the Operating System Software – 5: Automated Updates • Automated patch update service - Manage patches locally instead using vendor’s online update service • Advantages: – Administrators can approve or decline updates for client systems, force updates to install by specific date, and obtain reports on what updates each computer needs. – Administrators can approve updates for "detection" only (allows them see which computers will require update without actually installing it) Security+ Guide to Network Security Fundamentals, Fifth Edition 42
Securing the Operating System Software – 5: Automated Updates • Automated patch update service - Manage patches locally instead using vendor’s online update service • Advantages: – Administrators can approve or decline updates for client systems, force updates to install by specific date, and obtain reports on what updates each computer needs. – Administrators can approve updates for "detection" only (allows them see which computers will require update without actually installing it) Security+ Guide to Network Security Fundamentals, Fifth Edition 42
 Securing the Operating System Software – 5: Advantages – Downloading patches from local server instead of using the vendor’s online update service can save bandwidth and time because each computer does not have to connect to an external server – Specific types of updates that organization does not test (hotfixes) can be automatically installed whenever they become available – Users cannot disable or circumvent updates as they can if computer configured to use vendor’s online update service Security+ Guide to Network Security Fundamentals, Fifth Edition 43
Securing the Operating System Software – 5: Advantages – Downloading patches from local server instead of using the vendor’s online update service can save bandwidth and time because each computer does not have to connect to an external server – Specific types of updates that organization does not test (hotfixes) can be automatically installed whenever they become available – Users cannot disable or circumvent updates as they can if computer configured to use vendor’s online update service Security+ Guide to Network Security Fundamentals, Fifth Edition 43
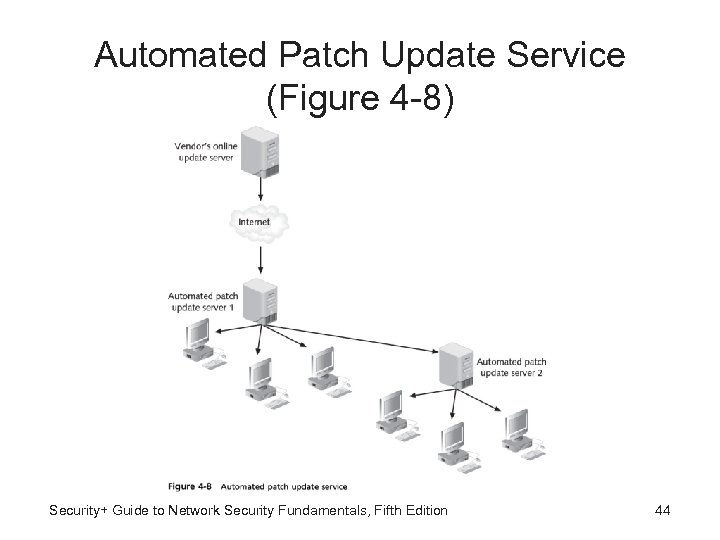 Automated Patch Update Service (Figure 4 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 44
Automated Patch Update Service (Figure 4 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 44
 Security Through Design • Other techniques used instead of managing different security options on an operating system that has already been deployed • OS hardening - Necessary to tighten security during design and coding of OS • Trusted OS - Operating system that has been designed through OS hardening Security+ Guide to Network Security Fundamentals, Fifth Edition 45
Security Through Design • Other techniques used instead of managing different security options on an operating system that has already been deployed • OS hardening - Necessary to tighten security during design and coding of OS • Trusted OS - Operating system that has been designed through OS hardening Security+ Guide to Network Security Fundamentals, Fifth Edition 45
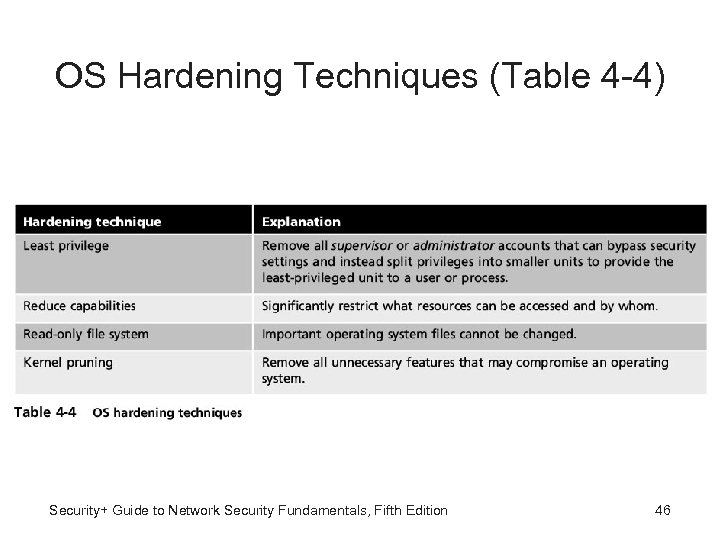 OS Hardening Techniques (Table 4 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 46
OS Hardening Techniques (Table 4 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 46
 Securing With Antimalware • Operating system software continued to add security protections to core set of features • Third-party antimalware software packages can provide added security • Antimalware software: – – Antivirus Antispam Popup blockers and antispyware Host-based firewalls Security+ Guide to Network Security Fundamentals, Fifth Edition 47
Securing With Antimalware • Operating system software continued to add security protections to core set of features • Third-party antimalware software packages can provide added security • Antimalware software: – – Antivirus Antispam Popup blockers and antispyware Host-based firewalls Security+ Guide to Network Security Fundamentals, Fifth Edition 47
 Antivirus • Antivirus (AV) - Software that examines computer for infections • Static analysis - Scan files by attempting to match known virus patterns against potentially infected files • Host AV software contains virus scanning engine and database of known virus signatures • By comparing virus signatures against potentially infected file (string scanning) match may indicate infected file Security+ Guide to Network Security Fundamentals, Fifth Edition 48
Antivirus • Antivirus (AV) - Software that examines computer for infections • Static analysis - Scan files by attempting to match known virus patterns against potentially infected files • Host AV software contains virus scanning engine and database of known virus signatures • By comparing virus signatures against potentially infected file (string scanning) match may indicate infected file Security+ Guide to Network Security Fundamentals, Fifth Edition 48
 Antivirus Scanning • Wildcard scanning - Wildcard is allowed to skip bytes or ranges of bytes instead of looking for an exact match • Mismatch scanning - Mismatches allow set number of bytes in string to be any value regardless of their position in the string • Weakness of static analysis is AV vendor must constantly be searching for new viruses, extracting virus signatures, and distributing those updated databases to all users Security+ Guide to Network Security Fundamentals, Fifth Edition 49
Antivirus Scanning • Wildcard scanning - Wildcard is allowed to skip bytes or ranges of bytes instead of looking for an exact match • Mismatch scanning - Mismatches allow set number of bytes in string to be any value regardless of their position in the string • Weakness of static analysis is AV vendor must constantly be searching for new viruses, extracting virus signatures, and distributing those updated databases to all users Security+ Guide to Network Security Fundamentals, Fifth Edition 49
 Antivirus Detection • Dynamic heuristic detection - Uses variety of techniques to spot characteristics of virus instead of attempting to make matches • Code emulation - Virtual environment is created that simulates the central processing unit (CPU) and memory of the computer • Any questionable program code is executed in virtual environment (no actual virus code is executed by the real CPU) to determine if is virus Security+ Guide to Network Security Fundamentals, Fifth Edition 50
Antivirus Detection • Dynamic heuristic detection - Uses variety of techniques to spot characteristics of virus instead of attempting to make matches • Code emulation - Virtual environment is created that simulates the central processing unit (CPU) and memory of the computer • Any questionable program code is executed in virtual environment (no actual virus code is executed by the real CPU) to determine if is virus Security+ Guide to Network Security Fundamentals, Fifth Edition 50
 Antispam • Spammers can distribute malware through email attachments or use for social engineering attacks • Bayesian filtering - Analyzes every word in each email and determines how frequently a word occurs in “spam” pile compared to “not-spam” pile • Create lists of senders: – Blacklist - Allow everything in unless it appears on the list – Whitelist - List of approved senders Security+ Guide to Network Security Fundamentals, Fifth Edition 51
Antispam • Spammers can distribute malware through email attachments or use for social engineering attacks • Bayesian filtering - Analyzes every word in each email and determines how frequently a word occurs in “spam” pile compared to “not-spam” pile • Create lists of senders: – Blacklist - Allow everything in unless it appears on the list – Whitelist - List of approved senders Security+ Guide to Network Security Fundamentals, Fifth Edition 51
 Pop-up Blocker • Pop-up - Small window appearing over webpage usually created by advertisers • Pop-up blocker - Separate program as part of antispyware package incorporated within browser that allows user to limit or block most pop-ups • Alert can be displayed in browser and gives user option to display pop-up Security+ Guide to Network Security Fundamentals, Fifth Edition 52
Pop-up Blocker • Pop-up - Small window appearing over webpage usually created by advertisers • Pop-up blocker - Separate program as part of antispyware package incorporated within browser that allows user to limit or block most pop-ups • Alert can be displayed in browser and gives user option to display pop-up Security+ Guide to Network Security Fundamentals, Fifth Edition 52
 Host-Based Application Firewall • Firewall (packet filter) - Designed prevent malicious packets from entering/leaving • May be hardware or software-based • Host-based application firewall - Software firewall runs on local system • Application running on a host computer may need send and receive transmissions that normally would be blocked by firewall • Opening the firewall can be created by the user simply by approving application Security+ Guide to Network Security Fundamentals, Fifth Edition 53
Host-Based Application Firewall • Firewall (packet filter) - Designed prevent malicious packets from entering/leaving • May be hardware or software-based • Host-based application firewall - Software firewall runs on local system • Application running on a host computer may need send and receive transmissions that normally would be blocked by firewall • Opening the firewall can be created by the user simply by approving application Security+ Guide to Network Security Fundamentals, Fifth Edition 53
 Securing Static Environments • As number of devices with microprocessors grows these becoming targets • Static environment - Types of devices with microprocessors not designed to be updated • Embedded system - Computer system with a dedicated function within a larger electrical or mechanical system • OS often stripped-down versions of generalpurpose operating systems and may contain many of the same vulnerabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 54
Securing Static Environments • As number of devices with microprocessors grows these becoming targets • Static environment - Types of devices with microprocessors not designed to be updated • Embedded system - Computer system with a dedicated function within a larger electrical or mechanical system • OS often stripped-down versions of generalpurpose operating systems and may contain many of the same vulnerabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 54
 Consoles, Smartphones & Mainframes • Game consoles - Many consumer game consoles contain adaptations of general-purpose operating systems and may contain some of same vulnerabilities • Smartphone - Includes an operating system that allows it to run third-party applications but operating systems have vulnerabilities that attackers can exploit • Mainframe - Very large computing systems that have significant processing capabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 55
Consoles, Smartphones & Mainframes • Game consoles - Many consumer game consoles contain adaptations of general-purpose operating systems and may contain some of same vulnerabilities • Smartphone - Includes an operating system that allows it to run third-party applications but operating systems have vulnerabilities that attackers can exploit • Mainframe - Very large computing systems that have significant processing capabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 55
 Automobile and SCADA • In-vehicle computer systems - Automobile functions that are controlled by microprocessors • SCADA (supervisory control and data acquisition) - Large-scale industrial-control systems found in military installations, oil pipeline control systems, manufacturing environments, and nuclear power plants Security+ Guide to Network Security Fundamentals, Fifth Edition 56
Automobile and SCADA • In-vehicle computer systems - Automobile functions that are controlled by microprocessors • SCADA (supervisory control and data acquisition) - Large-scale industrial-control systems found in military installations, oil pipeline control systems, manufacturing environments, and nuclear power plants Security+ Guide to Network Security Fundamentals, Fifth Edition 56
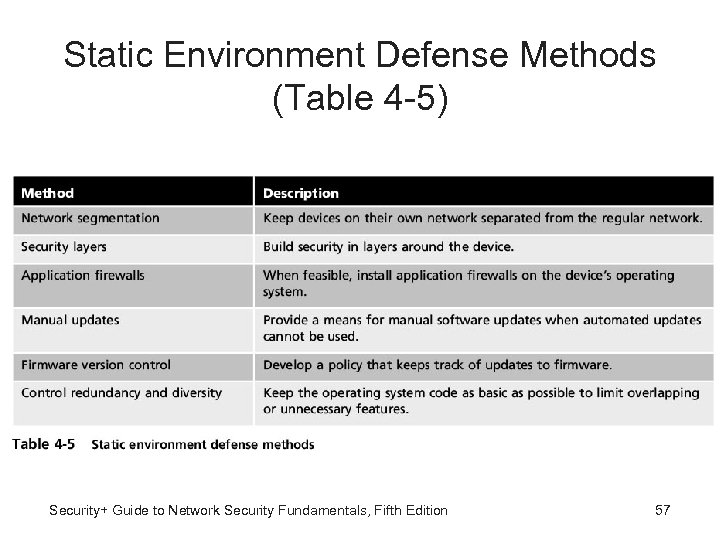 Static Environment Defense Methods (Table 4 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 57
Static Environment Defense Methods (Table 4 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 57
 Application Security • Along with securing the operating system software on hosts and in static environments, is equally need to protect applications that run on the devices • Application security: – Application development security – Application hardening and patch management Security+ Guide to Network Security Fundamentals, Fifth Edition 58
Application Security • Along with securing the operating system software on hosts and in static environments, is equally need to protect applications that run on the devices • Application security: – Application development security – Application hardening and patch management Security+ Guide to Network Security Fundamentals, Fifth Edition 58
 Application Development Security • Security for applications must be considered through all phases of development cycle • Application configuration baselines: – Standard environment settings can establish a secure baseline – Includes each development system, build system, and test system – Must include system and network configurations Security+ Guide to Network Security Fundamentals, Fifth Edition 59
Application Development Security • Security for applications must be considered through all phases of development cycle • Application configuration baselines: – Standard environment settings can establish a secure baseline – Includes each development system, build system, and test system – Must include system and network configurations Security+ Guide to Network Security Fundamentals, Fifth Edition 59
 Secure Coding Concepts • Secure coding concepts – Coding standards increase applications’ consistency, reliability, and security – Coding standards useful in code review process – Wrapper functions – Used to write error-checking routines for preexisting system functions (wrapper function is a substitute for a regular function that is used in testing) Security+ Guide to Network Security Fundamentals, Fifth Edition 60
Secure Coding Concepts • Secure coding concepts – Coding standards increase applications’ consistency, reliability, and security – Coding standards useful in code review process – Wrapper functions – Used to write error-checking routines for preexisting system functions (wrapper function is a substitute for a regular function that is used in testing) Security+ Guide to Network Security Fundamentals, Fifth Edition 60
 Exceptions • Errors (exceptions) - Faults that occur while application is running • Response should be based on the error • Improper handling can lead to application failure or insecurity • Fuzz testing (fuzzing) - Software testing technique that deliberately provides invalid, unexpected, or random data as inputs to computer program Security+ Guide to Network Security Fundamentals, Fifth Edition 61
Exceptions • Errors (exceptions) - Faults that occur while application is running • Response should be based on the error • Improper handling can lead to application failure or insecurity • Fuzz testing (fuzzing) - Software testing technique that deliberately provides invalid, unexpected, or random data as inputs to computer program Security+ Guide to Network Security Fundamentals, Fifth Edition 61
 Error Handling • Error handling practices to avoid: – Failing to check return codes or handle exceptions or improperly checking them – Handling all return codes or exceptions in the same manner – Divulging potentially sensitive data in error information Security+ Guide to Network Security Fundamentals, Fifth Edition 62
Error Handling • Error handling practices to avoid: – Failing to check return codes or handle exceptions or improperly checking them – Handling all return codes or exceptions in the same manner – Divulging potentially sensitive data in error information Security+ Guide to Network Security Fundamentals, Fifth Edition 62
 Input Validation • Verify user responses to application: – Could cause program to abort – Necessary to check for XSS, SQL, or XML injection attacks – Cross-site request forgery (XSRF) - Attack uses the user’s web browser settings to impersonate the user • Input validation – Verifies a user’s input to an application and is performed after data entered but before destination is known Security+ Guide to Network Security Fundamentals, Fifth Edition 63
Input Validation • Verify user responses to application: – Could cause program to abort – Necessary to check for XSS, SQL, or XML injection attacks – Cross-site request forgery (XSRF) - Attack uses the user’s web browser settings to impersonate the user • Input validation – Verifies a user’s input to an application and is performed after data entered but before destination is known Security+ Guide to Network Security Fundamentals, Fifth Edition 63
 Server and Client Validation • Server-side validation - Input validation generally uses the server to perform the validation • Client-side validation - Client perform the validation Security+ Guide to Network Security Fundamentals, Fifth Edition 64
Server and Client Validation • Server-side validation - Input validation generally uses the server to perform the validation • Client-side validation - Client perform the validation Security+ Guide to Network Security Fundamentals, Fifth Edition 64
 SQL Alternatives • Instead of input validation, more drastic approach to preventing SQL injection attacks is avoid using SQL relational databases altogether • No. SQL - New nonrelational databases that are better tuned for accessing large data sets • No. SQL databases vs. SQL database – Argument over which database technology is better Security+ Guide to Network Security Fundamentals, Fifth Edition 65
SQL Alternatives • Instead of input validation, more drastic approach to preventing SQL injection attacks is avoid using SQL relational databases altogether • No. SQL - New nonrelational databases that are better tuned for accessing large data sets • No. SQL databases vs. SQL database – Argument over which database technology is better Security+ Guide to Network Security Fundamentals, Fifth Edition 65
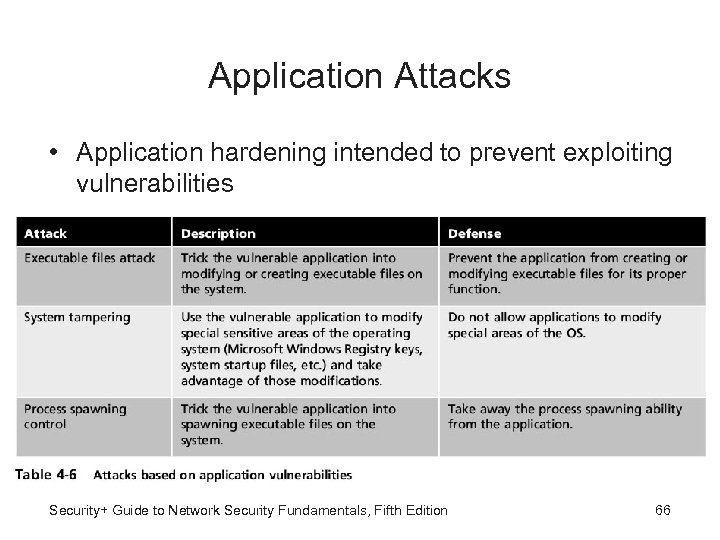 Application Attacks • Application hardening intended to prevent exploiting vulnerabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 66
Application Attacks • Application hardening intended to prevent exploiting vulnerabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 66
 Application Patch Management • Application patch management rare until recently • Users unaware of the existence of patches or where to acquire them • More application patch management systems are being developed today Security+ Guide to Network Security Fundamentals, Fifth Edition 67
Application Patch Management • Application patch management rare until recently • Users unaware of the existence of patches or where to acquire them • More application patch management systems are being developed today Security+ Guide to Network Security Fundamentals, Fifth Edition 67
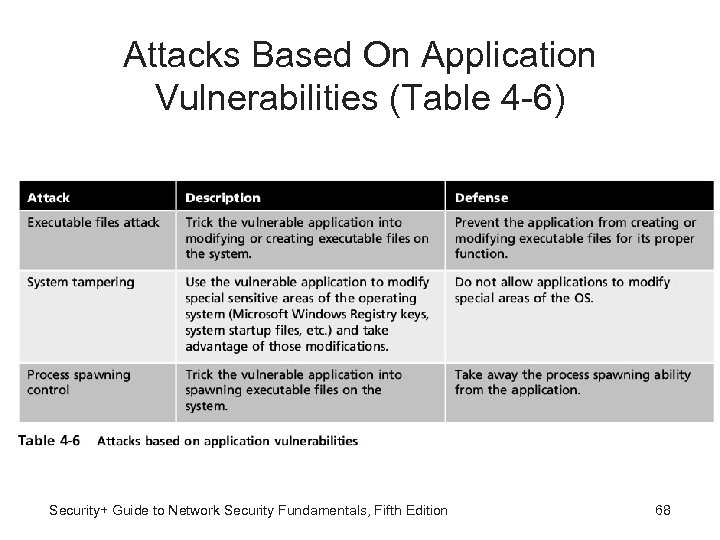 Attacks Based On Application Vulnerabilities (Table 4 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 68
Attacks Based On Application Vulnerabilities (Table 4 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 68
 Securing Data • Work today involves electronic collaboration, so data must flow freely but securely • Data loss prevention (DLP) - System of security tools used to recognize and identify critical data and ensure it is protected • Goal is protect data: – Data in-use - Data actions being performed by “endpoint devices” – Data in-transit - Actions that transmit the data across a network – Data at-rest - Stored on electronic media Security+ Guide to Network Security Fundamentals, Fifth Edition 69
Securing Data • Work today involves electronic collaboration, so data must flow freely but securely • Data loss prevention (DLP) - System of security tools used to recognize and identify critical data and ensure it is protected • Goal is protect data: – Data in-use - Data actions being performed by “endpoint devices” – Data in-transit - Actions that transmit the data across a network – Data at-rest - Stored on electronic media Security+ Guide to Network Security Fundamentals, Fifth Edition 69
 DLP Techniques • Content inspection - Security analysis of transaction and takes context into account • DLP systems also can use index matching: – Documents identified as needing protection, such as the program source code for a new software application, are analyzed by DLP system – Complex computations are conducted based on analysis Security+ Guide to Network Security Fundamentals, Fifth Edition 70
DLP Techniques • Content inspection - Security analysis of transaction and takes context into account • DLP systems also can use index matching: – Documents identified as needing protection, such as the program source code for a new software application, are analyzed by DLP system – Complex computations are conducted based on analysis Security+ Guide to Network Security Fundamentals, Fifth Edition 70
 DLP Sensors • DLP sensors: – DLP network sensors - Installed on perimeter of network to protect data in-transit by monitoring all network traffic – DLP storage sensors - Sensors on network storage devices are designed to protect data at-rest – DLP agent sensors - Sensors are installed on each host device (desktop, laptop, tablet, etc. ) and protect data in-use Security+ Guide to Network Security Fundamentals, Fifth Edition 71
DLP Sensors • DLP sensors: – DLP network sensors - Installed on perimeter of network to protect data in-transit by monitoring all network traffic – DLP storage sensors - Sensors on network storage devices are designed to protect data at-rest – DLP agent sensors - Sensors are installed on each host device (desktop, laptop, tablet, etc. ) and protect data in-use Security+ Guide to Network Security Fundamentals, Fifth Edition 71
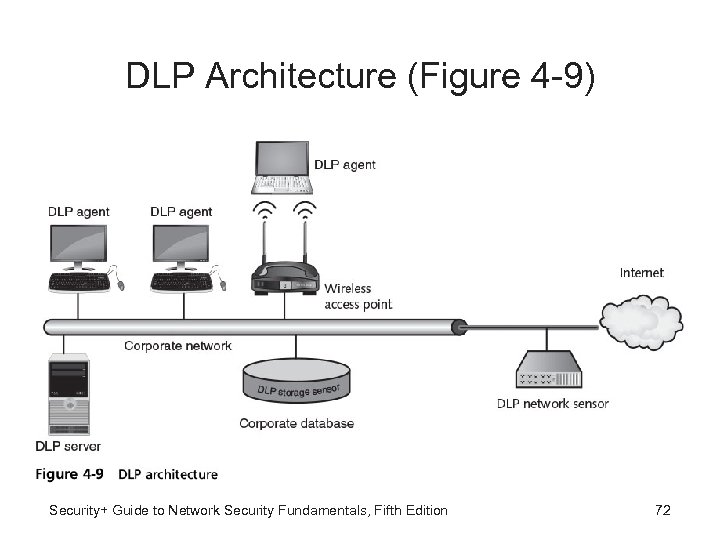 DLP Architecture (Figure 4 -9) Security+ Guide to Network Security Fundamentals, Fifth Edition 72
DLP Architecture (Figure 4 -9) Security+ Guide to Network Security Fundamentals, Fifth Edition 72
 DLP Report (Figure 4 -10) Security+ Guide to Network Security Fundamentals, Fifth Edition 73
DLP Report (Figure 4 -10) Security+ Guide to Network Security Fundamentals, Fifth Edition 73
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 4 Application, Data, and Host Security
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 4 Application, Data, and Host Security


