4b2709fbeb06dce4f0176abe58821a09.ppt
- Количество слайдов: 22

Security, Access and Privacy GIS Management’s Responsibilities As a computer, I find your faith in technology rather amusing. Anon. 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 1

Five Primary Responsibilities • Integrity – assuring that info. is correct and protected from unauthorized alteration • Recoverability – assuring that no essential information is lost and data can be recovered in the event of any disruption • Continuity – assuring that the agency’s essential operations can be reactivated in the event of any disruption • Confidentiality – assuring that legally protected data is not disclosed to the public or others • Accessibility – assuring that appropriate information is available to all persons with a right to know, including users, management and the public 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 2

Other Issues • GIS is data driven – these primary responsibilities reflect data-related issues • other security and ethics-related issues, not specifically addressed here, include – responsibility, accountability, and liability • snow storm, roof collapses, people lose money, who is liable? – intellectual property: trade secrets, copyright, patents • It’s certainly more than controlling software copying – equity, access, and social impact • does info. access widen social and economic divisions? – personal protection and health • safety hazards in the workplace 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 3

Security and Risk Management • The five primary responsibilities fundamentally revolve around appropriate security policies and procedures • in turn, these are part of a broader concept of risk management, previously primarily considered in the private sector, but since 9/11 critical in both private and public sectors. • Dealing with these requires familiarity, not just with technology, but also with – – federal laws and regulations state laws and regulations local (city, county, etc. ) ordinances organizational policies And with the nature of risk itself. 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 4
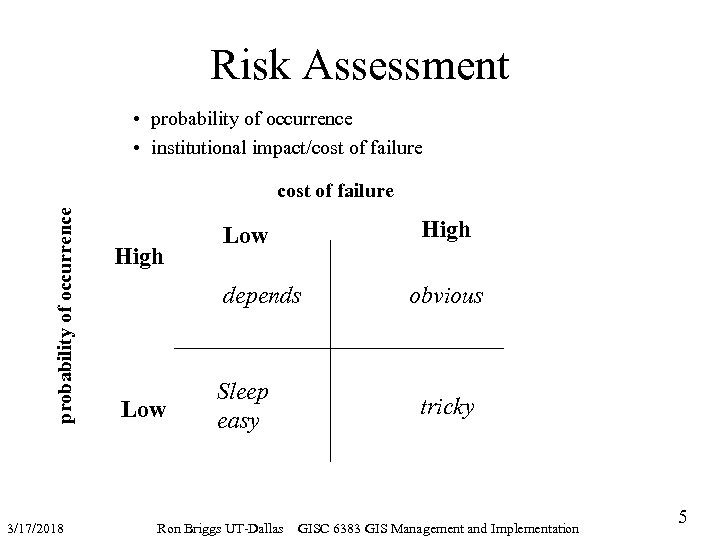
Risk Assessment • probability of occurrence • institutional impact/cost of failure probability of occurrence cost of failure 3/17/2018 High Low depends Low Sleep easy Ron Briggs UT-Dallas obvious tricky GISC 6383 GIS Management and Implementation 5

Contingency Planning “The bottom line is that there is, and always has been, a direct correlation between technology’s ability to give us power one moment and to render us powerless the next. There a number of ways to deal with this dilemma. One is to avoid technology completely--keep your money in a mattress, correspond by mail, ride a horse, burn candles. But there are drawbacks even here, like saddle sores and melted wax stuck to tables. And for {GIS managers} it would mean choosing another profession, like pottery, basket weaving or glass blowing. A better answer is to get the most out of technology when it works, but to be prepared when it doesn’t. Industry vernacular refers to it as contingency planning. I call it common sense. ” John Foley Communications Week, 1/14/91 Contingency Planning…planning for the five responsibilities… 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 6

Integrity • error control: ensuring data is correct – data entry and change • automated capture at the source • double input • input masks and validation rules (domains and defaults) – journaling: tracking all changes – data audits • security policy/procedures: preventing unauthorized access & alteration – – written policies & procedures for security employee training and awareness programs CRUD rules for every employee or employee class (create, read, update, delete) software capable of implementing policies & rules • personal verification: required by federal law – policies/procedures for how persons verify correctness of their records – policies/procedures for how identified errors are corrected Industry standard databases (e. g Oracle) have more capabilities in these regards than GIS-specific database systems (e. g. Info and even Geodatabase) 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 7

Integrity as a Process • Authentification of User Access – User. Id/Passwords – Smart cards – Biometrics (finger print, retina scan, etc. . ) • Communication Encryption – Integrity of data as it moves – Encryption of data stream • Data Access Control (to data base elements) – Control of individual users down to data element level: • fine grain CRUD policies – No knowledge of access level • Unauthorized data is invisible • Unaware of level of access (don’t know if know everything) • Data Integrity (of data base elements) – Integrity of data at it rests – Entered correctly and changed legitimately • Comprehensive Auditing (of all data access) – Tracking “who, what, when” for all entry and change – In case any of the above steps fail 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 8

Recoverability • disaster recovery methods – back-ups – mirroring/fault tolerant systems • disaster recovery implementation – on-site copies for rapid recovery from equipment failures – off-site copies “ beyond destruction radius” for disasters Issues – must be applied to desktop systems (if they contain critical data) as well as central servers – applies equally to non-digital and digital data – the early unreliability of digital data storage devices has heightened our awareness of the need for back-up for all data 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 9

• Requires Continuity – Data – Systems – People: what happens if your staff (and/or you) are wiped out? • disaster recovery methods – mirroring/fault tolerant systems • useless for destructive disasters! – interagency swop agreements – commercial services: hot sites/cold sites • disaster recovery planning – cannot be “dealt with when it happens” – written plan essential • prioritize data/applications to be recovered – regular testing of plan essential for training and refinement Issues – not just for 911 and public safety issues – can you generate tax bills or payroll? 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 10

Confidentiality Classifying Data • Texas law requires state agencies to classify all data as • confidential (exempt from Open Records Act), or • sensitive (accuracy and integrity critical), or • open and freely available • It’s good practice for other public organizations to do likewise Ensuring Confidentiality • methods for achieving confidentiality are the same as for ensuring integrity • consistent and continuous implementation of security policies and procedures is the essential key • any new GIS manager should begin by requesting a copy of the agency’s security and/or information access policies and procedures, and be most concerned if they don’t exist! 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 11

Accessibility: Open Records • Open Records laws exist at both the federal and state levels • fundamentally, they provide the public with the right to inspect government records (digital or non-digital) • purpose of these laws is primarily – to ensure correctness of records – to prevent tyranny and inappropriate record collection – to expose inefficiency and ineptitude • laws can vary considerable between states, with Texas having an especially aggressive law – all government held data is openly available unless it is specifically exempt (and thus by definition is confidential) • these laws give rise to several managerial challenges! 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 12

Accessibility: Open Records versus Privacy • Open Records versus Privacy (confidentiality) is a fundamental dilemma for all persons involved in information management in the public sector • you are legally required to make records available for public inspection and to protect the confidentiality of individuals • these frequently conflict but each is deeply engrained in US • openness of government: – deeply engrained as a protection against government tyranny, and lately, ineptitude and inefficiency • the right to personal privacy: – equally deeply engrained in the constitution and the law • the conflict cannot be resolved, only balanced • balancing should be done via policy developed (or at least approved) by senior agency management, not on an ad hoc basis by the GIS manager – But GIS managers may need to take the initiative to get a policy in place! 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 13

Accessibility: Open Records and Public Domain • information “in the public domain” can be freely used, copied, modified, distributed, or sold by any person or organization for any purpose including profit making • open records laws, in effect, place all government data (unless specifically exempted) “in the public domain” • further, federal, and many state laws (including Texas), limit the cost governments my charge for data to the “cost of reproduction” and specifically prohibit recovery of “costs for data collection” (which are invariably dramatically higher) • Texas, for a temporary period, had a specific exemption for data derived from “geographic information systems” but this has long expired • internationally, US policy is more the exception than the norm Get a copy of: Office of the Texas Attorney General Public Information Handbook, now on-line at http: //www. oag. state. tx. us/AG_Publications/pdfs/publicinfo_hb 2006. pdf 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 14

Accessibility: The Public Domain Debate Pro • required to ensure integrity of the open records policy • tax payers have already paid once, should not have to pay twice • free information flow essential to the operation of a democracy • information is in essence a public good (like police and the military) and should be treated as such • information availability has fostered US dominance of info-based industries (e. g. GIS and GPS) 3/17/2018 Ron Briggs UT-Dallas Con • costs should be paid by people who use the data, not by everyone • taxes could be reduced for everyone if governments could recoup data collection costs • information is a valuable resource (like land), which governments should manage as such (and not give away!) • better data (updated, maintained, etc. ) would be available if governments could benefit financially • encourages “freeloaders” who avoid their “fair share” of cooperative projects since data will be free later GISC 6383 GIS Management and Implementation 15

Major Texas Legislation • Texas Public Information Act, 1997 (as amended) – requires that government records be made available upon request – Originally enacted as Texas Open Records Act, 1973 – much amended; recodified in 1993 as Title 5, Chp. 552 Open Records • Office of the Attorney General 2006 Public Information Handbook http: //www. oag. state. tx. us/AG_Publications/pdfs/publicinfo_hb 2006. pdf – Applies to all state and local agencies and boards • Information Resources Management Act, 1992 (as amended) IRMA § 2054 (see also Texas Administrative Code 1 -TAC-201— Texas Department of Information Resources) – incorporates a wide array of issues including requirements for designating an information resources manager with responsibility for strategic planning, computer and network security policies, classification of data, risk assessment, etc. – mandatory only for state agencies, but is a useful guide for non-state organizations For entire text, go to: http: //www. capitol. state. tx. us/statutes/docs/GV/content/htm/gv. 010. 002054. 00. htm For summary of requirements to be met by any state agency go to: http: //www. dir. state. tx. us/standards/checklist. htm For security-specific information and requirements, go to: http: //www. dir. state. tx. us/security/policies/index. htm Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 16

GIS-Specific Requirements and Policies • For Texas: Texas Geographic Information Council: http: //www. dir. state. tx. us/tgic/pubs. htm • At Federal level: Federal Geographic Data Committee Policy on Access to Public Information http: //www. fgdc. gov/fgdc/policies. html Appropriate Access to Geospatial Data in Response to Security Concerns http: //www. fgdc. gov/fgdc/homeland/index. html • GIS data on web and its implications for homeland security (RAND, 2004) – http: //www. rand. org/news/press. 04/03. 25. html Press release and conclusion – http: //www. rand. org/publications/RB/RB 9045/ Summary of study – http: //www. rand. org/pubs/monographs/2004/RAND_MG 142. pdf Full document • GIS Code of Ethics from URISA (Urban and Regional Information Systems Association) http: //www. urisa. org/ethics/code_of_ethics. htm 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 17

Homeland Security: all disasters are local! Mitigation • Prevention Reaction • Preparedness – Apprehension of terrorists before attack – Information sharing, hot spatial analysis • Protection – control access to hazards & critical infrastructure – location of hazards, establish buffer zones, limit web information? • Detection – Of intrusions – Real-time display of sensor data with map – Preparing for actual emergences – Backups, emergency supplies and their location • Response – Rescue, evacuation, medical care, secondary damage control – assess scope of disaster; coordinate response • Recovery – Short term: food, water, etc Long term: restore to prior state – Visual status maps Planning is the essential component. Data, its distribution, and its display is the critical GIS contribution R. W. Green: Confronting Catastrophe: A GIS Handbook ESRI Press, 2002 3/17/2018

Emergency Management & Homeland Security • Homeland Security is simply a special case of emergency management • The same principles apply in dealing with any emergency. • Indeed, your “five security responsibilities” are nothing more than the application of emergency management principles to your own operation Emergency Types: differ by --mitigation options available --length of planning horizon Natural Disasters: unplanned natural events such as tornados, hurricanes, floods, droughts, insect infestations, extreme heat or cold – Limited mitigation options—generally cannot prevent Human disasters: unplanned events or accidents from human activity such as chemical or radiological spills, fires, explosions, etc. . – More mitigation options Internal disturbances: events planned by groups to deliberately cause disruption, but not necessarily destruction – More mitigation options; longer planning horizon for reaction Material shortages: caused by strikes, price wars, resource scarcity, etc. . – More mitigation options; even longer planning horizon (usually) for reaction Attacks: acts of large scale terrorism using conventional, nuclear or biological weapons – Mitigation may differ, but reaction is the same as for natural or human disasters. 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 19

The Great Dilemna • Data, its distribution, and its display is the critical GIS contribution. • Open access to data essential in all disasters. • But will it help terrorists, who cause only a small portion of all disasters? 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 20

The New Reality—a Perfect Storm? • New Technology – Big weapons available to small people – High school biology labs today top Soviet cold war capabilities • New Enemy – Radical ideologies – Only a small percent believe, but it only takes a few • New Approach – apocalyptic terrorism, where the perpetrators death is accepted, even revered • New Vulnerability – technology, especially the power and computer grids – Specialization, for example nobody grows their own food – Processes, such as just in time delivery (a 4 -day food supply in stores) 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 21

More Food for Thought • Google implemented in 2003 a feature wherein you enter someone’s telephone number into the search bar--and get a map to his or her house. • go to: Google www. google. com Type your phone number in the search bar with or without dashes (i. e. 555 -1212 or 5555551212) and hit enter – Then select Mapquest to get a map – Or use Google Earth to get satellite picture • The controversy surrounding the initial introduction of this feature has since died down, but: – The implications of GIS for personal privacy and other important societal values are substantial – as a GIS professional, you must be sensitive to these 3/17/2018 Ron Briggs UT-Dallas GISC 6383 GIS Management and Implementation 22
4b2709fbeb06dce4f0176abe58821a09.ppt