a4f051331972470c2032c29eda342b31.ppt
- Количество слайдов: 47

Security Features and Implementations in Unix Robert Wylie, DBA, VLC Upendra Singh Rathore, DBA, VLC O/o, The Accountant General(A&E), Rajasthan, Jaipur. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Thinking About Security ¨ Security discussions often begin by considering the kinds of threats facing a system. ¨ Before we can address any security-related issue on our system, we need to be able to answer the following questions: – What are we trying to protect? – What valuable asset might be lost? Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Continued… ¨ If you can answer these questions, we go a long way toward identifying and solving potential security problems. ¨ Imagine one morning that your entire computer system had been stolen. This would upset everyone, but for many different reasons: – Loss of equipment – Loss of data or information – Loss of use Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Continued… ¨ Once you’ve identified what needs to be protected as well as the potential acts and/or events from which it needs to be protected, you’ll be in a much better position to determine what concrete steps to take to secure your system or site. ¨ The final complication is that security inevitably varies inversely with convenience: the more secure a system, the less convenient it is to use, and viceversa. (For example, isolated systems are easier to make secure than those on networks. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Continued… ¨ The key to a well-secured system is a combination of policies that: – Prevent every possible relevant threat, to the extent that they can be prevented. – Plan and prepare for what to do when the worst happens anyway. It’s helpful to imagine that even the impossible can happen. If it’s important that certain people not have access to the root account, then don’t leave root logged in on an unattended terminal, not even on the console in the locked machine room. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Policies and Plans ¨ Many sites find written security policies and plans helpful. At some sites, the computer security policy is part of a more comprehensive security policy. ¨ Security policies A good computer security policy will cover these areas: – Who is allowed to use the account – Password requirements and prohibitions – Proper and improper use of local computers and those accessed via the Internet. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Policies (Contd…) – Conditions under which the user can lose his account. – Rules about what kinds of use are allowed on which computers. – Consent to monitoring of all aspects of account activity by system administration staff. – Policies concerning how printed output is to be disposed of. Some sites will need more than one policy for different classes of users. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Plans ¨ Formulating or revising a security plan is often a good way to assess and review the general state of security on a system or network. – General computer access policies: what general classes of users are present on the system, along with the access and privileges that they are allowed. – Optional system security features that are in effect. – Preventative measures in effect. – What periodic system monitoring is performed and how it is implemented. – How often complete system security audits are performed and what items they encompass. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Plans (Contd…) – Policies and strategies for actively handling and recovering from security breaches. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

UNIX Lines of Defense ¨ Unix offers two basic ways of preventing security problems: – Passwords are designed to prevent unauthorized users from obtaining any access to the system at all. – File permissions are designed to allow to the various commands, files, programs, and system resources only to designated groups of authorized users. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Unix Lines of Defense (Contd…) ¨ In theory, passwords prevent the bad guys from getting on the system in the first place, and proper file permissions prevent normal users from doing things they aren’t supposed to, but the presence of networks, dialup lines, or nonsecure terminals and workstations complicates the picture enormously. ¨ Physical security The first line of defense is the physical access to your computer. The most security-conscious installations protect their computers by eliminating all network and dialup access and then strictly limiting who can get near them. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Unix Lines of Defense (Contd…) Although this extreme level of physical security is not needed by most sites, all administrators will face some physical security issues. Some of the most common include: – Preventing theft and vandalism, by locking the door or locking the equipment to a table or desk. – Limiting access to the console and the CPU unit to prevent someone from crashing the system and rebooting it to single-user mode. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Unix Lines of Defense (Contd…) – Controlling environmental factors, as much as is realistically possible. This concern can include considering special power systems to prevent downtime or loss of data, and fire detection and extinguishing systems to prevent equipment damage. – Restricting or monitoring access to other parts of the system, like terminals, workstations, network cables, and so on. – Limiting access to backup tapes. If the security of its data is important to your system backup tapes need to be protected from theft and damage as well as the system itself. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Unix Lines of Defense (Contd…) ¨ Passwords If someone gains access to the system, or you have voluntarily given up complete physical security, passwords form the next line of defense against unauthorized users and the risks associated with them. ¨ File permissions form the next line of defense, against both bad guys who’ve succeeded in breaking into an account and legitimate users trying to do something they’re not supposed to. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Unix Lines of Defense (Contd…) Properly set up file protection can prevent many potential problems. ¨ Encrypting data There is one exception to the complete loss of security if the root account is compromised. For some of data files, encryption can form a fourth line of defense, providing protection against root and other privileged accounts. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Unix Lines of Defense (Contd…) ¨ Backups provide the final line of defense against some kinds of security problems and system disasters. In these cases, a good backup scheme will almost always enable you to restore the system to something near its previous state. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Managing Access Control Lists (ACLs) ¨ Access Control Lists (ACLs) give you a more precise way to control access to files. The ACL contains one-line entries naming specific users and groups and what access is granted to each. ¨ ACLs are associated with each file on the Secure (sfs) and Veritas (vxfs) filesystems. ¨ A plus sign (+) appears at the end of the permission bit characters. It shows that additional access permissions, beyond those shown by the three sets of three bits, have been granted or denied through the ACL mechanism. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Managing Access(Contd…) ¨ There at least four (4) entries in an ACL and correspond to the permissions on the file. ¨ For example, if a file’s permissions were 644, the ACL entries are: ¨ user: : rwgroup: ¨ : r-¨ class: : r-¨ other: : --¨ The class entry is the maximum permission that can be granted to another group, however, it can be overridden. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Managing Access(Contd…) ¨ The root user and the owner of a file can set or unset ACLs. ¨ You can view ACLs with the getacl(1) command, enter: ¨ getacl filename Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Describing Trusted System Concepts ¨ Because no computer system is completely free from risk, systems are referred to as “trusted” rather than “secure. ” A trusted system is one that achieves a greater level of control over access to information, providing mechanisms to prevent (or at least detect) unauthorized access, along with additional means to confirm that these mechanisms are functioning properly. ¨ In addition to traditional UNIX security, passwords, and permissions, Unix. Ware 7 incorporates a trust, known as Trusted Facility Management (TFM). The TFM is a collection of software that maintains parts of the operating system related to security. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Describing Trusted (Contd…) ¨ When combined with traditional UNIX security, these features are provided: Discretionary Access Control (DAC) determines the objects a user can access, including ¨ programs, data files, and directories Identification and Authentication (I&A) offers greater control over login attempts and the entire login process Accountability traces an action to an individual user Authorizations specify user attributes required to perform a certain action Protected Subsystems offer related collections of files, devices, and commands that serve particular functions. The security features provide control of the users who maintain these functions. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Describing Trusted (Contd…) ¨ The TFM implements the security policy of the system. The security policy is a set of rules to oversee and guard interaction between “subjects” (processes running on the system) and “objects” (files and devices). ¨ Object Reuse ensures that information is cleared in RAM before reallocating the resource to another process. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations in Unix ¨ System Security – Administrators should keep in mind that a system is vulnerable when the host is placed in an easily accessible location. – Beyond physical security, there are several ways in which Unix. Ware 7 helps administrators to govern access to the systems under their control. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) Security Profiles – Unix. Ware 7 offers four predefined security profiles: - Low - Traditional - Improved - High Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) ¨ Low Security Low security is the least restrictive. It is recommended for systems that are not publicly accessible and that have a small number of cooperating users. With low security: – A maximum of 99 unsuccessful login attempts may be made before the login terminates. – There is no minimum delay between login attempts on a terminal. – Logins must be completed with in a maximum of 300 seconds. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) – Umask defaults to 022 (Read and Execute permissions for group members as well as other users) – User accounts can be deleted, and UIDs can be reused. – Passwords are not required on accounts and never expire. – The minimum password length is one. – The maximum generated password length is eight. – Remote printing is allowed. – All networking services are enable. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.
Security Implementations (Contd…) ¨ Traditional Security Traditional security is recommended for systems on which standard UNIX security is desired. With traditional security: – A maximum of 99 unsuccessful login attempts may be made before the login terminates. – There is a minimum delay of 10 seconds between login attempts on a terminal. – Logins must be completed with in a maximum of 60 seconds Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) – Umask defaults to 022 (Read and Execute permissions for group members as well as other users) – User accounts can be deleted, and UIDs can be reused. – Passwords are not required on accounts and never expire. – The minimum password length is three. – The maximum generated password length is eight. – Remote printing is allowed. – All networking services are enable Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) ¨ Improved Security Improved security is recommended for systems on which groups of users can share information. With improved security: – A maximum of five unsuccessful login attempts may be made before the login terminates. – There is a minimum delay of 20 seconds between login attempts on a terminal. – Logins must be completed with in a maximum of 60 seconds Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) – Umask defaults to 027 (Read and Execute permissions for group members and no permissions for other users) – User accounts can be deleted, and UIDs can be reused after sufficient aging. – Passwords are required on accounts and have a maximum life of 24 days. – The minimum password length is six. – The maximum generated password length is ten. – Remote printing is not allowed. – Most networking services are enable Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.
Security Implementations (Contd…) ¨ High Security High security is recommended for systems on which many users access confidential information individually. With high security: – A maximum of three unsuccessful login attempts may be made before the login terminates. – There is a minimum delay of 20 seconds between login attempts on a terminal. – Logins must be completed with in a maximum of 60 seconds Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.
Security Implementations (Contd…) – Umask defaults to 077 (no permissions for group members or other users) – User accounts can be deleted, but UIDs cannot be reused. – Passwords are required on accounts and have a maximum life of 12 days. – The minimum password length is eight. – The maximum generated password length is ten. – Remote printing is not allowed. – Networking services are limited. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) ¨ Changing Security Profiles – While you are allowed to change security profiles to one that is more restrictive than your current setting, it is not recommended. – The security profile on a system can be changed through SCOadmin, System, Security Profile Manager. – If you select a higher security profile, you are warned that security may have been compromised while at the lower settings, but are still allowed to make the change. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Security Implementations (Contd…) ¨ User Security User privileges on a system can be governed in a number of ways. – System Owner Privileges User accounts can be granted system owner privileges. The system owner can perform system administration tasks and has the following privileges: – Shut Down System – Use the Shutdown Manager to shut down the system. – Administer Printers – Use the Printer Manager to add, configure, and remove printers. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.
User Security (Contd…) – Administer File Systems – Use the Filesystem Manager to add, configure and manage filesystems. – Change System Tunables – Use the System Tuner Manager to change tunable kernel parameters. – Monitor System Resources – Use the System Monitor to view usage of system resources. – Administer Intranet – Use the Network Configuration manager to configure and manage network connections to remote systems. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

User Security (Contd…) These privileges are available to the system owner from the desktop only; this account cannot perform system administration tasks from the command line. These authorizations can be added to and removed from user accounts through SCOadmin, Account Manager. – Roles and Command Access Roles can be defined to encompass groups of permissions. You can then assign one or more roles to a user account. By using roles you can eliminate the need for any users to know the root password. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Roles and Command (Contd…) • Adding and Removing Roles – The adminrole command is used with the –n option to create a new role. • #adminrole –n wylie To list the commands associated with an existing role, use adminrole with no options followed by the name of role. To remove a role, use adminrole with –d option. • Associating Commands with a Role When a role has been created, you can define which commands are associated with it. The allprivs privilege must be given along with the desired commands to allow non-root users to execute rootonly commands. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Roles and Command (Contd…) – To add commands to a role, use the adminrole command with the –a option, followed by the command, its path, and the privilege associated with the command. For example, to add the shutdown command to the role of wylie, use #adminrole –a shutdown: /sbin/shutdown: allprivs wylie – Use the –r option to adminrole to remove commands from a role. To remove the shutdown command from the role of wylie, use #adminrole -r shutdown wylie • Assigning Roles to Users – The adminuser command assigns the defined roles to user accounts. The first time you assign a role to a user, use –n option otherwise use -o option. For example, to assign the wylie role to the user vlc, use #adminuser –n –o wylie vlc Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

– Restricting Root Logins • Root logins can be restricted to the console only. The root account will not be allowed access from any other location. To set this feature, edit the /etc/default/login file and add the following entry: CONSOLE=/dev/console – Monitoring the Use of the su Command • To enable logging of attempts to use the su command, both successful and unsuccessful, verify that the following entry exists in /etc/default/su: SULOG=/var/adm/sulog Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Monitoring the Use of the su Command (Contd…) • You can check the sulog in /var/adm to monitor su attempts. If the attempt was successful, a plus sign (+) appears after the date and time. If unsuccessful, a minus sign ( -) will be recorded. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Network Security ¨ In addition to handling security through system and user controls, you can use several tools to increase network security. Restricting FTP access, TCP wrappers, packet filtering, and proxy servers are all tools in creating a more secure network environment. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Network Security(Contd…) – ftpusers • Individual user accounts can be restricted from FTP access by entering the usernames in /etc/ftpusers, one per line. By default, root is restricted from FTP access. – TCP Wrappers • Unix. Ware 7 provides a service called TCP wrappers. This enables you to control access to a host on a persystem and per-service basis. The in. tcpd daemon handles TCP wrappers. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.
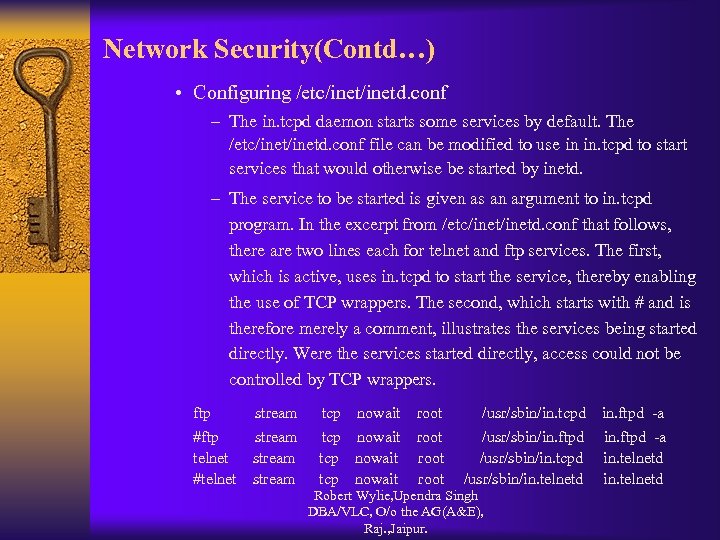
Network Security(Contd…) • Configuring /etc/inetd. conf – The in. tcpd daemon starts some services by default. The /etc/inetd. conf file can be modified to use in in. tcpd to start services that would otherwise be started by inetd. – The service to be started is given as an argument to in. tcpd program. In the excerpt from /etc/inetd. conf that follows, there are two lines each for telnet and ftp services. The first, which is active, uses in. tcpd to start the service, thereby enabling the use of TCP wrappers. The second, which starts with # and is therefore merely a comment, illustrates the services being started directly. Were the services started directly, access could not be controlled by TCP wrappers. ftp #ftp telnet #telnet stream tcp nowait root /usr/sbin/in. tcpd /usr/sbin/in. ftpd /usr/sbin/in. tcpd /usr/sbin/in. telnetd Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur. in. ftpd -a in. telnetd

Network Security(Contd…) • Configuring hosts. allow and hosts. deny – TCP wrappers control access with two files: /etc/inet/hosts. allow /etc/inet/hosts. deny – These files contain rules that in. tcpd applies to service requests to determine whether to grant access. – When a service request is received, in. tcpd first checks the hosts. allow file. If the host requesting service is allowed to use that service, either by explicit statement or by a rule containing wildcards, the service daemon is invoked immediately. Otherwise, the hosts. deny file is checked. – Although the files are named hosts. allow and hosts. deny, rules to allow or deny service can be placed in either file. The rules in the hosts. allow file will be applied before hosts. deny is read, however. Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

Network Security(Contd…) – The rules in hosts. allow and hosts. deny should be formatted as follows: daemon_list : client_list [: options] [: allow | deny] – For example, one way to configure a system in which only hosts on the 10. 1. 1 subnet can access services, and only the host 10. 1. 1. 103 is authorized for telnet, is to add the following entries to the /etc/inet/hosts. allow file: in. telnetd: ALL EXCEPT 10. 1. 1. 103: DENY ALL: 10. 1. 1. 0/255. 0 ALL: DENY Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

More Administrative Virtues ¨ Security monitoring primarily requires two of the seven administrative virtues: attention to detail and adherence to routine. They are related, of course, and mutually reinforce on another. Both also depend on that metavirtue, foresight, to keep you on the right path during those times when it seems like too much trouble. – Attention to detail: Many large security problems display only tiny symptoms, which the inattentive system administrator will miss, but you will not. – Adherence to routine: The night you decide to forego security monitoring so that some other job can run overnight has a much better than average chance of being the night the crackers find your Robert Wylie, Upendra Singh system. DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.

The End Robert Wylie, Upendra Singh DBA/VLC, O/o the AG(A&E), Raj. , Jaipur.
a4f051331972470c2032c29eda342b31.ppt