1656f7fe742743372d5dc08f076b0adc.ppt
- Количество слайдов: 67
 Security+ All-In-One Edition Chapter 9 – Authentication and Remote Access Brian E. Brzezicki
Security+ All-In-One Edition Chapter 9 – Authentication and Remote Access Brian E. Brzezicki
 AAA
AAA
 AAA (n/b) Authentication, Authorization and Accounting
AAA (n/b) Authentication, Authorization and Accounting
 Identification (242) Identification is a necessary component of Authentication, Authorization and Accounting. The idea is that each entity has a unique ID. – IDs should NEVER be shared – IDs are a foundational component of AAA
Identification (242) Identification is a necessary component of Authentication, Authorization and Accounting. The idea is that each entity has a unique ID. – IDs should NEVER be shared – IDs are a foundational component of AAA
 Authentication (243) The idea of verifying an entities identity. We already talked about Authentication, but let’s recap the 3 types 1. Something you _____ 2. Something you _____ 3. Something you _____ Multi-factor Authentication = Strong Authentication
Authentication (243) The idea of verifying an entities identity. We already talked about Authentication, but let’s recap the 3 types 1. Something you _____ 2. Something you _____ 3. Something you _____ Multi-factor Authentication = Strong Authentication
 Mutual Authentication (246) Normally we authenticate to a server. Mutual Authentication requires both parties to authenticate to each other! Why would we use this? • Online Banking • Authentication Servers • Web Servers / Avoid Phishing attacks! • What technology is used with websites to have the server authenticate to the client?
Mutual Authentication (246) Normally we authenticate to a server. Mutual Authentication requires both parties to authenticate to each other! Why would we use this? • Online Banking • Authentication Servers • Web Servers / Avoid Phishing attacks! • What technology is used with websites to have the server authenticate to the client?
 Authorization (247) Once identified, Authorization tells a system what you have access to. Some common Authorization types we previously talked about are • Access Control Lists • Unix Permissions • Rules (example time of day access)
Authorization (247) Once identified, Authorization tells a system what you have access to. Some common Authorization types we previously talked about are • Access Control Lists • Unix Permissions • Rules (example time of day access)
 Accounting Being able to measure usage, also related is Auditing
Accounting Being able to measure usage, also related is Auditing
 Auditing (n/b) Auditing is the concept of reviewing access attempts. Auditing SHOULD be carried out manually or through software. Audit Logs should have • Identity of user • Identify of resource • Date/Time • Success or Failure (more)
Auditing (n/b) Auditing is the concept of reviewing access attempts. Auditing SHOULD be carried out manually or through software. Audit Logs should have • Identity of user • Identify of resource • Date/Time • Success or Failure (more)
 Auditing Look for • People trying and failing to access things • People accessing things that they have access to… but maybe shouldn’t
Auditing Look for • People trying and failing to access things • People accessing things that they have access to… but maybe shouldn’t
 Clipping Level (n/b)
Clipping Level (n/b)
 Clipping Level – a threshold for audit events, beneath which we do not log attempts. Used to avoid overwhelming auditors with “false positives” • Example: a clipping level of 3 for login failure. (don’t log failure unless someone fails with password more than 3 times… to avoid “caps lock” problems : )
Clipping Level – a threshold for audit events, beneath which we do not log attempts. Used to avoid overwhelming auditors with “false positives” • Example: a clipping level of 3 for login failure. (don’t log failure unless someone fails with password more than 3 times… to avoid “caps lock” problems : )
 Authentication Protocols
Authentication Protocols
 PAP (257) Password Authentication Protocol • Username and Password sent in plain text Security Concerns • Sniffing • Playback attacks
PAP (257) Password Authentication Protocol • Username and Password sent in plain text Security Concerns • Sniffing • Playback attacks
 CHAP
CHAP
 CHAP (256) Challenge Handshake Authentication Protocol – Avoids ever sending a password. • Server knows your password, as do you • Server creates a “challenge”, example: banana and an increasing number • You take the challenge + number + your password and do a hash of it, send the hash to the server • Server calculates the hash the same way, and compares if your hash is the same as it’s hash, if so you must be who you say you are. Advantages • Avoids reply attacks • Never sends password in plaintext
CHAP (256) Challenge Handshake Authentication Protocol – Avoids ever sending a password. • Server knows your password, as do you • Server creates a “challenge”, example: banana and an increasing number • You take the challenge + number + your password and do a hash of it, send the hash to the server • Server calculates the hash the same way, and compares if your hash is the same as it’s hash, if so you must be who you say you are. Advantages • Avoids reply attacks • Never sends password in plaintext
 EAP (257) Extensible Authentication Protocol – More of a framework. Vendors can actually insert their own authentication schemes • Biometrics • Digital Signatures • Token Devices • etc
EAP (257) Extensible Authentication Protocol – More of a framework. Vendors can actually insert their own authentication schemes • Biometrics • Digital Signatures • Token Devices • etc
 Tokens (245) Generally a hardware device used in Challenge Response Authentication. • Usually not used alone, use in conjunction with a PIN or something else – why?
Tokens (245) Generally a hardware device used in Challenge Response Authentication. • Usually not used alone, use in conjunction with a PIN or something else – why?
 Network Authentication Protocols
Network Authentication Protocols
 Kerberos (244)
Kerberos (244)
 Kerberos (244) A network authentication protocol designed from MITs project Athena. Kerberos tries to ensure authentication security in an insecure environment • Used in Windows 2000+ and some Unix • Allows for single sign on • Never transfers passwords • Uses PRIVATE key encryption to verify Identifications • Avoids replay attacks
Kerberos (244) A network authentication protocol designed from MITs project Athena. Kerberos tries to ensure authentication security in an insecure environment • Used in Windows 2000+ and some Unix • Allows for single sign on • Never transfers passwords • Uses PRIVATE key encryption to verify Identifications • Avoids replay attacks
 Kerberos Components • Principals – users or network services • KDC – Key Distribution Center, stores secret keys (passwords) for principals • Tickets – Ticket Granting Ticket (TGT) gets you more tickets – Service Tickets – access to specific network services (ex. File sharing) • Realms – a grouping of principals that a KDC provides service for, looks like a domain name – Example: somedepartment. mycompany. com
Kerberos Components • Principals – users or network services • KDC – Key Distribution Center, stores secret keys (passwords) for principals • Tickets – Ticket Granting Ticket (TGT) gets you more tickets – Service Tickets – access to specific network services (ex. File sharing) • Realms – a grouping of principals that a KDC provides service for, looks like a domain name – Example: somedepartment. mycompany. com
 Kerberos Concerns • Computers must have clocks synchronized within 5 minutes of each other • Tickets are stored on the workstation. If the workstation is compromised your identity can be forged. • Single point of failure if not backup KDC • If your KDC is hacked, security is lost • Often hard for admins and end users
Kerberos Concerns • Computers must have clocks synchronized within 5 minutes of each other • Tickets are stored on the workstation. If the workstation is compromised your identity can be forged. • Single point of failure if not backup KDC • If your KDC is hacked, security is lost • Often hard for admins and end users
 How Kerberos Works NEED a slide and description
How Kerberos Works NEED a slide and description
 SESAME An extension of Kerberos that uses Public Key Cryptography (digital certificates) rather that shared secret keys.
SESAME An extension of Kerberos that uses Public Key Cryptography (digital certificates) rather that shared secret keys.
 LAN Manager / NTLM LM – Lan Manager – MS previous to NT 4. 0 used LM – LM is a password hash, and the hashing algorithm is NOT strong, NTLM is stronger. – Challenge Response NTLM – NTLM used in Windows NT 4. 0 and windows 2000+ when communicating with NT 4. 0 – Used in windows 2000+ where AD is not implemented – Challenge Response – 2 versions of NTLM, v 1 and v 2 was introduced in NT 4. 0 SP 4 and is more secure than v 1
LAN Manager / NTLM LM – Lan Manager – MS previous to NT 4. 0 used LM – LM is a password hash, and the hashing algorithm is NOT strong, NTLM is stronger. – Challenge Response NTLM – NTLM used in Windows NT 4. 0 and windows 2000+ when communicating with NT 4. 0 – Used in windows 2000+ where AD is not implemented – Challenge Response – 2 versions of NTLM, v 1 and v 2 was introduced in NT 4. 0 SP 4 and is more secure than v 1
 Radius, Diameter, TACACS+ Hey we already talked about these right? . . . So we don’t have to discuss them again?
Radius, Diameter, TACACS+ Hey we already talked about these right? . . . So we don’t have to discuss them again?
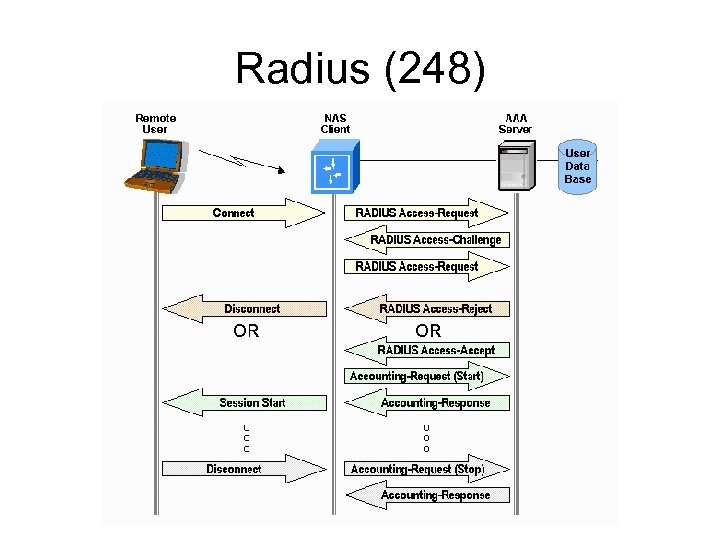 Radius (248)
Radius (248)
 Radius (248) Network AAA protocol • Originally developed by “Livingston” for dial up modem access • Connectionless protocol, using UDP • Port 1812 (authentication) 1813 (accounting) • Requires a radius server and a client (NAS) • Client (NAS) requests for authentication from server (more)
Radius (248) Network AAA protocol • Originally developed by “Livingston” for dial up modem access • Connectionless protocol, using UDP • Port 1812 (authentication) 1813 (accounting) • Requires a radius server and a client (NAS) • Client (NAS) requests for authentication from server (more)
 Radius (248) • Uses “attribute/pair” values (256 different possible attributes/8 bits) – Ex: Framed-IP-Address: 192. 168. 1. 1 • Supports Accounting of usage etc. • Can use PAP, CHAP, EAP for authentication • Main concepts (“Access-Request” and “Access. Accept” or “Access-Reject”) • Radius is used HEAVILY • Can pass other info rather than just “Allow or Deny” such as IP address, or VLAN Problems with Radius next
Radius (248) • Uses “attribute/pair” values (256 different possible attributes/8 bits) – Ex: Framed-IP-Address: 192. 168. 1. 1 • Supports Accounting of usage etc. • Can use PAP, CHAP, EAP for authentication • Main concepts (“Access-Request” and “Access. Accept” or “Access-Reject”) • Radius is used HEAVILY • Can pass other info rather than just “Allow or Deny” such as IP address, or VLAN Problems with Radius next
 Radius Issues (248) • • Only 256 attributes (8 bits of identifiers) Uses UDP, so packets can be lost No encryption of data Radius server cannot connect back to NAS. (could not inform modem bank to kick off a user)
Radius Issues (248) • • Only 256 attributes (8 bits of identifiers) Uses UDP, so packets can be lost No encryption of data Radius server cannot connect back to NAS. (could not inform modem bank to kick off a user)
 Diameter (250) Replacement to RADIUS, is it twice as good? • Uses TCP rather than UDP • Has 128 bits of attribute identifiers (4 billion x 4 billion… NOT 16 billion) • Encrypts messages to avoid Mi. M attacks and recon • Supports Acknowledgements • Allows Server to contact the NAS (could inform the NAS to kick off a user)
Diameter (250) Replacement to RADIUS, is it twice as good? • Uses TCP rather than UDP • Has 128 bits of attribute identifiers (4 billion x 4 billion… NOT 16 billion) • Encrypts messages to avoid Mi. M attacks and recon • Supports Acknowledgements • Allows Server to contact the NAS (could inform the NAS to kick off a user)
 TACACS+ (251) • Similar purpose to Radius • TACACS evolved to XTACACS which evolved to TACACS+, not backwards compatible • Core concept is that each AAA function can be “outsourced” to another server (extensible) • Uses TCP port 49 • Uses Encryption (private key) to secure communication
TACACS+ (251) • Similar purpose to Radius • TACACS evolved to XTACACS which evolved to TACACS+, not backwards compatible • Core concept is that each AAA function can be “outsourced” to another server (extensible) • Uses TCP port 49 • Uses Encryption (private key) to secure communication
 The Golden Ring of Network Authentication
The Golden Ring of Network Authentication
 Single Sign On (n/b) In a large environment with different accounts and passwords it get hard to manage. • Multiple users to create/disable • Passwords to remember, leads to passwords security issues • Reduces user frustration and IT frustration! • This is the “golden ring of network authentication”
Single Sign On (n/b) In a large environment with different accounts and passwords it get hard to manage. • Multiple users to create/disable • Passwords to remember, leads to passwords security issues • Reduces user frustration and IT frustration! • This is the “golden ring of network authentication”
 Remote Access Methods
Remote Access Methods
 Dial Up (n/b) Often companies used to have modems for remote dial up access. If you knew the modems phone number you could dial up and access computing resources. This lead to War dialing (next)
Dial Up (n/b) Often companies used to have modems for remote dial up access. If you knew the modems phone number you could dial up and access computing resources. This lead to War dialing (next)
 War Dialing
War Dialing
 War dialing (n/b) Would you like to play a game… NO! Someone explain war dialing for me. Countermeasures • Require authentication • Require caller id verification – Problems - spoof able • Call backs – Problems - Call forwarding
War dialing (n/b) Would you like to play a game… NO! Someone explain war dialing for me. Countermeasures • Require authentication • Require caller id verification – Problems - spoof able • Call backs – Problems - Call forwarding
 Telnet (258) The original “virtual” terminal program to emulate “serial terminals” (more)
Telnet (258) The original “virtual” terminal program to emulate “serial terminals” (more)
 Telnet (258) • • Virtual Network Terminal TCP port 23 Still used today (though it shouldn’t be) Downside – NO Encryption at ALL Let’s look at a wireshark capture of telnet traffic in real time!
Telnet (258) • • Virtual Network Terminal TCP port 23 Still used today (though it shouldn’t be) Downside – NO Encryption at ALL Let’s look at a wireshark capture of telnet traffic in real time!
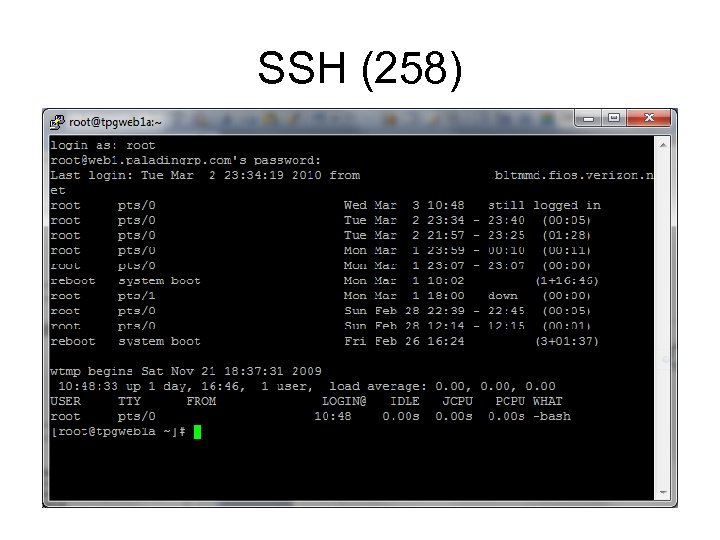 SSH (258)
SSH (258)
 SSH (258) • Secure SHell • Like Telnet but secure • Encrypted, using multiple methods, RSA, 3 DES, Blowfish, IDEA, AES 256 • Can use digital signatures for authentication! Get rid of passwords altogether! • Can be used for tunneling (later) • You should use SSH!
SSH (258) • Secure SHell • Like Telnet but secure • Encrypted, using multiple methods, RSA, 3 DES, Blowfish, IDEA, AES 256 • Can use digital signatures for authentication! Get rid of passwords altogether! • Can be used for tunneling (later) • You should use SSH!
 VNC (n/b) Virtual Network Console • Graphical screen/login of remote machine • Uses LOTS of bandwidth • Authentication is weakly encrypted • Screen “data” is NOT encrypted
VNC (n/b) Virtual Network Console • Graphical screen/login of remote machine • Uses LOTS of bandwidth • Authentication is weakly encrypted • Screen “data” is NOT encrypted
 RDP
RDP
 RDP Remote Desktop Protocol • A Microsoft remote desktop protocol • TCP 3389 • Encryption with RC 4 (newer versions of RDP) • Audio, printer, and file redirection
RDP Remote Desktop Protocol • A Microsoft remote desktop protocol • TCP 3389 • Encryption with RC 4 (newer versions of RDP) • Audio, printer, and file redirection
 VPNs
VPNs
 VPN
VPN
 VPN (260) Virtual Private Network – Generic term for building a secure “virtual” network over a normal network (such as the Internet) • Can simply encrypt traffic between two points • Can actually “tunnel” one type of network traffic over another Network type • Can encrypt tunneled data • Can provide authentication of data endpoints • Often used for remote access for users • Often used to tie organizations remote offices together
VPN (260) Virtual Private Network – Generic term for building a secure “virtual” network over a normal network (such as the Internet) • Can simply encrypt traffic between two points • Can actually “tunnel” one type of network traffic over another Network type • Can encrypt tunneled data • Can provide authentication of data endpoints • Often used for remote access for users • Often used to tie organizations remote offices together
 VPN protocols We’ll talk about IPSec, L 2 TP and PPTP next
VPN protocols We’ll talk about IPSec, L 2 TP and PPTP next
 PPTP (254) Point to Point Tunneling protocol • Lead by Microsoft protocol for “tunneling VPN” • Uses TCP port 1723 (must keep open on firewall) • Uses RC 4 encryption with 40 or 128 key • Generally implemented in software
PPTP (254) Point to Point Tunneling protocol • Lead by Microsoft protocol for “tunneling VPN” • Uses TCP port 1723 (must keep open on firewall) • Uses RC 4 encryption with 40 or 128 key • Generally implemented in software
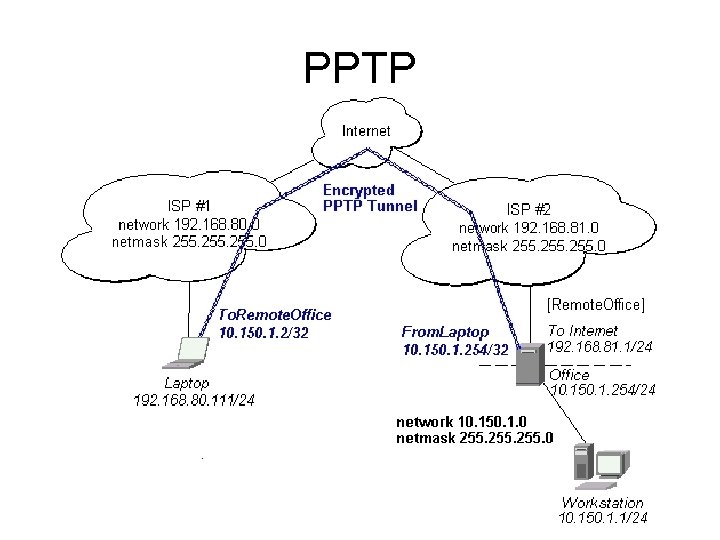
 PPTP operation (254) 1. Remote user connects to ISP, get’s an Internet Address 2. Establishes VPN connection to work VPN server, get’s Internal IP address. 3. Sends “Private IP packets” encrypted within packets sent on the Internet using “public IP addresses” visualization next slide
PPTP operation (254) 1. Remote user connects to ISP, get’s an Internet Address 2. Establishes VPN connection to work VPN server, get’s Internal IP address. 3. Sends “Private IP packets” encrypted within packets sent on the Internet using “public IP addresses” visualization next slide
 PPTP
PPTP
 PPTP issues • Only can tunnel network packets within IP packets
PPTP issues • Only can tunnel network packets within IP packets
 L 2 TP (257) Layer 2 Tunneling Protocol • Cisco protocol • Designed for use over multiple different networks including Layer 2 networks (ATM, Frame Relay etc) • Uses UDP port 1701 (must allow firewall access) • Generally implemented in hardware
L 2 TP (257) Layer 2 Tunneling Protocol • Cisco protocol • Designed for use over multiple different networks including Layer 2 networks (ATM, Frame Relay etc) • Uses UDP port 1701 (must allow firewall access) • Generally implemented in hardware
 L 2 TP (257) Problems • Doesn’t encrypt data, though can be combined with IPSec to do encryption
L 2 TP (257) Problems • Doesn’t encrypt data, though can be combined with IPSec to do encryption
 IP Sec (261) • Intended to add security to IPv 6, back ported to IPv 4 • Can provide Integrity and Confidentiality as well as data origin authentication. • Uses additional headers – AH – ESP • Tunnel, or Transport – what’s the difference (next) • Uses Security Associations (SA) (in a few) • Uses IP protocol 50 ESP headers, 51 for AH headers.
IP Sec (261) • Intended to add security to IPv 6, back ported to IPv 4 • Can provide Integrity and Confidentiality as well as data origin authentication. • Uses additional headers – AH – ESP • Tunnel, or Transport – what’s the difference (next) • Uses Security Associations (SA) (in a few) • Uses IP protocol 50 ESP headers, 51 for AH headers.
 Transport and Tunneling • Transport does not actually tunnel IP within IP. It only encapsulates the transport layer and above • Tunnel actually encapsulates IP within IP an entirely new IP packet is encapsulated within an external IP packet See next slide
Transport and Tunneling • Transport does not actually tunnel IP within IP. It only encapsulates the transport layer and above • Tunnel actually encapsulates IP within IP an entirely new IP packet is encapsulated within an external IP packet See next slide
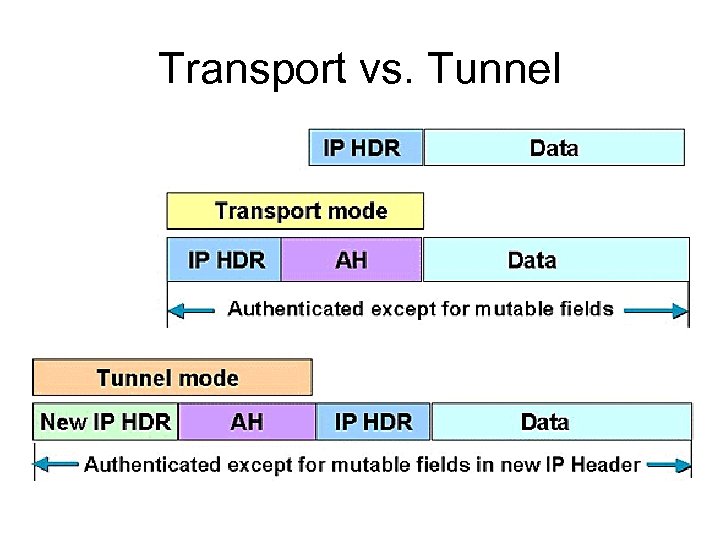 Transport vs. Tunnel
Transport vs. Tunnel
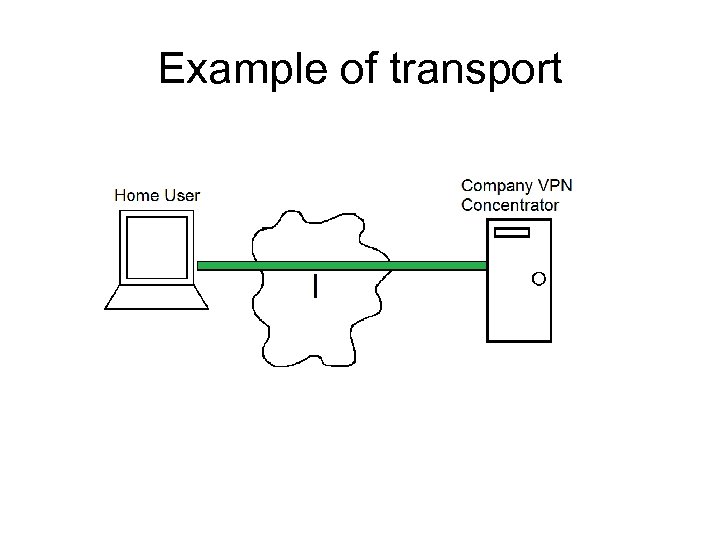 Example of transport
Example of transport
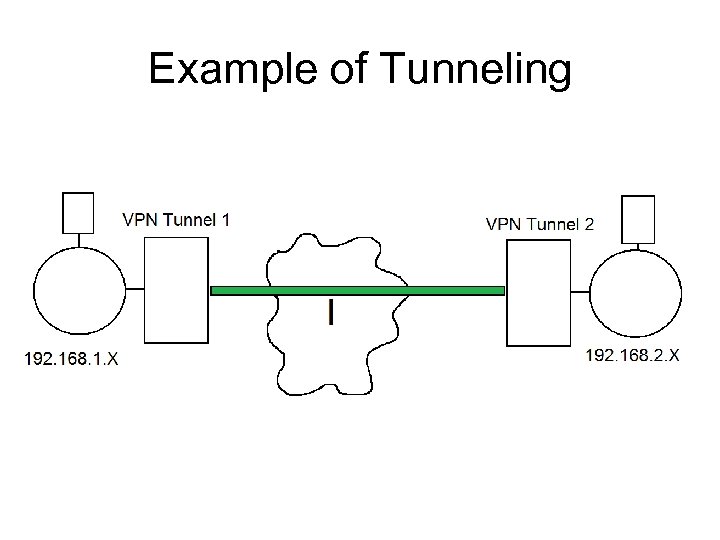 Example of Tunneling
Example of Tunneling
 IPSEC • AH - authentication header – Protocol number 51 – Authentication only • ESP – Encapsulating security payload – Protocol number 50 – Encryption
IPSEC • AH - authentication header – Protocol number 51 – Authentication only • ESP – Encapsulating security payload – Protocol number 50 – Encryption
 IP SEC SA From Cisco: The concept of a security association (SA) is fundamental to IPSec. An SA is a relationship between two or more entities that describes how the entities will use security services to communicate securely. IPSec provides many options for performing network encryption and authentication. Each IPSec connection can provide encryption, integrity, authenticity, or all three. When the security service is determined, the two IPSec peers must determine exactly which algorithms to use (for example, DES or 3 DES for encryption, MD 5 or SHA for integrity). After deciding on the algorithms, the two devices must share session keys. As you can see, there is quite a bit of information to manage. The security association is the method that IPSec uses to track all the particulars concerning a given IPSec communication session (more)
IP SEC SA From Cisco: The concept of a security association (SA) is fundamental to IPSec. An SA is a relationship between two or more entities that describes how the entities will use security services to communicate securely. IPSec provides many options for performing network encryption and authentication. Each IPSec connection can provide encryption, integrity, authenticity, or all three. When the security service is determined, the two IPSec peers must determine exactly which algorithms to use (for example, DES or 3 DES for encryption, MD 5 or SHA for integrity). After deciding on the algorithms, the two devices must share session keys. As you can see, there is quite a bit of information to manage. The security association is the method that IPSec uses to track all the particulars concerning a given IPSec communication session (more)
 IP Sec SA (262) • Unidirectional, need two for bi-directional communication • SAs are identified by an SPI (Security Parameter Index )
IP Sec SA (262) • Unidirectional, need two for bi-directional communication • SAs are identified by an SPI (Security Parameter Index )
 IPSEC random info • Does not define specific encryption algorithms, open framework. • Uses ISAKMP (TCP 500) for SA and key exchange
IPSEC random info • Does not define specific encryption algorithms, open framework. • Uses ISAKMP (TCP 500) for SA and key exchange
 Chapter 9 – Review Questions Q. Name the 3 AAA protocols we talked about Q. Which of the following items does Kerberos use. – – Shared keys Tickets Public keys Digital signatures Q. Does L 2 TP use TCP or UDP? Q. Explain the difference between CHAP and PAP
Chapter 9 – Review Questions Q. Name the 3 AAA protocols we talked about Q. Which of the following items does Kerberos use. – – Shared keys Tickets Public keys Digital signatures Q. Does L 2 TP use TCP or UDP? Q. Explain the difference between CHAP and PAP
 Chapter 9 – Review Questions Q. What protocol (TCP/UDP) does Radius use, how about TACACS+ Q. Why is Telnet bad? Q. What is the purpose of a VPN? Q. What protocol does PPTP require for operation?
Chapter 9 – Review Questions Q. What protocol (TCP/UDP) does Radius use, how about TACACS+ Q. Why is Telnet bad? Q. What is the purpose of a VPN? Q. What protocol does PPTP require for operation?


