ac761e746d909dac8a7a671220117788.ppt
- Количество слайдов: 35
 Security Chapter 15
Security Chapter 15
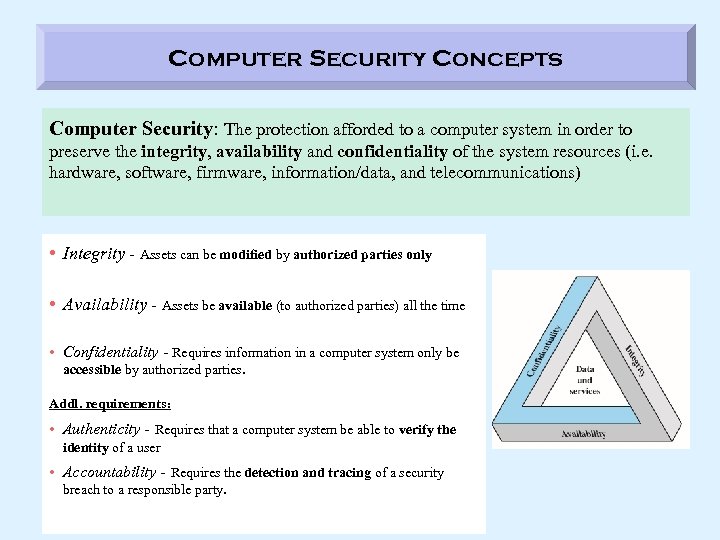 Computer Security Concepts Computer Security: The protection afforded to a computer system in order to preserve the integrity, availability and confidentiality of the system resources (i. e. hardware, software, firmware, information/data, and telecommunications) • Integrity - Assets can be modified by authorized parties only • Availability - Assets be available (to authorized parties) all the time • Confidentiality - Requires information in a computer system only be accessible by authorized parties. Addl. requirements: • Authenticity - Requires that a computer system be able to verify the identity of a user • Accountability - Requires the detection and tracing of a security breach to a responsible party.
Computer Security Concepts Computer Security: The protection afforded to a computer system in order to preserve the integrity, availability and confidentiality of the system resources (i. e. hardware, software, firmware, information/data, and telecommunications) • Integrity - Assets can be modified by authorized parties only • Availability - Assets be available (to authorized parties) all the time • Confidentiality - Requires information in a computer system only be accessible by authorized parties. Addl. requirements: • Authenticity - Requires that a computer system be able to verify the identity of a user • Accountability - Requires the detection and tracing of a security breach to a responsible party.
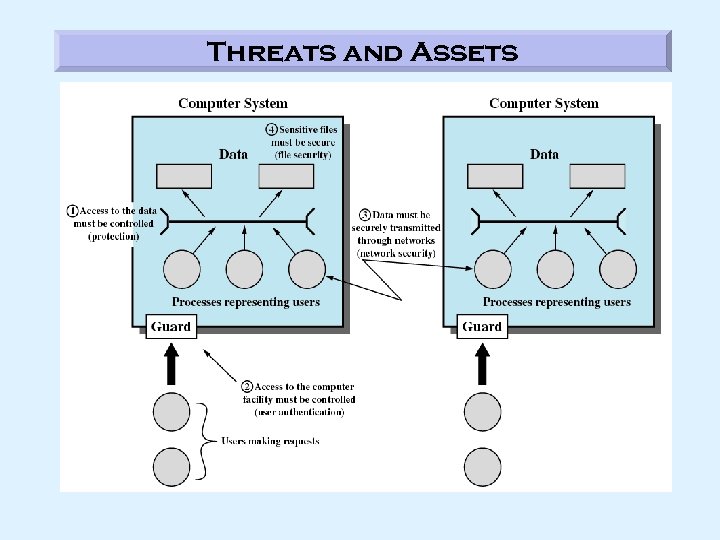 Threats and Assets
Threats and Assets
 System Access Threats System access threats fall into two general categories: Intruders Malicious software
System Access Threats System access threats fall into two general categories: Intruders Malicious software
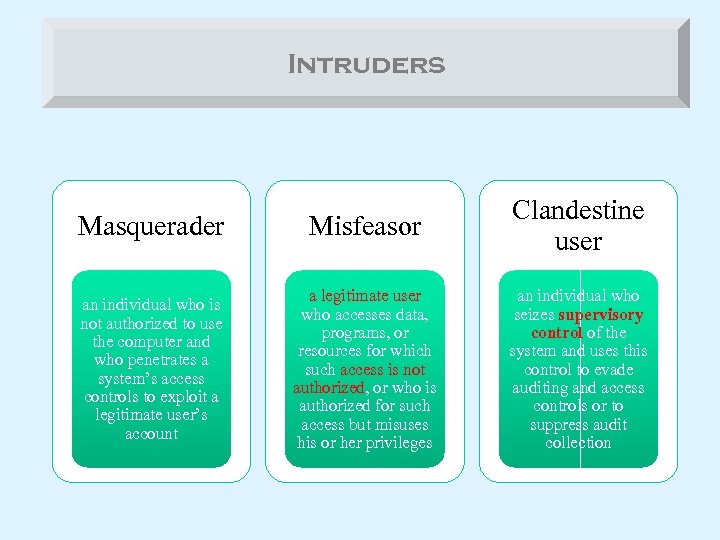 Intruders Masquerader Misfeasor Clandestine user an individual who is not authorized to use the computer and who penetrates a system’s access controls to exploit a legitimate user’s account a legitimate user who accesses data, programs, or resources for which such access is not authorized, or who is authorized for such access but misuses his or her privileges an individual who seizes supervisory control of the system and uses this control to evade auditing and access controls or to suppress audit collection
Intruders Masquerader Misfeasor Clandestine user an individual who is not authorized to use the computer and who penetrates a system’s access controls to exploit a legitimate user’s account a legitimate user who accesses data, programs, or resources for which such access is not authorized, or who is authorized for such access but misuses his or her privileges an individual who seizes supervisory control of the system and uses this control to evade auditing and access controls or to suppress audit collection
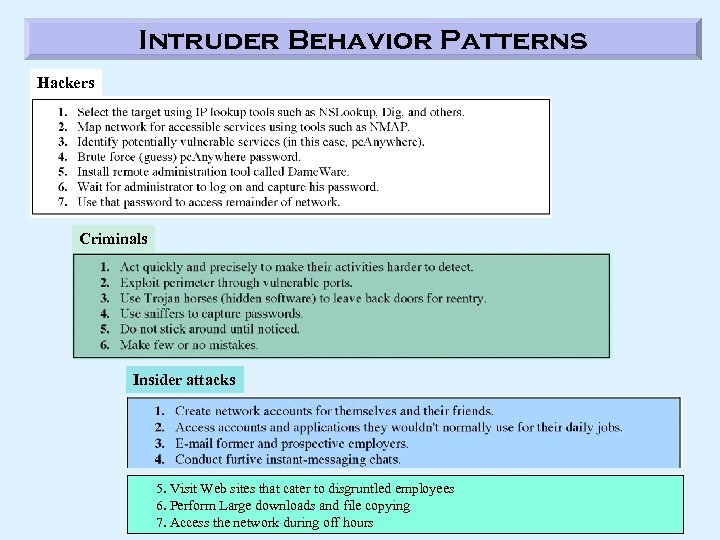 Intruder Behavior Patterns Hackers Criminals Insider attacks 5. Visit Web sites that cater to disgruntled employees 6. Perform Large downloads and file copying 7. Access the network during off hours
Intruder Behavior Patterns Hackers Criminals Insider attacks 5. Visit Web sites that cater to disgruntled employees 6. Perform Large downloads and file copying 7. Access the network during off hours
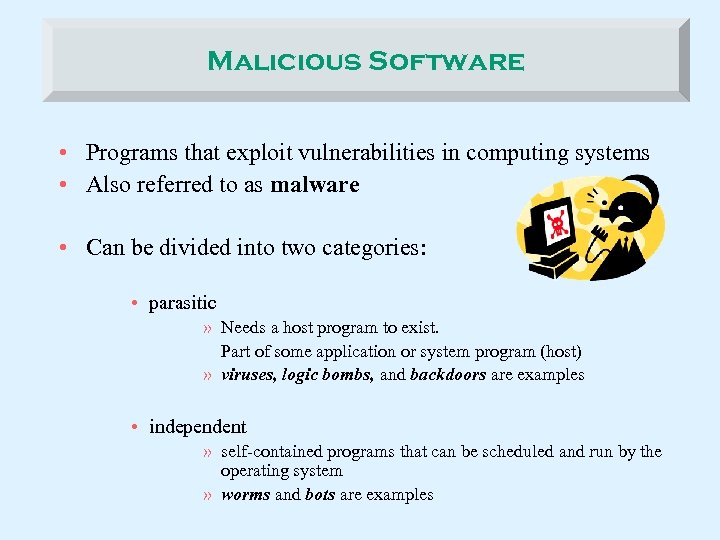 Malicious Software • Programs that exploit vulnerabilities in computing systems • Also referred to as malware • Can be divided into two categories: • parasitic » Needs a host program to exist. Part of some application or system program (host) » viruses, logic bombs, and backdoors are examples • independent » self-contained programs that can be scheduled and run by the operating system » worms and bots are examples
Malicious Software • Programs that exploit vulnerabilities in computing systems • Also referred to as malware • Can be divided into two categories: • parasitic » Needs a host program to exist. Part of some application or system program (host) » viruses, logic bombs, and backdoors are examples • independent » self-contained programs that can be scheduled and run by the operating system » worms and bots are examples
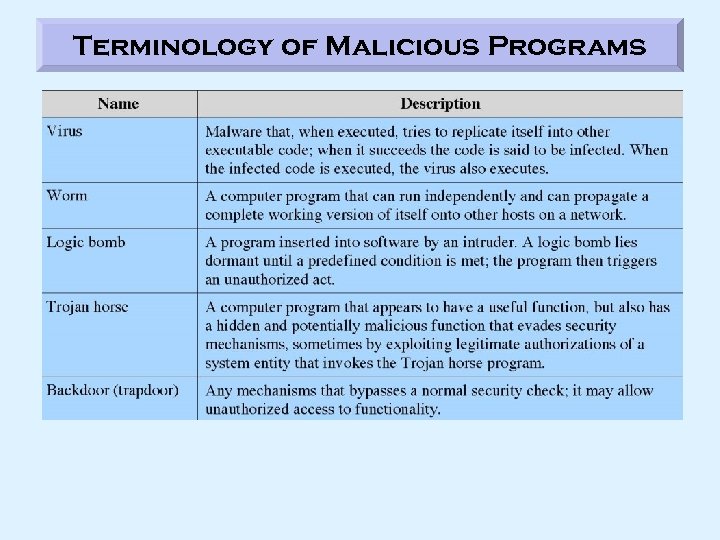
 Malicious Software (malware) Backdoor (Trapdoor) • Entry point into a program that allows someone who is aware of trapdoor to gain access • used by programmers to be able to debug and test programs while skipping a lengthy setup/authentication process during development – Avoids necessary setup and authentication Logic Bomb • Code embedded in a legitimate program that is set to “explode” when certain conditions are met • Presence or absence of certain files, particular day of the week, particular user running application • One of the oldest types of program threats, predating viruses and worms Trojan Horse • Useful program that contains hidden code; when invoked performs some harmful function – Can be installed through software downloads, bundling, email attachments, websites with executable content, etc. Trojan-type malware is on the rise, accounting for a very high percentage of the global malware. Viruses Program that can “infect” other programs by modifying them in such a way that the infected program can infect other programs E-mail Virus • Activated when recipient opens the e-mail attachment (e. g. Melissa virus). • Sends itself to everyone on the mailing list of the infected user
Malicious Software (malware) Backdoor (Trapdoor) • Entry point into a program that allows someone who is aware of trapdoor to gain access • used by programmers to be able to debug and test programs while skipping a lengthy setup/authentication process during development – Avoids necessary setup and authentication Logic Bomb • Code embedded in a legitimate program that is set to “explode” when certain conditions are met • Presence or absence of certain files, particular day of the week, particular user running application • One of the oldest types of program threats, predating viruses and worms Trojan Horse • Useful program that contains hidden code; when invoked performs some harmful function – Can be installed through software downloads, bundling, email attachments, websites with executable content, etc. Trojan-type malware is on the rise, accounting for a very high percentage of the global malware. Viruses Program that can “infect” other programs by modifying them in such a way that the infected program can infect other programs E-mail Virus • Activated when recipient opens the e-mail attachment (e. g. Melissa virus). • Sends itself to everyone on the mailing list of the infected user
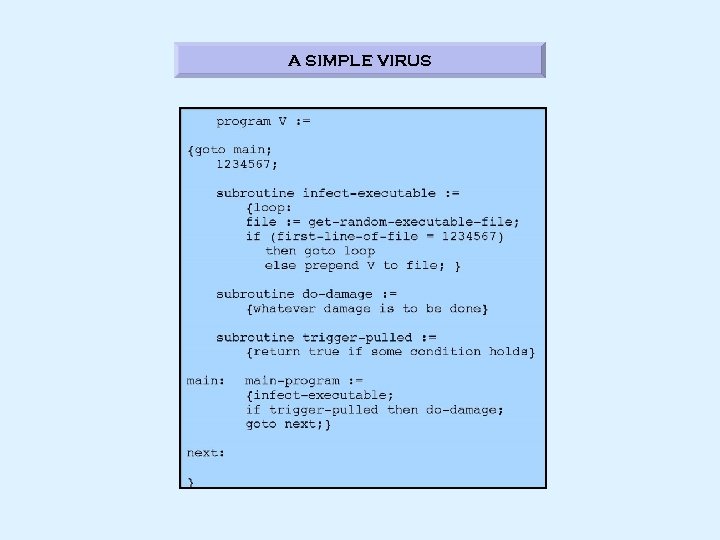 A SIMPLE VIRUS
A SIMPLE VIRUS
 Malware Defense Antivirus Approaches – (1) Detection (2) Identification (3) Removal As virus arms race has evolved, antivirus software have grown more complex. Two sophisticated ones are: Generic Decryption and Digital Immune System Generic Decryption (GD) Contains three essential parts: • CPU emulator – Instructions in an executable file are interpreted by the emulator rather than the processor in a controlled environment. If the code includes a decryption routine, it is also interpreted and the virus is exposed. Virus itself does the decryption for the antivirus program (GD) • Virus signature scanner – Scan target code looking for known virus signatures • Emulation control module – Controls the execution of the target code. Periodically, it interrupts the interpretation to scan the target code for virus signatures
Malware Defense Antivirus Approaches – (1) Detection (2) Identification (3) Removal As virus arms race has evolved, antivirus software have grown more complex. Two sophisticated ones are: Generic Decryption and Digital Immune System Generic Decryption (GD) Contains three essential parts: • CPU emulator – Instructions in an executable file are interpreted by the emulator rather than the processor in a controlled environment. If the code includes a decryption routine, it is also interpreted and the virus is exposed. Virus itself does the decryption for the antivirus program (GD) • Virus signature scanner – Scan target code looking for known virus signatures • Emulation control module – Controls the execution of the target code. Periodically, it interrupts the interpretation to scan the target code for virus signatures
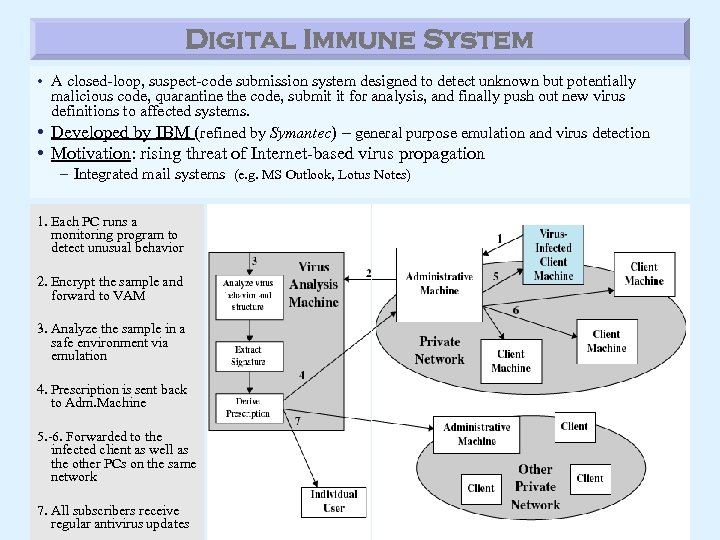 Digital Immune System • A closed-loop, suspect-code submission system designed to detect unknown but potentially malicious code, quarantine the code, submit it for analysis, and finally push out new virus definitions to affected systems. • Developed by IBM (refined by Symantec) – general purpose emulation and virus detection • Motivation: rising threat of Internet-based virus propagation – Integrated mail systems (e. g. MS Outlook, Lotus Notes) 1. Each PC runs a monitoring program to detect unusual behavior 2. Encrypt the sample and forward to VAM 3. Analyze the sample in a safe environment via emulation 4. Prescription is sent back to Adm. Machine 5. -6. Forwarded to the infected client as well as the other PCs on the same network 7. All subscribers receive regular antivirus updates
Digital Immune System • A closed-loop, suspect-code submission system designed to detect unknown but potentially malicious code, quarantine the code, submit it for analysis, and finally push out new virus definitions to affected systems. • Developed by IBM (refined by Symantec) – general purpose emulation and virus detection • Motivation: rising threat of Internet-based virus propagation – Integrated mail systems (e. g. MS Outlook, Lotus Notes) 1. Each PC runs a monitoring program to detect unusual behavior 2. Encrypt the sample and forward to VAM 3. Analyze the sample in a safe environment via emulation 4. Prescription is sent back to Adm. Machine 5. -6. Forwarded to the infected client as well as the other PCs on the same network 7. All subscribers receive regular antivirus updates
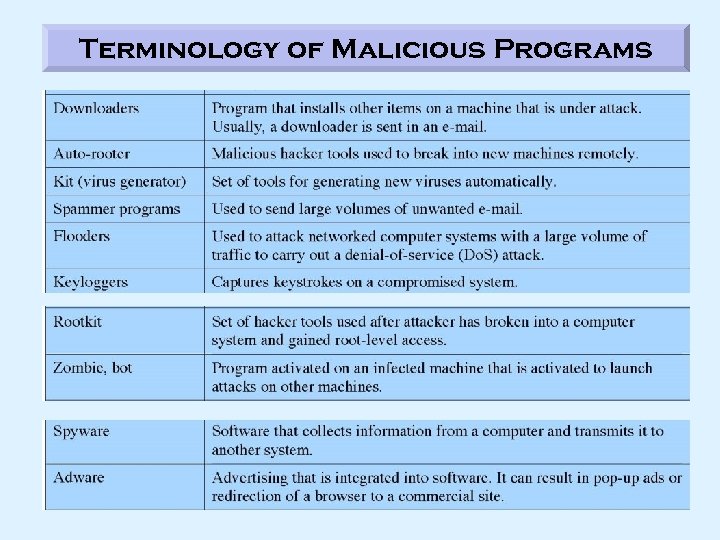
 Malicious Software (cont. ) Worms Exhibits similar characteristics as an e-mail virus, but worm does not need a host program and it is not passive, it actively seeks out more machines to infect via • Electronic mail facility: A worm mails a copy of itself to other systems • Remote execution: A worm executes a copy of itself on another system • Remote log-in: A worm logs on to a remote system as a user and then copies itself from one system to the other Some worms are used to create bots (zombies) Bots (Zombie or drone) • Program that secretly takes over another Internet-attached computer and uses it to launch attacks that are difficult to trace to the bot’s creator • planted on hundreds of computers belonging to unsuspecting third parties and then used to overwhelm a target Web site by launching an overwhelming onslaught of Internet traffic • The collection of bots acting in a coordinated manner is called botnet Uses of Bots • DDo. S (Distributed Denial of Service attacks), spamming, sniffing traffic on a compromised machine, keylogging, spreading new malware, manipulating online polls/games/clicks for ads (every bot has a distinct IP address), etc.
Malicious Software (cont. ) Worms Exhibits similar characteristics as an e-mail virus, but worm does not need a host program and it is not passive, it actively seeks out more machines to infect via • Electronic mail facility: A worm mails a copy of itself to other systems • Remote execution: A worm executes a copy of itself on another system • Remote log-in: A worm logs on to a remote system as a user and then copies itself from one system to the other Some worms are used to create bots (zombies) Bots (Zombie or drone) • Program that secretly takes over another Internet-attached computer and uses it to launch attacks that are difficult to trace to the bot’s creator • planted on hundreds of computers belonging to unsuspecting third parties and then used to overwhelm a target Web site by launching an overwhelming onslaught of Internet traffic • The collection of bots acting in a coordinated manner is called botnet Uses of Bots • DDo. S (Distributed Denial of Service attacks), spamming, sniffing traffic on a compromised machine, keylogging, spreading new malware, manipulating online polls/games/clicks for ads (every bot has a distinct IP address), etc.
 ROOTKITS Rootkit • Malware which consists of a set of programs designed to take fundamental control of a computer system and hide the fact that a system has been compromised e. g. Poison Ivy Remote Access Tool (RAT) • Typically, rootkits act to obscure their presence on the system through subversion or evasion of standard OS security mechanisms. • Techniques used to accomplish this can include concealing running processes from monitoring programs, or hiding files or system data from the OS • Rootkits may also install a "back door" in a system by replacing the login mechanism (such as /bin/login) with an executable that steals a login combination, which is used to access the system illegally. • With root access, an attacker has complete control of the system to do anything Rootkit Installation • Usually via a Trojan horse. A user is induced to load a Trojan horse which then installs the rootkit. • Another means of rootkit installation is by hacker activity which is a rather lengthy process.
ROOTKITS Rootkit • Malware which consists of a set of programs designed to take fundamental control of a computer system and hide the fact that a system has been compromised e. g. Poison Ivy Remote Access Tool (RAT) • Typically, rootkits act to obscure their presence on the system through subversion or evasion of standard OS security mechanisms. • Techniques used to accomplish this can include concealing running processes from monitoring programs, or hiding files or system data from the OS • Rootkits may also install a "back door" in a system by replacing the login mechanism (such as /bin/login) with an executable that steals a login combination, which is used to access the system illegally. • With root access, an attacker has complete control of the system to do anything Rootkit Installation • Usually via a Trojan horse. A user is induced to load a Trojan horse which then installs the rootkit. • Another means of rootkit installation is by hacker activity which is a rather lengthy process.
 BOTS Bots (Zombie or drone) • Program that secretly takes over another Internet-attached computer and uses it to launch attacks that are difficult to trace to the bot’s creator Remote Control Facility • A worm propagates and activates itself, whereas a bot is controlled from a central facility • Once a communication path is established, the control module can activate the bots in host machines (which are taken hostage). For greater flexibility, the control module can instruct the bots to download a file from an internet site and execute it. This way, a bot can be used for different kinds of attacks. Constructing the Attack Network 3 things needed: (1) attack software (2) a large number of vulnerable machines (3) locating these machines (scanning or fingerprinting). Scanning is generally done in a nested (or recursive) manner. Scanning strategies: • Random – check random IP addresses for vulnerability (generates suspicious internet traffic) • Hit list – a long list is compiled a priori. Each infected machine is given a partial list to infect generates less internet traffic and therefore makes it more difficult to detect. • Topological – uses information contained on an infected machine to find more hosts to scan • Local subnet – if a host could be infected behind a firewall, that host could be used to infect others on the same subnet (all behind the same firewall).
BOTS Bots (Zombie or drone) • Program that secretly takes over another Internet-attached computer and uses it to launch attacks that are difficult to trace to the bot’s creator Remote Control Facility • A worm propagates and activates itself, whereas a bot is controlled from a central facility • Once a communication path is established, the control module can activate the bots in host machines (which are taken hostage). For greater flexibility, the control module can instruct the bots to download a file from an internet site and execute it. This way, a bot can be used for different kinds of attacks. Constructing the Attack Network 3 things needed: (1) attack software (2) a large number of vulnerable machines (3) locating these machines (scanning or fingerprinting). Scanning is generally done in a nested (or recursive) manner. Scanning strategies: • Random – check random IP addresses for vulnerability (generates suspicious internet traffic) • Hit list – a long list is compiled a priori. Each infected machine is given a partial list to infect generates less internet traffic and therefore makes it more difficult to detect. • Topological – uses information contained on an infected machine to find more hosts to scan • Local subnet – if a host could be infected behind a firewall, that host could be used to infect others on the same subnet (all behind the same firewall).
 Buffer Overflow Attacks • Also known as a buffer overrun • Defined in the NIST (National Institute of Standards and Technology) Glossary of Key Information Security Terms as: “A condition at an interface under which more input can be placed into a buffer or data-holding area than the capacity allocated, overwriting other information. Attackers exploit such a condition to crash a system or to insert specially crafted code that allows them to gain control of the system” • • One of the most prevalent and dangerous types of security attacks Modern Languages provide bounds checking at run time to prevent buffer overflow. Therefore, more robust against such attacks.
Buffer Overflow Attacks • Also known as a buffer overrun • Defined in the NIST (National Institute of Standards and Technology) Glossary of Key Information Security Terms as: “A condition at an interface under which more input can be placed into a buffer or data-holding area than the capacity allocated, overwriting other information. Attackers exploit such a condition to crash a system or to insert specially crafted code that allows them to gain control of the system” • • One of the most prevalent and dangerous types of security attacks Modern Languages provide bounds checking at run time to prevent buffer overflow. Therefore, more robust against such attacks.
 Countermeasures • An Intrusion Detection System (IDS) is a security service that monitors and analyzes system events to detect unauthorized access • Intrusion detection systems (IDSs) can be classified as: • host-based IDS » monitors the characteristics of a single host and the events occurring within that host for suspicious activity • network-based IDS » monitors network traffic for particular network segments or devices and analyzes network, transport, and application protocols to identify suspicious activity
Countermeasures • An Intrusion Detection System (IDS) is a security service that monitors and analyzes system events to detect unauthorized access • Intrusion detection systems (IDSs) can be classified as: • host-based IDS » monitors the characteristics of a single host and the events occurring within that host for suspicious activity • network-based IDS » monitors network traffic for particular network segments or devices and analyzes network, transport, and application protocols to identify suspicious activity
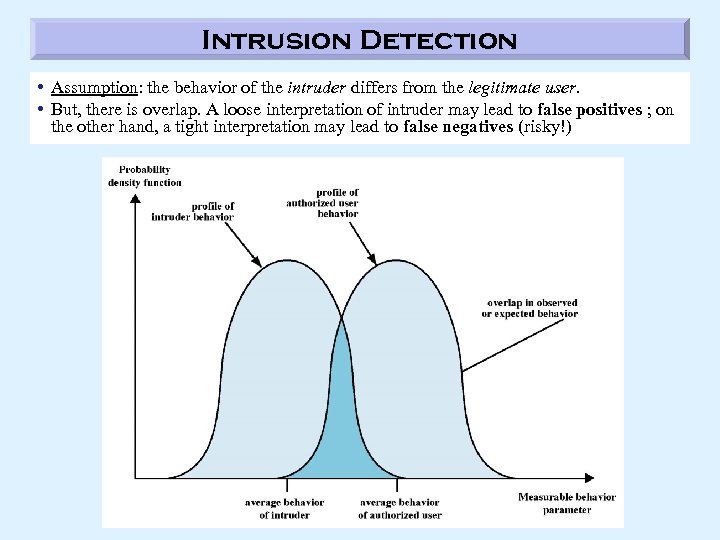 Intrusion Detection • Assumption: the behavior of the intruder differs from the legitimate user. • But, there is overlap. A loose interpretation of intruder may lead to false positives ; on the other hand, a tight interpretation may lead to false negatives (risky!)
Intrusion Detection • Assumption: the behavior of the intruder differs from the legitimate user. • But, there is overlap. A loose interpretation of intruder may lead to false positives ; on the other hand, a tight interpretation may lead to false negatives (risky!)
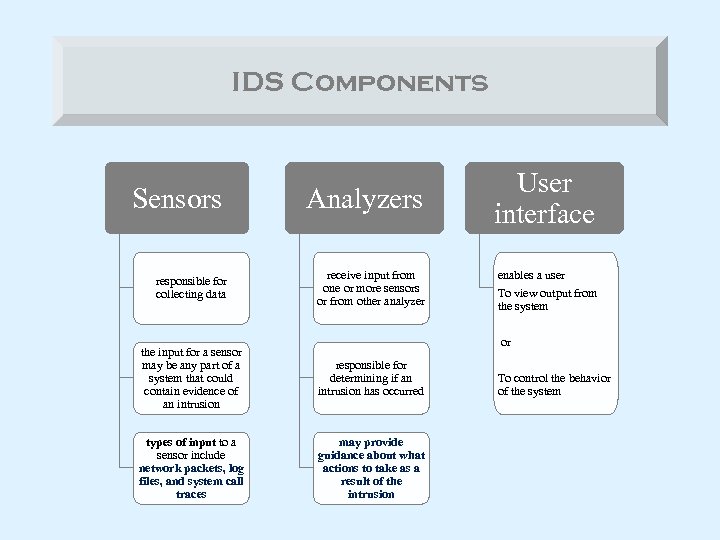 IDS Components Sensors responsible for collecting data Analyzers receive input from one or more sensors or from other analyzer User interface enables a user To view output from the system or the input for a sensor may be any part of a system that could contain evidence of an intrusion responsible for determining if an intrusion has occurred types of input to a sensor include network packets, log files, and system call traces may provide guidance about what actions to take as a result of the intrusion To control the behavior of the system
IDS Components Sensors responsible for collecting data Analyzers receive input from one or more sensors or from other analyzer User interface enables a user To view output from the system or the input for a sensor may be any part of a system that could contain evidence of an intrusion responsible for determining if an intrusion has occurred types of input to a sensor include network packets, log files, and system call traces may provide guidance about what actions to take as a result of the intrusion To control the behavior of the system
 Firewalls Design goals: • effective in protecting a system from network-based security threats while affording access to the outside world via the Internet • Traditionally, a firewall is a dedicated computer that interfaces with computers outside a network and protects sensitive files on computers within the network • Today, Personal Firewalls on PCs are also common 1) The firewall acts as a choke point, so that all incoming traffic and all outgoing traffic must pass through the firewall 2) Only authorized traffic, as defined by the local security policy, will be allowed to pass. 3) The firewall is secure against attacks
Firewalls Design goals: • effective in protecting a system from network-based security threats while affording access to the outside world via the Internet • Traditionally, a firewall is a dedicated computer that interfaces with computers outside a network and protects sensitive files on computers within the network • Today, Personal Firewalls on PCs are also common 1) The firewall acts as a choke point, so that all incoming traffic and all outgoing traffic must pass through the firewall 2) Only authorized traffic, as defined by the local security policy, will be allowed to pass. 3) The firewall is secure against attacks
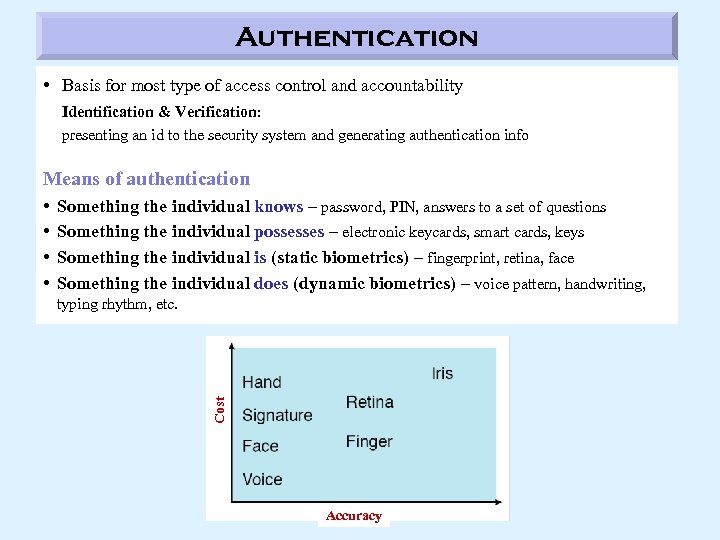 Authentication • Basis for most type of access control and accountability Identification & Verification: presenting an id to the security system and generating authentication info Means of authentication Something the individual knows – password, PIN, answers to a set of questions Something the individual possesses – electronic keycards, smart cards, keys Something the individual is (static biometrics) – fingerprint, retina, face Something the individual does (dynamic biometrics) – voice pattern, handwriting, typing rhythm, etc. Cost • • Accuracy
Authentication • Basis for most type of access control and accountability Identification & Verification: presenting an id to the security system and generating authentication info Means of authentication Something the individual knows – password, PIN, answers to a set of questions Something the individual possesses – electronic keycards, smart cards, keys Something the individual is (static biometrics) – fingerprint, retina, face Something the individual does (dynamic biometrics) – voice pattern, handwriting, typing rhythm, etc. Cost • • Accuracy
 Password Selection • Computer generated passwords – Users have difficulty remembering them; Need to write it down – Have history of poor acceptance • Reactive password checking strategy – System periodically runs its own password cracker to find guessable passwords. It cancels passwords that are guessed and notifies user • Proactive password checker – The system checks at the time of selection if the password is allowable – With guidance from the system, users can select memorable passwords that are difficult to guess
Password Selection • Computer generated passwords – Users have difficulty remembering them; Need to write it down – Have history of poor acceptance • Reactive password checking strategy – System periodically runs its own password cracker to find guessable passwords. It cancels passwords that are guessed and notifies user • Proactive password checker – The system checks at the time of selection if the password is allowable – With guidance from the system, users can select memorable passwords that are difficult to guess
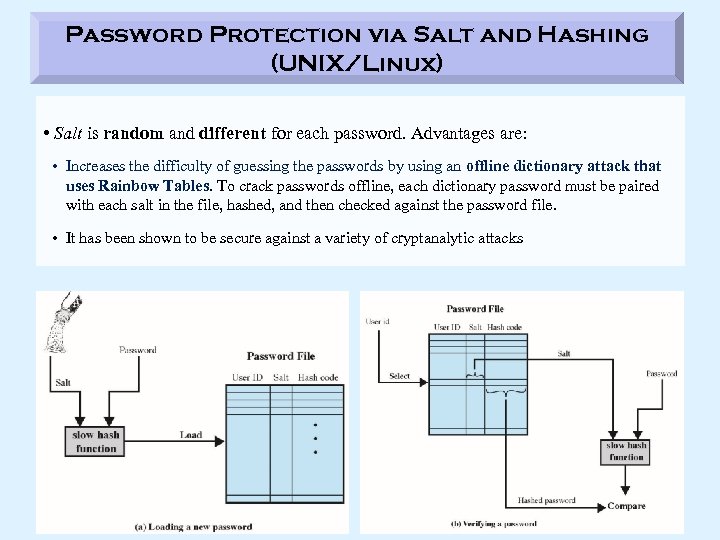 Password Protection via Salt and Hashing (UNIX/Linux) • Salt is random and different for each password. Advantages are: • Increases the difficulty of guessing the passwords by using an offline dictionary attack that uses Rainbow Tables. To crack passwords offline, each dictionary password must be paired with each salt in the file, hashed, and then checked against the password file. • It has been shown to be secure against a variety of cryptanalytic attacks
Password Protection via Salt and Hashing (UNIX/Linux) • Salt is random and different for each password. Advantages are: • Increases the difficulty of guessing the passwords by using an offline dictionary attack that uses Rainbow Tables. To crack passwords offline, each dictionary password must be paired with each salt in the file, hashed, and then checked against the password file. • It has been shown to be secure against a variety of cryptanalytic attacks
 Access Control • Implements a security policy that specifies who or what may have access to each resource and the type of access that is permitted in each instance • A security administrator maintains an authorization database that specifies what type of access to which resources is allowed for this user – the access control function consults this database to determine whether to grant access • An auditing function monitors and keeps a record (logs) of user accesses to system resources
Access Control • Implements a security policy that specifies who or what may have access to each resource and the type of access that is permitted in each instance • A security administrator maintains an authorization database that specifies what type of access to which resources is allowed for this user – the access control function consults this database to determine whether to grant access • An auditing function monitors and keeps a record (logs) of user accesses to system resources
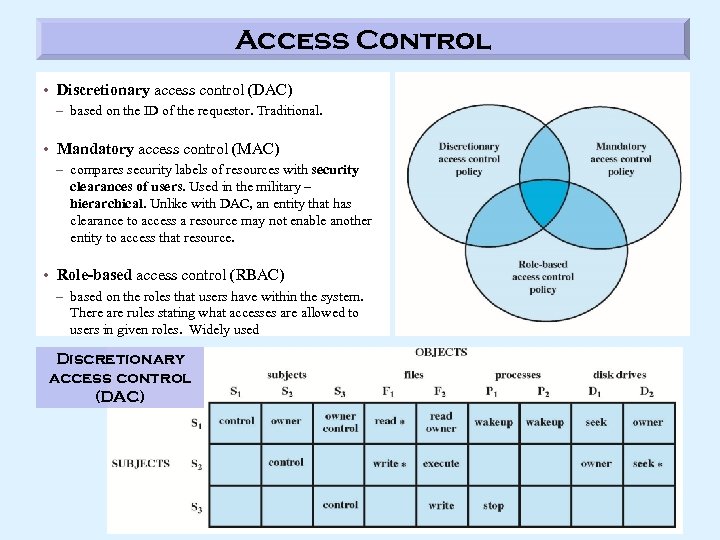 Access Control • Discretionary access control (DAC) – based on the ID of the requestor. Traditional. • Mandatory access control (MAC) – compares security labels of resources with security clearances of users. Used in the military – hierarchical. Unlike with DAC, an entity that has clearance to access a resource may not enable another entity to access that resource. • Role-based access control (RBAC) – based on the roles that users have within the system. There are rules stating what accesses are allowed to users in given roles. Widely used Discretionary access control (DAC)
Access Control • Discretionary access control (DAC) – based on the ID of the requestor. Traditional. • Mandatory access control (MAC) – compares security labels of resources with security clearances of users. Used in the military – hierarchical. Unlike with DAC, an entity that has clearance to access a resource may not enable another entity to access that resource. • Role-based access control (RBAC) – based on the roles that users have within the system. There are rules stating what accesses are allowed to users in given roles. Widely used Discretionary access control (DAC)
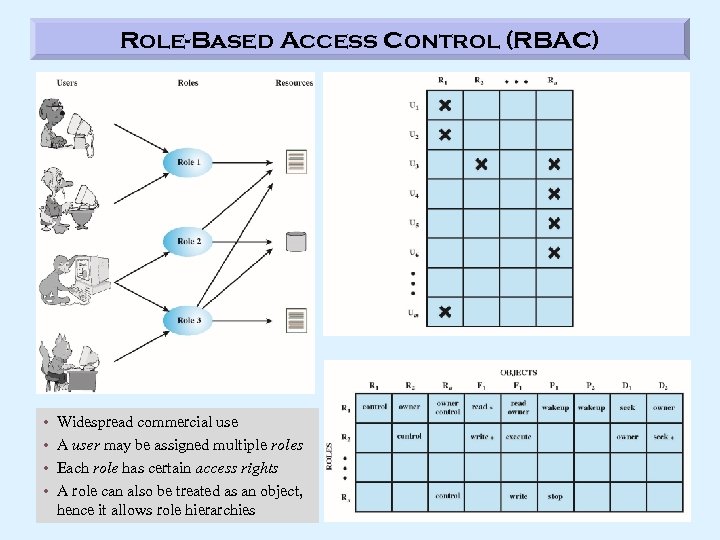 Role-Based Access Control (RBAC) • • Widespread commercial use A user may be assigned multiple roles Each role has certain access rights A role can also be treated as an object, hence it allows role hierarchies
Role-Based Access Control (RBAC) • • Widespread commercial use A user may be assigned multiple roles Each role has certain access rights A role can also be treated as an object, hence it allows role hierarchies
 Terminology of Malicious Programs
Terminology of Malicious Programs
 Terminology of Malicious Programs
Terminology of Malicious Programs
 Operating System Installation: Initial Setup and Patching System security begins with the installation of the operating system Ideally new systems should be constructed on a protected network The initial installation should comprise the minimum necessary for the desired system, with additional software packages included only if they are required for the function of the system Care is also required with the selection and installation of any additional device driver code, since this executes with full kernel level privileges, but is often supplied by a third party
Operating System Installation: Initial Setup and Patching System security begins with the installation of the operating system Ideally new systems should be constructed on a protected network The initial installation should comprise the minimum necessary for the desired system, with additional software packages included only if they are required for the function of the system Care is also required with the selection and installation of any additional device driver code, since this executes with full kernel level privileges, but is often supplied by a third party
 Remove Unnecessary Services, Applications, and Protocols • To improve security, identify what is actually required for a given system so that a suitable level of functionality is provided. Installation should be customized and only the required packages are installed • Eliminate software that is not required. • Follow the security-hardening guides which provide lists of services, applications, and protocols that should not be installed if not required • Since many uninstall scripts fail to completely remove all components of a package, do not install optional software • should an attacker succeed in gaining some access to a system, disabled software could be re-enabled and used to further compromise a system
Remove Unnecessary Services, Applications, and Protocols • To improve security, identify what is actually required for a given system so that a suitable level of functionality is provided. Installation should be customized and only the required packages are installed • Eliminate software that is not required. • Follow the security-hardening guides which provide lists of services, applications, and protocols that should not be installed if not required • Since many uninstall scripts fail to completely remove all components of a package, do not install optional software • should an attacker succeed in gaining some access to a system, disabled software could be re-enabled and used to further compromise a system
 Configure Users, Groups, and Authentication • The system planning process should consider: the categories of users on the system the privileges they have the types of informatio n they can access • Restrict elevated privileges to only those users that require them • Those accounts which are not required should be removed or disabled • System accounts that manage services on the system should be set such that they cannot be used for interactive logins • Any passwords installed by default should be changed to new values with appropriate security • Once the users and their associated groups are defined, appropriate permissions can be set on data and resources
Configure Users, Groups, and Authentication • The system planning process should consider: the categories of users on the system the privileges they have the types of informatio n they can access • Restrict elevated privileges to only those users that require them • Those accounts which are not required should be removed or disabled • System accounts that manage services on the system should be set such that they cannot be used for interactive logins • Any passwords installed by default should be changed to new values with appropriate security • Once the users and their associated groups are defined, appropriate permissions can be set on data and resources
 Install Additional Security Controls • Further security improvements: Install: antivirus software host-based firewall, IDS or IPS (Intrusion Prevention System). • Some of these may be supplied as part of the operating systems installation, but not configured and enabled by default • Given the wide-spread prevalence of malware, appropriate antivirus is a critical security component • IDS and IPS software may include additional mechanisms such as traffic monitoring or file integrity checking to identify and even respond to some types of attack
Install Additional Security Controls • Further security improvements: Install: antivirus software host-based firewall, IDS or IPS (Intrusion Prevention System). • Some of these may be supplied as part of the operating systems installation, but not configured and enabled by default • Given the wide-spread prevalence of malware, appropriate antivirus is a critical security component • IDS and IPS software may include additional mechanisms such as traffic monitoring or file integrity checking to identify and even respond to some types of attack
 Logging • Log data is generated by the system, network, and applications • • Effective logging helps ensure that in the event of a system breach or failure, system administrators can quickly and accurately identify what happened and more effectively focus their remediation and recovery efforts Logging can generate significant volumes of information so it is important that sufficient space is allocated for them • manual analysis of logs is tedious and unreliable therefore automated analysis must be done
Logging • Log data is generated by the system, network, and applications • • Effective logging helps ensure that in the event of a system breach or failure, system administrators can quickly and accurately identify what happened and more effectively focus their remediation and recovery efforts Logging can generate significant volumes of information so it is important that sufficient space is allocated for them • manual analysis of logs is tedious and unreliable therefore automated analysis must be done
 Data Backup and Archive • Performing periodic backups of data on a system is important and critical • The policy relating to backup and archive should be determined during the system planning stage – Key decisions: • should the copies be kept online or offline? • Should the copies be stored locally or transported to a remote site? • Archive: retaining copies over extended periods of time (months/years) in order to meet legal and operational requirements to access past data
Data Backup and Archive • Performing periodic backups of data on a system is important and critical • The policy relating to backup and archive should be determined during the system planning stage – Key decisions: • should the copies be kept online or offline? • Should the copies be stored locally or transported to a remote site? • Archive: retaining copies over extended periods of time (months/years) in order to meet legal and operational requirements to access past data
 Test the System Security • To ensure that the security configuration steps are correctly implemented and to identify any possible vulnerabilities we must perform security testing • Suitable checklists are included in many security-hardening guides • There are programs specifically designed to review a system and ensure that it meets the basic security requirements and scan for known vulnerabilities and poor configuration practices • This should be done following the initial hardening of the system and then repeated periodically as part of the security maintenance process
Test the System Security • To ensure that the security configuration steps are correctly implemented and to identify any possible vulnerabilities we must perform security testing • Suitable checklists are included in many security-hardening guides • There are programs specifically designed to review a system and ensure that it meets the basic security requirements and scan for known vulnerabilities and poor configuration practices • This should be done following the initial hardening of the system and then repeated periodically as part of the security maintenance process
 Security Maintenance • The process of security maintenance includes the following steps: Testing system security regularly performing regular backups recovering from security compromises monitoring and analyzing logging information Patching and updating all critical software Monitoring and Revising configuration as needed
Security Maintenance • The process of security maintenance includes the following steps: Testing system security regularly performing regular backups recovering from security compromises monitoring and analyzing logging information Patching and updating all critical software Monitoring and Revising configuration as needed


