740b053aa14ca753be9f8267a5fcdae4.ppt
- Количество слайдов: 58

Security Grid Computing, B. Wilkinson, 2004 1

Secure Connections • Secure connections are needed in many computer related activities, including ebusiness and grid computing. Grid Computing, B. Wilkinson, 2004 2

Key requirements for ensuring a secure connection • Data Confidentiality - information exchange needs to protected against eavesdroppers. • Authentication - access needs to be restricted to those (humans or systems) that can provide proof of identity. • Data Integrity - need to assure that message was not modified in transit (intentionally or by accident). • Non-repudiation - guarantees that sender cannot deny that he/she sent message. Similarly receiver not deny receiving message. Grid Computing, B. Wilkinson, 2004 3
Additional Factors • Authorization - The process of deciding whether a particular identity can access a particular resource. • Access control - broader aspect of authorization and controlling specific types of access. Grid Computing, B. Wilkinson, 2004 4

Authentication Password-Based • User enters a user name and password. • User name and password sent through network to server. • Server validates name and password and responds. Grid Computing, B. Wilkinson, 2004 5

Name and Password • Consider a login prompt: login% gshrub There is no such user login% • A different login prompt behavior: login% gshrub password% ****** authentication failed login% • Second version a little more secure because it reveals less information to a potential intruder, but. . . Grid Computing, B. Wilkinson, 2004 6

Name and Password • Since name and password sent in plain text, vulnerable to interference and being stolen. • Need a system in which in one can be sure of sender. Grid Computing, B. Wilkinson, 2004 7

Two aspects: • Send information in an encrypted form. • Have a trusted third party or some sure way of proving identity. Grid Computing, B. Wilkinson, 2004 8

Cryptography • Basic idea: convert clear text (also called plain text – the original message) to ciphertext (the encrypted message) ciphertext = encrypt(plaintext) plaintext = decrypt(ciphertext) • Can either make encryption process hidden, so that an intruder cannot know it, or • Can use a known technique and use a hidden key Grid Computing, B. Wilkinson, 2004 9
Cryptography algorithms with keys • Converts data into scrambled binary patterns, using a large binary number called a key. • A key is also used to convert the scrambled patterns back to the original data. • Algorithms are well-known - it is a specific key that must be kept secure. Grid Computing, B. Wilkinson, 2004 10

Secret Key Cryptography • Sender and receiver has a same secret key in their possession. • Sender uses secret key to encrypt data. • Receiver uses same key to decrypt data. • Known as symmetric cryptography. Key is called a symmetric key. Grid Computing, B. Wilkinson, 2004 11
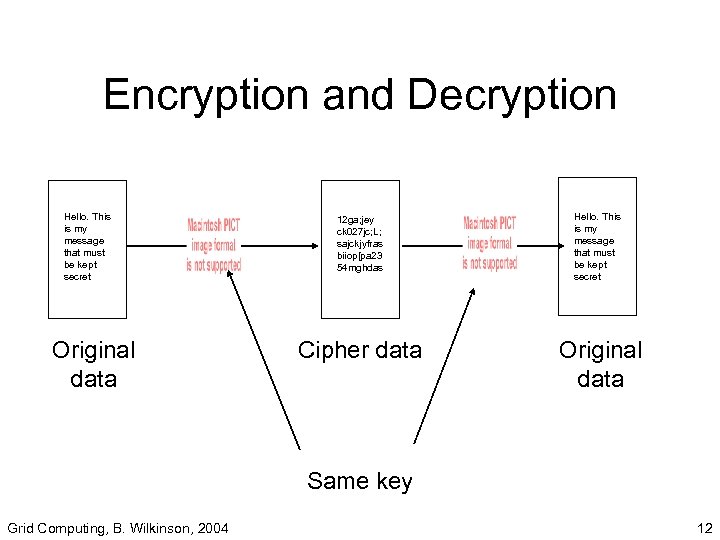
Encryption and Decryption Hello. This is my message that must be kept secret Original data 12 ga; jey ck 027 jc; L; sajckjyfras biiop[pa 23 54 mghdas Cipher data Hello. This is my message that must be kept secret Original data Same key Grid Computing, B. Wilkinson, 2004 12
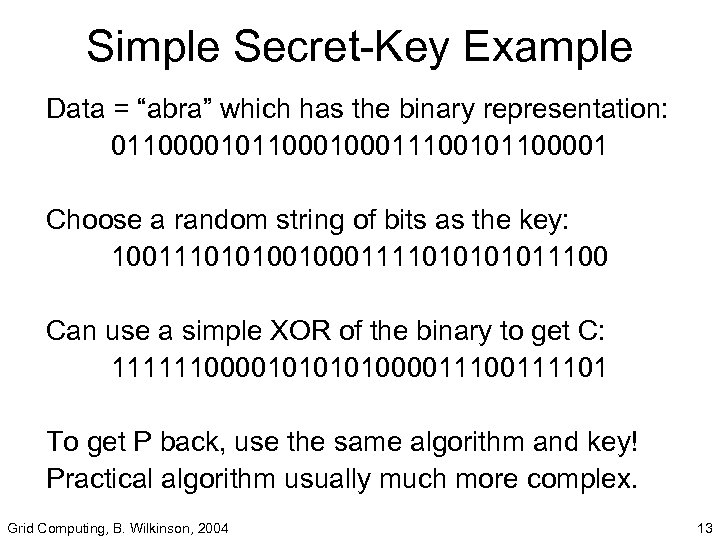
Simple Secret-Key Example Data = “abra” which has the binary representation: 0110000101100011100101100001 Choose a random string of bits as the key: 1001110101001000111101011100 Can use a simple XOR of the binary to get C: 11111100001010000111101 To get P back, use the same algorithm and key! Practical algorithm usually much more complex. Grid Computing, B. Wilkinson, 2004 13

Common Symmetric Key Cryptography Systems • Data Encryption Standard (DES) 56 -bit key plus 8 parity bits - IBM 1970’s. • Triple-DES 112 bit key plus 16 parity bits or 168 -bit plus 24 parity bits. • RC 2 and RC 4 variable sized key, often 40 to 128 bits. Grid Computing, B. Wilkinson, 2004 14

Problems with Symmetric key Cryptography • Need a way of both sender and receiver to obtain secret key without anyone else knowing the key. • Need a different key for each receiver that a sender may communicate with. Grid Computing, B. Wilkinson, 2004 15

Advantages of Symmetric Key Cryptography • Fast encryption/decryption (compared to asymmetric key cryptography (see next). Used because of speed in conjunction with asymmetric key cryptography. Grid Computing, B. Wilkinson, 2004 16

Public-Key Cryptography • Public invention due to Whitfield Diffie & Martin Hellman at Stanford Univ. in 1976 – known earlier in classified community • Probably most significant advance in the 3000 year history of cryptography • Uses clever application of number theoretic concepts of functions • Complements rather than replaces secret key cryptography Grid Computing, B. Wilkinson, 2004 17

Public Key Cryptography (Asymmetric key pair) Two keys are formed: • a public key to encrypt the transmission, and • a private key to decrypt the transmission (or vice versa). Grid Computing, B. Wilkinson, 2004 18
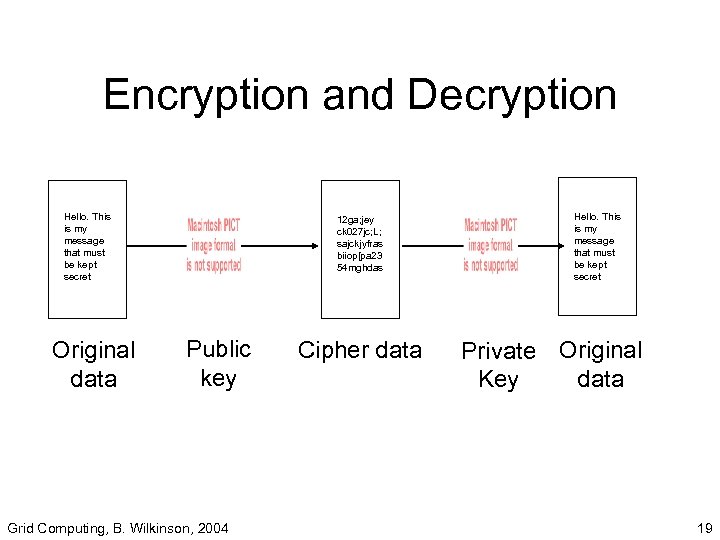
Encryption and Decryption Hello. This is my message that must be kept secret Original data 12 ga; jey ck 027 jc; L; sajckjyfras biiop[pa 23 54 mghdas Public key Grid Computing, B. Wilkinson, 2004 Cipher data Hello. This is my message that must be kept secret Private Original data Key 19

Public Key and Private Key • Public and private keys are pairs such that a message encrypted with the public key can only be decrypted with the private key (and vice versa). • Public key, as the name suggests, is available to all. • Private key is only known by it’s owner. • It is not possible to find the private key from the public key for all practical purposes. Grid Computing, B. Wilkinson, 2004 20
Public-Key Cryptography Grid Computing, B. Wilkinson, 2004 21

Non-repudiation • Public key cryptography can provide for non-repudiation - a sender cannot deny they sent out a message if encrypted with their private key. Can be read with their public key. Grid Computing, B. Wilkinson, 2004 22

How secure is public key encryption? • like private key schemes, brute force exhaustive search attack is always theoretically possible but • requires the use of very large numbers • hence is slow compared to private key schemes Grid Computing, B. Wilkinson, 2004 23

Aside • One of the assignments we have considered is breaking codes by exhausive search. Grid Computing, B. Wilkinson, 2004 24

Sequential Search This figure does come from my own book: Parallel Programming: Techniques and Application Using Networked Workstations and Parallel Computers 2 nd edition, by Barry Wilkinson and Michael Allen, Prentice Hall Inc. , 2004. Grid Computing, B. Wilkinson, 2004 25
Using Multiple Identical Grid Services Grid Computing, B. Wilkinson, 2004 26

Public Key Cryptography Example • Rivest, Shanir, and Adleman (RSA) variable sized key, usually between 512 - 2048 bits Grid Computing, B. Wilkinson, 2004 27

Problem with Public Key Cryptography • Slow • Cannot be sure that a sender is sending the message encrypted with the public key as everyone knows this key Grid Computing, B. Wilkinson, 2004 28

Digital Signatures • A way of achieving authentication and data integrity. • Uses a hash function to create a message digest, a “footprint” of the message which is encrypted with sender’s private key to create a digital signature. Grid Computing, B. Wilkinson, 2004 29

Hash Function • Applying hash function to data will create a small fixed sized block of data called in this in text a message digest • Cannot obtain original data from the digest - hence one-way. • Changes to the data will usually alter the message digest. Grid Computing, B. Wilkinson, 2004 30
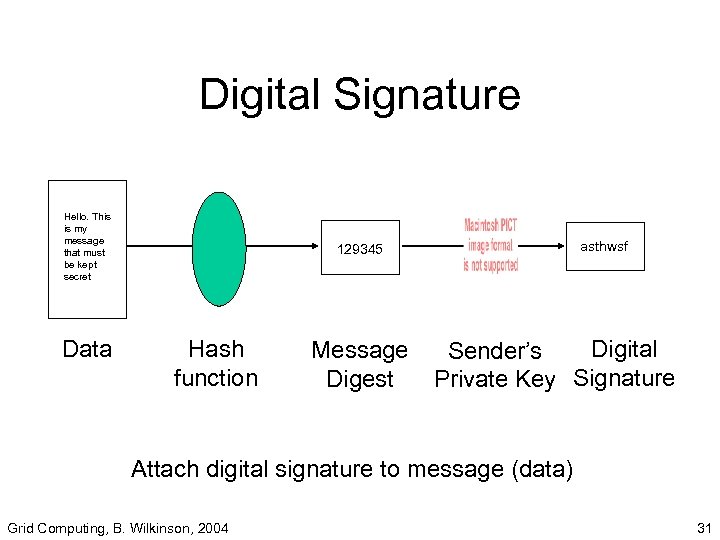
Digital Signature Hello. This is my message that must be kept secret Data asthwsf 129345 Hash function Message Digest Digital Sender’s Private Key Signature Attach digital signature to message (data) Grid Computing, B. Wilkinson, 2004 31

Checking digital signature Receiver can do the following 1. Create a message digest from message using same hash function. 2. Decrypt message digest with sender’s public key. 3. Compare two message digests - if same message should be from sender and not altered. Grid Computing, B. Wilkinson, 2004 32
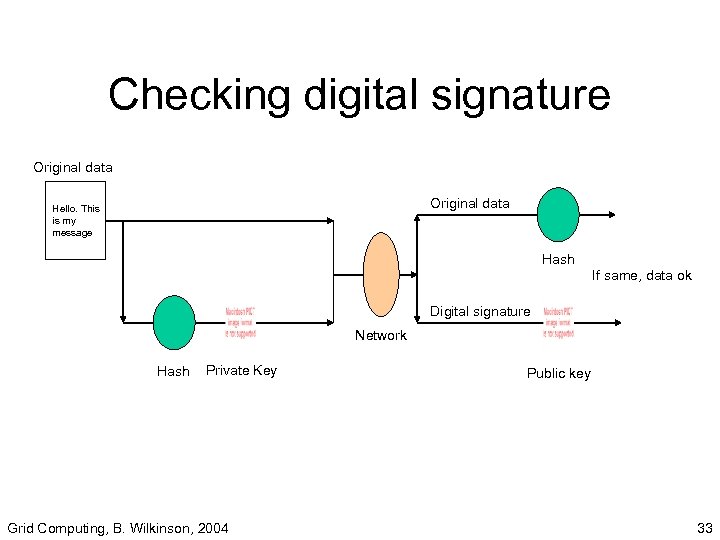
Checking digital signature Original data Hello. This is my message Hash If same, data ok Digital signature Network Hash Private Key Grid Computing, B. Wilkinson, 2004 Public key 33

• Digital signature alone not sufficient to ensure data not altered and is from the sender - possible that public key is a fake. Still could get matching digital signatures. Grid Computing, B. Wilkinson, 2004 34

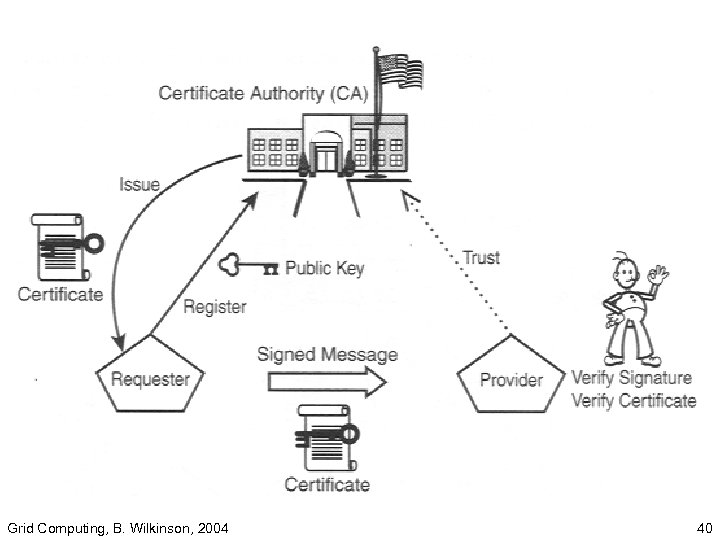
Certificates • A digital document belonging to the “End. Entity” listing its specific public key. • A trusted party (a certificate authority, CA) certifies that the public key does in fact belong to the end-entity on the certificate. • Certificate comparable to a Driver’s license or passport. Grid Computing, B. Wilkinson, 2004 35

Certificate This certificate belongs to: Barry Wilkinson Public key of certificate owner: Signature of Certificate Authority: My. CA Other information also on certificate, see later. Grid Computing, B. Wilkinson, 2004 36

Certificate Authority • Certificate Authority has to first create it’s own certificate to identify itself (keeping its private key protected). • End-Entities submit their details to CA for CA to issue a certificate back to End. Entity. Grid Computing, B. Wilkinson, 2004 37

Types of Certificates • X. 509 most widely used. • Defined by International Telecommunications Union (ITU) • Version 1 defined in 1988 • Version 2 , Version 3 (1996) adds fields, see next slide. Grid Computing, B. Wilkinson, 2004 38
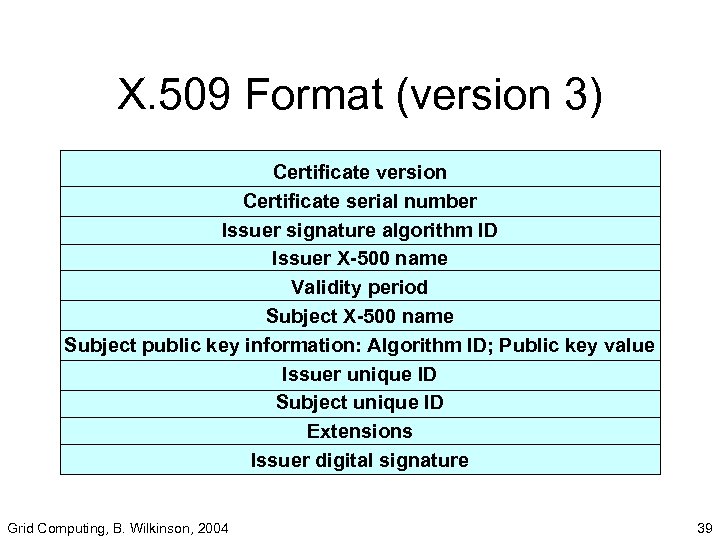
X. 509 Format (version 3) Certificate version Certificate serial number Issuer signature algorithm ID Issuer X-500 name Validity period Subject X-500 name Subject public key information: Algorithm ID; Public key value Issuer unique ID Subject unique ID Extensions Issuer digital signature Grid Computing, B. Wilkinson, 2004 39
Grid Computing, B. Wilkinson, 2004 40

Public Key Certificates • IF you trust the Certificate Authority • AND you are confident that the key that you have is really the public key of the Certificate Authority • THEN, you can decrypt the certificate with confidence to obtain the public key of the sender Read http: //docs. sun. com/source/8166154 -10/contents. htm, section starting with Certificates and Authentication Grid Computing, B. Wilkinson, 2004 41

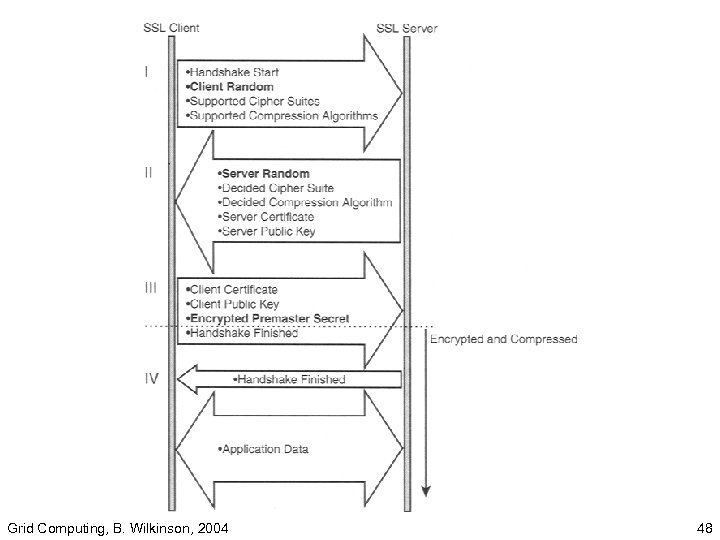
SSL (Secure Socket Layer) Protocol • Uses public/private keys. • Introduced by Netscape and widely adopted. • Supported by both Netscape and Microsoft Internet Explorer browser. • TLS (Transport Layer Security) newer but similar. Grid Computing, B. Wilkinson, 2004 42

• Requires several message to be exchanged between client and server. • Described here in four phases. Grid Computing, B. Wilkinson, 2004 43

Phase I • Client starts handshake and sends: – a random number, X. – list of supported ciphers and compression algorithms Grid Computing, B. Wilkinson, 2004 44

Phase II • Server selects cipher and compression algorithm, and notifies client. Then it sends: – another random number, Y. – a server certificate which includes public key Grid Computing, B. Wilkinson, 2004 45

Phase III • Client sends: – a “premaster” secret encrypting it with server public key – possibly a client certificate Grid Computing, B. Wilkinson, 2004 46

Phase IV • Handshake finished. Message sent to inform client. . • Server and client each generate a master secret by combining random numbers X and Y, and the premaster secret. • Several secret keys are generated from the master secret, one to encrypt the data. • Encrypted data then sent to client. Grid Computing, B. Wilkinson, 2004 47
Grid Computing, B. Wilkinson, 2004 48

SSL Ensures: • Authentication (by verifying certificates) • Confidentiality ((by encrypting data with secret key) • Integrity (by digesting data) Non-repudiation not ensured because Message Authentication Code (MAC) of transmitted data calculated with common secret key. Grid Computing, B. Wilkinson, 2004 49

Globus Grid Security Infrastructure(GSI) • Uses public key cryptography • Secure communication for authentication etc. • Task communication can be encrypted with shared key if required • Security across organizational boundaries (how? ) • Proxies provide “single sign-on” Grid Computing, B. Wilkinson, 2004 50

Certificates • Every user and service on grid identified with a certificate • X. 509 format • Certified by a Certificate Authority Globus provides one, “Simple CA”. Grid Computing, B. Wilkinson, 2004 51
Getting certificate from Simple CA Run: $GLOBUS_LOCATION/bin/grid-cert-request Certificate request stored in: $HOME/. globus/usercert_request. pem Email this request to certificate authority given in request. Grid Computing, B. Wilkinson, 2004 52

“Single sign-on” • to enable user and it’s agents to acquire additional resources without repeated authentication (passwords) • Achieved with “proxies” Grid Computing, B. Wilkinson, 2004 53

Proxy • Consists of a new certificate with new public, private keys, and owner’s identify (/CN=proxy added to name). • Certificate signed by owner (not CA) • Proxy given limited lifetimes • Proxy’s private key does not need to be kept as secure as owner’s private key setting file permissions usually sufficient Grid Computing, B. Wilkinson, 2004 54
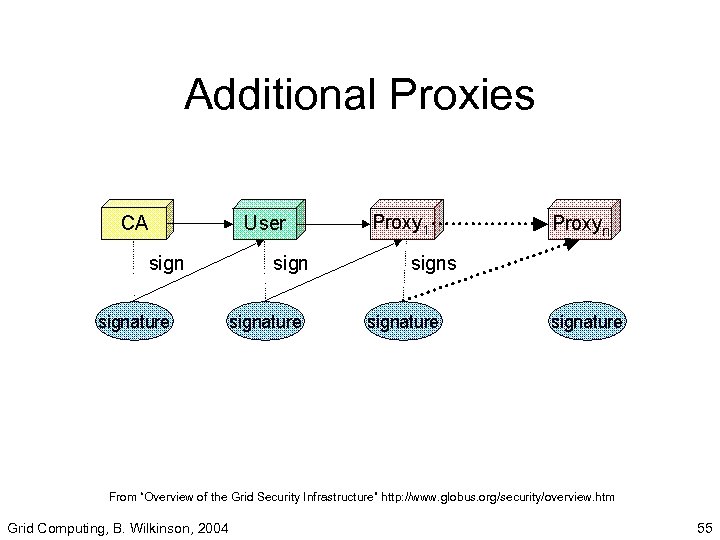
Additional Proxies From “Overview of the Grid Security Infrastructure” http: //www. globus. org/security/overview. htm Grid Computing, B. Wilkinson, 2004 55

Mutual Authentication with Proxies • Remote party receives owner’s certificate and owner’s proxy certificate. Chain of trust • Owner’s public key from owner’s certificate used to validate proxy signature on proxy certificate • Certificate authority (CA) public key used to validate owner’s signature on owner’s certificate Grid Computing, B. Wilkinson, 2004 56

More Information On-line • “Deploying a Public Key Infrastucture, ” IBM Redbooks, www. redbooks. ibm. com, 2000, SG 24 -5512 -00. • For SSL protocol: http: //developer. netscape. com/docs/manuals/secu rity/sslin/index. html • Digital signatures: http: //www. youdzone. com/signature. html Grid Computing, B. Wilkinson, 2004 57

Books • Cryptography and Network Security 3 rd edition, by William Stalling. Grid Computing, B. Wilkinson, 2004 58
740b053aa14ca753be9f8267a5fcdae4.ppt