9b5fda4e526a4207d5f67c87f3d9790b.ppt
- Количество слайдов: 63
 Securing Wireless Sensor Networks Wenliang (Kevin) Du Department of Electrical Engineering and Computer Science Syracuse University
Securing Wireless Sensor Networks Wenliang (Kevin) Du Department of Electrical Engineering and Computer Science Syracuse University
 Overview l l Overview of Wireless Sensor Networks (WSN). Security in wireless sensor networks. l l Our recent work on securing WSN using deployment knowledge l l l Why is it different? Authenticating public keys (Mobihoc’ 05) Robust Location discovery (Infocom’ 05) Summary
Overview l l Overview of Wireless Sensor Networks (WSN). Security in wireless sensor networks. l l Our recent work on securing WSN using deployment knowledge l l l Why is it different? Authenticating public keys (Mobihoc’ 05) Robust Location discovery (Infocom’ 05) Summary
 Wireless Sensors Berkeley Motes
Wireless Sensors Berkeley Motes
 Mica Motes l Mica Mote: l l l Processor: 4 Mhz Memory: 128 KB Flash and 4 KB RAM Radio: 916 Mhz and 40 Kbits/second. Transmission range: 100 Feet Tiny. OS operating System: small, open source and energy efficient.
Mica Motes l Mica Mote: l l l Processor: 4 Mhz Memory: 128 KB Flash and 4 KB RAM Radio: 916 Mhz and 40 Kbits/second. Transmission range: 100 Feet Tiny. OS operating System: small, open source and energy efficient.
 Wireless Sensor Networks (WSN) Sensors Deploy
Wireless Sensor Networks (WSN) Sensors Deploy
 Applications of WSN l Battle ground surveillance l l Environmental monitoring l l l Enemy movement (tanks, soldiers, etc) Habitat monitoring Forrest fire monitoring Hospital tracking systems l Tracking patients, doctors, drug administrators.
Applications of WSN l Battle ground surveillance l l Environmental monitoring l l l Enemy movement (tanks, soldiers, etc) Habitat monitoring Forrest fire monitoring Hospital tracking systems l Tracking patients, doctors, drug administrators.
 Securing WSN • Motivation: why security? • Why not use existing security mechanisms? – WSN features that affect security.
Securing WSN • Motivation: why security? • Why not use existing security mechanisms? – WSN features that affect security.
 Why Security? • Protecting confidentiality, integrity, and availability of the communications and computations • Sensor networks are vulnerable to security attacks due to the broadcast nature of transmission • Sensor nodes can be physically captured or destroyed
Why Security? • Protecting confidentiality, integrity, and availability of the communications and computations • Sensor networks are vulnerable to security attacks due to the broadcast nature of transmission • Sensor nodes can be physically captured or destroyed
 Why Security is Different? • Sensor Node Constraints – Battery, – CPU power, – Memory. • Networking Constraints and Features – Wireless, – Ad hoc, – Unattended.
Why Security is Different? • Sensor Node Constraints – Battery, – CPU power, – Memory. • Networking Constraints and Features – Wireless, – Ad hoc, – Unattended.
 Sensor Node Constraints • Battery Power Constraints – Computational Energy Consumption • Crypto algorithms • Public key vs. Symmetric key – Communications Energy Consumption • Exchange of keys, certificates, etc. • Per-message additions (padding, signatures, authentication tags)
Sensor Node Constraints • Battery Power Constraints – Computational Energy Consumption • Crypto algorithms • Public key vs. Symmetric key – Communications Energy Consumption • Exchange of keys, certificates, etc. • Per-message additions (padding, signatures, authentication tags)
 Memory Constraints • Program Storage and Working Memory – Embedded OS, security functions (Flash) – Working memory (RAM) • Mica Motes: • 128 KB Flash and 4 KB RAM
Memory Constraints • Program Storage and Working Memory – Embedded OS, security functions (Flash) – Working memory (RAM) • Mica Motes: • 128 KB Flash and 4 KB RAM
 An Efficient Scheme for Authenticating Public Keys in Sensor Networks
An Efficient Scheme for Authenticating Public Keys in Sensor Networks
 Wireless Sensor Networks Sensors Deploy
Wireless Sensor Networks Sensors Deploy
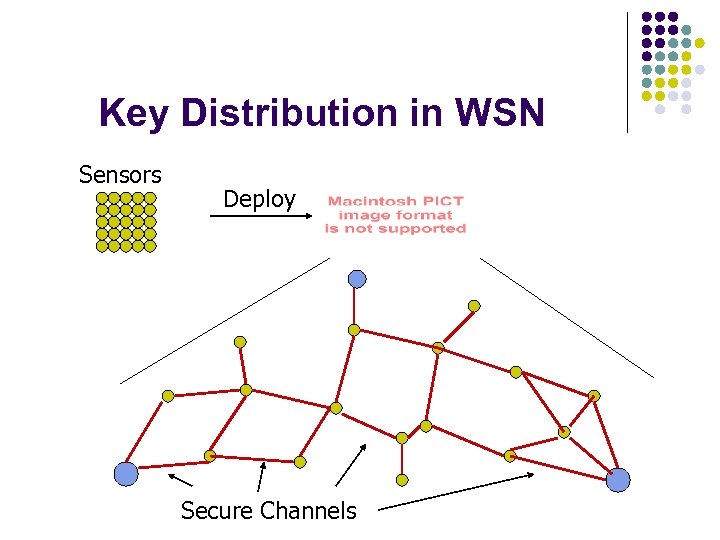 Key Distribution in WSN Sensors Deploy Secure Channels
Key Distribution in WSN Sensors Deploy Secure Channels
 Existing Approaches l Key Pre-distribution Schemes l l l Eschenauer and Gligor, CCS’ 02 Chan, Perrig, and Song, S&P’ 03 Du, Deng, Han, and Varshney, CCS’ 03 Du, Deng, Han, Chen, Varshney, INFOCOM’ 04 Liu and Ning, CCS’ 03 Assumption l l Public Keys are impractical for WSN We need to use Symmetric Keys
Existing Approaches l Key Pre-distribution Schemes l l l Eschenauer and Gligor, CCS’ 02 Chan, Perrig, and Song, S&P’ 03 Du, Deng, Han, and Varshney, CCS’ 03 Du, Deng, Han, Chen, Varshney, INFOCOM’ 04 Liu and Ning, CCS’ 03 Assumption l l Public Keys are impractical for WSN We need to use Symmetric Keys
 Three Years Later l Has Public-Key Cryptography (PKC) became practical yet? l l The answer might still be NO, but … Recent Studies on using PKC on sensors l l PKC is feasible for WSN ECC signature verification takes 1. 6 s on Crossbow motes (Gura et al. )
Three Years Later l Has Public-Key Cryptography (PKC) became practical yet? l l The answer might still be NO, but … Recent Studies on using PKC on sensors l l PKC is feasible for WSN ECC signature verification takes 1. 6 s on Crossbow motes (Gura et al. )
 The Advantage of PKC l Resilience versus Connectivity l l SKC-based schemes have to make tradeoffs between resilience and connectivity PKC-based Key Distribution l l 100% resilience 100% connectivity
The Advantage of PKC l Resilience versus Connectivity l l SKC-based schemes have to make tradeoffs between resilience and connectivity PKC-based Key Distribution l l 100% resilience 100% connectivity
 Let’s Switch to PKC? l Sorry, I forgot to mention one thing: The gap between SKC and PKC is not going to change much unless a breakthrough in PKC occurs. l Computation costs l l RC 5 is 200 times faster than ECC Communication costs l Signatures: ECC (320 bits), RSA (1024 bits), SHA 1 (160 bits)
Let’s Switch to PKC? l Sorry, I forgot to mention one thing: The gap between SKC and PKC is not going to change much unless a breakthrough in PKC occurs. l Computation costs l l RC 5 is 200 times faster than ECC Communication costs l Signatures: ECC (320 bits), RSA (1024 bits), SHA 1 (160 bits)
 New Focuses l My observation: We will be able to use PKC, but we will use SKC if that can save energy. l We are doing this in traditional networks l l Example: session keys Research Problem Can we reduce the amount of PKC computations with the help of SKC?
New Focuses l My observation: We will be able to use PKC, but we will use SKC if that can save energy. l We are doing this in traditional networks l l Example: session keys Research Problem Can we reduce the amount of PKC computations with the help of SKC?
 Public Key Authentication l Before a public key is used, it must be authenticated l l In traditional networks: we use certificates. Verifying certificates is a public key operation
Public Key Authentication l Before a public key is used, it must be authenticated l l In traditional networks: we use certificates. Verifying certificates is a public key operation
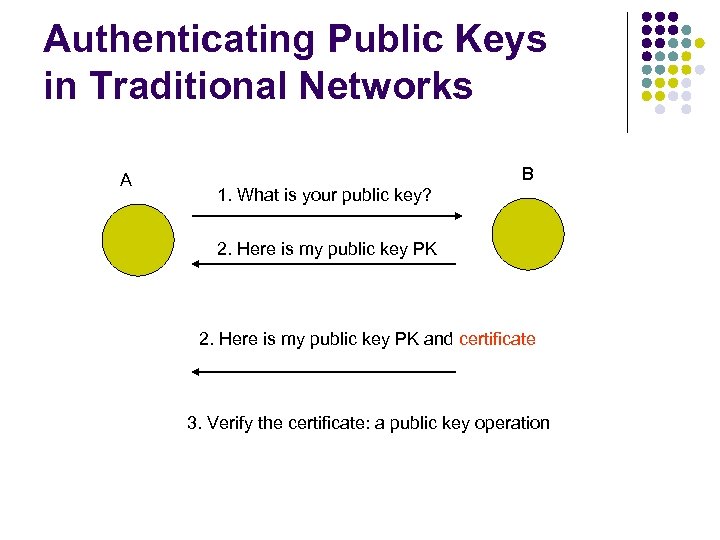 Authenticating Public Keys in Traditional Networks A B 1. What is your public key? 2. Here is my public key PK and certificate 3. Verify the certificate: a public key operation
Authenticating Public Keys in Traditional Networks A B 1. What is your public key? 2. Here is my public key PK and certificate 3. Verify the certificate: a public key operation
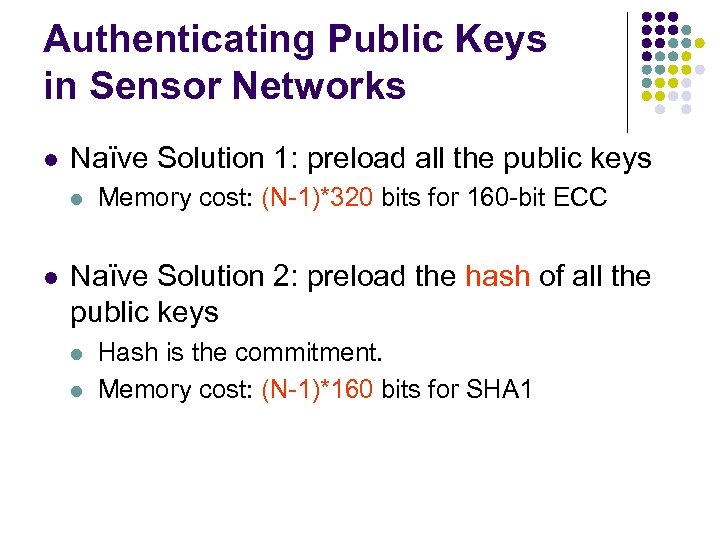 Authenticating Public Keys in Sensor Networks l Naïve Solution 1: preload all the public keys l l Memory cost: (N-1)*320 bits for 160 -bit ECC Naïve Solution 2: preload the hash of all the public keys l l Hash is the commitment. Memory cost: (N-1)*160 bits for SHA 1
Authenticating Public Keys in Sensor Networks l Naïve Solution 1: preload all the public keys l l Memory cost: (N-1)*320 bits for 160 -bit ECC Naïve Solution 2: preload the hash of all the public keys l l Hash is the commitment. Memory cost: (N-1)*160 bits for SHA 1
 Can We Improve Memory Usage? l Much less than N-1 commitments l l l Hash everything together: need 1 commitment Communication cost: O(N) A standard technique: Merkle Tree l l Memory cost: O(log N) Communication cost: O(log N)
Can We Improve Memory Usage? l Much less than N-1 commitments l l l Hash everything together: need 1 commitment Communication cost: O(N) A standard technique: Merkle Tree l l Memory cost: O(log N) Communication cost: O(log N)
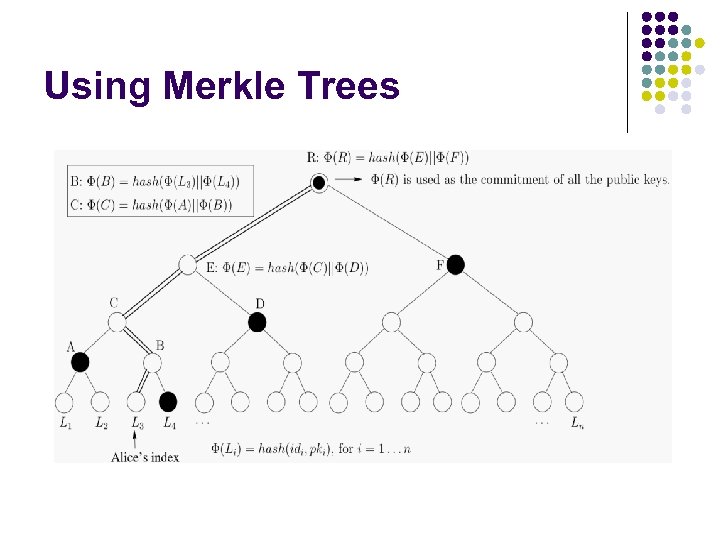 Using Merkle Trees
Using Merkle Trees
 Performance l Memory Usage l l Computation Cost l l 1 + log(N) hash values (compared to N-1) Log(N) hash operations Communication Overhead l l If we use 160 -bit SHA 1 160 * log(N) bits When N=10, 000, cost=2080 bits, worse than PKC We need to reduce the height
Performance l Memory Usage l l Computation Cost l l 1 + log(N) hash values (compared to N-1) Log(N) hash operations Communication Overhead l l If we use 160 -bit SHA 1 160 * log(N) bits When N=10, 000, cost=2080 bits, worse than PKC We need to reduce the height
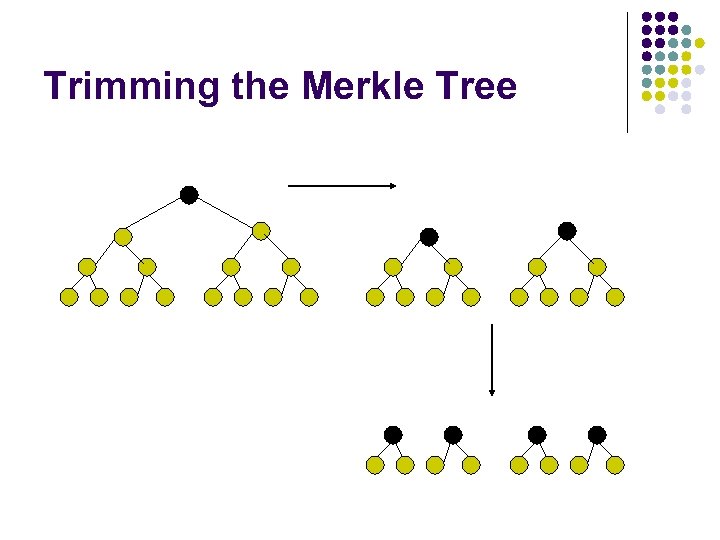 Trimming the Merkle Tree
Trimming the Merkle Tree
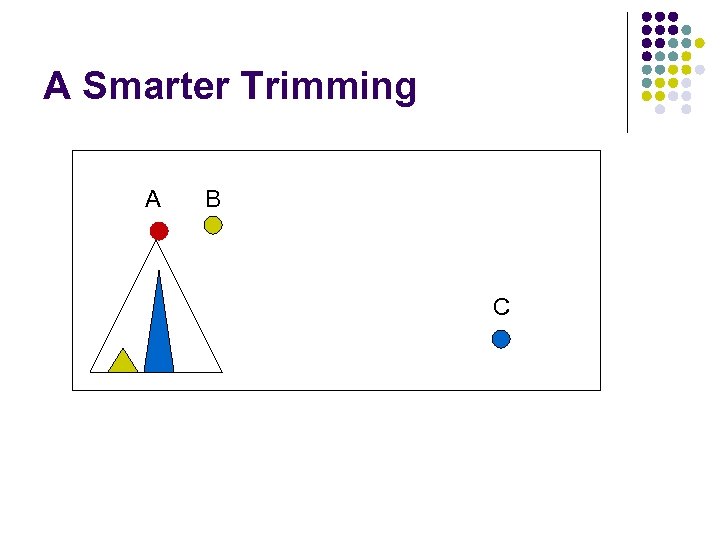 A Smarter Trimming A B C
A Smarter Trimming A B C
 Deployment Knowledge l l How do we know that some nodes might more likely be neighbors than others? Deployment knowledge model.
Deployment Knowledge l l How do we know that some nodes might more likely be neighbors than others? Deployment knowledge model.
 A Group-Based Deployment Scheme
A Group-Based Deployment Scheme
 A Group-Based Deployment Scheme
A Group-Based Deployment Scheme
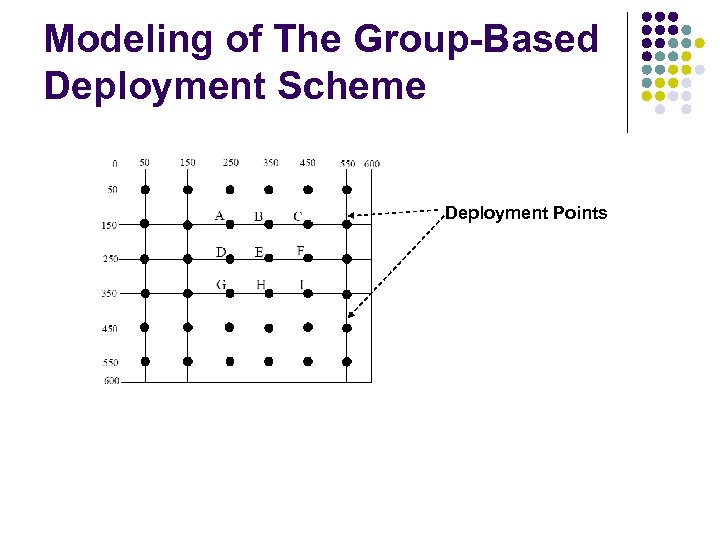 Modeling of The Group-Based Deployment Scheme Deployment Points
Modeling of The Group-Based Deployment Scheme Deployment Points
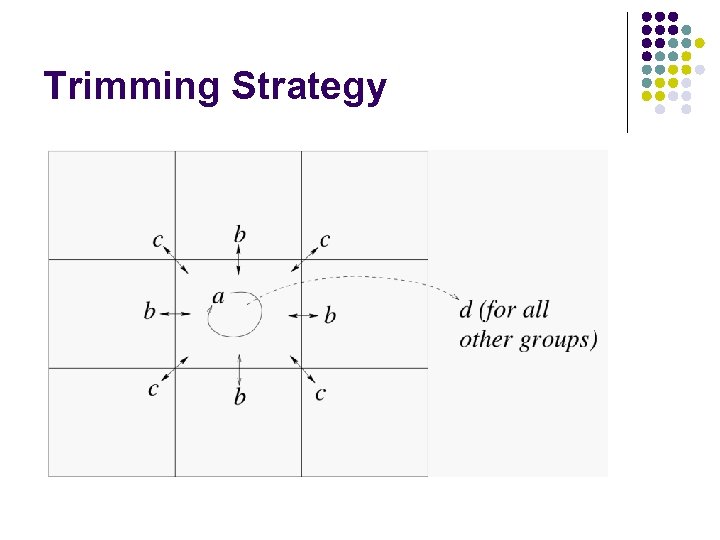 Trimming Strategy
Trimming Strategy
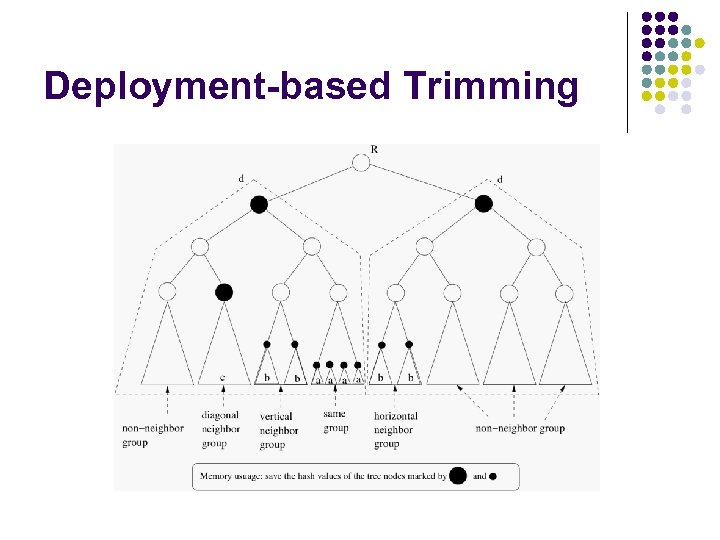 Deployment-based Trimming
Deployment-based Trimming
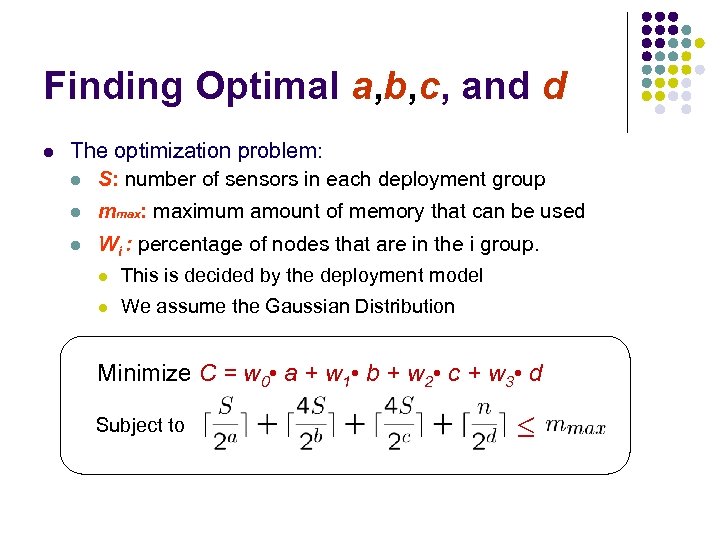 Finding Optimal a, b, c, and d l The optimization problem: l S: number of sensors in each deployment group l mmax: maximum amount of memory that can be used l Wi : percentage of nodes that are in the i group. l This is decided by the deployment model l We assume the Gaussian Distribution Minimize C = w 0 • a + w 1 • b + w 2 • c + w 3 • d Subject to
Finding Optimal a, b, c, and d l The optimization problem: l S: number of sensors in each deployment group l mmax: maximum amount of memory that can be used l Wi : percentage of nodes that are in the i group. l This is decided by the deployment model l We assume the Gaussian Distribution Minimize C = w 0 • a + w 1 • b + w 2 • c + w 3 • d Subject to
 Evaluation
Evaluation
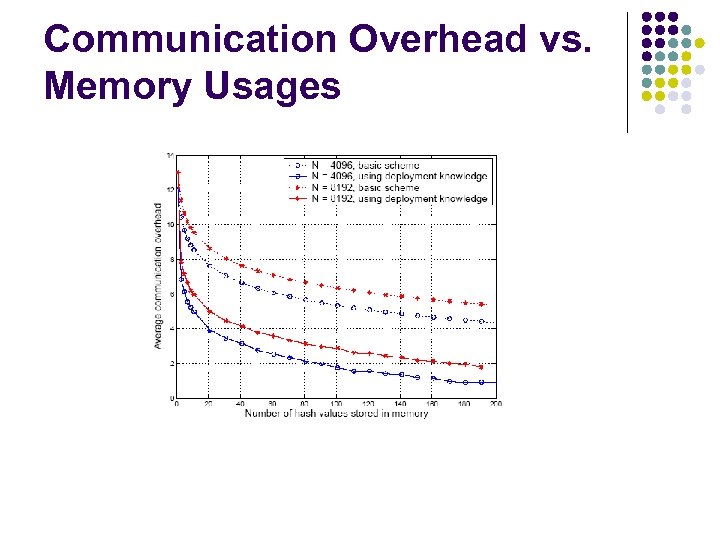 Communication Overhead vs. Memory Usages
Communication Overhead vs. Memory Usages
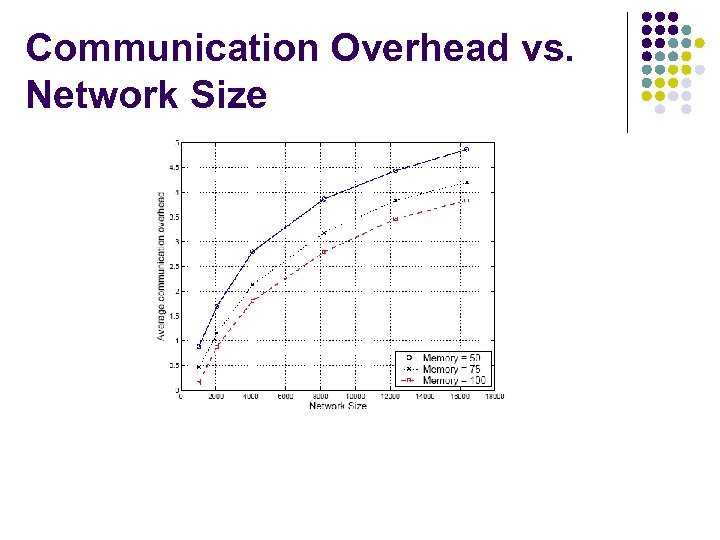 Communication Overhead vs. Network Size
Communication Overhead vs. Network Size
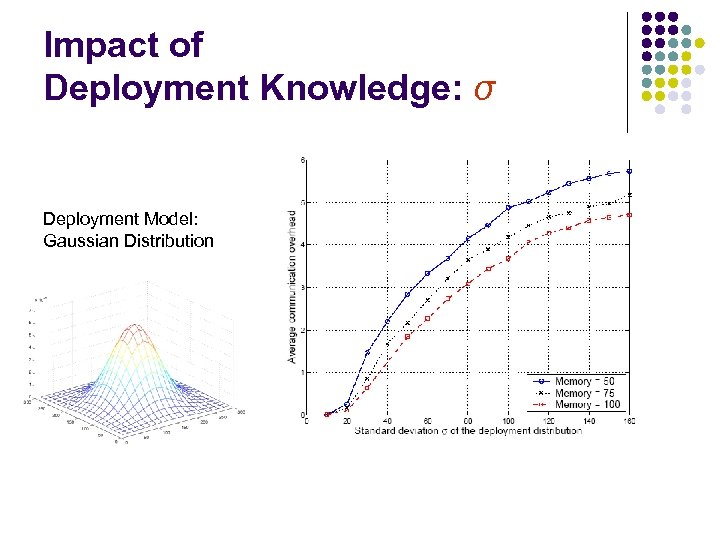 Impact of Deployment Knowledge: σ Deployment Model: Gaussian Distribution
Impact of Deployment Knowledge: σ Deployment Model: Gaussian Distribution
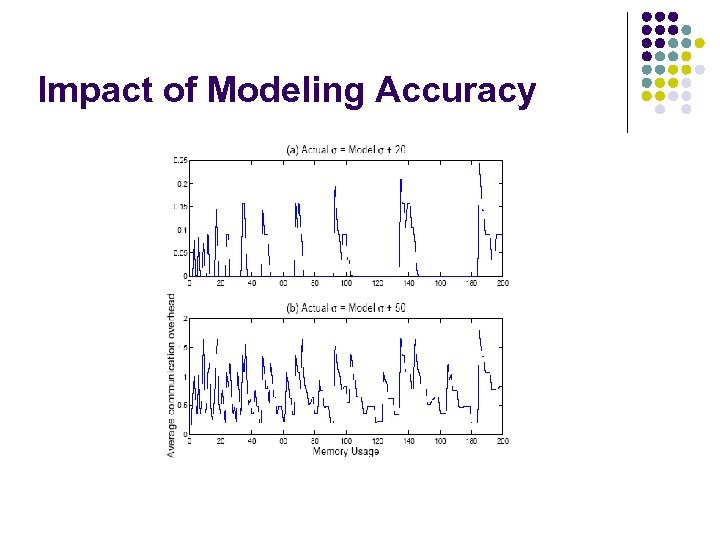 Impact of Modeling Accuracy
Impact of Modeling Accuracy
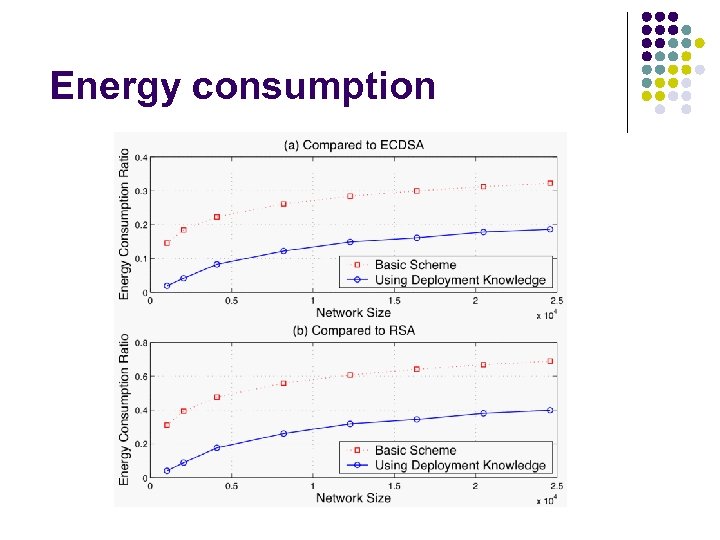 Energy consumption
Energy consumption
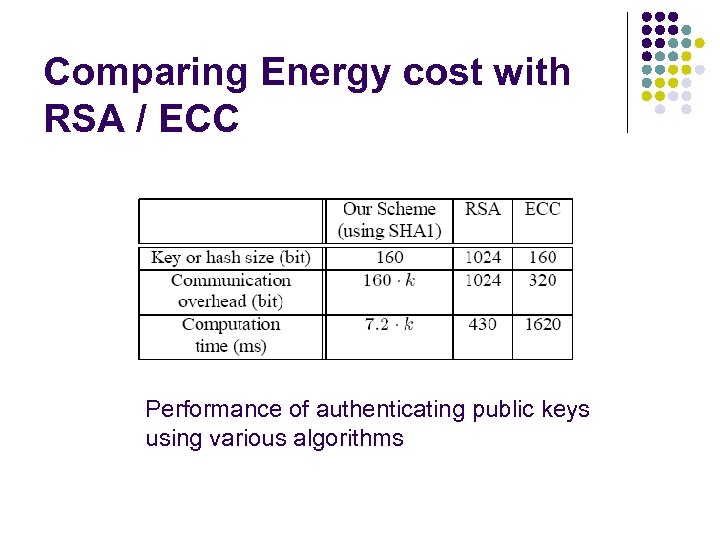 Comparing Energy cost with RSA / ECC Performance of authenticating public keys using various algorithms
Comparing Energy cost with RSA / ECC Performance of authenticating public keys using various algorithms
 Summary l Public Key Cryptography (PKC) l Will soon be available for sensor networks l l l Intel Motes: very powerful. Usage of PKC should still be minimized We propose an efficient scheme to achieve public key authentication.
Summary l Public Key Cryptography (PKC) l Will soon be available for sensor networks l l l Intel Motes: very powerful. Usage of PKC should still be minimized We propose an efficient scheme to achieve public key authentication.
 A Beacon-Less Location Discovery Scheme for Wireless Sensor Networks
A Beacon-Less Location Discovery Scheme for Wireless Sensor Networks
 Location Discovery in WSN l Sensor nodes need to find their locations l l Rescue missions Geographic routing protocols Many other applications Constraints l l No GPS on sensors Cost must be low
Location Discovery in WSN l Sensor nodes need to find their locations l l Rescue missions Geographic routing protocols Many other applications Constraints l l No GPS on sensors Cost must be low
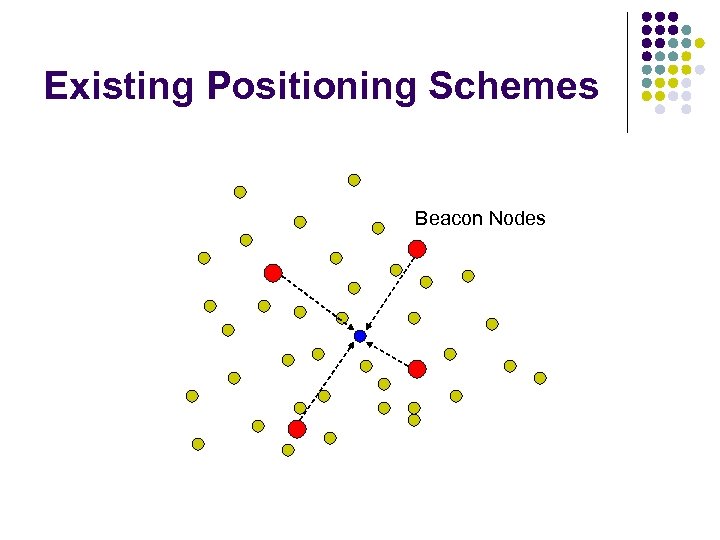 Existing Positioning Schemes Beacon Nodes
Existing Positioning Schemes Beacon Nodes
 Two Important Elements l Reference points l l l They must know their locations. e. g. beacon nodes, satellites. Relationship between nodes and reference points l l Distance Angle of arrival Time difference of arrival
Two Important Elements l Reference points l l l They must know their locations. e. g. beacon nodes, satellites. Relationship between nodes and reference points l l Distance Angle of arrival Time difference of arrival
 The Beacon-Less Scheme l Without using beacon nodes l l l Beacon nodes are more expensive They can be the main target of attacks Nonetheless, we still have to find reference points and the corresponding relationships. l Remember: the locations of the reference points must be known.
The Beacon-Less Scheme l Without using beacon nodes l l l Beacon nodes are more expensive They can be the main target of attacks Nonetheless, we still have to find reference points and the corresponding relationships. l Remember: the locations of the reference points must be known.
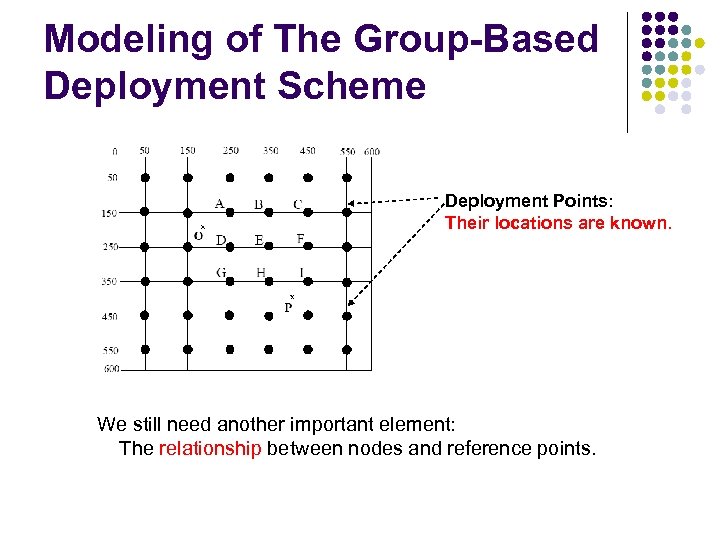 Modeling of The Group-Based Deployment Scheme Deployment Points: Their locations are known. We still need another important element: The relationship between nodes and reference points.
Modeling of The Group-Based Deployment Scheme Deployment Points: Their locations are known. We still need another important element: The relationship between nodes and reference points.
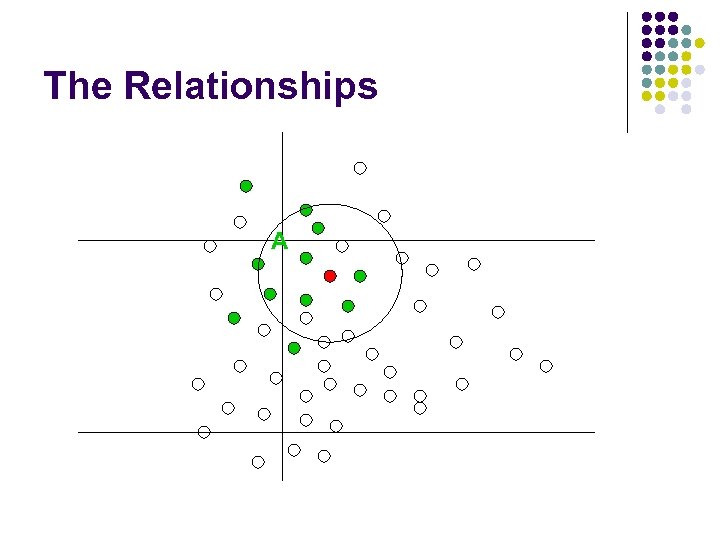 The Relationships A
The Relationships A
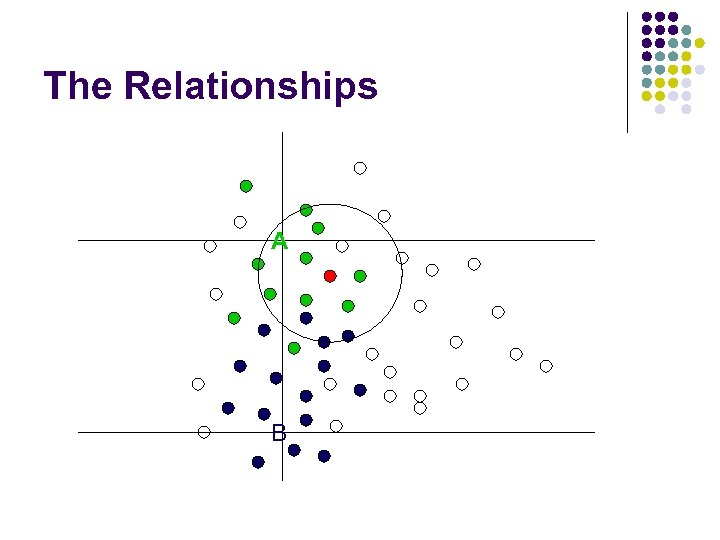 The Relationships A B
The Relationships A B
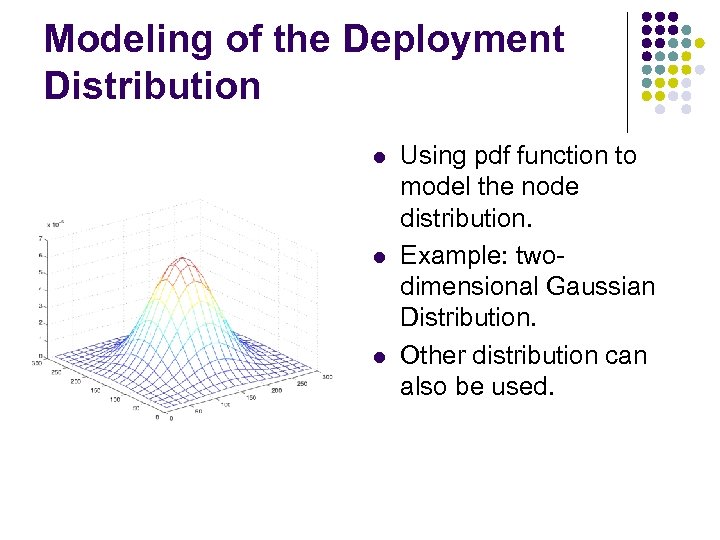 Modeling of the Deployment Distribution l l l Using pdf function to model the node distribution. Example: twodimensional Gaussian Distribution. Other distribution can also be used.
Modeling of the Deployment Distribution l l l Using pdf function to model the node distribution. Example: twodimensional Gaussian Distribution. Other distribution can also be used.
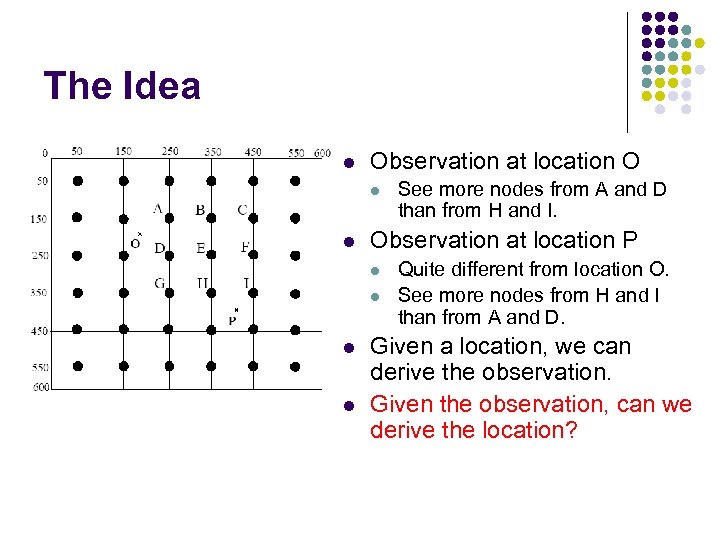 The Idea l Observation at location O l l Observation at location P l l See more nodes from A and D than from H and I. Quite different from location O. See more nodes from H and I than from A and D. Given a location, we can derive the observation. Given the observation, can we derive the location?
The Idea l Observation at location O l l Observation at location P l l See more nodes from A and D than from H and I. Quite different from location O. See more nodes from H and I than from A and D. Given a location, we can derive the observation. Given the observation, can we derive the location?
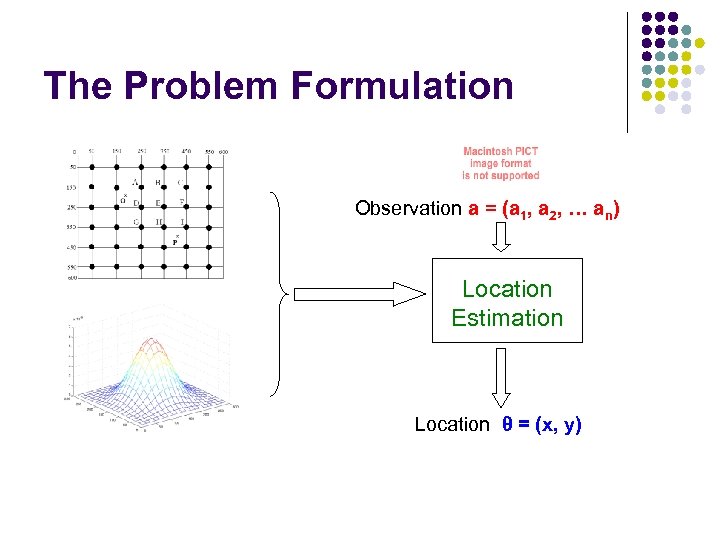 The Problem Formulation Observation a = (a 1, a 2, … an) Location Estimation Location θ = (x, y)
The Problem Formulation Observation a = (a 1, a 2, … an) Location Estimation Location θ = (x, y)
 A Solution l Definitions a = (a 1, a 2, … an): The observation. fn(a | θ): The probability of observing a at location θ. l Maximum-Likelihood-Estimation (MLE) Principle: find θ, such that fn(a | θ) is maximized.
A Solution l Definitions a = (a 1, a 2, … an): The observation. fn(a | θ): The probability of observing a at location θ. l Maximum-Likelihood-Estimation (MLE) Principle: find θ, such that fn(a | θ) is maximized.
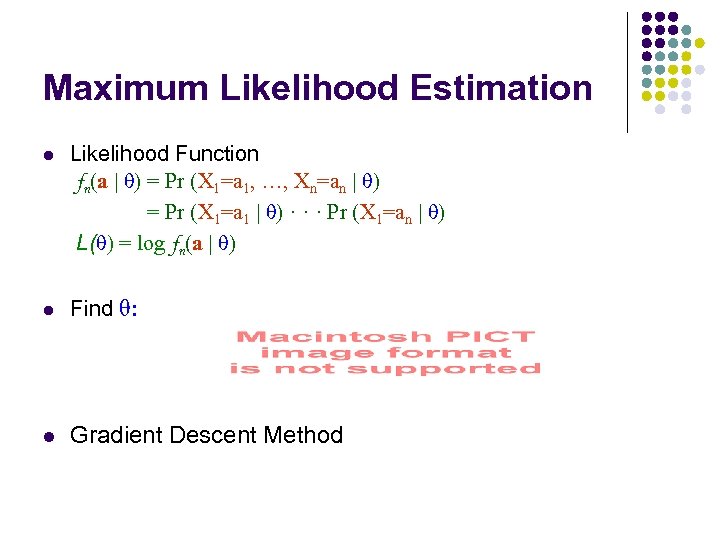 Maximum Likelihood Estimation l Likelihood Function fn(a | θ) = Pr (X 1=a 1, …, Xn=an | θ) = Pr (X 1=a 1 | θ) · · · Pr (X 1=an | θ) L(θ) = log fn(a | θ) l Find θ: l Gradient Descent Method
Maximum Likelihood Estimation l Likelihood Function fn(a | θ) = Pr (X 1=a 1, …, Xn=an | θ) = Pr (X 1=a 1 | θ) · · · Pr (X 1=an | θ) L(θ) = log fn(a | θ) l Find θ: l Gradient Descent Method
 Evaluation l Setup l l A square plane: 1000 meters by 1000 meters 10 by 10 grids (each is 100 m X 100 m) σ = 50 (Gaussian Distribution) What to evaluate? l l Accuracy vs. Density Accuracy vs. Transmission Range Boundary Effects Computation Costs.
Evaluation l Setup l l A square plane: 1000 meters by 1000 meters 10 by 10 grids (each is 100 m X 100 m) σ = 50 (Gaussian Distribution) What to evaluate? l l Accuracy vs. Density Accuracy vs. Transmission Range Boundary Effects Computation Costs.
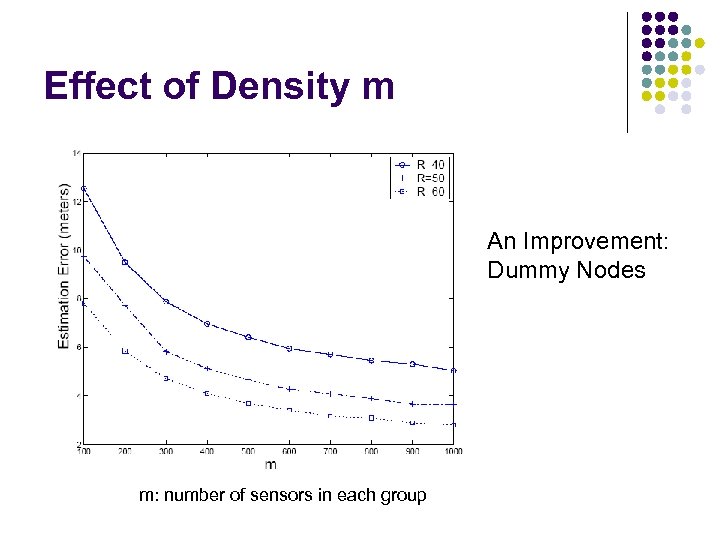 Effect of Density m An Improvement: Dummy Nodes m: number of sensors in each group
Effect of Density m An Improvement: Dummy Nodes m: number of sensors in each group
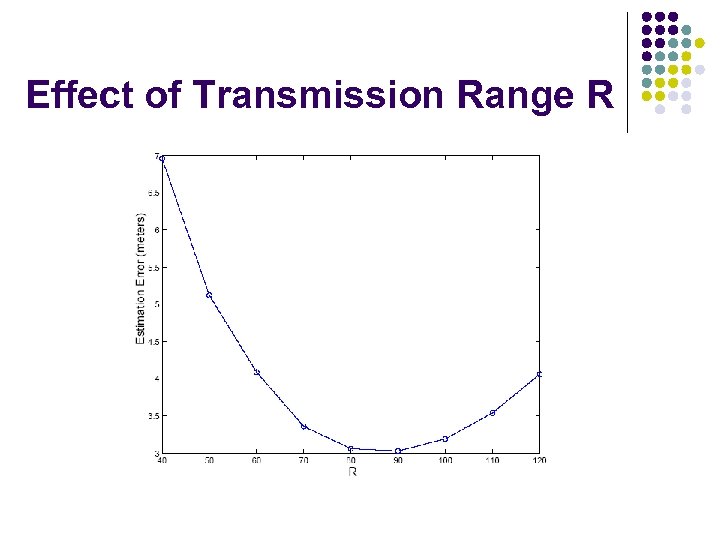 Effect of Transmission Range R
Effect of Transmission Range R
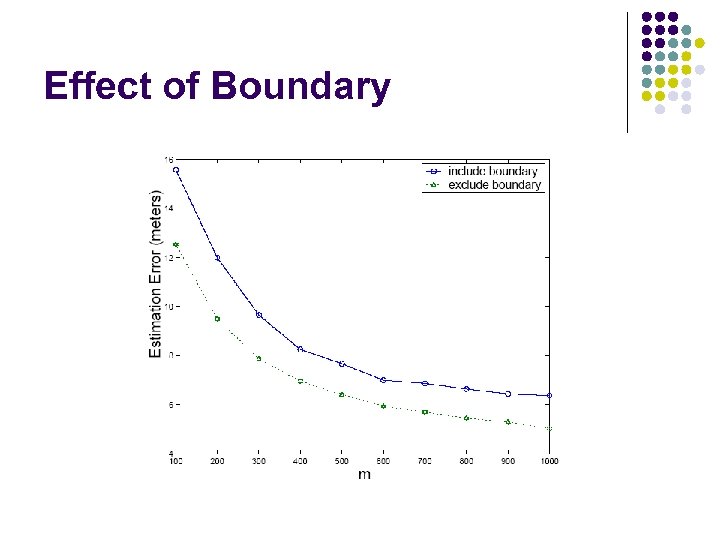 Effect of Boundary
Effect of Boundary
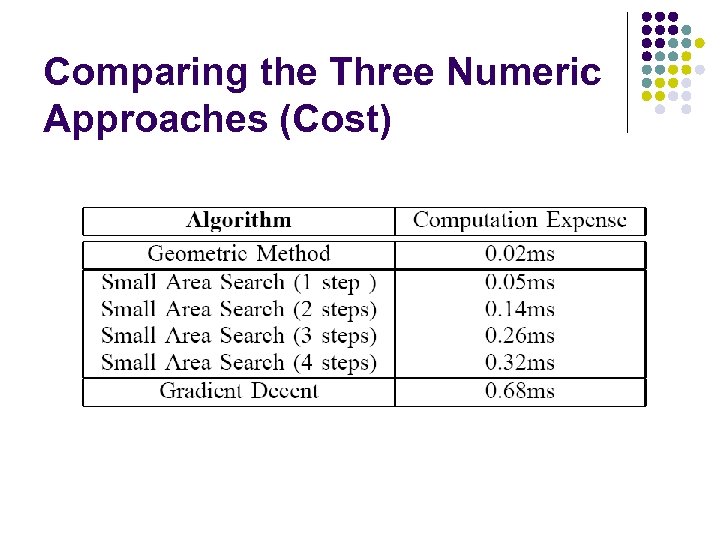 Comparing the Three Numeric Approaches (Cost)
Comparing the Three Numeric Approaches (Cost)
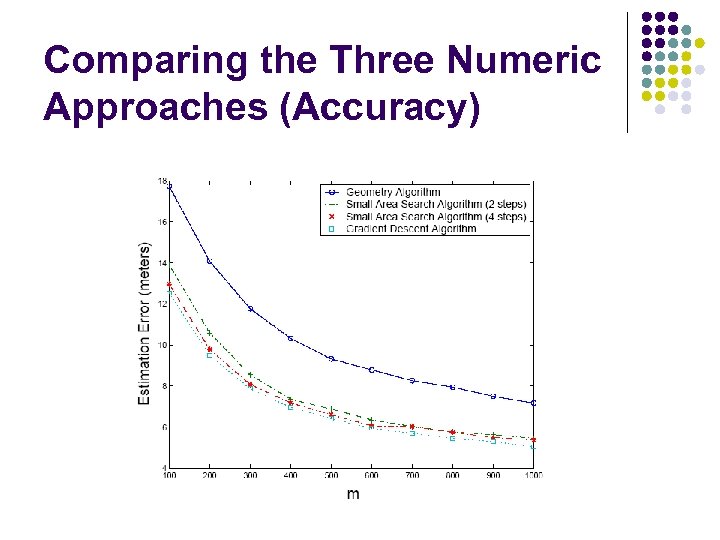 Comparing the Three Numeric Approaches (Accuracy)
Comparing the Three Numeric Approaches (Accuracy)
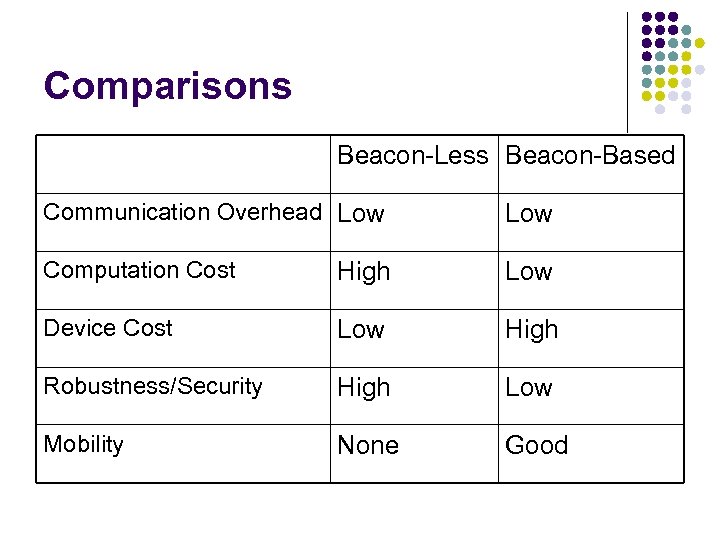 Comparisons Beacon-Less Beacon-Based Communication Overhead Low Computation Cost High Low Device Cost Low High Robustness/Security High Low Mobility None Good
Comparisons Beacon-Less Beacon-Based Communication Overhead Low Computation Cost High Low Device Cost Low High Robustness/Security High Low Mobility None Good
 Conclusion and Future Work l Two Applications of Deployment Knowledge l l Authenticating Public Keys Beacon-Less Location Discovery IPDPS’ 05 paper: Location Anomaly Detection Future Work l Optimizing public-key protocols for sensor networks
Conclusion and Future Work l Two Applications of Deployment Knowledge l l Authenticating Public Keys Beacon-Less Location Discovery IPDPS’ 05 paper: Location Anomaly Detection Future Work l Optimizing public-key protocols for sensor networks


