9cdbd12558a3d9fa015e9d05cde845ec.ppt
- Количество слайдов: 58
 Security and Cooperation in Wireless Networks http: //secowinet. epfl. ch Chapter 2 – Upcoming networks Generalities Mesh networks Vehicular networks Slides elaborated by Naouel Ben Salem, Panos Papadimitratos, and Maxim Raya © 2007 Levente Buttyán and Jean-Pierre Hubaux
Security and Cooperation in Wireless Networks http: //secowinet. epfl. ch Chapter 2 – Upcoming networks Generalities Mesh networks Vehicular networks Slides elaborated by Naouel Ben Salem, Panos Papadimitratos, and Maxim Raya © 2007 Levente Buttyán and Jean-Pierre Hubaux
 Introduction § Upcoming wireless networks: – Personal communications: • Wireless mesh networks • Hybrid ad hoc networks • Mobile ad hoc networks – – Vehicular networks Sensor networks RFID Mobility in the Internet Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 2/58
Introduction § Upcoming wireless networks: – Personal communications: • Wireless mesh networks • Hybrid ad hoc networks • Mobile ad hoc networks – – Vehicular networks Sensor networks RFID Mobility in the Internet Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 2/58
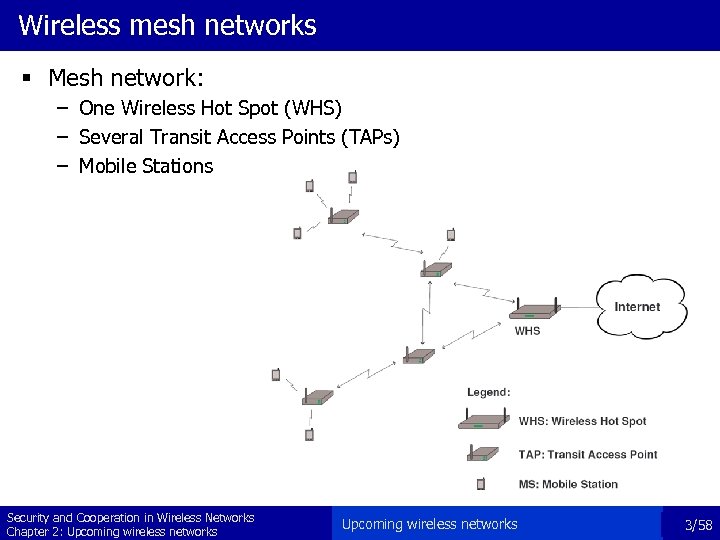 Wireless mesh networks § Mesh network: – One Wireless Hot Spot (WHS) – Several Transit Access Points (TAPs) – Mobile Stations Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 3/58
Wireless mesh networks § Mesh network: – One Wireless Hot Spot (WHS) – Several Transit Access Points (TAPs) – Mobile Stations Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 3/58
 Wireless mesh networks § Easy to deploy: – Single connection point to the Internet § Providing Internet connectivity in a sizable geographic area: – Much lower cost than classic Wi. Fi networks § Fairness and security are closely related § Not yet ready for wide-scale deployment: – Severe capacity and delay constraints – Lack of security guarantees Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 4/58
Wireless mesh networks § Easy to deploy: – Single connection point to the Internet § Providing Internet connectivity in a sizable geographic area: – Much lower cost than classic Wi. Fi networks § Fairness and security are closely related § Not yet ready for wide-scale deployment: – Severe capacity and delay constraints – Lack of security guarantees Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 4/58
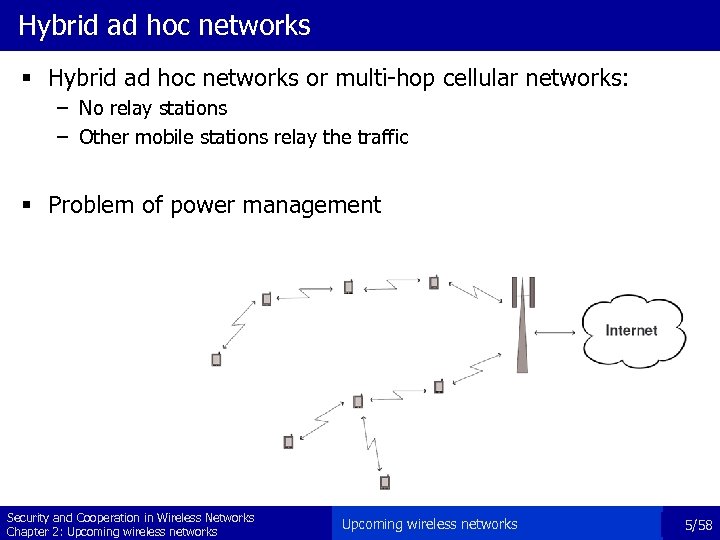 Hybrid ad hoc networks § Hybrid ad hoc networks or multi-hop cellular networks: – No relay stations – Other mobile stations relay the traffic § Problem of power management Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 5/58
Hybrid ad hoc networks § Hybrid ad hoc networks or multi-hop cellular networks: – No relay stations – Other mobile stations relay the traffic § Problem of power management Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 5/58
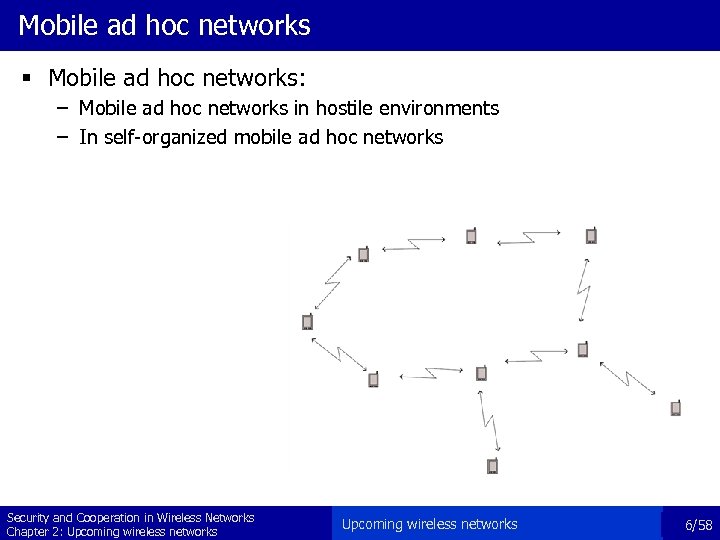 Mobile ad hoc networks § Mobile ad hoc networks: – Mobile ad hoc networks in hostile environments – In self-organized mobile ad hoc networks Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 6/58
Mobile ad hoc networks § Mobile ad hoc networks: – Mobile ad hoc networks in hostile environments – In self-organized mobile ad hoc networks Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 6/58
 Mobile ad hoc networks § Mobile ad hoc networks in hostile environments: – Presence of a strong attacker: military networks – Security challenges: • Secure routing • Prevention of traffic analysis • Resistance of a captured device to reverse engineering and key retrieval. § In self-organized mobile ad hoc networks: – No authority in the initialization phase – Nodes have to figure out how to secure the communications – Selfishness can be a serious issue: • Nodes selfishly refuse to forward packets • Greedily overuse the common channel Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 7/58
Mobile ad hoc networks § Mobile ad hoc networks in hostile environments: – Presence of a strong attacker: military networks – Security challenges: • Secure routing • Prevention of traffic analysis • Resistance of a captured device to reverse engineering and key retrieval. § In self-organized mobile ad hoc networks: – No authority in the initialization phase – Nodes have to figure out how to secure the communications – Selfishness can be a serious issue: • Nodes selfishly refuse to forward packets • Greedily overuse the common channel Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 7/58
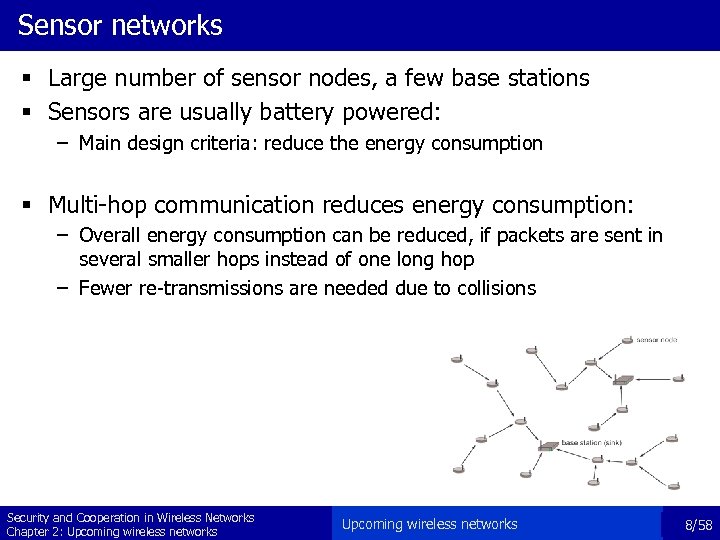 Sensor networks § Large number of sensor nodes, a few base stations § Sensors are usually battery powered: – Main design criteria: reduce the energy consumption § Multi-hop communication reduces energy consumption: – Overall energy consumption can be reduced, if packets are sent in several smaller hops instead of one long hop – Fewer re-transmissions are needed due to collisions Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 8/58
Sensor networks § Large number of sensor nodes, a few base stations § Sensors are usually battery powered: – Main design criteria: reduce the energy consumption § Multi-hop communication reduces energy consumption: – Overall energy consumption can be reduced, if packets are sent in several smaller hops instead of one long hop – Fewer re-transmissions are needed due to collisions Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 8/58
 Sensor networks § Security requirements: – Integrity – Confidentiality – Availability § Special conditions: – Energy consumption – Computing and storage capacity of sensors is limited – Access to the sensors cannot be monitored Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 9/58
Sensor networks § Security requirements: – Integrity – Confidentiality – Availability § Special conditions: – Energy consumption – Computing and storage capacity of sensors is limited – Access to the sensors cannot be monitored Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 9/58
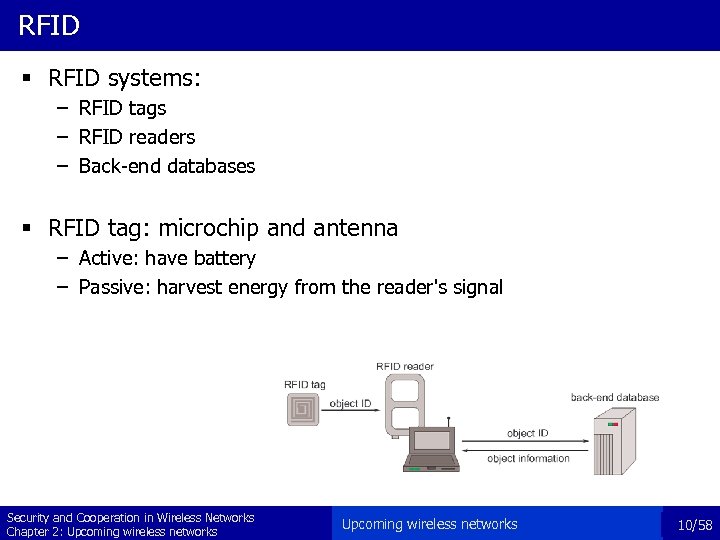 RFID § RFID systems: – RFID tags – RFID readers – Back-end databases § RFID tag: microchip and antenna – Active: have battery – Passive: harvest energy from the reader's signal Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 10/58
RFID § RFID systems: – RFID tags – RFID readers – Back-end databases § RFID tag: microchip and antenna – Active: have battery – Passive: harvest energy from the reader's signal Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 10/58
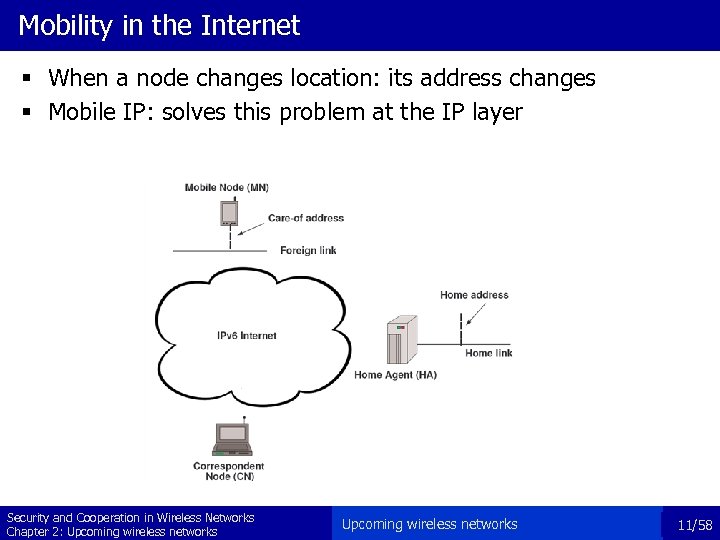 Mobility in the Internet § When a node changes location: its address changes § Mobile IP: solves this problem at the IP layer Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 11/58
Mobility in the Internet § When a node changes location: its address changes § Mobile IP: solves this problem at the IP layer Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 11/58
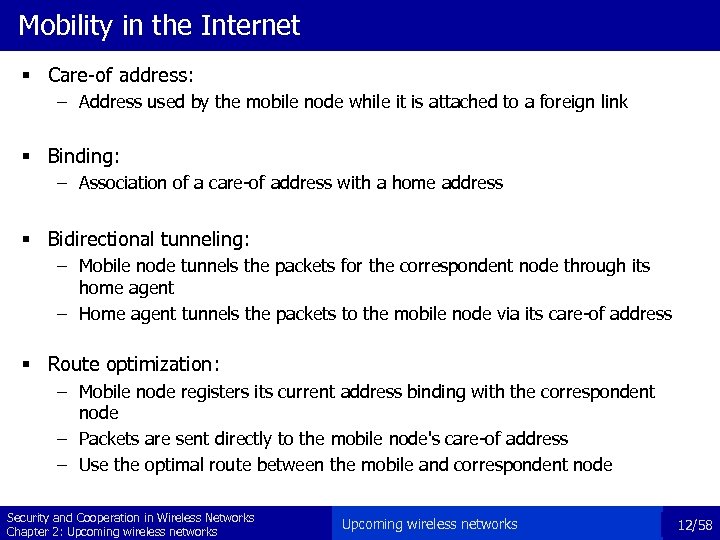 Mobility in the Internet § Care-of address: – Address used by the mobile node while it is attached to a foreign link § Binding: – Association of a care-of address with a home address § Bidirectional tunneling: – Mobile node tunnels the packets for the correspondent node through its home agent – Home agent tunnels the packets to the mobile node via its care-of address § Route optimization: – Mobile node registers its current address binding with the correspondent node – Packets are sent directly to the mobile node's care-of address – Use the optimal route between the mobile and correspondent node Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 12/58
Mobility in the Internet § Care-of address: – Address used by the mobile node while it is attached to a foreign link § Binding: – Association of a care-of address with a home address § Bidirectional tunneling: – Mobile node tunnels the packets for the correspondent node through its home agent – Home agent tunnels the packets to the mobile node via its care-of address § Route optimization: – Mobile node registers its current address binding with the correspondent node – Packets are sent directly to the mobile node's care-of address – Use the optimal route between the mobile and correspondent node Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 12/58
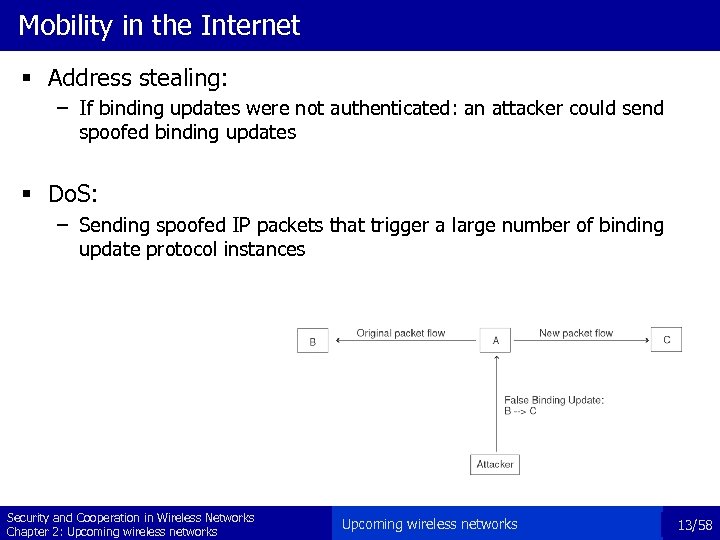 Mobility in the Internet § Address stealing: – If binding updates were not authenticated: an attacker could send spoofed binding updates § Do. S: – Sending spoofed IP packets that trigger a large number of binding update protocol instances Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 13/58
Mobility in the Internet § Address stealing: – If binding updates were not authenticated: an attacker could send spoofed binding updates § Do. S: – Sending spoofed IP packets that trigger a large number of binding update protocol instances Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 13/58
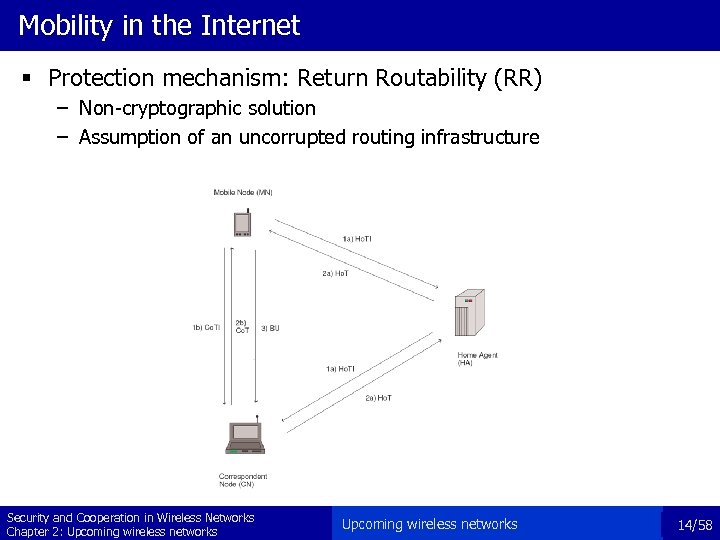 Mobility in the Internet § Protection mechanism: Return Routability (RR) – Non-cryptographic solution – Assumption of an uncorrupted routing infrastructure Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 14/58
Mobility in the Internet § Protection mechanism: Return Routability (RR) – Non-cryptographic solution – Assumption of an uncorrupted routing infrastructure Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 14/58
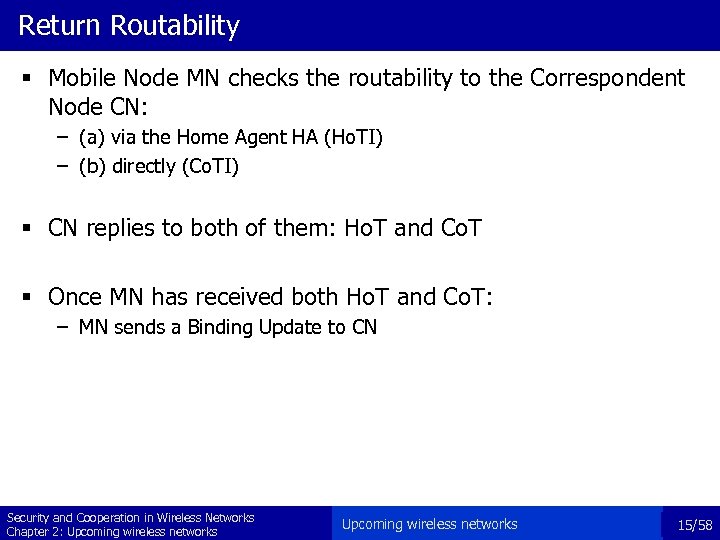 Return Routability § Mobile Node MN checks the routability to the Correspondent Node CN: – (a) via the Home Agent HA (Ho. TI) – (b) directly (Co. TI) § CN replies to both of them: Ho. T and Co. T § Once MN has received both Ho. T and Co. T: – MN sends a Binding Update to CN Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 15/58
Return Routability § Mobile Node MN checks the routability to the Correspondent Node CN: – (a) via the Home Agent HA (Ho. TI) – (b) directly (Co. TI) § CN replies to both of them: Ho. T and Co. T § Once MN has received both Ho. T and Co. T: – MN sends a Binding Update to CN Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 15/58
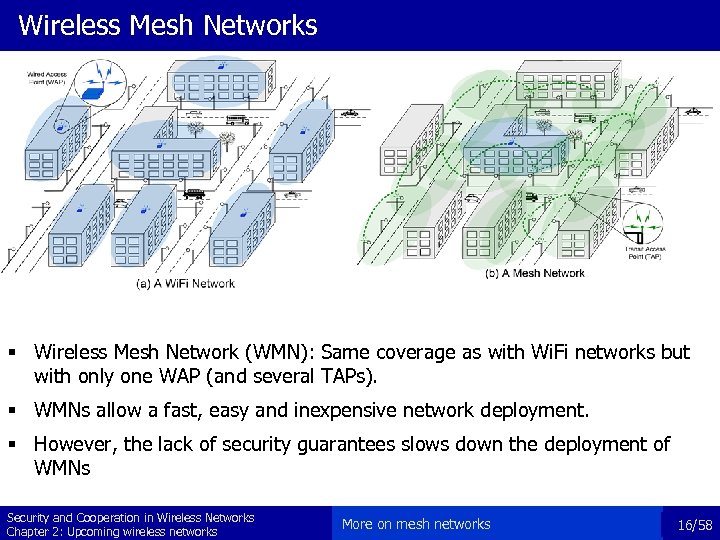 Wireless Mesh Networks § Wireless Mesh Network (WMN): Same coverage as with Wi. Fi networks but with only one WAP (and several TAPs). § WMNs allow a fast, easy and inexpensive network deployment. § However, the lack of security guarantees slows down the deployment of WMNs Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 16/58
Wireless Mesh Networks § Wireless Mesh Network (WMN): Same coverage as with Wi. Fi networks but with only one WAP (and several TAPs). § WMNs allow a fast, easy and inexpensive network deployment. § However, the lack of security guarantees slows down the deployment of WMNs Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 16/58
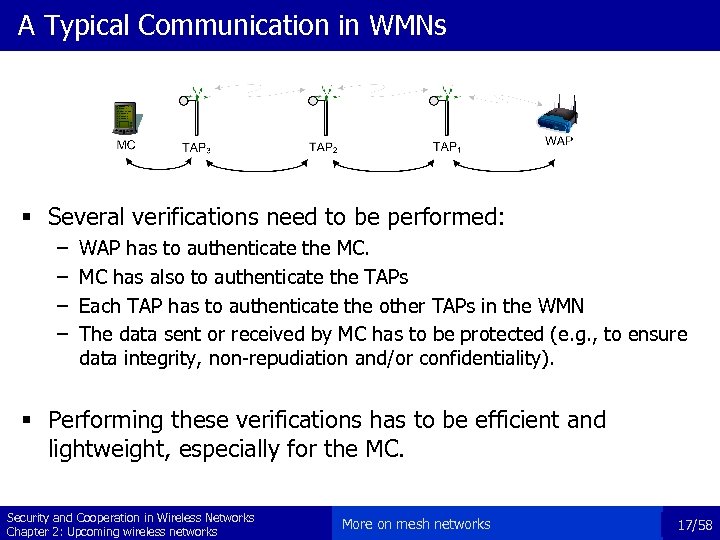 A Typical Communication in WMNs § Several verifications need to be performed: – – WAP has to authenticate the MC. MC has also to authenticate the TAPs Each TAP has to authenticate the other TAPs in the WMN The data sent or received by MC has to be protected (e. g. , to ensure data integrity, non-repudiation and/or confidentiality). § Performing these verifications has to be efficient and lightweight, especially for the MC. Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 17/58
A Typical Communication in WMNs § Several verifications need to be performed: – – WAP has to authenticate the MC. MC has also to authenticate the TAPs Each TAP has to authenticate the other TAPs in the WMN The data sent or received by MC has to be protected (e. g. , to ensure data integrity, non-repudiation and/or confidentiality). § Performing these verifications has to be efficient and lightweight, especially for the MC. Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 17/58
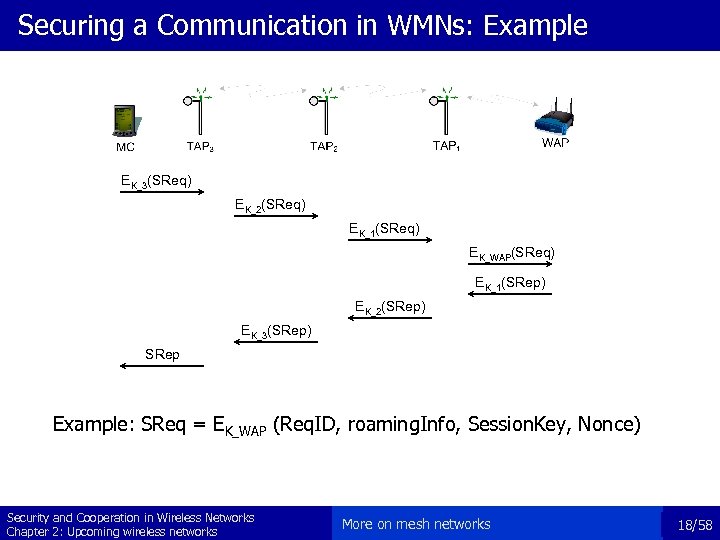 Securing a Communication in WMNs: Example EK_3(SReq) EK_2(SReq) EK_1(SReq) EK_WAP(SReq) EK_1(SRep) EK_2(SRep) EK_3(SRep) SRep Example: SReq = EK_WAP (Req. ID, roaming. Info, Session. Key, Nonce) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 18/58
Securing a Communication in WMNs: Example EK_3(SReq) EK_2(SReq) EK_1(SReq) EK_WAP(SReq) EK_1(SRep) EK_2(SRep) EK_3(SRep) SRep Example: SReq = EK_WAP (Req. ID, roaming. Info, Session. Key, Nonce) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 18/58
 Characteristics of WMNs § Multi-hop communications: Ø Delayed detection and treatment of attacks Ø Routing becomes critical Ø Unfairness § The TAPs are not physically protected: Ø Capture Ø Cloning Ø Tampering Ä Three fundamental security operations: Ä Detection of corrupt nodes Ä Secure routing Ä Fairness Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 19/58
Characteristics of WMNs § Multi-hop communications: Ø Delayed detection and treatment of attacks Ø Routing becomes critical Ø Unfairness § The TAPs are not physically protected: Ø Capture Ø Cloning Ø Tampering Ä Three fundamental security operations: Ä Detection of corrupt nodes Ä Secure routing Ä Fairness Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 19/58
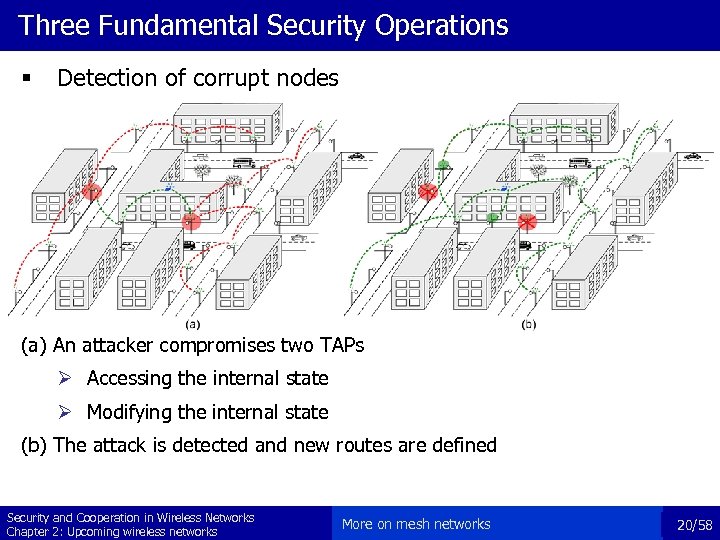 Three Fundamental Security Operations § Detection of corrupt nodes (a) An attacker compromises two TAPs Ø Accessing the internal state Ø Modifying the internal state (b) The attack is detected and new routes are defined Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 20/58
Three Fundamental Security Operations § Detection of corrupt nodes (a) An attacker compromises two TAPs Ø Accessing the internal state Ø Modifying the internal state (b) The attack is detected and new routes are defined Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 20/58
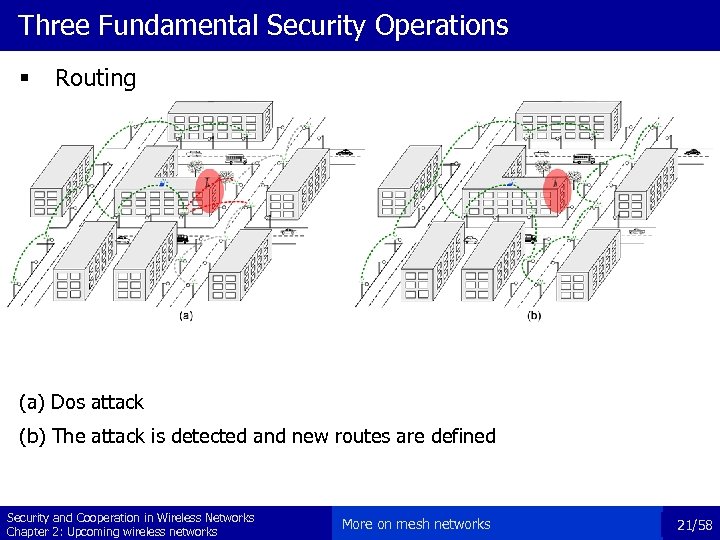 Three Fundamental Security Operations § Routing (a) Dos attack (b) The attack is detected and new routes are defined Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 21/58
Three Fundamental Security Operations § Routing (a) Dos attack (b) The attack is detected and new routes are defined Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 21/58
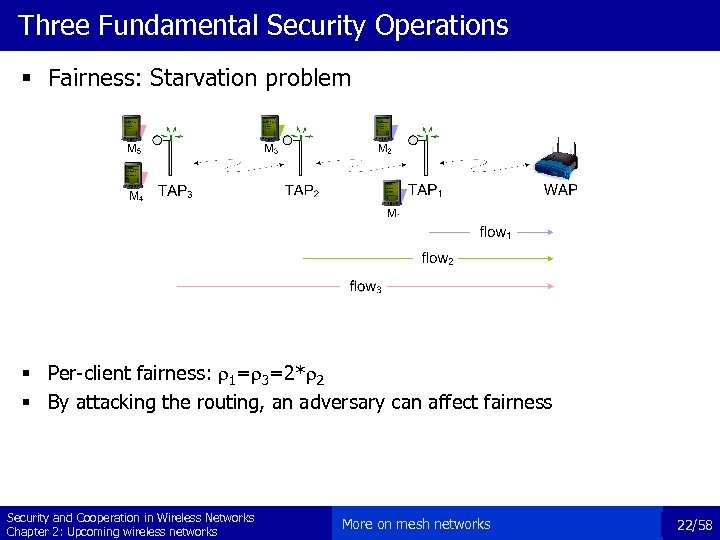 Three Fundamental Security Operations § Fairness: Starvation problem § Per-client fairness: 1= 3=2* 2 § By attacking the routing, an adversary can affect fairness Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 22/58
Three Fundamental Security Operations § Fairness: Starvation problem § Per-client fairness: 1= 3=2* 2 § By attacking the routing, an adversary can affect fairness Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 22/58
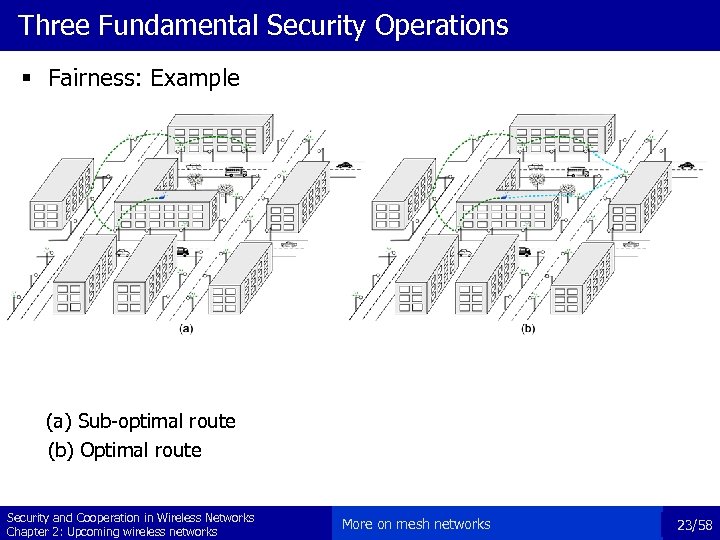 Three Fundamental Security Operations § Fairness: Example (a) Sub-optimal route (b) Optimal route Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 23/58
Three Fundamental Security Operations § Fairness: Example (a) Sub-optimal route (b) Optimal route Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 23/58
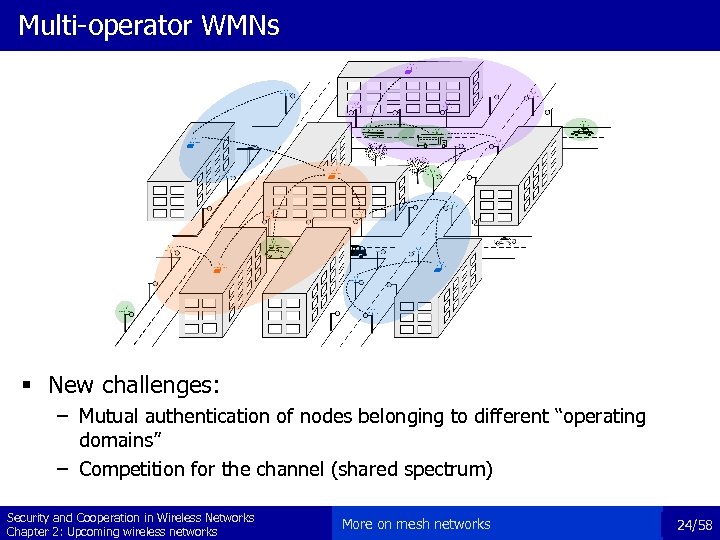 Multi-operator WMNs § New challenges: – Mutual authentication of nodes belonging to different “operating domains” – Competition for the channel (shared spectrum) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 24/58
Multi-operator WMNs § New challenges: – Mutual authentication of nodes belonging to different “operating domains” – Competition for the channel (shared spectrum) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks More on mesh networks 24/58
 Outline § Motivation § Threat model and specific attacks § Security architecture § Security analysis § Performance evaluation § Certificate revocation § Secure positioning § Conclusion Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 25/58
Outline § Motivation § Threat model and specific attacks § Security architecture § Security analysis § Performance evaluation § Certificate revocation § Secure positioning § Conclusion Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 25/58
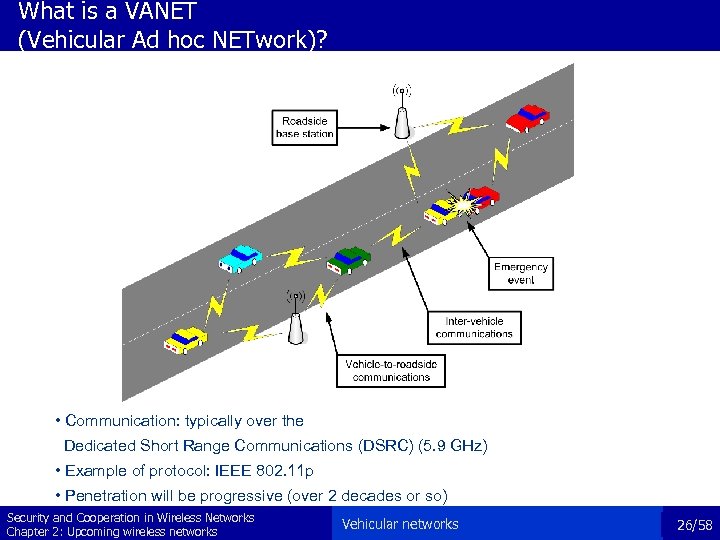 What is a VANET (Vehicular Ad hoc NETwork)? • Communication: typically over the Dedicated Short Range Communications (DSRC) (5. 9 GHz) • Example of protocol: IEEE 802. 11 p • Penetration will be progressive (over 2 decades or so) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 26/58
What is a VANET (Vehicular Ad hoc NETwork)? • Communication: typically over the Dedicated Short Range Communications (DSRC) (5. 9 GHz) • Example of protocol: IEEE 802. 11 p • Penetration will be progressive (over 2 decades or so) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 26/58
 Vehicular communications: why? § Combat the awful side-effects of road traffic – In the EU, around 40’ 000 people die yearly on the roads; more than 1. 5 millions are injured – Traffic jams generate a tremendous waste of time and of fuel § Most of these problems can be solved by providing appropriate information to the driver or to the vehicle Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 27/58
Vehicular communications: why? § Combat the awful side-effects of road traffic – In the EU, around 40’ 000 people die yearly on the roads; more than 1. 5 millions are injured – Traffic jams generate a tremendous waste of time and of fuel § Most of these problems can be solved by providing appropriate information to the driver or to the vehicle Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 27/58
 Why is VANET security important? § Large projects have explored vehicular communications: Fleetnet, PATH (UC Berkeley), … § No solution can be deployed if not properly secured § The problem is non-trivial – Specific requirements (speed, real-time constraints) – Contradictory expectations § Industry front: standards are still under development and suffer from serious weaknesses – IEEE P 1609. 2: Standard for Wireless Access in Vehicular Environments Security Services for Applications and Management Messages § Research front – Very few papers Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 28/58
Why is VANET security important? § Large projects have explored vehicular communications: Fleetnet, PATH (UC Berkeley), … § No solution can be deployed if not properly secured § The problem is non-trivial – Specific requirements (speed, real-time constraints) – Contradictory expectations § Industry front: standards are still under development and suffer from serious weaknesses – IEEE P 1609. 2: Standard for Wireless Access in Vehicular Environments Security Services for Applications and Management Messages § Research front – Very few papers Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 28/58
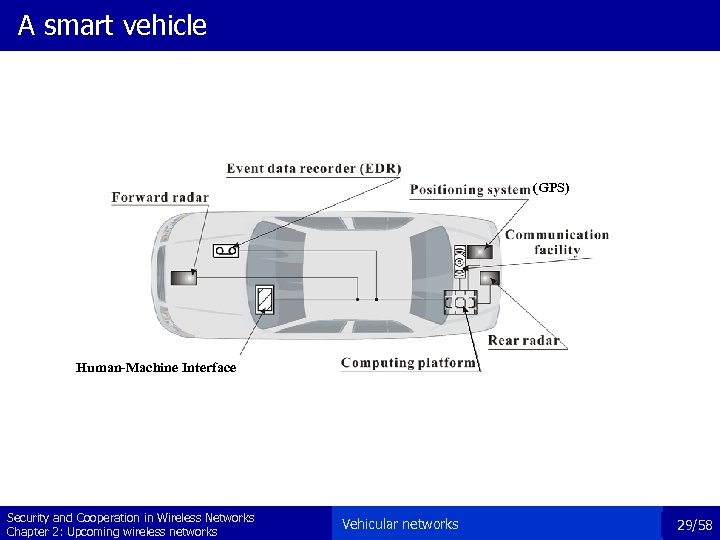 A smart vehicle (GPS) Human-Machine Interface Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 29/58
A smart vehicle (GPS) Human-Machine Interface Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 29/58
 Threat model § An attacker can be: – Insider / Outsider – Malicious / Rational – Active / Passive – Local / Extended § Attacks can be mounted on: – Safety-related applications – Traffic optimization applications – Payment-based applications – Privacy Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 30/58
Threat model § An attacker can be: – Insider / Outsider – Malicious / Rational – Active / Passive – Local / Extended § Attacks can be mounted on: – Safety-related applications – Traffic optimization applications – Payment-based applications – Privacy Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 30/58
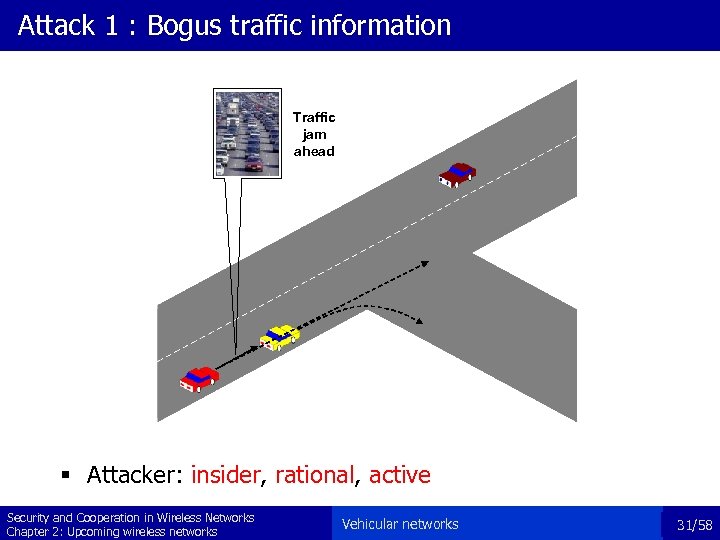 Attack 1 : Bogus traffic information Traffic jam ahead § Attacker: insider, rational, active Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 31/58
Attack 1 : Bogus traffic information Traffic jam ahead § Attacker: insider, rational, active Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 31/58
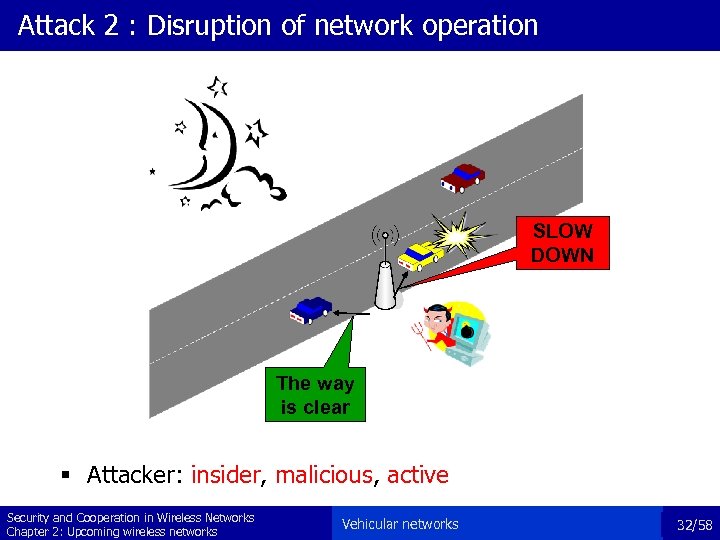 Attack 2 : Disruption of network operation SLOW DOWN The way is clear § Attacker: insider, malicious, active Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 32/58
Attack 2 : Disruption of network operation SLOW DOWN The way is clear § Attacker: insider, malicious, active Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 32/58
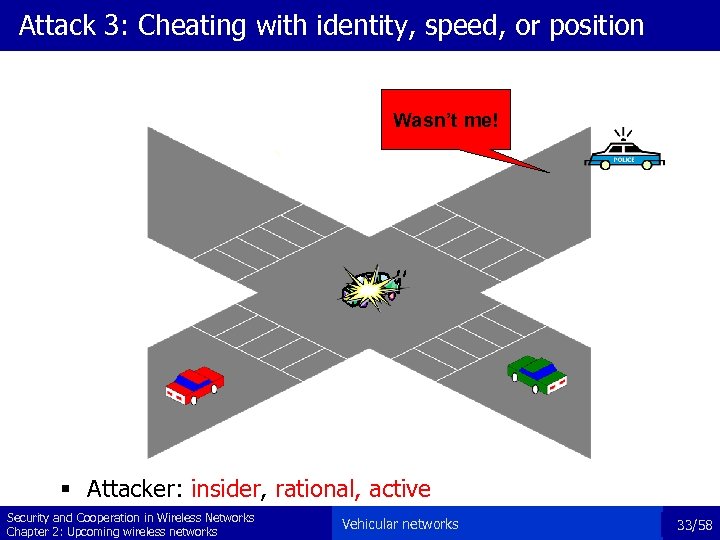 Attack 3: Cheating with identity, speed, or position Wasn’t me! § Attacker: insider, rational, active Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 33/58
Attack 3: Cheating with identity, speed, or position Wasn’t me! § Attacker: insider, rational, active Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 33/58
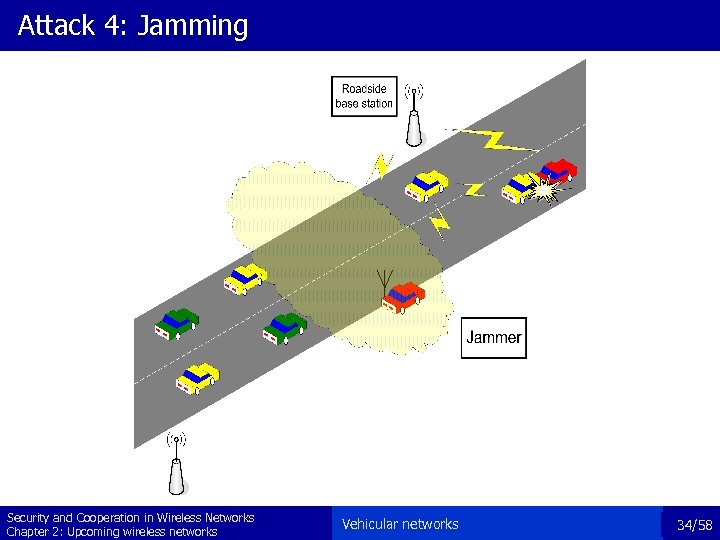 Attack 4: Jamming Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 34/58
Attack 4: Jamming Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 34/58
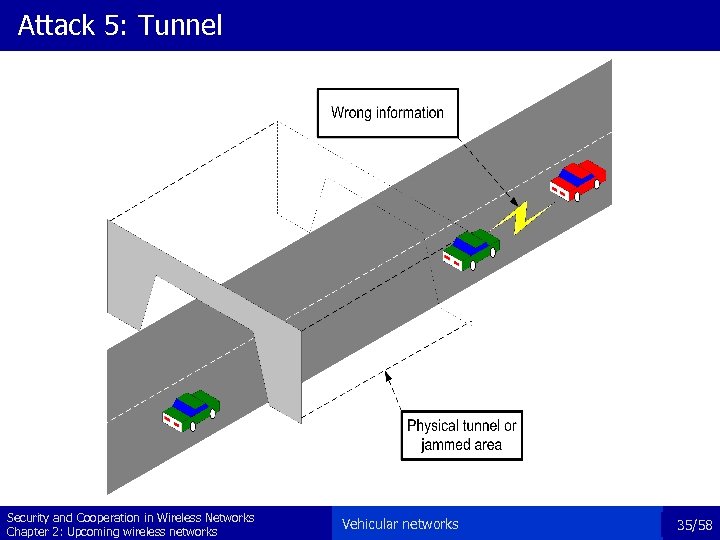 Attack 5: Tunnel Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 35/58
Attack 5: Tunnel Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 35/58
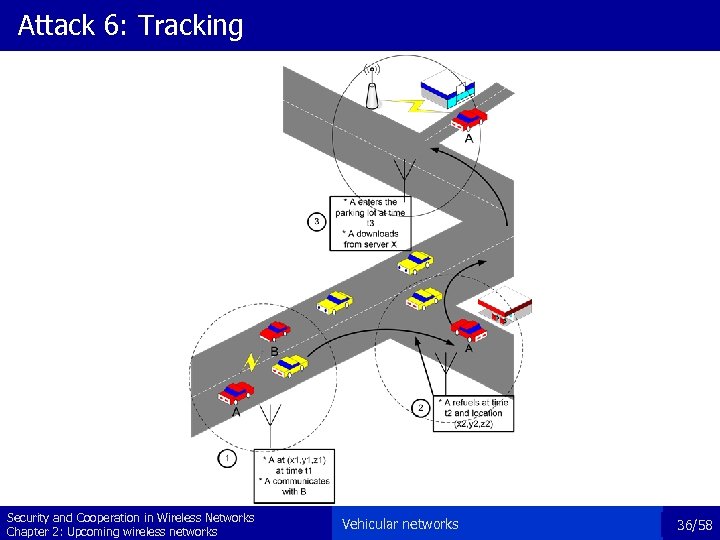 Attack 6: Tracking Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 36/58
Attack 6: Tracking Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 36/58
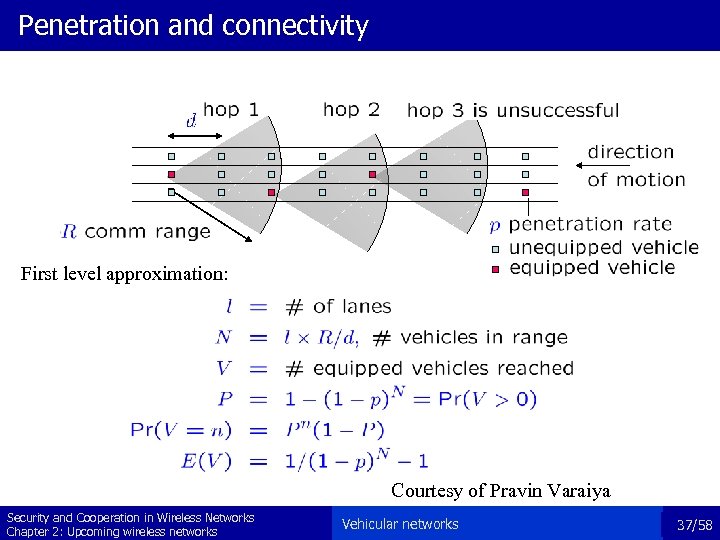 Penetration and connectivity First level approximation: Courtesy of Pravin Varaiya Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 37/58
Penetration and connectivity First level approximation: Courtesy of Pravin Varaiya Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 37/58
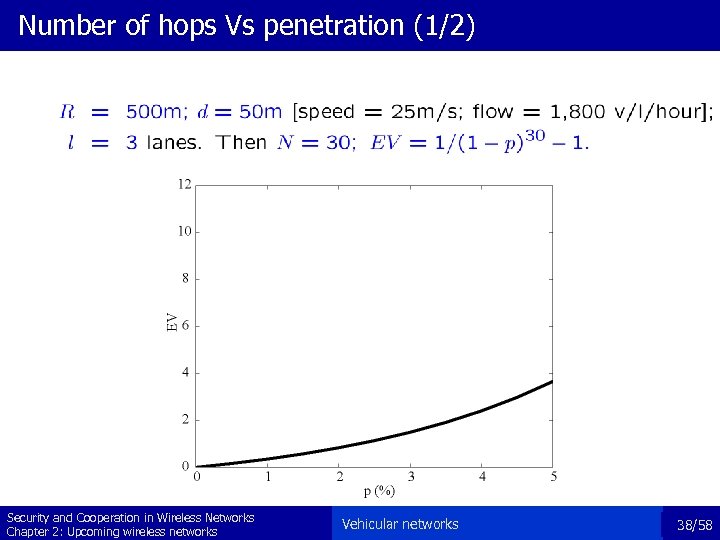 Number of hops Vs penetration (1/2) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 38/58
Number of hops Vs penetration (1/2) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 38/58
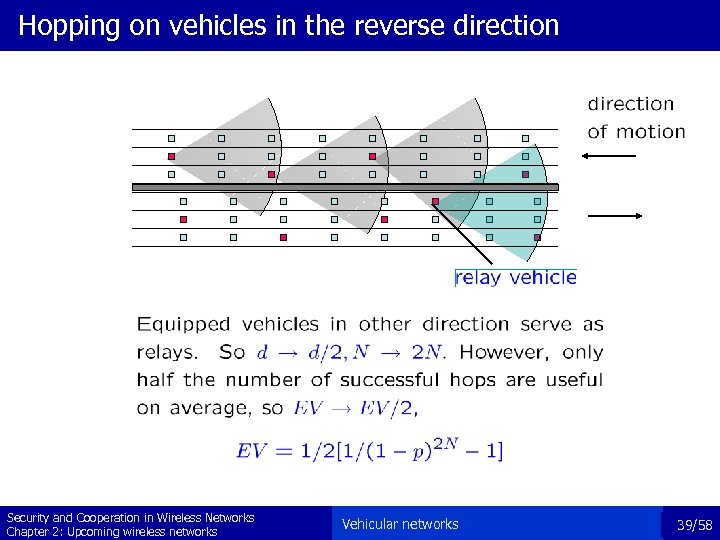 Hopping on vehicles in the reverse direction Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 39/58
Hopping on vehicles in the reverse direction Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 39/58
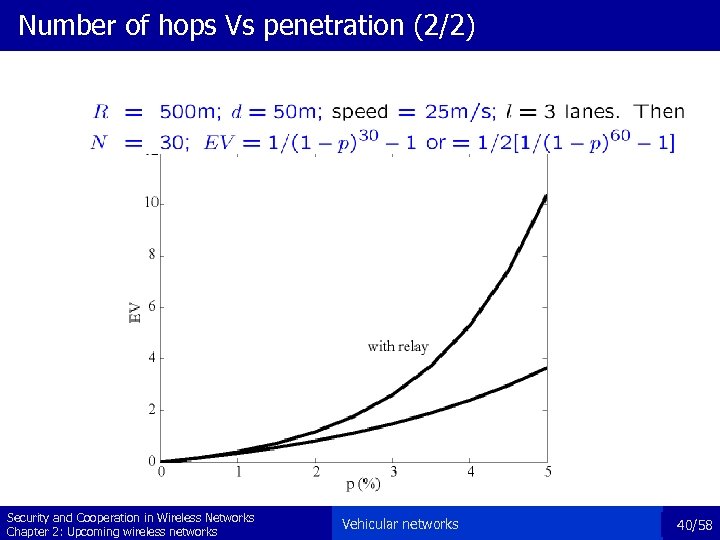 Number of hops Vs penetration (2/2) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 40/58
Number of hops Vs penetration (2/2) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 40/58
 Proposed homework Compute connectivity in this case ; -) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 41/58
Proposed homework Compute connectivity in this case ; -) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 41/58
 Our scope § We consider communications specific to road traffic: safety and traffic optimization – Safety-related messages – Messages related to traffic information § We do not consider more generic applications, e. g. toll collect, access to audio/video files, games, … Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 42/58
Our scope § We consider communications specific to road traffic: safety and traffic optimization – Safety-related messages – Messages related to traffic information § We do not consider more generic applications, e. g. toll collect, access to audio/video files, games, … Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 42/58
 Security system requirements § Sender authentication § Verification of data consistency § Availability § Non-repudiation § Privacy § Real-time constraints Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 43/58
Security system requirements § Sender authentication § Verification of data consistency § Availability § Non-repudiation § Privacy § Real-time constraints Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 43/58
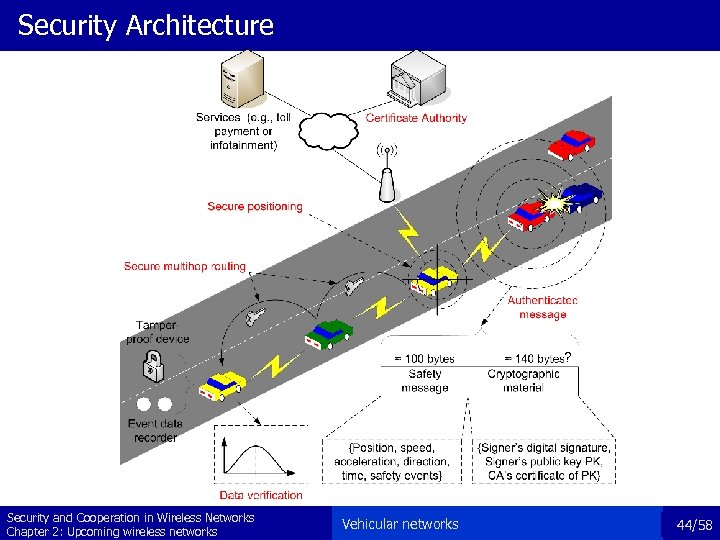 Security Architecture ? Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 44/58
Security Architecture ? Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 44/58
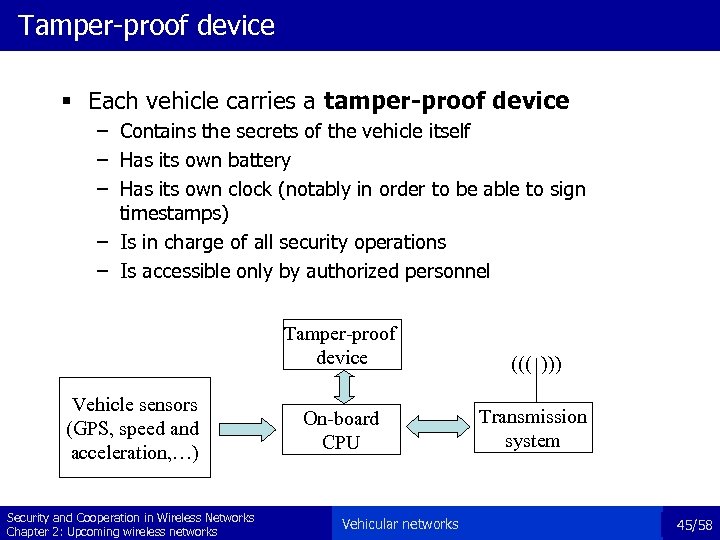 Tamper-proof device § Each vehicle carries a tamper-proof device – Contains the secrets of the vehicle itself – Has its own battery – Has its own clock (notably in order to be able to sign timestamps) – Is in charge of all security operations – Is accessible only by authorized personnel Tamper-proof device Vehicle sensors (GPS, speed and acceleration, …) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks ((( ))) On-board CPU Transmission system Vehicular networks 45/58
Tamper-proof device § Each vehicle carries a tamper-proof device – Contains the secrets of the vehicle itself – Has its own battery – Has its own clock (notably in order to be able to sign timestamps) – Is in charge of all security operations – Is accessible only by authorized personnel Tamper-proof device Vehicle sensors (GPS, speed and acceleration, …) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks ((( ))) On-board CPU Transmission system Vehicular networks 45/58
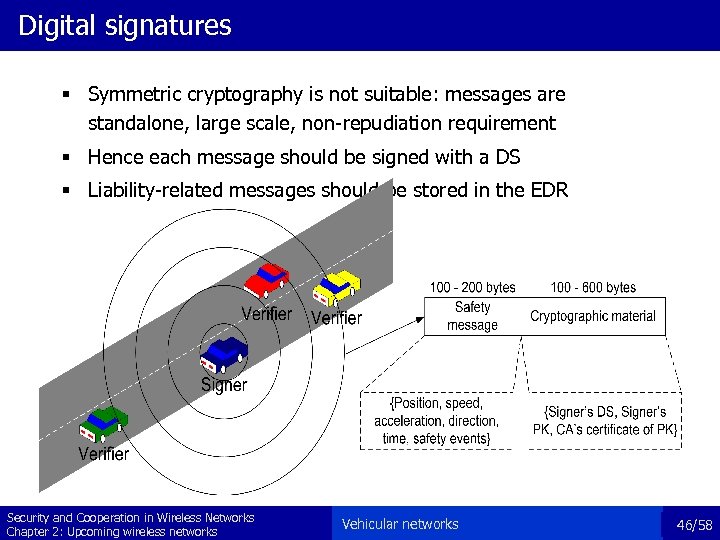 Digital signatures § Symmetric cryptography is not suitable: messages are standalone, large scale, non-repudiation requirement § Hence each message should be signed with a DS § Liability-related messages should be stored in the EDR Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 46/58
Digital signatures § Symmetric cryptography is not suitable: messages are standalone, large scale, non-repudiation requirement § Hence each message should be signed with a DS § Liability-related messages should be stored in the EDR Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 46/58
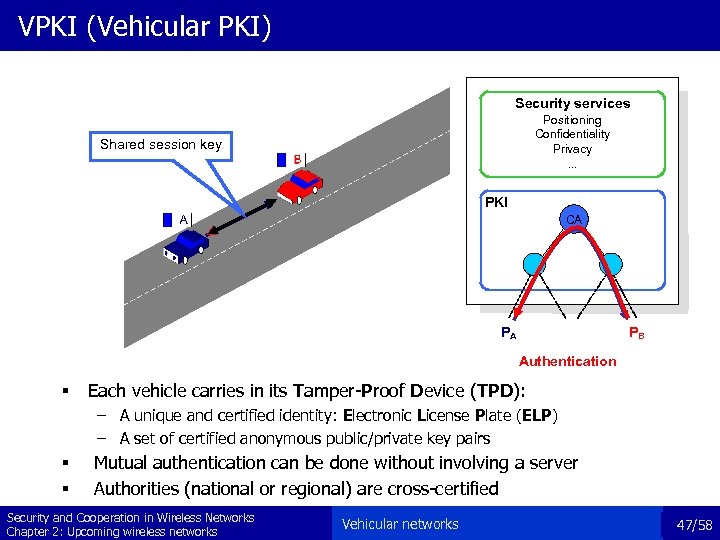 VPKI (Vehicular PKI) Security services Positioning Confidentiality Privacy. . . Shared session key PKI CA PA PB Authentication § Each vehicle carries in its Tamper-Proof Device (TPD): – A unique and certified identity: Electronic License Plate (ELP) – A set of certified anonymous public/private key pairs § § Mutual authentication can be done without involving a server Authorities (national or regional) are cross-certified Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 47/58
VPKI (Vehicular PKI) Security services Positioning Confidentiality Privacy. . . Shared session key PKI CA PA PB Authentication § Each vehicle carries in its Tamper-Proof Device (TPD): – A unique and certified identity: Electronic License Plate (ELP) – A set of certified anonymous public/private key pairs § § Mutual authentication can be done without involving a server Authorities (national or regional) are cross-certified Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 47/58
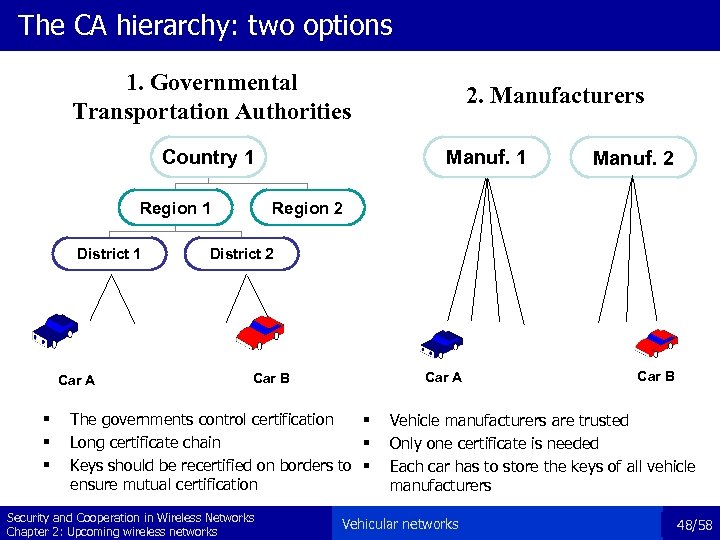 The CA hierarchy: two options 1. Governmental Transportation Authorities Country 1 Region 1 District 1 Car A § § § 2. Manufacturers Manuf. 1 Manuf. 2 Region 2 District 2 Car A Car B The governments control certification § Long certificate chain § Keys should be recertified on borders to § ensure mutual certification Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Car B Vehicle manufacturers are trusted Only one certificate is needed Each car has to store the keys of all vehicle manufacturers Vehicular networks 48/58
The CA hierarchy: two options 1. Governmental Transportation Authorities Country 1 Region 1 District 1 Car A § § § 2. Manufacturers Manuf. 1 Manuf. 2 Region 2 District 2 Car A Car B The governments control certification § Long certificate chain § Keys should be recertified on borders to § ensure mutual certification Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Car B Vehicle manufacturers are trusted Only one certificate is needed Each car has to store the keys of all vehicle manufacturers Vehicular networks 48/58
 Secure VC Building Blocks § Authorities – Trusted entities issuing and managing identities and credentials Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 49/58
Secure VC Building Blocks § Authorities – Trusted entities issuing and managing identities and credentials Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 49/58
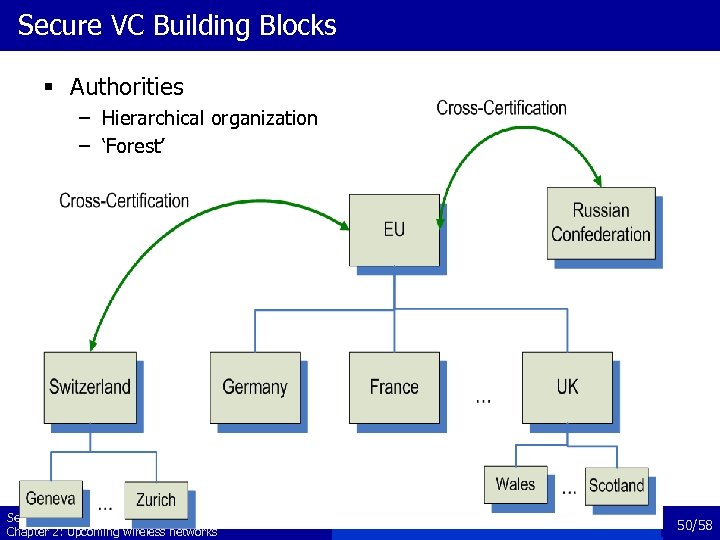 Secure VC Building Blocks § Authorities – Hierarchical organization – ‘Forest’ Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 50/58
Secure VC Building Blocks § Authorities – Hierarchical organization – ‘Forest’ Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks 50/58
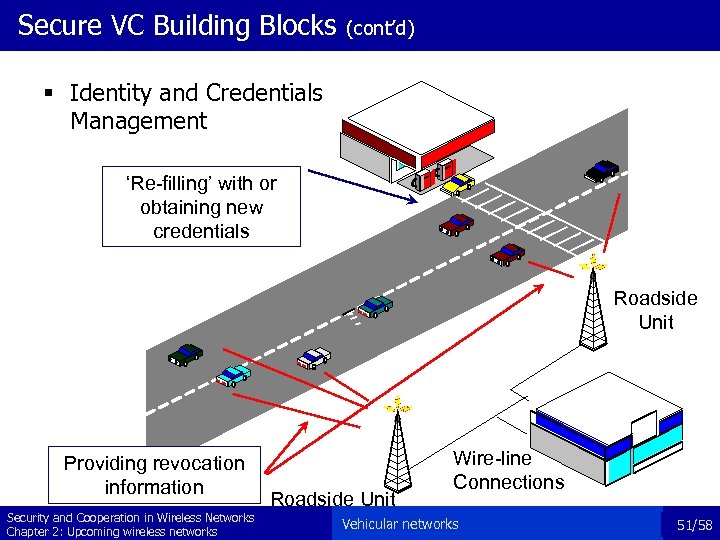 Secure VC Building Blocks (cont’d) § Identity and Credentials Management ‘Re-filling’ with or obtaining new credentials Roadside Unit Providing revocation information Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Roadside Unit Wire-line Connections Vehicular networks 51/58
Secure VC Building Blocks (cont’d) § Identity and Credentials Management ‘Re-filling’ with or obtaining new credentials Roadside Unit Providing revocation information Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Roadside Unit Wire-line Connections Vehicular networks 51/58
 Anonymous keys § Preserve identity and location privacy § Keys can be preloaded at periodic checkups § The certificate of V’s ith key: § Keys renewal algorithm according to vehicle speed (e. g. , ≈ 1 min at 100 km/h) § Anonymity is conditional on the scenario § The authorization to link keys with ELPs is distributed Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 52/58
Anonymous keys § Preserve identity and location privacy § Keys can be preloaded at periodic checkups § The certificate of V’s ith key: § Keys renewal algorithm according to vehicle speed (e. g. , ≈ 1 min at 100 km/h) § Anonymity is conditional on the scenario § The authorization to link keys with ELPs is distributed Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 52/58
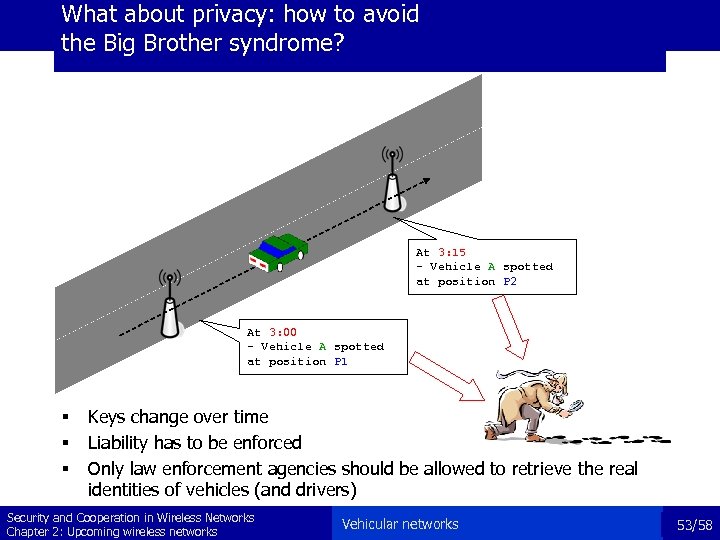 What about privacy: how to avoid the Big Brother syndrome? At 3: 15 - Vehicle A spotted at position P 2 At 3: 00 - Vehicle A spotted at position P 1 § § § Keys change over time Liability has to be enforced Only law enforcement agencies should be allowed to retrieve the real identities of vehicles (and drivers) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 53/58
What about privacy: how to avoid the Big Brother syndrome? At 3: 15 - Vehicle A spotted at position P 2 At 3: 00 - Vehicle A spotted at position P 1 § § § Keys change over time Liability has to be enforced Only law enforcement agencies should be allowed to retrieve the real identities of vehicles (and drivers) Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 53/58
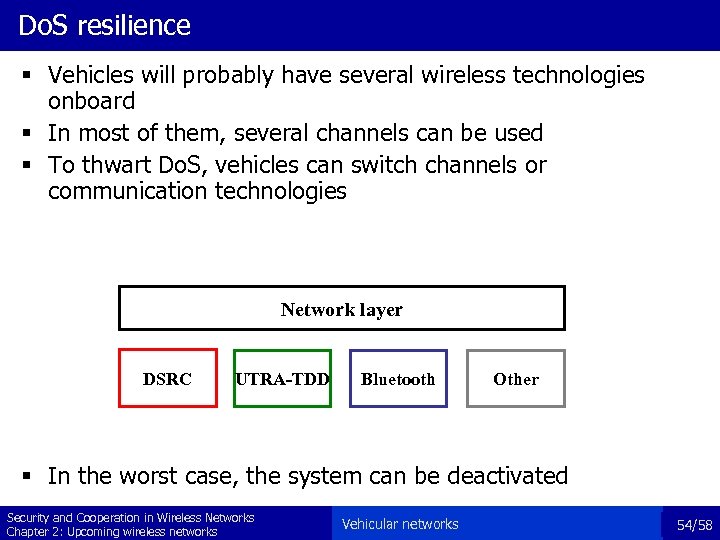 Do. S resilience § Vehicles will probably have several wireless technologies onboard § In most of them, several channels can be used § To thwart Do. S, vehicles can switch channels or communication technologies Network layer DSRC UTRA-TDD Bluetooth Other § In the worst case, the system can be deactivated Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 54/58
Do. S resilience § Vehicles will probably have several wireless technologies onboard § In most of them, several channels can be used § To thwart Do. S, vehicles can switch channels or communication technologies Network layer DSRC UTRA-TDD Bluetooth Other § In the worst case, the system can be deactivated Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 54/58
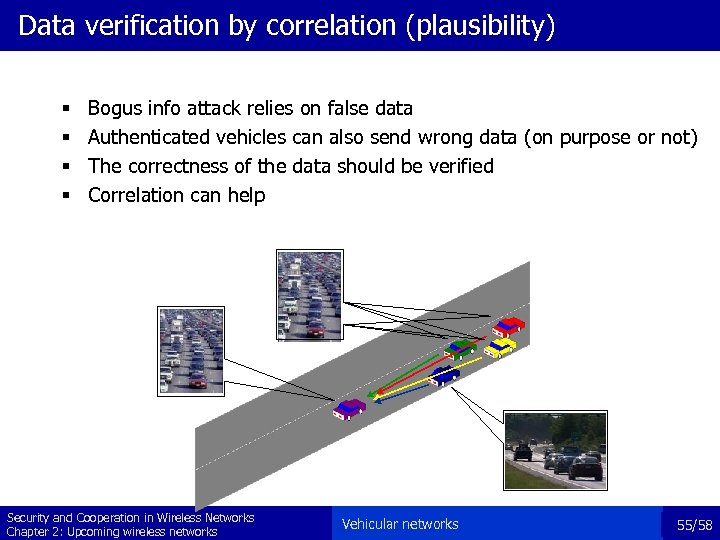 Data verification by correlation (plausibility) § § Bogus info attack relies on false data Authenticated vehicles can also send wrong data (on purpose or not) The correctness of the data should be verified Correlation can help Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 55/58
Data verification by correlation (plausibility) § § Bogus info attack relies on false data Authenticated vehicles can also send wrong data (on purpose or not) The correctness of the data should be verified Correlation can help Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 55/58
 Security analysis § How much can we secure VANETs? § Messages are authenticated by their signatures § Authentication protects the network from outsiders § Correlation and fast revocation reinforce correctness § Availability remains a problem that can be alleviated § Non-repudiation is achieved because: – ELP and anonymous keys are specific to one vehicle – Position is correct if secure positioning is in place Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 56/58
Security analysis § How much can we secure VANETs? § Messages are authenticated by their signatures § Authentication protects the network from outsiders § Correlation and fast revocation reinforce correctness § Availability remains a problem that can be alleviated § Non-repudiation is achieved because: – ELP and anonymous keys are specific to one vehicle – Position is correct if secure positioning is in place Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 56/58
 Conclusion on the security of vehicular communications § The security of vehicular communications is a difficult and highly relevant problem § Car manufacturers seem to be poised to massively invest in this area § Slow penetration makes connectivity more difficult § Security leads to a substantial overhead and must be taken into account from the beginning of the design process § The field offers plenty of novel research challenges § Pitfalls – Defer the design of security – Security by obscurity § More information at http: //ivc. epfl. ch Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 57/58
Conclusion on the security of vehicular communications § The security of vehicular communications is a difficult and highly relevant problem § Car manufacturers seem to be poised to massively invest in this area § Slow penetration makes connectivity more difficult § Security leads to a substantial overhead and must be taken into account from the beginning of the design process § The field offers plenty of novel research challenges § Pitfalls – Defer the design of security – Security by obscurity § More information at http: //ivc. epfl. ch Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks Vehicular networks 57/58
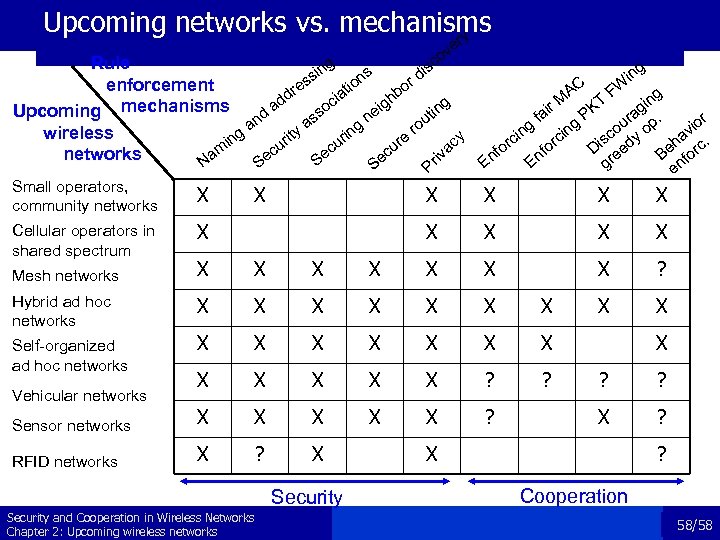 Upcoming networks vs. mechanisms ry e ov c S Small operators, community networks X Cellular operators in shared spectrum X X Pr iv ac y Rule g is sin ns rd s enforcement e o tio dr ia hb d c g ig o Upcoming mechanisms nd a tin ne ss u a ro ya ng wireless g it ri e in ur ur cu m c networks ec Se Na Se g in AC FW ng M gi KT ir P r fa ra p. io g ou o ng v i in rc isc edy ha rc. rc o o D e Be fo nf nf r E E g en X X X X X ? X X Mesh networks X X X Hybrid ad hoc networks X X X X Self-organized ad hoc networks X X X ? ? Sensor networks X X X ? RFID networks X ? X Vehicular networks Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks X ? ? X ? Cooperation 58/58
Upcoming networks vs. mechanisms ry e ov c S Small operators, community networks X Cellular operators in shared spectrum X X Pr iv ac y Rule g is sin ns rd s enforcement e o tio dr ia hb d c g ig o Upcoming mechanisms nd a tin ne ss u a ro ya ng wireless g it ri e in ur ur cu m c networks ec Se Na Se g in AC FW ng M gi KT ir P r fa ra p. io g ou o ng v i in rc isc edy ha rc. rc o o D e Be fo nf nf r E E g en X X X X X ? X X Mesh networks X X X Hybrid ad hoc networks X X X X Self-organized ad hoc networks X X X ? ? Sensor networks X X X ? RFID networks X ? X Vehicular networks Security and Cooperation in Wireless Networks Chapter 2: Upcoming wireless networks X ? ? X ? Cooperation 58/58


