2963f66d7807d510cecf8e03d85928d4.ppt
- Количество слайдов: 46
 Security Engineering for Roles and Resources in a Distributed Environment Lt. Col. Charles E. Phillips, Jr. Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 charlesp@engr. uconn. edu Profs. Steven A. Demurjian and T. C. Ting Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 http: //www. engr. uconn. edu/~steve@engr. uconn. edu ISSEA 2002 -1
Security Engineering for Roles and Resources in a Distributed Environment Lt. Col. Charles E. Phillips, Jr. Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 charlesp@engr. uconn. edu Profs. Steven A. Demurjian and T. C. Ting Computer Science & Engineering Department 191 Auditorium Road, Box U-155 The University of Connecticut Storrs, Connecticut 06269 -3155 http: //www. engr. uconn. edu/~steve@engr. uconn. edu ISSEA 2002 -1
 Overview of Presentation m m m m Introduction Distributed Security Model Enforcement Framework Experimental Prototype Supporting Advanced Applications Conclusions Future Work ISSEA 2002 -2
Overview of Presentation m m m m Introduction Distributed Security Model Enforcement Framework Experimental Prototype Supporting Advanced Applications Conclusions Future Work ISSEA 2002 -2
 Introduction Goals of Our Research m m m Incorporation of Role-Based Security within a Distributed Resource Environment q Highly-Available Distributed Applications Constructed Using Middleware Tools q Demonstrate Use of Lookup Service to Provide Role-based Access of Clients to Resources Propose Software Architecture and Role-Based Security Model with Constraints for q Authorization of Clients Based on Role q Authentication of Clients and Resources q Enforcement and Tracking so Clients Only Use Authorized Services (of Resource) Propose a Flexible Security Solution for Clients and Services (Resources) in Dynamic Coalitions ISSEA 2002 -3
Introduction Goals of Our Research m m m Incorporation of Role-Based Security within a Distributed Resource Environment q Highly-Available Distributed Applications Constructed Using Middleware Tools q Demonstrate Use of Lookup Service to Provide Role-based Access of Clients to Resources Propose Software Architecture and Role-Based Security Model with Constraints for q Authorization of Clients Based on Role q Authentication of Clients and Resources q Enforcement and Tracking so Clients Only Use Authorized Services (of Resource) Propose a Flexible Security Solution for Clients and Services (Resources) in Dynamic Coalitions ISSEA 2002 -3
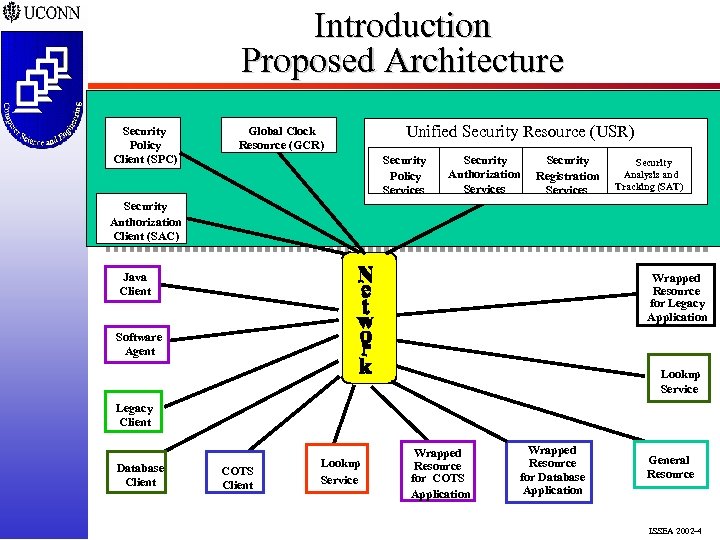 Introduction Proposed Architecture Security Policy Client (SPC) Global Clock Resource (GCR) Unified Security Resource (USR) Security Policy Services Security Authorization Services Security Registration Services Security Analysis and Tracking (SAT) Security Authorization Client (SAC) Java Client Wrapped Resource for Legacy Application Software Agent Lookup Service Legacy Client Database Client COTS Client Lookup Service Wrapped Resource for COTS Application Wrapped Resource for Database Application General Resource ISSEA 2002 -4
Introduction Proposed Architecture Security Policy Client (SPC) Global Clock Resource (GCR) Unified Security Resource (USR) Security Policy Services Security Authorization Services Security Registration Services Security Analysis and Tracking (SAT) Security Authorization Client (SAC) Java Client Wrapped Resource for Legacy Application Software Agent Lookup Service Legacy Client Database Client COTS Client Lookup Service Wrapped Resource for COTS Application Wrapped Resource for Database Application General Resource ISSEA 2002 -4
 Distributed Security Model Lookup Service Middleware m m m Construct Distributed Applications by q Federating Groups of Users q Resources Provide Services for Users A Resource Provides a Set of Services for Use by Clients (Users) and Other Resources (Services) A Service is Similar to a set of Public Methods q Exportable - Analogous to API q Any Entity Utilized by Person or Program q Samples Include: Ø Computation, Persistent Store, Printer, Sensor Ø Software Filter, Real-Time Data Source Services: Concrete Interfaces of Components Services Register with Lookup Service q m ISSEA 2002 -5
Distributed Security Model Lookup Service Middleware m m m Construct Distributed Applications by q Federating Groups of Users q Resources Provide Services for Users A Resource Provides a Set of Services for Use by Clients (Users) and Other Resources (Services) A Service is Similar to a set of Public Methods q Exportable - Analogous to API q Any Entity Utilized by Person or Program q Samples Include: Ø Computation, Persistent Store, Printer, Sensor Ø Software Filter, Real-Time Data Source Services: Concrete Interfaces of Components Services Register with Lookup Service q m ISSEA 2002 -5
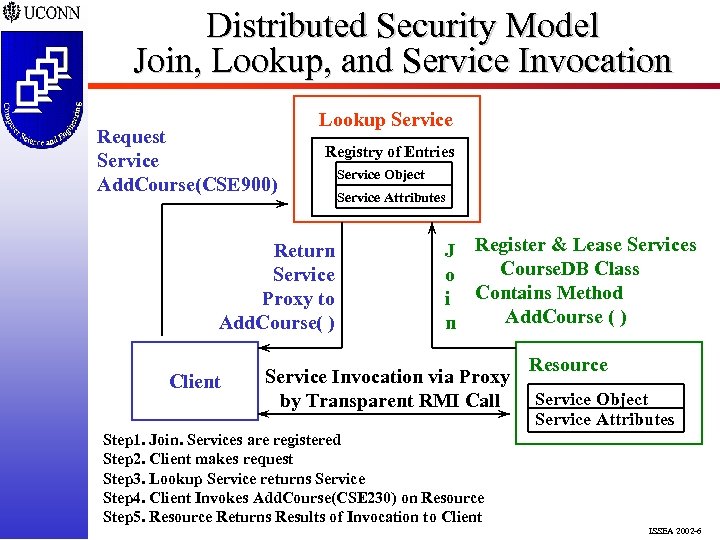 Distributed Security Model Join, Lookup, and Service Invocation Request Service Add. Course(CSE 900) Lookup Service Registry of Entries Return Service Proxy to Add. Course( ) Client Service Object Service Attributes J Register & Lease Services Course. DB Class o i Contains Method Add. Course ( ) n Service Invocation via Proxy by Transparent RMI Call Resource Service Object Service Attributes Step 1. Join. Services are registered Step 2. Client makes request Step 3. Lookup Service returns Service Step 4. Client Invokes Add. Course(CSE 230) on Resource Step 5. Resource Returns Results of Invocation to Client ISSEA 2002 -6
Distributed Security Model Join, Lookup, and Service Invocation Request Service Add. Course(CSE 900) Lookup Service Registry of Entries Return Service Proxy to Add. Course( ) Client Service Object Service Attributes J Register & Lease Services Course. DB Class o i Contains Method Add. Course ( ) n Service Invocation via Proxy by Transparent RMI Call Resource Service Object Service Attributes Step 1. Join. Services are registered Step 2. Client makes request Step 3. Lookup Service returns Service Step 4. Client Invokes Add. Course(CSE 230) on Resource Step 5. Resource Returns Results of Invocation to Client ISSEA 2002 -6
 Distributed Security Model Lookup Service Shortfalls m m m Many Current Lookup Services q Successfully Dictates Service Utilization q Requires Programmatic Solution for Security q Does Not Selectively and Dynamically Control Access Based on Client Role Security of a Distributed Resource Should Selectively and Dynamically Control Client Access to Services Based on the Role Our Approach q Define Dedicated Resources to Authorize, Authenticate, and Enforce Security by Role q Proposed Unified Security Resources (USR) Ø Policy Services, Authoriz. Services, Registration Services, & Analysis/Tracking Services ISSEA 2002 -7
Distributed Security Model Lookup Service Shortfalls m m m Many Current Lookup Services q Successfully Dictates Service Utilization q Requires Programmatic Solution for Security q Does Not Selectively and Dynamically Control Access Based on Client Role Security of a Distributed Resource Should Selectively and Dynamically Control Client Access to Services Based on the Role Our Approach q Define Dedicated Resources to Authorize, Authenticate, and Enforce Security by Role q Proposed Unified Security Resources (USR) Ø Policy Services, Authoriz. Services, Registration Services, & Analysis/Tracking Services ISSEA 2002 -7
 Distributed Security Model Resource, Service, Methods m m Definition 1: A Distributed Application Consists of M Software/system Resources (Legacy, COTS, Database, Web Server, Etc. ) Uniquely Identifiable Definition 2: Each Resource is Composed of Services That Are Uniquely Identifiable Definition 3: Each Service is Composed of a Set of Uniquely Identifiable Methods. Note That the Triple (R-id, S-id, M-id) is Unique. Definition 4: The Signature of a Method of Service of Resource is Unique, and Consists of: q Method Name q Parameter List of Names/Types q Return Type (possible Null) ISSEA 2002 -8
Distributed Security Model Resource, Service, Methods m m Definition 1: A Distributed Application Consists of M Software/system Resources (Legacy, COTS, Database, Web Server, Etc. ) Uniquely Identifiable Definition 2: Each Resource is Composed of Services That Are Uniquely Identifiable Definition 3: Each Service is Composed of a Set of Uniquely Identifiable Methods. Note That the Triple (R-id, S-id, M-id) is Unique. Definition 4: The Signature of a Method of Service of Resource is Unique, and Consists of: q Method Name q Parameter List of Names/Types q Return Type (possible Null) ISSEA 2002 -8
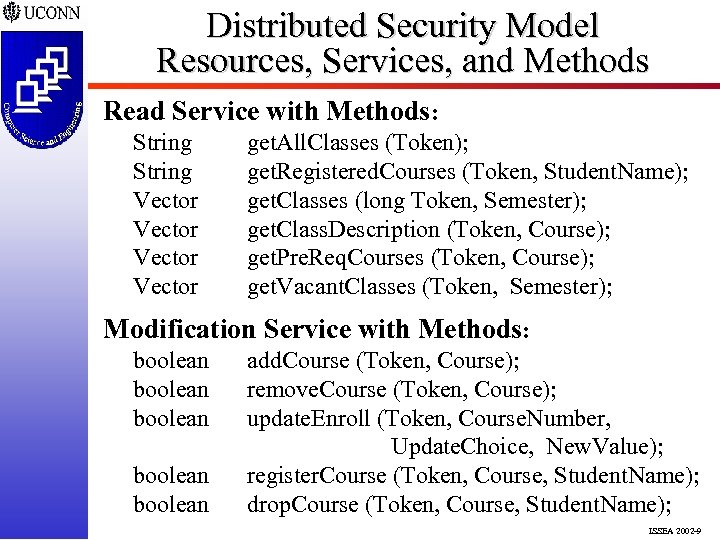 Distributed Security Model Resources, Services, and Methods Read Service with Methods: String Vector get. All. Classes (Token); get. Registered. Courses (Token, Student. Name); get. Classes (long Token, Semester); get. Class. Description (Token, Course); get. Pre. Req. Courses (Token, Course); get. Vacant. Classes (Token, Semester); Modification Service with Methods: boolean boolean add. Course (Token, Course); remove. Course (Token, Course); update. Enroll (Token, Course. Number, Update. Choice, New. Value); register. Course (Token, Course, Student. Name); drop. Course (Token, Course, Student. Name); ISSEA 2002 -9
Distributed Security Model Resources, Services, and Methods Read Service with Methods: String Vector get. All. Classes (Token); get. Registered. Courses (Token, Student. Name); get. Classes (long Token, Semester); get. Class. Description (Token, Course); get. Pre. Req. Courses (Token, Course); get. Vacant. Classes (Token, Semester); Modification Service with Methods: boolean boolean add. Course (Token, Course); remove. Course (Token, Course); update. Enroll (Token, Course. Number, Update. Choice, New. Value); register. Course (Token, Course, Student. Name); drop. Course (Token, Course, Student. Name); ISSEA 2002 -9
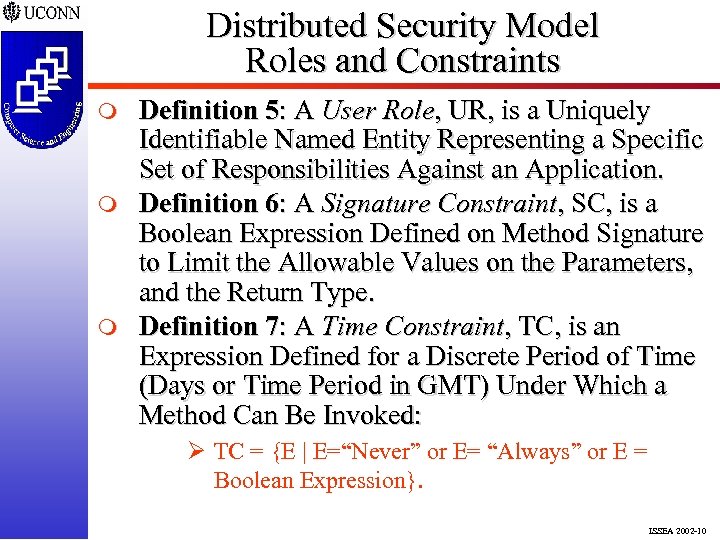 Distributed Security Model Roles and Constraints m m m Definition 5: A User Role, UR, is a Uniquely Identifiable Named Entity Representing a Specific Set of Responsibilities Against an Application. Definition 6: A Signature Constraint, SC, is a Boolean Expression Defined on Method Signature to Limit the Allowable Values on the Parameters, and the Return Type. Definition 7: A Time Constraint, TC, is an Expression Defined for a Discrete Period of Time (Days or Time Period in GMT) Under Which a Method Can Be Invoked: Ø TC = {E | E=“Never” or E= “Always” or E = Boolean Expression}. ISSEA 2002 -10
Distributed Security Model Roles and Constraints m m m Definition 5: A User Role, UR, is a Uniquely Identifiable Named Entity Representing a Specific Set of Responsibilities Against an Application. Definition 6: A Signature Constraint, SC, is a Boolean Expression Defined on Method Signature to Limit the Allowable Values on the Parameters, and the Return Type. Definition 7: A Time Constraint, TC, is an Expression Defined for a Discrete Period of Time (Days or Time Period in GMT) Under Which a Method Can Be Invoked: Ø TC = {E | E=“Never” or E= “Always” or E = Boolean Expression}. ISSEA 2002 -10
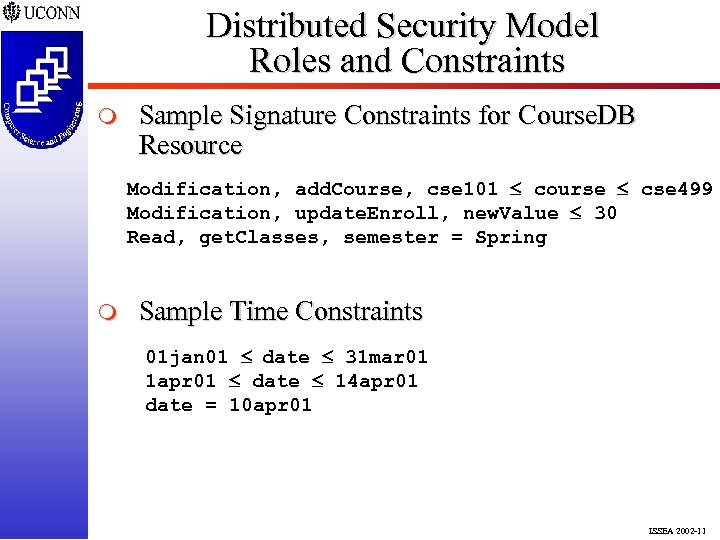 Distributed Security Model Roles and Constraints m Sample Signature Constraints for Course. DB Resource Modification, add. Course, cse 101 course cse 499 Modification, update. Enroll, new. Value 30 Read, get. Classes, semester = Spring m Sample Time Constraints 01 jan 01 date 31 mar 01 1 apr 01 date 14 apr 01 date = 10 apr 01 ISSEA 2002 -11
Distributed Security Model Roles and Constraints m Sample Signature Constraints for Course. DB Resource Modification, add. Course, cse 101 course cse 499 Modification, update. Enroll, new. Value 30 Read, get. Classes, semester = Spring m Sample Time Constraints 01 jan 01 date 31 mar 01 1 apr 01 date 14 apr 01 date = 10 apr 01 ISSEA 2002 -11
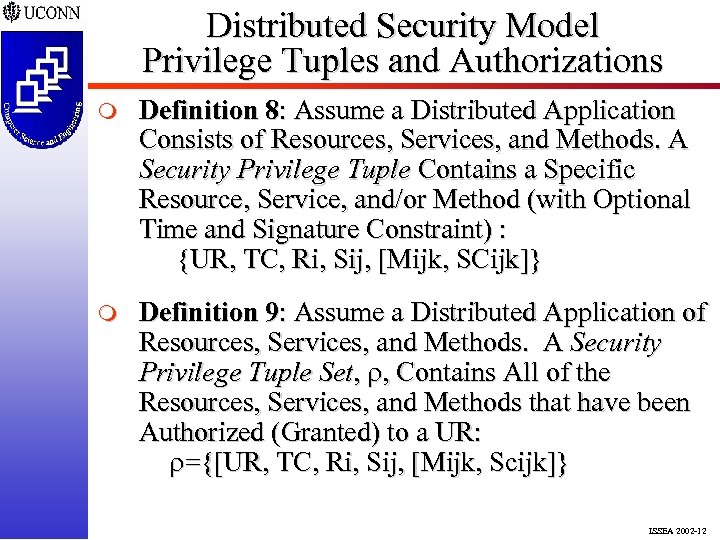 Distributed Security Model Privilege Tuples and Authorizations m Definition 8: Assume a Distributed Application Consists of Resources, Services, and Methods. A Security Privilege Tuple Contains a Specific Resource, Service, and/or Method (with Optional Time and Signature Constraint) : {UR, TC, Ri, Sij, [Mijk, SCijk]} m Definition 9: Assume a Distributed Application of Resources, Services, and Methods. A Security Privilege Tuple Set, , Contains All of the Resources, Services, and Methods that have been Authorized (Granted) to a UR: ={[UR, TC, Ri, Sij, [Mijk, Scijk]} ISSEA 2002 -12
Distributed Security Model Privilege Tuples and Authorizations m Definition 8: Assume a Distributed Application Consists of Resources, Services, and Methods. A Security Privilege Tuple Contains a Specific Resource, Service, and/or Method (with Optional Time and Signature Constraint) : {UR, TC, Ri, Sij, [Mijk, SCijk]} m Definition 9: Assume a Distributed Application of Resources, Services, and Methods. A Security Privilege Tuple Set, , Contains All of the Resources, Services, and Methods that have been Authorized (Granted) to a UR: ={[UR, TC, Ri, Sij, [Mijk, Scijk]} ISSEA 2002 -12
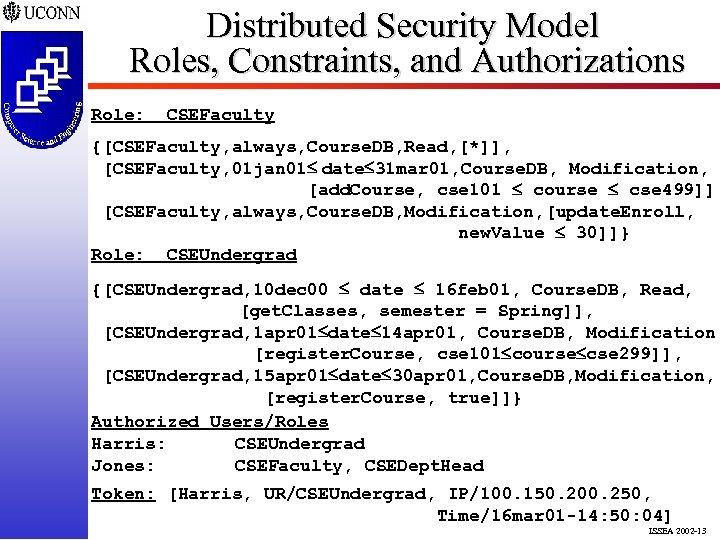 Distributed Security Model Roles, Constraints, and Authorizations Role: CSEFaculty {[CSEFaculty, always, Course. DB, Read, [*]], [CSEFaculty, 01 jan 01 date 31 mar 01, Course. DB, Modification, [add. Course, cse 101 course cse 499]], [CSEFaculty, always, Course. DB, Modification, [update. Enroll, new. Value 30]]} Role: CSEUndergrad {[CSEUndergrad, 10 dec 00 date 16 feb 01, Course. DB, Read, [get. Classes, semester = Spring]], [CSEUndergrad, 1 apr 01 date 14 apr 01, Course. DB, Modification, [register. Course, cse 101 course cse 299]], [CSEUndergrad, 15 apr 01 date 30 apr 01, Course. DB, Modification, [register. Course, true]]} Authorized Users/Roles Harris: CSEUndergrad Jones: CSEFaculty, CSEDept. Head Token: [Harris, UR/CSEUndergrad, IP/100. 150. 200. 250, Time/16 mar 01 -14: 50: 04] ISSEA 2002 -13
Distributed Security Model Roles, Constraints, and Authorizations Role: CSEFaculty {[CSEFaculty, always, Course. DB, Read, [*]], [CSEFaculty, 01 jan 01 date 31 mar 01, Course. DB, Modification, [add. Course, cse 101 course cse 499]], [CSEFaculty, always, Course. DB, Modification, [update. Enroll, new. Value 30]]} Role: CSEUndergrad {[CSEUndergrad, 10 dec 00 date 16 feb 01, Course. DB, Read, [get. Classes, semester = Spring]], [CSEUndergrad, 1 apr 01 date 14 apr 01, Course. DB, Modification, [register. Course, cse 101 course cse 299]], [CSEUndergrad, 15 apr 01 date 30 apr 01, Course. DB, Modification, [register. Course, true]]} Authorized Users/Roles Harris: CSEUndergrad Jones: CSEFaculty, CSEDept. Head Token: [Harris, UR/CSEUndergrad, IP/100. 150. 200. 250, Time/16 mar 01 -14: 50: 04] ISSEA 2002 -13
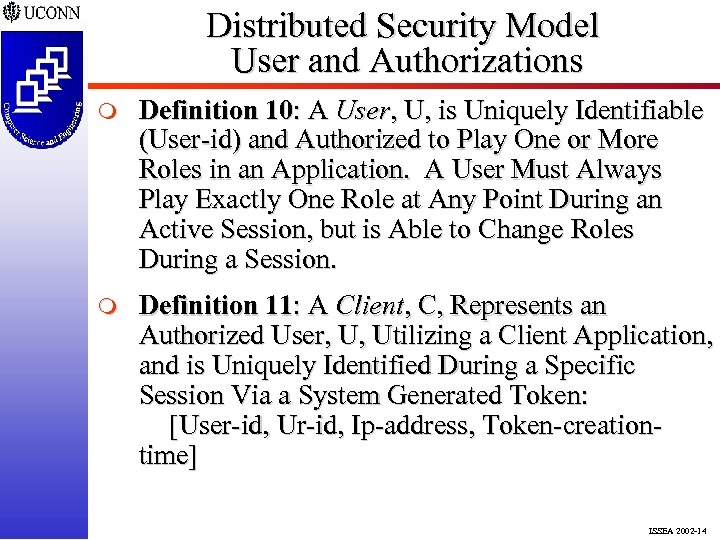 Distributed Security Model User and Authorizations m Definition 10: A User, U, is Uniquely Identifiable (User-id) and Authorized to Play One or More Roles in an Application. A User Must Always Play Exactly One Role at Any Point During an Active Session, but is Able to Change Roles During a Session. m Definition 11: A Client, C, Represents an Authorized User, U, Utilizing a Client Application, and is Uniquely Identified During a Specific Session Via a System Generated Token: [User-id, Ur-id, Ip-address, Token-creationtime] ISSEA 2002 -14
Distributed Security Model User and Authorizations m Definition 10: A User, U, is Uniquely Identifiable (User-id) and Authorized to Play One or More Roles in an Application. A User Must Always Play Exactly One Role at Any Point During an Active Session, but is Able to Change Roles During a Session. m Definition 11: A Client, C, Represents an Authorized User, U, Utilizing a Client Application, and is Uniquely Identified During a Specific Session Via a System Generated Token: [User-id, Ur-id, Ip-address, Token-creationtime] ISSEA 2002 -14
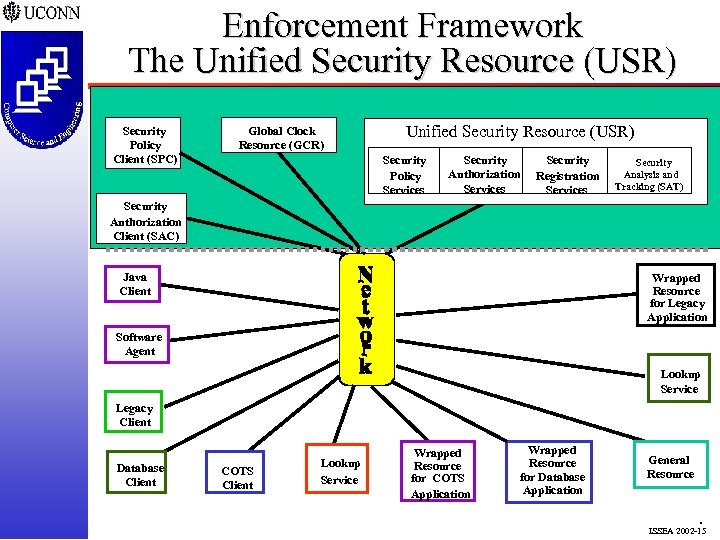 Enforcement Framework The Unified Security Resource (USR) Security Policy Client (SPC) Global Clock Resource (GCR) Unified Security Resource (USR) Security Policy Services Security Authorization Services Security Registration Services Security Analysis and Tracking (SAT) Security Authorization Client (SAC) Java Client Wrapped Resource for Legacy Application Software Agent Lookup Service Legacy Client Database Client COTS Client Lookup Service Wrapped Resource for COTS Application Wrapped Resource for Database Application General Resource . ISSEA 2002 -15
Enforcement Framework The Unified Security Resource (USR) Security Policy Client (SPC) Global Clock Resource (GCR) Unified Security Resource (USR) Security Policy Services Security Authorization Services Security Registration Services Security Analysis and Tracking (SAT) Security Authorization Client (SAC) Java Client Wrapped Resource for Legacy Application Software Agent Lookup Service Legacy Client Database Client COTS Client Lookup Service Wrapped Resource for COTS Application Wrapped Resource for Database Application General Resource . ISSEA 2002 -15
 Enforcement Framework Security Policy Services Register Service: Register_Resource(R_Id); Register_Service(R_Id, S_Id); Register_Method(R_Id, S_Id, M_Id); Register_Signature(R_Id, S_Id, M_Id, Signat); Un. Register_Resource(R_Id); Un. Register_Service(R_Id, S_Id); Un. Register_Method(R_Id, S_Id, M_Id); Unregister_Token(Token) Query Privileges Service: Query_Avail. Resource(); Query_Avail. Method(R_Id); Query_Method(Token, R_Id, S_Id, M_Id); Check_Privileges(Token, R_Id, S_Id, M_Id, Param. Value. List) User Role Service: Create_New_Role(UR_Name, UR_Disc, UR_Id); Delete_Role(UR_Id); Constraint Service: Define. TC(R_Id, S_Id, M_Id, SC); Define. SC(R_Id, S_Id, M_Id, SC); Check. TC(Token, R_Id, S_Id, M_ID); Check. SC(Token, R_Id, S_Id, M_ID, Param. Value. List); Grant-Revoke Service: Grant{Revoke}_Resource(UR_Id, R_Id); Grant{Revoke}_Service(UR_Id, S_Id); Grant{Revoke}_Method(UR_Id, S_Id, M_Id); Grant{Revoke}_SC(UR_Id, S_Id, M_Id, SC); Grant{Revoke}_TC(UR_Id, S_Id, M_Id, TC); ISSEA 2002 -16
Enforcement Framework Security Policy Services Register Service: Register_Resource(R_Id); Register_Service(R_Id, S_Id); Register_Method(R_Id, S_Id, M_Id); Register_Signature(R_Id, S_Id, M_Id, Signat); Un. Register_Resource(R_Id); Un. Register_Service(R_Id, S_Id); Un. Register_Method(R_Id, S_Id, M_Id); Unregister_Token(Token) Query Privileges Service: Query_Avail. Resource(); Query_Avail. Method(R_Id); Query_Method(Token, R_Id, S_Id, M_Id); Check_Privileges(Token, R_Id, S_Id, M_Id, Param. Value. List) User Role Service: Create_New_Role(UR_Name, UR_Disc, UR_Id); Delete_Role(UR_Id); Constraint Service: Define. TC(R_Id, S_Id, M_Id, SC); Define. SC(R_Id, S_Id, M_Id, SC); Check. TC(Token, R_Id, S_Id, M_ID); Check. SC(Token, R_Id, S_Id, M_ID, Param. Value. List); Grant-Revoke Service: Grant{Revoke}_Resource(UR_Id, R_Id); Grant{Revoke}_Service(UR_Id, S_Id); Grant{Revoke}_Method(UR_Id, S_Id, M_Id); Grant{Revoke}_SC(UR_Id, S_Id, M_Id, SC); Grant{Revoke}_TC(UR_Id, S_Id, M_Id, TC); ISSEA 2002 -16
 Enforcement Framework Other Services SECURITY AUTHORIZATION SERVICES Authorize Role Service Grant_Role(UR_Id, User_Id); Revoke_Role(UR_Id, User_Id); Client Profile Service Verify_UR(User_Id, UR_Id); Erase_Client(User_Id); Find_All_Clients(); SECURITY REGISTRATION SERVICES Register Client Service Create_Token(User_Id, UR_Id, Token); Register_Client(User_Id, IP_Addr, UR_Id); Un. Register_Client(User_Id, IP_Addr, UR_Id); Is. Client_Registered(Token); Find_Client(User_Id, IP_Addr); Security Tracking and Analysis Services Tracking Service: Logfile(Log String) Analysis Service: Analyze (Java Class File) ISSEA 2002 -17
Enforcement Framework Other Services SECURITY AUTHORIZATION SERVICES Authorize Role Service Grant_Role(UR_Id, User_Id); Revoke_Role(UR_Id, User_Id); Client Profile Service Verify_UR(User_Id, UR_Id); Erase_Client(User_Id); Find_All_Clients(); SECURITY REGISTRATION SERVICES Register Client Service Create_Token(User_Id, UR_Id, Token); Register_Client(User_Id, IP_Addr, UR_Id); Un. Register_Client(User_Id, IP_Addr, UR_Id); Is. Client_Registered(Token); Find_Client(User_Id, IP_Addr); Security Tracking and Analysis Services Tracking Service: Logfile(Log String) Analysis Service: Analyze (Java Class File) ISSEA 2002 -17
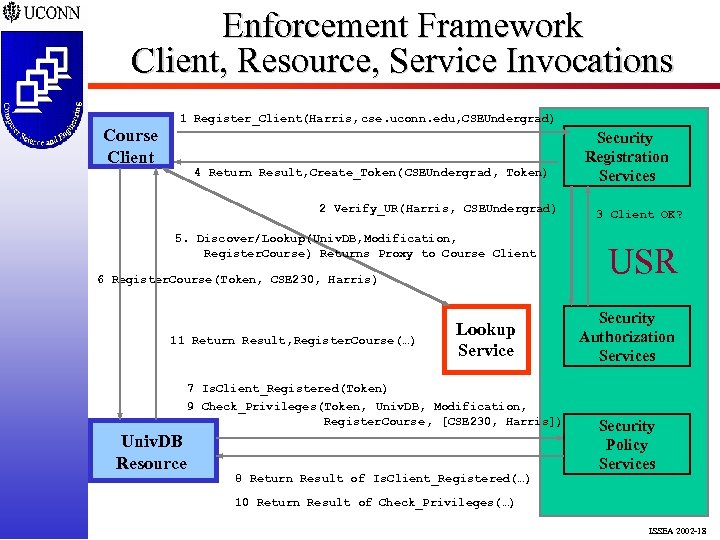 Enforcement Framework Client, Resource, Service Invocations Course Client 1 Register_Client(Harris, cse. uconn. edu, CSEUndergrad) 4 Return Result, Create_Token( CSEUndergrad, Token) 2 Verify_UR(Harris, CSEUndergrad) 5. Discover/Lookup(Univ. DB, Modification, Register. Course) Returns Proxy to Course Client 6 Register. Course(Token, CSE 230, Harris) 11 Return Result, Register. Course(…) Lookup Service 7 Is. Client_Registered(Token) 9 Check_Privileges(Token, Univ. DB, Modification, Register. Course , [CSE 230, Harris]) Univ. DB Resource 8 Return Result of Is. Client_Registered(…) Security Registration Services 3 Client OK? USR Security Authorization Services Security Policy Services 10 Return Result of Check_Privileges(…) ISSEA 2002 -18
Enforcement Framework Client, Resource, Service Invocations Course Client 1 Register_Client(Harris, cse. uconn. edu, CSEUndergrad) 4 Return Result, Create_Token( CSEUndergrad, Token) 2 Verify_UR(Harris, CSEUndergrad) 5. Discover/Lookup(Univ. DB, Modification, Register. Course) Returns Proxy to Course Client 6 Register. Course(Token, CSE 230, Harris) 11 Return Result, Register. Course(…) Lookup Service 7 Is. Client_Registered(Token) 9 Check_Privileges(Token, Univ. DB, Modification, Register. Course , [CSE 230, Harris]) Univ. DB Resource 8 Return Result of Is. Client_Registered(…) Security Registration Services 3 Client OK? USR Security Authorization Services Security Policy Services 10 Return Result of Check_Privileges(…) ISSEA 2002 -18
 Enforcement Framework Security Prototype (JINI and CORBA) m m m During the Past Two Years, Extensive Prototype has Been Developed on NT/Linux Using: q Java as Main Development Language q JINI/Corba as Middleware q Oracle/MS Access as Databases Security Management/Administration Tools q Security Policy Client q Security Authorization Client q Tracking/Analysis Client We’ll Discuss Each in Turn by Reviewing a Series of GUI Bitmaps ISSEA 2002 -19
Enforcement Framework Security Prototype (JINI and CORBA) m m m During the Past Two Years, Extensive Prototype has Been Developed on NT/Linux Using: q Java as Main Development Language q JINI/Corba as Middleware q Oracle/MS Access as Databases Security Management/Administration Tools q Security Policy Client q Security Authorization Client q Tracking/Analysis Client We’ll Discuss Each in Turn by Reviewing a Series of GUI Bitmaps ISSEA 2002 -19
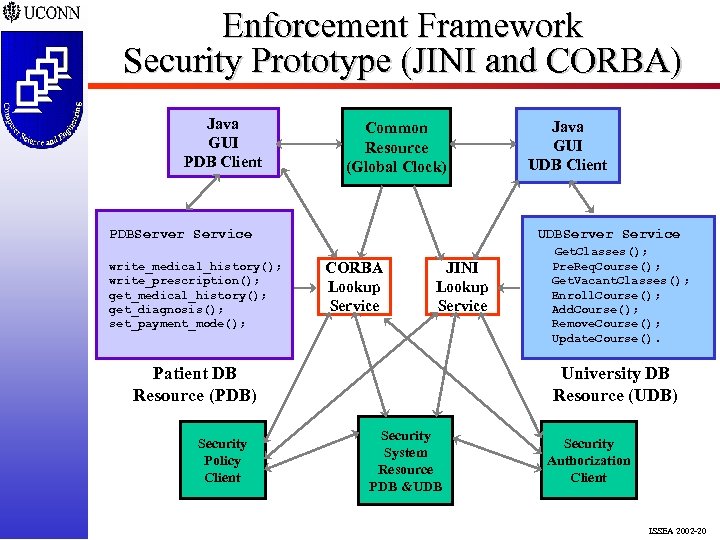 Enforcement Framework Security Prototype (JINI and CORBA) Java GUI PDB Client Common Resource (Global Clock) PDBServer Service write_medical_history(); write_prescription(); get_medical_history(); get_diagnosis(); set_payment_mode(); UDBServer Service CORBA Lookup Service JINI Lookup Service Patient DB Resource (PDB) Security Policy Client Java GUI UDB Client Get. Classes(); Pre. Req. Course(); Get. Vacant. Classes(); Enroll. Course(); Add. Course(); Remove. Course(); Update. Course(). University DB Resource (UDB) Security System Resource PDB &UDB Security Authorization Client ISSEA 2002 -20
Enforcement Framework Security Prototype (JINI and CORBA) Java GUI PDB Client Common Resource (Global Clock) PDBServer Service write_medical_history(); write_prescription(); get_medical_history(); get_diagnosis(); set_payment_mode(); UDBServer Service CORBA Lookup Service JINI Lookup Service Patient DB Resource (PDB) Security Policy Client Java GUI UDB Client Get. Classes(); Pre. Req. Course(); Get. Vacant. Classes(); Enroll. Course(); Add. Course(); Remove. Course(); Update. Course(). University DB Resource (UDB) Security System Resource PDB &UDB Security Authorization Client ISSEA 2002 -20
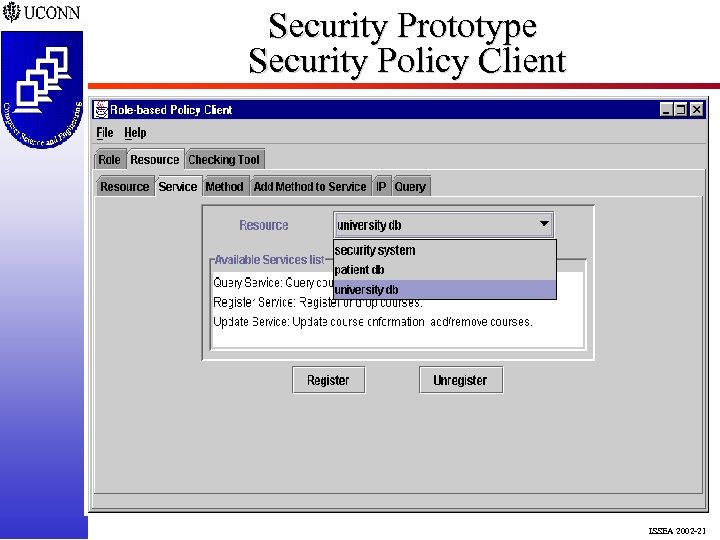 Security Prototype Security Policy Client ISSEA 2002 -21
Security Prototype Security Policy Client ISSEA 2002 -21
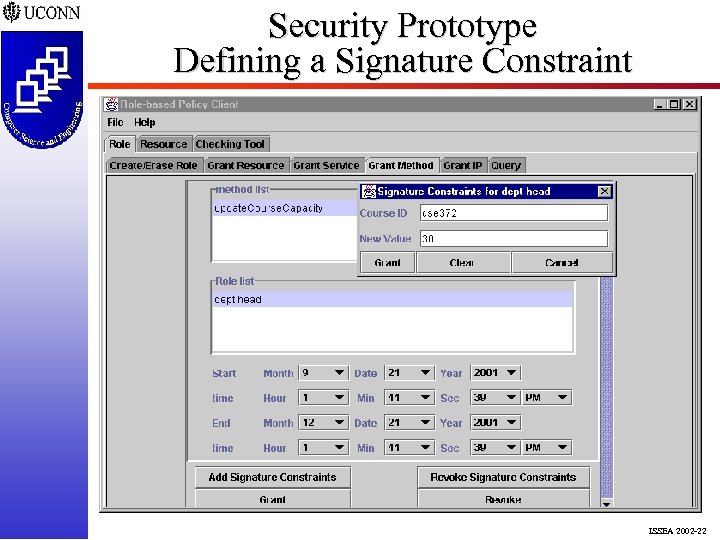 Security Prototype Defining a Signature Constraint ISSEA 2002 -22
Security Prototype Defining a Signature Constraint ISSEA 2002 -22
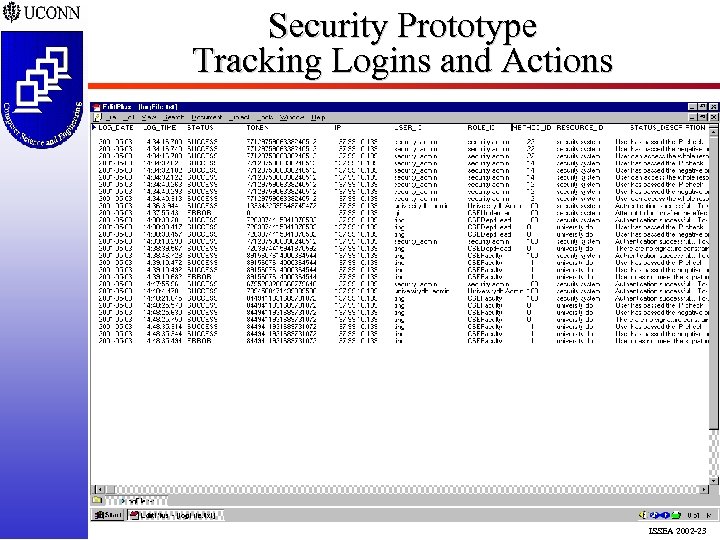 Security Prototype Tracking Logins and Actions ISSEA 2002 -23
Security Prototype Tracking Logins and Actions ISSEA 2002 -23
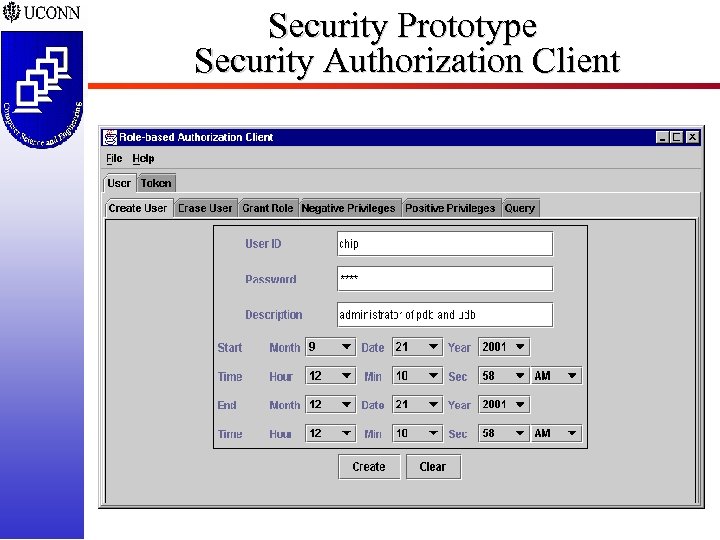 Security Prototype Security Authorization Client ISSEA 2002 -24
Security Prototype Security Authorization Client ISSEA 2002 -24
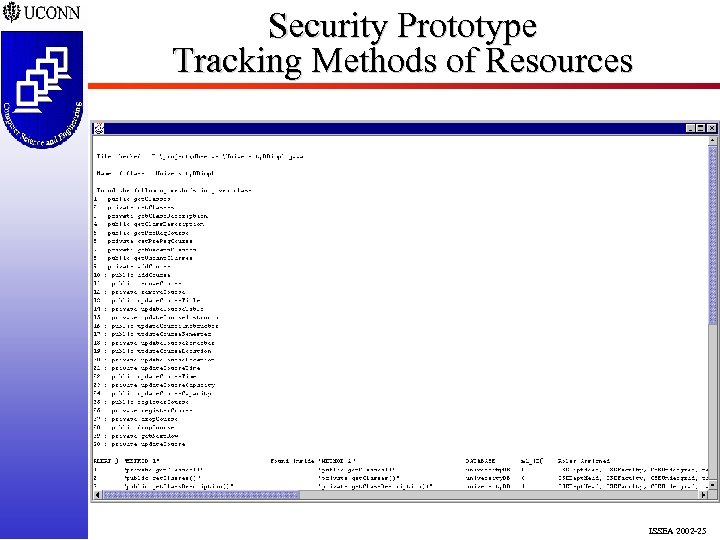 Security Prototype Tracking Methods of Resources ISSEA 2002 -25
Security Prototype Tracking Methods of Resources ISSEA 2002 -25
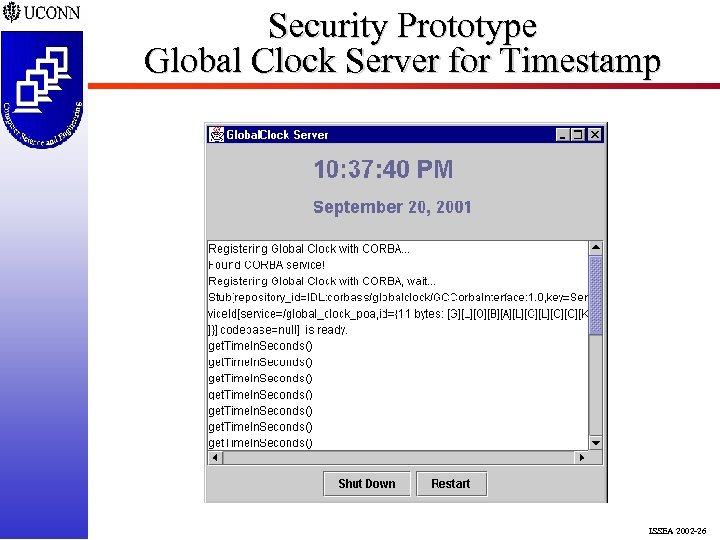 Security Prototype Global Clock Server for Timestamp ISSEA 2002 -26
Security Prototype Global Clock Server for Timestamp ISSEA 2002 -26
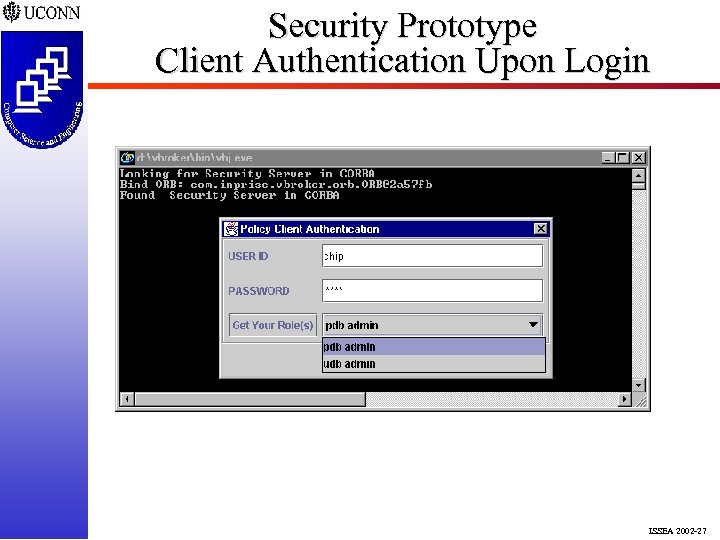 Security Prototype Client Authentication Upon Login ISSEA 2002 -27
Security Prototype Client Authentication Upon Login ISSEA 2002 -27
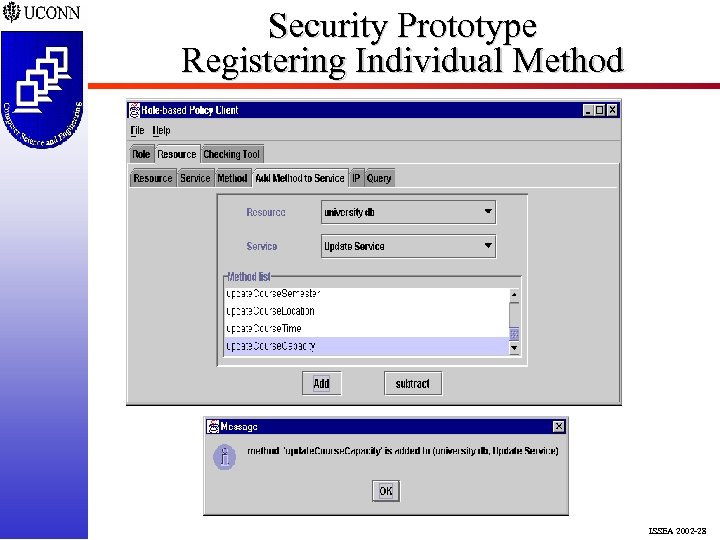 Security Prototype Registering Individual Method ISSEA 2002 -28
Security Prototype Registering Individual Method ISSEA 2002 -28
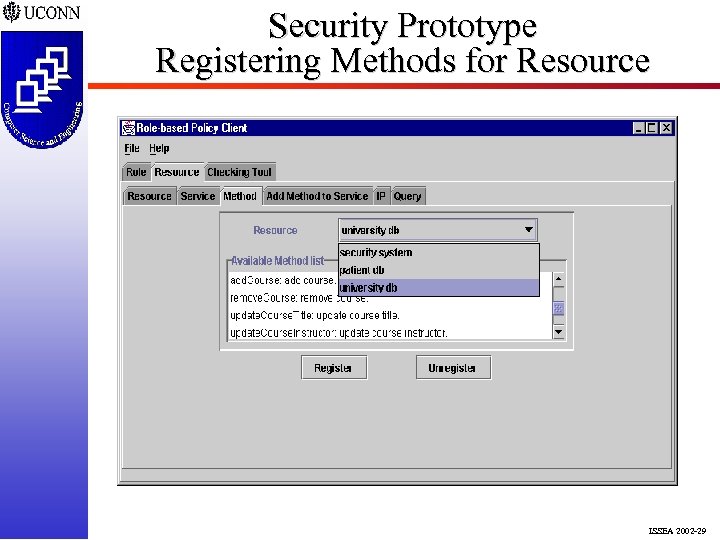 Security Prototype Registering Methods for Resource ISSEA 2002 -29
Security Prototype Registering Methods for Resource ISSEA 2002 -29
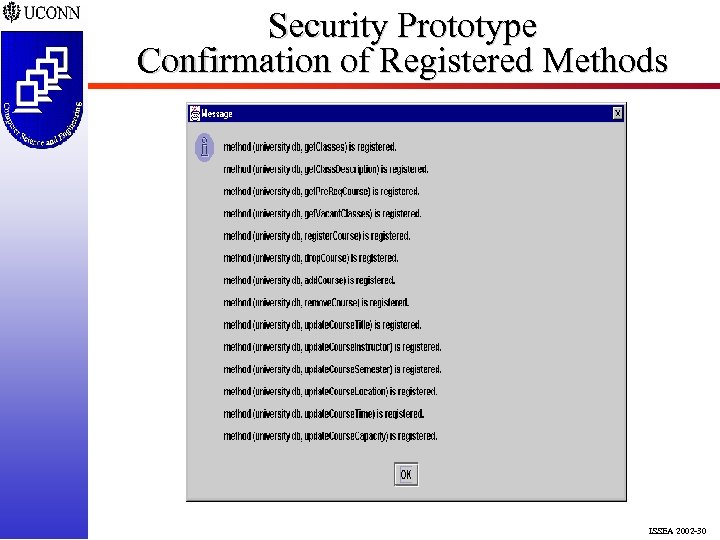 Security Prototype Confirmation of Registered Methods ISSEA 2002 -30
Security Prototype Confirmation of Registered Methods ISSEA 2002 -30
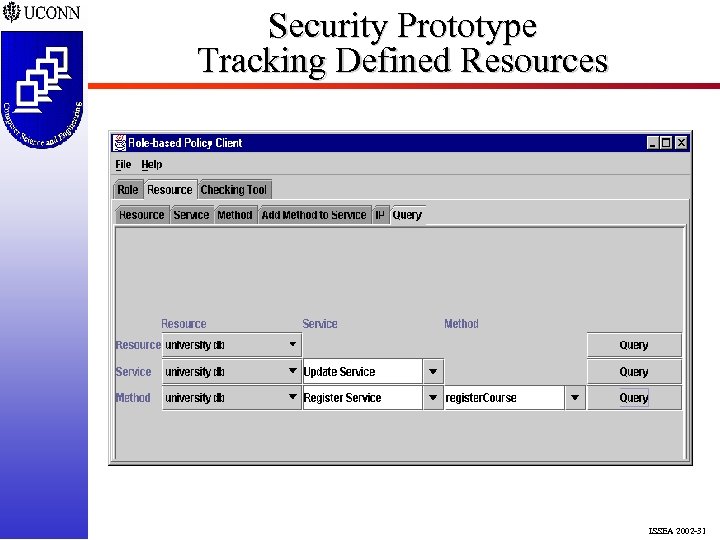 Security Prototype Tracking Defined Resources ISSEA 2002 -31
Security Prototype Tracking Defined Resources ISSEA 2002 -31
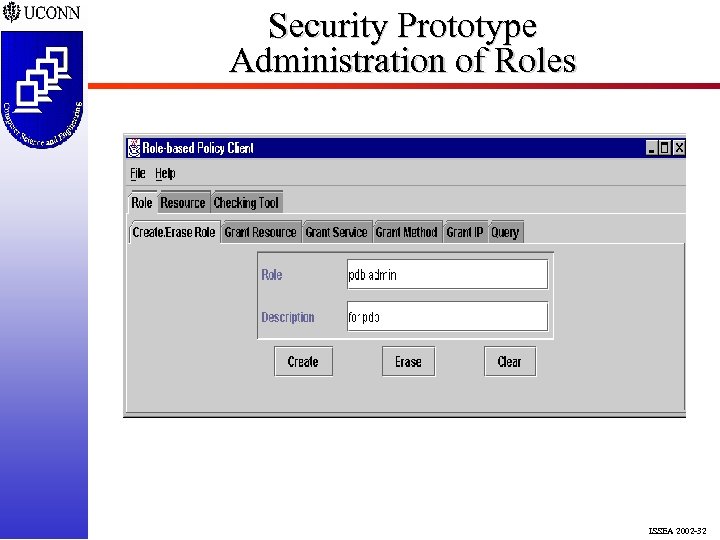 Security Prototype Administration of Roles ISSEA 2002 -32
Security Prototype Administration of Roles ISSEA 2002 -32
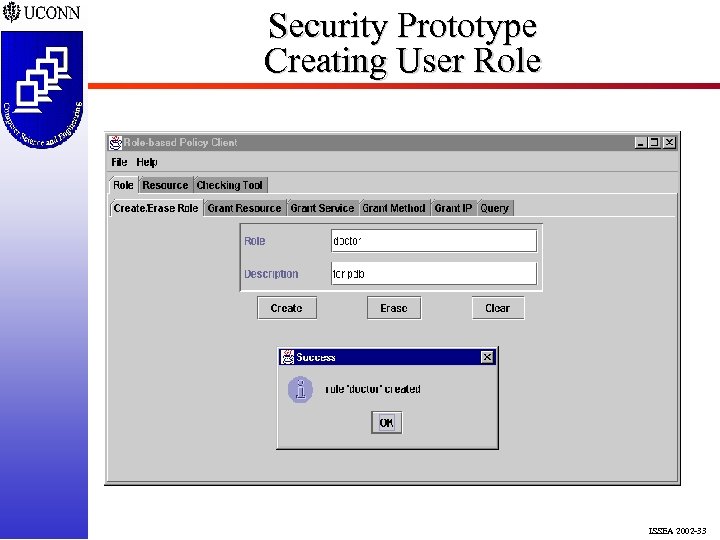 Security Prototype Creating User Role ISSEA 2002 -33
Security Prototype Creating User Role ISSEA 2002 -33
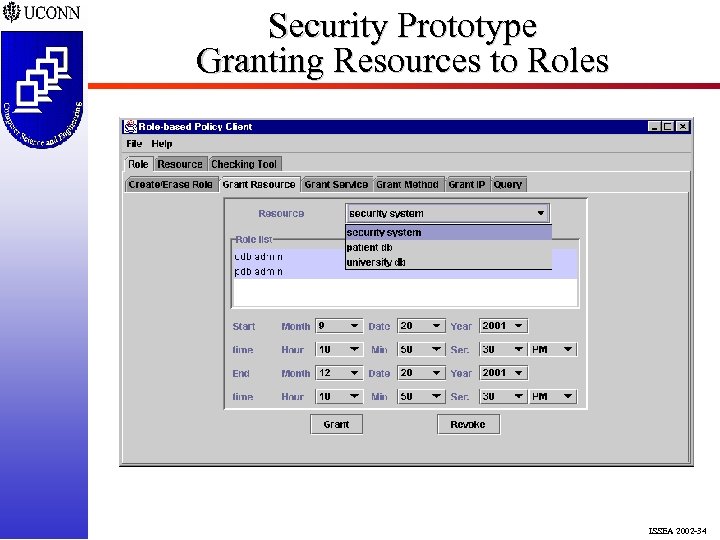 Security Prototype Granting Resources to Roles ISSEA 2002 -34
Security Prototype Granting Resources to Roles ISSEA 2002 -34
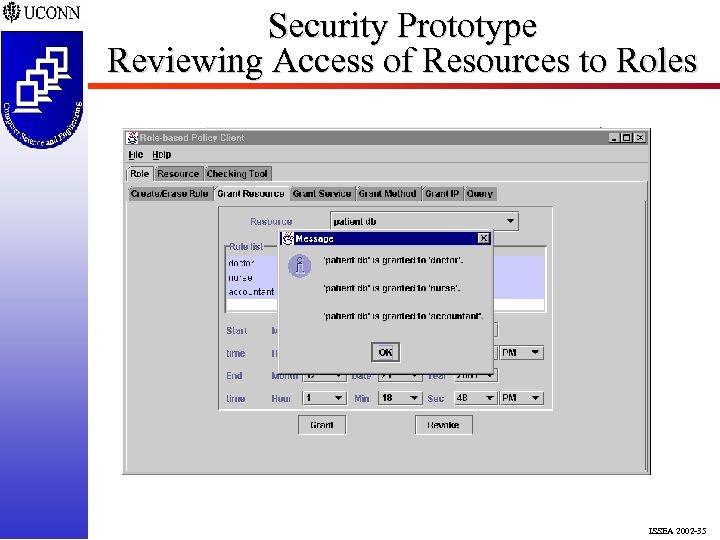 Security Prototype Reviewing Access of Resources to Roles ISSEA 2002 -35
Security Prototype Reviewing Access of Resources to Roles ISSEA 2002 -35
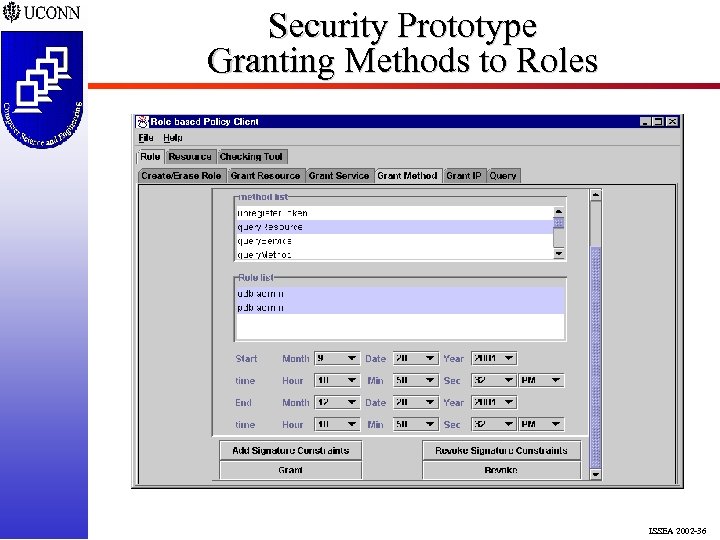 Security Prototype Granting Methods to Roles ISSEA 2002 -36
Security Prototype Granting Methods to Roles ISSEA 2002 -36
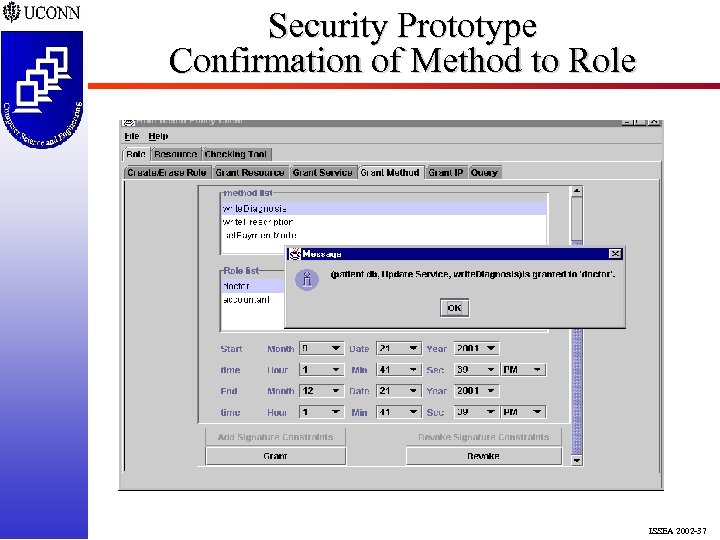 Security Prototype Confirmation of Method to Role ISSEA 2002 -37
Security Prototype Confirmation of Method to Role ISSEA 2002 -37
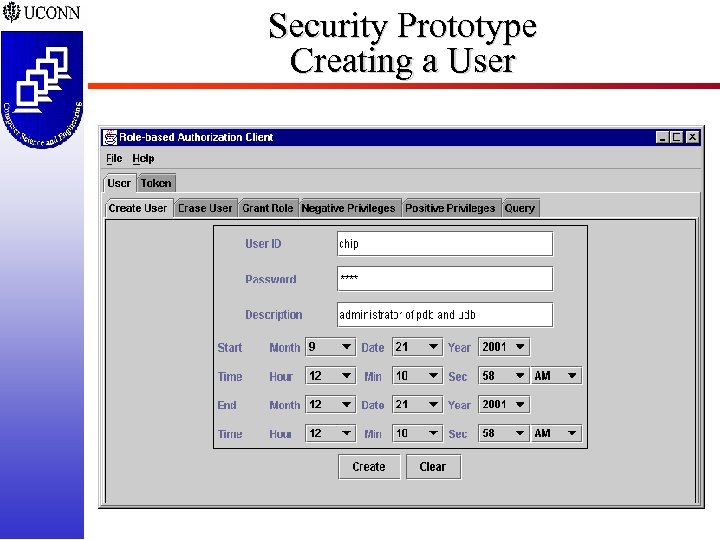 Security Prototype Creating a User ISSEA 2002 -38
Security Prototype Creating a User ISSEA 2002 -38
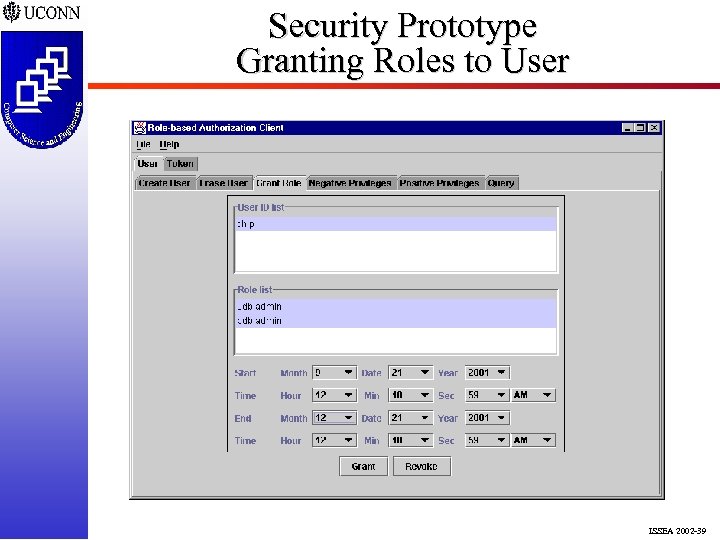 Security Prototype Granting Roles to User ISSEA 2002 -39
Security Prototype Granting Roles to User ISSEA 2002 -39
 Supporting Advanced Applications Dynamic Coalition Problem m m A Crisis is Any Situation Requiring National or International Attention as Determined by the President of the United States or UN A Coalition is an Alliance of Organizations: Military, Civilian, International or any Combination A Dynamic Coalition is Formed in a Crisis and Changes as Crisis Develops, with the Key Concern Being the Most Effective way to Solve the Crisis Dynamic Coalition Problem (DCP) is the Inherent Security, Resource, and/or Information Sharing Risks that Occur as a Result of the Coalition Being Formed Quickly ISSEA 2002 -40
Supporting Advanced Applications Dynamic Coalition Problem m m A Crisis is Any Situation Requiring National or International Attention as Determined by the President of the United States or UN A Coalition is an Alliance of Organizations: Military, Civilian, International or any Combination A Dynamic Coalition is Formed in a Crisis and Changes as Crisis Develops, with the Key Concern Being the Most Effective way to Solve the Crisis Dynamic Coalition Problem (DCP) is the Inherent Security, Resource, and/or Information Sharing Risks that Occur as a Result of the Coalition Being Formed Quickly ISSEA 2002 -40
 Supporting Advanced Applications Global Command And Control System m GCCS is Used to Manage Activities in a Joint and Combined Environment q Joint Refers to More than One Branch Army, Navy, Air Force, Marines, or Coast Guard and Combined Means More Than One Country GCCS Provides a Local Commander With Operational Awareness in Near Real-time Through an Integrated Set of Resources and Services GCCS Provides Information-Processing Support to Planning, Mobility, Sustainment, and Messaging by Bringing Together 20 Separate Automated Systems With Several Additions Planned ISSEA 2002 -41
Supporting Advanced Applications Global Command And Control System m GCCS is Used to Manage Activities in a Joint and Combined Environment q Joint Refers to More than One Branch Army, Navy, Air Force, Marines, or Coast Guard and Combined Means More Than One Country GCCS Provides a Local Commander With Operational Awareness in Near Real-time Through an Integrated Set of Resources and Services GCCS Provides Information-Processing Support to Planning, Mobility, Sustainment, and Messaging by Bringing Together 20 Separate Automated Systems With Several Additions Planned ISSEA 2002 -41
 Supporting Advanced Applications GCCS Shortfalls m m m Does Not Consider Multiple Roles for Users Does Not Place Time Limitations on Users Does Not Use Any Resource Constraints Is Not a Multi-level Secure System Is a U. S. Only System ISSEA 2002 -42
Supporting Advanced Applications GCCS Shortfalls m m m Does Not Consider Multiple Roles for Users Does Not Place Time Limitations on Users Does Not Use Any Resource Constraints Is Not a Multi-level Secure System Is a U. S. Only System ISSEA 2002 -42
 Supporting Advanced Applications DCP Objectives m m m m Federate Users Quickly and Dynamically Bring Together Resources Without Modification Dynamically Realize and Manage Simultaneous Crises Identify Users by their Roles to Finely Tune Access Authorize, Authenticate, and Enforce a Scalable Security Policy That is Flexible in Response to Collation Needs Security Solution that is Portable, Extensible, and Redundant for Survivability Management, and Introspection Capabilities to Track and Monitor System Behavior ISSEA 2002 -43
Supporting Advanced Applications DCP Objectives m m m m Federate Users Quickly and Dynamically Bring Together Resources Without Modification Dynamically Realize and Manage Simultaneous Crises Identify Users by their Roles to Finely Tune Access Authorize, Authenticate, and Enforce a Scalable Security Policy That is Flexible in Response to Collation Needs Security Solution that is Portable, Extensible, and Redundant for Survivability Management, and Introspection Capabilities to Track and Monitor System Behavior ISSEA 2002 -43
 Concluding Remarks m m For a Distributed Resource Environment q Proposed & Explained a Constraint-Based Approach to Role Security q Authorize, Authenticate, and Enforce Presented an Software Architecture Containing q Constraint-Based Security Model for Role Security in a Distributed Resource Environment q An Enforcement Framework for Security with Registration, Authorization, and Policy Services ISSEA 2002 -44
Concluding Remarks m m For a Distributed Resource Environment q Proposed & Explained a Constraint-Based Approach to Role Security q Authorize, Authenticate, and Enforce Presented an Software Architecture Containing q Constraint-Based Security Model for Role Security in a Distributed Resource Environment q An Enforcement Framework for Security with Registration, Authorization, and Policy Services ISSEA 2002 -44
 Concluding Remarks m m Developed Prototype System q JINI and CORBA-Based Prototype for Role. Based Security Model that Allows Role Access q System is Flexible, Scalable and Redundant q System Uses Constraints to Realize Policy Presented Real-World Issues q Defined the Dynamic Coalition Problem q Discussed the Global Command Control System and Its Shortcomings q Offered a Set of Objectives for Realization of Distributed Security in a Dynamic Setting ISSEA 2002 -45
Concluding Remarks m m Developed Prototype System q JINI and CORBA-Based Prototype for Role. Based Security Model that Allows Role Access q System is Flexible, Scalable and Redundant q System Uses Constraints to Realize Policy Presented Real-World Issues q Defined the Dynamic Coalition Problem q Discussed the Global Command Control System and Its Shortcomings q Offered a Set of Objectives for Realization of Distributed Security in a Dynamic Setting ISSEA 2002 -45
 Ongoing and Future Work m m Integrating Mandatory Access Controls q Currently Integrated into Security Prototype q Model Extended to Include Classifications Role Deconfliction and Mutual Exclusion q Preliminary Model Being Designed q Prototyping Planned in Near Future User Constraints q Extend to Include User Constraints q Prototyping Underway User Role Delegation Authority q Preliminary Model Designed q Prototyping Underway ISSEA 2002 -46
Ongoing and Future Work m m Integrating Mandatory Access Controls q Currently Integrated into Security Prototype q Model Extended to Include Classifications Role Deconfliction and Mutual Exclusion q Preliminary Model Being Designed q Prototyping Planned in Near Future User Constraints q Extend to Include User Constraints q Prototyping Underway User Role Delegation Authority q Preliminary Model Designed q Prototyping Underway ISSEA 2002 -46


