7caea0f0522273d3282c02a3436cd5da.ppt
- Количество слайдов: 38
 Securing Your Wireless Network Ian Hellen Stirling Goetz Microsoft
Securing Your Wireless Network Ian Hellen Stirling Goetz Microsoft
 Agenda Wireless LAN security explained Secure wireless deployment components, Microsoft offerings and benefits Selecting the right WLAN options Microsoft wireless security solutions Microsoft IT case study WLAN scalability and management
Agenda Wireless LAN security explained Secure wireless deployment components, Microsoft offerings and benefits Selecting the right WLAN options Microsoft wireless security solutions Microsoft IT case study WLAN scalability and management
 Wireless LAN Security Many (most? ) WLANs have no security or inadequate security 1 in 3 WLANs in major cities unsecured (RSA) But number of WLANs growing by 66% each year (RSA) Small businesses making most use of WLANs Static WEP (Wired Equivalent Privacy) is easily broken: Tools to generate required traffic Statistical cryptanalysis breaks keys quickly The world is not a nice place: Viruses, worms, trojans, spyware, botnets Hackers, spammers, criminals
Wireless LAN Security Many (most? ) WLANs have no security or inadequate security 1 in 3 WLANs in major cities unsecured (RSA) But number of WLANs growing by 66% each year (RSA) Small businesses making most use of WLANs Static WEP (Wired Equivalent Privacy) is easily broken: Tools to generate required traffic Statistical cryptanalysis breaks keys quickly The world is not a nice place: Viruses, worms, trojans, spyware, botnets Hackers, spammers, criminals
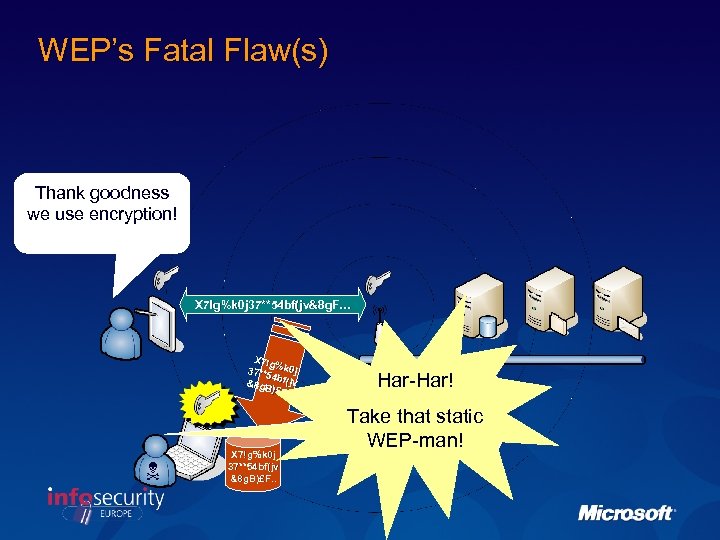 WEP’s Fatal Flaw(s) Thank goodness we use encryption! X 7!g%k 0 j 37**54 bf(jv&8 g. F… X 7!g % 37**5 k 0 j 4 bf(j v &8 g. B )£F. . N X 7!g%k 0 j 37**54 bf(jv &8 g. B)£F. . Har-Har! Take that static WEP-man!
WEP’s Fatal Flaw(s) Thank goodness we use encryption! X 7!g%k 0 j 37**54 bf(jv&8 g. F… X 7!g % 37**5 k 0 j 4 bf(j v &8 g. B )£F. . N X 7!g%k 0 j 37**54 bf(jv &8 g. B)£F. . Har-Har! Take that static WEP-man!
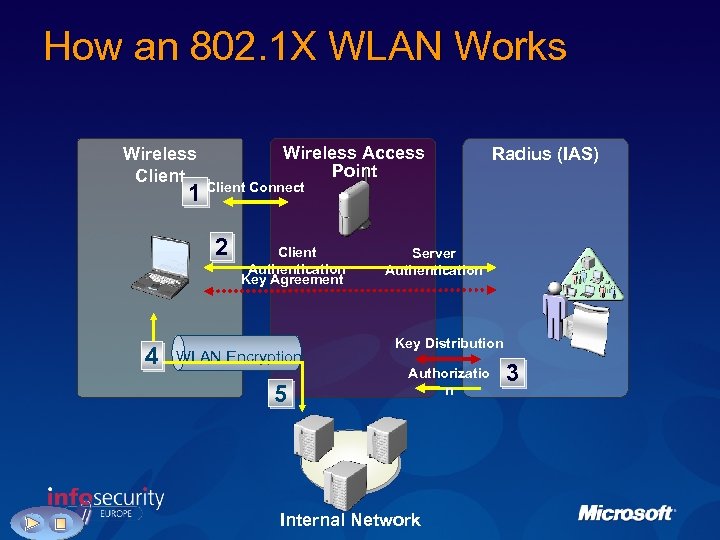 How an 802. 1 X WLAN Works Wireless Access Point Wireless Client Radius (IAS) 1 Client Connect 2 4 Client Authentication Key Agreement WLAN Encryption 5 Server Authentication Key Distribution Authorizatio n Internal Network 3
How an 802. 1 X WLAN Works Wireless Access Point Wireless Client Radius (IAS) 1 Client Connect 2 4 Client Authentication Key Agreement WLAN Encryption 5 Server Authentication Key Distribution Authorizatio n Internal Network 3
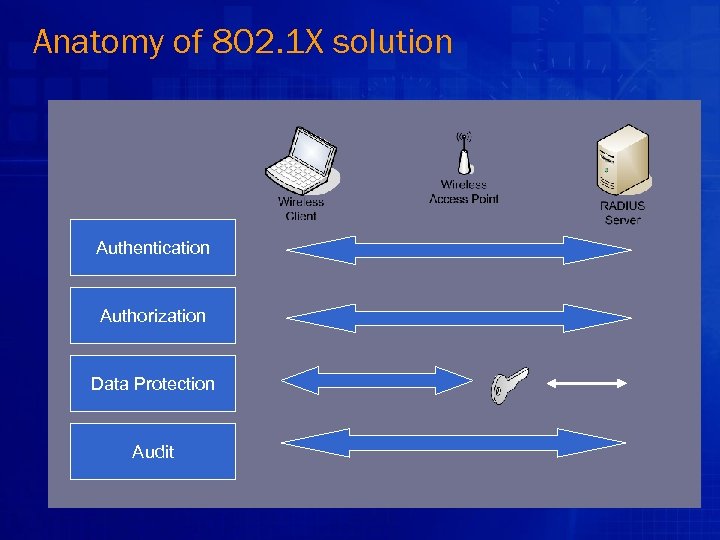 Anatomy of 802. 1 X solution Authentication Authorization Data Protection Audit
Anatomy of 802. 1 X solution Authentication Authorization Data Protection Audit
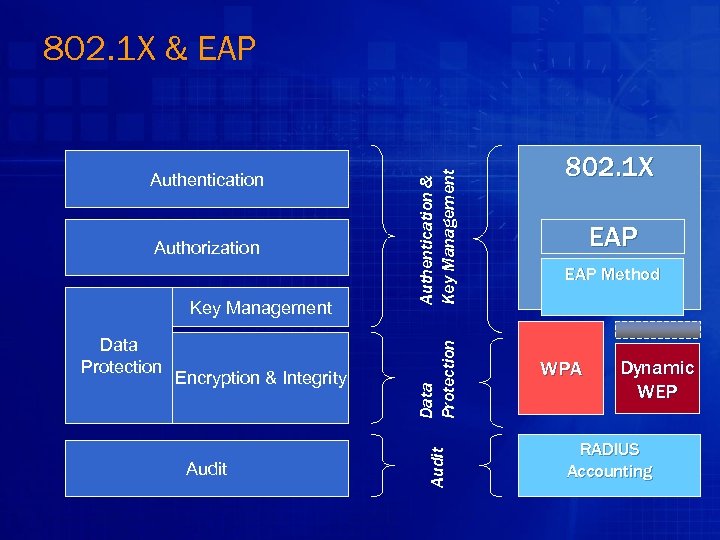 Key Management Data Protection Encryption & Integrity Audit Data Protection Authorization Audit Authentication & Key Management 802. 1 X & EAP 802. 1 X EAP Method WPA Dynamic WEP RADIUS Accounting
Key Management Data Protection Encryption & Integrity Audit Data Protection Authorization Audit Authentication & Key Management 802. 1 X & EAP 802. 1 X EAP Method WPA Dynamic WEP RADIUS Accounting
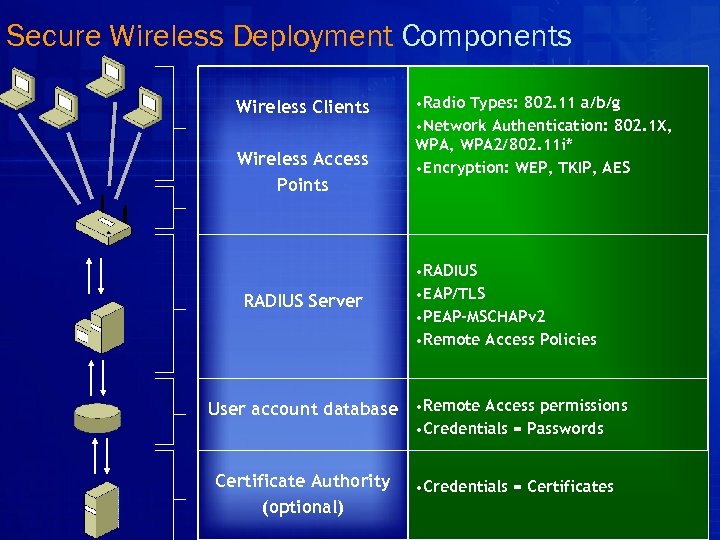 Secure Wireless Deployment Components Wireless Clients Wireless Access Points RADIUS Server • Radio Types: 802. 11 a/b/g • Network Authentication: 802. 1 X, WPA 2/802. 11 i* • Encryption: WEP, TKIP, AES • RADIUS • EAP/TLS • PEAP-MSCHAPv 2 • Remote Access Policies User account database • Remote Access permissions • Credentials = Passwords Certificate Authority (optional) • Credentials = Certificates
Secure Wireless Deployment Components Wireless Clients Wireless Access Points RADIUS Server • Radio Types: 802. 11 a/b/g • Network Authentication: 802. 1 X, WPA 2/802. 11 i* • Encryption: WEP, TKIP, AES • RADIUS • EAP/TLS • PEAP-MSCHAPv 2 • Remote Access Policies User account database • Remote Access permissions • Credentials = Passwords Certificate Authority (optional) • Credentials = Certificates
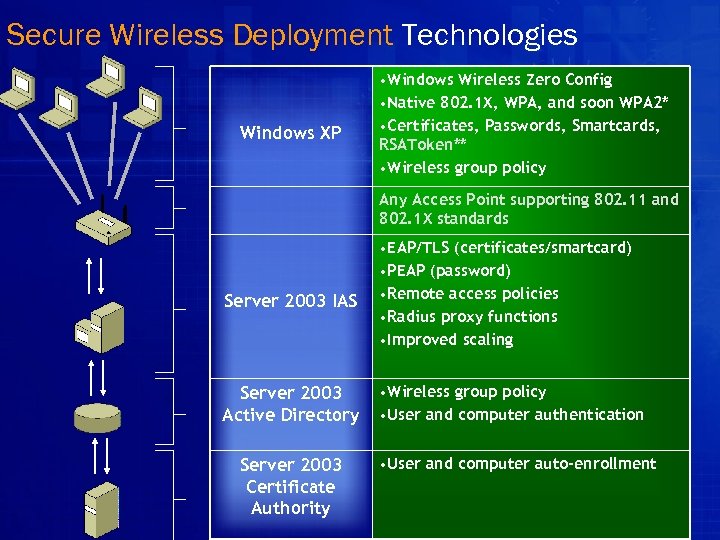 Secure Wireless Deployment Technologies Windows XP • Windows Wireless Zero Config • Native 802. 1 X, WPA, and soon WPA 2* • Certificates, Passwords, Smartcards, RSAToken** • Wireless group policy Any Access Point supporting 802. 11 and 802. 1 X standards Server 2003 IAS • EAP/TLS (certificates/smartcard) • PEAP (password) • Remote access policies • Radius proxy functions • Improved scaling Server 2003 Active Directory • Wireless group policy • User and computer authentication Server 2003 Certificate Authority • User and computer auto-enrollment
Secure Wireless Deployment Technologies Windows XP • Windows Wireless Zero Config • Native 802. 1 X, WPA, and soon WPA 2* • Certificates, Passwords, Smartcards, RSAToken** • Wireless group policy Any Access Point supporting 802. 11 and 802. 1 X standards Server 2003 IAS • EAP/TLS (certificates/smartcard) • PEAP (password) • Remote access policies • Radius proxy functions • Improved scaling Server 2003 Active Directory • Wireless group policy • User and computer authentication Server 2003 Certificate Authority • User and computer auto-enrollment
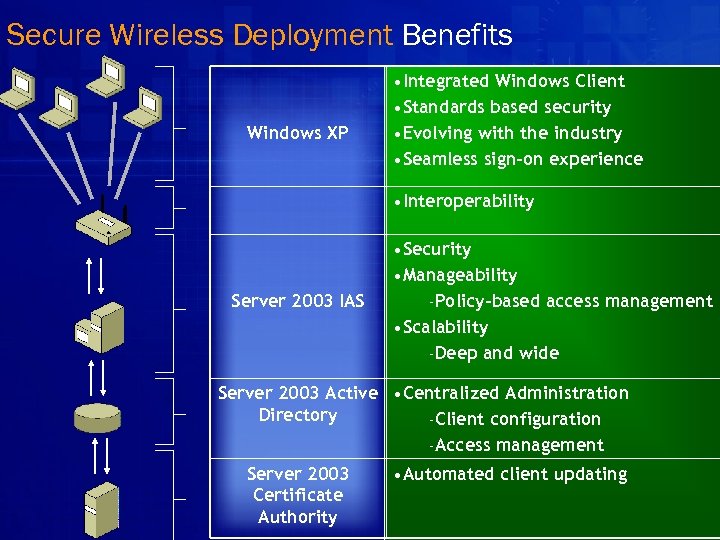 Secure Wireless Deployment Benefits Windows XP • Integrated Windows Client • Standards based security • Evolving with the industry • Seamless sign-on experience • Interoperability Server 2003 IAS • Security • Manageability –Policy-based access management • Scalability –Deep and wide Server 2003 Active • Centralized Administration Directory –Client configuration –Access Server 2003 Certificate Authority management • Automated client updating
Secure Wireless Deployment Benefits Windows XP • Integrated Windows Client • Standards based security • Evolving with the industry • Seamless sign-on experience • Interoperability Server 2003 IAS • Security • Manageability –Policy-based access management • Scalability –Deep and wide Server 2003 Active • Centralized Administration Directory –Client configuration –Access Server 2003 Certificate Authority management • Automated client updating
 Security Best Practices What NOT to do Hidden SSID Does not provide any real security Easily discoverable in well-used environments Windows client experience is impacted MAC Filtering Does not scale NIC management issue MAC is spoofable “Shared” mode Sounds like more security but is actually worse Not to be confused with Pre-Shared Key (PSK) which is more secure Open networks and VPN’s Grants everyone access to the wireless segment Great for hotspots, not for your business
Security Best Practices What NOT to do Hidden SSID Does not provide any real security Easily discoverable in well-used environments Windows client experience is impacted MAC Filtering Does not scale NIC management issue MAC is spoofable “Shared” mode Sounds like more security but is actually worse Not to be confused with Pre-Shared Key (PSK) which is more secure Open networks and VPN’s Grants everyone access to the wireless segment Great for hotspots, not for your business
 Security Best Practices What to do Chose an authentication type (EAP Type) EAP-TLS and both user and computer certificates PEAP-MS-CHAP v 2 and enforce strong user passwords Pre-Shared Key (only with WPA) Chose a WLAN Data Protection Method WPA using TKIP or AES encryption Dynamic WEP using 802. 1 X, forcing periodic reauthentication (10 mins) to renew keys
Security Best Practices What to do Chose an authentication type (EAP Type) EAP-TLS and both user and computer certificates PEAP-MS-CHAP v 2 and enforce strong user passwords Pre-Shared Key (only with WPA) Chose a WLAN Data Protection Method WPA using TKIP or AES encryption Dynamic WEP using 802. 1 X, forcing periodic reauthentication (10 mins) to renew keys
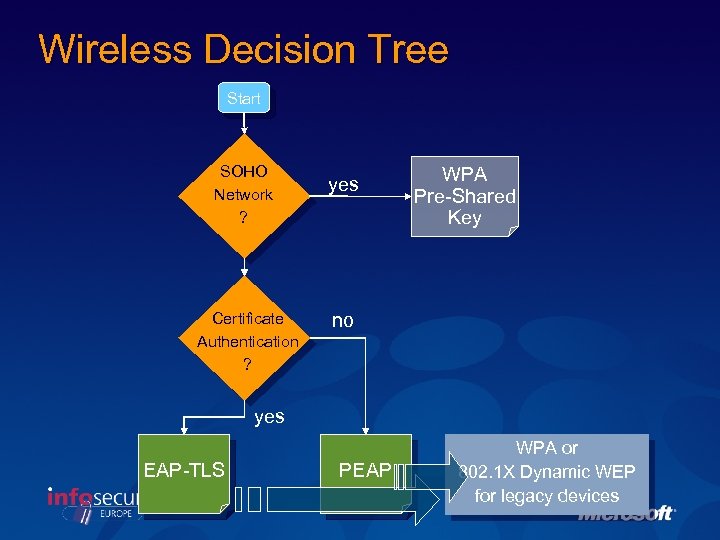 Wireless Decision Tree Start SOHO Network ? Certificate Authentication ? yes WPA Pre-Shared Key no yes EAP-TLS PEAP WPA or 802. 1 X Dynamic WEP for legacy devices
Wireless Decision Tree Start SOHO Network ? Certificate Authentication ? yes WPA Pre-Shared Key no yes EAP-TLS PEAP WPA or 802. 1 X Dynamic WEP for legacy devices
 Configuring WPA-PSK Demonstration
Configuring WPA-PSK Demonstration
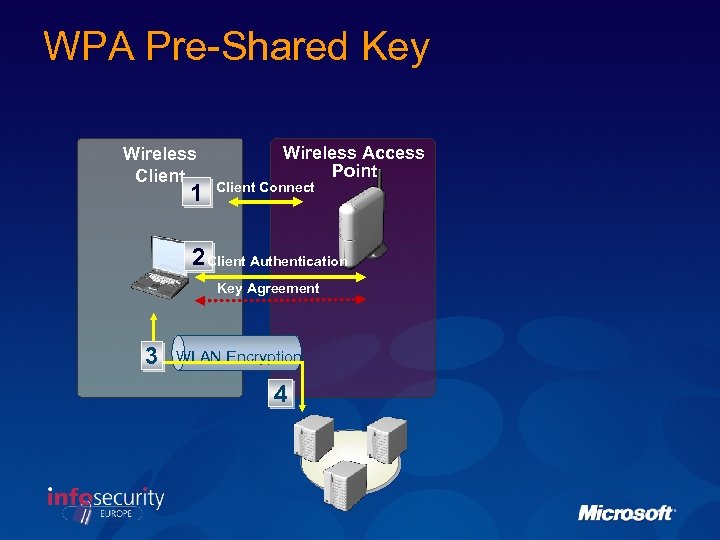 WPA Pre-Shared Key Wireless Client 1 Wireless Access Point Client Connect 2 Client Authentication Key Agreement 3 WLAN Encryption 4
WPA Pre-Shared Key Wireless Client 1 Wireless Access Point Client Connect 2 Client Authentication Key Agreement 3 WLAN Encryption 4
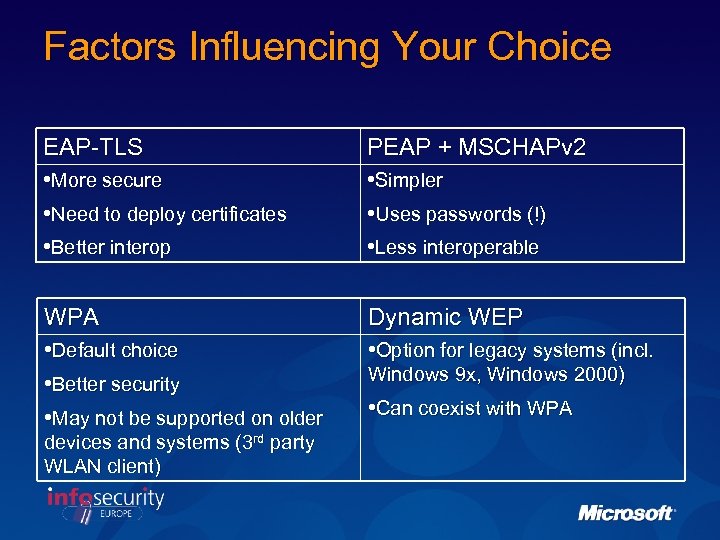 Factors Influencing Your Choice EAP-TLS PEAP + MSCHAPv 2 • More secure • Need to deploy certificates • Better interop • Simpler • Uses passwords (!) • Less interoperable WPA Dynamic WEP • Default choice • Better security • May not be supported on older • Option for legacy systems (incl. devices and systems (3 rd party WLAN client) Windows 9 x, Windows 2000) • Can coexist with WPA
Factors Influencing Your Choice EAP-TLS PEAP + MSCHAPv 2 • More secure • Need to deploy certificates • Better interop • Simpler • Uses passwords (!) • Less interoperable WPA Dynamic WEP • Default choice • Better security • May not be supported on older • Option for legacy systems (incl. devices and systems (3 rd party WLAN client) Windows 9 x, Windows 2000) • Can coexist with WPA
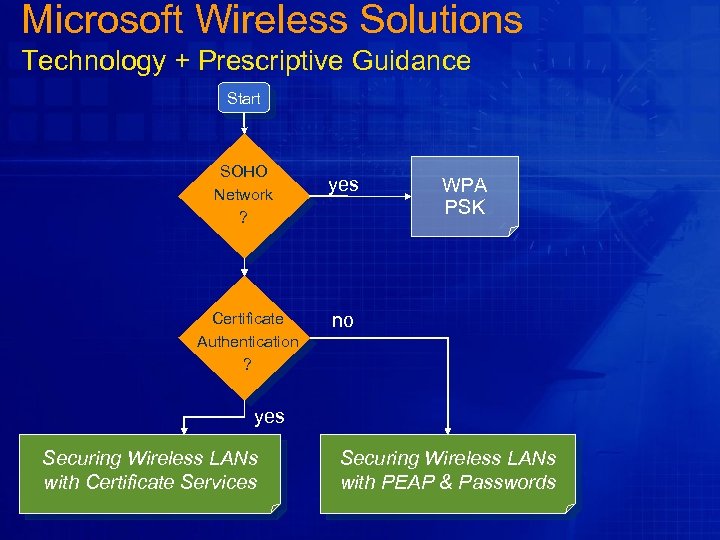 Microsoft Wireless Solutions Technology + Prescriptive Guidance Start SOHO Network ? Certificate Authentication ? yes WPA PSK no yes Securing Wireless LANs with Certificate Services Securing Wireless LANs with PEAP & Passwords
Microsoft Wireless Solutions Technology + Prescriptive Guidance Start SOHO Network ? Certificate Authentication ? yes WPA PSK no yes Securing Wireless LANs with Certificate Services Securing Wireless LANs with PEAP & Passwords
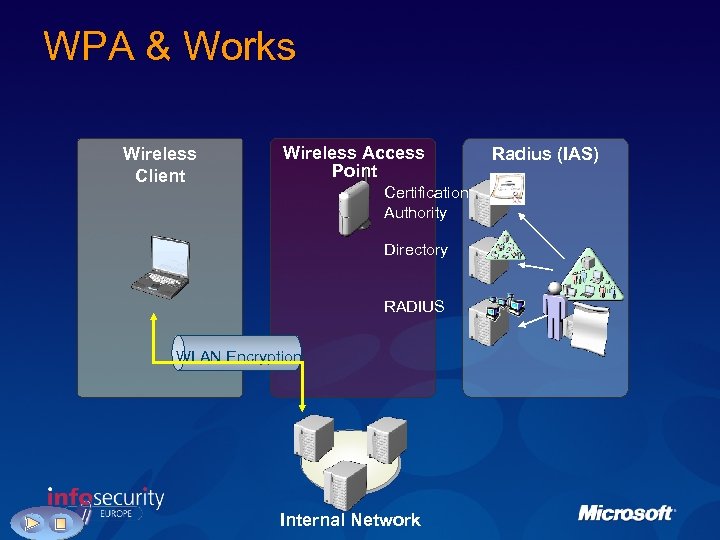 WPA & Works Wireless Client Wireless Access Point Certification Authority Directory RADIUS WLAN Encryption Internal Network Radius (IAS)
WPA & Works Wireless Client Wireless Access Point Certification Authority Directory RADIUS WLAN Encryption Internal Network Radius (IAS)
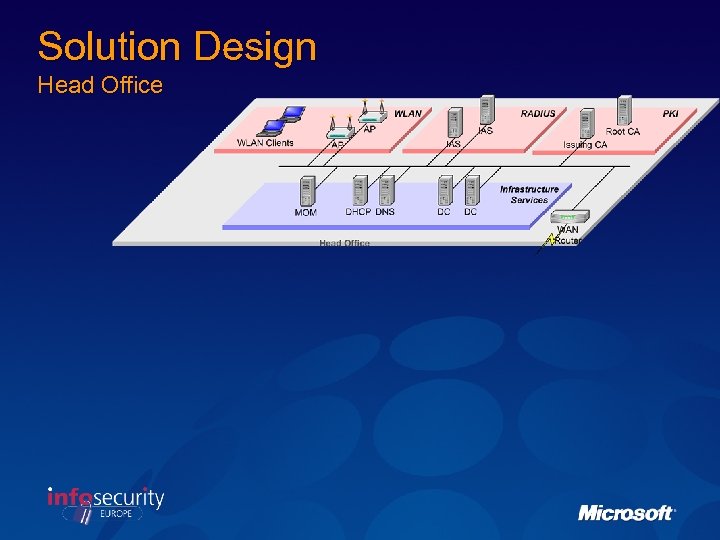 Solution Design Head Office
Solution Design Head Office
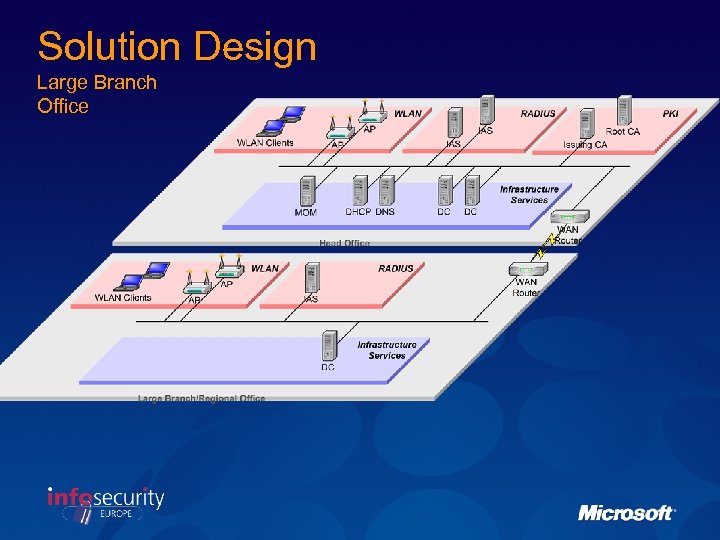 Solution Design Large Branch Office
Solution Design Large Branch Office
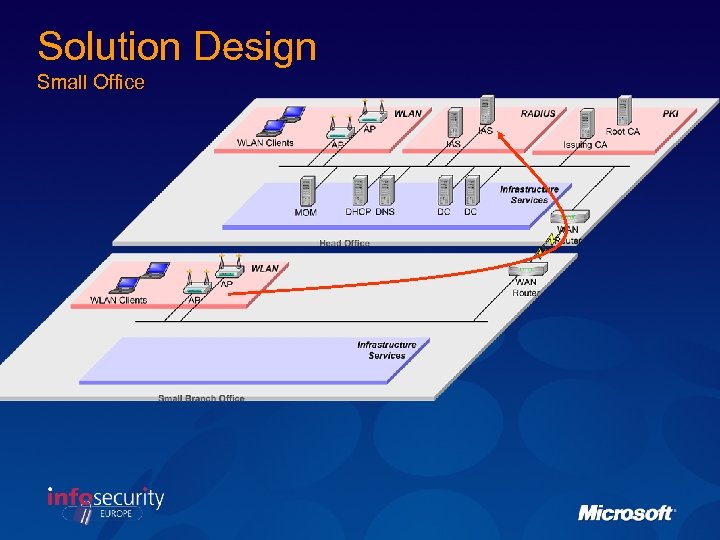 Solution Design Small Office
Solution Design Small Office
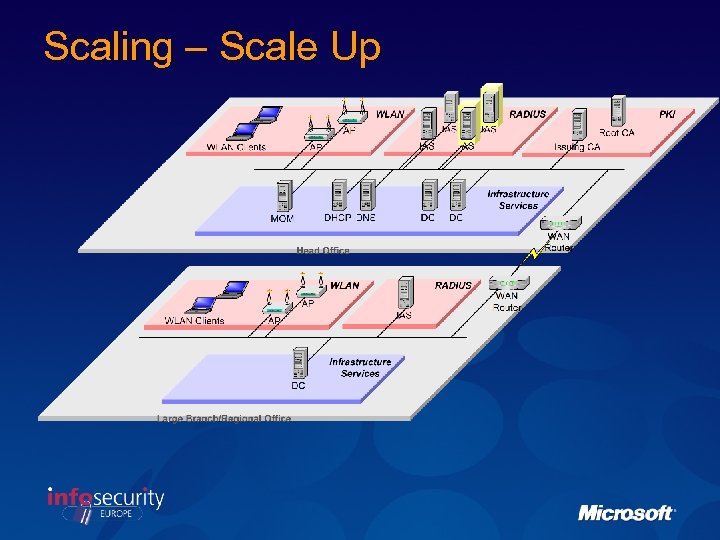 Scaling – Scale Up
Scaling – Scale Up
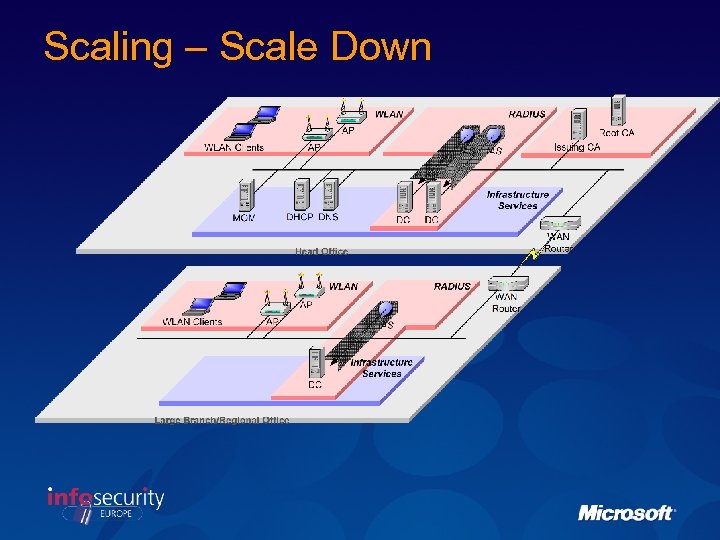 Scaling – Scale Down
Scaling – Scale Down
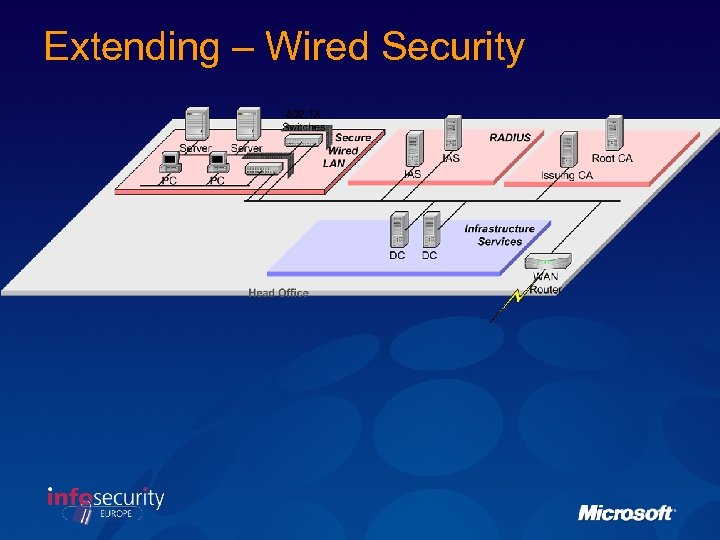 Extending – Wired Security
Extending – Wired Security
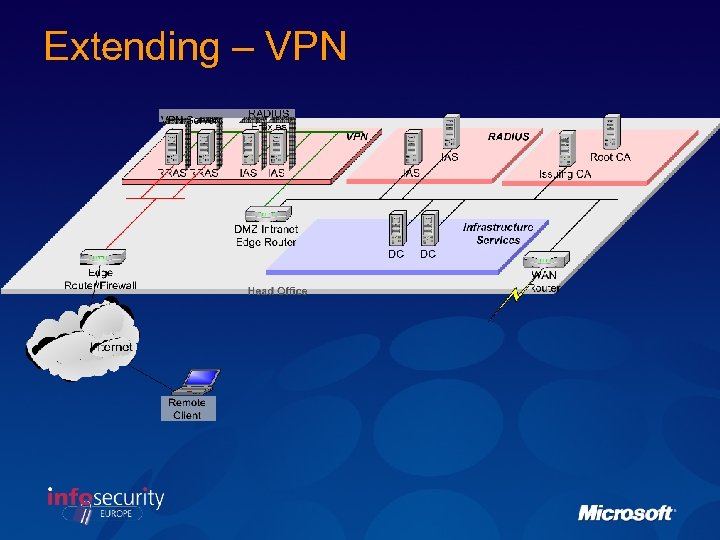 Extending – VPN
Extending – VPN
 Setting up IAS Policies Demonstration
Setting up IAS Policies Demonstration
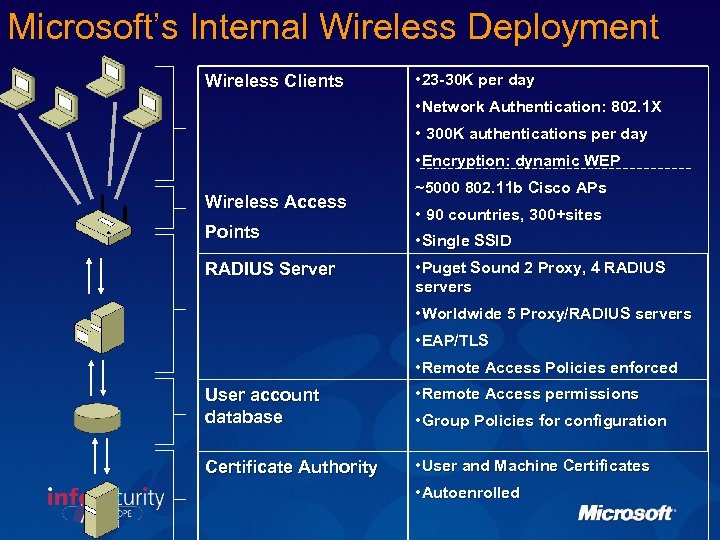 Microsoft’s Internal Wireless Deployment Wireless Clients Wireless Access • 23 -30 K per day • Network Authentication: 802. 1 X • 300 K authentications per day • Encryption: dynamic WEP ~5000 802. 11 b Cisco APs RADIUS Server • 90 countries, 300+sites • Single SSID • Puget Sound 2 Proxy, 4 RADIUS User account database • Worldwide 5 Proxy/RADIUS servers • EAP/TLS • Remote Access Policies enforced • Remote Access permissions • Group Policies for configuration Points Certificate Authority servers • User and Machine Certificates • Autoenrolled
Microsoft’s Internal Wireless Deployment Wireless Clients Wireless Access • 23 -30 K per day • Network Authentication: 802. 1 X • 300 K authentications per day • Encryption: dynamic WEP ~5000 802. 11 b Cisco APs RADIUS Server • 90 countries, 300+sites • Single SSID • Puget Sound 2 Proxy, 4 RADIUS User account database • Worldwide 5 Proxy/RADIUS servers • EAP/TLS • Remote Access Policies enforced • Remote Access permissions • Group Policies for configuration Points Certificate Authority servers • User and Machine Certificates • Autoenrolled
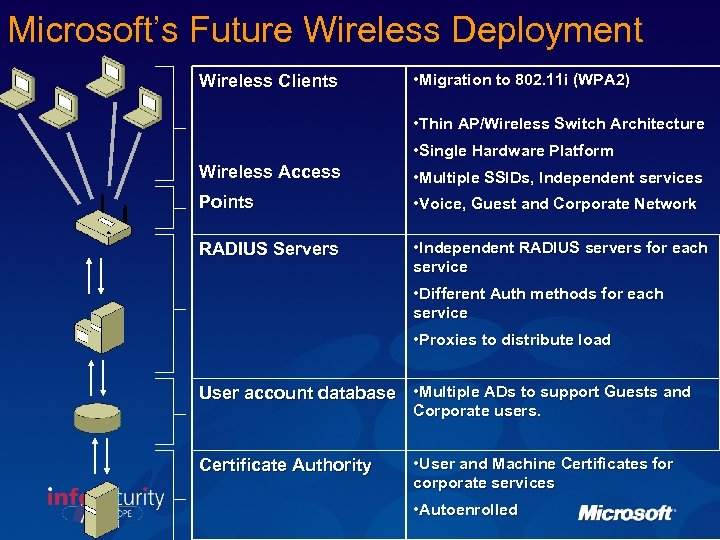 Microsoft’s Future Wireless Deployment Wireless Clients • Migration to 802. 11 i (WPA 2) Wireless Access Points • Thin AP/Wireless Switch Architecture • Single Hardware Platform • Multiple SSIDs, Independent services • Voice, Guest and Corporate Network RADIUS Servers • Independent RADIUS servers for each service • Different Auth methods for each service • Proxies to distribute load User account database • Multiple ADs to support Guests and Corporate users. Certificate Authority • User and Machine Certificates for corporate services • Autoenrolled
Microsoft’s Future Wireless Deployment Wireless Clients • Migration to 802. 11 i (WPA 2) Wireless Access Points • Thin AP/Wireless Switch Architecture • Single Hardware Platform • Multiple SSIDs, Independent services • Voice, Guest and Corporate Network RADIUS Servers • Independent RADIUS servers for each service • Different Auth methods for each service • Proxies to distribute load User account database • Multiple ADs to support Guests and Corporate users. Certificate Authority • User and Machine Certificates for corporate services • Autoenrolled
 Best Practices: Scalability Microsoft RADIUS – Internet Authentication Service (IAS) Install at least two IAS RADIUS servers For best performance, install IAS on domain controllers Use strong RADIUS shared secrets Use as many different RADIUS shared secrets as possible Use IAS RADIUS proxies to scale authentication traffic Use IAS RADIUS proxies for separate account databases
Best Practices: Scalability Microsoft RADIUS – Internet Authentication Service (IAS) Install at least two IAS RADIUS servers For best performance, install IAS on domain controllers Use strong RADIUS shared secrets Use as many different RADIUS shared secrets as possible Use IAS RADIUS proxies to scale authentication traffic Use IAS RADIUS proxies for separate account databases
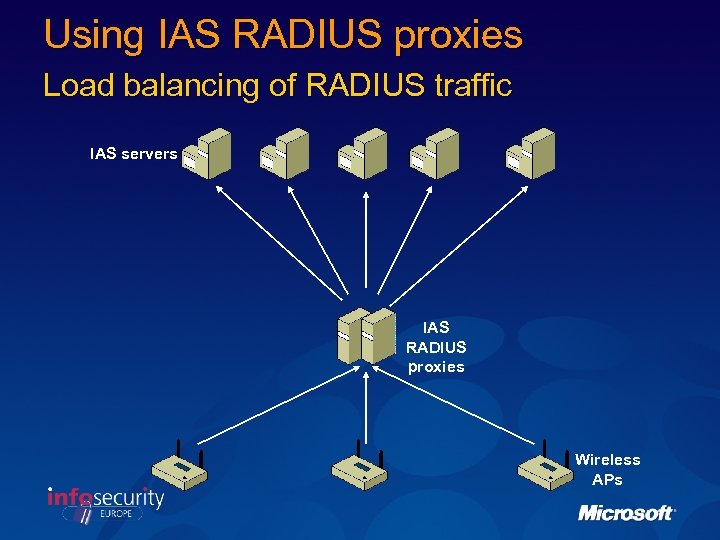 Using IAS RADIUS proxies Load balancing of RADIUS traffic IAS servers IAS RADIUS proxies Wireless APs
Using IAS RADIUS proxies Load balancing of RADIUS traffic IAS servers IAS RADIUS proxies Wireless APs
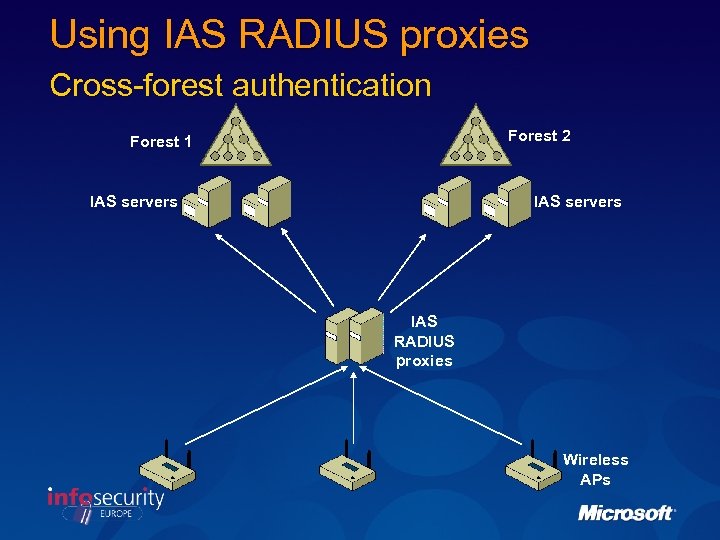 Using IAS RADIUS proxies Cross-forest authentication Forest 2 Forest 1 IAS servers IAS RADIUS proxies Wireless APs
Using IAS RADIUS proxies Cross-forest authentication Forest 2 Forest 1 IAS servers IAS RADIUS proxies Wireless APs
 Security Best Practices Preventing Rogue WLANs User education and policy Ongoing Monitoring Don’t use Hidden SSIDs Do use Wireless Group Policy
Security Best Practices Preventing Rogue WLANs User education and policy Ongoing Monitoring Don’t use Hidden SSIDs Do use Wireless Group Policy
 Best Practices: Management Use the Wireless Network (IEEE 802. 11) Policies Group Policy settings to automatically configure wireless clients running Windows XP and Windows Server 2003 with your SSID If you have a native-mode domain, use universal groups and global groups to organize your wireless computer and user accounts into a single group. Use certificate auto-enrollment for computer certificates Use certificate auto-enrollment for user certificates "Best Practices for Implementing a Microsoft Windows Server 2003 Public Key Infrastructure" on http: //www. microsoft. com/pki.
Best Practices: Management Use the Wireless Network (IEEE 802. 11) Policies Group Policy settings to automatically configure wireless clients running Windows XP and Windows Server 2003 with your SSID If you have a native-mode domain, use universal groups and global groups to organize your wireless computer and user accounts into a single group. Use certificate auto-enrollment for computer certificates Use certificate auto-enrollment for user certificates "Best Practices for Implementing a Microsoft Windows Server 2003 Public Key Infrastructure" on http: //www. microsoft. com/pki.
 Wireless Group Policy Demonstration
Wireless Group Policy Demonstration
 Summary You cannot afford to leave your WLANs unprotected Protecting WLANs is simple Chose the right options for you: SOHO – WPA PSK SMORG-Enterprise – WPA + PEAP (Passwords) LORG-Enterprise – WPA + EAP-TLS (Certs)
Summary You cannot afford to leave your WLANs unprotected Protecting WLANs is simple Chose the right options for you: SOHO – WPA PSK SMORG-Enterprise – WPA + PEAP (Passwords) LORG-Enterprise – WPA + EAP-TLS (Certs)
 Resources Securing Wireless LANs with Certificates http: //go. microsoft. com/fwlink/? Link. Id=14843 Security Wireless LANs with PEAP and Passwords http: //www. microsoft. com/technet/security/topics/cryptographyetc/peap_0. mspx Microsoft Wireless Portal http: //www. microsoft. com/wifi Microsoft Security Solutions http: //www. microsoft. com/technet/security
Resources Securing Wireless LANs with Certificates http: //go. microsoft. com/fwlink/? Link. Id=14843 Security Wireless LANs with PEAP and Passwords http: //www. microsoft. com/technet/security/topics/cryptographyetc/peap_0. mspx Microsoft Wireless Portal http: //www. microsoft. com/wifi Microsoft Security Solutions http: //www. microsoft. com/technet/security
 Microsoft Technical Roadshow 2005 2 -days of in-depth technology information Birmingham – 24 -25 May Harrogate – 1 -2 June London – 7 -8 June Register now at: www. microsoft. com/uk/techroadshow
Microsoft Technical Roadshow 2005 2 -days of in-depth technology information Birmingham – 24 -25 May Harrogate – 1 -2 June London – 7 -8 June Register now at: www. microsoft. com/uk/techroadshow
 www. microsoft. com/uk/security www. microsoft. com/uk/technet/learning © 2005 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
www. microsoft. com/uk/security www. microsoft. com/uk/technet/learning © 2005 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.


