0e6e24fbbc898962aa18be3b6459e860.ppt
- Количество слайдов: 80
 Security Chapter 10 Copyright 2001 Prentice Hall Revision 2: May 2001
Security Chapter 10 Copyright 2001 Prentice Hall Revision 2: May 2001
 Security Hackers break into organizations from the outside However, most security breaches are internal, by employees and exemployees
Security Hackers break into organizations from the outside However, most security breaches are internal, by employees and exemployees
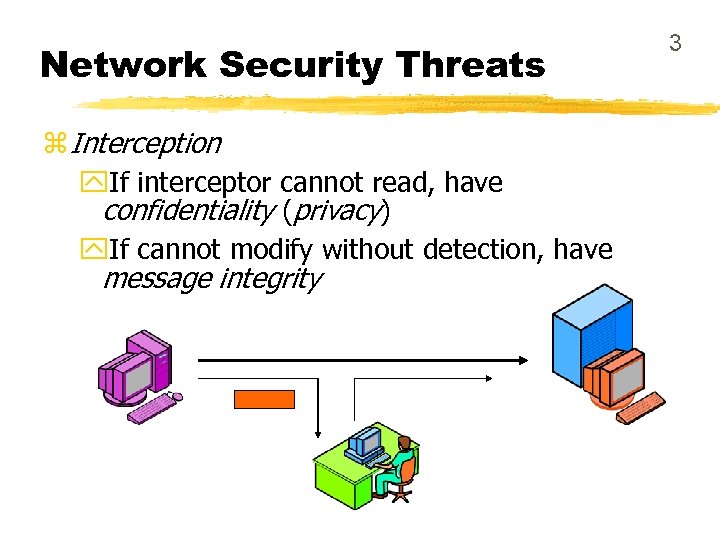 Network Security Threats z Interception y. If interceptor cannot read, have confidentiality (privacy) y. If cannot modify without detection, have message integrity 3
Network Security Threats z Interception y. If interceptor cannot read, have confidentiality (privacy) y. If cannot modify without detection, have message integrity 3
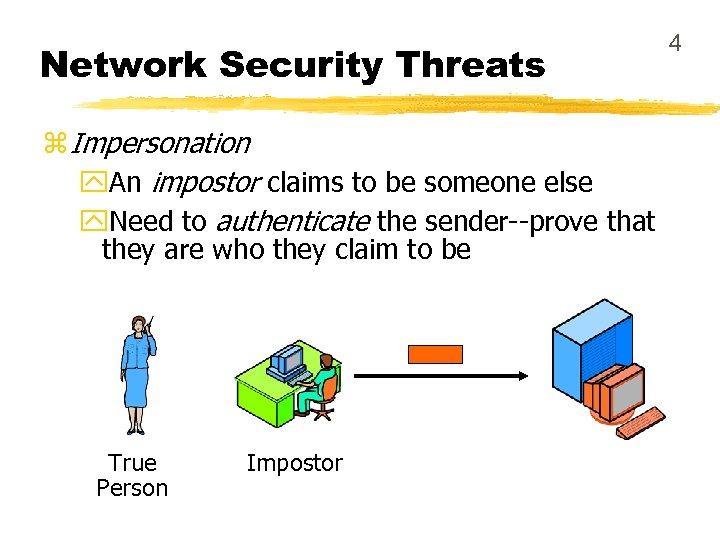 Network Security Threats z Impersonation y. An impostor claims to be someone else y. Need to authenticate the sender--prove that they are who they claim to be True Person Impostor 4
Network Security Threats z Impersonation y. An impostor claims to be someone else y. Need to authenticate the sender--prove that they are who they claim to be True Person Impostor 4
 Network Security Threats z Denial of Service (DOS) Attacks y. Overload system with a flood of messages y. Or, send a single message that crashes the machine 5
Network Security Threats z Denial of Service (DOS) Attacks y. Overload system with a flood of messages y. Or, send a single message that crashes the machine 5
 Network Security Threats z Remotely Log in as Root User y. Requires cracking the root login password y. Then control the machine y. Read and/or steal information y. Damage data (erase hard disk) y. Create backdoor user account that will let them in easily later Root Login Command 6
Network Security Threats z Remotely Log in as Root User y. Requires cracking the root login password y. Then control the machine y. Read and/or steal information y. Damage data (erase hard disk) y. Create backdoor user account that will let them in easily later Root Login Command 6
 Super Accounts 7 New z Have Access to Everything on the Machine y. UNIX/LINUX: root y. Microsoft: Administrator y. Net. Ware: Supervisor y. Other accounts can be given equivalent rights z Dangerous y. If intruder gets the password to this account x. Protect with a super-strong password y. If the server administrator is dishonest
Super Accounts 7 New z Have Access to Everything on the Machine y. UNIX/LINUX: root y. Microsoft: Administrator y. Net. Ware: Supervisor y. Other accounts can be given equivalent rights z Dangerous y. If intruder gets the password to this account x. Protect with a super-strong password y. If the server administrator is dishonest
 Security Threats 8 z Content Threats y. Application layer content may cause problems x. Viruses x. In many ways, most severe security problem in corporations today x. Must examine the contents of application messages • At least extensions of files or MIME data type being transferred
Security Threats 8 z Content Threats y. Application layer content may cause problems x. Viruses x. In many ways, most severe security problem in corporations today x. Must examine the contents of application messages • At least extensions of files or MIME data type being transferred
 Encryption for Confidentiality
Encryption for Confidentiality
 10 Encryption z Encryption: Transforms Message so that Interceptor Cannot Read it y. For confidentiality, do not want an interceptor to read the message y. Plaintext (original message) x. Not necessarily text; Can be graphics, etc. “ 47” Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
10 Encryption z Encryption: Transforms Message so that Interceptor Cannot Read it y. For confidentiality, do not want an interceptor to read the message y. Plaintext (original message) x. Not necessarily text; Can be graphics, etc. “ 47” Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
 11 Encryption z Encryption: Transforms Message so that Interceptor Cannot Read it y. Ciphertext (transformed) for transmission x. Stream of ones and zeros for transmission x. Interceptor cannot make sense of it 101101 Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
11 Encryption z Encryption: Transforms Message so that Interceptor Cannot Read it y. Ciphertext (transformed) for transmission x. Stream of ones and zeros for transmission x. Interceptor cannot make sense of it 101101 Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
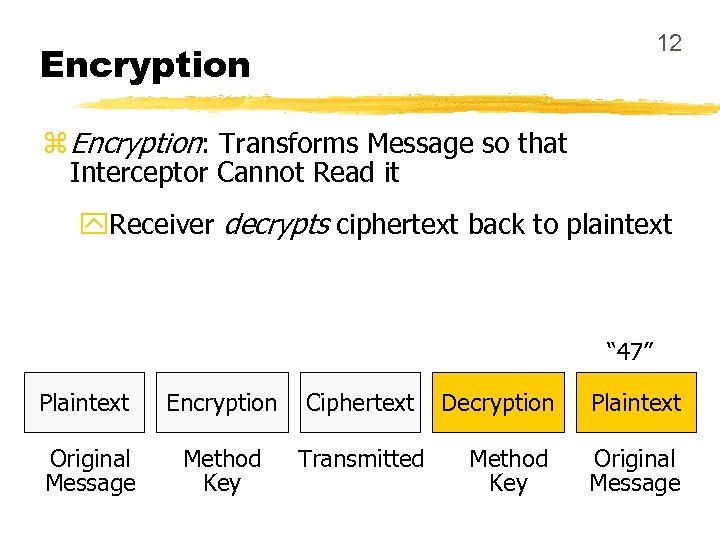 12 Encryption z Encryption: Transforms Message so that Interceptor Cannot Read it y. Receiver decrypts ciphertext back to plaintext “ 47” Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
12 Encryption z Encryption: Transforms Message so that Interceptor Cannot Read it y. Receiver decrypts ciphertext back to plaintext “ 47” Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
 13 Encryption z. Encryption Requires a Method and a Key y. Encryption method is the specific mathematical transformation process y. Key is a string of bits used in the method y. Get different ciphertexts with different keys Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
13 Encryption z. Encryption Requires a Method and a Key y. Encryption method is the specific mathematical transformation process y. Key is a string of bits used in the method y. Get different ciphertexts with different keys Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
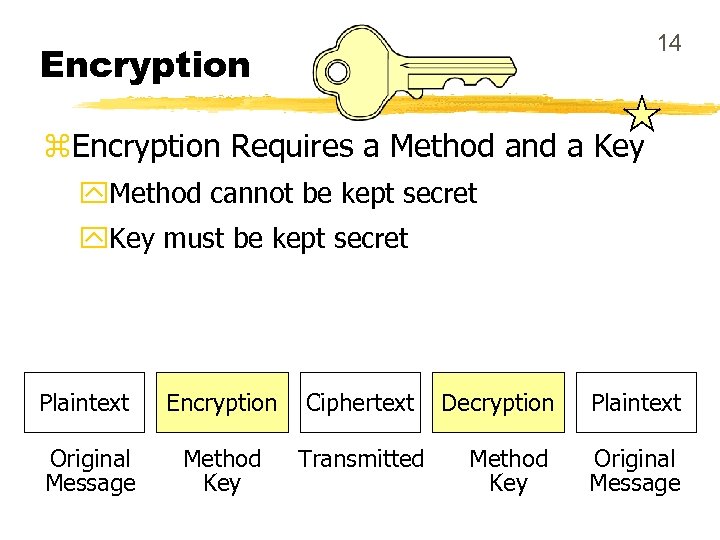 14 Encryption z. Encryption Requires a Method and a Key y. Method cannot be kept secret y. Key must be kept secret Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
14 Encryption z. Encryption Requires a Method and a Key y. Method cannot be kept secret y. Key must be kept secret Plaintext Encryption Ciphertext Original Message Method Key Transmitted Decryption Plaintext Method Key Original Message
 Encryption: Key Length z Key can be “guessed” by exhaustive search y. Try all possible keys y. See which one decrypts the message z Long keys make exhaustive search difficult y. If length is n bits, 2 n tries maximum needed y. Today: <100 bits are weak y. Today: >100 bit keys are strong y. Tomorrow will need even longer keys 15
Encryption: Key Length z Key can be “guessed” by exhaustive search y. Try all possible keys y. See which one decrypts the message z Long keys make exhaustive search difficult y. If length is n bits, 2 n tries maximum needed y. Today: <100 bits are weak y. Today: >100 bit keys are strong y. Tomorrow will need even longer keys 15
 Methods and Algorithms z Encryption Method Categories y. Two general ways of doing encryption y. Symmetric key versus public key encryption z Encryption Method Algorithms y. Specific ways of doing encryption y. With symmetric key encryption: DES, 3 DES, AES, IDEA, Blowfish, and RC 5 algorithms y. With public key encryption: RSA, elliptical curve cryptosystem (ECC) algorithms 16
Methods and Algorithms z Encryption Method Categories y. Two general ways of doing encryption y. Symmetric key versus public key encryption z Encryption Method Algorithms y. Specific ways of doing encryption y. With symmetric key encryption: DES, 3 DES, AES, IDEA, Blowfish, and RC 5 algorithms y. With public key encryption: RSA, elliptical curve cryptosystem (ECC) algorithms 16
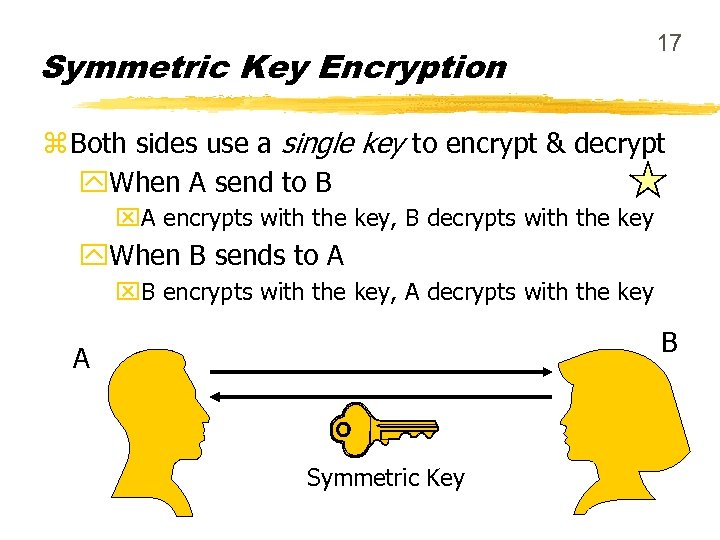 Symmetric Key Encryption 17 z Both sides use a single key to encrypt & decrypt y. When A send to B x. A encrypts with the key, B decrypts with the key y. When B sends to A x. B encrypts with the key, A decrypts with the key B A Symmetric Key
Symmetric Key Encryption 17 z Both sides use a single key to encrypt & decrypt y. When A send to B x. A encrypts with the key, B decrypts with the key y. When B sends to A x. B encrypts with the key, A decrypts with the key B A Symmetric Key
 Symmetric Key Encryption 18 z Symmetric key encryption and decryption processes are simple enough for fast encryption/decryption y. Fast enough for long messages B A Symmetric Key
Symmetric Key Encryption 18 z Symmetric key encryption and decryption processes are simple enough for fast encryption/decryption y. Fast enough for long messages B A Symmetric Key
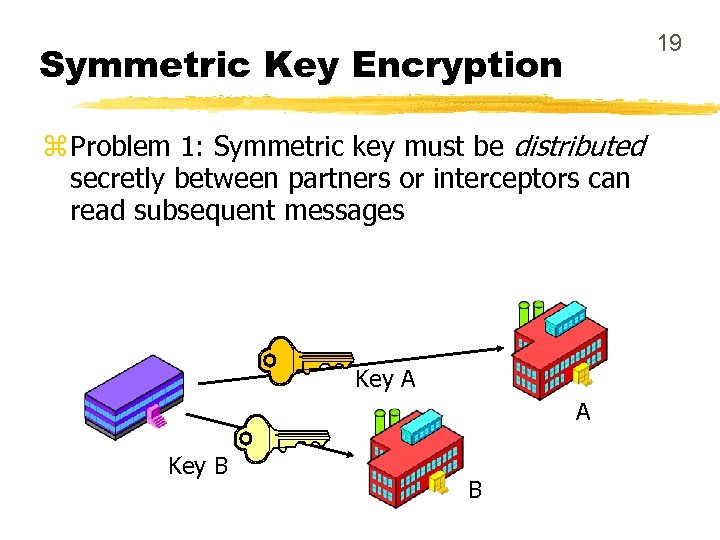 19 Symmetric Key Encryption z Problem 1: Symmetric key must be distributed secretly between partners or interceptors can read subsequent messages Key A A Key B B
19 Symmetric Key Encryption z Problem 1: Symmetric key must be distributed secretly between partners or interceptors can read subsequent messages Key A A Key B B
 20 Symmetric Key Encryption z Problem 2: Need a different symmetric key for each business partner y. Or other partners could read messages y. Complicates symmetric key distribution Key A A Key B B
20 Symmetric Key Encryption z Problem 2: Need a different symmetric key for each business partner y. Or other partners could read messages y. Complicates symmetric key distribution Key A A Key B B
 Symmetric Key Encryption z. Data Encryption Standard (DES) y. Extremely popular symmetric key algorithm y. Uses 56 -bit key, which is inadequate for consumer transactions z 3 DES (Triple DES) y. Uses three 56 -bit keys for 3 stages of encryption y 168 -bit effective key length y. Sufficient for financial networks 21
Symmetric Key Encryption z. Data Encryption Standard (DES) y. Extremely popular symmetric key algorithm y. Uses 56 -bit key, which is inadequate for consumer transactions z 3 DES (Triple DES) y. Uses three 56 -bit keys for 3 stages of encryption y 168 -bit effective key length y. Sufficient for financial networks 21
 Symmetric Key Encryption z DES is an old algorithm y. Developed in 1970 s y 3 DES is merely a way of extending its life z Advanced Encryption System (AES) y. Being developed by the U. S. National Institutes for Standards and Technology y. Will be much stronger with longer keys y. Will be efficient enough to implement on hand-held devices 22
Symmetric Key Encryption z DES is an old algorithm y. Developed in 1970 s y 3 DES is merely a way of extending its life z Advanced Encryption System (AES) y. Being developed by the U. S. National Institutes for Standards and Technology y. Will be much stronger with longer keys y. Will be efficient enough to implement on hand-held devices 22
 Public Key Encryption z Recap: There are Two General Encryption Method Categories y. Symmetric key encryption (just seen) y. Public key encryption (next) 23
Public Key Encryption z Recap: There are Two General Encryption Method Categories y. Symmetric key encryption (just seen) y. Public key encryption (next) 23
 24 Public Key Encryption Methods z Different keys for encryption and decryption y. Encryption with receiver’s public key y. Decryption with receiver’s private key y. Once encrypted, sender cannot decrypt the ciphertext; does not have receiver’s private key Plaintext Encryption Ciphertext Receiver’s Public Key Decryption Plaintext Receiver’s Private Key
24 Public Key Encryption Methods z Different keys for encryption and decryption y. Encryption with receiver’s public key y. Decryption with receiver’s private key y. Once encrypted, sender cannot decrypt the ciphertext; does not have receiver’s private key Plaintext Encryption Ciphertext Receiver’s Public Key Decryption Plaintext Receiver’s Private Key
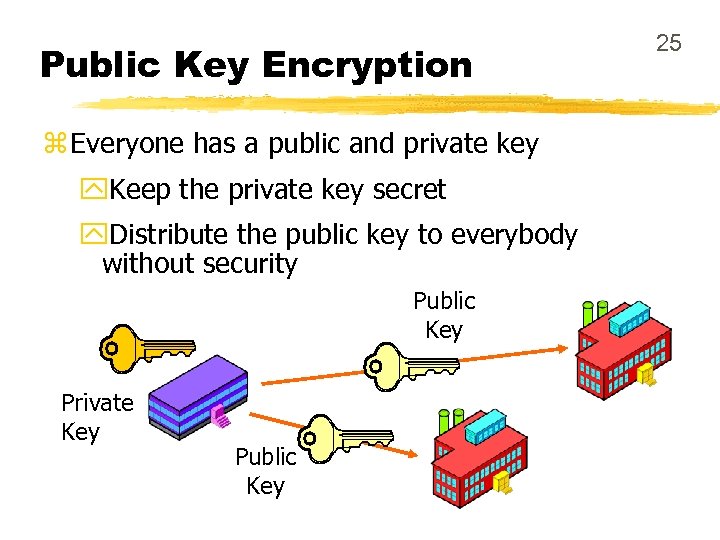 Public Key Encryption z Everyone has a public and private key y. Keep the private key secret y. Distribute the public key to everybody without security Public Key Private Key Public Key 25
Public Key Encryption z Everyone has a public and private key y. Keep the private key secret y. Distribute the public key to everybody without security Public Key Private Key Public Key 25
 Public Key Encryption 26 z Then anyone can encrypt messages to you using your public key z But only you can decrypt the messages Encryption Private Key Public Key
Public Key Encryption 26 z Then anyone can encrypt messages to you using your public key z But only you can decrypt the messages Encryption Private Key Public Key
 Public Key Encryption 27 z Four Keys Needed for Two-Way Communication y. Encrypt with receiver’s public key y. Decrypt with sender’s private key A B’s Pub Key B’s Priv Key A’s Pub Key B
Public Key Encryption 27 z Four Keys Needed for Two-Way Communication y. Encrypt with receiver’s public key y. Decrypt with sender’s private key A B’s Pub Key B’s Priv Key A’s Pub Key B
 Public Key Encryption 28 z Four Keys Needed for Two-Way Communication y. Never refer to public and private keys without saying to whose public or private key you are referring A B’s Pub Key B’s Priv Key A’s Pub Key B
Public Key Encryption 28 z Four Keys Needed for Two-Way Communication y. Never refer to public and private keys without saying to whose public or private key you are referring A B’s Pub Key B’s Priv Key A’s Pub Key B
 Public Key Encryption 29 z Unfortunately, highly processing-intensive y 100 times slower than symmetric key encryption y. So can only encrypt small messages y. Also, often can only encrypt messages about the size of the public key (typically a few thousand bits because of limitations in the algorithms) New
Public Key Encryption 29 z Unfortunately, highly processing-intensive y 100 times slower than symmetric key encryption y. So can only encrypt small messages y. Also, often can only encrypt messages about the size of the public key (typically a few thousand bits because of limitations in the algorithms) New
 Combining Public, Symmetric Key 30 z Symmetric Key Encryption and Public Key Encryption are Complementary, not Competitors z Often, partners first communicate with public key encryption y. Including initial authentication B A Public Key Authentication
Combining Public, Symmetric Key 30 z Symmetric Key Encryption and Public Key Encryption are Complementary, not Competitors z Often, partners first communicate with public key encryption y. Including initial authentication B A Public Key Authentication
 Combining Public, Symmetric Key 31 z Then one sides generates a symmetric key y. Encrypts symmetric key with partner’s public key, sends to partner y. Now, both sides have the symmetric key A Public Key Encryption Symmetric Session Key B
Combining Public, Symmetric Key 31 z Then one sides generates a symmetric key y. Encrypts symmetric key with partner’s public key, sends to partner y. Now, both sides have the symmetric key A Public Key Encryption Symmetric Session Key B
 Combining Public, Symmetric Key 32 z Afterward, both sides communicate with the symmetric key z This symmetric “session key” is good only for this session--single flow of communications A Symmetric Session Key B
Combining Public, Symmetric Key 32 z Afterward, both sides communicate with the symmetric key z This symmetric “session key” is good only for this session--single flow of communications A Symmetric Session Key B
 Public Key Algorithms 33 z Public Key Encryption is a Method Category y. Must Use a Specific Public Key Algorithm z RSA y. Most widely used public key algorithm y. Patented, but public domain in October 2000 z Elliptical Curve Cryptosystem (ECC) y. Can use smaller keys than RSA with same degree of protection y. Faster than RSA
Public Key Algorithms 33 z Public Key Encryption is a Method Category y. Must Use a Specific Public Key Algorithm z RSA y. Most widely used public key algorithm y. Patented, but public domain in October 2000 z Elliptical Curve Cryptosystem (ECC) y. Can use smaller keys than RSA with same degree of protection y. Faster than RSA
 Authentication
Authentication
 Confidentiality versus Authentication z Confidentiality (Privacy) y. Interceptors cannot read messages z Authentication: proving the sender’s identity y. The Problem of Impostors y. Uses encryption y. So encryption is not only for confidentiality! 35
Confidentiality versus Authentication z Confidentiality (Privacy) y. Interceptors cannot read messages z Authentication: proving the sender’s identity y. The Problem of Impostors y. Uses encryption y. So encryption is not only for confidentiality! 35
 Authentication 36 z. Authentication methods: Passwords y. Short passwords are easy to guess with exhaustive search y. Passwords that are common words or repetitive letter combinations are even easier to guess y. Automated password cracking is very effective for weak passwords y. Users must be forced to pick long passwords containing case changes and numerals, such as Tri 6 Vial
Authentication 36 z. Authentication methods: Passwords y. Short passwords are easy to guess with exhaustive search y. Passwords that are common words or repetitive letter combinations are even easier to guess y. Automated password cracking is very effective for weak passwords y. Users must be forced to pick long passwords containing case changes and numerals, such as Tri 6 Vial
 Authentication z Authentication methods y. Biometrics x. Fingerprint analysis, iris analysis, etc. x. New and not standardized y. Authentication Card x. Push into slot of a machine x. Also must give password usually y. Public Key Authentication x. Prove that sender holds their private key, which only they should know 37
Authentication z Authentication methods y. Biometrics x. Fingerprint analysis, iris analysis, etc. x. New and not standardized y. Authentication Card x. Push into slot of a machine x. Also must give password usually y. Public Key Authentication x. Prove that sender holds their private key, which only they should know 37
 38 Authentication z Verifier is the party who wishes the other party to authenticate themselves z Applicant is the other party, which wishes to prove its identity Can We Talk? Applicant Prove Your Identity Verifier
38 Authentication z Verifier is the party who wishes the other party to authenticate themselves z Applicant is the other party, which wishes to prove its identity Can We Talk? Applicant Prove Your Identity Verifier
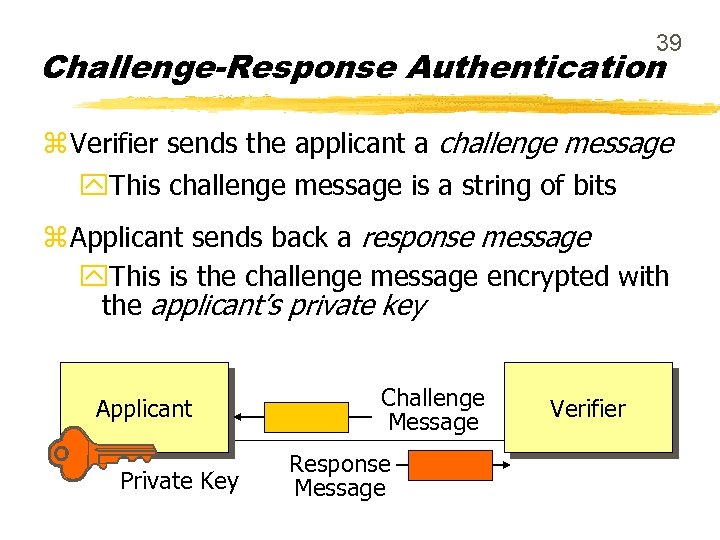 39 Challenge-Response Authentication z Verifier sends the applicant a challenge message y. This challenge message is a string of bits z Applicant sends back a response message y. This is the challenge message encrypted with the applicant’s private key Applicant Private Key Challenge Message Response Message Verifier
39 Challenge-Response Authentication z Verifier sends the applicant a challenge message y. This challenge message is a string of bits z Applicant sends back a response message y. This is the challenge message encrypted with the applicant’s private key Applicant Private Key Challenge Message Response Message Verifier
 40 Challenge-Response Authentication z Verifier decrypts the response message with the true party’s public key y. If matches the challenge message, was encrypted with the true party’s private key, which only the true party should know y. Applicant is authenticated Challenge Message Response Message Applicant Verifier
40 Challenge-Response Authentication z Verifier decrypts the response message with the true party’s public key y. If matches the challenge message, was encrypted with the true party’s private key, which only the true party should know y. Applicant is authenticated Challenge Message Response Message Applicant Verifier
 Frequency of Authentication 41 z Challenge-Response Authentication y. Only done initially y. Or done at most a few times during a session z Digital Signature Authentication (next) y. Provides authentication for every message y. Called message-by-message authentication y. Also provides message integrity—proof that the message has not been changed en route
Frequency of Authentication 41 z Challenge-Response Authentication y. Only done initially y. Or done at most a few times during a session z Digital Signature Authentication (next) y. Provides authentication for every message y. Called message-by-message authentication y. Also provides message integrity—proof that the message has not been changed en route
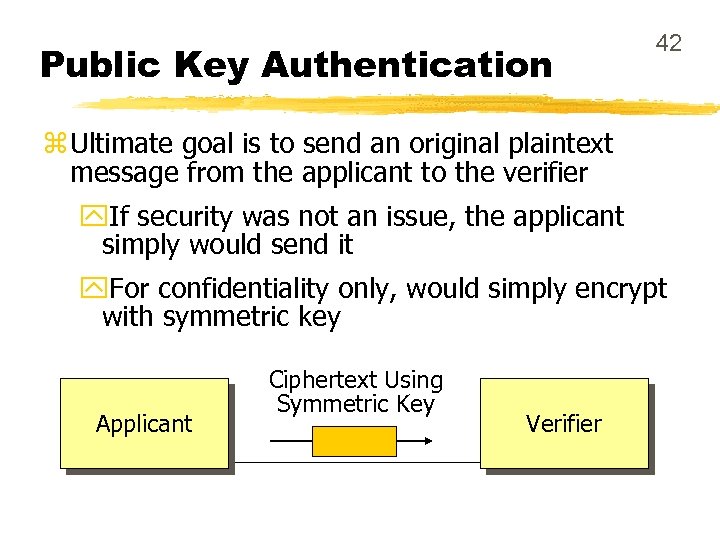 Public Key Authentication 42 z Ultimate goal is to send an original plaintext message from the applicant to the verifier y. If security was not an issue, the applicant simply would send it y. For confidentiality only, would simply encrypt with symmetric key Applicant Ciphertext Using Symmetric Key Verifier
Public Key Authentication 42 z Ultimate goal is to send an original plaintext message from the applicant to the verifier y. If security was not an issue, the applicant simply would send it y. For confidentiality only, would simply encrypt with symmetric key Applicant Ciphertext Using Symmetric Key Verifier
 Public Key Authentication 43 z For authentication, also send a digital signature with each packet z First create a message digest (MD) y. A small binary string calculated on the basis of all of the bits in the message Message Calculation Message Digest
Public Key Authentication 43 z For authentication, also send a digital signature with each packet z First create a message digest (MD) y. A small binary string calculated on the basis of all of the bits in the message Message Calculation Message Digest
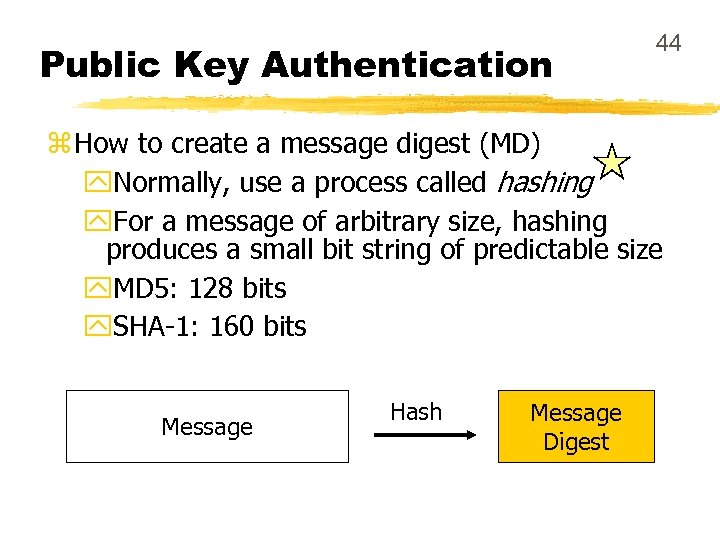 Public Key Authentication 44 z How to create a message digest (MD) y. Normally, use a process called hashing y. For a message of arbitrary size, hashing produces a small bit string of predictable size y. MD 5: 128 bits y. SHA-1: 160 bits Message Hash Message Digest
Public Key Authentication 44 z How to create a message digest (MD) y. Normally, use a process called hashing y. For a message of arbitrary size, hashing produces a small bit string of predictable size y. MD 5: 128 bits y. SHA-1: 160 bits Message Hash Message Digest
 Public Key Authentication z Hashing y. Hashing is not reversible y. Cannot get back original message if you know its hash y. Just done to produce something small enough (message digest) to encrypt with public key encryption Message Digest 45
Public Key Authentication z Hashing y. Hashing is not reversible y. Cannot get back original message if you know its hash y. Just done to produce something small enough (message digest) to encrypt with public key encryption Message Digest 45
 Public Key Authentication z Next create a digital signature y. Encrypt the message digest with sender’s private key, which only the sender should be able to do y. Also called signing the message digest with the sender’s private key Message Digest Encrypt with Sender’s Private Key Digital Signature 46
Public Key Authentication z Next create a digital signature y. Encrypt the message digest with sender’s private key, which only the sender should be able to do y. Also called signing the message digest with the sender’s private key Message Digest Encrypt with Sender’s Private Key Digital Signature 46
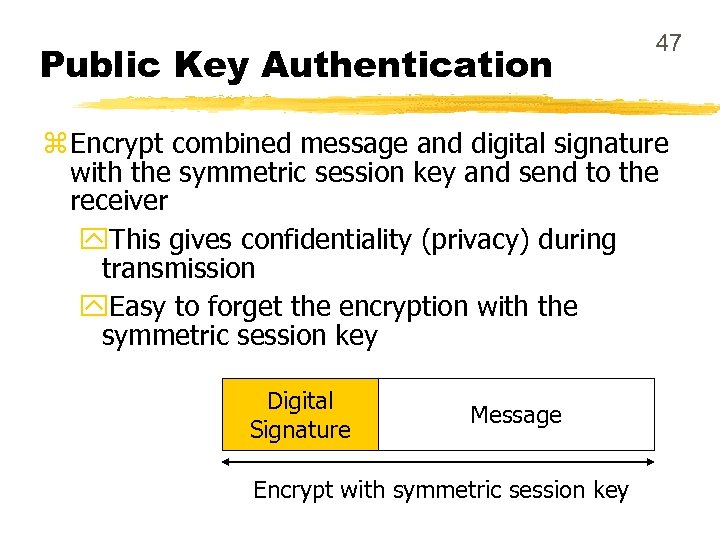 Public Key Authentication 47 z Encrypt combined message and digital signature with the symmetric session key and send to the receiver y. This gives confidentiality (privacy) during transmission y. Easy to forget the encryption with the symmetric session key Digital Signature Message Encrypt with symmetric session key
Public Key Authentication 47 z Encrypt combined message and digital signature with the symmetric session key and send to the receiver y. This gives confidentiality (privacy) during transmission y. Easy to forget the encryption with the symmetric session key Digital Signature Message Encrypt with symmetric session key
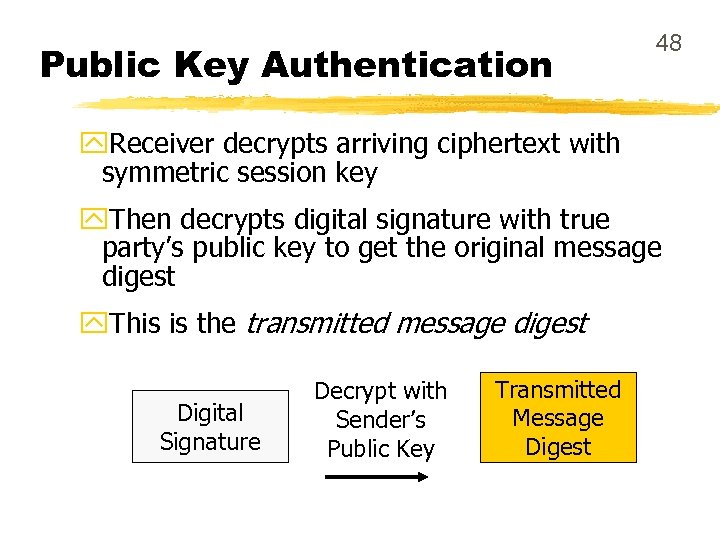 Public Key Authentication 48 y. Receiver decrypts arriving ciphertext with symmetric session key y. Then decrypts digital signature with true party’s public key to get the original message digest y. This is the transmitted message digest Digital Signature Decrypt with Sender’s Public Key Transmitted Message Digest
Public Key Authentication 48 y. Receiver decrypts arriving ciphertext with symmetric session key y. Then decrypts digital signature with true party’s public key to get the original message digest y. This is the transmitted message digest Digital Signature Decrypt with Sender’s Public Key Transmitted Message Digest
 Public Key Authentication 49 y. Then decrypts digital signature with true party’s public key to get the original message digest (transmitted message digest) y. Receiver then hashes the original plaintext, just as the sender did (computed message digest) Message Digest from Digital Signature Message Digest Computed from Original Plaintext
Public Key Authentication 49 y. Then decrypts digital signature with true party’s public key to get the original message digest (transmitted message digest) y. Receiver then hashes the original plaintext, just as the sender did (computed message digest) Message Digest from Digital Signature Message Digest Computed from Original Plaintext
 Public Key Authentication 50 z Digital Signature also Provides a Second Benefit: Message Integrity y. Proof that the message has not been altered en route y. If message has been changed by error or by an attacker, message digests will not match Message Digest from Digital Signature Message Digest Computed from Original Plaintext
Public Key Authentication 50 z Digital Signature also Provides a Second Benefit: Message Integrity y. Proof that the message has not been altered en route y. If message has been changed by error or by an attacker, message digests will not match Message Digest from Digital Signature Message Digest Computed from Original Plaintext
 Digital Certificates Public Key Deception Digital Certificates Certificate Authorities Public Key Infrastructures (PKIs)
Digital Certificates Public Key Deception Digital Certificates Certificate Authorities Public Key Infrastructures (PKIs)
 Public Key Deception 52 z Impostor Claims to be a True Party y. True party has a public and private key y. Impostor also has a public and private key z Impostor sends impostor’s own public key to the verifier y. Says, “This is the true party’s public key” y. This is the critical step in the deception y. Impostor would be “authenticated” using any public key authentication method
Public Key Deception 52 z Impostor Claims to be a True Party y. True party has a public and private key y. Impostor also has a public and private key z Impostor sends impostor’s own public key to the verifier y. Says, “This is the true party’s public key” y. This is the critical step in the deception y. Impostor would be “authenticated” using any public key authentication method
 53 Digital Certificates z Created by a Certificate Authority y. Certificate authority is the trusted third party y. However, not regulated today Digital Certificate Authenticated Party Certificate Authority
53 Digital Certificates z Created by a Certificate Authority y. Certificate authority is the trusted third party y. However, not regulated today Digital Certificate Authenticated Party Certificate Authority
 Digital Certificates z Assert that a true party (named) has the public key contained in the digital certificate y. Provides a name-public key pair x. To prevent public key deception y. Fields and content are standardized by the ITU-T X. 509 Standard y. Does not vouch for integrity of the named party—only their public Key 54
Digital Certificates z Assert that a true party (named) has the public key contained in the digital certificate y. Provides a name-public key pair x. To prevent public key deception y. Fields and content are standardized by the ITU-T X. 509 Standard y. Does not vouch for integrity of the named party—only their public Key 54
 Digital Certificates 55 z Certificate authorities may revoke digital certificates y. Revoked certificate ID numbers are placed in a certificate revocation list (CRL) y. Verifier must check with the certificate authority to determine if a digital certificate is on the CRL z Without the CRL check, digital certificates do not support authentication
Digital Certificates 55 z Certificate authorities may revoke digital certificates y. Revoked certificate ID numbers are placed in a certificate revocation list (CRL) y. Verifier must check with the certificate authority to determine if a digital certificate is on the CRL z Without the CRL check, digital certificates do not support authentication
 Public Key Infrastructures (PKIs) 56 z To use public key methods, an organization must establish a comprehensive Public Key Infrastructure (PKI) y. A PKI automates most aspects of using public key encryption and authentication y. Uses a PKI Server
Public Key Infrastructures (PKIs) 56 z To use public key methods, an organization must establish a comprehensive Public Key Infrastructure (PKI) y. A PKI automates most aspects of using public key encryption and authentication y. Uses a PKI Server
 57 PKIs z PKI Server Creates Public Key-Private Key Pairs y. Distributes private keys to applicants securely y. Often, private keys are embedded in delivered software Private Key PKI Server
57 PKIs z PKI Server Creates Public Key-Private Key Pairs y. Distributes private keys to applicants securely y. Often, private keys are embedded in delivered software Private Key PKI Server
 58 PKIs z PKI Server Provides CRL Checks y. Distributes digital certificates to verifiers y. Checks certificate revocation list before sending digital certificates Digital Certificate PKI Server
58 PKIs z PKI Server Provides CRL Checks y. Distributes digital certificates to verifiers y. Checks certificate revocation list before sending digital certificates Digital Certificate PKI Server
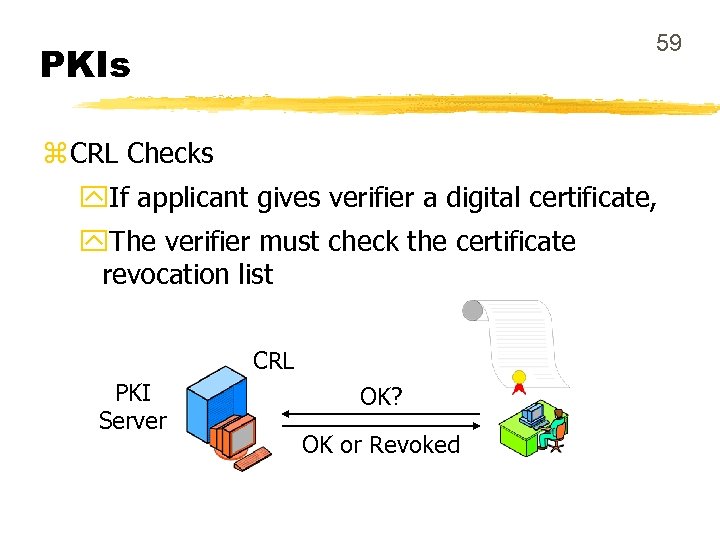 59 PKIs z CRL Checks y. If applicant gives verifier a digital certificate, y. The verifier must check the certificate revocation list CRL PKI Server OK? OK or Revoked
59 PKIs z CRL Checks y. If applicant gives verifier a digital certificate, y. The verifier must check the certificate revocation list CRL PKI Server OK? OK or Revoked
 Integrated Security Systems
Integrated Security Systems
 Integrated Security System z When two parties communicate … y. Their software usually handles the details y. First, negotiate security methods y. Then, authenticate one another y. Then, exchange symmetric session key y. Then can communicate securely using symmetric session key and message-bymessage authentication 61
Integrated Security System z When two parties communicate … y. Their software usually handles the details y. First, negotiate security methods y. Then, authenticate one another y. Then, exchange symmetric session key y. Then can communicate securely using symmetric session key and message-bymessage authentication 61
 SSL Integrated Security System 62 z SSL y. Secure Sockets Layer y. Developed by Netscape y. Protects at the transport layer; protects any SSL-enabled application program y. Supported by almost all browsers y. Almost universal in Web financial transactions y. Netscape gave IETF control over SSL y. IETF renamed it Transport Layer Security
SSL Integrated Security System 62 z SSL y. Secure Sockets Layer y. Developed by Netscape y. Protects at the transport layer; protects any SSL-enabled application program y. Supported by almost all browsers y. Almost universal in Web financial transactions y. Netscape gave IETF control over SSL y. IETF renamed it Transport Layer Security
 SSL Operation z SSL ISS Process y. Two sides negotiate security parameters y. Webserver authenticates itself y. Browser may authenticate itself but rarely does y. Browser generates a random symmetric session key, sends to webserver y. Adds a digital signature and encrypts all messages with the symmetric key 63
SSL Operation z SSL ISS Process y. Two sides negotiate security parameters y. Webserver authenticates itself y. Browser may authenticate itself but rarely does y. Browser generates a random symmetric session key, sends to webserver y. Adds a digital signature and encrypts all messages with the symmetric key 63
 Other ISSs z SSL is merely an example integrated security system z Many other ISSs exist y. IPsec (Chapter 9 and Module F) y. PPTP and L 2 TP (Module F) y. Etc. 64
Other ISSs z SSL is merely an example integrated security system z Many other ISSs exist y. IPsec (Chapter 9 and Module F) y. PPTP and L 2 TP (Module F) y. Etc. 64
 Other Security Issues Multi-Layer Security Firewalls Total Security Intrusion Detection Trust
Other Security Issues Multi-Layer Security Firewalls Total Security Intrusion Detection Trust
 Multi-Layer Security z Security Can be Applied at Multiple Layers Simultaneously y. Application layer security for database, email, etc. y. Transport layer: SSL y. Internet layer: IPsec (Chapter 9, Module F) y. Data link layer: PPTP, L 2 TP (Module F) y. Physical layer: locks 66
Multi-Layer Security z Security Can be Applied at Multiple Layers Simultaneously y. Application layer security for database, email, etc. y. Transport layer: SSL y. Internet layer: IPsec (Chapter 9, Module F) y. Data link layer: PPTP, L 2 TP (Module F) y. Physical layer: locks 66
 Multi-Layer Security 67 z Applying security at 2 or more layers is good y. If security is broken at one layer, the communication will still be secure z However, y. Security slows down processing y. Multi-Layer security slows down processing at each layer
Multi-Layer Security 67 z Applying security at 2 or more layers is good y. If security is broken at one layer, the communication will still be secure z However, y. Security slows down processing y. Multi-Layer security slows down processing at each layer
 68 Firewalls z Firewall sits between the corporate network and the Internet y. Prevents unauthorized access from the Internet y. Facilitates internal users’ access to the Internet Firewall OK No Access only if Authenticated
68 Firewalls z Firewall sits between the corporate network and the Internet y. Prevents unauthorized access from the Internet y. Facilitates internal users’ access to the Internet Firewall OK No Access only if Authenticated
 69 Firewalls z Packet Filter Firewalls y. Examine each incoming IP packet y. Examine IP and TCP header fields y. If bad behavior is detected, reject the packet y. Usually no sense of previous communication: analyzes each packet in isolation IP Firewall IP Packet
69 Firewalls z Packet Filter Firewalls y. Examine each incoming IP packet y. Examine IP and TCP header fields y. If bad behavior is detected, reject the packet y. Usually no sense of previous communication: analyzes each packet in isolation IP Firewall IP Packet
 Firewalls z Application (Proxy) Firewalls y. Filter based on application behavior x. Viruses, extensions of files transferred, etc. y. Do not examine packets in isolation: use history x. In HTTP, do not accept a response unless an HTTP request has just gone out to that site Application 70
Firewalls z Application (Proxy) Firewalls y. Filter based on application behavior x. Viruses, extensions of files transferred, etc. y. Do not examine packets in isolation: use history x. In HTTP, do not accept a response unless an HTTP request has just gone out to that site Application 70
 Firewalls 71 z Application (Proxy) Firewall y. Hides internal internet addresses through Network Address Translation y. Accepts packet from internal host; packet has internal host’s IP address Packet With Internal IP Address
Firewalls 71 z Application (Proxy) Firewall y. Hides internal internet addresses through Network Address Translation y. Accepts packet from internal host; packet has internal host’s IP address Packet With Internal IP Address
 72 Firewalls z Application (Proxy) Firewalls y. Proxy program replaces internal IP address with another IP address, sends to external host Packet With Another IP Address
72 Firewalls z Application (Proxy) Firewalls y. Proxy program replaces internal IP address with another IP address, sends to external host Packet With Another IP Address
 Firewalls z Application (Proxy) Firewalls y. Proxy server receives returning IP packet to the other IP address y. Passes it on to the internal host 73
Firewalls z Application (Proxy) Firewalls y. Proxy server receives returning IP packet to the other IP address y. Passes it on to the internal host 73
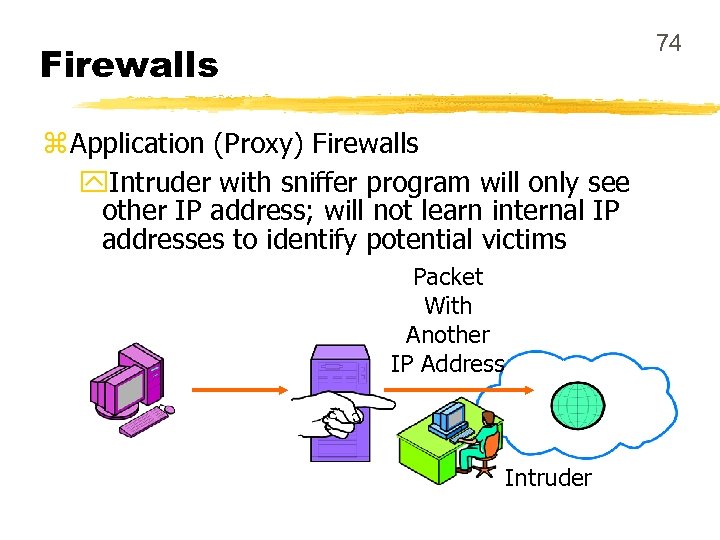 74 Firewalls z Application (Proxy) Firewalls y. Intruder with sniffer program will only see other IP address; will not learn internal IP addresses to identify potential victims Packet With Another IP Address Intruder
74 Firewalls z Application (Proxy) Firewalls y. Intruder with sniffer program will only see other IP address; will not learn internal IP addresses to identify potential victims Packet With Another IP Address Intruder
 Firewalls z Application Firewalls y. Need a separate program (proxy) for each application y. Not all applications have rules that allow filtering 75
Firewalls z Application Firewalls y. Need a separate program (proxy) for each application y. Not all applications have rules that allow filtering 75
 Total Security z Network Security is Only Part z Server Security y. Occasionally, weakness are discovered in server operating systems y. Hackers use these known security weaknesses to hack into or crash servers y. Companies must install patches to fix these weaknesses; often fail to do so 76
Total Security z Network Security is Only Part z Server Security y. Occasionally, weakness are discovered in server operating systems y. Hackers use these known security weaknesses to hack into or crash servers y. Companies must install patches to fix these weaknesses; often fail to do so 76
 Total Security 77 z Client PC Security y. Known security weaknesses exist but patches are rarely downloaded y. Users often have no passwords or weak passwords on their computer y. Adversaries take over client PCs and can therefore take over control over SSL, other secure communication protocols
Total Security 77 z Client PC Security y. Known security weaknesses exist but patches are rarely downloaded y. Users often have no passwords or weak passwords on their computer y. Adversaries take over client PCs and can therefore take over control over SSL, other secure communication protocols
 Total Security z Managing Users y. Often violate security procedures, making technical security worthless y. Social engineering: attacker tricks user into violating security procedures 78
Total Security z Managing Users y. Often violate security procedures, making technical security worthless y. Social engineering: attacker tricks user into violating security procedures 78
 Intrusion Detection 79 z Intrusion detection software to detect and report intrusions as they are occurring z Needed y. Lets organization stop intruders so that intruders do not have unlimited time to probe for weaknesses y. Helps organization assess security threats y. Audit logs list where intruder has been: vital in legal prosecution
Intrusion Detection 79 z Intrusion detection software to detect and report intrusions as they are occurring z Needed y. Lets organization stop intruders so that intruders do not have unlimited time to probe for weaknesses y. Helps organization assess security threats y. Audit logs list where intruder has been: vital in legal prosecution
 80 Trust z System A may trust System B y. Not check closely for security problems y. This reduces security processing costs y. If trusted system is taken over, disaster x. Hacker can exploit systems that trust it B A Trust C Trust
80 Trust z System A may trust System B y. Not check closely for security problems y. This reduces security processing costs y. If trusted system is taken over, disaster x. Hacker can exploit systems that trust it B A Trust C Trust


