0ce0c08c3ba99aca92bc62f86fa2c146.ppt
- Количество слайдов: 31

Security Basics

Agenda • • Properties of a secure communication Symmetric encryption Asymmetric encryption Public key encryption Digital Signatures Encryption in the network History 2/31 Groep T Leuven – Information department 2003 -2004 - Information management 2

Properties of a secure communication • Authentication (identity) –Who are you? • Authorization –What can you do ? • Accounting (active audit) –What did you do ? • Confidentiality –What can you see ? 3/31 Groep T Leuven – Information department • Integrity –Nothing has been modified • Non Repudiation –The sender cannot deny he has sent it • Anti Replay 2003 -2004 - Information management 3
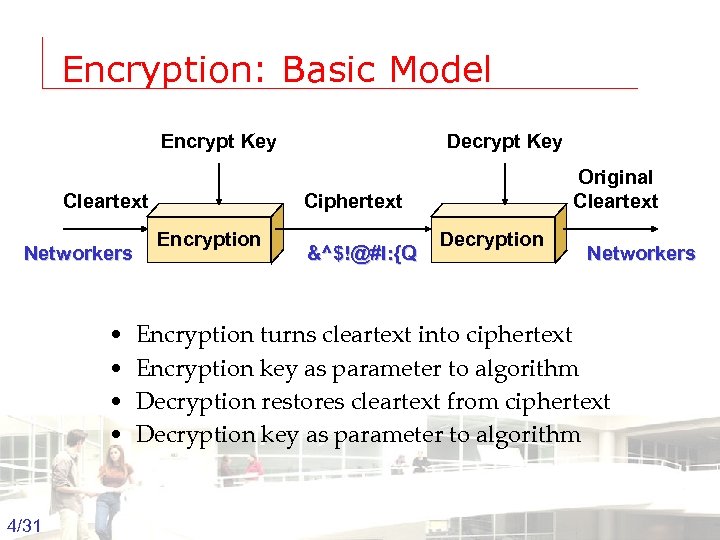
Encryption: Basic Model Encrypt Key Cleartext Networkers • • Decrypt Key Original Cleartext Ciphertext Encryption &^$!@#l: {Q Decryption Networkers Encryption turns cleartext into ciphertext Encryption key as parameter to algorithm Decryption restores cleartext from ciphertext Decryption key as parameter to algorithm 4/31 Groep T Leuven – Information department 2003 -2004 - Information management 4
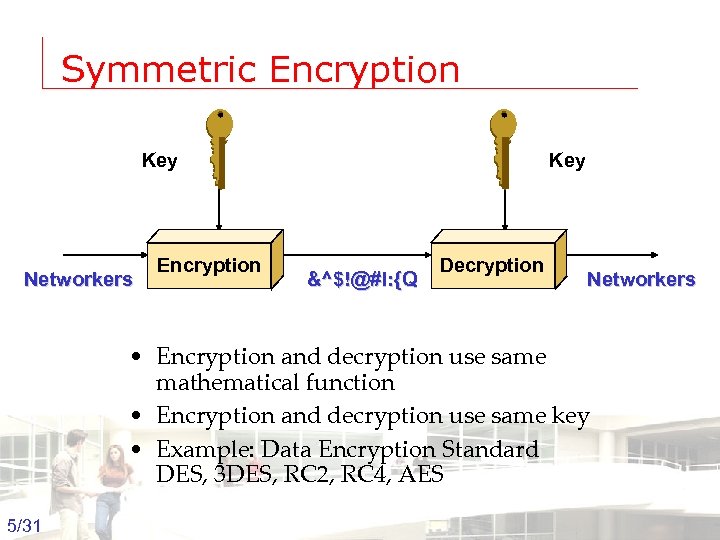
Symmetric Encryption Key Networkers Encryption Key &^$!@#l: {Q Decryption Networkers • Encryption and decryption use same mathematical function • Encryption and decryption use same key • Example: Data Encryption Standard DES, 3 DES, RC 2, RC 4, AES 5/31 Groep T Leuven – Information department 2003 -2004 - Information management 5
Challenges with Symmetric Encryption • Keys must be changed frequently to avoid analysis, limit risks • Shared keys must be generated and distributed securely • Multiple techniques to achieve this 6/31 Groep T Leuven – Information department 2003 -2004 - Information management 6
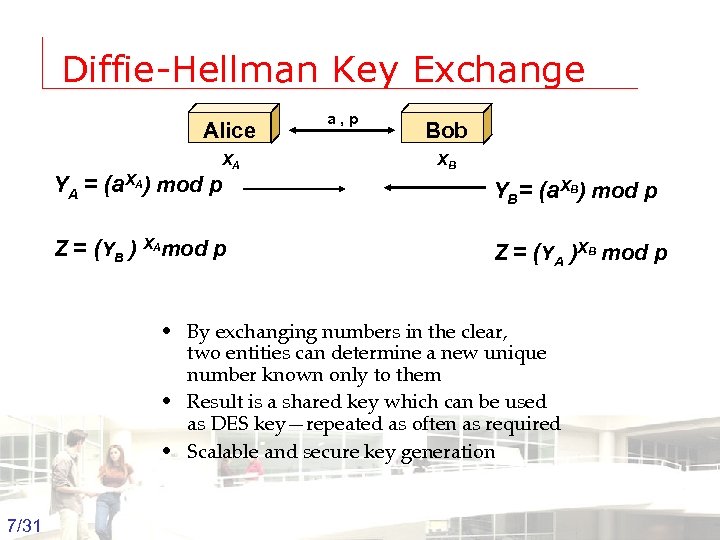
Diffie-Hellman Key Exchange Alice a, p XA YA = (a. XA) mod p Z = (YB ) XAmod p Bob XB YB= (a. XB) mod p Z = (YA )XB mod p • By exchanging numbers in the clear, two entities can determine a new unique number known only to them • Result is a shared key which can be used as DES key—repeated as often as required • Scalable and secure key generation 7/31 Groep T Leuven – Information department 2003 -2004 - Information management 7
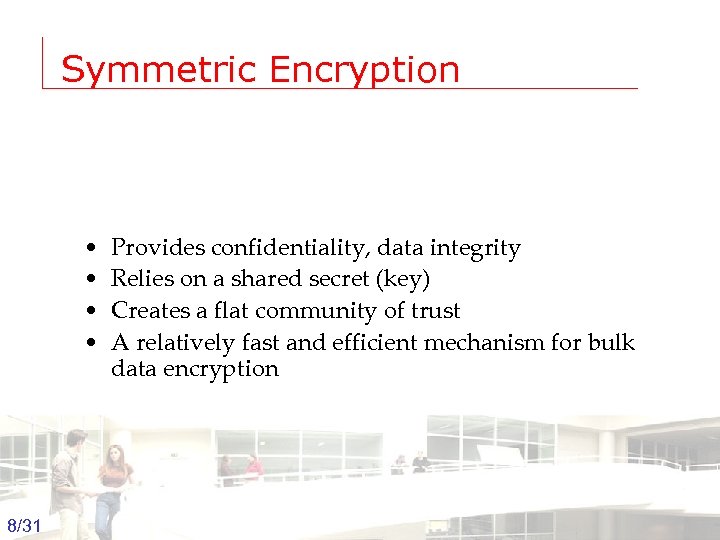
Symmetric Encryption • • Provides confidentiality, data integrity Relies on a shared secret (key) Creates a flat community of trust A relatively fast and efficient mechanism for bulk data encryption 8/31 Groep T Leuven – Information department 2003 -2004 - Information management 8
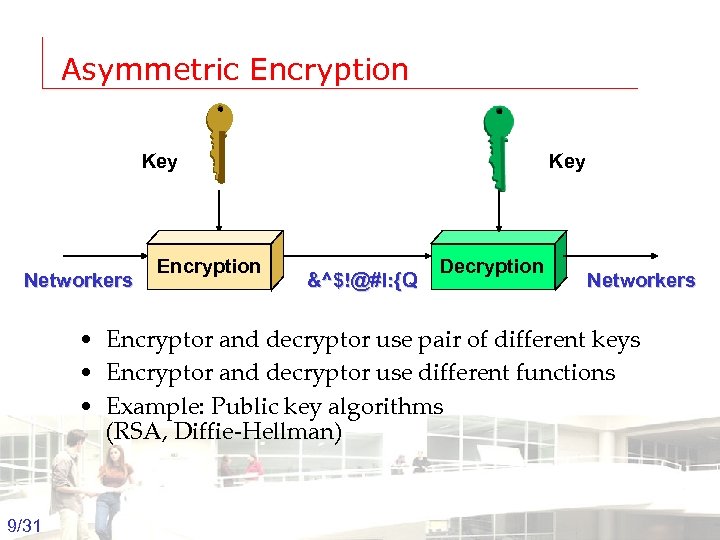
Asymmetric Encryption Key Networkers Encryption Key &^$!@#l: {Q Decryption Networkers • Encryptor and decryptor use pair of different keys • Encryptor and decryptor use different functions • Example: Public key algorithms (RSA, Diffie-Hellman) 9/31 Groep T Leuven – Information department 2003 -2004 - Information management 9
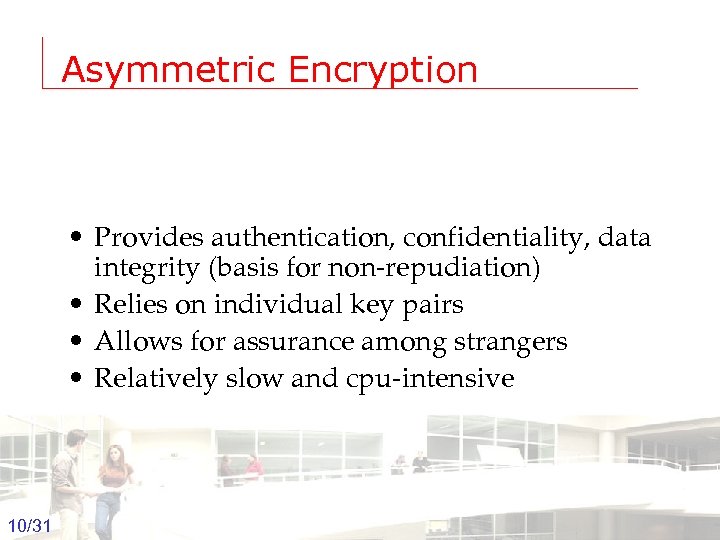
Asymmetric Encryption • Provides authentication, confidentiality, data integrity (basis for non-repudiation) • Relies on individual key pairs • Allows for assurance among strangers • Relatively slow and cpu-intensive 10/31 Groep T Leuven – Information department 2003 -2004 - Information management 10

Public Key Encryption • • Public/private keys Digital signatures Certificates Certifying Authority (CA) 11/31 Groep T Leuven – Information department 2003 -2004 - Information management 11
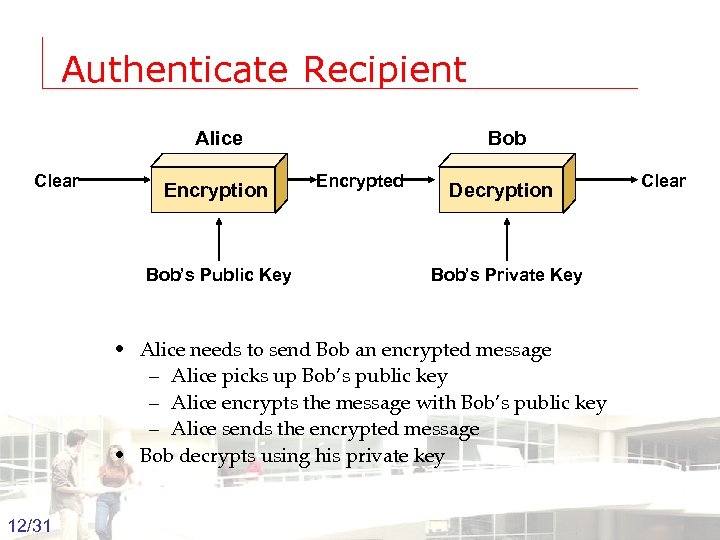
Authenticate Recipient Alice Clear Encryption Bob Encrypted Bob’s Public Key Decryption Clear Bob’s Private Key • Alice needs to send Bob an encrypted message – Alice picks up Bob’s public key – Alice encrypts the message with Bob’s public key – Alice sends the encrypted message • Bob decrypts using his private key 12/31 Groep T Leuven – Information department 2003 -2004 - Information management 12
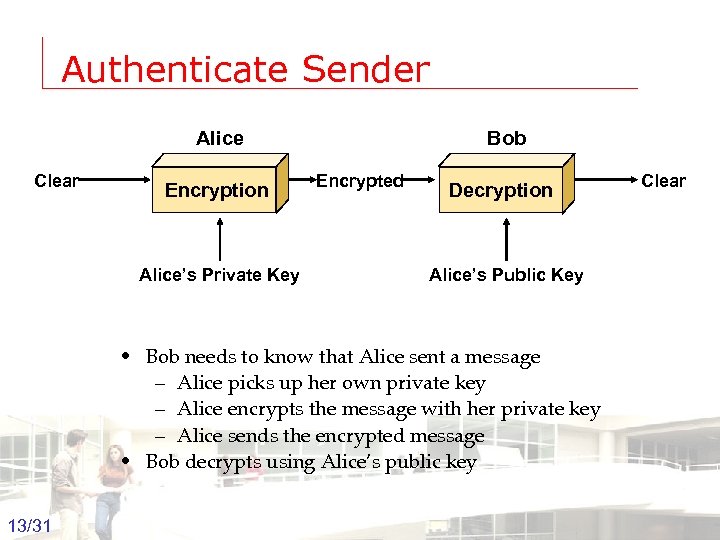
Authenticate Sender Alice Clear Encryption Bob Encrypted Alice’s Private Key Decryption Clear Alice’s Public Key • Bob needs to know that Alice sent a message – Alice picks up her own private key – Alice encrypts the message with her private key – Alice sends the encrypted message • Bob decrypts using Alice’s public key 13/31 Groep T Leuven – Information department 2003 -2004 - Information management 13
Digital Signature Invoice Payment Signature • A digital signature is a message that is appended to a document • It can be used to prove the identity of the sender and the integrity of the document 14/31 Groep T Leuven – Information department 2003 -2004 - Information management 14
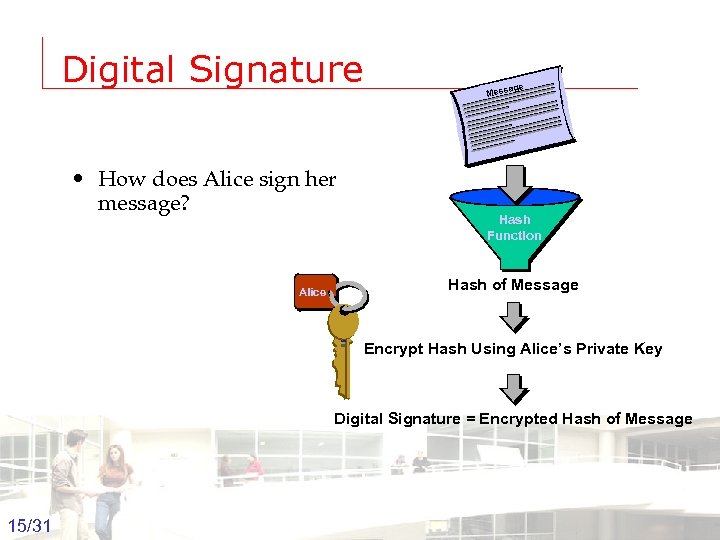
Digital Signature • How does Alice sign her message? e ag Mess Hash Function Hash of Message Alice Encrypt Hash Using Alice’s Private Key Digital Signature = Encrypted Hash of Message 15/31 Groep T Leuven – Information department 2003 -2004 - Information management 15
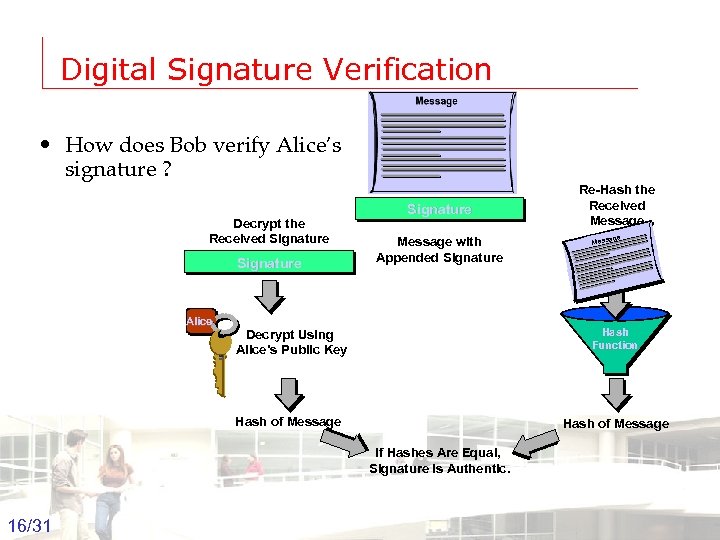
Digital Signature Verification • How does Bob verify Alice’s signature ? Decrypt the Received Signature Alice Signature Message with Appended Signature Re-Hash the Received Message Mess Decrypt Using Alice’s Public Key Hash Function Hash of Message If Hashes Are Equal, Signature Is Authentic. 16/31 Groep T Leuven – Information department 2003 -2004 - Information management 16

Digital Signature • Two common public-key digital signature techniques: • RSA (Rivest, Shamir, Adelman) • DSS (Digital Signature Standard) • A sender uses his secret key to sign a document • The receiver of the document uses the sender’s public key to verify the signature • If the verification is successful, we are assured of two things: • The document has not been altered • The identity of the author 17/31 Groep T Leuven – Information department 2003 -2004 - Information management 17
Key Attack Secu re 18/31 Groep T Leuven – Information department 2003 -2004 - Information management 18

Where Did the Public Key Come From? • How can Bob be assured that Alice’s public key belongs to the real Alice? Alice “I’m Margaret Thatcher. ” 19/31 Groep T Leuven – Information department Bob “I’m Mickey Mouse. ” 2003 -2004 - Information management 19

Digital Certificate • A signed message that attests to the authenticity of the users public key • A digital certificate contains: • • • Serial number of the certificate Issuer algorithm information (digest/hash, PK type, PK) Valid to/from date User public key information (PK type, PK) Signature of issuing authority 0000123 SHA, DH, 3837829. . 1/1/93 to 12/31/98 Alice Smith, Acme Corporation DH, 3813710. . . Acme Corporation, Security Dept. SHA, DH, 2393702347. . . 20/31 Groep T Leuven – Information department 2003 -2004 - Information management 20
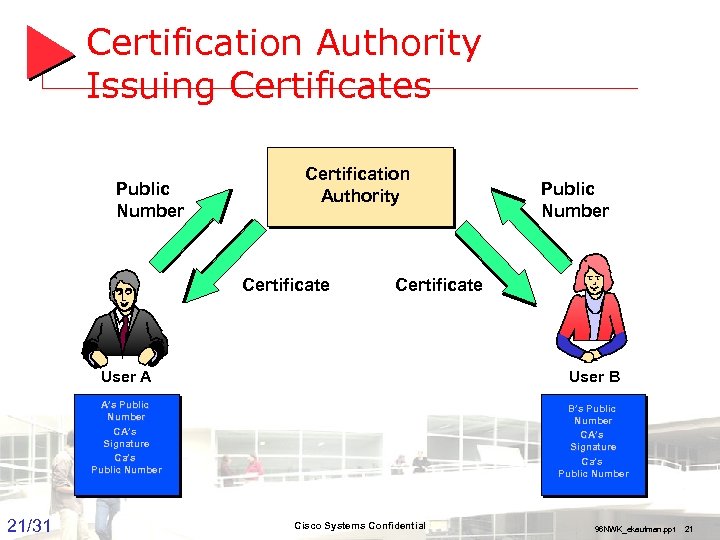
Certification Authority Issuing Certificates Public Number Certification Authority Certificate Public Number Certificate User A User B A’s Public Number CA’s Signature Ca’s Public Number B’s Public Number CA’s Signature Ca’s Public Number Cisco Systems 2003 -2004 - Information management 96 NWK_ekaufman. ppt 21 21/31 Groep T Leuven – Information department Confidential 21
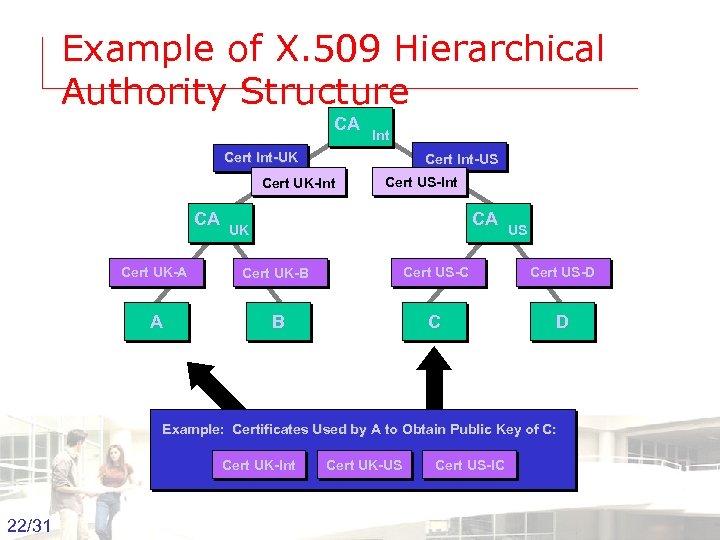
Example of X. 509 Hierarchical Authority Structure CA Int Cert Int-UK Cert Int-US Cert UK-Int CA Cert US-Int CA UK US Cert UK-A Cert UK-B Cert US-C Cert US-D A B C D Example: Certificates Used by A to Obtain Public Key of C: Cert UK-Int Cert UK-US 22/31 Groep T Leuven – Information department Cert US-IC 2003 -2004 - Information management 22
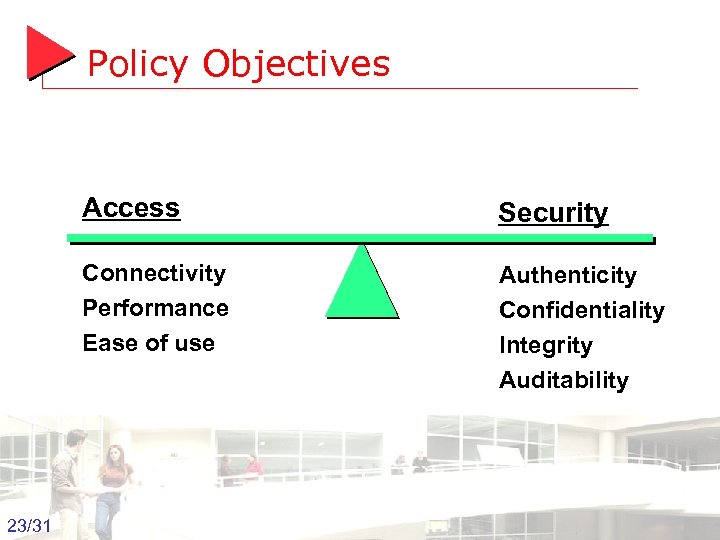
Policy Objectives Access Security Connectivity Performance Ease of use Authenticity Confidentiality Integrity Auditability 23/31 Groep T Leuven – Information department 2003 -2004 - Information management 23
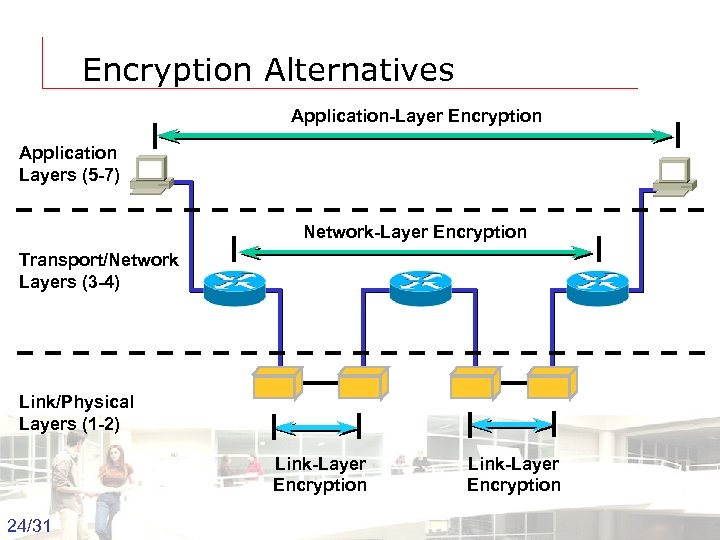
Encryption Alternatives Application-Layer Encryption Application Layers (5 -7) Network-Layer Encryption Transport/Network Layers (3 -4) Link/Physical Layers (1 -2) Link-Layer Encryption 24/31 Groep T Leuven – Information department Link-Layer Encryption 2003 -2004 - Information management 24
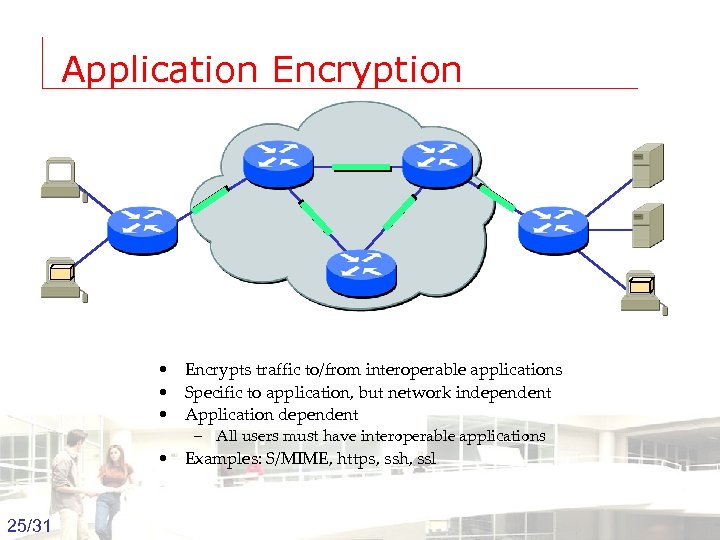
Application Encryption • Encrypts traffic to/from interoperable applications • Specific to application, but network independent • Application dependent – All users must have interoperable applications • Examples: S/MIME, https, ssh, ssl 25/31 Groep T Leuven – Information department 2003 -2004 - Information management 25
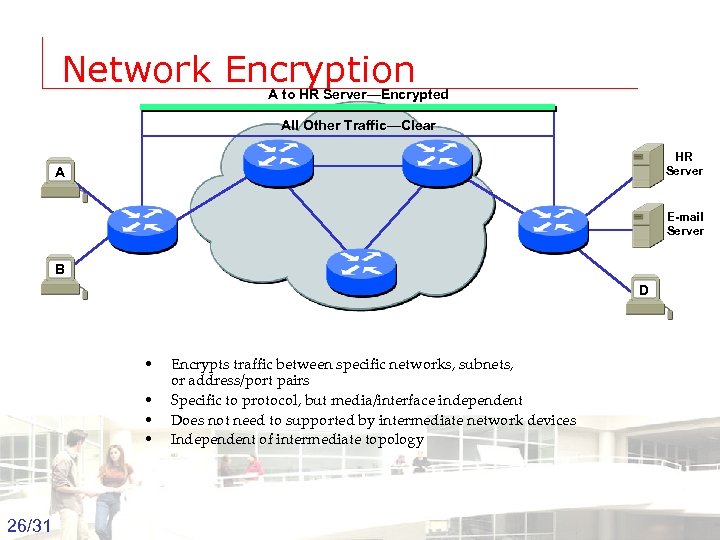
Network Encryption A to HR Server—Encrypted All Other Traffic—Clear HR Server A E-mail Server B D • • Encrypts traffic between specific networks, subnets, or address/port pairs Specific to protocol, but media/interface independent Does not need to supported by intermediate network devices Independent of intermediate topology 26/31 Groep T Leuven – Information department 2003 -2004 - Information management 26
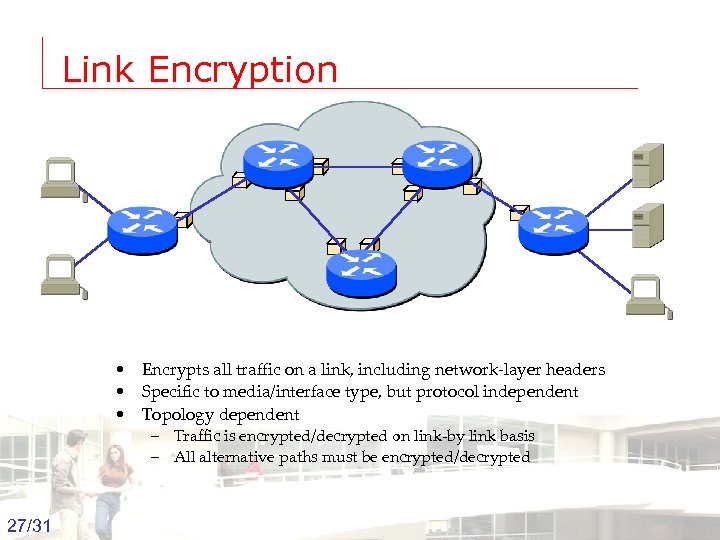
Link Encryption • Encrypts all traffic on a link, including network-layer headers • Specific to media/interface type, but protocol independent • Topology dependent – Traffic is encrypted/decrypted on link-by link basis – All alternative paths must be encrypted/decrypted 27/31 Groep T Leuven – Information department 2003 -2004 - Information management 27

Evolution of Public Key Cryptography • 1976 Public key principles established by Diffie and Hellman • 1978 Public key implementation defined by Rivest, Shamir, Aldeman for digital signatures • 1985 First product incorporating public key introduced by Cylink • 1985 El Gamal develops public key digital signature and encryption scheme based on exponentiation 28/31 Groep T Leuven – Information department 2003 -2004 - Information management 28
Evolution of Public Key Cryptography (Cont. ) • 1987 -89 • • 1987 -95 • Public key emerging as standard in Europe Endorsed by SWIFT, EFTPOS (1987) ISO/OSI standards in review phase (1988) Public key evolving as U. S. standard Used in STU-III Secure Telephone (1987) Adopted by Treasury and Justice (1988) Adopted by Internet (1989) NIST standards in review phase (1989) ANSI X 9. 17 proposal in review (1989) Digital signature standard (DSS) (1994) FIPS-186 DSS (1994) ANSI X 0. 42 (draft) for Diffie-Hellman (1995) 29/31 Groep T Leuven – Information department 2003 -2004 - Information management 29

Public Key Standards • OSI/IEC 9594 -8 Recommendation X. 509 (also ITU X. 509): the Directory: Authentication Framework • AS 28095. 5. 3 (Australian Government)—Electronic Data Transfer-Requirements for Interfaces: Part 5. 3 Data Encipherment Algorithms (RSA) • ISO 9796: Information Technology, Security Techniques: Digital Signature Scheme Giving Message Recovery • ANSI X 9. 31 (Draft): Public Key Cryptography using Reversible Algorithms for the Financial Services Industry: Part 1: the RSA Signature Algorithm 30/31 Groep T Leuven – Information department 2003 -2004 - Information management 30

Public Key Standards (Cont. ) • ANSI X 9. 30 (Draft): Public Key Cryptography for the Financial Service Industry: Part 1: The Digital Signature Algorithm • X 9. 42 (Draft): Diffie-Hellman Public Key Exchange • Federal Information Processing Standard FIPS-186: Digital Signature Standard • Others: – ETEBAC 5, (France) ISO draft standard CD 11166 IEEE draft 802. 11 Secure Interoperability Standard for LANs 31/31 Groep T Leuven – Information department 2003 -2004 - Information management 31
0ce0c08c3ba99aca92bc62f86fa2c146.ppt