1dc0fc7c43beb4ecd67ca7eff06c639b.ppt
- Количество слайдов: 30

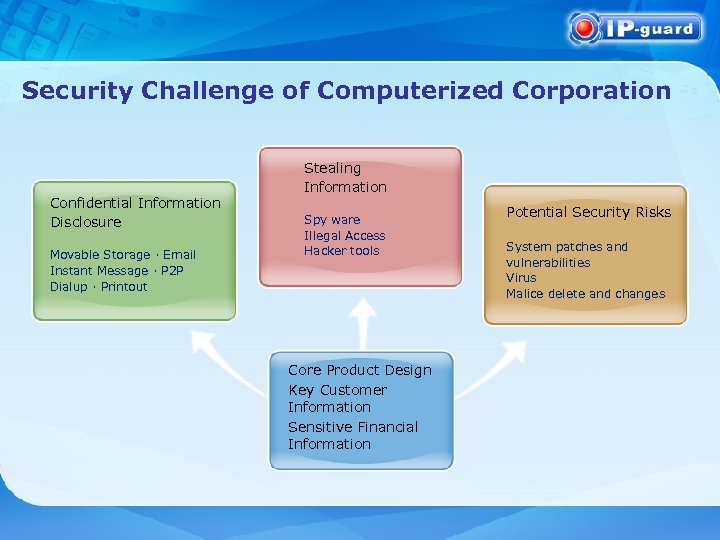 Security Challenge of Computerized Corporation Confidential Information Disclosure Movable Storage · Email Instant Message · P 2 P Dialup · Printout Stealing Information Spy ware Illegal Access Hacker tools Core Product Design Key Customer Information Sensitive Financial Information Potential Security Risks System patches and vulnerabilities Virus Malice delete and changes
Security Challenge of Computerized Corporation Confidential Information Disclosure Movable Storage · Email Instant Message · P 2 P Dialup · Printout Stealing Information Spy ware Illegal Access Hacker tools Core Product Design Key Customer Information Sensitive Financial Information Potential Security Risks System patches and vulnerabilities Virus Malice delete and changes
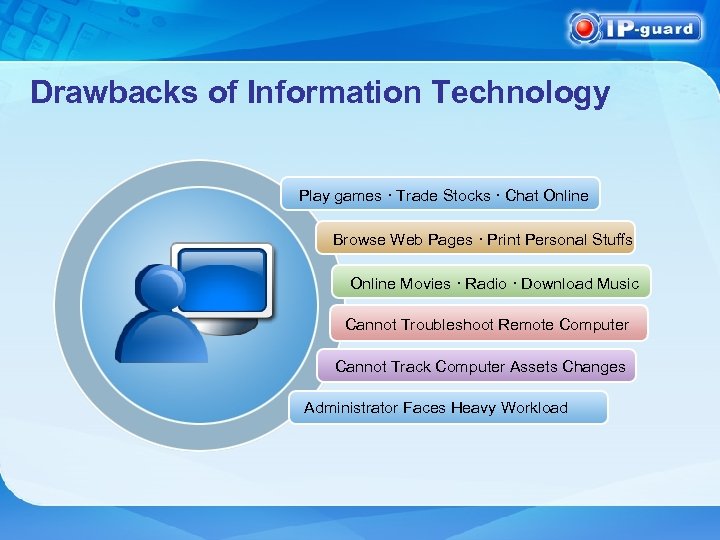 Drawbacks of Information Technology Play games · Trade Stocks · Chat Online Browse Web Pages · Print Personal Stuffs Online Movies · Radio · Download Music Cannot Troubleshoot Remote Computer Cannot Track Computer Assets Changes Administrator Faces Heavy Workload
Drawbacks of Information Technology Play games · Trade Stocks · Chat Online Browse Web Pages · Print Personal Stuffs Online Movies · Radio · Download Music Cannot Troubleshoot Remote Computer Cannot Track Computer Assets Changes Administrator Faces Heavy Workload
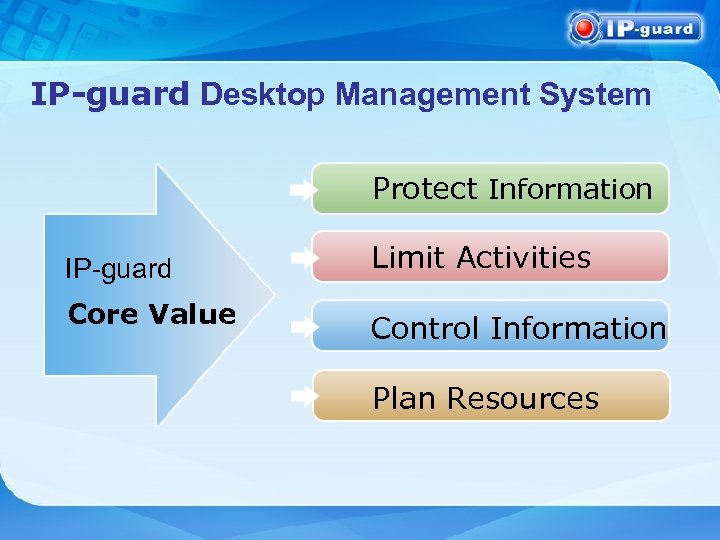 IP-guard Desktop Management System Protect Information IP-guard Core Value Limit Activities Control Information Plan Resources
IP-guard Desktop Management System Protect Information IP-guard Core Value Limit Activities Control Information Plan Resources
 Different Modules Suit for Different Corporations Needs Document Operation Management Printing Management Network Control Application Management Website Management Instant Message Management Screen Snapshots E-Mail Management Bandwidth Management Asset Management Removable Storage Management Device Management Remote Maintenance
Different Modules Suit for Different Corporations Needs Document Operation Management Printing Management Network Control Application Management Website Management Instant Message Management Screen Snapshots E-Mail Management Bandwidth Management Asset Management Removable Storage Management Device Management Remote Maintenance
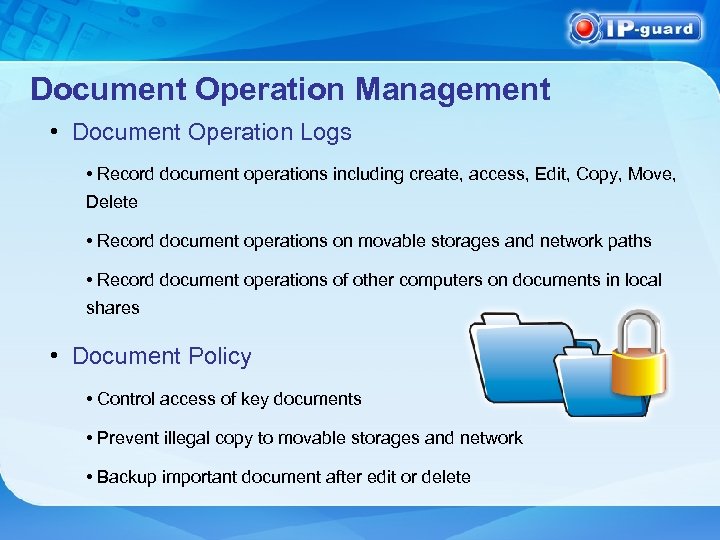 Document Operation Management • Document Operation Logs • Record document operations including create, access, Edit, Copy, Move, Delete • Record document operations on movable storages and network paths • Record document operations of other computers on documents in local shares • Document Policy • Control access of key documents • Prevent illegal copy to movable storages and network • Backup important document after edit or delete
Document Operation Management • Document Operation Logs • Record document operations including create, access, Edit, Copy, Move, Delete • Record document operations on movable storages and network paths • Record document operations of other computers on documents in local shares • Document Policy • Control access of key documents • Prevent illegal copy to movable storages and network • Backup important document after edit or delete
 Removable Storage Management • Removable Storage device File/Full Disk Encryption / Decryption • Removable Storage devices Authorization uses • only the authorized devices can encrypt and decrypt the files • computers without authorization cannot open the encrypted file properly
Removable Storage Management • Removable Storage device File/Full Disk Encryption / Decryption • Removable Storage devices Authorization uses • only the authorized devices can encrypt and decrypt the files • computers without authorization cannot open the encrypted file properly
 Application Management • Application logs and statistic • Record application startup and shut down • Record window changes and title changes to track computer usage • Application statistic to estimate staffs efficiency • Application Policy • Stop games and chat programs • Stop malice programs
Application Management • Application logs and statistic • Record application startup and shut down • Record window changes and title changes to track computer usage • Application statistic to estimate staffs efficiency • Application Policy • Stop games and chat programs • Stop malice programs
 Website Management • Web Statistic • Summarized types of website visited to estimate Internet usage • Web Logs • Record website URL and title in detail • Web Policy • Block websites irrelevant to work • Block websites with harmful messages
Website Management • Web Statistic • Summarized types of website visited to estimate Internet usage • Web Logs • Record website URL and title in detail • Web Policy • Block websites irrelevant to work • Block websites with harmful messages
 EMail Management • EMail Record • Record normal email, webmail, exchange, and Lotus Notes mail. • Record complete email message and attachments • EMail Policy • Limit sender accounts • Block specific recipients • Block email with attachment of specific file name or exceed certain size
EMail Management • EMail Record • Record normal email, webmail, exchange, and Lotus Notes mail. • Record complete email message and attachments • EMail Policy • Limit sender accounts • Block specific recipients • Block email with attachment of specific file name or exceed certain size
 Instant Message Management • Instant Message Record • IM File Policy • Limit outgoing file name or file type • Limit outgoing file size • Backup outgoing files Instant message • Record full content of the IM session
Instant Message Management • Instant Message Record • IM File Policy • Limit outgoing file name or file type • Limit outgoing file size • Backup outgoing files Instant message • Record full content of the IM session
 Printing Management • Print Logs • Record information on printing application, printer, user and document name • Record pages printed to estimate usage • Printing Policy • Block Illegal application from printing • Block printing on specific printer • Backup printed out document in JPEG format
Printing Management • Print Logs • Record information on printing application, printer, user and document name • Record pages printed to estimate usage • Printing Policy • Block Illegal application from printing • Block printing on specific printer • Backup printed out document in JPEG format
 Screen Snapshot • Real Time Monitoring • View agent screen in real time • Support multi-monitors • Multi-screen function to view several computer at one time • Snapshot History • Completely record screen history for future analyze • Set different snapshot frequency on different application to focus on some sensitive information • Optimized storage by compression
Screen Snapshot • Real Time Monitoring • View agent screen in real time • Support multi-monitors • Multi-screen function to view several computer at one time • Snapshot History • Completely record screen history for future analyze • Set different snapshot frequency on different application to focus on some sensitive information • Optimized storage by compression
 Device Management • Storage Control • Control usage of storage (Floppy· CD· USB· Movable storage· Memory card. . . ) • Communication Device Control • Control data transfer to external ports or devices (Serial port· Parallel port· MODEM· Infrared· Bluetooth· Direct connection· Dialup) • Other Device Control USB devices, Wireless card, or other new devices.
Device Management • Storage Control • Control usage of storage (Floppy· CD· USB· Movable storage· Memory card. . . ) • Communication Device Control • Control data transfer to external ports or devices (Serial port· Parallel port· MODEM· Infrared· Bluetooth· Direct connection· Dialup) • Other Device Control USB devices, Wireless card, or other new devices.
 Network Control • Network Communication Control • Provide firewall functions to control communication of specific address and port • Eliminate the use of specific port and communicate with unauthorized computers • IP/MAC Binding • Prevent users from changing network setting • Intrusion Detection • Scan the whole network and prevent illegal access to the network
Network Control • Network Communication Control • Provide firewall functions to control communication of specific address and port • Eliminate the use of specific port and communicate with unauthorized computers • IP/MAC Binding • Prevent users from changing network setting • Intrusion Detection • Scan the whole network and prevent illegal access to the network
 Bandwidth Management • Network Traffic Statistic • Show network traffic statistic by IP • Show network traffic statistic by ports • Analyze data in specific time zone • Network Traffic Policy • Assign different bandwidth to different IP and ports • Prevent BT,P 2 P,network media, and download tools to use up network resources
Bandwidth Management • Network Traffic Statistic • Show network traffic statistic by IP • Show network traffic statistic by ports • Analyze data in specific time zone • Network Traffic Policy • Assign different bandwidth to different IP and ports • Prevent BT,P 2 P,network media, and download tools to use up network resources
 Asset Management • Manage Hardware and Software • Complete hardware and software information • Detail asset change history • Self defined properties to additional information to the asset • Self defined asset to add non-computer assets for standardize management
Asset Management • Manage Hardware and Software • Complete hardware and software information • Detail asset change history • Self defined properties to additional information to the asset • Self defined asset to add non-computer assets for standardize management
 Remote Maintenance • Real Time Maintenance • View agents’ system messages in real time • Remote diagnostic agent’s problems and check system status • Remote Control • Easy assist users and demonstrate system operation to users • Remote File Transfer • Remote file transfer help administrators to collect and update files more efficiently
Remote Maintenance • Real Time Maintenance • View agents’ system messages in real time • Remote diagnostic agent’s problems and check system status • Remote Control • Easy assist users and demonstrate system operation to users • Remote File Transfer • Remote file transfer help administrators to collect and update files more efficiently
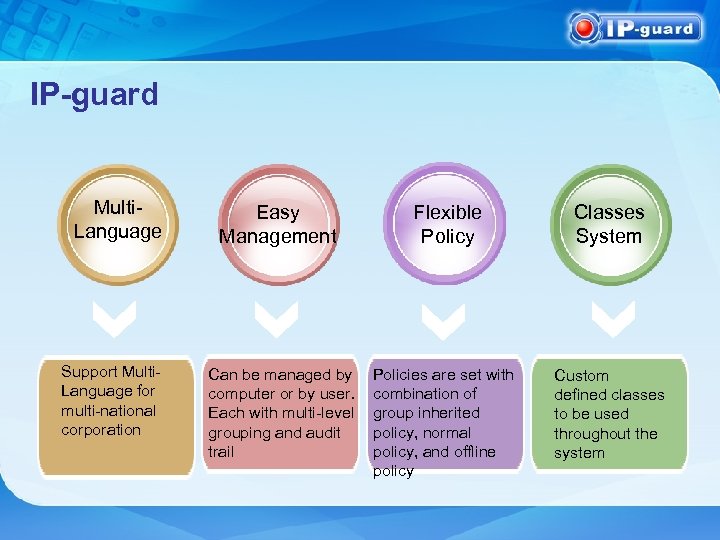 IP-guard Multi. Language Support Multi. Language for multi-national corporation Easy Management Flexible Policy Classes System Can be managed by computer or by user. Each with multi-level grouping and audit trail Policies are set with combination of group inherited policy, normal policy, and offline policy Custom defined classes to be used throughout the system
IP-guard Multi. Language Support Multi. Language for multi-national corporation Easy Management Flexible Policy Classes System Can be managed by computer or by user. Each with multi-level grouping and audit trail Policies are set with combination of group inherited policy, normal policy, and offline policy Custom defined classes to be used throughout the system
 Information Security Solution & Behavior Management Solution Confidential information such as source codes, chemical formulas, and design blue prints are saved in documents. Therefore, document security is the core of information security. Monitor and control computer usage of employees. Plan network resources accordingly to ensure company resources are effectively used.
Information Security Solution & Behavior Management Solution Confidential information such as source codes, chemical formulas, and design blue prints are saved in documents. Therefore, document security is the core of information security. Monitor and control computer usage of employees. Plan network resources accordingly to ensure company resources are effectively used.
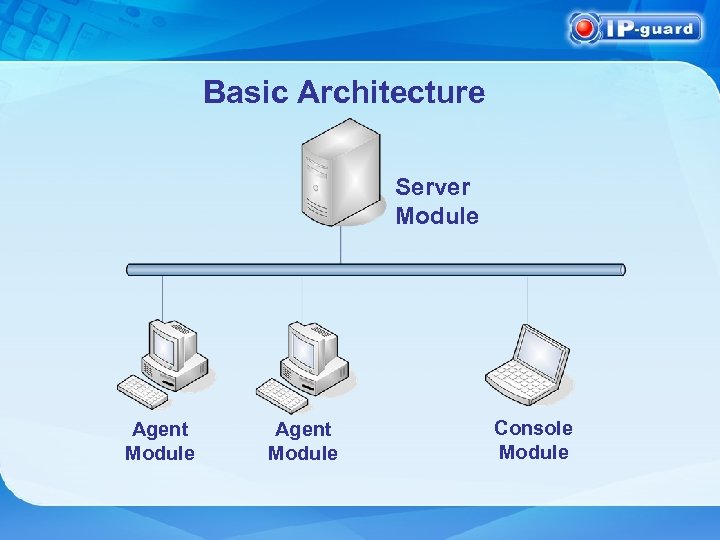 Basic Architecture Server Module Agent Module Console Module
Basic Architecture Server Module Agent Module Console Module
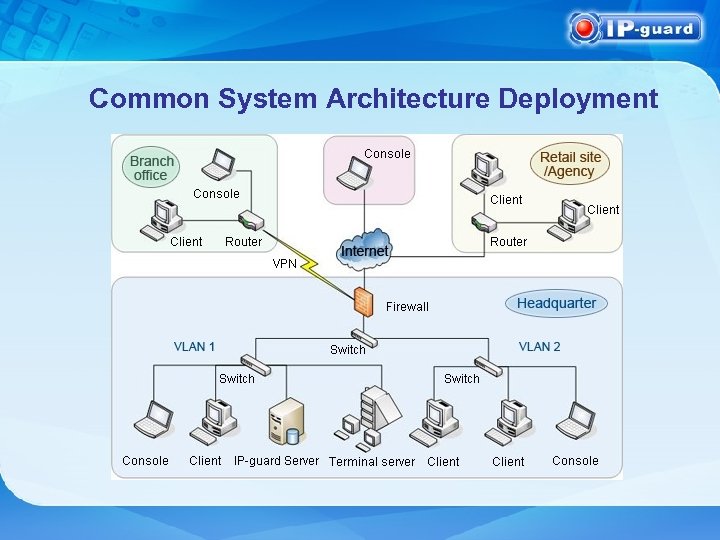 Common System Architecture Deployment
Common System Architecture Deployment
 Minimum Requirement Console Module Agent Module • • Pentium III 500 128 MB Memory 1 G HDD OS Win NT 4 Win 2000 / XP Win 2003 / Vista / Win 7 • • Pentium III 1 G 256 MB Memory 4 G HDD OS Win 2000 / XP Win 2003 / Vista / Win 7 Server Module • • Pentium 4 2 G 512 MB Memory 200 GB HDD OS Win 2000 SP 4 / XP SP 2 Win 2003 SP 1 / Win 2008 • Database SQL Server 2000 SP 4 / 2005 SP 1 / MSDE / 2005 /2008 R 2(Express)
Minimum Requirement Console Module Agent Module • • Pentium III 500 128 MB Memory 1 G HDD OS Win NT 4 Win 2000 / XP Win 2003 / Vista / Win 7 • • Pentium III 1 G 256 MB Memory 4 G HDD OS Win 2000 / XP Win 2003 / Vista / Win 7 Server Module • • Pentium 4 2 G 512 MB Memory 200 GB HDD OS Win 2000 SP 4 / XP SP 2 Win 2003 SP 1 / Win 2008 • Database SQL Server 2000 SP 4 / 2005 SP 1 / MSDE / 2005 /2008 R 2(Express)
 Major Clients in Government & Related Organization Independent Commission Against Corruption The Treasury The Government of the Hong Kong Special Administrative Region Hong Kong Jewellery and Jade Manufacturers Association
Major Clients in Government & Related Organization Independent Commission Against Corruption The Treasury The Government of the Hong Kong Special Administrative Region Hong Kong Jewellery and Jade Manufacturers Association
 Major Clients in Hong Kong
Major Clients in Hong Kong
 Major Clients in Hong Kong Defond Group John Manufacturing Ltd Nine Dragons Paper (Holdings) Limited IDT International Limited VTech Holdings Ltd Kowloon Engineering Ltd. China Aerospace International Holdings Ltd. GAM Hong Kong Limited NAM TAI ELECTRONIC & ELECTRICAL PRODUCTS LIMITED
Major Clients in Hong Kong Defond Group John Manufacturing Ltd Nine Dragons Paper (Holdings) Limited IDT International Limited VTech Holdings Ltd Kowloon Engineering Ltd. China Aerospace International Holdings Ltd. GAM Hong Kong Limited NAM TAI ELECTRONIC & ELECTRICAL PRODUCTS LIMITED
 Major Clients in China Mobile Ltd. China Telecom Corporation Limited China Unicom Petro China Company Limited Hangzhou Wahaha Group Co. , Ltd. China Aerospace Science and Technology Corporation (CASC)
Major Clients in China Mobile Ltd. China Telecom Corporation Limited China Unicom Petro China Company Limited Hangzhou Wahaha Group Co. , Ltd. China Aerospace Science and Technology Corporation (CASC)
 Major Clients in China Shandong Xinhua Pharmaceutical Co. , Ltd. Kao (China) Holding Company Ltd. LIBY Group Co. Ltd.
Major Clients in China Shandong Xinhua Pharmaceutical Co. , Ltd. Kao (China) Holding Company Ltd. LIBY Group Co. Ltd.
 Major Clients in China Shanghai Metersbonwe Fashion and Accessories Co. , Ltd Beyond Home Textile
Major Clients in China Shanghai Metersbonwe Fashion and Accessories Co. , Ltd Beyond Home Textile
 Thank you for your interest and support to our product Thank You!
Thank you for your interest and support to our product Thank You!


