a35346129c8f0b125ec3e3163a66f01d.ppt
- Количество слайдов: 22

SECURITY AWARENESS FOR THE NET GENERATION Tuesday November 3, 2009 (modified slightly for online posting)

ABOUT THE PRESENTERS Scott Z. Wilson Ben Woelk Information Security and Policy Information Manager Information Security Communications and Training Specialist

RIT AWARENESS GOALS • increase security “consciousness” • enable digital self defense • decrease losses

CHALLENGES (SOUND FAMILIAR? ) who is RIT? multiple audiences • not all tech savvy • new students each year • 3000 faculty and staff • white noise/competing priorities •

FALL ORIENTATION information security standards • copyright and illegal file sharing • safe social networking •
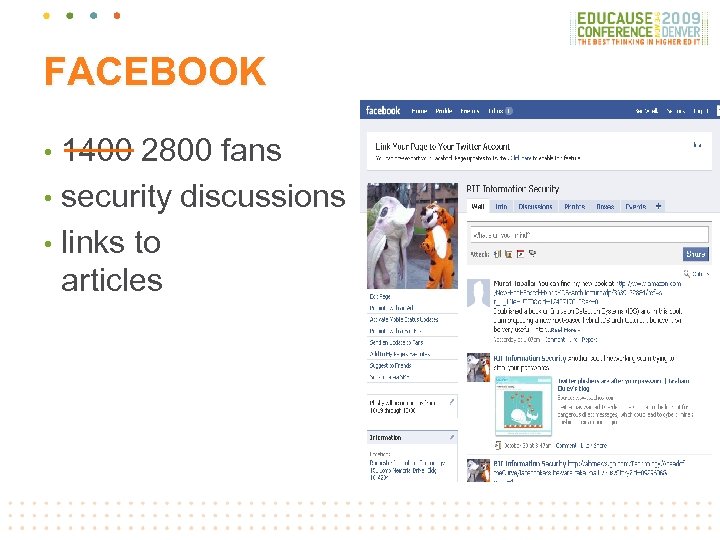
FACEBOOK 1400 2800 fans • security discussions • links to articles •
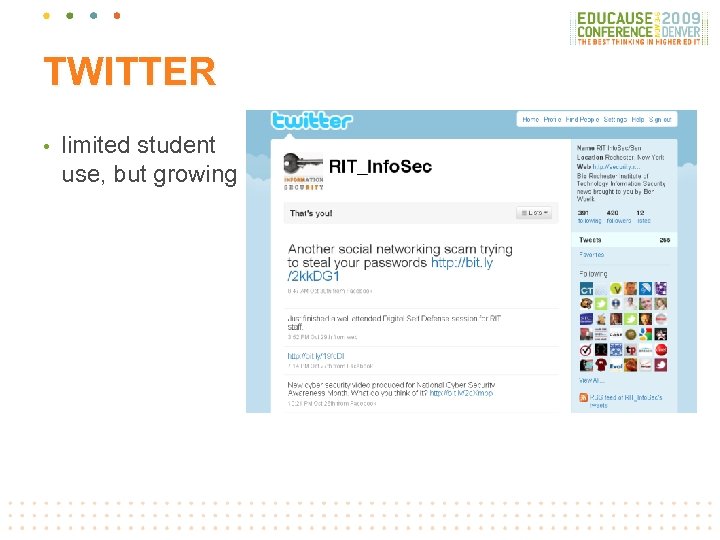
TWITTER • limited student use, but growing

THIS SESSION… Discuss characteristics of the “Net Generation” • 3 Progression sessions • 1: 30 pm – 2: 00 pm • 2: 00 pm – 2: 30 pm • 3: 00 pm – 3: 30 pm • Review • 3: 30 pm – 4: 15 pm • Wrap up • 4: 15 pm – 4: 30 pm •

THE NET GENERATION… Understanding your audience • Respecting your audience •


UNDERSTANDING YOUR AUDIENCE

“THEY'RE DUMBER THAN WE WERE AT THEIR AGE” Evidence suggests they are the smartest generation ever Students challenging themselves • AP tests have doubled between 1997 and 2005 • Raw IQ scores are climbing •
“THEY SPEND TOO MUCH TIME IN FRONT OF THE SCREEN” They use technology different than boomers Net Geners chat, research, collaborate, do homework, and receive entertainment through the Internet. Simultaneously. • Most of their computer time is what used to be TV time. • 77% said they would rather live w/o TV; 23% said live w/o internet •

“PARENTS CODDLE THEM, THEY'RE ADRIFT AND CAN'T CHOOSE A PATH. ” No work ethic and will be bad employees. They steal, and bully friends online “They don't give a damn”
Net Geners want freedom in everything: choice, expression, etc • Older generations sometimes feel overwhelmed by proliferation of choices, not so with Net Geners love to personalize and customize • • • desktops, ring tones, news sources, entertainment they don't just access the Web, they create and reshape it freedom to use technology to escape traditional office constraints and integrate work lives with their home and social lives enjoy their work, experience a mix of work/play choose job locations, customize job descriptions
Net Geners are the new scrutinizers look for integrity • ensure a company's mission aligns with their own — both with products they buy and organizations they work for • Use technology to act. • tools like Facebook to rally and communicate
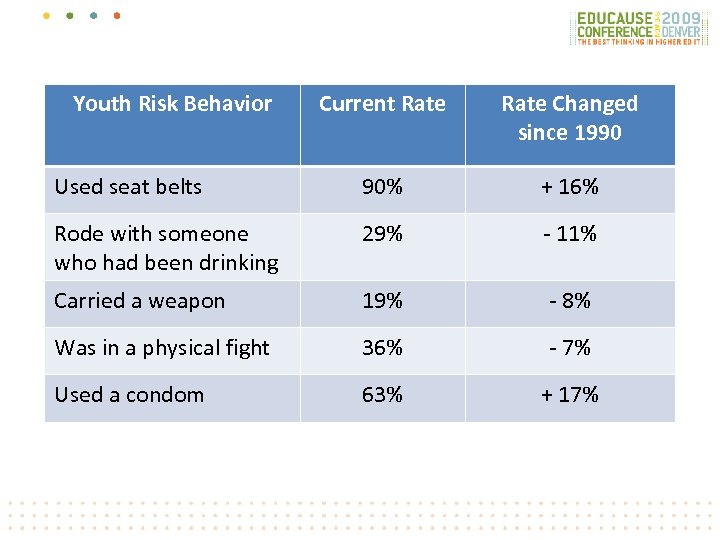
Youth Risk Behavior Current Rate Changed since 1990 Used seat belts 90% + 16% Rode with someone who had been drinking 29% - 11% Carried a weapon 19% - 8% Was in a physical fight 36% - 7% Used a condom 63% + 17%
respect your audience If you want their attention, their action: • use their mediums • speak their language • Golden Rule of communication? ? • Net Geners have GREAT BS detectors • EXAMPLES http: //www. theonion. com/content/video/facebook_twitter_revolutionizing • http: //www. youtube. com/watch? v=d. GCJ 46 vy. R 9 o •

PROGRESSION SESSIONS • talk about issues you’re facing • topics you wish to communicate more effectively • top 10 topics?

WRAPPING UP…

NOTES • • Data Exposure • Data security • Application firewalls • Building a culture of security • interviews with student papers, media outlets/publications Phishing • awareness in Email signatures about not asking for university • employees asking for credentials • develop a clear, unambiguous message • phishing site blacklists • using geolocation to flag suspicious logins • helps detect helicopter parents • mail usage alerts • known safe sites • can be directed to w/o provision of URL • leverage tools like Open DNS • Ignorance • warning students who are too trusting • "ignorance is bliss" requires less effort than the alternative • invitations work less than meeting others in their natural space • "road show" concept more effective • provide relevant examples of what happens when things "go wrong” • have the student/victim tell the story • P 2 P • • What effective practices do you have currently? • working with subsets • student employees, student groups • use of EV SSL certs • BAYU (Be Aware You're Uploading - University of Michigan [bayu. umich. edu]) Passwords difficulty vetting identities for password resets segmenting passwords with unique, site-specific information (password scheme) • "something you know" plus a prefix/suffix use of passphrases mitigating use of identical credentials all over the Net advocating use of password/passphrase vaulting • PWD Hash

Copyright Ben Woelk and Scott Wilson, 2009. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author.
a35346129c8f0b125ec3e3163a66f01d.ppt