d037c4b2a12784dd6ba4205bbe8c4ac8.ppt
- Количество слайдов: 37
 Security and Privacy in an Online Vehicle Infrastructure Erhan J. Kartaltepe, MCPD Lead Consultant, Denim Group Ltd. July 23 th, 2008
Security and Privacy in an Online Vehicle Infrastructure Erhan J. Kartaltepe, MCPD Lead Consultant, Denim Group Ltd. July 23 th, 2008
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 1
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 1
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 2
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 2
 Intelligent Transportation Systems (ITS) • ITS add information and communications technology to – transportation infrastructure – Individual and fleet vehicles – traffic management centers (TMC) • The Federal Highway Authority – wanted ITS deployments in 75 major cities – wanted them in 10 years (from January 2000) – got what they wanted (over 100 “major” cities so far) 3
Intelligent Transportation Systems (ITS) • ITS add information and communications technology to – transportation infrastructure – Individual and fleet vehicles – traffic management centers (TMC) • The Federal Highway Authority – wanted ITS deployments in 75 major cities – wanted them in 10 years (from January 2000) – got what they wanted (over 100 “major” cities so far) 3
 What are ITS Systems? • To a civil engineer • To an electrical engineer • To a software engineer 4
What are ITS Systems? • To a civil engineer • To an electrical engineer • To a software engineer 4
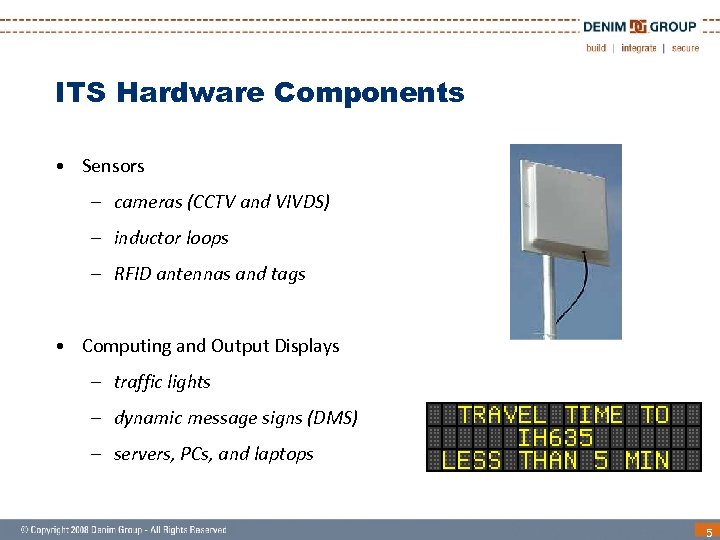 ITS Hardware Components • Sensors – cameras (CCTV and VIVDS) – inductor loops – RFID antennas and tags • Computing and Output Displays – traffic lights – dynamic message signs (DMS) – servers, PCs, and laptops 5
ITS Hardware Components • Sensors – cameras (CCTV and VIVDS) – inductor loops – RFID antennas and tags • Computing and Output Displays – traffic lights – dynamic message signs (DMS) – servers, PCs, and laptops 5
 ITS Software Components • Software Applications Used by the Public – travel times – flow management – passive (informational) mapping • Software Applications Used by the TMCs – incident management – data archiving – active (controller) mapping • Plenty More on Both Sides 6
ITS Software Components • Software Applications Used by the Public – travel times – flow management – passive (informational) mapping • Software Applications Used by the TMCs – incident management – data archiving – active (controller) mapping • Plenty More on Both Sides 6
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 7
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 7
 Software Standards • Communication between systems are generally proprietary • Some standards exist under NTCIP (National Transportation Communications for ITS Protocol) – DMS sign communication – CCTV camera high-level control – C 2 C applications • Many NTCIP protocols use XML and HTTP-like communication 8
Software Standards • Communication between systems are generally proprietary • Some standards exist under NTCIP (National Transportation Communications for ITS Protocol) – DMS sign communication – CCTV camera high-level control – C 2 C applications • Many NTCIP protocols use XML and HTTP-like communication 8
 NTCIP Protocols • National Transportation Communications for ITS Protocol (NTCIP) – Comprised of working groups to standardize protocols – Both hardware and software protocols – Working body for message format and markup • Standardization – Goal of NTCIP working groups is to get work ratified – Protocols tend to be request or request-response – Messages use simple proprietary markups • Now tend to use XML 9
NTCIP Protocols • National Transportation Communications for ITS Protocol (NTCIP) – Comprised of working groups to standardize protocols – Both hardware and software protocols – Working body for message format and markup • Standardization – Goal of NTCIP working groups is to get work ratified – Protocols tend to be request or request-response – Messages use simple proprietary markups • Now tend to use XML 9
![Example—Multi Message Format • [128][30][2][TRAVEL TIME TO][LF][CULEBRA RD] [LF][5 -7 MINUTES][EL] • Not self-describing Example—Multi Message Format • [128][30][2][TRAVEL TIME TO][LF][CULEBRA RD] [LF][5 -7 MINUTES][EL] • Not self-describing](https://present5.com/presentation/d037c4b2a12784dd6ba4205bbe8c4ac8/image-11.jpg) Example—Multi Message Format • [128][30][2][TRAVEL TIME TO][LF][CULEBRA RD] [LF][5 -7 MINUTES][EL] • Not self-describing • Request-only protocol • No security built into the schema 10
Example—Multi Message Format • [128][30][2][TRAVEL TIME TO][LF][CULEBRA RD] [LF][5 -7 MINUTES][EL] • Not self-describing • Request-only protocol • No security built into the schema 10
![Multi Message Format Hardware Attack • [1][30][2][LEFT LANE CLOSED][LF][NEXT TWO MILES] [LF][CHANGE LANES][EL] • Multi Message Format Hardware Attack • [1][30][2][LEFT LANE CLOSED][LF][NEXT TWO MILES] [LF][CHANGE LANES][EL] •](https://present5.com/presentation/d037c4b2a12784dd6ba4205bbe8c4ac8/image-12.jpg) Multi Message Format Hardware Attack • [1][30][2][LEFT LANE CLOSED][LF][NEXT TWO MILES] [LF][CHANGE LANES][EL] • Attack only works per sign • Physical access control limits value of attack • Proprietary manufacturer’s hardware prevents “scalability” 11
Multi Message Format Hardware Attack • [1][30][2][LEFT LANE CLOSED][LF][NEXT TWO MILES] [LF][CHANGE LANES][EL] • Attack only works per sign • Physical access control limits value of attack • Proprietary manufacturer’s hardware prevents “scalability” 11
![Multi Message Format Software Attack • <xml><token>A 39 F 7 ED 2</token><message><mfr>Gideon </mfr><dms>[1][30][2][LEFT LANE Multi Message Format Software Attack • <xml><token>A 39 F 7 ED 2</token><message><mfr>Gideon </mfr><dms>[1][30][2][LEFT LANE](https://present5.com/presentation/d037c4b2a12784dd6ba4205bbe8c4ac8/image-13.jpg) Multi Message Format Software Attack •
Multi Message Format Software Attack •
 More than Just Informational Systems • Passive Informational Mapping – traffic data – lane closures – weather sensor information • Active Control – TMS Map and main GUI – CCTV Camera control – DMS and LCS control – Police/EMS deployment 13
More than Just Informational Systems • Passive Informational Mapping – traffic data – lane closures – weather sensor information • Active Control – TMS Map and main GUI – CCTV Camera control – DMS and LCS control – Police/EMS deployment 13
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 14
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 14
 Embedded Technology • Currently, ITS is mainly infrastructure-driven – CCTV cameras deployed on road – DMS and LCS over highways – inductor loops in ground – TMC centers as centralized hub • Move ITS to be vehicle-driven – vehicle as mobile all-in-one sensor – cell phone or in-vehicle-navigation system as TMC – wireless communication to transmit data for analysis 15
Embedded Technology • Currently, ITS is mainly infrastructure-driven – CCTV cameras deployed on road – DMS and LCS over highways – inductor loops in ground – TMC centers as centralized hub • Move ITS to be vehicle-driven – vehicle as mobile all-in-one sensor – cell phone or in-vehicle-navigation system as TMC – wireless communication to transmit data for analysis 15
 Locational Technologies • Automated Vehicle Location systems – geopositional systems (GPS) – inertia navigation systems (INS) – cell-phone positioning systems • Convergent technologies in use today – Smart parking (Japan, San Francisco) – City transit and school buses – Police department and EMS vehicles – Fed. Ex and UPS 16
Locational Technologies • Automated Vehicle Location systems – geopositional systems (GPS) – inertia navigation systems (INS) – cell-phone positioning systems • Convergent technologies in use today – Smart parking (Japan, San Francisco) – City transit and school buses – Police department and EMS vehicles – Fed. Ex and UPS 16
 Probe Data Platform • Probe data standards – SAE J 1939 (heavy-duty vehicles) – SAE J 1979 (“regular” vehicles) • • • (a) Probe data is carried on CANbus (b) An onboard unit extracts and send probe/GPS data to a roadside unit (c) Roadside unit packages all messages to an ITS message for TMC (d) TMC accepts the data from roadside units for processing (e) Other applications compute relevant information for end user — mapping — travel times — data archiving — env. systems • (f) Users get updates on internal screen display 17
Probe Data Platform • Probe data standards – SAE J 1939 (heavy-duty vehicles) – SAE J 1979 (“regular” vehicles) • • • (a) Probe data is carried on CANbus (b) An onboard unit extracts and send probe/GPS data to a roadside unit (c) Roadside unit packages all messages to an ITS message for TMC (d) TMC accepts the data from roadside units for processing (e) Other applications compute relevant information for end user — mapping — travel times — data archiving — env. systems • (f) Users get updates on internal screen display 17
 Probe Data Platform Deployments • Integrated heavy-duty vehicle probe data into Texas Department of Transportation fleet vehicles • Incorporated the system into commercial fleet management for sparse system deployments (truck stops) in Texas • Applied automated vehicle location technology for municipal heavy-duty vehicles in Florida • More advanced and expensive technologies and routing algorithms in use – shipping companies – large department stores – police and emergency vehicles 18
Probe Data Platform Deployments • Integrated heavy-duty vehicle probe data into Texas Department of Transportation fleet vehicles • Incorporated the system into commercial fleet management for sparse system deployments (truck stops) in Texas • Applied automated vehicle location technology for municipal heavy-duty vehicles in Florida • More advanced and expensive technologies and routing algorithms in use – shipping companies – large department stores – police and emergency vehicles 18
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 19
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 19
 Vehicle Infrastructure Integration • Federal Highway Administration (FHWA) Initiative – fostering software and engineering research – applications research and development • Directly links road vehicles to their physical surroundings – improve safety and efficiency – Vehicle-to-infrastructure (V 2 I) communication – later, vehicle-to-vehicle (V 2 V) communication 20
Vehicle Infrastructure Integration • Federal Highway Administration (FHWA) Initiative – fostering software and engineering research – applications research and development • Directly links road vehicles to their physical surroundings – improve safety and efficiency – Vehicle-to-infrastructure (V 2 I) communication – later, vehicle-to-vehicle (V 2 V) communication 20
 Why VII? • Safety – On US highways (2006): • Nearly 43, 000 fatalities, 3 million injuries • Over $230 billion cost to society • Efficiency – Traffic jams waste time and fuel – In 2007, American drivers lost over four billion hours and six billion gallons of fuel due to heavy traffic congestion • Profit – Safety features and high-tech devices have become product differentiators 21
Why VII? • Safety – On US highways (2006): • Nearly 43, 000 fatalities, 3 million injuries • Over $230 billion cost to society • Efficiency – Traffic jams waste time and fuel – In 2007, American drivers lost over four billion hours and six billion gallons of fuel due to heavy traffic congestion • Profit – Safety features and high-tech devices have become product differentiators 21
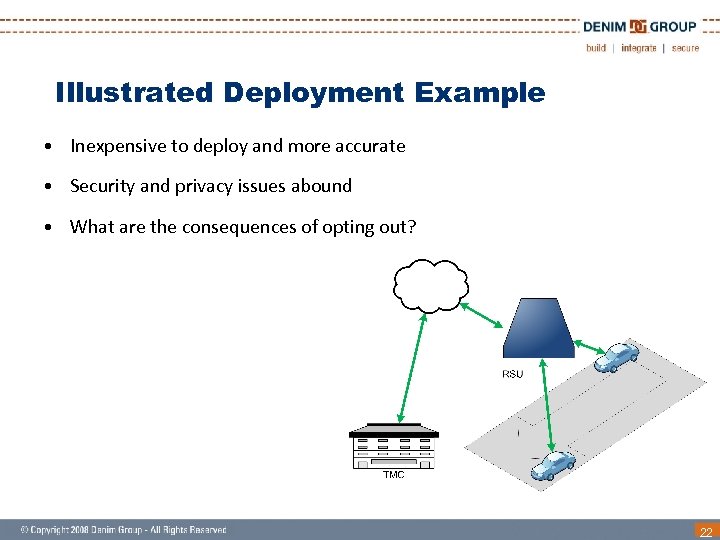 Illustrated Deployment Example • Inexpensive to deploy and more accurate • Security and privacy issues abound • What are the consequences of opting out? 22
Illustrated Deployment Example • Inexpensive to deploy and more accurate • Security and privacy issues abound • What are the consequences of opting out? 22
 Security as an Afterthought • Ubiquity and utility of V 2 I communication make them targets for attack • Attacks may have deadly consequences • VII working group – Over one hundred VII applications – Zero for security 23
Security as an Afterthought • Ubiquity and utility of V 2 I communication make them targets for attack • Attacks may have deadly consequences • VII working group – Over one hundred VII applications – Zero for security 23
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 24
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 24
 Adversaries • Greedy drivers • Snoops • Pranksters • Industrial insiders • Malicious attackers 25
Adversaries • Greedy drivers • Snoops • Pranksters • Industrial insiders • Malicious attackers 25
 Known Attacks in a New Environment • Distributed Denial of Service (DDo. S) – Attempts to overwhelm network – Dangerous if users rely on the service • Message Suppression Attacks – Drop congestion alerts • Fabrication – Lie about congestion ahead or lie about identity • Alteration Attacks – Replay transmissions to simulate congestion 26
Known Attacks in a New Environment • Distributed Denial of Service (DDo. S) – Attempts to overwhelm network – Dangerous if users rely on the service • Message Suppression Attacks – Drop congestion alerts • Fabrication – Lie about congestion ahead or lie about identity • Alteration Attacks – Replay transmissions to simulate congestion 26
 Authentication and Privacy Challenges • Each vehicle should only have one identity – Prevents spoofed congestion or platoon rerouting – Allows use of external mechanisms for emergency vehicles • Drivers value their privacy – Legal requirements vary from country to country – …and from state to state – …and from city to city 27
Authentication and Privacy Challenges • Each vehicle should only have one identity – Prevents spoofed congestion or platoon rerouting – Allows use of external mechanisms for emergency vehicles • Drivers value their privacy – Legal requirements vary from country to country – …and from state to state – …and from city to city 27
 Availability and Key Distro Challenges • Applications will require real-time responses – Increases vulnerability to DDo. S – Unreliable communication medium, like the “old days” • Key distribution: Manufacturers or Government – Manufacturers requires cooperation, interoperability, user’s trust – Government: Handled at the state level; also requires cooperation and interoperability 28
Availability and Key Distro Challenges • Applications will require real-time responses – Increases vulnerability to DDo. S – Unreliable communication medium, like the “old days” • Key distribution: Manufacturers or Government – Manufacturers requires cooperation, interoperability, user’s trust – Government: Handled at the state level; also requires cooperation and interoperability 28
 Bootstrap and Resiliency Challenges • Initially, only a small number of vehicles will have access – Limited support deployment of infrastructure • Low tolerance for errors implies strong need for resiliency – With so many cars, even if the application works 99. 99999% of the time, it likely will fail on a car in motion – Life-and-death applications must be resilient to this – Focus on prevention, rather than detection and recovery – Safety-related apps may not have margin for driver reaction time 29
Bootstrap and Resiliency Challenges • Initially, only a small number of vehicles will have access – Limited support deployment of infrastructure • Low tolerance for errors implies strong need for resiliency – With so many cars, even if the application works 99. 99999% of the time, it likely will fail on a car in motion – Life-and-death applications must be resilient to this – Focus on prevention, rather than detection and recovery – Safety-related apps may not have margin for driver reaction time 29
 Secure Message Origin • Prevents attacks – Attackers on road cannot spoof vehicles – Attackers cannot modify messages to simulate congestion • Alternately, use entanglement – Each vehicle broadcasts its ID and which vehicles it has passed – Establishes relative ordering – Evaluates report consistency using aggregation
Secure Message Origin • Prevents attacks – Attackers on road cannot spoof vehicles – Attackers cannot modify messages to simulate congestion • Alternately, use entanglement – Each vehicle broadcasts its ID and which vehicles it has passed – Establishes relative ordering – Evaluates report consistency using aggregation
 Anonymization Service • May only need to deliver content to any vehicle, rather than a specific one – Authenticate to anonymization service with permanent ID – Anonymization service can issue a temporary ID • Example environments: toll roads, border facilities – Controlled entrance and exit points – All IDs are issued temporarily by the same authorit
Anonymization Service • May only need to deliver content to any vehicle, rather than a specific one – Authenticate to anonymization service with permanent ID – Anonymization service can issue a temporary ID • Example environments: toll roads, border facilities – Controlled entrance and exit points – All IDs are issued temporarily by the same authorit
 Other Security Primitives • Secure Aggregation – Count vehicles to report congestion – Disregard outliers • Key Establishment – Session keys for vehicle platooning – Session keys for automatic cruise control • Message Authentication and Expiration – Prevent replay attacks – Prevent Sybil attacks
Other Security Primitives • Secure Aggregation – Count vehicles to report congestion – Disregard outliers • Key Establishment – Session keys for vehicle platooning – Session keys for automatic cruise control • Message Authentication and Expiration – Prevent replay attacks – Prevent Sybil attacks
 Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 33
Overview • Intelligent Transportation Systems: A Primer • Vehicle Infrastructure Communication Standards • Embedded Commercial Fleet Vehicle Technology • Vehicle Infrastructure Initiative • Challenges and Security Primitives • Conclusions 33
 Conclusions • ITS systems add information and communications technology to transportation infrastructure, individual and fleet vehicles, and TMCs • ITS systems are distributed in nature, with internal and public-facing access points, and as demand grows, so does the attack surface area • ITS and online vehicle infrastructure have security/privacy vulnerabilities • Weaknesses in common with other web services and apps • Unique weaknesses related to vehicular networks • Potentially fatal losses due to insecure applications 34
Conclusions • ITS systems add information and communications technology to transportation infrastructure, individual and fleet vehicles, and TMCs • ITS systems are distributed in nature, with internal and public-facing access points, and as demand grows, so does the attack surface area • ITS and online vehicle infrastructure have security/privacy vulnerabilities • Weaknesses in common with other web services and apps • Unique weaknesses related to vehicular networks • Potentially fatal losses due to insecure applications 34
 Conclusions • Vehicle networks exist today and are moving from – Fleet vehicles using proprietary and custom units – Individuals’ vehicles using inexpensive, mass-produced on-board units • Adversaries and attacks are rampant — authentication — authorization — privacy — availability — key management —initialization • Security primitives exist and when applied can prevent attacks – VII working group does not build security into standards – Building security in early will prevent serious and possibly fatal attacks 35
Conclusions • Vehicle networks exist today and are moving from – Fleet vehicles using proprietary and custom units – Individuals’ vehicles using inexpensive, mass-produced on-board units • Adversaries and attacks are rampant — authentication — authorization — privacy — availability — key management —initialization • Security primitives exist and when applied can prevent attacks – VII working group does not build security into standards – Building security in early will prevent serious and possibly fatal attacks 35
 Questions? 36
Questions? 36


