487f95bbe3767a09766efe111f1aaea7.ppt
- Количество слайдов: 42
 Security-Assessment. com A Step into the Computer Underground “By Understanding The Enemy We Are Better Prepared To Defend Ourselves” by Brett Moore Copyright Security-Assessment. com 2003
Security-Assessment. com A Step into the Computer Underground “By Understanding The Enemy We Are Better Prepared To Defend Ourselves” by Brett Moore Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Hackers, Crackers, Phreakers, Black Hats Ø Males and Females, All Ages Ø Computer Underground Ø Warez Pirates Ø Warez == Slang For Pirated Software Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Hackers, Crackers, Phreakers, Black Hats Ø Males and Females, All Ages Ø Computer Underground Ø Warez Pirates Ø Warez == Slang For Pirated Software Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Internet Gives Worldwide Access To People With Similar Interests Ø Credit Cards Ø Free Software Ø DVD Copies Ø Pornography Ø MP 3 Music Files Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Internet Gives Worldwide Access To People With Similar Interests Ø Credit Cards Ø Free Software Ø DVD Copies Ø Pornography Ø MP 3 Music Files Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Dialup access with modems Ø BBS (Bulletin Board Systems) Ø Online Handles (Alias) Ø Leave Messages And Trade Files Ø Free Long Distance Phone Calls Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Dialup access with modems Ø BBS (Bulletin Board Systems) Ø Online Handles (Alias) Ø Leave Messages And Trade Files Ø Free Long Distance Phone Calls Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Stolen Credit Cards Ø Stolen Calling Card Numbers Ø Hacked PBX Systems Ø Voice Mail Systems Ø Blueboxing Ø MF Tones To ‘Talk’ To The Exchanges Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Stolen Credit Cards Ø Stolen Calling Card Numbers Ø Hacked PBX Systems Ø Voice Mail Systems Ø Blueboxing Ø MF Tones To ‘Talk’ To The Exchanges Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Phone Hackers == Phreaker Ø Explored The Phone Systems Ø John Drapner (Captain Crunch) Ø 1960’s, 1970’s => 1990’s Ø 2600 Hertz MF Tone Ø KP 2 + CC + AC + # + ST Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Phone Hackers == Phreaker Ø Explored The Phone Systems Ø John Drapner (Captain Crunch) Ø 1960’s, 1970’s => 1990’s Ø 2600 Hertz MF Tone Ø KP 2 + CC + AC + # + ST Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Software Has Been Pirated Since Before The Commodore 64 Ø Amiga, Mid 1980’s Ø Warez Scene (Community) Ø Software Piracy (Warez Trading) Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Software Has Been Pirated Since Before The Commodore 64 Ø Amiga, Mid 1980’s Ø Warez Scene (Community) Ø Software Piracy (Warez Trading) Copyright Security-Assessment. com 2003
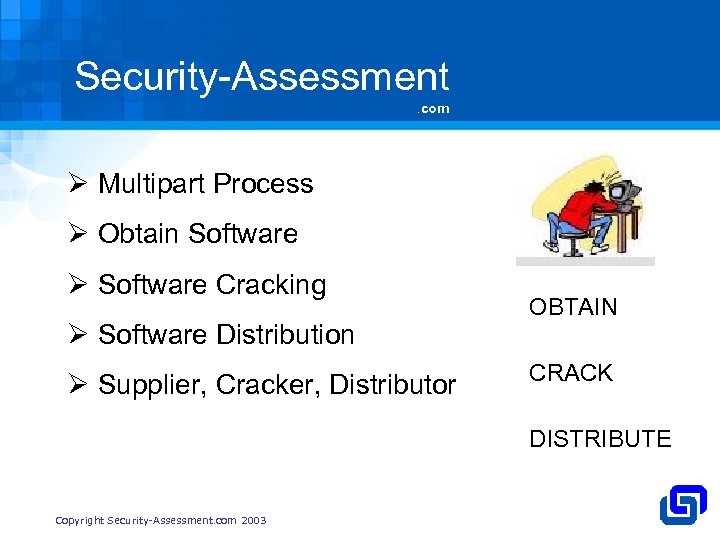 Security-Assessment. com Ø Multipart Process Ø Obtain Software Ø Software Cracking Ø Software Distribution Ø Supplier, Cracker, Distributor OBTAIN CRACK DISTRIBUTE Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Multipart Process Ø Obtain Software Ø Software Cracking Ø Software Distribution Ø Supplier, Cracker, Distributor OBTAIN CRACK DISTRIBUTE Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Phreakers Provided Free Phone Calls Ø BBS Sites For Distribution Ø HQ’s, Group Distribution Sites Ø Courier Groups Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Phreakers Provided Free Phone Calls Ø BBS Sites For Distribution Ø HQ’s, Group Distribution Sites Ø Courier Groups Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Not Just Geeky Kids • RAZOR 1911 Ø Organised Groups • THC Ø Different Countries Ø Peer Respect And Recognition Ø To Be The Top Group Ø Since Early 1980’s Copyright Security-Assessment. com 2003 • TRSI • FAIRLIGHT • PARADIGM • 4 -D (NZ)
Security-Assessment. com Ø Not Just Geeky Kids • RAZOR 1911 Ø Organised Groups • THC Ø Different Countries Ø Peer Respect And Recognition Ø To Be The Top Group Ø Since Early 1980’s Copyright Security-Assessment. com 2003 • TRSI • FAIRLIGHT • PARADIGM • 4 -D (NZ)
 Security-Assessment. com Ø Internet Savvy Ø Replaced BBS’s With FTP And Web Sites Ø New Groups Formed Ø Older Groups Expanded Ø Groups Within Groups Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Internet Savvy Ø Replaced BBS’s With FTP And Web Sites Ø New Groups Formed Ø Older Groups Expanded Ø Groups Within Groups Copyright Security-Assessment. com 2003
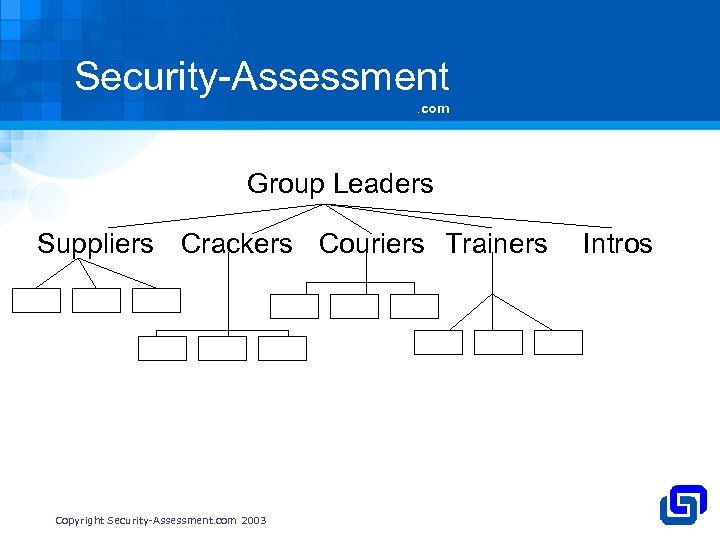 Security-Assessment. com Group Leaders Suppliers Crackers Couriers Trainers Copyright Security-Assessment. com 2003 Intros
Security-Assessment. com Group Leaders Suppliers Crackers Couriers Trainers Copyright Security-Assessment. com 2003 Intros
 Security-Assessment. com Ø Latest Technology Ø Encrypted High Speed Links Ø High Speed Is Expensive Ø Hacking Techniques To Steal Bandwith From Others Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Latest Technology Ø Encrypted High Speed Links Ø High Speed Is Expensive Ø Hacking Techniques To Steal Bandwith From Others Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Scanners / Site Finders Ø Unprotected FTP Sites Ø Vulnerable Web Servers Ø Distros – Private Distribution Ø Pubstros – Public Distribution Ø Scanstros – For More Scanning Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Scanners / Site Finders Ø Unprotected FTP Sites Ø Vulnerable Web Servers Ø Distros – Private Distribution Ø Pubstros – Public Distribution Ø Scanstros – For More Scanning Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Exploit Tools Allow Even Novice Hackers To Compromise Systems Ø Available On The Internet Ø Step By Step Instructions Ø Access To More Tools Ø “Just Press Go” Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Exploit Tools Allow Even Novice Hackers To Compromise Systems Ø Available On The Internet Ø Step By Step Instructions Ø Access To More Tools Ø “Just Press Go” Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Unlimited Time Resources Ø FXP Transfers Ø Automated Scanning Ø Constantly Scanning Ø Every Internet Connection Will Get Scanned Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Unlimited Time Resources Ø FXP Transfers Ø Automated Scanning Ø Constantly Scanning Ø Every Internet Connection Will Get Scanned Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Not Just Games Ø Software Applications Ø DVD Movies Ø Music MP 3’s Ø Pornographic Images And Videos Ø Distribution Process Is The Same Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Not Just Games Ø Software Applications Ø DVD Movies Ø Music MP 3’s Ø Pornographic Images And Videos Ø Distribution Process Is The Same Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø A Virus Normally Requires Human Action To Spread Ø May Already Be Infected Before Definitions Available Ø Shutdown Anti Virus And Firewall Programs Ø Some Can Auto Execute Copyright Security-Assessment. com 2003
Security-Assessment. com Ø A Virus Normally Requires Human Action To Spread Ø May Already Be Infected Before Definitions Available Ø Shutdown Anti Virus And Firewall Programs Ø Some Can Auto Execute Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Internet Worms Execute And Spread Automatically Ø Search For An Infect Thousands Of Computers Ø Old Worms Of 2001 Are Still Active Sadmind, Code Red, Nimda ØNewer Worms SQL Slammer, Apache Slapper Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Internet Worms Execute And Spread Automatically Ø Search For An Infect Thousands Of Computers Ø Old Worms Of 2001 Are Still Active Sadmind, Code Red, Nimda ØNewer Worms SQL Slammer, Apache Slapper Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Hackers Use Virus And Worm Technology Ø Virus Creation Kits Ø Virus Scanners Are Important Ø Employee Education About The Dangers Of Running Attachments Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Hackers Use Virus And Worm Technology Ø Virus Creation Kits Ø Virus Scanners Are Important Ø Employee Education About The Dangers Of Running Attachments Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Backdoor Or Trojan Allows Access After A System Is Patched Ø Run Commands, View And Edit Files Ø Scanning Ø Denial Of Service Attacks Ø Proxies To Bounce Communications Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Backdoor Or Trojan Allows Access After A System Is Patched Ø Run Commands, View And Edit Files Ø Scanning Ø Denial Of Service Attacks Ø Proxies To Bounce Communications Copyright Security-Assessment. com 2003
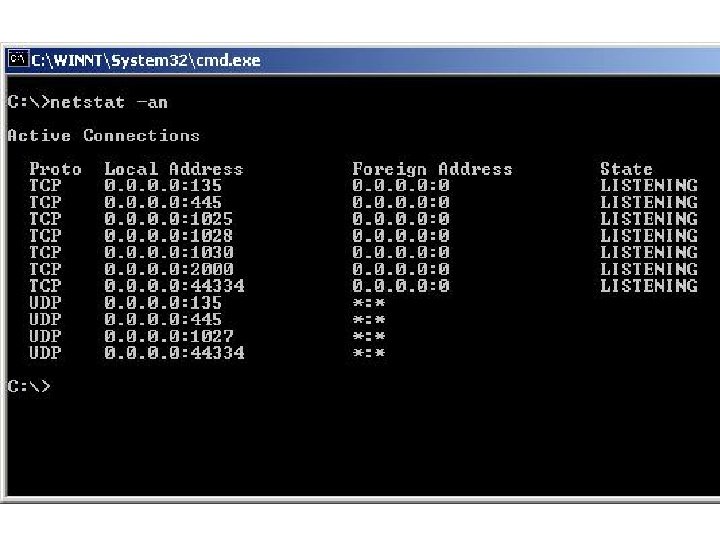
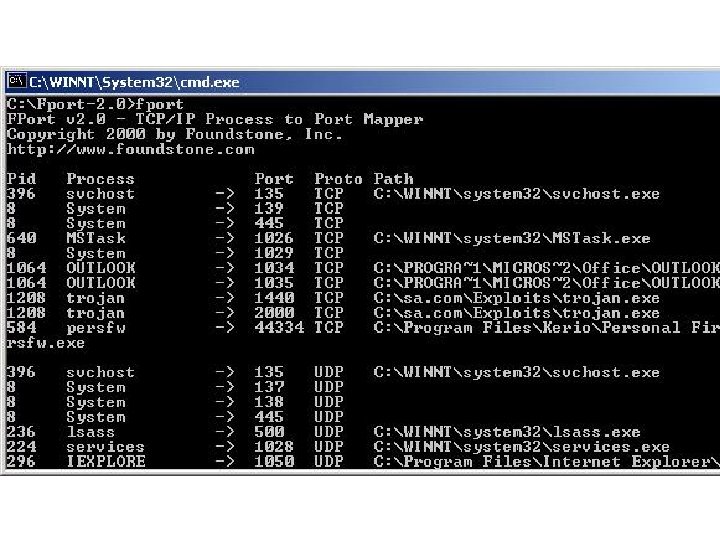
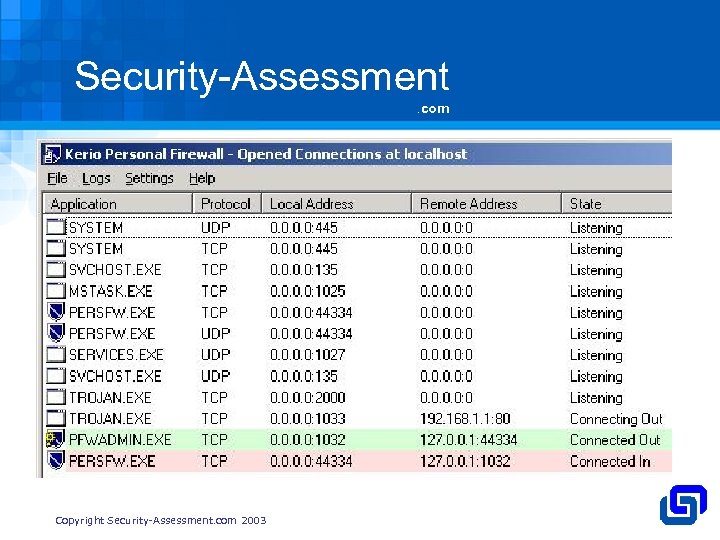
 Security-Assessment. com Ø Edit Web Script Or Create New Ø Rootkits, Hard To Detect Ø Listening Trojans Can Be Detected Ø Netstat, Fport, Personal Firewalls Ø Communication Over HTTP, TCP, ICMP Ø Communication Encrypted Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Edit Web Script Or Create New Ø Rootkits, Hard To Detect Ø Listening Trojans Can Be Detected Ø Netstat, Fport, Personal Firewalls Ø Communication Over HTTP, TCP, ICMP Ø Communication Encrypted Copyright Security-Assessment. com 2003
 Security-Assessment. com Copyright Security-Assessment. com 2003
Security-Assessment. com Copyright Security-Assessment. com 2003
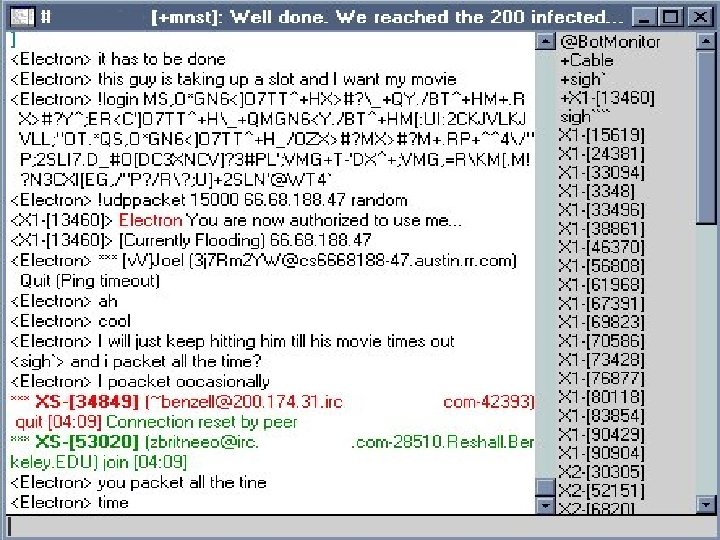
 Security-Assessment. com Ø IRC To Communicate With Trojans Ø Zombie Computer – Under The Control Of A Hacker Ø Trojan Connects To IRC And Awaits Commands Ø Hacker Does Not Need To Know The IP Of The Compromised Computer Copyright Security-Assessment. com 2003
Security-Assessment. com Ø IRC To Communicate With Trojans Ø Zombie Computer – Under The Control Of A Hacker Ø Trojan Connects To IRC And Awaits Commands Ø Hacker Does Not Need To Know The IP Of The Compromised Computer Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø 0 Day – Hole That The Vendor Is Not Aware Of Ø No Patches Ø White Hat == Good Guys Ø Black Hat == Bad Guys Ø Responsible Disclosure Of Security Holes Copyright Security-Assessment. com 2003
Security-Assessment. com Ø 0 Day – Hole That The Vendor Is Not Aware Of Ø No Patches Ø White Hat == Good Guys Ø Black Hat == Bad Guys Ø Responsible Disclosure Of Security Holes Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø March 2003, 0 Day Exploit In Use Ø Attack On US Military Web Site Ø Webdav – Distributed Authoring And Versioning Ø Webdav – Enabled By Default Copyright Security-Assessment. com 2003
Security-Assessment. com Ø March 2003, 0 Day Exploit In Use Ø Attack On US Military Web Site Ø Webdav – Distributed Authoring And Versioning Ø Webdav – Enabled By Default Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Ensure Servers Are Up To Date With Security Patches Ø Subscribe To Security Newsletters Ø Conduct External Penetration Testing Ø Running A Bare Minimum Server Ø All Extra Servives And Files Should Be REMOVED Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Ensure Servers Are Up To Date With Security Patches Ø Subscribe To Security Newsletters Ø Conduct External Penetration Testing Ø Running A Bare Minimum Server Ø All Extra Servives And Files Should Be REMOVED Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Defence In Depth – A Multi-layered Approach To Security Ø Do Not Rely On The First Fence! Ø Web Servers Are The Most Commonly Hacked Servers Ø Restrict Outbound And Internally Directed Traffic With Firewalls Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Defence In Depth – A Multi-layered Approach To Security Ø Do Not Rely On The First Fence! Ø Web Servers Are The Most Commonly Hacked Servers Ø Restrict Outbound And Internally Directed Traffic With Firewalls Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Script Kiddies – Little Or No Real Hacking Skill Ø Elite Hackers – Able To Create Exploit Tools, Worms, Rootkits And More Ø Elite Hackers Will Share With Other Group Memebers Ø Script Kiddies Gain Access To Elite Hacking Tools Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Script Kiddies – Little Or No Real Hacking Skill Ø Elite Hackers – Able To Create Exploit Tools, Worms, Rootkits And More Ø Elite Hackers Will Share With Other Group Memebers Ø Script Kiddies Gain Access To Elite Hacking Tools Copyright Security-Assessment. com 2003
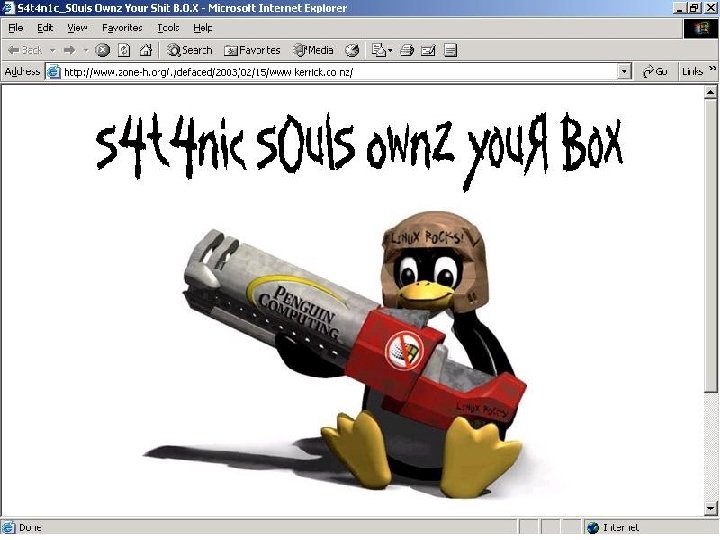
 Security-Assessment. com Ø Web Site Defacement – When The Main Page Is Changed Ø Cyber-Graffiti Ø Over 250 NZ Defacements So Far In 2003 Ø Zone-H. org Web Site Defacement Mirror Ø WWW. CCIP. GOVT. NZ Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Web Site Defacement – When The Main Page Is Changed Ø Cyber-Graffiti Ø Over 250 NZ Defacements So Far In 2003 Ø Zone-H. org Web Site Defacement Mirror Ø WWW. CCIP. GOVT. NZ Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Denial Of Service Attacks – When Large Amounts Of Fake Traffic Cause Another Internet Connection To Become Unavailable Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Denial Of Service Attacks – When Large Amounts Of Fake Traffic Cause Another Internet Connection To Become Unavailable Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Information Theft Ø Credit Card Fraud Ø Identity Theft Ø Industrial Espionage Ø Blackmail / Extortion Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Information Theft Ø Credit Card Fraud Ø Identity Theft Ø Industrial Espionage Ø Blackmail / Extortion Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø Cost Is Difficult To Estimate Ø Charged For FTP And Do. S Traffic Ø Email And Internet Access May Need To Be Shut Down Ø Web Site Defacement Could Lead To Loss Of Customer Confidence Copyright Security-Assessment. com 2003
Security-Assessment. com Ø Cost Is Difficult To Estimate Ø Charged For FTP And Do. S Traffic Ø Email And Internet Access May Need To Be Shut Down Ø Web Site Defacement Could Lead To Loss Of Customer Confidence Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø NZ Has Hackers! Ø Ve. No. Mou. S – Linked With Overseas Groups, Arrested And Charged For Hacking Local Companies Ø Crimes Ammendment Bill No 6 Ø Problems Will Arise Through Jurisdictional Disputes Across Countries Copyright Security-Assessment. com 2003
Security-Assessment. com Ø NZ Has Hackers! Ø Ve. No. Mou. S – Linked With Overseas Groups, Arrested And Charged For Hacking Local Companies Ø Crimes Ammendment Bill No 6 Ø Problems Will Arise Through Jurisdictional Disputes Across Countries Copyright Security-Assessment. com 2003
 Security-Assessment. com Ø International Problem Ø International Hackers Hack Internationally Ø No Borders, No Distance Ø Size Doesn’t Matter BECAUSE THEY CAN! Copyright Security-Assessment. com 2003
Security-Assessment. com Ø International Problem Ø International Hackers Hack Internationally Ø No Borders, No Distance Ø Size Doesn’t Matter BECAUSE THEY CAN! Copyright Security-Assessment. com 2003
 Security-Assessment. com Presentation Slides And Speech Available For Download From: http: //www. security-assessment. com Copyright Security-Assessment. com 2003
Security-Assessment. com Presentation Slides And Speech Available For Download From: http: //www. security-assessment. com Copyright Security-Assessment. com 2003


