38144022466a89984876c216731bae46.ppt
- Количество слайдов: 33
 Security and Systems
Security and Systems
 Three tenets of security l Confidentiality l Integrity l Availability
Three tenets of security l Confidentiality l Integrity l Availability
 e-Security –the problem is real l 90% of companies surveyed by the FBI have detected cyber attacks recently l Disgruntled employees, industrial espionage, and data theft are responsible for 70 -80% of security breaches l Increase in external threats from hackers, ex-employees, competitors and cyber terrorists l The rise of “Script Kiddies” - Hackers who do not target specific organizations, but run scripts scanning the net for ANY vulnerable network
e-Security –the problem is real l 90% of companies surveyed by the FBI have detected cyber attacks recently l Disgruntled employees, industrial espionage, and data theft are responsible for 70 -80% of security breaches l Increase in external threats from hackers, ex-employees, competitors and cyber terrorists l The rise of “Script Kiddies” - Hackers who do not target specific organizations, but run scripts scanning the net for ANY vulnerable network
 Security Myths l Nobody would want our data. l Who knows us? We are anonymous l There is no danger to my network at all. l I am not on the Internet, I am safe. l I don’t need any security devices. I have a Firewall l I have an antivirus on my server. I am safe l All our employees are very committed & reliable!
Security Myths l Nobody would want our data. l Who knows us? We are anonymous l There is no danger to my network at all. l I am not on the Internet, I am safe. l I don’t need any security devices. I have a Firewall l I have an antivirus on my server. I am safe l All our employees are very committed & reliable!
 Know your IT law l Cyber crimes – l Interception by Government – l Hacking , damage to computer source code, publishing lascivious information in an electronic form, breach of privacy / confidentiality, publishing digital signature, etc. intercept any information transmitted through any computer resource if the same is necessary in the interest of the sovereignty or integrity of India, Digital Signatures legally valid and enforceable.
Know your IT law l Cyber crimes – l Interception by Government – l Hacking , damage to computer source code, publishing lascivious information in an electronic form, breach of privacy / confidentiality, publishing digital signature, etc. intercept any information transmitted through any computer resource if the same is necessary in the interest of the sovereignty or integrity of India, Digital Signatures legally valid and enforceable.
 Know your IT law l Authentication of electronic records in India shall be effected by the use of asymmetric crypto system and hash function l If someone uses your network to attack an external network and the attacked complains, you are liable to be penalized l Companies must have a detailed I T Security Policy in tune with the mandatory specific provisions of the IT Act and IT Rules.
Know your IT law l Authentication of electronic records in India shall be effected by the use of asymmetric crypto system and hash function l If someone uses your network to attack an external network and the attacked complains, you are liable to be penalized l Companies must have a detailed I T Security Policy in tune with the mandatory specific provisions of the IT Act and IT Rules.
 Threats to data
Threats to data
 Protectable Data assets l l Business Information – contracts, SLAs, financial data, customer details, etc Intellectual property – source codes, inventions, research papers, etc National secrets E-commerce
Protectable Data assets l l Business Information – contracts, SLAs, financial data, customer details, etc Intellectual property – source codes, inventions, research papers, etc National secrets E-commerce
 Threats to data l l l l Accessed by External hackers Divulged by ignorant employees Corrupted by virus attacks Hardware failures Inadequate access controls Badly designed applications Clear transmission over public internet Last but not the least system administrators !!
Threats to data l l l l Accessed by External hackers Divulged by ignorant employees Corrupted by virus attacks Hardware failures Inadequate access controls Badly designed applications Clear transmission over public internet Last but not the least system administrators !!
 Types of External Attacks l l l l Malicious code attacks Corporate espionage Web graffiti Denial-of-service Database hacks Installing Back doors Identity Theft
Types of External Attacks l l l l Malicious code attacks Corporate espionage Web graffiti Denial-of-service Database hacks Installing Back doors Identity Theft
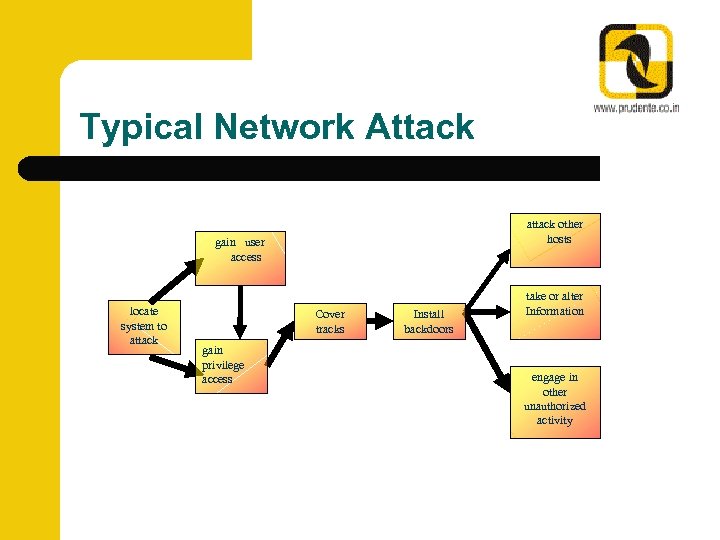 Typical Network Attack attack other hosts gain user access locate system to attack Cover tracks gain privilege access Install backdoors take or alter Information engage in other unauthorized activity
Typical Network Attack attack other hosts gain user access locate system to attack Cover tracks gain privilege access Install backdoors take or alter Information engage in other unauthorized activity
 Methods adopted in attacks l l l l l Pinging Sniffing Probing Flooding Hacking Cracking Scripting Buffer Overflow Reverse engineering
Methods adopted in attacks l l l l l Pinging Sniffing Probing Flooding Hacking Cracking Scripting Buffer Overflow Reverse engineering
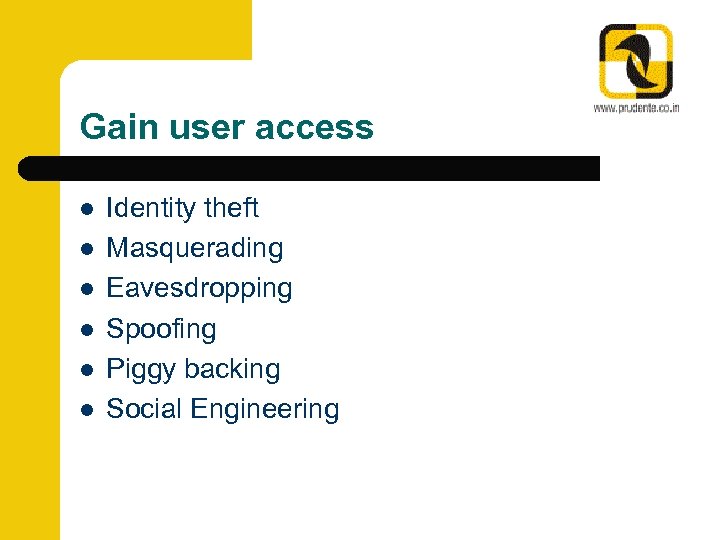 Gain user access l l l Identity theft Masquerading Eavesdropping Spoofing Piggy backing Social Engineering
Gain user access l l l Identity theft Masquerading Eavesdropping Spoofing Piggy backing Social Engineering
 Alter or steal information l l Sniffing Man-in-the middle attacks Cookies Sabotage by employees
Alter or steal information l l Sniffing Man-in-the middle attacks Cookies Sabotage by employees
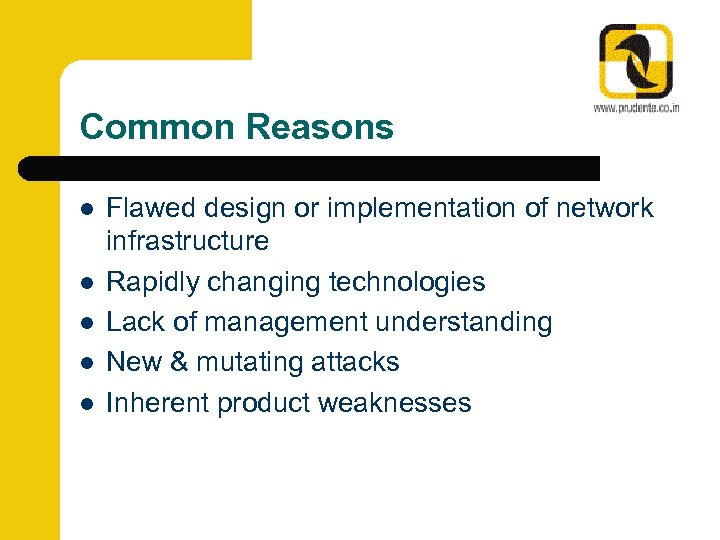 Common Reasons l l l Flawed design or implementation of network infrastructure Rapidly changing technologies Lack of management understanding New & mutating attacks Inherent product weaknesses
Common Reasons l l l Flawed design or implementation of network infrastructure Rapidly changing technologies Lack of management understanding New & mutating attacks Inherent product weaknesses
 Internal Threats l l l Unrestricted access to internal systems Bad security practices Ignorant users Lack of management understanding New & mutating attacks Inherent product weaknesses
Internal Threats l l l Unrestricted access to internal systems Bad security practices Ignorant users Lack of management understanding New & mutating attacks Inherent product weaknesses
 Protection mechanisms
Protection mechanisms
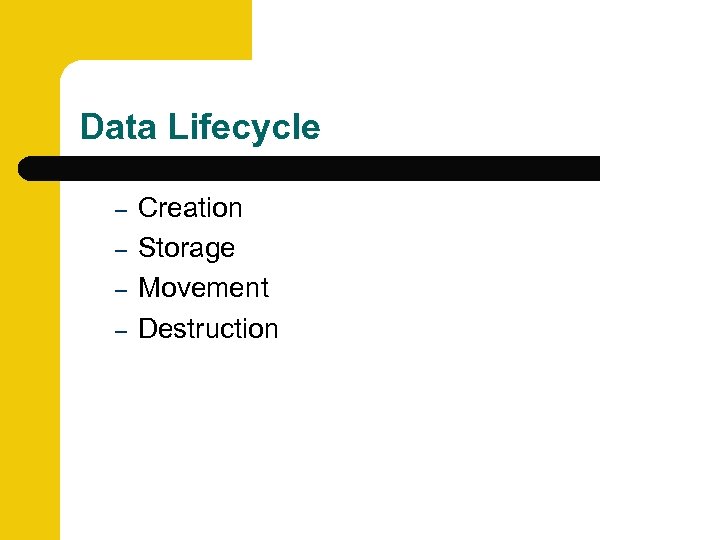 Data Lifecycle – – Creation Storage Movement Destruction
Data Lifecycle – – Creation Storage Movement Destruction
 Key security elements – – – Security Policy Identity management Robust Perimeter Security Storage Security Secure Transmission of data Good Security Practices
Key security elements – – – Security Policy Identity management Robust Perimeter Security Storage Security Secure Transmission of data Good Security Practices
 Identity l l Accurate and positive identification of network users, hosts, applications, services, and resources. Standard technologies – – l Kerberos one-time password Technologies used – – – digital certificates smart cards directory services (e. g. LDAP, ADS)
Identity l l Accurate and positive identification of network users, hosts, applications, services, and resources. Standard technologies – – l Kerberos one-time password Technologies used – – – digital certificates smart cards directory services (e. g. LDAP, ADS)
 Perimeter Security l l Deals with controlling data that is passed between LAN and public internet Perimeter is controlled by – – – Routers and switches Firewalls IDS / IPS Antivirus URL Filters Network Traffic Analyzers
Perimeter Security l l Deals with controlling data that is passed between LAN and public internet Perimeter is controlled by – – – Routers and switches Firewalls IDS / IPS Antivirus URL Filters Network Traffic Analyzers
 Secure transmission l l The ability to provide authenticated, confidential communication between systems Data privacy is achieved by – – Layer 2 Tunneling Protocol (L 2 TP) IPsec Data Encryption PGP
Secure transmission l l The ability to provide authenticated, confidential communication between systems Data privacy is achieved by – – Layer 2 Tunneling Protocol (L 2 TP) IPsec Data Encryption PGP
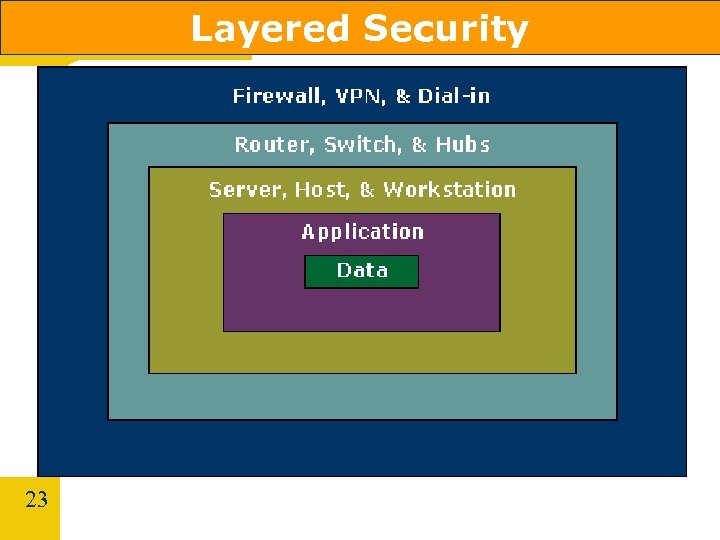 Layered Security 23
Layered Security 23
 Security Standards / Laws l l l BS 7799 / IS 17799 Data Protection Act HIPAA SOX IT Act (Indian cyberlaws)
Security Standards / Laws l l l BS 7799 / IS 17799 Data Protection Act HIPAA SOX IT Act (Indian cyberlaws)
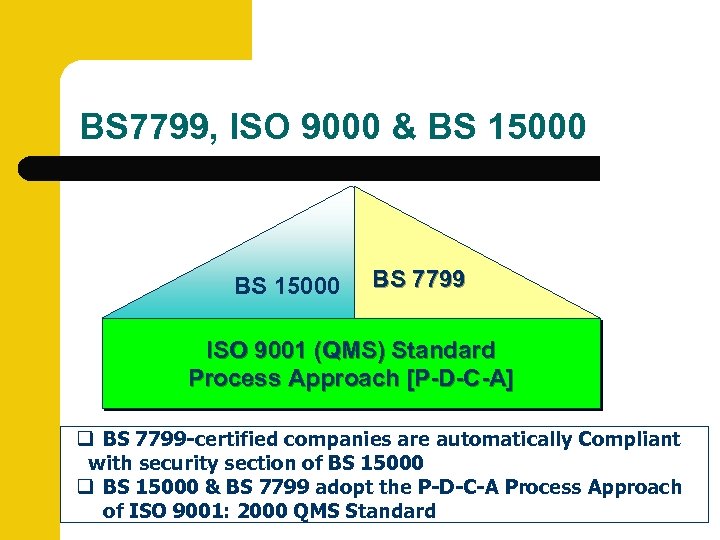 BS 7799, ISO 9000 & BS 15000 BS 7799 ISO 9001 (QMS) Standard Process Approach [P-D-C-A] q BS 7799 -certified companies are automatically Compliant with security section of BS 15000 q BS 15000 & BS 7799 adopt the P-D-C-A Process Approach of ISO 9001: 2000 QMS Standard
BS 7799, ISO 9000 & BS 15000 BS 7799 ISO 9001 (QMS) Standard Process Approach [P-D-C-A] q BS 7799 -certified companies are automatically Compliant with security section of BS 15000 q BS 15000 & BS 7799 adopt the P-D-C-A Process Approach of ISO 9001: 2000 QMS Standard
 Policy Management l l l Defining a clear security objective Articulating clear policy Implemented by suitable procedures Audited regularly to ensure compliance Training users Improvising the procedures
Policy Management l l l Defining a clear security objective Articulating clear policy Implemented by suitable procedures Audited regularly to ensure compliance Training users Improvising the procedures
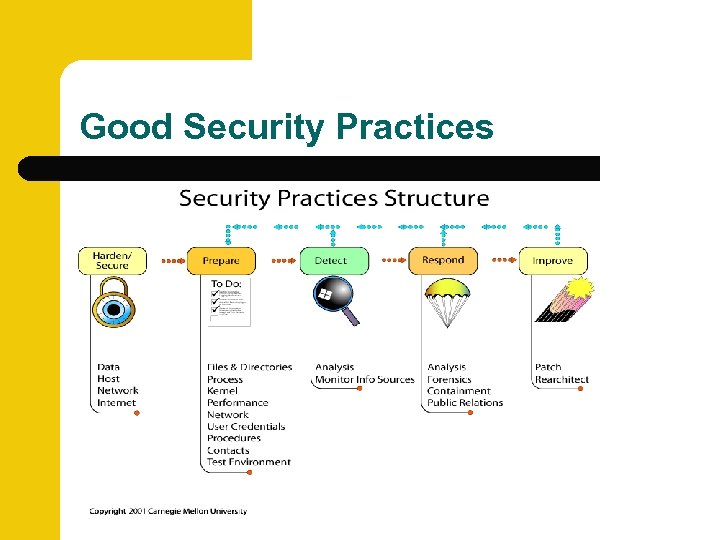 Good Security Practices
Good Security Practices
 Proactive measures
Proactive measures
 Testing methods – Vulnerability assessment – Penetration testing – Detection measures – Response measures
Testing methods – Vulnerability assessment – Penetration testing – Detection measures – Response measures
 Best Practices l l l Understanding of the business needs A security mission statement Identification & Risk Analysis on Data A strong commitment from upper management to allocate necessary resources Clearly defined implemented and documented security policies and procedures
Best Practices l l l Understanding of the business needs A security mission statement Identification & Risk Analysis on Data A strong commitment from upper management to allocate necessary resources Clearly defined implemented and documented security policies and procedures
 Best Practices l l l A suite of host and network based security auditing and improvement tools A security awareness program that reaches everyone in the organization A dedicated team of trained security professionals and consultants to make it all happen
Best Practices l l l A suite of host and network based security auditing and improvement tools A security awareness program that reaches everyone in the organization A dedicated team of trained security professionals and consultants to make it all happen
 To conclude l l l No technology used to protect your organization is 100% hackerproof Good policies drive good implementation Best policies without necessary awareness among personnel is in vain Security is not a one-size-fits-all solution. Security of organization assets is everyone’s responsibility.
To conclude l l l No technology used to protect your organization is 100% hackerproof Good policies drive good implementation Best policies without necessary awareness among personnel is in vain Security is not a one-size-fits-all solution. Security of organization assets is everyone’s responsibility.
 Prudenté Solution Pvt Ltd Phone: 080 - 30667171 email: srimathi@prudente. co. in
Prudenté Solution Pvt Ltd Phone: 080 - 30667171 email: srimathi@prudente. co. in


