 Security Contents
Security Contents
 Security requirements
Security requirements
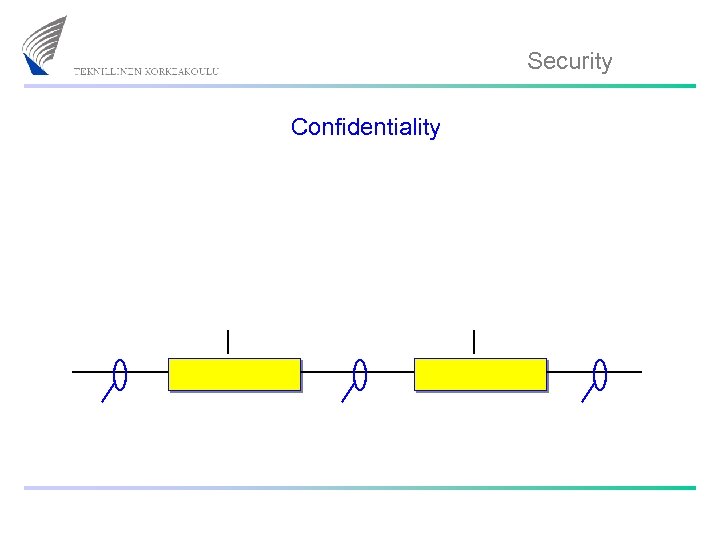 Security Confidentiality
Security Confidentiality
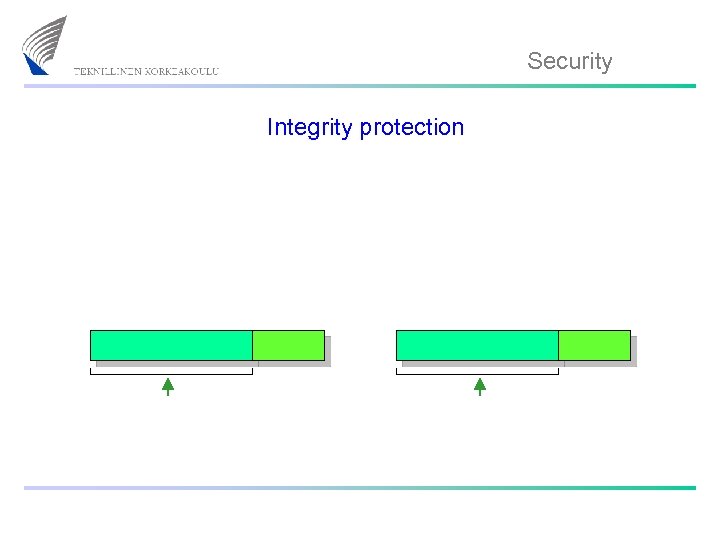 Security Integrity protection
Security Integrity protection
 Security Authentication
Security Authentication
 Security Public key cryptography
Security Public key cryptography
 Security Diffie-Hellman vs. RSA
Security Diffie-Hellman vs. RSA
 Security Symmetric keys vs. private/public keys
Security Symmetric keys vs. private/public keys
 Security Key agreement scheme
Security Key agreement scheme
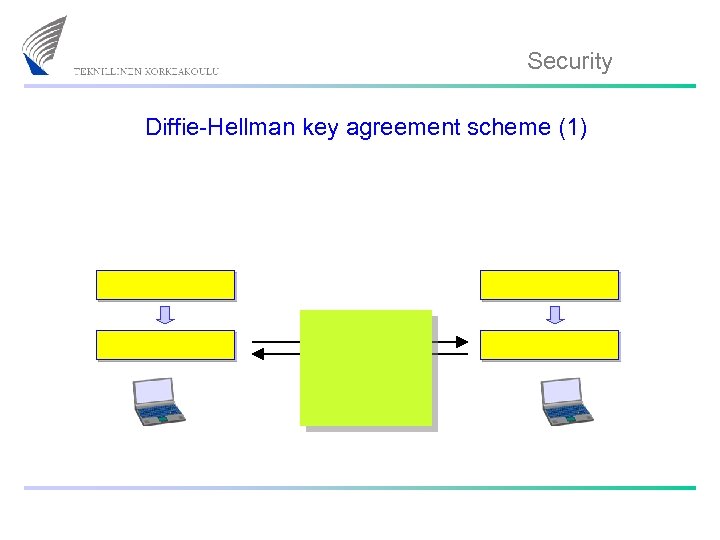 Security Diffie-Hellman key agreement scheme (1)
Security Diffie-Hellman key agreement scheme (1)
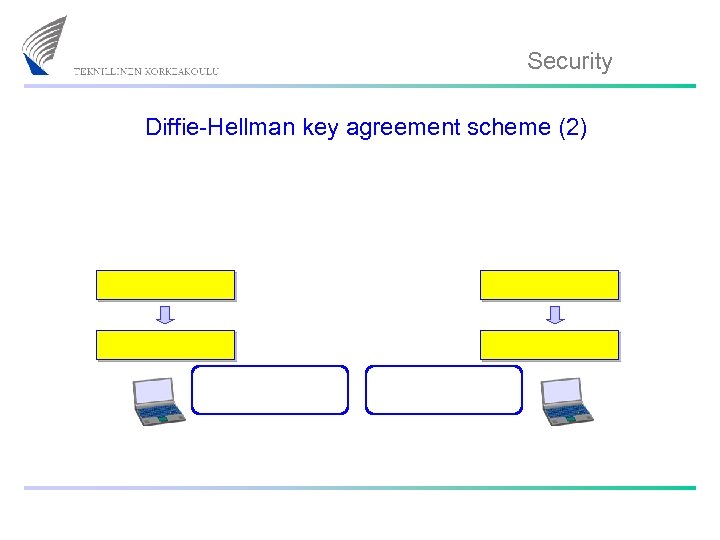 Security Diffie-Hellman key agreement scheme (2)
Security Diffie-Hellman key agreement scheme (2)
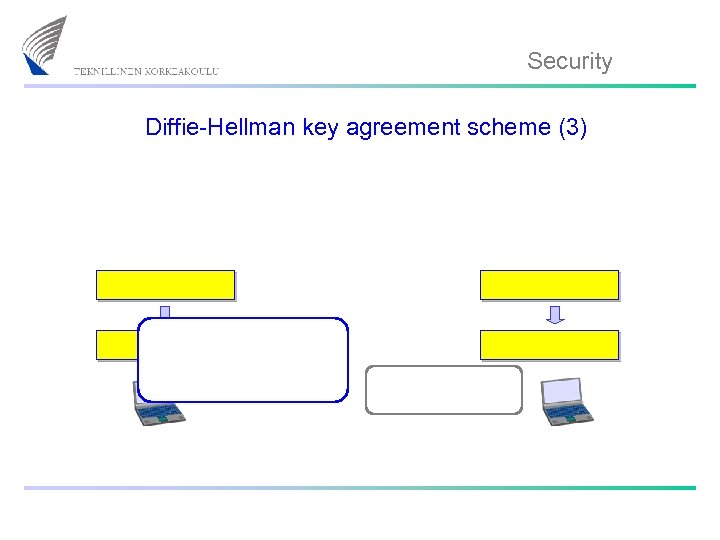 Security Diffie-Hellman key agreement scheme (3)
Security Diffie-Hellman key agreement scheme (3)
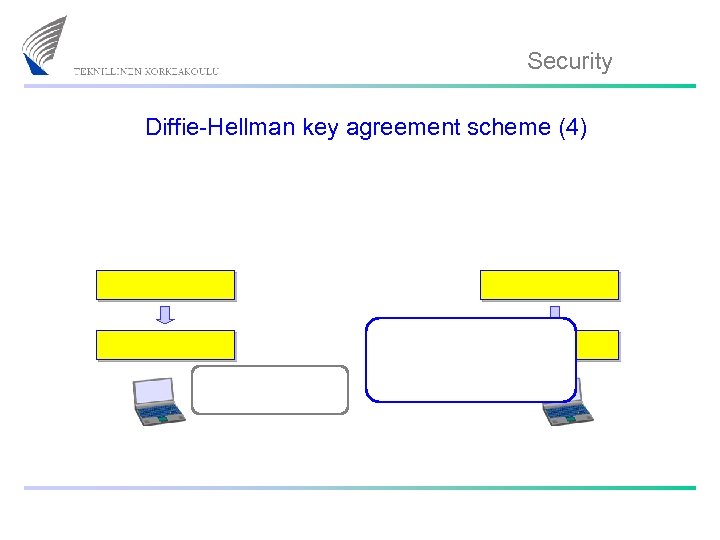 Security Diffie-Hellman key agreement scheme (4)
Security Diffie-Hellman key agreement scheme (4)
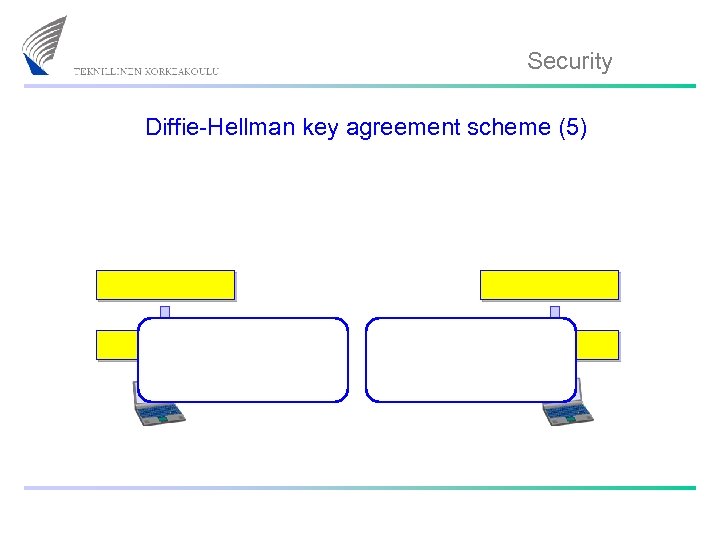 Security Diffie-Hellman key agreement scheme (5)
Security Diffie-Hellman key agreement scheme (5)
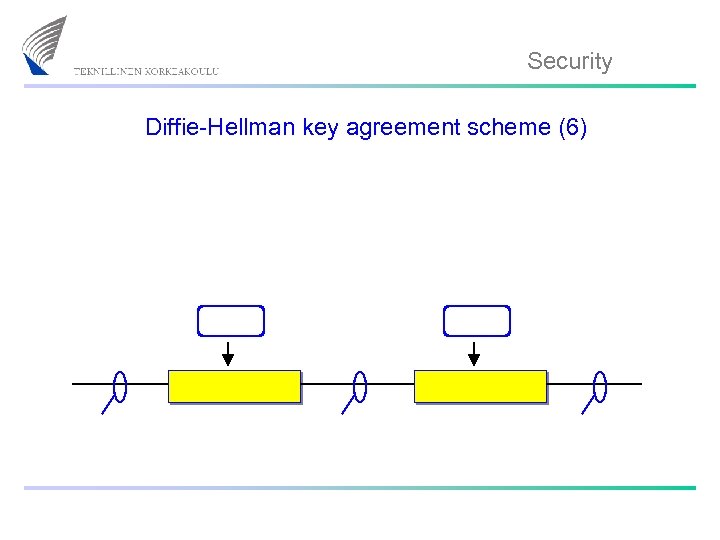 Security Diffie-Hellman key agreement scheme (6)
Security Diffie-Hellman key agreement scheme (6)
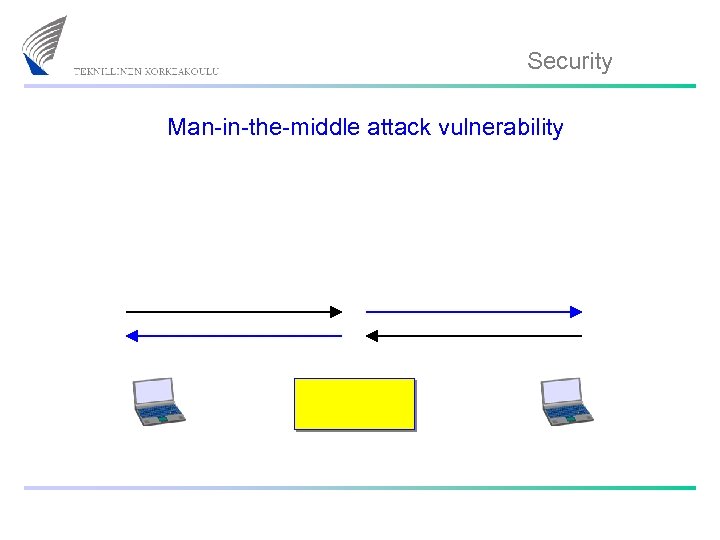 Security Man-in-the-middle attack vulnerability
Security Man-in-the-middle attack vulnerability
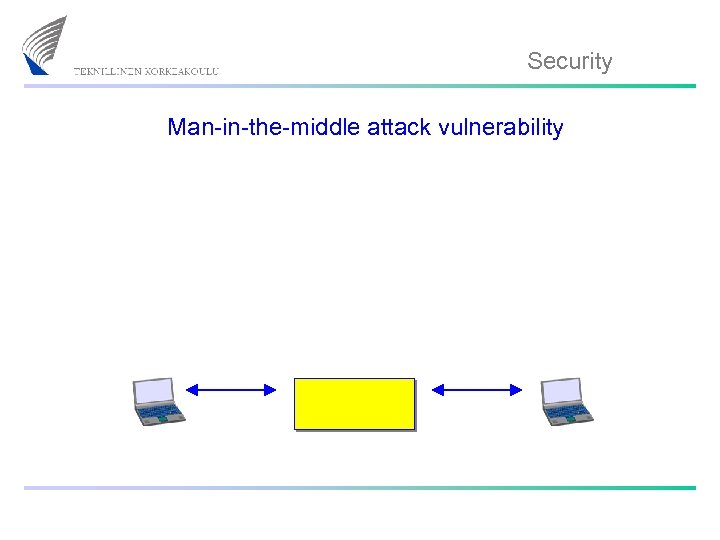 Security Man-in-the-middle attack vulnerability
Security Man-in-the-middle attack vulnerability
 Security Key transport scheme
Security Key transport scheme
 Security Digital signature (for authentication)
Security Digital signature (for authentication)
 Security RSA vs. DSA
Security RSA vs. DSA
 Security Symmetrical encryption (for confidentiality)
Security Symmetrical encryption (for confidentiality)
 Security Message digests (for integrity protection)
Security Message digests (for integrity protection)
 Security Certificates
Security Certificates
 Security Key length
Security Key length
 Security Putting it all together
Security Putting it all together
 Security SSL (TLS)
Security SSL (TLS)
 Security Basic SSL handshake operation (1)
Security Basic SSL handshake operation (1)
 Security Basic SSL handshake operation (2)
Security Basic SSL handshake operation (2)
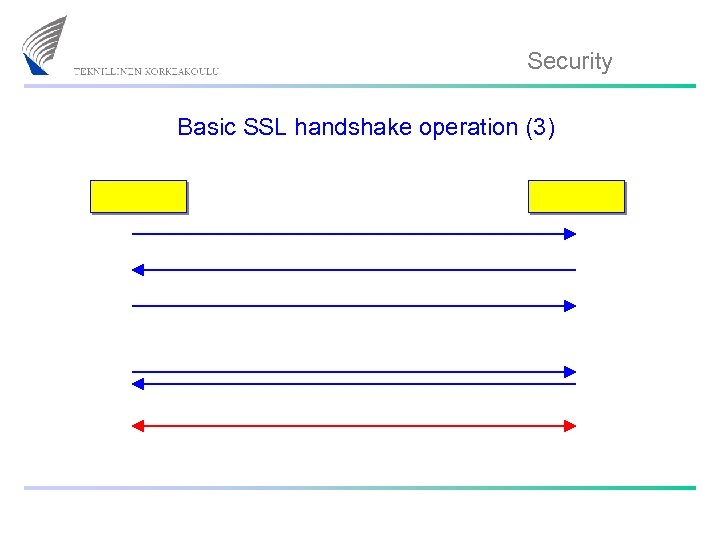 Security Basic SSL handshake operation (3)
Security Basic SSL handshake operation (3)
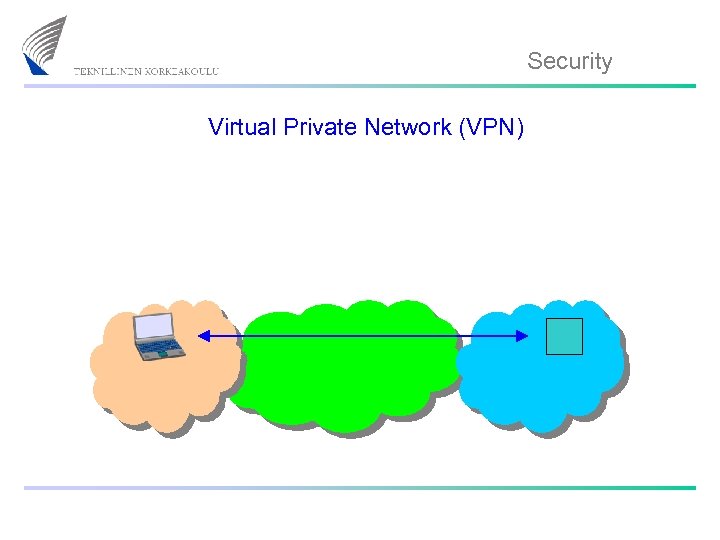 Security Virtual Private Network (VPN)
Security Virtual Private Network (VPN)
 Security Implementing VPN using IPSec
Security Implementing VPN using IPSec
 Security Two modes of IPSec
Security Two modes of IPSec
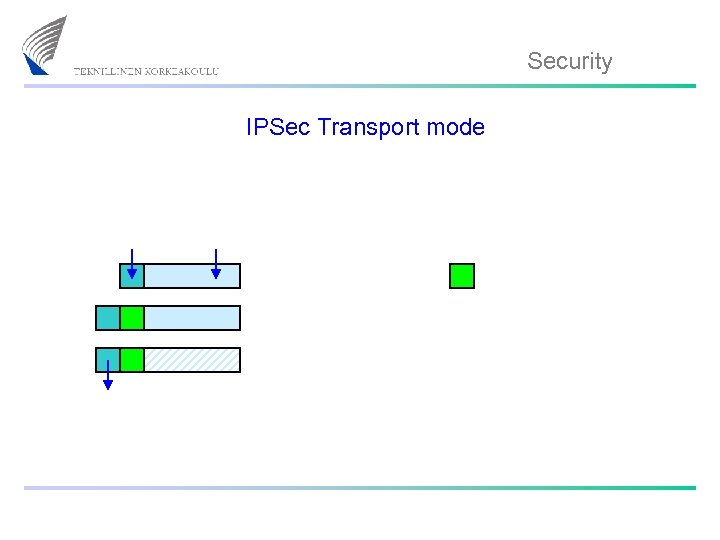 Security IPSec Transport mode
Security IPSec Transport mode
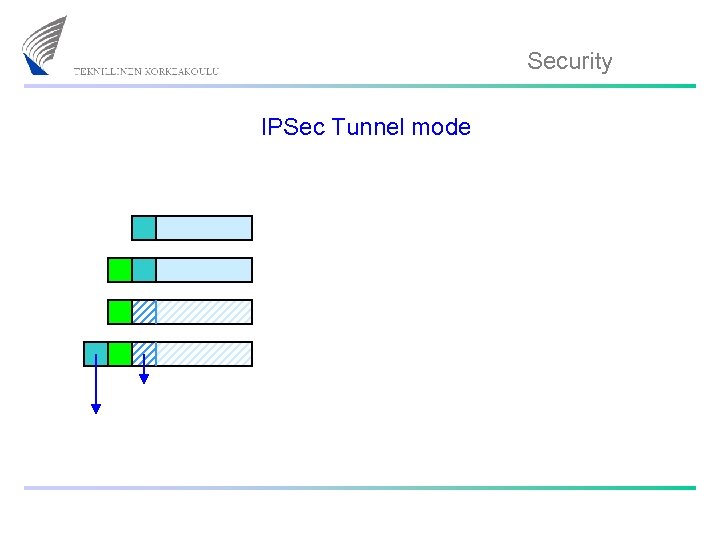 Security IPSec Tunnel mode
Security IPSec Tunnel mode
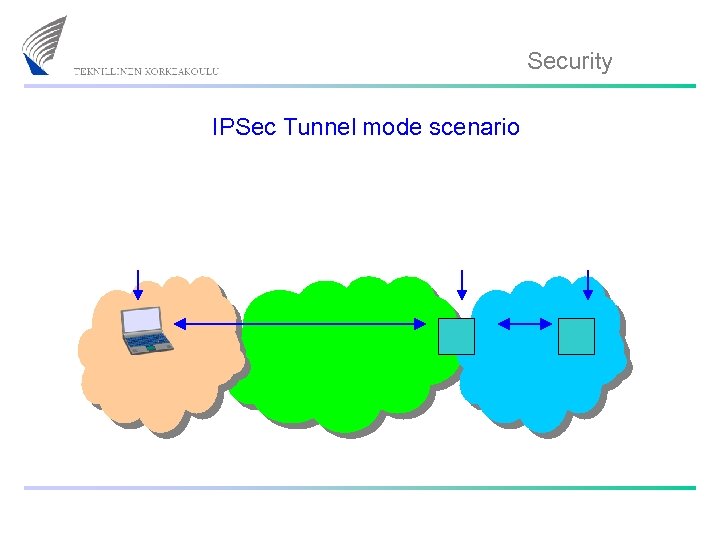 Security IPSec Tunnel mode scenario
Security IPSec Tunnel mode scenario
 Security IPSec security features
Security IPSec security features
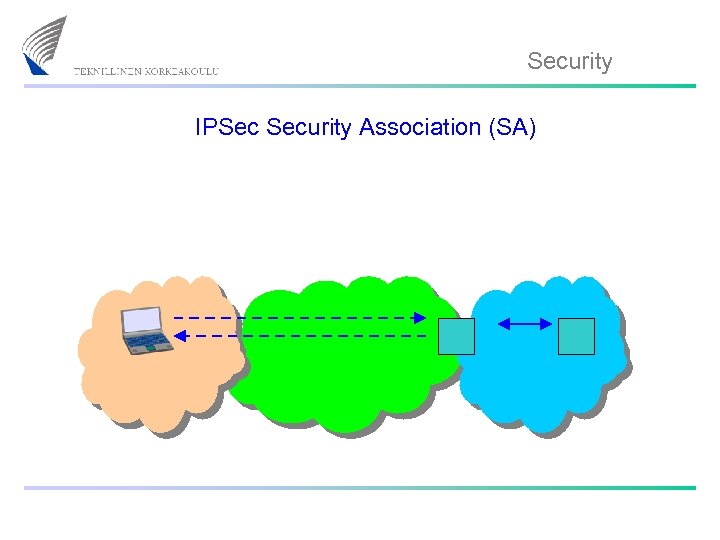 Security IPSec Security Association (SA)
Security IPSec Security Association (SA)
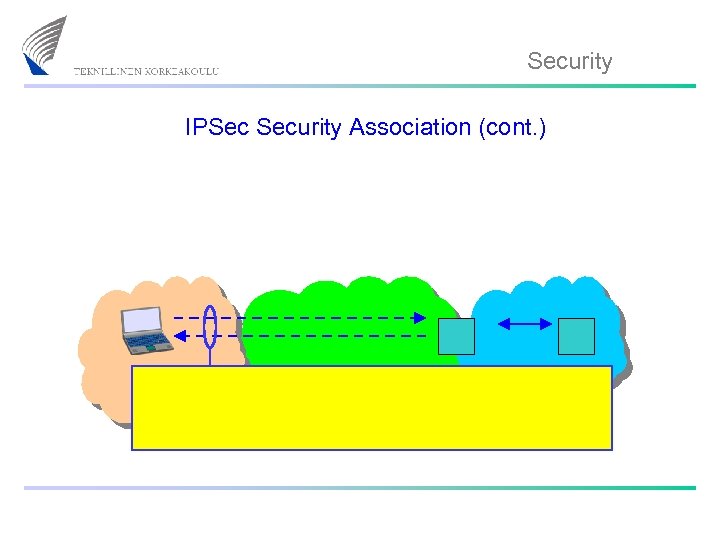 Security IPSec Security Association (cont. )
Security IPSec Security Association (cont. )