85ae76fb7e6797872508da515925d76e.ppt
- Количество слайдов: 37
 Security at different layers Link layer: WEP / 802. 11 i Application layer: PGP Transport layer: SSL Network layer: IPsec approach: r r HTTP/SMTP/IM TCP/UDP/ICMP IPsec can provide security between any pair of network-layer entities (eg, between two hosts, two routers, or a host and a router). 1
Security at different layers Link layer: WEP / 802. 11 i Application layer: PGP Transport layer: SSL Network layer: IPsec approach: r r HTTP/SMTP/IM TCP/UDP/ICMP IPsec can provide security between any pair of network-layer entities (eg, between two hosts, two routers, or a host and a router). 1
 IP Security r IP datagrams have no inherent security m IP source address can be spoofed m Content of IP datagrams can be sniffed m Content of IP datagrams can be modified m IP datagrams can be replayed r IPSec is a method for protecting IP datagrams m Standardized by IETF: dozens of RFCs. m Only sender and receiver have to be IPsec compliant • Rest of network can be regular IP 2
IP Security r IP datagrams have no inherent security m IP source address can be spoofed m Content of IP datagrams can be sniffed m Content of IP datagrams can be modified m IP datagrams can be replayed r IPSec is a method for protecting IP datagrams m Standardized by IETF: dozens of RFCs. m Only sender and receiver have to be IPsec compliant • Rest of network can be regular IP 2
 What is confidentiality at the network-layer? Between two network entities: r Sending entity encrypts the payloads of datagrams. Payload could be: m TCP segment, UDP segment, ICMP message, OSPF message, and so on. r All data sent from one entity to the other would be hidden: m Web pages, e-mail, P 2 P file transfers, TCP SYN packets, and so on. r That is, “blanket coverage”. 3
What is confidentiality at the network-layer? Between two network entities: r Sending entity encrypts the payloads of datagrams. Payload could be: m TCP segment, UDP segment, ICMP message, OSPF message, and so on. r All data sent from one entity to the other would be hidden: m Web pages, e-mail, P 2 P file transfers, TCP SYN packets, and so on. r That is, “blanket coverage”. 3
 Virtual Private Networks (VPNs) r Institutions often want private networks for security. m Costly! Separate routers, links, DNS infrastructure. r With a VPN, institution’s inter-office traffic is sent over public Internet instead. m But inter-office traffic is encrypted before entering public Internet 4
Virtual Private Networks (VPNs) r Institutions often want private networks for security. m Costly! Separate routers, links, DNS infrastructure. r With a VPN, institution’s inter-office traffic is sent over public Internet instead. m But inter-office traffic is encrypted before entering public Internet 4
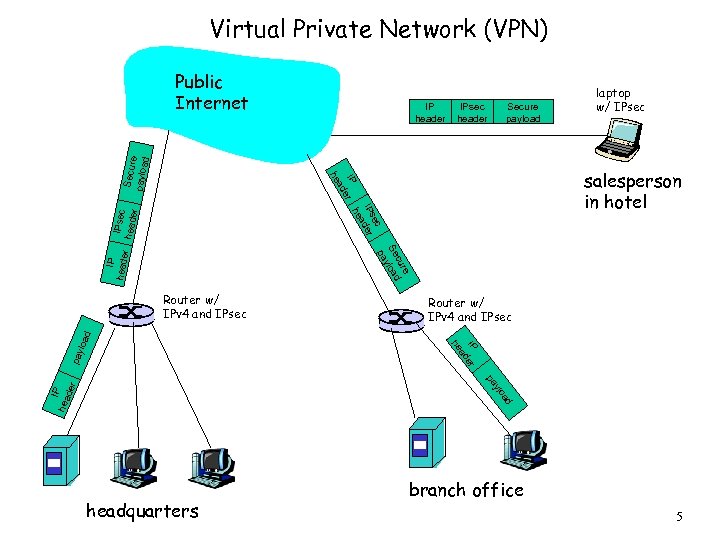 Virtual Private Network (VPN) IP header IPsec header Secure payload IP er ad ec IPs der a he IPsec heade r laptop w/ IPsec salesperson in hotel he Secur e payloa d Public Internet IP heade r re cu Se load y pa IP er ad pay Router w/ IPv 4 and IPsec he loa d Router w/ IPv 4 and IPsec ylo IP hea der pa ad headquarters branch office 5
Virtual Private Network (VPN) IP header IPsec header Secure payload IP er ad ec IPs der a he IPsec heade r laptop w/ IPsec salesperson in hotel he Secur e payloa d Public Internet IP heade r re cu Se load y pa IP er ad pay Router w/ IPv 4 and IPsec he loa d Router w/ IPv 4 and IPsec ylo IP hea der pa ad headquarters branch office 5
 IPsec services r Data integrity r Origin authentication r Replay attack prevention r Confidentiality r Two protocols providing different service models: m AH m ESP 6
IPsec services r Data integrity r Origin authentication r Replay attack prevention r Confidentiality r Two protocols providing different service models: m AH m ESP 6
 IPsec Transport Mode IPsec r IPsec datagram emitted and received by end-system. r Protects upper level protocols 7
IPsec Transport Mode IPsec r IPsec datagram emitted and received by end-system. r Protects upper level protocols 7
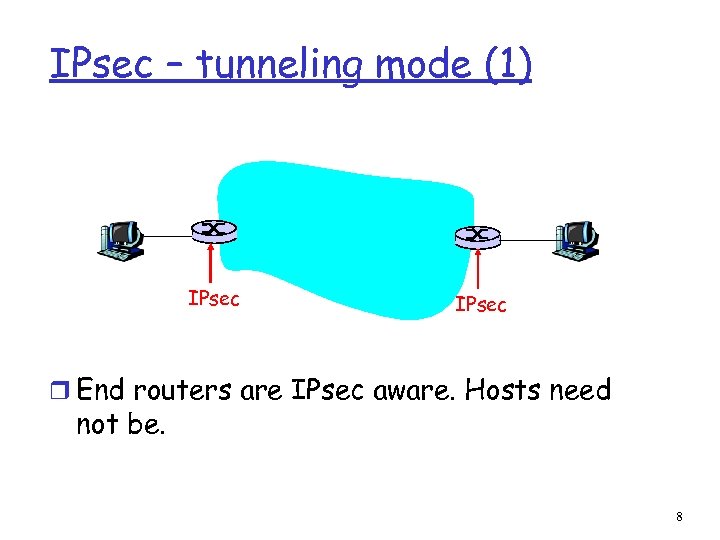 IPsec – tunneling mode (1) IPsec r End routers are IPsec aware. Hosts need not be. 8
IPsec – tunneling mode (1) IPsec r End routers are IPsec aware. Hosts need not be. 8
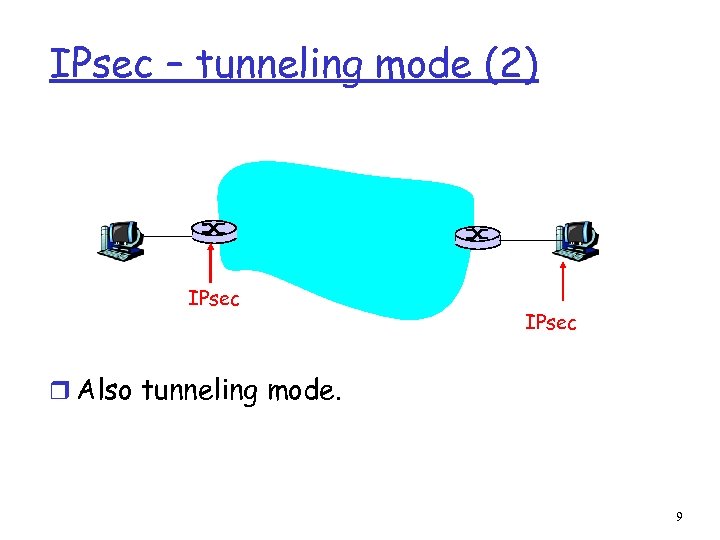 IPsec – tunneling mode (2) IPsec r Also tunneling mode. 9
IPsec – tunneling mode (2) IPsec r Also tunneling mode. 9
 Two protocols r Authentication Header (AH) protocol m provides source authentication & data integrity but not confidentiality r Encapsulation Security Protocol (ESP) m provides source authentication, data integrity, and confidentiality m more widely used than AH 10
Two protocols r Authentication Header (AH) protocol m provides source authentication & data integrity but not confidentiality r Encapsulation Security Protocol (ESP) m provides source authentication, data integrity, and confidentiality m more widely used than AH 10
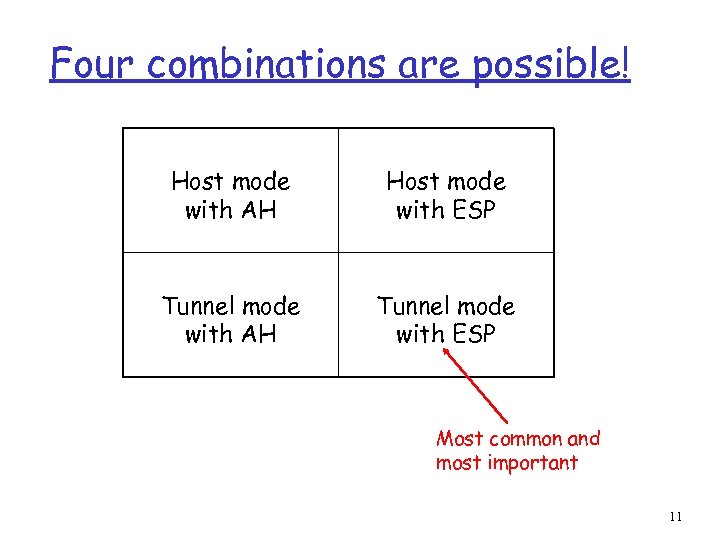 Four combinations are possible! Host mode with AH Host mode with ESP Tunnel mode with AH Tunnel mode with ESP Most common and most important 11
Four combinations are possible! Host mode with AH Host mode with ESP Tunnel mode with AH Tunnel mode with ESP Most common and most important 11
 Security associations (SAs) r Before sending data, a virtual connection is established from sending entity to receiving entity. r Called “security association (SA)” m SAs are simplex: for only one direction r Both sending and receiving entites maintain state information about the SA m m Recall that TCP endpoints also maintain state information. IP is connectionless; IPsec is connection-oriented! r How many SAs in VPN w/ headquarters, branch office, and n traveling salesperson? 12
Security associations (SAs) r Before sending data, a virtual connection is established from sending entity to receiving entity. r Called “security association (SA)” m SAs are simplex: for only one direction r Both sending and receiving entites maintain state information about the SA m m Recall that TCP endpoints also maintain state information. IP is connectionless; IPsec is connection-oriented! r How many SAs in VPN w/ headquarters, branch office, and n traveling salesperson? 12
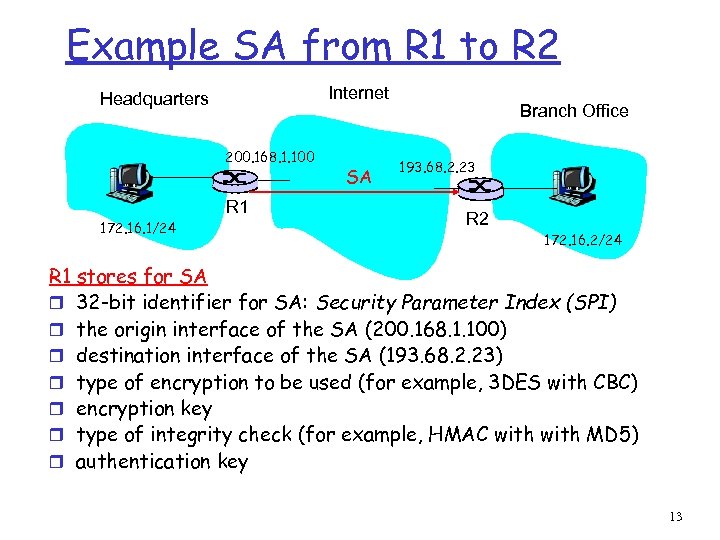 Example SA from R 1 to R 2 Internet Headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 SA Branch Office 193. 68. 2. 23 R 2 172. 16. 2/24 R 1 stores for SA r 32 -bit identifier for SA: Security Parameter Index (SPI) r the origin interface of the SA (200. 168. 1. 100) r destination interface of the SA (193. 68. 2. 23) r type of encryption to be used (for example, 3 DES with CBC) r encryption key r type of integrity check (for example, HMAC with MD 5) r authentication key 13
Example SA from R 1 to R 2 Internet Headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 SA Branch Office 193. 68. 2. 23 R 2 172. 16. 2/24 R 1 stores for SA r 32 -bit identifier for SA: Security Parameter Index (SPI) r the origin interface of the SA (200. 168. 1. 100) r destination interface of the SA (193. 68. 2. 23) r type of encryption to be used (for example, 3 DES with CBC) r encryption key r type of integrity check (for example, HMAC with MD 5) r authentication key 13
 Security Association Database (SAD) r Endpoint holds state of its SAs in a SAD, where it can locate them during processing. r With n salespersons, 2 + 2 n SAs in R 1’s SAD r When sending IPsec datagram, R 1 accesses SAD to determine how to process datagram. r When IPsec datagram arrives to R 2, R 2 examines SPI in IPsec datagram, indexes SAD with SPI, and processes datagram accordingly. 14
Security Association Database (SAD) r Endpoint holds state of its SAs in a SAD, where it can locate them during processing. r With n salespersons, 2 + 2 n SAs in R 1’s SAD r When sending IPsec datagram, R 1 accesses SAD to determine how to process datagram. r When IPsec datagram arrives to R 2, R 2 examines SPI in IPsec datagram, indexes SAD with SPI, and processes datagram accordingly. 14
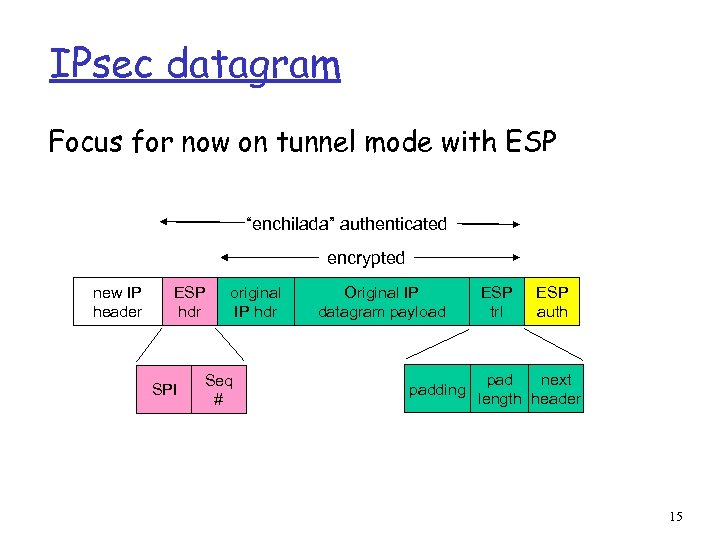 IPsec datagram Focus for now on tunnel mode with ESP “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 15
IPsec datagram Focus for now on tunnel mode with ESP “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 15
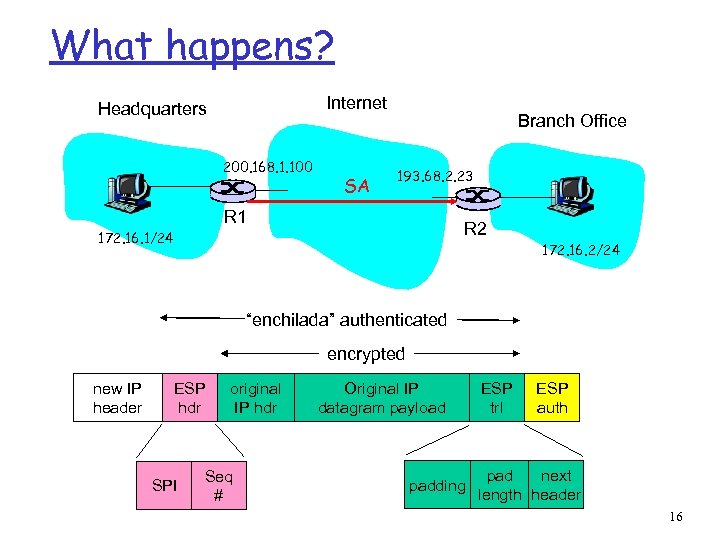 What happens? Internet Headquarters 200. 168. 1. 100 SA Branch Office 193. 68. 2. 23 R 1 R 2 172. 16. 1/24 172. 16. 2/24 “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 16
What happens? Internet Headquarters 200. 168. 1. 100 SA Branch Office 193. 68. 2. 23 R 1 R 2 172. 16. 1/24 172. 16. 2/24 “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 16
 R 1 converts original datagram into IPsec datagram r Appends to back of original datagram (which includes r r r original header fields!) an “ESP trailer” field. Encrypts result using algorithm & key specified by SA. Appends to front of this encrypted quantity the “ESP header, creating “enchilada”. Creates authentication MAC over the whole enchilada, using algorithm and key specified in SA; Appends MAC to back of enchilada, forming payload; Creates brand new IP header, with all the classic IPv 4 header fields, which it appends before payload. 17
R 1 converts original datagram into IPsec datagram r Appends to back of original datagram (which includes r r r original header fields!) an “ESP trailer” field. Encrypts result using algorithm & key specified by SA. Appends to front of this encrypted quantity the “ESP header, creating “enchilada”. Creates authentication MAC over the whole enchilada, using algorithm and key specified in SA; Appends MAC to back of enchilada, forming payload; Creates brand new IP header, with all the classic IPv 4 header fields, which it appends before payload. 17
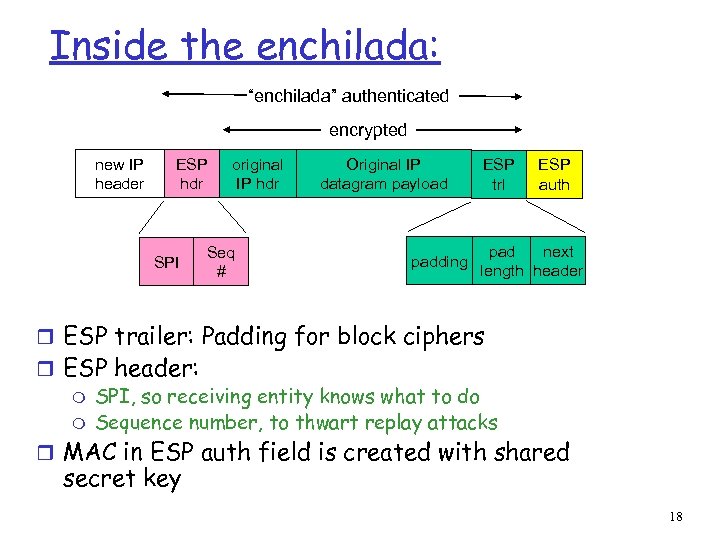 Inside the enchilada: “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header r ESP trailer: Padding for block ciphers r ESP header: m SPI, so receiving entity knows what to do m Sequence number, to thwart replay attacks r MAC in ESP auth field is created with shared secret key 18
Inside the enchilada: “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header r ESP trailer: Padding for block ciphers r ESP header: m SPI, so receiving entity knows what to do m Sequence number, to thwart replay attacks r MAC in ESP auth field is created with shared secret key 18
 IPsec sequence numbers r For new SA, sender initializes seq. # to 0 r Each time datagram is sent on SA: m Sender increments seq # counter m Places value in seq # field r Goal: m Prevent attacker from sniffing and replaying a packet • Receipt of duplicate, authenticated IP packets may disrupt service r Method: m Destination checks for duplicates m But doesn’t keep track of ALL received packets; instead uses a window 19
IPsec sequence numbers r For new SA, sender initializes seq. # to 0 r Each time datagram is sent on SA: m Sender increments seq # counter m Places value in seq # field r Goal: m Prevent attacker from sniffing and replaying a packet • Receipt of duplicate, authenticated IP packets may disrupt service r Method: m Destination checks for duplicates m But doesn’t keep track of ALL received packets; instead uses a window 19
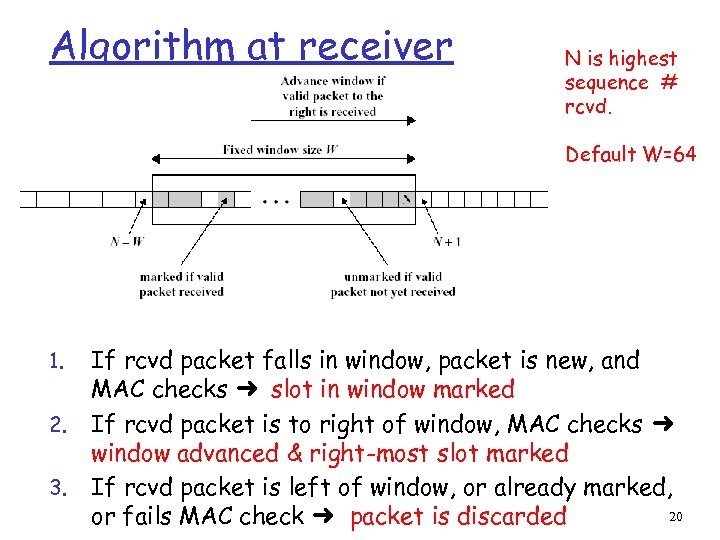 Algorithm at receiver N is highest sequence # rcvd. Default W=64 1. 2. 3. If rcvd packet falls in window, packet is new, and MAC checks ➜ slot in window marked If rcvd packet is to right of window, MAC checks ➜ window advanced & right-most slot marked If rcvd packet is left of window, or already marked, 20 or fails MAC check ➜ packet is discarded
Algorithm at receiver N is highest sequence # rcvd. Default W=64 1. 2. 3. If rcvd packet falls in window, packet is new, and MAC checks ➜ slot in window marked If rcvd packet is to right of window, MAC checks ➜ window advanced & right-most slot marked If rcvd packet is left of window, or already marked, 20 or fails MAC check ➜ packet is discarded
 Security Policy Database (SPD) r Policy: For a given datagram, sending entity needs to know if it should use IPsec. r Needs also to know which SA to use m May use: source and destination IP address; protocol number. r Info in SPD indicates “what” to do with arriving datagram; r Info in the SAD indicates “how” to do it. 21
Security Policy Database (SPD) r Policy: For a given datagram, sending entity needs to know if it should use IPsec. r Needs also to know which SA to use m May use: source and destination IP address; protocol number. r Info in SPD indicates “what” to do with arriving datagram; r Info in the SAD indicates “how” to do it. 21
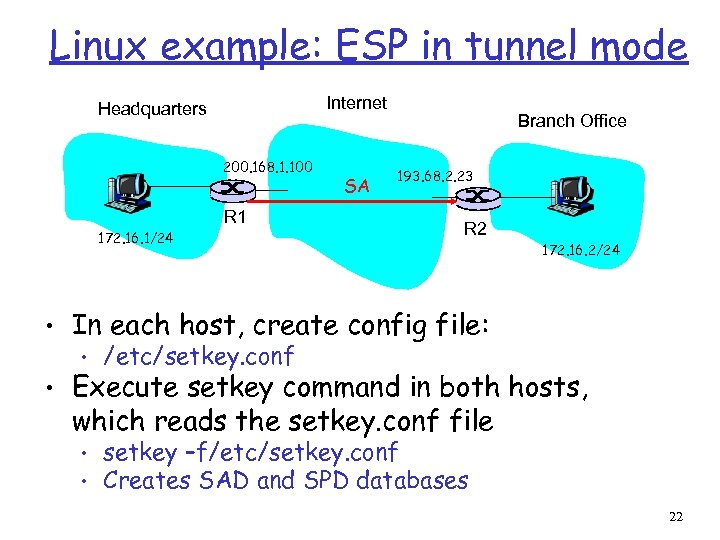 Linux example: ESP in tunnel mode Internet Headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 SA Branch Office 193. 68. 2. 23 R 2 172. 16. 2/24 • In each host, create config file: • /etc/setkey. conf • Execute setkey command in both hosts, which reads the setkey. conf file • • setkey –f/etc/setkey. conf Creates SAD and SPD databases 22
Linux example: ESP in tunnel mode Internet Headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 SA Branch Office 193. 68. 2. 23 R 2 172. 16. 2/24 • In each host, create config file: • /etc/setkey. conf • Execute setkey command in both hosts, which reads the setkey. conf file • • setkey –f/etc/setkey. conf Creates SAD and SPD databases 22
 setkey. conf for R 1 # Flush the SAD and SPD flush; spdflush; ESP protocol SPI # SAs encrypt w/ 192 bit keys & auth w/ 128 bit keys 2 SAs added to SAD Add 200. 168. 1. 100 193. 68. 2. 23 esp 0 x 201 -m tunnel -E 3 des-cbc 0 x 7 aeaca 3 f 87 d 060 a 12 f 4 a 4487 d 5 a 5 c 3355920 fae 69 a 96 c 831 -A hmac-md 5 0 xc 0291 ff 014 dccdd 03874 d 9 e 8 e 4 cdf 3 e 6; Add 193. 68. 2. 23 200. 168. 1. 100 esp 0 x 301 -m tunnel -E 3 des-cbc 0 xf 6 ddb 555 acfd 9 d 77 b 03 ea 3843 f 2653255 afe 8 eb 5573965 df -A hmac-md 5 0 x 96358 c 90783 bbfa 3 d 7 b 196 ceabe 0536 b; # Security policies 2 policies added to SPD apply to all packets spdadd 172. 16. 1. 0/24 172. 16. 2. 0/24 any -P out ipsec esp/tunnel/ 200. 168. 1. 100 - 193. 68. 2. 23 /require; spdadd 172. 16. 2. 0/24 172. 16. 1. 0/24 any -P in ipsec esp/tunnel/ 193. 68. 2. 23 - 200. 168. 1. 100 /require; 23
setkey. conf for R 1 # Flush the SAD and SPD flush; spdflush; ESP protocol SPI # SAs encrypt w/ 192 bit keys & auth w/ 128 bit keys 2 SAs added to SAD Add 200. 168. 1. 100 193. 68. 2. 23 esp 0 x 201 -m tunnel -E 3 des-cbc 0 x 7 aeaca 3 f 87 d 060 a 12 f 4 a 4487 d 5 a 5 c 3355920 fae 69 a 96 c 831 -A hmac-md 5 0 xc 0291 ff 014 dccdd 03874 d 9 e 8 e 4 cdf 3 e 6; Add 193. 68. 2. 23 200. 168. 1. 100 esp 0 x 301 -m tunnel -E 3 des-cbc 0 xf 6 ddb 555 acfd 9 d 77 b 03 ea 3843 f 2653255 afe 8 eb 5573965 df -A hmac-md 5 0 x 96358 c 90783 bbfa 3 d 7 b 196 ceabe 0536 b; # Security policies 2 policies added to SPD apply to all packets spdadd 172. 16. 1. 0/24 172. 16. 2. 0/24 any -P out ipsec esp/tunnel/ 200. 168. 1. 100 - 193. 68. 2. 23 /require; spdadd 172. 16. 2. 0/24 172. 16. 1. 0/24 any -P in ipsec esp/tunnel/ 193. 68. 2. 23 - 200. 168. 1. 100 /require; 23
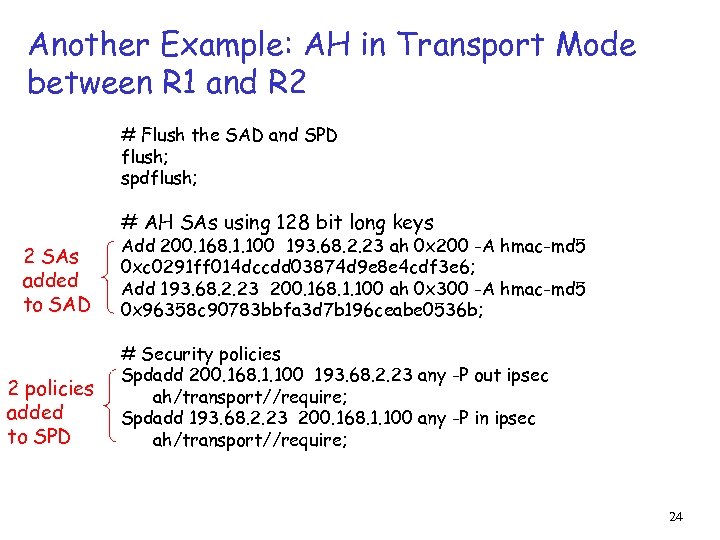 Another Example: AH in Transport Mode between R 1 and R 2 # Flush the SAD and SPD flush; spdflush; # AH SAs using 128 bit long keys 2 SAs added to SAD 2 policies added to SPD Add 200. 168. 1. 100 193. 68. 2. 23 ah 0 x 200 -A hmac-md 5 0 xc 0291 ff 014 dccdd 03874 d 9 e 8 e 4 cdf 3 e 6; Add 193. 68. 2. 23 200. 168. 1. 100 ah 0 x 300 -A hmac-md 5 0 x 96358 c 90783 bbfa 3 d 7 b 196 ceabe 0536 b; # Security policies Spdadd 200. 168. 1. 100 193. 68. 2. 23 any -P out ipsec ah/transport//require; Spdadd 193. 68. 2. 23 200. 168. 1. 100 any -P in ipsec ah/transport//require; 24
Another Example: AH in Transport Mode between R 1 and R 2 # Flush the SAD and SPD flush; spdflush; # AH SAs using 128 bit long keys 2 SAs added to SAD 2 policies added to SPD Add 200. 168. 1. 100 193. 68. 2. 23 ah 0 x 200 -A hmac-md 5 0 xc 0291 ff 014 dccdd 03874 d 9 e 8 e 4 cdf 3 e 6; Add 193. 68. 2. 23 200. 168. 1. 100 ah 0 x 300 -A hmac-md 5 0 x 96358 c 90783 bbfa 3 d 7 b 196 ceabe 0536 b; # Security policies Spdadd 200. 168. 1. 100 193. 68. 2. 23 any -P out ipsec ah/transport//require; Spdadd 193. 68. 2. 23 200. 168. 1. 100 any -P in ipsec ah/transport//require; 24
 Possible encryption algorithms r DES r 3 DES r AES r RC 5 r IDEA r 3 -IDEA r CAST r Blowfish r …. 25
Possible encryption algorithms r DES r 3 DES r AES r RC 5 r IDEA r 3 -IDEA r CAST r Blowfish r …. 25
 IPsec services r Suppose Trudy sits somewhere between R 1 and R 2. She doesn’t know the keys. m Will Trudy be able to see contents of original datagram? How about source, dest IP address, transport protocol, application port? m Flip bits without detection? m Masquerade as R 1 using R 1’s IP address? m Replay a datagram? 26
IPsec services r Suppose Trudy sits somewhere between R 1 and R 2. She doesn’t know the keys. m Will Trudy be able to see contents of original datagram? How about source, dest IP address, transport protocol, application port? m Flip bits without detection? m Masquerade as R 1 using R 1’s IP address? m Replay a datagram? 26
 IPsec vs. SSL r SSL is in application; IPsec in OS m IPsec protects all apps r SSL is susceptible to a Do. S attack: m Attacker inserts bogus TCP segment into packet stream: • with correct TCP checksum and seq #s m TCP acks segment and sends segment’s payload up to SSL will discard since integrity check is bogus Real segment arrives: m SSL never gets real segment m m • TCP rejects since it has the wrong seq # • SSL closes connection since it can’t provide lossless byte stream service r What happens if an attacker inserts a bogus IPsec datagram? m m IPsec at receiver drops datagram since integrity check is bogus; not marked as arrived in seq # window Real segment arrives, passes integrity check and passed up to TCP – no problem! 27
IPsec vs. SSL r SSL is in application; IPsec in OS m IPsec protects all apps r SSL is susceptible to a Do. S attack: m Attacker inserts bogus TCP segment into packet stream: • with correct TCP checksum and seq #s m TCP acks segment and sends segment’s payload up to SSL will discard since integrity check is bogus Real segment arrives: m SSL never gets real segment m m • TCP rejects since it has the wrong seq # • SSL closes connection since it can’t provide lossless byte stream service r What happens if an attacker inserts a bogus IPsec datagram? m m IPsec at receiver drops datagram since integrity check is bogus; not marked as arrived in seq # window Real segment arrives, passes integrity check and passed up to TCP – no problem! 27
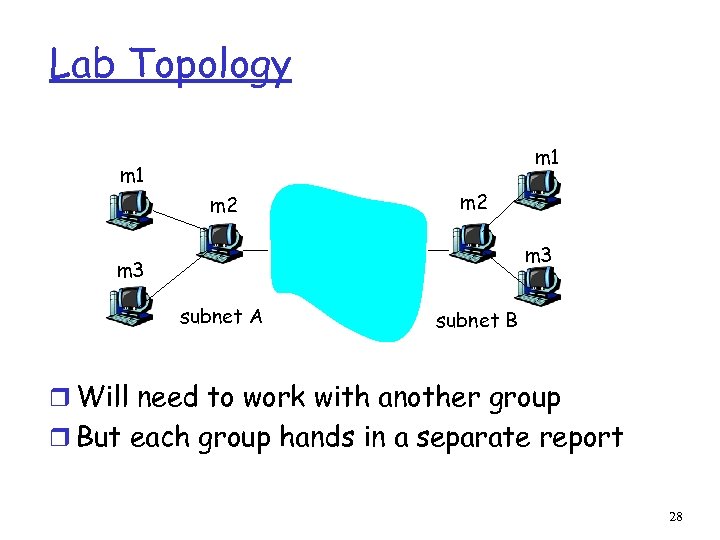 Lab Topology m 1 m 2 m 3 subnet A subnet B r Will need to work with another group r But each group hands in a separate report 28
Lab Topology m 1 m 2 m 3 subnet A subnet B r Will need to work with another group r But each group hands in a separate report 28
 Lab: Use ESP protocol throughout r Part 1: manual keying m Setup IPsec between your group’s m 1 and m 3 using transport mode r Part 2: manual keying m Setup IPsec between m 2 and partner’s m 2 using tunnel mode m Send traffic between m 1 and partner’s m 1 r Part 3: manual keying m Setup IPsec between m 1 and partner’s m 1 using transport mode 29
Lab: Use ESP protocol throughout r Part 1: manual keying m Setup IPsec between your group’s m 1 and m 3 using transport mode r Part 2: manual keying m Setup IPsec between m 2 and partner’s m 2 using tunnel mode m Send traffic between m 1 and partner’s m 1 r Part 3: manual keying m Setup IPsec between m 1 and partner’s m 1 using transport mode 29
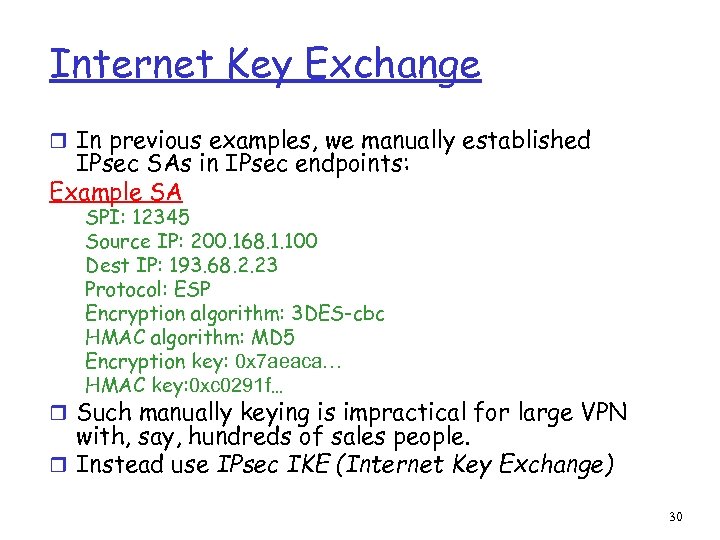 Internet Key Exchange r In previous examples, we manually established IPsec SAs in IPsec endpoints: Example SA SPI: 12345 Source IP: 200. 168. 1. 100 Dest IP: 193. 68. 2. 23 Protocol: ESP Encryption algorithm: 3 DES-cbc HMAC algorithm: MD 5 Encryption key: 0 x 7 aeaca… HMAC key: 0 xc 0291 f… r Such manually keying is impractical for large VPN with, say, hundreds of sales people. r Instead use IPsec IKE (Internet Key Exchange) 30
Internet Key Exchange r In previous examples, we manually established IPsec SAs in IPsec endpoints: Example SA SPI: 12345 Source IP: 200. 168. 1. 100 Dest IP: 193. 68. 2. 23 Protocol: ESP Encryption algorithm: 3 DES-cbc HMAC algorithm: MD 5 Encryption key: 0 x 7 aeaca… HMAC key: 0 xc 0291 f… r Such manually keying is impractical for large VPN with, say, hundreds of sales people. r Instead use IPsec IKE (Internet Key Exchange) 30
 IKE: PSK and PKI r Authentication (proof who you are) with either m pre-shared secret (PSK) or m with PKI (pubic/private keys and certificates). r With PSK, both sides start with secret: m then run IKE to authenticate each other and to generate IPsec SAs (one in each direction), including encryption and authentication keys r With PKI, both sides start with public/private key pair and certificate. m run IKE to authenticate each other and obtain IPsec SAs (one in each direction). m Similar with handshake in SSL. 31
IKE: PSK and PKI r Authentication (proof who you are) with either m pre-shared secret (PSK) or m with PKI (pubic/private keys and certificates). r With PSK, both sides start with secret: m then run IKE to authenticate each other and to generate IPsec SAs (one in each direction), including encryption and authentication keys r With PKI, both sides start with public/private key pair and certificate. m run IKE to authenticate each other and obtain IPsec SAs (one in each direction). m Similar with handshake in SSL. 31
 Linux example PSK (1) 172. 16. 1/24 IPsec 172. 16. 2/24 IPsec • In each host, create 3 files: • racoon. conf • setkey. conf • psk. txt • Execute racoon command in both hosts, which generates SAs 32
Linux example PSK (1) 172. 16. 1/24 IPsec 172. 16. 2/24 IPsec • In each host, create 3 files: • racoon. conf • setkey. conf • psk. txt • Execute racoon command in both hosts, which generates SAs 32
 Linux example PSK (2) r psk. txt m Holds the preshared secret; access is protected r racoon. conf m Indicates IKE “mode” m Cryptography preferences for phase 1 and phase 2 r setkey. conf m security policies section (similar with manual keying) m But no security association block (since SAs established with IKE) 33
Linux example PSK (2) r psk. txt m Holds the preshared secret; access is protected r racoon. conf m Indicates IKE “mode” m Cryptography preferences for phase 1 and phase 2 r setkey. conf m security policies section (similar with manual keying) m But no security association block (since SAs established with IKE) 33
 Linux example: certificates r Use open SSL to generate public/private key pair and certificate in both hosts r racoon. conf file m Provides path to certificate m IKE “mode” m Whether correspondent’s certificate needs to be validated m Cryptography algorithms for two IKE phases r setkey. conf m Similar for PSK r No psk. txt file! 34
Linux example: certificates r Use open SSL to generate public/private key pair and certificate in both hosts r racoon. conf file m Provides path to certificate m IKE “mode” m Whether correspondent’s certificate needs to be validated m Cryptography algorithms for two IKE phases r setkey. conf m Similar for PSK r No psk. txt file! 34
 IKE Phases r IKE has two phases m Phase 1: Establish bi-directional IKE SA • Note: IKE SA different from IPsec SA • Also called ISAKMP security association m Phase 2: ISAKMP is used to securely negotiate the IPsec pair of SAs r Phase 1 has two modes: aggressive mode and main mode m Aggressive mode uses fewer messages m Main mode provides identity protection and is more flexible 35
IKE Phases r IKE has two phases m Phase 1: Establish bi-directional IKE SA • Note: IKE SA different from IPsec SA • Also called ISAKMP security association m Phase 2: ISAKMP is used to securely negotiate the IPsec pair of SAs r Phase 1 has two modes: aggressive mode and main mode m Aggressive mode uses fewer messages m Main mode provides identity protection and is more flexible 35
 IKE lab r Part 4: m IKE with PSK m Transport mode r Part 5: m IKE with certificates m Tunnel mode 36
IKE lab r Part 4: m IKE with PSK m Transport mode r Part 5: m IKE with certificates m Tunnel mode 36
 Summary of IPsec r IKE message exchange for algorithms, secret r r keys, SPI numbers Either the AH or the ESP protocol (or both) The AH protocol provides integrity and source authentication The ESP protocol (with AH) additionally provides encryption IPsec peers can be two end systems, two routers/firewalls, or a router/firewall and an end system 37
Summary of IPsec r IKE message exchange for algorithms, secret r r keys, SPI numbers Either the AH or the ESP protocol (or both) The AH protocol provides integrity and source authentication The ESP protocol (with AH) additionally provides encryption IPsec peers can be two end systems, two routers/firewalls, or a router/firewall and an end system 37


