df2cc5e7af7240bfc69e6bf714272fe7.ppt
- Количество слайдов: 28
 Securing the University Environment EDUCAUSE Security Professionals Workshop May 18, 2004 Jinx Walton University of Pittsburgh Copyright 2004, Jinx P. Walton. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author.
Securing the University Environment EDUCAUSE Security Professionals Workshop May 18, 2004 Jinx Walton University of Pittsburgh Copyright 2004, Jinx P. Walton. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author.
 University of Pittsburgh • Founded in 1787 • 32, 000 Students • 3, 800 Faculty • 5, 800 Staff • Five Campuses • Over 100 Buildings on Main Campus • 18 Undergraduate, Graduate, and Professional Schools • 6 Health Science Schools • Affiliated with a World-Renowned Medical Center (UPMC) • 60, 000 user accounts • 28, 000 network connections
University of Pittsburgh • Founded in 1787 • 32, 000 Students • 3, 800 Faculty • 5, 800 Staff • Five Campuses • Over 100 Buildings on Main Campus • 18 Undergraduate, Graduate, and Professional Schools • 6 Health Science Schools • Affiliated with a World-Renowned Medical Center (UPMC) • 60, 000 user accounts • 28, 000 network connections
 University Security Issues • Requirement for Areas of Open Access • Departmentally Run Systems and Services • Diverse systems • Varying levels of expertise and awareness of regulations • Medical Center Affiliation and HIPAA Requirements • Residence Halls with 6, 000 Ethernet Ports • Connection of Unauthorized Network Devices • Vendor Access for Remote Support
University Security Issues • Requirement for Areas of Open Access • Departmentally Run Systems and Services • Diverse systems • Varying levels of expertise and awareness of regulations • Medical Center Affiliation and HIPAA Requirements • Residence Halls with 6, 000 Ethernet Ports • Connection of Unauthorized Network Devices • Vendor Access for Remote Support
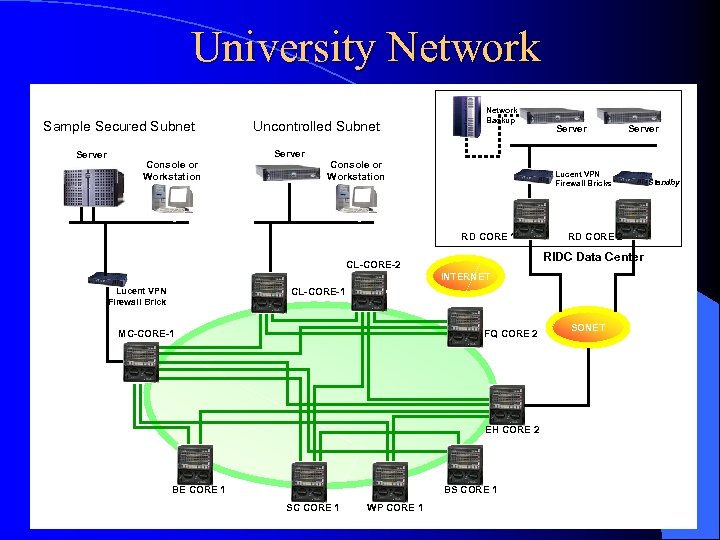 University Network Sample Secured Subnet Server Console or Workstation Uncontrolled Subnet Server Network Backup Console or Workstation Server Lucent VPN Firewall Bricks RD CORE 1 RD CORE 2 RIDC Data Center CL-CORE-2 INTERNET Lucent VPN Firewall Brick CL-CORE-1 MC-CORE-1 FQ CORE 2 EH CORE 2 BE CORE 1 BS CORE 1 SC CORE 1 WP CORE 1 Server SONET Standby
University Network Sample Secured Subnet Server Console or Workstation Uncontrolled Subnet Server Network Backup Console or Workstation Server Lucent VPN Firewall Bricks RD CORE 1 RD CORE 2 RIDC Data Center CL-CORE-2 INTERNET Lucent VPN Firewall Brick CL-CORE-1 MC-CORE-1 FQ CORE 2 EH CORE 2 BE CORE 1 BS CORE 1 SC CORE 1 WP CORE 1 Server SONET Standby
 Security Initiatives • Centralized Monitoring of Security Environment • Central Directory Service • Network-based Firewalls • Security Agreement Between University and Medical Center • Authenticated Remote Access Controls for Modem and Wireless Users
Security Initiatives • Centralized Monitoring of Security Environment • Central Directory Service • Network-based Firewalls • Security Agreement Between University and Medical Center • Authenticated Remote Access Controls for Modem and Wireless Users
 Security Initiatives • Network Security Control (Access Lists, MAC Address Correlation) • Migration to web-based interfaces • Retiring clear-text protocols • Promoting use of secure. FTP, SSH, and Secure. Copy • Security Patch and Antivirus Software (CDs) • Distribution of Security Information
Security Initiatives • Network Security Control (Access Lists, MAC Address Correlation) • Migration to web-based interfaces • Retiring clear-text protocols • Promoting use of secure. FTP, SSH, and Secure. Copy • Security Patch and Antivirus Software (CDs) • Distribution of Security Information
 Development of a Strategic Security Plan • Review the Current Security Environment • Assess the Security Posture of the University • Establish Security Procedures and Guidelines • Establish Security Principals • Develop a Security Architecture Model • Develop a Security Awareness Strategy • Develop a Security Roadmap
Development of a Strategic Security Plan • Review the Current Security Environment • Assess the Security Posture of the University • Establish Security Procedures and Guidelines • Establish Security Principals • Develop a Security Architecture Model • Develop a Security Awareness Strategy • Develop a Security Roadmap
 Control Standards • Fully Implemented • Partially Implemented • Fault Tolerance, Backup & Recovery • Auditing, Logging & Monitoring • Authentication & Access • Physical Access • Change Control • Confidentiality & Non-Repudiation • External 3 rd party access • Incident Response & Reporting • Maintenance & Operations • Network • Physical Media • Remote Access • Security Awareness and Training • Security Guideline Administration • Vendors and Consultants • System Configuration
Control Standards • Fully Implemented • Partially Implemented • Fault Tolerance, Backup & Recovery • Auditing, Logging & Monitoring • Authentication & Access • Physical Access • Change Control • Confidentiality & Non-Repudiation • External 3 rd party access • Incident Response & Reporting • Maintenance & Operations • Network • Physical Media • Remote Access • Security Awareness and Training • Security Guideline Administration • Vendors and Consultants • System Configuration
 Communicating the Plan to Administration and Faculty • Outline the Risks – Reason for Developing the Plan • Provide Overview of the Plan and Architecture • Provide Implementation Updates
Communicating the Plan to Administration and Faculty • Outline the Risks – Reason for Developing the Plan • Provide Overview of the Plan and Architecture • Provide Implementation Updates
 State of Security Threats at Universities “Our Universities are under attack. Networks comprised of heterogeneous hosts with fast Internet connections make universities desirable targets to a wide variety of attackers. Members of university communities are often not concerned with security because they assume that hackers attack systems to obtain confidential information. These academics have not realized that many attacks are instead quests for disk space or processor time and that the information stored on a server is sometimes irrelevant to the attacker. The resulting lack of system security at universities has allowed attackers to quickly make universities the preferred staging areas for distributed denial of service attacks. — Douglas P. Brown, SANS Institute 2002 “Universities are the major source of hacks today – probably three-quarters of the total number of attacks. The attacks may not originate there, but most of them jump through them. ” — Richard Clarke, Sixth National Colloquium on Information Systems Security Education, 2003
State of Security Threats at Universities “Our Universities are under attack. Networks comprised of heterogeneous hosts with fast Internet connections make universities desirable targets to a wide variety of attackers. Members of university communities are often not concerned with security because they assume that hackers attack systems to obtain confidential information. These academics have not realized that many attacks are instead quests for disk space or processor time and that the information stored on a server is sometimes irrelevant to the attacker. The resulting lack of system security at universities has allowed attackers to quickly make universities the preferred staging areas for distributed denial of service attacks. — Douglas P. Brown, SANS Institute 2002 “Universities are the major source of hacks today – probably three-quarters of the total number of attacks. The attacks may not originate there, but most of them jump through them. ” — Richard Clarke, Sixth National Colloquium on Information Systems Security Education, 2003
 University IT Security Risks • • • Liability due to file sharing copyright infringement Malicious actions and attacks—internal and external Unintended consequences and outages Non-compliance with state, federal and international regulations Loss of intellectual property Computer-aided fraud Pervasive and wireless computing egress Insecure integration of systems and applications—internal & 3 rd party Launch point for cyber terrorism and Internet infrastructure attacks
University IT Security Risks • • • Liability due to file sharing copyright infringement Malicious actions and attacks—internal and external Unintended consequences and outages Non-compliance with state, federal and international regulations Loss of intellectual property Computer-aided fraud Pervasive and wireless computing egress Insecure integration of systems and applications—internal & 3 rd party Launch point for cyber terrorism and Internet infrastructure attacks
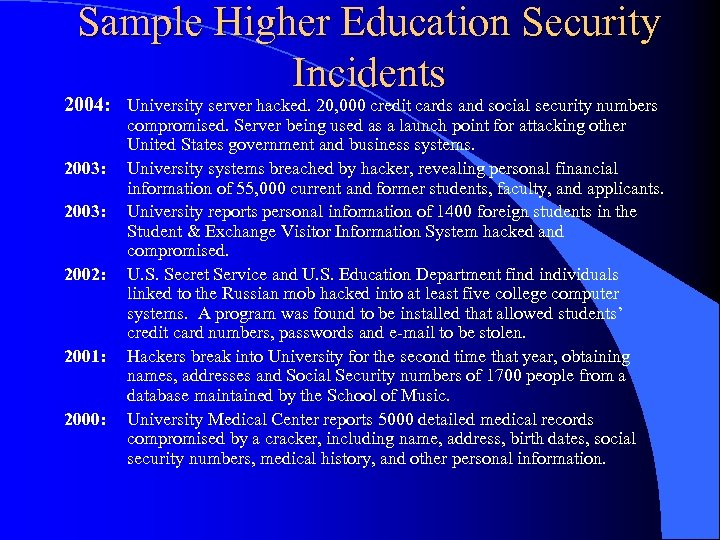 Sample Higher Education Security Incidents 2004: University server hacked. 20, 000 credit cards and social security numbers 2003: 2002: 2001: 2000: compromised. Server being used as a launch point for attacking other United States government and business systems. University systems breached by hacker, revealing personal financial information of 55, 000 current and former students, faculty, and applicants. University reports personal information of 1400 foreign students in the Student & Exchange Visitor Information System hacked and compromised. U. S. Secret Service and U. S. Education Department find individuals linked to the Russian mob hacked into at least five college computer systems. A program was found to be installed that allowed students’ credit card numbers, passwords and e-mail to be stolen. Hackers break into University for the second time that year, obtaining names, addresses and Social Security numbers of 1700 people from a database maintained by the School of Music. University Medical Center reports 5000 detailed medical records compromised by a cracker, including name, address, birth dates, social security numbers, medical history, and other personal information.
Sample Higher Education Security Incidents 2004: University server hacked. 20, 000 credit cards and social security numbers 2003: 2002: 2001: 2000: compromised. Server being used as a launch point for attacking other United States government and business systems. University systems breached by hacker, revealing personal financial information of 55, 000 current and former students, faculty, and applicants. University reports personal information of 1400 foreign students in the Student & Exchange Visitor Information System hacked and compromised. U. S. Secret Service and U. S. Education Department find individuals linked to the Russian mob hacked into at least five college computer systems. A program was found to be installed that allowed students’ credit card numbers, passwords and e-mail to be stolen. Hackers break into University for the second time that year, obtaining names, addresses and Social Security numbers of 1700 people from a database maintained by the School of Music. University Medical Center reports 5000 detailed medical records compromised by a cracker, including name, address, birth dates, social security numbers, medical history, and other personal information.
 Risk Scenarios Considered • Operations (such as student registration, payroll, etc. ) disabled by hacker, virus or worm during the worst possible time (such as the beginning of the semester). • Integrity of research data called into question. • Faculty and student private health and financial information (such as social security numbers) compromised. • University servers compromised and used as a platform to launch attacks, spread spam, or distribute copyrighted or illegal material.
Risk Scenarios Considered • Operations (such as student registration, payroll, etc. ) disabled by hacker, virus or worm during the worst possible time (such as the beginning of the semester). • Integrity of research data called into question. • Faculty and student private health and financial information (such as social security numbers) compromised. • University servers compromised and used as a platform to launch attacks, spread spam, or distribute copyrighted or illegal material.
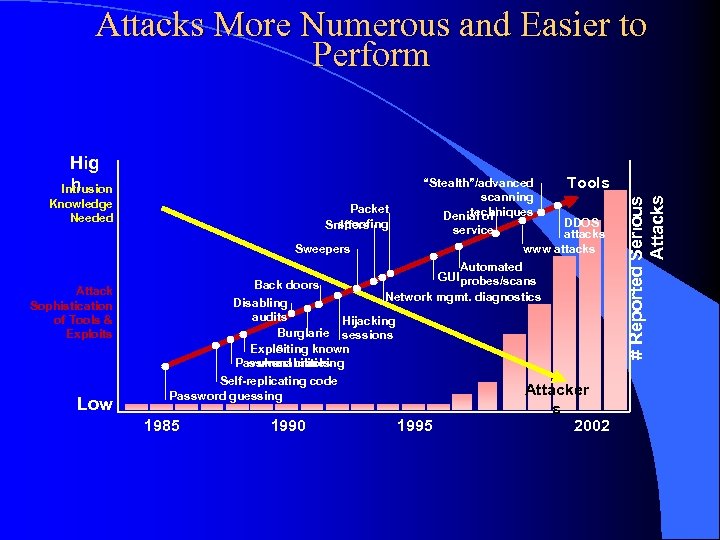 Attacks More Numerous and Easier to Perform Knowledge Needed Packet spoofing Sniffers service Sweepers Attack Sophistication of Tools & Exploits Low Tools “Stealth”/advanced scanning techniques Denial of DDOS attacks www attacks Automated GUI probes/scans Back doors Network mgmt. diagnostics Disabling audits Hijacking Burglarie sessions s Exploiting known Password cracking vulnerabilities Self-replicating code Attacker Password guessing 1985 1990 1995 s 2002 # Reported Serious Attacks Hig h Intrusion
Attacks More Numerous and Easier to Perform Knowledge Needed Packet spoofing Sniffers service Sweepers Attack Sophistication of Tools & Exploits Low Tools “Stealth”/advanced scanning techniques Denial of DDOS attacks www attacks Automated GUI probes/scans Back doors Network mgmt. diagnostics Disabling audits Hijacking Burglarie sessions s Exploiting known Password cracking vulnerabilities Self-replicating code Attacker Password guessing 1985 1990 1995 s 2002 # Reported Serious Attacks Hig h Intrusion
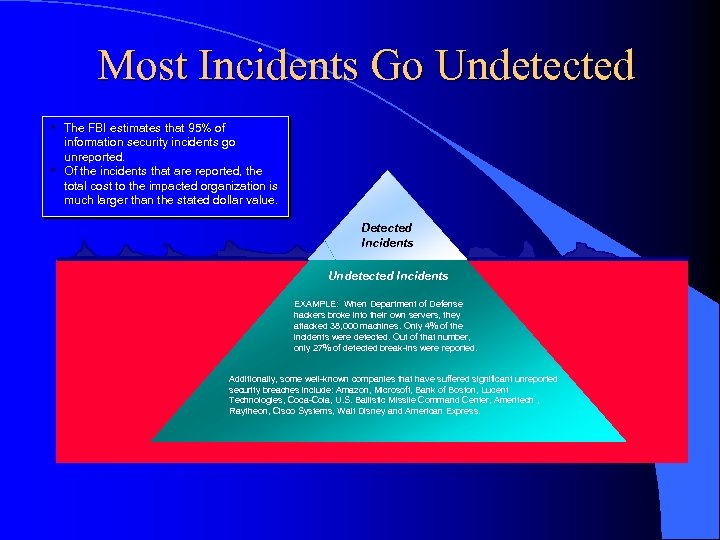 Most Incidents Go Undetected § The FBI estimates that 95% of information security incidents go unreported. § Of the incidents that are reported, the total cost to the impacted organization is much larger than the stated dollar value. Detected Incidents Undetected Incidents EXAMPLE: When Department of Defense hackers broke into their own servers, they attacked 38, 000 machines. Only 4% of the incidents were detected. Out of that number, only 27% of detected break-ins were reported. Additionally, some well-known companies that have suffered significant unreported security breaches include: Amazon, Microsoft, Bank of Boston, Lucent Technologies, Coca-Cola, U. S. Ballistic Missile Command Center, Ameritech , Raytheon, Cisco Systems, Walt Disney and American Express.
Most Incidents Go Undetected § The FBI estimates that 95% of information security incidents go unreported. § Of the incidents that are reported, the total cost to the impacted organization is much larger than the stated dollar value. Detected Incidents Undetected Incidents EXAMPLE: When Department of Defense hackers broke into their own servers, they attacked 38, 000 machines. Only 4% of the incidents were detected. Out of that number, only 27% of detected break-ins were reported. Additionally, some well-known companies that have suffered significant unreported security breaches include: Amazon, Microsoft, Bank of Boston, Lucent Technologies, Coca-Cola, U. S. Ballistic Missile Command Center, Ameritech , Raytheon, Cisco Systems, Walt Disney and American Express.
 HIPAA Risk Impact • • Civil penalties • Health plans, providers and clearinghouses that violate these standards will be subject to civil liability • Civil money penalties are $100 per violation, up to $25, 000 person, per year for each requirement or prohibition violated Pe Federal criminal penalties rso Co na • Under HIPAA, Congress also established criminal st! l penalties for knowingly violating patient privacy • Criminal penalties are up to $50, 000 and one year in prison for obtaining or disclosing protected health information; up to $100, 000 and up to five years in prison for obtaining protected health information under "false pretenses"; and up to $250, 000 and up to 10 years in prison for obtaining or disclosing protected health information with the intent to sell, transfer or use it for commercial advantage, personal gain or malicious harm
HIPAA Risk Impact • • Civil penalties • Health plans, providers and clearinghouses that violate these standards will be subject to civil liability • Civil money penalties are $100 per violation, up to $25, 000 person, per year for each requirement or prohibition violated Pe Federal criminal penalties rso Co na • Under HIPAA, Congress also established criminal st! l penalties for knowingly violating patient privacy • Criminal penalties are up to $50, 000 and one year in prison for obtaining or disclosing protected health information; up to $100, 000 and up to five years in prison for obtaining protected health information under "false pretenses"; and up to $250, 000 and up to 10 years in prison for obtaining or disclosing protected health information with the intent to sell, transfer or use it for commercial advantage, personal gain or malicious harm
 GLB Risk Impact • (a) IN GENERAL- Whoever knowingly and intentionally violates, or knowingly and intentionally attempts to violate, section 521 shall be fined in accordance with title 18, United States Code, or imprisoned for not more than 5 years, or both. • (b) ENHANCED PENALTY FOR AGGRAVATED CASESWhoever violates, or attempts to violate, section 521 while violating another law of the United States or as part of a pattern of any illegal activity involving more than $100, 000 in a 12 month period shall be fined twice the amount provided in subsection (b)(3) or (c)(3) (as the case may be) of section 3571 of title 18, United States Code, imprisoned for not more than 10 years, or both.
GLB Risk Impact • (a) IN GENERAL- Whoever knowingly and intentionally violates, or knowingly and intentionally attempts to violate, section 521 shall be fined in accordance with title 18, United States Code, or imprisoned for not more than 5 years, or both. • (b) ENHANCED PENALTY FOR AGGRAVATED CASESWhoever violates, or attempts to violate, section 521 while violating another law of the United States or as part of a pattern of any illegal activity involving more than $100, 000 in a 12 month period shall be fined twice the amount provided in subsection (b)(3) or (c)(3) (as the case may be) of section 3571 of title 18, United States Code, imprisoned for not more than 10 years, or both.
 Significant Cost Impacts Type of Economic Impact on Organization Immediate economic impact on a university • • • Short-term economic impact on a university • • Long-term economic impact on a university • • • Consequences of Impact Damage to systems that require human intervention to repair or replace Disruption of administrative and academic operations Delays in transactions and cash flow Loss of contractual relationships with other organizations Loss of grants and other sources of funding Negative impact on reputation Hindrance to the development of new programs and funding Insurance recovery costs Regulatory fines and regulatory response Legal costs forensics, depositions, and defense Increased insurance premiums Decline in alumni confidence Long-term funding decline or interruption
Significant Cost Impacts Type of Economic Impact on Organization Immediate economic impact on a university • • • Short-term economic impact on a university • • Long-term economic impact on a university • • • Consequences of Impact Damage to systems that require human intervention to repair or replace Disruption of administrative and academic operations Delays in transactions and cash flow Loss of contractual relationships with other organizations Loss of grants and other sources of funding Negative impact on reputation Hindrance to the development of new programs and funding Insurance recovery costs Regulatory fines and regulatory response Legal costs forensics, depositions, and defense Increased insurance premiums Decline in alumni confidence Long-term funding decline or interruption
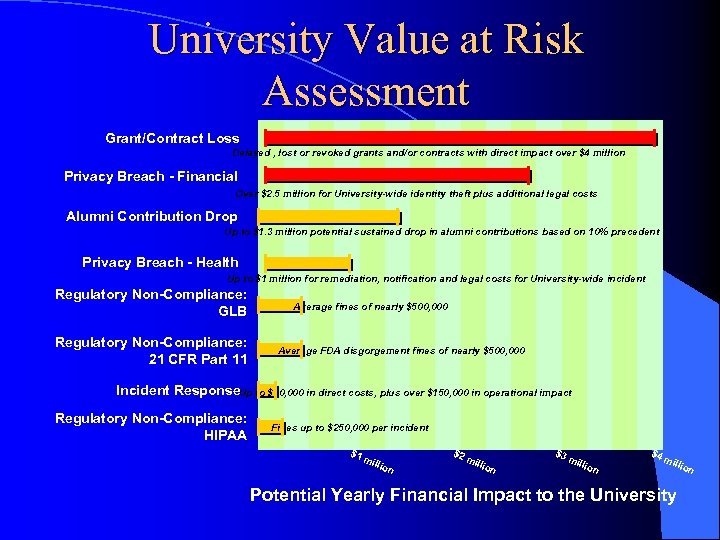 University Value at Risk Assessment Grant/Contract Loss Delayed , lost or revoked grants and/or contracts with direct impact over $4 million Privacy Breach - Financial Over $2. 5 million for University-wide identity theft plus additional legal costs Alumni Contribution Drop Up to $1. 3 million potential sustained drop in alumni contributions based on 10% precedent Privacy Breach - Health Up to $1 million for remediation, notification and legal costs for University-wide incident Regulatory Non-Compliance: GLB Regulatory Non-Compliance: 21 CFR Part 11 Average fines of nearly $500, 000 Average FDA disgorgement fines of nearly $500, 000 Incident Response. Up to $30, 000 in direct costs, plus over $150, 000 in operational impact Regulatory Non-Compliance: HIPAA Fines up to $250, 000 per incident $1 mil lion $2 mil lion $3 mil lion $4 mil lion Potential Yearly Financial Impact to the University
University Value at Risk Assessment Grant/Contract Loss Delayed , lost or revoked grants and/or contracts with direct impact over $4 million Privacy Breach - Financial Over $2. 5 million for University-wide identity theft plus additional legal costs Alumni Contribution Drop Up to $1. 3 million potential sustained drop in alumni contributions based on 10% precedent Privacy Breach - Health Up to $1 million for remediation, notification and legal costs for University-wide incident Regulatory Non-Compliance: GLB Regulatory Non-Compliance: 21 CFR Part 11 Average fines of nearly $500, 000 Average FDA disgorgement fines of nearly $500, 000 Incident Response. Up to $30, 000 in direct costs, plus over $150, 000 in operational impact Regulatory Non-Compliance: HIPAA Fines up to $250, 000 per incident $1 mil lion $2 mil lion $3 mil lion $4 mil lion Potential Yearly Financial Impact to the University
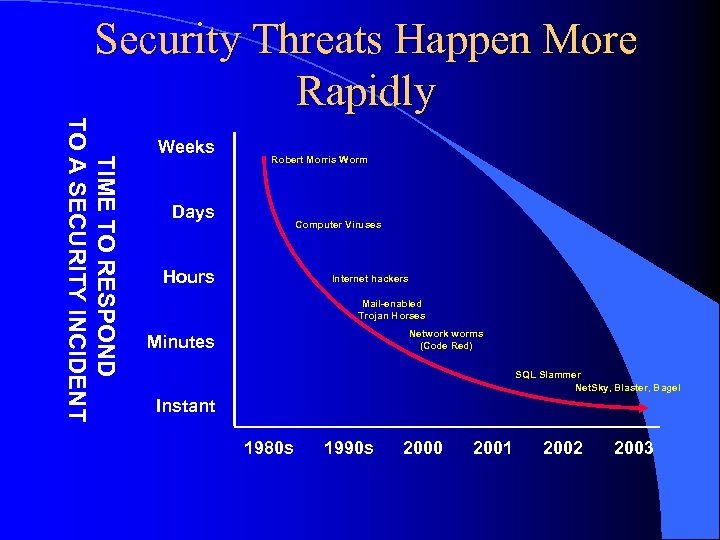 Security Threats Happen More Rapidly TIME TO RESPOND TO A SECURITY INCIDENT Weeks Robert Morris Worm Days Computer Viruses Hours Internet hackers Mail-enabled Trojan Horses Network worms (Code Red) Minutes SQL Slammer Net. Sky, Blaster, Bagel Instant 1980 s 1990 s 2000 2001 2002 2003
Security Threats Happen More Rapidly TIME TO RESPOND TO A SECURITY INCIDENT Weeks Robert Morris Worm Days Computer Viruses Hours Internet hackers Mail-enabled Trojan Horses Network worms (Code Red) Minutes SQL Slammer Net. Sky, Blaster, Bagel Instant 1980 s 1990 s 2000 2001 2002 2003
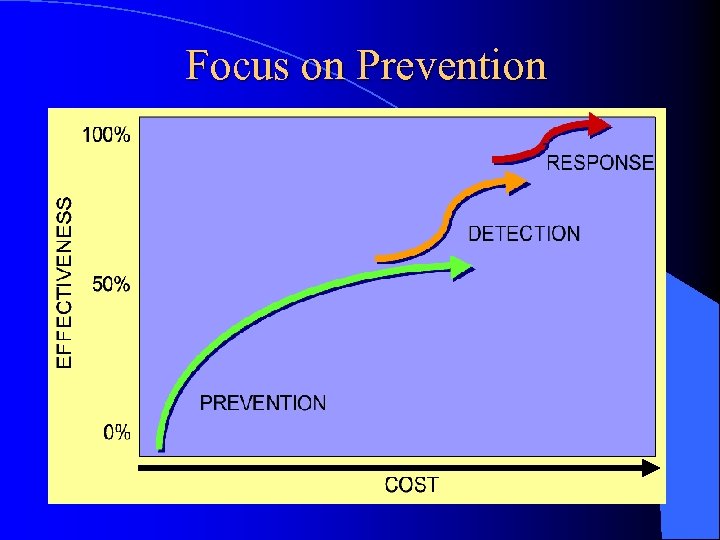 Focus on Prevention
Focus on Prevention
 Three-Year Security Program • • • Introduce cost-effective security control solutions Balances the University’s need for open information exchange with controls that protect University systems and data Strategic architectural approach: • Network-centric security • Risk classification-based prioritization • Zones of trust
Three-Year Security Program • • • Introduce cost-effective security control solutions Balances the University’s need for open information exchange with controls that protect University systems and data Strategic architectural approach: • Network-centric security • Risk classification-based prioritization • Zones of trust
 Security Project Summary • 2004 Projects Security Program • Security awareness • Security guidelines • Security procedures NOC • • • Asset management Data classification inventory NOC security monitoring Vulnerability reporting Enterprise patch management Log file archiving and analysis Authentication & Authorization • SSL VPN rollout SNAP • Vulnerability assessment Incident Prevention § Security MSBs 2005 Projects NOC § § Enterprise security console IDS (host and network) 2006 Projects Authentication & Authorization q Authentication & Authorization § Password self-service Incident Prevention § § Enterprise anti-virus Active content inspection User provisioning
Security Project Summary • 2004 Projects Security Program • Security awareness • Security guidelines • Security procedures NOC • • • Asset management Data classification inventory NOC security monitoring Vulnerability reporting Enterprise patch management Log file archiving and analysis Authentication & Authorization • SSL VPN rollout SNAP • Vulnerability assessment Incident Prevention § Security MSBs 2005 Projects NOC § § Enterprise security console IDS (host and network) 2006 Projects Authentication & Authorization q Authentication & Authorization § Password self-service Incident Prevention § § Enterprise anti-virus Active content inspection User provisioning
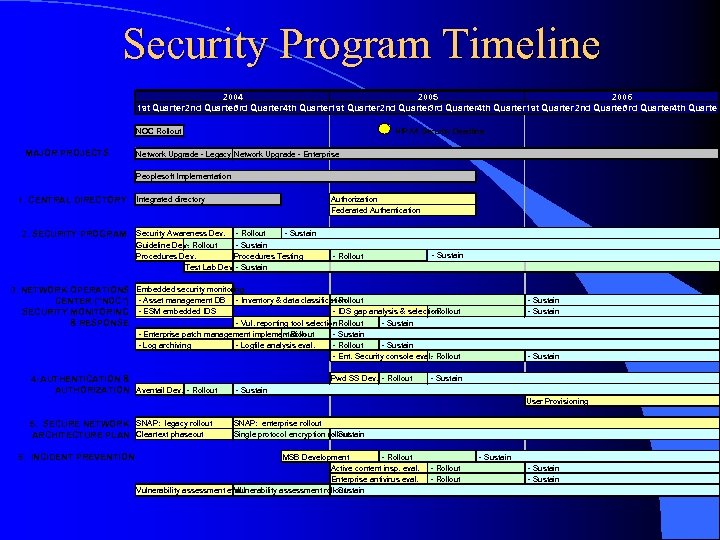 Security Program Timeline 2004 2005 2006 1 st Quarter 2 nd Quarter 3 rd Quarter 4 th Quarter NOC Rollout MAJOR PROJECTS HIPAA Security Deadline Network Upgrade - Legacy Network Upgrade - Enterprise Peoplesoft Implementation 1. CENTRAL DIRECTORY 2. SECURITY PROGRAM Integrated directory Authorization Federated Authentication Security Awareness Dev. - Rollout - Sustain Guideline Dev. - Rollout - Sustain Procedures Dev. Procedures Testing Test Lab Dev - Sustain - Rollout Sustain -- Sustain 3. NETWORK OPERATIONS Embedded security monitoring - Rollout CENTER ("NOC") - Asset management DB - Inventory & data classification - IDS gap analysis & selection - Rollout SECURITY MONITORING - ESM embedded IDS - Vul. reporting tool selection Rollout - Sustain & RESPONSE - Enterprise patch management implementation - Rollout - Log archiving - Logfile analysis eval. 4. AUTHENTICATION & AUTHORIZATION Aventail Dev. - Rollout - Sustain - Rollout - Sustain - Ent. Security console eval. Rollout Pwd SS Dev. - Rollout - Sustain User Provisioning 5. SECURE NETWORK SNAP: legacy rollout ARCHITECTURE PLAN Cleartext phaseout 6. INCIDENT PREVENTION SNAP: enterprise rollout Single protocol encryption rollout - Sustain MSB Development - Rollout Active content insp. eval. Enterprise antivirus eval. Vulnerability assessment rollout - Sustain - Rollout - Sustain
Security Program Timeline 2004 2005 2006 1 st Quarter 2 nd Quarter 3 rd Quarter 4 th Quarter NOC Rollout MAJOR PROJECTS HIPAA Security Deadline Network Upgrade - Legacy Network Upgrade - Enterprise Peoplesoft Implementation 1. CENTRAL DIRECTORY 2. SECURITY PROGRAM Integrated directory Authorization Federated Authentication Security Awareness Dev. - Rollout - Sustain Guideline Dev. - Rollout - Sustain Procedures Dev. Procedures Testing Test Lab Dev - Sustain - Rollout Sustain -- Sustain 3. NETWORK OPERATIONS Embedded security monitoring - Rollout CENTER ("NOC") - Asset management DB - Inventory & data classification - IDS gap analysis & selection - Rollout SECURITY MONITORING - ESM embedded IDS - Vul. reporting tool selection Rollout - Sustain & RESPONSE - Enterprise patch management implementation - Rollout - Log archiving - Logfile analysis eval. 4. AUTHENTICATION & AUTHORIZATION Aventail Dev. - Rollout - Sustain - Rollout - Sustain - Ent. Security console eval. Rollout Pwd SS Dev. - Rollout - Sustain User Provisioning 5. SECURE NETWORK SNAP: legacy rollout ARCHITECTURE PLAN Cleartext phaseout 6. INCIDENT PREVENTION SNAP: enterprise rollout Single protocol encryption rollout - Sustain MSB Development - Rollout Active content insp. eval. Enterprise antivirus eval. Vulnerability assessment rollout - Sustain - Rollout - Sustain
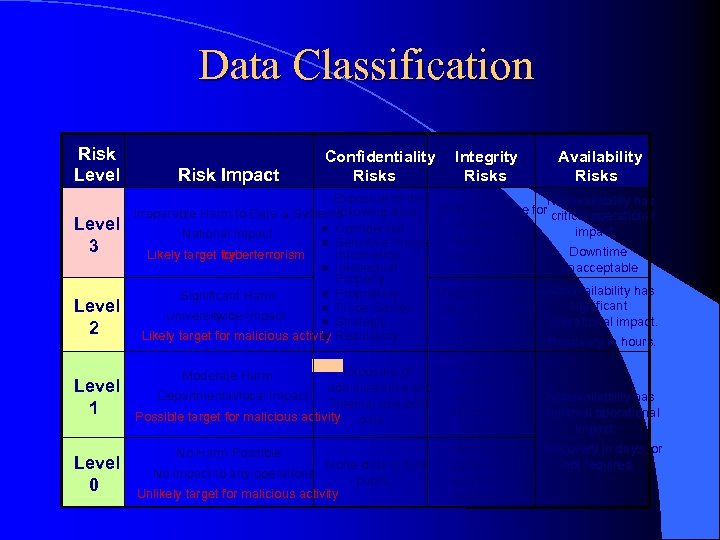 Data Classification Risk Level 3 Level 2 Level 1 Level 0 Risk Impact Confidentiality Risks Integrity Risks Availability Risks Exposure of the Non -availability has following data: ZERO tolerance for critical operational Irreparable Harm to Data & Systems unauthorized n Confidential impact. National Impact activity and n Sensitive Private Downtime Likely target for cyberterrorism Information modification. unacceptable n Intellectual Property -availability has Moderate tolerance. Non n Proprietary Significant Harm significant n Trade Secret for unauthorized University -wide Impact operational impact. n Strategic activity and n Regulatory Likely target for malicious activity modification Recovery in hours. Exposure of administrative and Departmental/local Impact “internal use only” Possible target for malicious activity data. Moderate Harm No Harm Possible None —data is fully public. Unlikely target for malicious activity No impact to any operations Possible unauthorized activity and modification tolerable No need to authorize any activities and modifications Non -availability has minimal operational impact. Recovery in days, or not required.
Data Classification Risk Level 3 Level 2 Level 1 Level 0 Risk Impact Confidentiality Risks Integrity Risks Availability Risks Exposure of the Non -availability has following data: ZERO tolerance for critical operational Irreparable Harm to Data & Systems unauthorized n Confidential impact. National Impact activity and n Sensitive Private Downtime Likely target for cyberterrorism Information modification. unacceptable n Intellectual Property -availability has Moderate tolerance. Non n Proprietary Significant Harm significant n Trade Secret for unauthorized University -wide Impact operational impact. n Strategic activity and n Regulatory Likely target for malicious activity modification Recovery in hours. Exposure of administrative and Departmental/local Impact “internal use only” Possible target for malicious activity data. Moderate Harm No Harm Possible None —data is fully public. Unlikely target for malicious activity No impact to any operations Possible unauthorized activity and modification tolerable No need to authorize any activities and modifications Non -availability has minimal operational impact. Recovery in days, or not required.
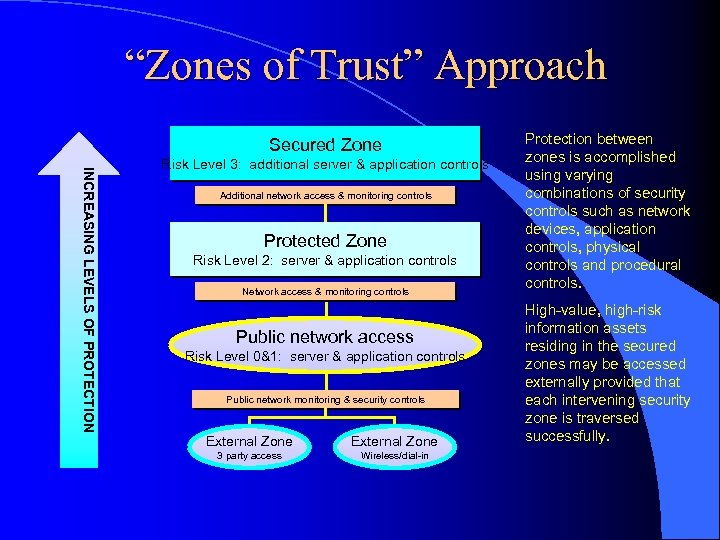 “Zones of Trust” Approach Secured Zone INCREASING LEVELS OF PROTECTION Risk Level 3: additional server & application controls Additional network access & monitoring controls Protected Zone Risk Level 2: server & application controls Network access & monitoring controls Public network access Risk Level 0&1: server & application controls Public network monitoring & security controls External Zone 3 party access Wireless/dial-in Protection between zones is accomplished using varying combinations of security controls such as network devices, application controls, physical controls and procedural controls. High-value, high-risk information assets residing in the secured zones may be accessed externally provided that each intervening security zone is traversed successfully.
“Zones of Trust” Approach Secured Zone INCREASING LEVELS OF PROTECTION Risk Level 3: additional server & application controls Additional network access & monitoring controls Protected Zone Risk Level 2: server & application controls Network access & monitoring controls Public network access Risk Level 0&1: server & application controls Public network monitoring & security controls External Zone 3 party access Wireless/dial-in Protection between zones is accomplished using varying combinations of security controls such as network devices, application controls, physical controls and procedural controls. High-value, high-risk information assets residing in the secured zones may be accessed externally provided that each intervening security zone is traversed successfully.
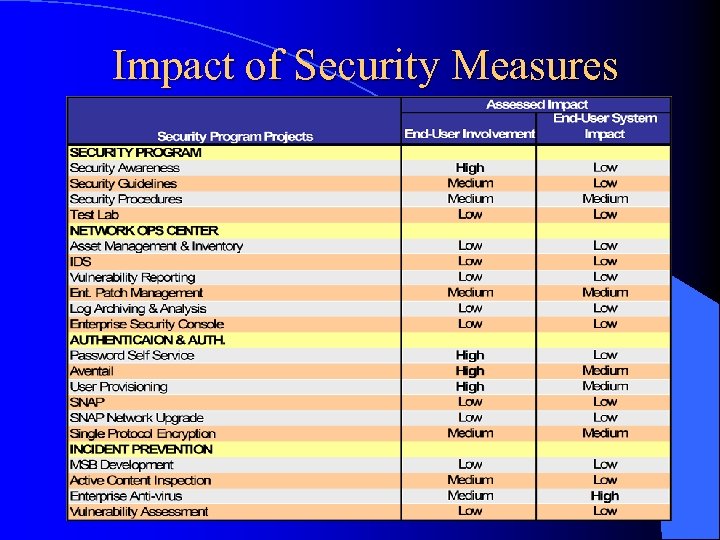 Impact of Security Measures
Impact of Security Measures
 Accomplishments • Completed “current state” security risk review • Identified needed guidelines and procedures • Completed security architecture program • Completed security architecture roadmap
Accomplishments • Completed “current state” security risk review • Identified needed guidelines and procedures • Completed security architecture program • Completed security architecture roadmap


