484c69b765bdee7d91dca8344fd464f2.ppt
- Количество слайдов: 63
 Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 8 Administering a Secure Network
Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 8 Administering a Secure Network
 Objectives • List and describe the functions of common network protocols • Explain how network administration principles can be applied • Define the new types of network applications and how they can be secured Security+ Guide to Network Security Fundamentals, Fifth Edition 2
Objectives • List and describe the functions of common network protocols • Explain how network administration principles can be applied • Define the new types of network applications and how they can be secured Security+ Guide to Network Security Fundamentals, Fifth Edition 2
 Common Network Protocols • Protocols - Rules of conduct and communication • Essential for proper communication between network devices • Transmission Control Protocol/Internet Protocol (TCP/IP) - Most common protocol suite used for local area networks and the Internet Security+ Guide to Network Security Fundamentals, Fifth Edition 3
Common Network Protocols • Protocols - Rules of conduct and communication • Essential for proper communication between network devices • Transmission Control Protocol/Internet Protocol (TCP/IP) - Most common protocol suite used for local area networks and the Internet Security+ Guide to Network Security Fundamentals, Fifth Edition 3
 IP and TCP • IP - Protocol that functions primarily at Open Systems Interconnection (OSI) Network Layer (Layer 3) • TCP - Transport Layer (Layer 4) protocol that establishes connections and reliable data transport between devices • TCP/IP uses four layer architecture: – – Network Interface Internet Transport Application Security+ Guide to Network Security Fundamentals, Fifth Edition 4
IP and TCP • IP - Protocol that functions primarily at Open Systems Interconnection (OSI) Network Layer (Layer 3) • TCP - Transport Layer (Layer 4) protocol that establishes connections and reliable data transport between devices • TCP/IP uses four layer architecture: – – Network Interface Internet Transport Application Security+ Guide to Network Security Fundamentals, Fifth Edition 4
 OSI model vs. TCP/IP model (Figure 8 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 5
OSI model vs. TCP/IP model (Figure 8 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 5
 Internet Control Message Protocol (ICMP) • Internet Control Message Protocol (ICMP) - One of core protocols of TCP/IP • Used by devices to communicate updates or send information to other devices • Used to relay query messages • ICMP messages divided into two classes: – Informational and query messages – Error messages Security+ Guide to Network Security Fundamentals, Fifth Edition 6
Internet Control Message Protocol (ICMP) • Internet Control Message Protocol (ICMP) - One of core protocols of TCP/IP • Used by devices to communicate updates or send information to other devices • Used to relay query messages • ICMP messages divided into two classes: – Informational and query messages – Error messages Security+ Guide to Network Security Fundamentals, Fifth Edition 6
 ICMP Message Fields • ICMP message fields: – Type - Identifies general message category – Code - Gives additional information about the Type field – Checksum - Verifies message integrity – Message Body Security+ Guide to Network Security Fundamentals, Fifth Edition 7
ICMP Message Fields • ICMP message fields: – Type - Identifies general message category – Code - Gives additional information about the Type field – Checksum - Verifies message integrity – Message Body Security+ Guide to Network Security Fundamentals, Fifth Edition 7
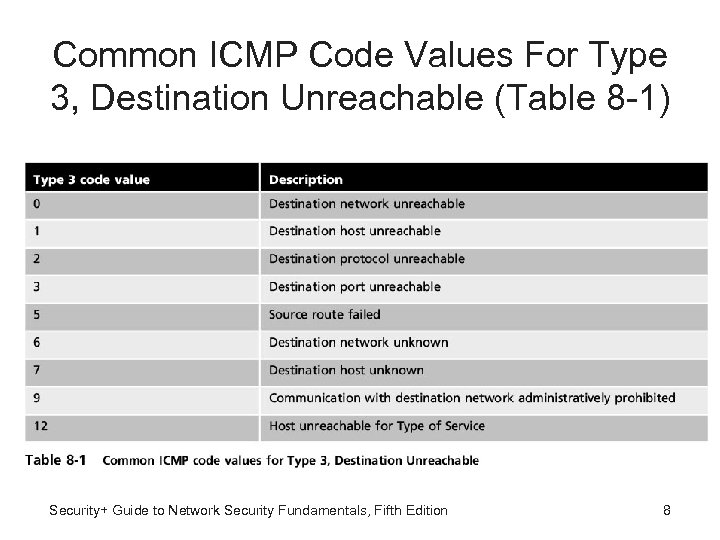 Common ICMP Code Values For Type 3, Destination Unreachable (Table 8 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 8
Common ICMP Code Values For Type 3, Destination Unreachable (Table 8 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 8
 ICMP Attacks • Attacks that use ICMP: – – Network discovery Smurf attack ICMP redirect attack Ping of death Security+ Guide to Network Security Fundamentals, Fifth Edition 9
ICMP Attacks • Attacks that use ICMP: – – Network discovery Smurf attack ICMP redirect attack Ping of death Security+ Guide to Network Security Fundamentals, Fifth Edition 9
 Simple Network Management Protocol (SNMP) • Simple Network Management Protocol (SNMP) Popular protocol used manage network equipment and supported by most network equipment manufacturers • Allows administrators to remotely monitor, manage, and configure network devices • Functions by exchanging management information between network devices • Each SNMP-managed device has an agent or service that listens for and executes commands Security+ Guide to Network Security Fundamentals, Fifth Edition 10
Simple Network Management Protocol (SNMP) • Simple Network Management Protocol (SNMP) Popular protocol used manage network equipment and supported by most network equipment manufacturers • Allows administrators to remotely monitor, manage, and configure network devices • Functions by exchanging management information between network devices • Each SNMP-managed device has an agent or service that listens for and executes commands Security+ Guide to Network Security Fundamentals, Fifth Edition 10
 SNMP Security Vulnerabilities • Agents are password protected with password known as community string • Security vulnerabilities were present in SMNP versions 1 and 2 • Version 3 introduced in 1998 • Uses usernames and passwords along with encryption to address vulnerabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 11
SNMP Security Vulnerabilities • Agents are password protected with password known as community string • Security vulnerabilities were present in SMNP versions 1 and 2 • Version 3 introduced in 1998 • Uses usernames and passwords along with encryption to address vulnerabilities Security+ Guide to Network Security Fundamentals, Fifth Edition 11
 Domain Name System (DNS) • Domain Name System (DNS) - TCP/IP protocol that resolves (maps) a symbolic name (www. cengage. com) with its corresponding IP address (69. 32. 133. 11) • DNS database is organized as a hierarchy (tree) • Not on single server • DNS database is divided and distributed to many different servers on the Internet, each of which is responsible for different areas the Internet Security+ Guide to Network Security Fundamentals, Fifth Edition 12
Domain Name System (DNS) • Domain Name System (DNS) - TCP/IP protocol that resolves (maps) a symbolic name (www. cengage. com) with its corresponding IP address (69. 32. 133. 11) • DNS database is organized as a hierarchy (tree) • Not on single server • DNS database is divided and distributed to many different servers on the Internet, each of which is responsible for different areas the Internet Security+ Guide to Network Security Fundamentals, Fifth Edition 12
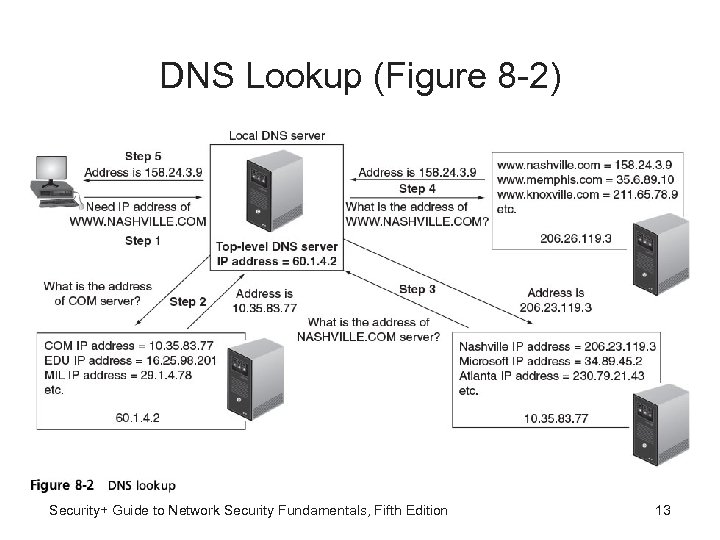 DNS Lookup (Figure 8 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 13
DNS Lookup (Figure 8 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 13
 DNS Attacks • DNS can be the focus of attacks • DNS poisoning - Substitutes fraudulent IP address • Can be done in local host table or external DNS server • Latest edition of DNS software prevents DNS poisoning • Zone transfer allows attacker access to network, hardware, and operating system information Security+ Guide to Network Security Fundamentals, Fifth Edition 14
DNS Attacks • DNS can be the focus of attacks • DNS poisoning - Substitutes fraudulent IP address • Can be done in local host table or external DNS server • Latest edition of DNS software prevents DNS poisoning • Zone transfer allows attacker access to network, hardware, and operating system information Security+ Guide to Network Security Fundamentals, Fifth Edition 14
 File Transfer Protocols • TCP/IP protocols used for transferring files: – File transfer protocol (FTP) – Secure transfer protocol (SCP) Security+ Guide to Network Security Fundamentals, Fifth Edition 15
File Transfer Protocols • TCP/IP protocols used for transferring files: – File transfer protocol (FTP) – Secure transfer protocol (SCP) Security+ Guide to Network Security Fundamentals, Fifth Edition 15
 File Transfer Protocol (FTP) • File Transfer Protocol (FTP) - Unsecure TCP/IP protocol for transferring • FTP used to connect to FTP server, much in same way that HTTP links to a web server • Trivial File Transfer Protocol (TFTP) - Uses small amount of memory but has limited functionality; often used for the automated transfer of configuration files between devices Security+ Guide to Network Security Fundamentals, Fifth Edition 16
File Transfer Protocol (FTP) • File Transfer Protocol (FTP) - Unsecure TCP/IP protocol for transferring • FTP used to connect to FTP server, much in same way that HTTP links to a web server • Trivial File Transfer Protocol (TFTP) - Uses small amount of memory but has limited functionality; often used for the automated transfer of configuration files between devices Security+ Guide to Network Security Fundamentals, Fifth Edition 16
 FTP Methods • Different methods for using FTP on a local computer: – From command prompt – Using web browser – Using FTP client Security+ Guide to Network Security Fundamentals, Fifth Edition 17
FTP Methods • Different methods for using FTP on a local computer: – From command prompt – Using web browser – Using FTP client Security+ Guide to Network Security Fundamentals, Fifth Edition 17
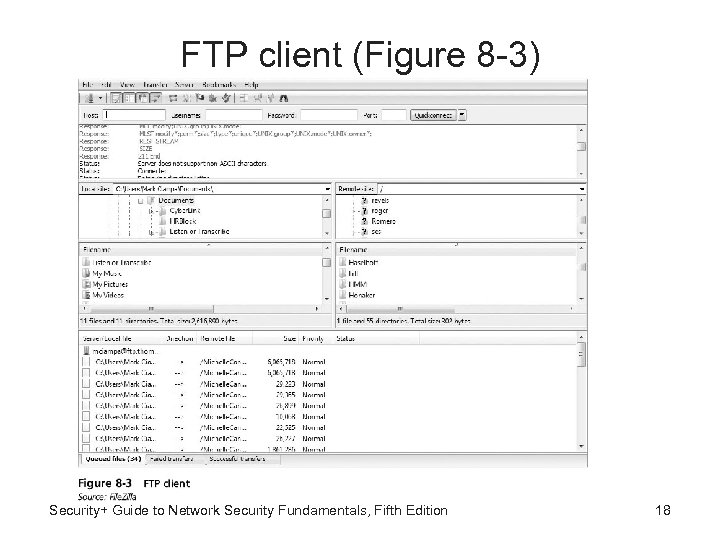 FTP client (Figure 8 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 18
FTP client (Figure 8 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 18
 FTP Security • FTP vulnerabilities: – Does not use encryption – Files transferred using FTP vulnerable to man-in-themiddle attacks • FTP Secure (FTPS) - Uses Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt commands • Secure FTP (SFTP) - Entire protocol uses single TCP port and encrypts and compresses all data and commands Security+ Guide to Network Security Fundamentals, Fifth Edition 19
FTP Security • FTP vulnerabilities: – Does not use encryption – Files transferred using FTP vulnerable to man-in-themiddle attacks • FTP Secure (FTPS) - Uses Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt commands • Secure FTP (SFTP) - Entire protocol uses single TCP port and encrypts and compresses all data and commands Security+ Guide to Network Security Fundamentals, Fifth Edition 19
 Secure Copy Protocol (SCP) • Secure Copy Protocol (SCP) - Enhanced version of Remote Copy Protocol • Encrypts files and commands • File transfer cannot be interrupted and resumed • Found mainly on Linux and UNIX platforms Security+ Guide to Network Security Fundamentals, Fifth Edition 20
Secure Copy Protocol (SCP) • Secure Copy Protocol (SCP) - Enhanced version of Remote Copy Protocol • Encrypts files and commands • File transfer cannot be interrupted and resumed • Found mainly on Linux and UNIX platforms Security+ Guide to Network Security Fundamentals, Fifth Edition 20
 Storage Protocols • Enterprise data storage facilities and networking protocols cannot always cope with the need to store and transmit large volumes of data • Storage area network (SAN) - Dedicated network storage facility that provides access to data storage over a high-speed network • SANs consolidate different storage facilities that appear as single pool of locally attached devices Security+ Guide to Network Security Fundamentals, Fifth Edition 21
Storage Protocols • Enterprise data storage facilities and networking protocols cannot always cope with the need to store and transmit large volumes of data • Storage area network (SAN) - Dedicated network storage facility that provides access to data storage over a high-speed network • SANs consolidate different storage facilities that appear as single pool of locally attached devices Security+ Guide to Network Security Fundamentals, Fifth Edition 21
 Common Storage Protocols • i. SCSI (Internet Small Computer System Interface) - IP-based storage networking standard for linking data storage facilities over LANs, wide area networks (WANs), and Internet • Fibre Channel (FC) - High-speed storage network protocol can transmit up to 16 gigabits per second • Fibre Channel over Ethernet (FCo. E) Encapsulates Fibre Channel frames over Ethernet networks so can use fast Ethernet networks while preserving Fibre Channel protocol Security+ Guide to Network Security Fundamentals, Fifth Edition 22
Common Storage Protocols • i. SCSI (Internet Small Computer System Interface) - IP-based storage networking standard for linking data storage facilities over LANs, wide area networks (WANs), and Internet • Fibre Channel (FC) - High-speed storage network protocol can transmit up to 16 gigabits per second • Fibre Channel over Ethernet (FCo. E) Encapsulates Fibre Channel frames over Ethernet networks so can use fast Ethernet networks while preserving Fibre Channel protocol Security+ Guide to Network Security Fundamentals, Fifth Edition 22
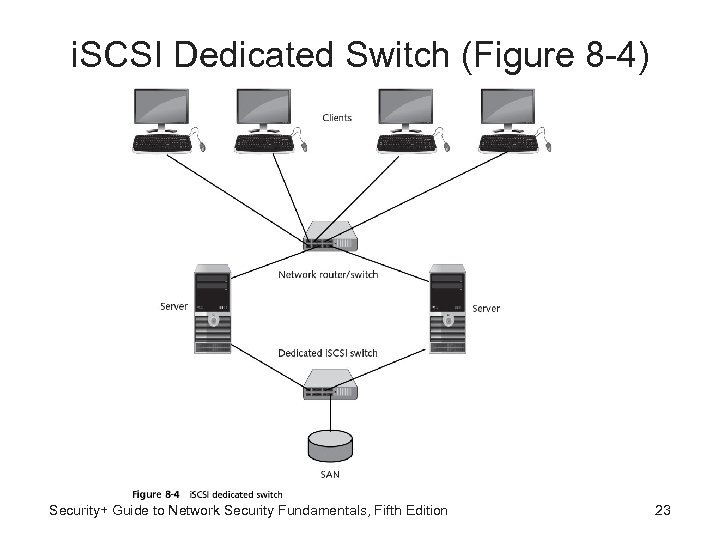 i. SCSI Dedicated Switch (Figure 8 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 23
i. SCSI Dedicated Switch (Figure 8 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 23
 Net. BIOS (Network Basic Input/Output System) • Net. BIOS (Network Basic Input/Output System) Transport protocol used by Microsoft Windows systems to allow applications on separate computers to communicate over LAN • Normally runs over TCP/IP through Net. BIOS over TCP/IP (NBT) protocol • Results in each computer in network having both IP address and Net. BIOS name Security+ Guide to Network Security Fundamentals, Fifth Edition 24
Net. BIOS (Network Basic Input/Output System) • Net. BIOS (Network Basic Input/Output System) Transport protocol used by Microsoft Windows systems to allow applications on separate computers to communicate over LAN • Normally runs over TCP/IP through Net. BIOS over TCP/IP (NBT) protocol • Results in each computer in network having both IP address and Net. BIOS name Security+ Guide to Network Security Fundamentals, Fifth Edition 24
 Net. BIOS Attacks • Attacker who determines Net. BIOS is running can use application to gather information regarding network to design attack: – Computer names – Contents of the remote name cache including IP addresses – List of local Net. BIOS names – List of resolved names Security+ Guide to Network Security Fundamentals, Fifth Edition 25
Net. BIOS Attacks • Attacker who determines Net. BIOS is running can use application to gather information regarding network to design attack: – Computer names – Contents of the remote name cache including IP addresses – List of local Net. BIOS names – List of resolved names Security+ Guide to Network Security Fundamentals, Fifth Edition 25
 Telnet • Telnet: – Older TCP/IP protocol for text-based communication – Terminal emulation application program that runs on local computer that connects to server on network • Several security vulnerabilities: – Does not encrypt data so any passwords sent over Telnet to log into the server can easily be discovered – Security weaknesses have been uncovered within this protocol Security+ Guide to Network Security Fundamentals, Fifth Edition 26
Telnet • Telnet: – Older TCP/IP protocol for text-based communication – Terminal emulation application program that runs on local computer that connects to server on network • Several security vulnerabilities: – Does not encrypt data so any passwords sent over Telnet to log into the server can easily be discovered – Security weaknesses have been uncovered within this protocol Security+ Guide to Network Security Fundamentals, Fifth Edition 26
 IPv 4 • IPv 4 - Current version of IP protocol • Developed in 1981 • Number of available IP address is limited to 4. 3 billion • Has security weaknesses Security+ Guide to Network Security Fundamentals, Fifth Edition 27
IPv 4 • IPv 4 - Current version of IP protocol • Developed in 1981 • Number of available IP address is limited to 4. 3 billion • Has security weaknesses Security+ Guide to Network Security Fundamentals, Fifth Edition 27
 IPv 6 • • IPv 6 - Internet Protocol version 6 Next generation of IP protocol Addresses weaknesses of IPv 4 Cryptographic protocols are part of the core protocol that provides secure data communication • New authentication headers prevent IP packets from being tampered or altered • Differences can be seen in different header structures Security+ Guide to Network Security Fundamentals, Fifth Edition 28
IPv 6 • • IPv 6 - Internet Protocol version 6 Next generation of IP protocol Addresses weaknesses of IPv 4 Cryptographic protocols are part of the core protocol that provides secure data communication • New authentication headers prevent IP packets from being tampered or altered • Differences can be seen in different header structures Security+ Guide to Network Security Fundamentals, Fifth Edition 28
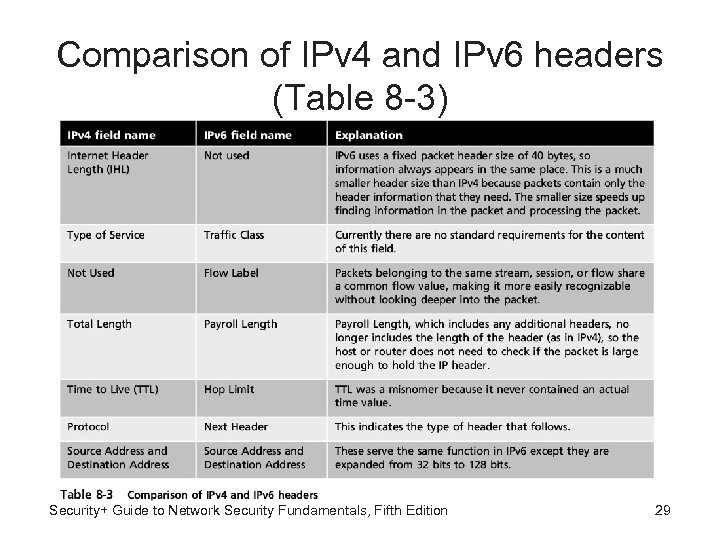 Comparison of IPv 4 and IPv 6 headers (Table 8 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 29
Comparison of IPv 4 and IPv 6 headers (Table 8 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 29
 IPv 6 Security • Provides enhanced security features: – Cryptographic protocols – New authentication headers prevent IP packets from being altered Security+ Guide to Network Security Fundamentals, Fifth Edition 30
IPv 6 Security • Provides enhanced security features: – Cryptographic protocols – New authentication headers prevent IP packets from being altered Security+ Guide to Network Security Fundamentals, Fifth Edition 30
 Network Administration Principles • Rule-based management approach - Relies on following procedures and rules • Rules may be external (applicable laws) or internal • Procedural rules dictate technical rules • Technical rules: – Device security – Network management and port security – Example: configuring a firewall to conform to procedural rules Security+ Guide to Network Security Fundamentals, Fifth Edition 31
Network Administration Principles • Rule-based management approach - Relies on following procedures and rules • Rules may be external (applicable laws) or internal • Procedural rules dictate technical rules • Technical rules: – Device security – Network management and port security – Example: configuring a firewall to conform to procedural rules Security+ Guide to Network Security Fundamentals, Fifth Edition 31
 Secure Router Configuration • Router operates at Network Layer (Layer 3) to forward packets across computer networks • Routers can perform a security function • Can be configured to filter out specific types of network traffic Security+ Guide to Network Security Fundamentals, Fifth Edition 32
Secure Router Configuration • Router operates at Network Layer (Layer 3) to forward packets across computer networks • Routers can perform a security function • Can be configured to filter out specific types of network traffic Security+ Guide to Network Security Fundamentals, Fifth Edition 32
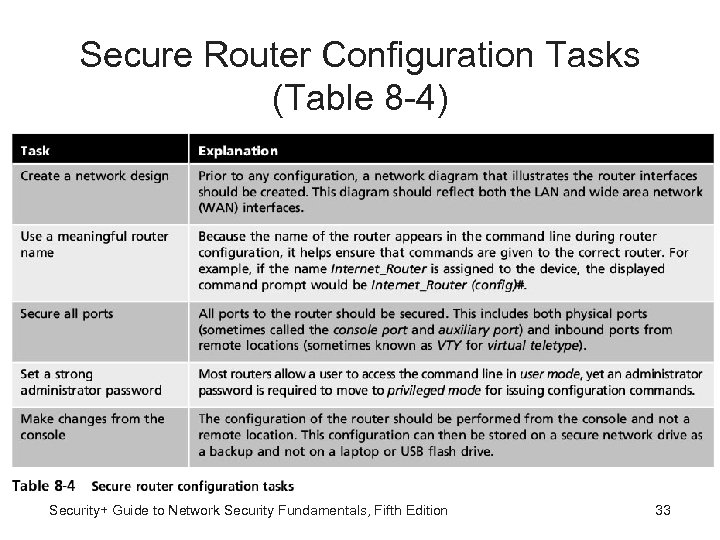 Secure Router Configuration Tasks (Table 8 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 33
Secure Router Configuration Tasks (Table 8 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 33
 Flood Guard • Do. S and DDo. S SYN flood attack takes advantage of procedures for initiating a session • Flood guard - Controls device’s tolerance for unanswered service requests • Set maximum number of “developing” connections • Commonly found on firewalls, IDSs, and IPSs • Protects against Do. S and DDo. S SYN flood attacks Security+ Guide to Network Security Fundamentals, Fifth Edition 34
Flood Guard • Do. S and DDo. S SYN flood attack takes advantage of procedures for initiating a session • Flood guard - Controls device’s tolerance for unanswered service requests • Set maximum number of “developing” connections • Commonly found on firewalls, IDSs, and IPSs • Protects against Do. S and DDo. S SYN flood attacks Security+ Guide to Network Security Fundamentals, Fifth Edition 34
 Monitoring and Analyzing Logs • Log - Record of events that occur • Security logs - Can reveal types of attacks being directed at network and if any were successful: – Access log - Provide details regarding requests for specific files on a system – Audit log - Used to record which user performed an action and what that action was – Event logs - Document any unsuccessful events and the most significant successful events • Almost all network devices can capture log data Security+ Guide to Network Security Fundamentals, Fifth Edition 35
Monitoring and Analyzing Logs • Log - Record of events that occur • Security logs - Can reveal types of attacks being directed at network and if any were successful: – Access log - Provide details regarding requests for specific files on a system – Audit log - Used to record which user performed an action and what that action was – Event logs - Document any unsuccessful events and the most significant successful events • Almost all network devices can capture log data Security+ Guide to Network Security Fundamentals, Fifth Edition 35
 Firewall Log • Example of items examined in firewall log: – IP addresses that are being rejected and dropped – Probes to ports that have no application services running on them – Source-routed packets – Suspicious outbound connections – Unsuccessful logins Security+ Guide to Network Security Fundamentals, Fifth Edition 36
Firewall Log • Example of items examined in firewall log: – IP addresses that are being rejected and dropped – Probes to ports that have no application services running on them – Source-routed packets – Suspicious outbound connections – Unsuccessful logins Security+ Guide to Network Security Fundamentals, Fifth Edition 36
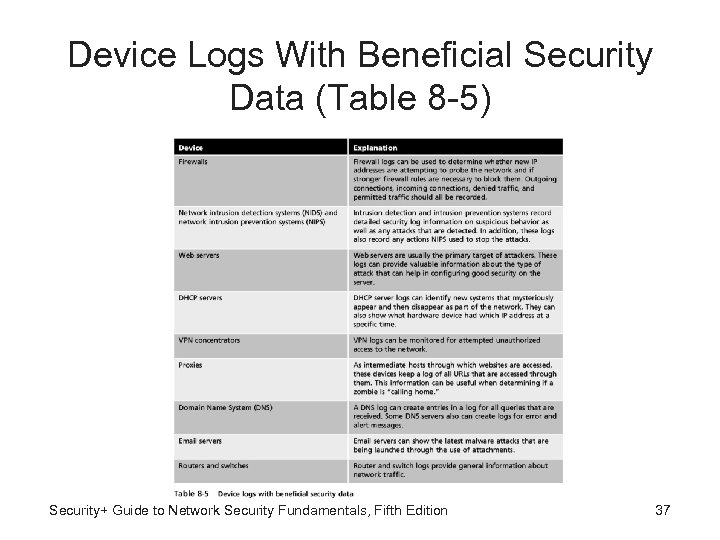 Device Logs With Beneficial Security Data (Table 8 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 37
Device Logs With Beneficial Security Data (Table 8 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 37
 Log Analyzer • Problems with log management (generating, transmitting, storing, analyzing, and disposing of computer security log data): – Multiple devices generating logs – Very large volume of data – Different log formats • One solution use centralized device log analyzer Security+ Guide to Network Security Fundamentals, Fifth Edition 38
Log Analyzer • Problems with log management (generating, transmitting, storing, analyzing, and disposing of computer security log data): – Multiple devices generating logs – Very large volume of data – Different log formats • One solution use centralized device log analyzer Security+ Guide to Network Security Fundamentals, Fifth Edition 38
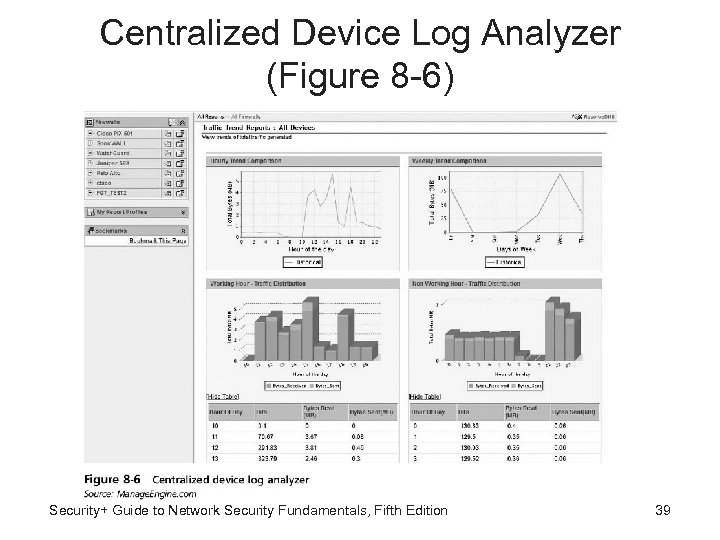 Centralized Device Log Analyzer (Figure 8 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 39
Centralized Device Log Analyzer (Figure 8 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 39
 Network Design Management • Several network design management principles should be followed to ensure security and viability of network are maintained: – Network separation to prevent bridging – Loop protection – VLAN management Security+ Guide to Network Security Fundamentals, Fifth Edition 40
Network Design Management • Several network design management principles should be followed to ensure security and viability of network are maintained: – Network separation to prevent bridging – Loop protection – VLAN management Security+ Guide to Network Security Fundamentals, Fifth Edition 40
 Network Separation • Separate secure parts of network from unsecure parts • Can physically separate users by connecting them to different switches and routers • Prevents bridging • Prevents reconfigured device from allowing that connection to occur Security+ Guide to Network Security Fundamentals, Fifth Edition 41
Network Separation • Separate secure parts of network from unsecure parts • Can physically separate users by connecting them to different switches and routers • Prevents bridging • Prevents reconfigured device from allowing that connection to occur Security+ Guide to Network Security Fundamentals, Fifth Edition 41
 Loop Protection • Switching loop causes broadcast storm as frames are broadcast, received, and rebroadcast by each switch • Broadcast storms can cripple network in matter of seconds to point no legitimate traffic can occur • Loop protection – Prevents broadcast storms • Spanning-tree algorithm (STA) - Uses IEEE 802. 1 d standard to determine that switch has multiple ways to communicate with host and then determine best path while blocking out other paths Security+ Guide to Network Security Fundamentals, Fifth Edition 42
Loop Protection • Switching loop causes broadcast storm as frames are broadcast, received, and rebroadcast by each switch • Broadcast storms can cripple network in matter of seconds to point no legitimate traffic can occur • Loop protection – Prevents broadcast storms • Spanning-tree algorithm (STA) - Uses IEEE 802. 1 d standard to determine that switch has multiple ways to communicate with host and then determine best path while blocking out other paths Security+ Guide to Network Security Fundamentals, Fifth Edition 42
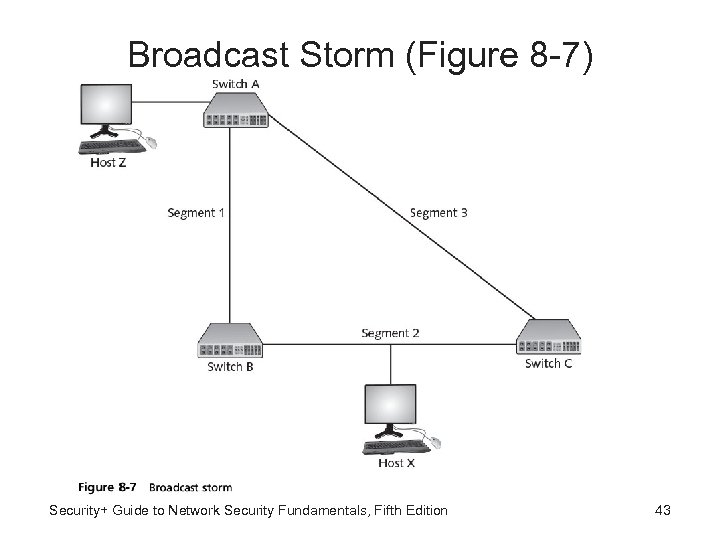 Broadcast Storm (Figure 8 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 43
Broadcast Storm (Figure 8 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 43
 VLAN Management • Virtual LAN (VLAN) management - Network may be segmented into logical groups of physical devices through VLAN • Scattered users may be logically grouped together regardless of which switch they are attached Security+ Guide to Network Security Fundamentals, Fifth Edition 44
VLAN Management • Virtual LAN (VLAN) management - Network may be segmented into logical groups of physical devices through VLAN • Scattered users may be logically grouped together regardless of which switch they are attached Security+ Guide to Network Security Fundamentals, Fifth Edition 44
 VLAN Management Principles • General principles for managing VLANs: – Configure empty switch ports to connect to an unused VLAN – Change any default VLAN names – Configure the ports on the switch that pass tagged VLAN packets to explicitly forward specific tags – Configure VLANs so that public devices are not on a private VLAN, forcing users to have access to that VLAN Security+ Guide to Network Security Fundamentals, Fifth Edition 45
VLAN Management Principles • General principles for managing VLANs: – Configure empty switch ports to connect to an unused VLAN – Change any default VLAN names – Configure the ports on the switch that pass tagged VLAN packets to explicitly forward specific tags – Configure VLANs so that public devices are not on a private VLAN, forcing users to have access to that VLAN Security+ Guide to Network Security Fundamentals, Fifth Edition 45
 Port Security • Disabling unused interfaces - Turn off ports not required on network • Often overlooked security technique • Switch without port security allows attackers to connect to unused ports and attack network • All ports should be secured before switch is deployed • Network administrator should issue shutdown command to each unused port Security+ Guide to Network Security Fundamentals, Fifth Edition 46
Port Security • Disabling unused interfaces - Turn off ports not required on network • Often overlooked security technique • Switch without port security allows attackers to connect to unused ports and attack network • All ports should be secured before switch is deployed • Network administrator should issue shutdown command to each unused port Security+ Guide to Network Security Fundamentals, Fifth Edition 46
 MAC Limiting and Filtering • MAC limiting and filtering - Filters and limits number of media access control (MAC) addresses allowed on port • Port can be set to limit of 1 • Specific MAC address can be assigned to a port • Enables only single authorized host to connect Security+ Guide to Network Security Fundamentals, Fifth Edition 47
MAC Limiting and Filtering • MAC limiting and filtering - Filters and limits number of media access control (MAC) addresses allowed on port • Port can be set to limit of 1 • Specific MAC address can be assigned to a port • Enables only single authorized host to connect Security+ Guide to Network Security Fundamentals, Fifth Edition 47
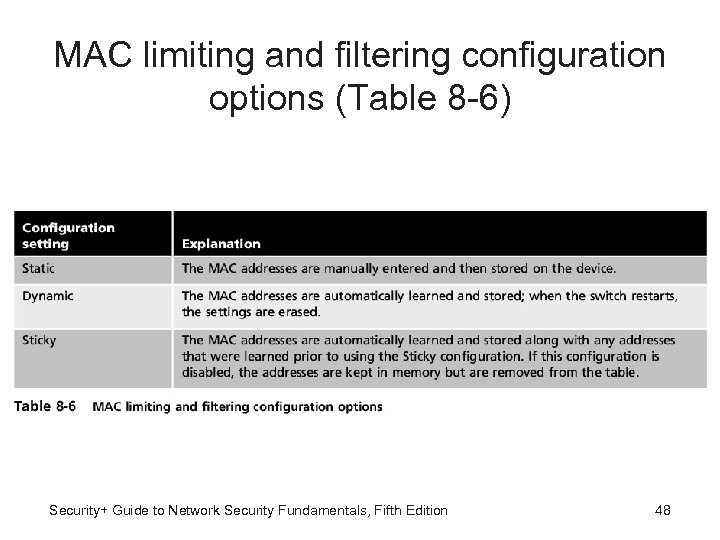 MAC limiting and filtering configuration options (Table 8 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 48
MAC limiting and filtering configuration options (Table 8 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 48
 IEEE 802. 1 x • IEEE 802. 1 x - Standard that provides highest degree of port security • Implements port-based authentication • Blocks all traffic on a port-by-port basis until client is authenticated Security+ Guide to Network Security Fundamentals, Fifth Edition 49
IEEE 802. 1 x • IEEE 802. 1 x - Standard that provides highest degree of port security • Implements port-based authentication • Blocks all traffic on a port-by-port basis until client is authenticated Security+ Guide to Network Security Fundamentals, Fifth Edition 49
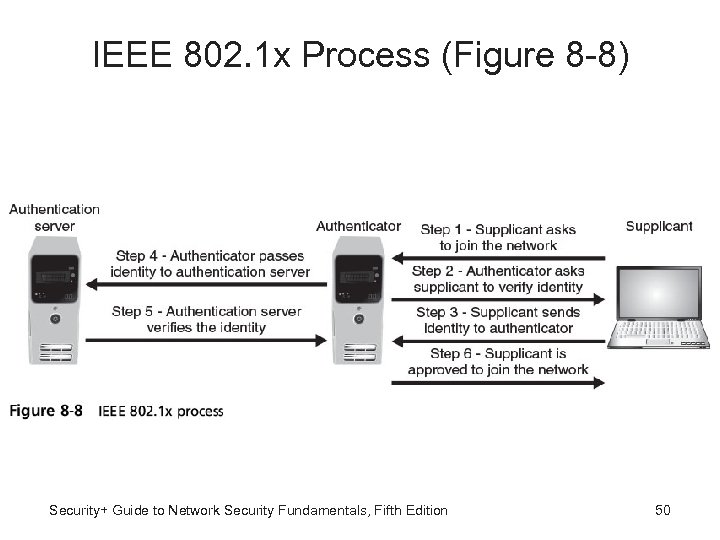 IEEE 802. 1 x Process (Figure 8 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 50
IEEE 802. 1 x Process (Figure 8 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 50
 Securing Network Applications & Platforms • Several relatively new network applications and platforms require special security considerations: – IP telephony – Virtualization – Cloud computing Security+ Guide to Network Security Fundamentals, Fifth Edition 51
Securing Network Applications & Platforms • Several relatively new network applications and platforms require special security considerations: – IP telephony – Virtualization – Cloud computing Security+ Guide to Network Security Fundamentals, Fifth Edition 51
 IP Telephony • Shift to all digital technology infrastructure is underway • Converges voice and data traffic over single IP network • IP telephony - Using data-based IP network to add digital voice clients and new voice applications onto IP network Security+ Guide to Network Security Fundamentals, Fifth Edition 52
IP Telephony • Shift to all digital technology infrastructure is underway • Converges voice and data traffic over single IP network • IP telephony - Using data-based IP network to add digital voice clients and new voice applications onto IP network Security+ Guide to Network Security Fundamentals, Fifth Edition 52
 IP Telephony Advantages • IP telephony advantages: – Cost savings – Managing single network for all applications – Applications can be developed more quickly with fewer resources – Reduced wired infrastructure requirements – Reduced regulatory requirements – Increased user productivity • Because they use IP networks, IP telephony has vulnerabilities and subject to attacks Security+ Guide to Network Security Fundamentals, Fifth Edition 53
IP Telephony Advantages • IP telephony advantages: – Cost savings – Managing single network for all applications – Applications can be developed more quickly with fewer resources – Reduced wired infrastructure requirements – Reduced regulatory requirements – Increased user productivity • Because they use IP networks, IP telephony has vulnerabilities and subject to attacks Security+ Guide to Network Security Fundamentals, Fifth Edition 53
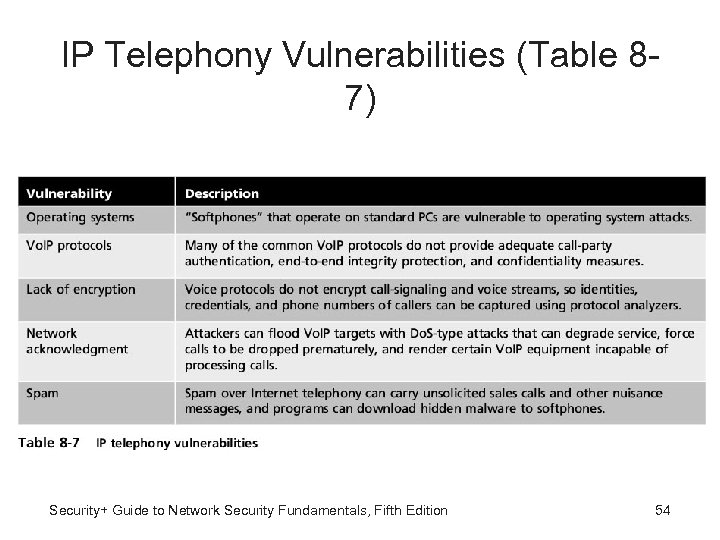 IP Telephony Vulnerabilities (Table 87) Security+ Guide to Network Security Fundamentals, Fifth Edition 54
IP Telephony Vulnerabilities (Table 87) Security+ Guide to Network Security Fundamentals, Fifth Edition 54
 Virtualization • Virtualization - Means of managing and presenting computer resources without regard to physical layout or location • Host virtualization - One type of virtualization in which entire operating system environment is simulated Security+ Guide to Network Security Fundamentals, Fifth Edition 55
Virtualization • Virtualization - Means of managing and presenting computer resources without regard to physical layout or location • Host virtualization - One type of virtualization in which entire operating system environment is simulated Security+ Guide to Network Security Fundamentals, Fifth Edition 55
 Virtualization Advantages • Virtualization advantages: – New virtual server machines can be quickly made available (host availability) – Resources like RAM or hard drive space can easily be expanded or contracted as needed (host elasticity) – Reduce costs – Providing uninterrupted server access to users Security+ Guide to Network Security Fundamentals, Fifth Edition 56
Virtualization Advantages • Virtualization advantages: – New virtual server machines can be quickly made available (host availability) – Resources like RAM or hard drive space can easily be expanded or contracted as needed (host elasticity) – Reduce costs – Providing uninterrupted server access to users Security+ Guide to Network Security Fundamentals, Fifth Edition 56
 Virtualization Security Advantages • Virtualization security advantages: – Patch compatibility - Latest patches can be downloaded and run in virtual machine to determine impact on other software – Snapshot – Image of particular state of virtual machine can be saved for later use – Security control testing - Testing existing security configuration – Sandboxing - Used test for potential malware Security+ Guide to Network Security Fundamentals, Fifth Edition 57
Virtualization Security Advantages • Virtualization security advantages: – Patch compatibility - Latest patches can be downloaded and run in virtual machine to determine impact on other software – Snapshot – Image of particular state of virtual machine can be saved for later use – Security control testing - Testing existing security configuration – Sandboxing - Used test for potential malware Security+ Guide to Network Security Fundamentals, Fifth Edition 57
 Virtualization Risks • Virtualization has several security risks: – Guest operating system that has remained dormant for a period of time may not contain the latest patches and other security updates – Not all hypervisors have the necessary security controls to keep out determined attackers – Existing security tools do not always adapt well to multiple virtual machines – Virtual machines must be protected from both outside networks and other virtual machines on the same physical computer Security+ Guide to Network Security Fundamentals, Fifth Edition 58
Virtualization Risks • Virtualization has several security risks: – Guest operating system that has remained dormant for a period of time may not contain the latest patches and other security updates – Not all hypervisors have the necessary security controls to keep out determined attackers – Existing security tools do not always adapt well to multiple virtual machines – Virtual machines must be protected from both outside networks and other virtual machines on the same physical computer Security+ Guide to Network Security Fundamentals, Fifth Edition 58
 Cloud Computing • • Cloud computing - Pay-per-use computing model Customers pay for only the resources they need May revolutionize computing Unlike hosted services, does not require long-term contracts Security+ Guide to Network Security Fundamentals, Fifth Edition 59
Cloud Computing • • Cloud computing - Pay-per-use computing model Customers pay for only the resources they need May revolutionize computing Unlike hosted services, does not require long-term contracts Security+ Guide to Network Security Fundamentals, Fifth Edition 59
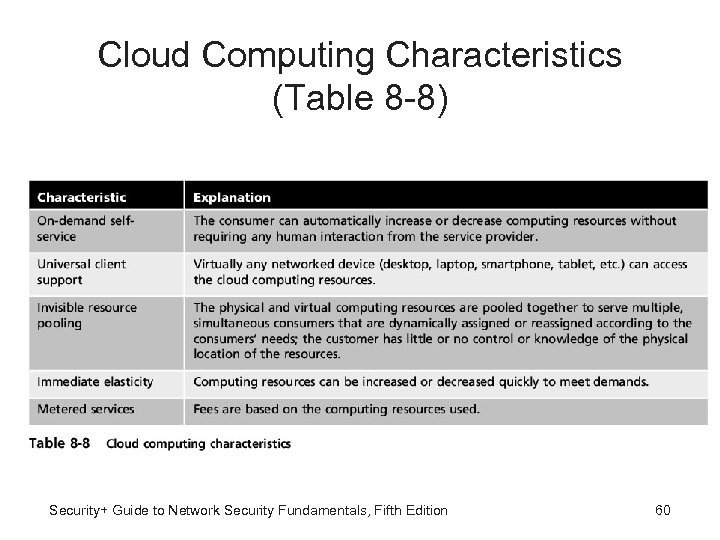 Cloud Computing Characteristics (Table 8 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 60
Cloud Computing Characteristics (Table 8 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 60
 Types of Clouds • Public cloud - Services and infrastructure offered to all users with access provided remotely through Internet • Community cloud - Open only to specific organizations that have common concerns • Private cloud - Created and maintained on private network • Hybrid cloud - Combination of public and private clouds • Cloud storage - No computational capabilities but only provides remote file storage Security+ Guide to Network Security Fundamentals, Fifth Edition 61
Types of Clouds • Public cloud - Services and infrastructure offered to all users with access provided remotely through Internet • Community cloud - Open only to specific organizations that have common concerns • Private cloud - Created and maintained on private network • Hybrid cloud - Combination of public and private clouds • Cloud storage - No computational capabilities but only provides remote file storage Security+ Guide to Network Security Fundamentals, Fifth Edition 61
 Cloud Computing Options • Software as a Service (Saa. S) - Cloud computing vendor provides access to vendor’s software applications running on cloud infrastructure • Platform as a Service (Paa. S) - Consumers can install and run their own specialized applications on cloud computing network • Infrastructure as a Service (Iaa. S) -Cloud computing vendor allows customers to deploy and run own software, including operating systems and applications Security+ Guide to Network Security Fundamentals, Fifth Edition 62
Cloud Computing Options • Software as a Service (Saa. S) - Cloud computing vendor provides access to vendor’s software applications running on cloud infrastructure • Platform as a Service (Paa. S) - Consumers can install and run their own specialized applications on cloud computing network • Infrastructure as a Service (Iaa. S) -Cloud computing vendor allows customers to deploy and run own software, including operating systems and applications Security+ Guide to Network Security Fundamentals, Fifth Edition 62
 Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 8 Administering a Secure Network
Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 8 Administering a Secure Network


