45c90d78c01feb6851269c2d570a49a5.ppt
- Количество слайдов: 42
 Securing the SIP Trunk Ravi Varanasi Vice President, Engineering Sipera Systems. ravi@sipera. com
Securing the SIP Trunk Ravi Varanasi Vice President, Engineering Sipera Systems. ravi@sipera. com
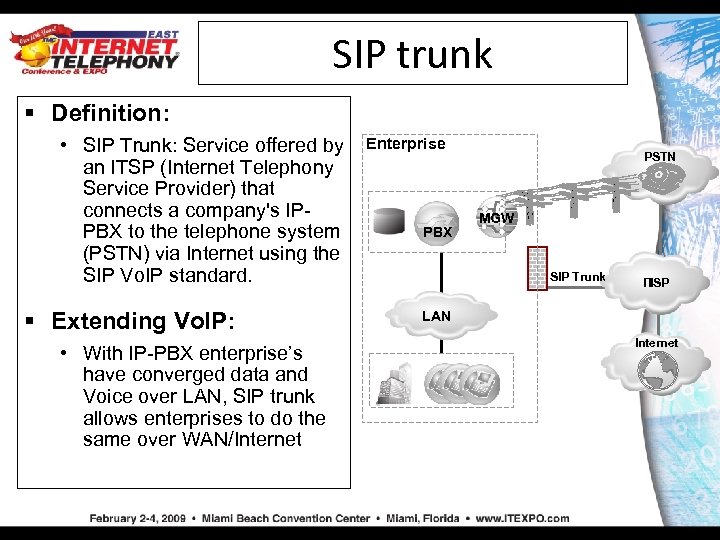 SIP trunk § Definition: • SIP Trunk: Service offered by an ITSP (Internet Telephony Service Provider) that connects a company's IPPBX to the telephone system (PSTN) via Internet using the SIP Vo. IP standard. § Extending Vo. IP: • With IP-PBX enterprise’s have converged data and Voice over LAN, SIP trunk allows enterprises to do the same over WAN/Internet Enterprise PBX PSTN MGW SIP Trunk ITSP ISP LAN Internet
SIP trunk § Definition: • SIP Trunk: Service offered by an ITSP (Internet Telephony Service Provider) that connects a company's IPPBX to the telephone system (PSTN) via Internet using the SIP Vo. IP standard. § Extending Vo. IP: • With IP-PBX enterprise’s have converged data and Voice over LAN, SIP trunk allows enterprises to do the same over WAN/Internet Enterprise PBX PSTN MGW SIP Trunk ITSP ISP LAN Internet
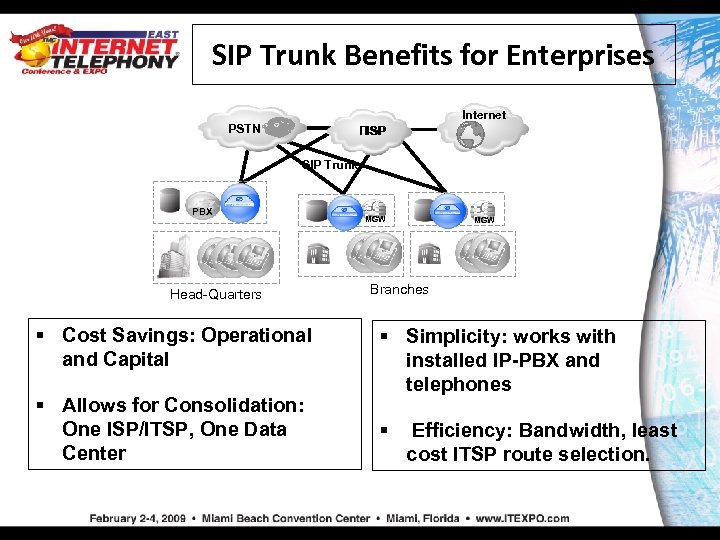 SIP Trunk Benefits for Enterprises Internet PSTN ITSP ISP SIP Trunk PBX MGW Head-Quarters § Cost Savings: Operational and Capital § Allows for Consolidation: One ISP/ITSP, One Data Center PBX MGW Branches § Simplicity: works with installed IP-PBX and telephones § Efficiency: Bandwidth, least cost ITSP route selection.
SIP Trunk Benefits for Enterprises Internet PSTN ITSP ISP SIP Trunk PBX MGW Head-Quarters § Cost Savings: Operational and Capital § Allows for Consolidation: One ISP/ITSP, One Data Center PBX MGW Branches § Simplicity: works with installed IP-PBX and telephones § Efficiency: Bandwidth, least cost ITSP route selection.
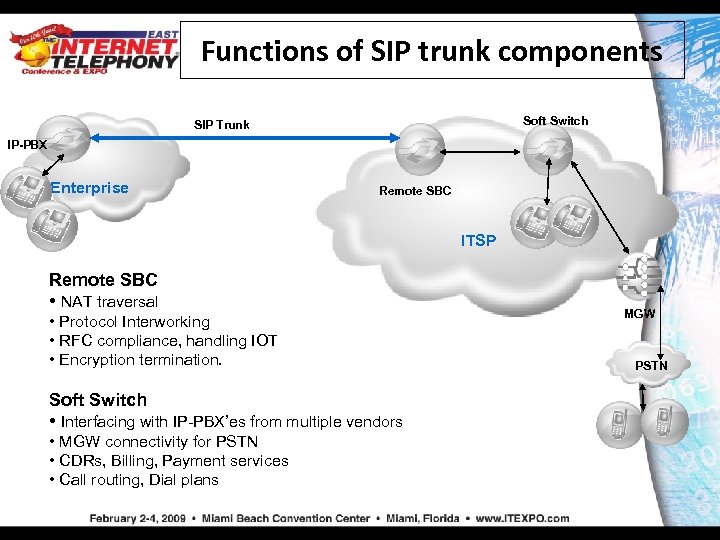 Functions of SIP trunk components Soft Switch SIP Trunk IP-PBX Enterprise Remote SBC ITSP Remote SBC • NAT traversal • Protocol Interworking • RFC compliance, handling IOT • Encryption termination. Soft Switch • Interfacing with IP-PBX’es from multiple vendors • MGW connectivity for PSTN • CDRs, Billing, Payment services • Call routing, Dial plans MGW PSTN
Functions of SIP trunk components Soft Switch SIP Trunk IP-PBX Enterprise Remote SBC ITSP Remote SBC • NAT traversal • Protocol Interworking • RFC compliance, handling IOT • Encryption termination. Soft Switch • Interfacing with IP-PBX’es from multiple vendors • MGW connectivity for PSTN • CDRs, Billing, Payment services • Call routing, Dial plans MGW PSTN
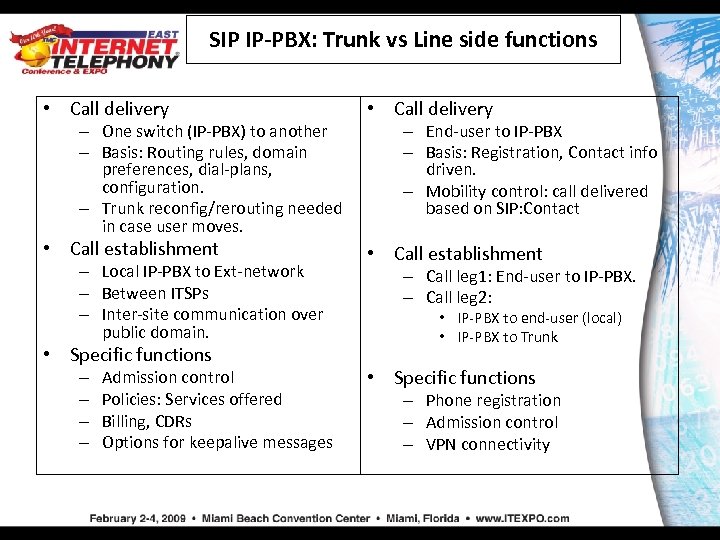 SIP IP-PBX: Trunk vs Line side functions • Call delivery • Call establishment – One switch (IP-PBX) to another – Basis: Routing rules, domain preferences, dial-plans, configuration. – Trunk reconfig/rerouting needed in case user moves. – Local IP-PBX to Ext-network – Between ITSPs – Inter-site communication over public domain. • Specific functions – – Admission control Policies: Services offered Billing, CDRs Options for keepalive messages – End-user to IP-PBX – Basis: Registration, Contact info driven. – Mobility control: call delivered based on SIP: Contact – Call leg 1: End-user to IP-PBX. – Call leg 2: • IP-PBX to end-user (local) • IP-PBX to Trunk • Specific functions – Phone registration – Admission control – VPN connectivity
SIP IP-PBX: Trunk vs Line side functions • Call delivery • Call establishment – One switch (IP-PBX) to another – Basis: Routing rules, domain preferences, dial-plans, configuration. – Trunk reconfig/rerouting needed in case user moves. – Local IP-PBX to Ext-network – Between ITSPs – Inter-site communication over public domain. • Specific functions – – Admission control Policies: Services offered Billing, CDRs Options for keepalive messages – End-user to IP-PBX – Basis: Registration, Contact info driven. – Mobility control: call delivered based on SIP: Contact – Call leg 1: End-user to IP-PBX. – Call leg 2: • IP-PBX to end-user (local) • IP-PBX to Trunk • Specific functions – Phone registration – Admission control – VPN connectivity
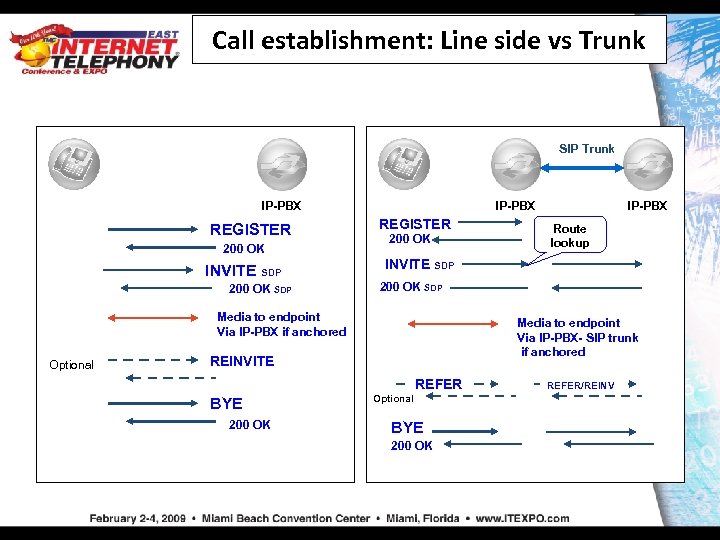 Call establishment: Line side vs Trunk SIP Trunk IP-PBX REGISTER 200 OK INVITE SDP 200 OK SDP IP-PBX REGISTER 200 OK SDP Media to endpoint Via IP-PBX- SIP trunk if anchored REINVITE REFER BYE 200 OK Route lookup INVITE SDP Media to endpoint Via IP-PBX if anchored Optional IP-PBX Optional BYE 200 OK REFER/REINV
Call establishment: Line side vs Trunk SIP Trunk IP-PBX REGISTER 200 OK INVITE SDP 200 OK SDP IP-PBX REGISTER 200 OK SDP Media to endpoint Via IP-PBX- SIP trunk if anchored REINVITE REFER BYE 200 OK Route lookup INVITE SDP Media to endpoint Via IP-PBX if anchored Optional IP-PBX Optional BYE 200 OK REFER/REINV
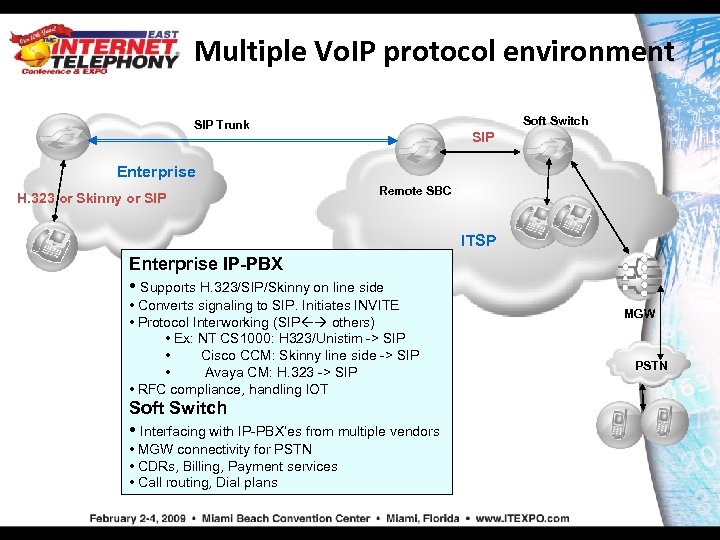 Multiple Vo. IP protocol environment Soft Switch SIP Trunk SIP Enterprise H. 323 or Skinny or SIP Remote SBC ITSP Enterprise IP-PBX • Supports H. 323/SIP/Skinny on line side • Converts signaling to SIP. Initiates INVITE • Protocol Interworking (SIP others) • Ex: NT CS 1000: H 323/Unistim -> SIP • Cisco CCM: Skinny line side -> SIP • Avaya CM: H. 323 -> SIP • RFC compliance, handling IOT Soft Switch • Interfacing with IP-PBX’es from multiple vendors • MGW connectivity for PSTN • CDRs, Billing, Payment services • Call routing, Dial plans MGW PSTN
Multiple Vo. IP protocol environment Soft Switch SIP Trunk SIP Enterprise H. 323 or Skinny or SIP Remote SBC ITSP Enterprise IP-PBX • Supports H. 323/SIP/Skinny on line side • Converts signaling to SIP. Initiates INVITE • Protocol Interworking (SIP others) • Ex: NT CS 1000: H 323/Unistim -> SIP • Cisco CCM: Skinny line side -> SIP • Avaya CM: H. 323 -> SIP • RFC compliance, handling IOT Soft Switch • Interfacing with IP-PBX’es from multiple vendors • MGW connectivity for PSTN • CDRs, Billing, Payment services • Call routing, Dial plans MGW PSTN
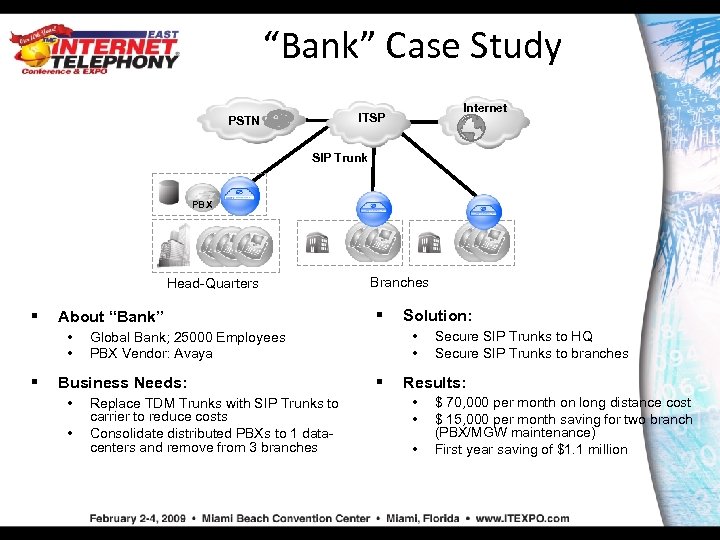 “Bank” Case Study Internet ITSP PSTN SIP Trunk PBX MGW Head-Quarters § About “Bank” • • § Replace TDM Trunks with SIP Trunks to carrier to reduce costs Consolidate distributed PBXs to 1 datacenters and remove from 3 branches Solution: • • Global Bank; 25000 Employees PBX Vendor: Avaya Business Needs: • Branches § Secure SIP Trunks to HQ Secure SIP Trunks to branches Results: • • • $ 70, 000 per month on long distance cost $ 15, 000 per month saving for two branch (PBX/MGW maintenance) First year saving of $1. 1 million
“Bank” Case Study Internet ITSP PSTN SIP Trunk PBX MGW Head-Quarters § About “Bank” • • § Replace TDM Trunks with SIP Trunks to carrier to reduce costs Consolidate distributed PBXs to 1 datacenters and remove from 3 branches Solution: • • Global Bank; 25000 Employees PBX Vendor: Avaya Business Needs: • Branches § Secure SIP Trunks to HQ Secure SIP Trunks to branches Results: • • • $ 70, 000 per month on long distance cost $ 15, 000 per month saving for two branch (PBX/MGW maintenance) First year saving of $1. 1 million
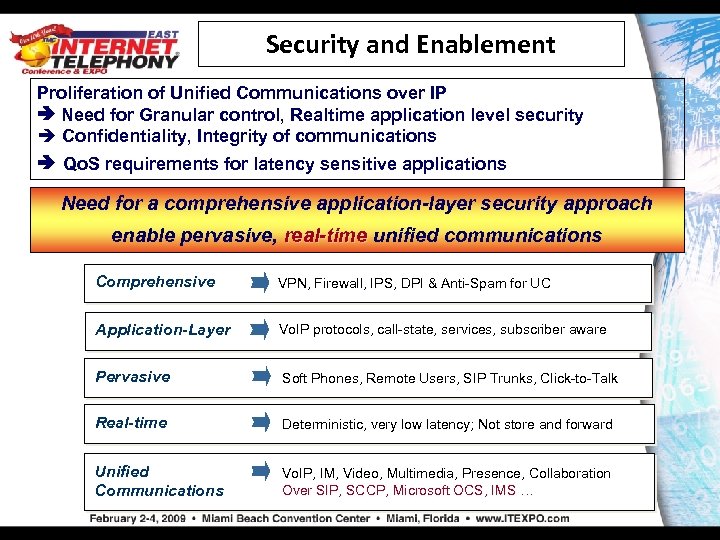 Security and Enablement Proliferation of Unified Communications over IP Need for Granular control, Realtime application level security è Confidentiality, Integrity of communications Qo. S requirements for latency sensitive applications Need for a comprehensive application-layer security approach enable pervasive, real-time unified communications Comprehensive VPN, Firewall, IPS, DPI & Anti-Spam for UC Application-Layer Vo. IP protocols, call-state, services, subscriber aware Pervasive Soft Phones, Remote Users, SIP Trunks, Click-to-Talk Real-time Deterministic, very low latency; Not store and forward Unified Communications Vo. IP, IM, Video, Multimedia, Presence, Collaboration Over SIP, SCCP, Microsoft OCS, IMS …
Security and Enablement Proliferation of Unified Communications over IP Need for Granular control, Realtime application level security è Confidentiality, Integrity of communications Qo. S requirements for latency sensitive applications Need for a comprehensive application-layer security approach enable pervasive, real-time unified communications Comprehensive VPN, Firewall, IPS, DPI & Anti-Spam for UC Application-Layer Vo. IP protocols, call-state, services, subscriber aware Pervasive Soft Phones, Remote Users, SIP Trunks, Click-to-Talk Real-time Deterministic, very low latency; Not store and forward Unified Communications Vo. IP, IM, Video, Multimedia, Presence, Collaboration Over SIP, SCCP, Microsoft OCS, IMS …
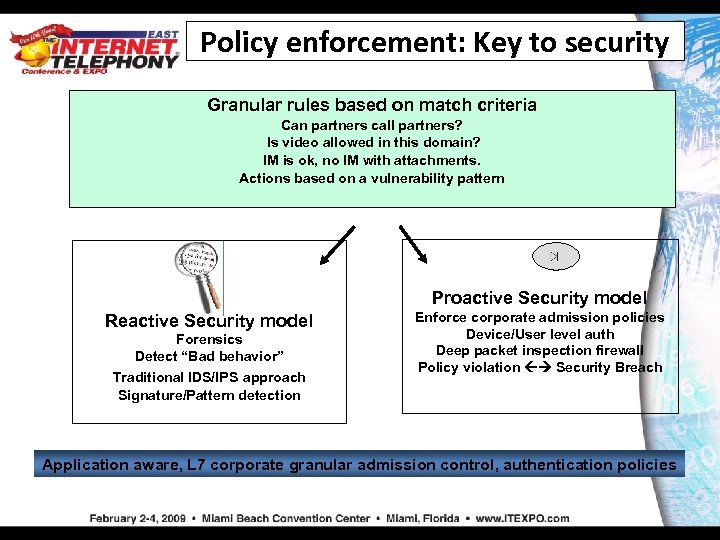 Policy enforcement: Key to security Granular rules based on match criteria Can partners call partners? Is video allowed in this domain? IM is ok, no IM with attachments. Actions based on a vulnerability pattern Proactive Security model Reactive Security model Forensics Detect “Bad behavior” Traditional IDS/IPS approach Signature/Pattern detection Enforce corporate admission policies Device/User level auth Deep packet inspection firewall Policy violation Security Breach Application aware, L 7 corporate granular admission control, authentication policies
Policy enforcement: Key to security Granular rules based on match criteria Can partners call partners? Is video allowed in this domain? IM is ok, no IM with attachments. Actions based on a vulnerability pattern Proactive Security model Reactive Security model Forensics Detect “Bad behavior” Traditional IDS/IPS approach Signature/Pattern detection Enforce corporate admission policies Device/User level auth Deep packet inspection firewall Policy violation Security Breach Application aware, L 7 corporate granular admission control, authentication policies
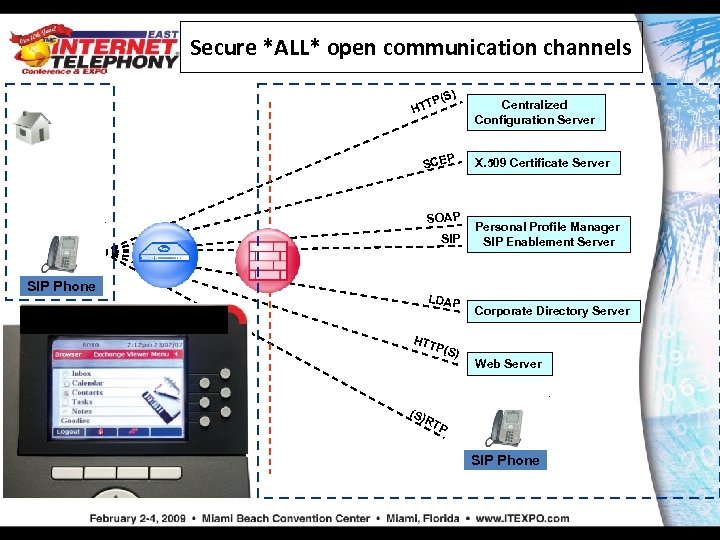 Secure *ALL* open communication channels (S) P HTT SCEP SOAP SIP Phone LDAP Centralized Configuration Server X. 509 Certificate Server Personal Profile Manager SIP Enablement Server Corporate Directory Server HTT P(S ) (S) Web Server RT P SIP Phone
Secure *ALL* open communication channels (S) P HTT SCEP SOAP SIP Phone LDAP Centralized Configuration Server X. 509 Certificate Server Personal Profile Manager SIP Enablement Server Corporate Directory Server HTT P(S ) (S) Web Server RT P SIP Phone
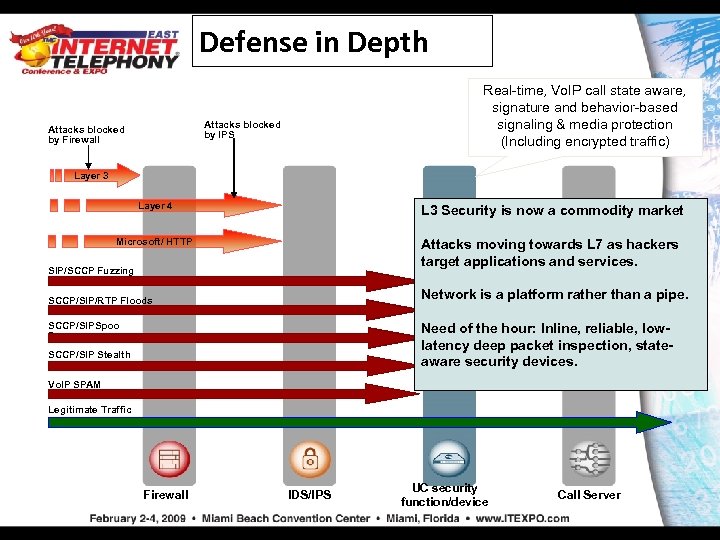 Defense in Depth Real-time, Vo. IP call state aware, signature and behavior-based signaling & media protection (Including encrypted traffic) Attacks blocked by IPS Attacks blocked by Firewall Layer 3 Layer 4 L 3 Security is now a commodity market Microsoft/ HTTP Attacks moving towards L 7 as hackers target applications and services. SIP/SCCP Fuzzing Network is a platform rather than a pipe. SCCP/SIP/RTP Floods Need of the hour: Inline, reliable, lowlatency deep packet inspection, stateaware security devices. SCCP/SIPSpoo fing SCCP/SIP Stealth Attacks Vo. IP SPAM Legitimate Traffic Firewall IDS/IPS UC security function/device Call Server
Defense in Depth Real-time, Vo. IP call state aware, signature and behavior-based signaling & media protection (Including encrypted traffic) Attacks blocked by IPS Attacks blocked by Firewall Layer 3 Layer 4 L 3 Security is now a commodity market Microsoft/ HTTP Attacks moving towards L 7 as hackers target applications and services. SIP/SCCP Fuzzing Network is a platform rather than a pipe. SCCP/SIP/RTP Floods Need of the hour: Inline, reliable, lowlatency deep packet inspection, stateaware security devices. SCCP/SIPSpoo fing SCCP/SIP Stealth Attacks Vo. IP SPAM Legitimate Traffic Firewall IDS/IPS UC security function/device Call Server
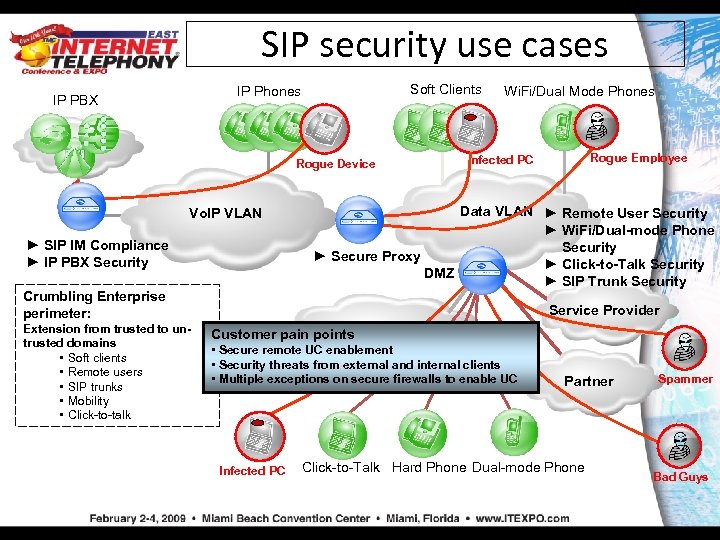 SIP security use cases Soft Clients IP Phones IP PBX Rogue Device Vo. IP VLAN ► SIP IM Compliance ► IP PBX Security Wi. Fi/Dual Mode Phones Data VLAN ► Remote User Security ► Wi. Fi/Dual-mode Phone Security ► Secure Proxy ► Click-to-Talk Security DMZ ► SIP Trunk Security Crumbling Enterprise perimeter: Extension from trusted to untrusted domains • Soft clients • Remote users • SIP trunks • Mobility • Click-to-talk Rogue Employee Infected PC Service Provider Customer pain points. Internet • Secure remote UC enablement • Security threats from external and internal clients • Multiple exceptions on secure firewalls to enable UC Infected PC Partner Click-to-Talk Hard Phone Dual-mode Phone Spammer Bad Guys
SIP security use cases Soft Clients IP Phones IP PBX Rogue Device Vo. IP VLAN ► SIP IM Compliance ► IP PBX Security Wi. Fi/Dual Mode Phones Data VLAN ► Remote User Security ► Wi. Fi/Dual-mode Phone Security ► Secure Proxy ► Click-to-Talk Security DMZ ► SIP Trunk Security Crumbling Enterprise perimeter: Extension from trusted to untrusted domains • Soft clients • Remote users • SIP trunks • Mobility • Click-to-talk Rogue Employee Infected PC Service Provider Customer pain points. Internet • Secure remote UC enablement • Security threats from external and internal clients • Multiple exceptions on secure firewalls to enable UC Infected PC Partner Click-to-Talk Hard Phone Dual-mode Phone Spammer Bad Guys
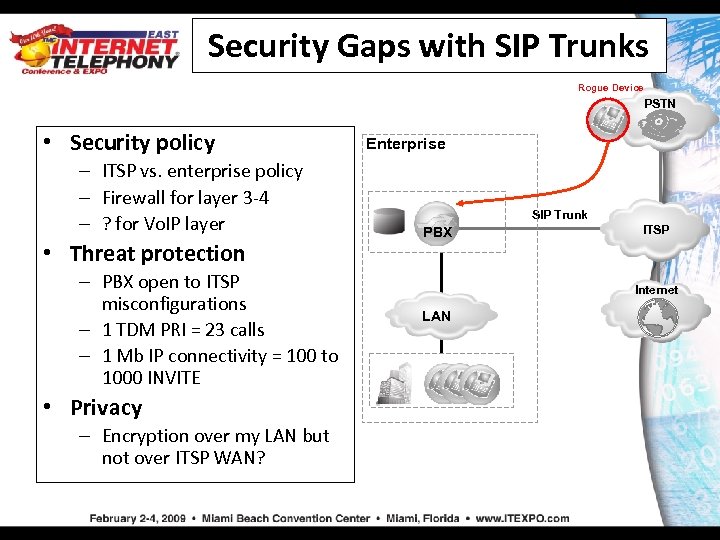 Security Gaps with SIP Trunks Rogue Device PSTN • Security policy – ITSP vs. enterprise policy – Firewall for layer 3 -4 – ? for Vo. IP layer • Threat protection – PBX open to ITSP misconfigurations – 1 TDM PRI = 23 calls – 1 Mb IP connectivity = 100 to 1000 INVITE • Privacy – Encryption over my LAN but not over ITSP WAN? Enterprise SIP Trunk PBX ITSP Internet LAN
Security Gaps with SIP Trunks Rogue Device PSTN • Security policy – ITSP vs. enterprise policy – Firewall for layer 3 -4 – ? for Vo. IP layer • Threat protection – PBX open to ITSP misconfigurations – 1 TDM PRI = 23 calls – 1 Mb IP connectivity = 100 to 1000 INVITE • Privacy – Encryption over my LAN but not over ITSP WAN? Enterprise SIP Trunk PBX ITSP Internet LAN
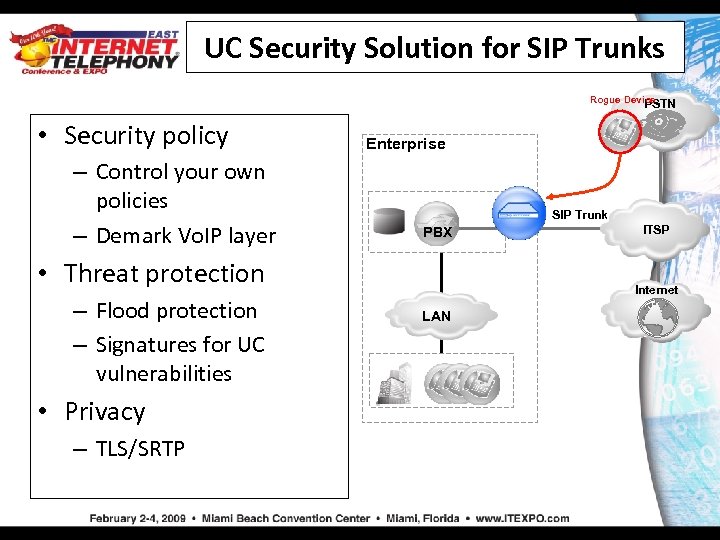 UC Security Solution for SIP Trunks Rogue Device PSTN • Security policy – Control your own policies – Demark Vo. IP layer Enterprise SIP Trunk PBX • Threat protection – Flood protection – Signatures for UC vulnerabilities • Privacy – TLS/SRTP ITSP Internet LAN
UC Security Solution for SIP Trunks Rogue Device PSTN • Security policy – Control your own policies – Demark Vo. IP layer Enterprise SIP Trunk PBX • Threat protection – Flood protection – Signatures for UC vulnerabilities • Privacy – TLS/SRTP ITSP Internet LAN
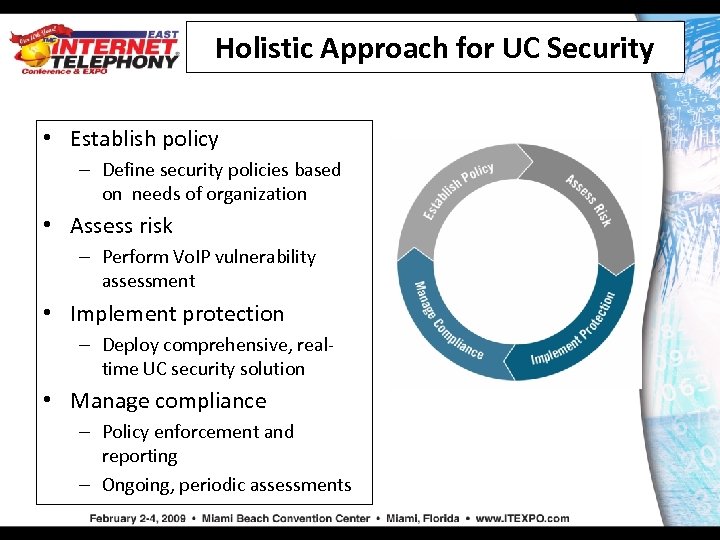 Holistic Approach for UC Security • Establish policy – Define security policies based on needs of organization • Assess risk – Perform Vo. IP vulnerability assessment • Implement protection – Deploy comprehensive, realtime UC security solution • Manage compliance – Policy enforcement and reporting – Ongoing, periodic assessments
Holistic Approach for UC Security • Establish policy – Define security policies based on needs of organization • Assess risk – Perform Vo. IP vulnerability assessment • Implement protection – Deploy comprehensive, realtime UC security solution • Manage compliance – Policy enforcement and reporting – Ongoing, periodic assessments
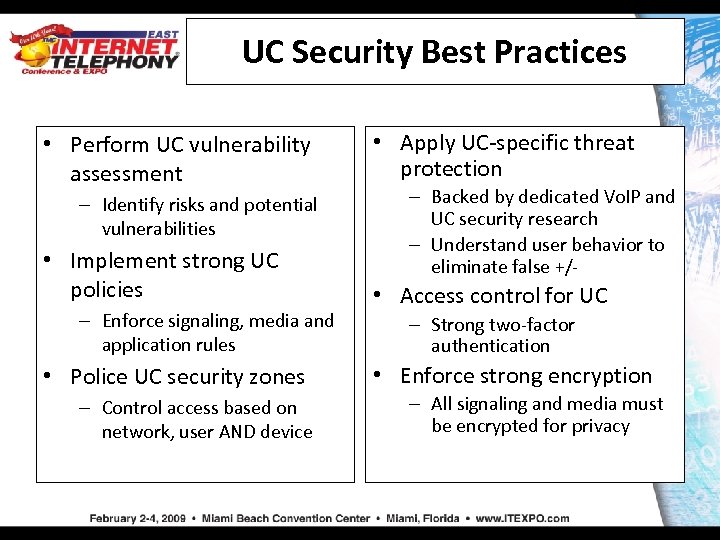 UC Security Best Practices • Perform UC vulnerability assessment – Identify risks and potential vulnerabilities • Implement strong UC policies – Enforce signaling, media and application rules • Police UC security zones – Control access based on network, user AND device • Apply UC-specific threat protection – Backed by dedicated Vo. IP and UC security research – Understand user behavior to eliminate false +/- • Access control for UC – Strong two-factor authentication • Enforce strong encryption – All signaling and media must be encrypted for privacy
UC Security Best Practices • Perform UC vulnerability assessment – Identify risks and potential vulnerabilities • Implement strong UC policies – Enforce signaling, media and application rules • Police UC security zones – Control access based on network, user AND device • Apply UC-specific threat protection – Backed by dedicated Vo. IP and UC security research – Understand user behavior to eliminate false +/- • Access control for UC – Strong two-factor authentication • Enforce strong encryption – All signaling and media must be encrypted for privacy
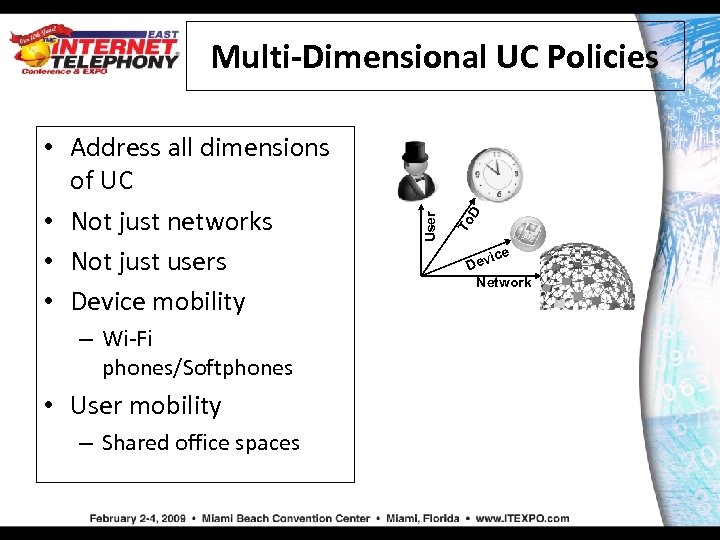 – Wi-Fi phones/Softphones • User mobility – Shared office spaces To D • Address all dimensions of UC • Not just networks • Not just users • Device mobility User Multi-Dimensional UC Policies ice Dev Network
– Wi-Fi phones/Softphones • User mobility – Shared office spaces To D • Address all dimensions of UC • Not just networks • Not just users • Device mobility User Multi-Dimensional UC Policies ice Dev Network
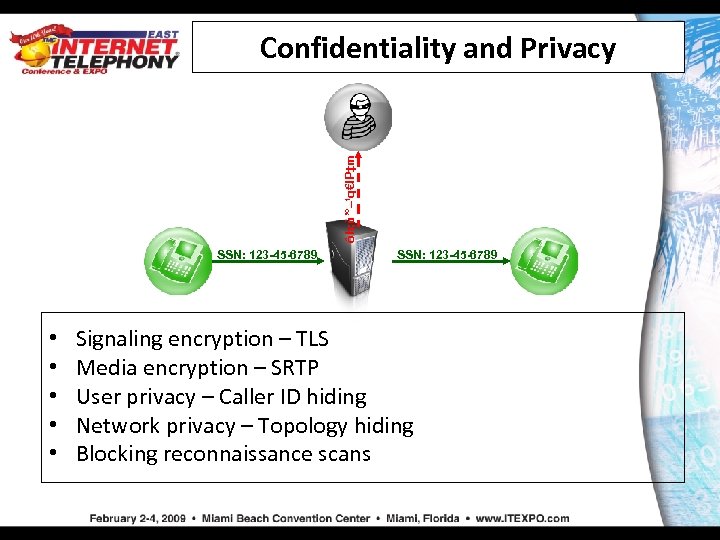 ôh; ù’°–¹q€IP‡m Confidentiality and Privacy SSN: 123 -45 -6789 • • • SSN: 123 -45 -6789 Signaling encryption – TLS Media encryption – SRTP User privacy – Caller ID hiding Network privacy – Topology hiding Blocking reconnaissance scans
ôh; ù’°–¹q€IP‡m Confidentiality and Privacy SSN: 123 -45 -6789 • • • SSN: 123 -45 -6789 Signaling encryption – TLS Media encryption – SRTP User privacy – Caller ID hiding Network privacy – Topology hiding Blocking reconnaissance scans
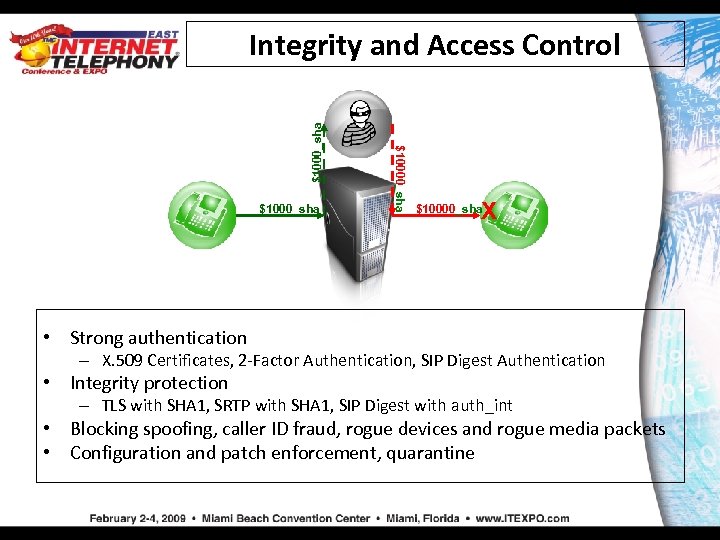 $1000_sha Integrity and Access Control X $10000_sha • Strong authentication – X. 509 Certificates, 2 -Factor Authentication, SIP Digest Authentication • Integrity protection – TLS with SHA 1, SRTP with SHA 1, SIP Digest with auth_int • Blocking spoofing, caller ID fraud, rogue devices and rogue media packets • Configuration and patch enforcement, quarantine
$1000_sha Integrity and Access Control X $10000_sha • Strong authentication – X. 509 Certificates, 2 -Factor Authentication, SIP Digest Authentication • Integrity protection – TLS with SHA 1, SRTP with SHA 1, SIP Digest with auth_int • Blocking spoofing, caller ID fraud, rogue devices and rogue media packets • Configuration and patch enforcement, quarantine
 Availability and Threat Protection X • • Blocking application layer Do. S floods Blocking distributed denial of service (DDo. S) Blocking stealth Do. S Blocking malformed or fuzzed messages
Availability and Threat Protection X • • Blocking application layer Do. S floods Blocking distributed denial of service (DDo. S) Blocking stealth Do. S Blocking malformed or fuzzed messages
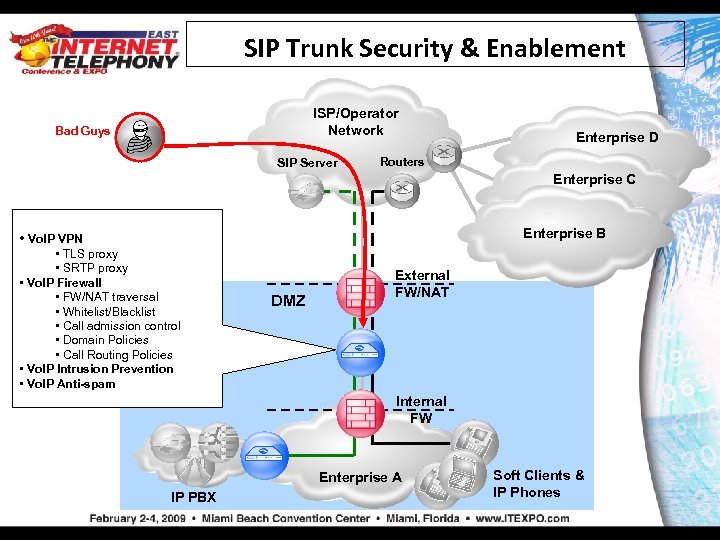 SIP Trunk Security & Enablement ISP/Operator Network Bad Guys SIP Server Enterprise D Routers Enterprise C Enterprise B • Vo. IP VPN • TLS proxy • SRTP proxy • Vo. IP Firewall • FW/NAT traversal • Whitelist/Blacklist • Call admission control • Domain Policies • Call Routing Policies • Vo. IP Intrusion Prevention • Vo. IP Anti-spam DMZ External FW/NAT Internal FW Enterprise A IP PBX Soft Clients & IP Phones
SIP Trunk Security & Enablement ISP/Operator Network Bad Guys SIP Server Enterprise D Routers Enterprise C Enterprise B • Vo. IP VPN • TLS proxy • SRTP proxy • Vo. IP Firewall • FW/NAT traversal • Whitelist/Blacklist • Call admission control • Domain Policies • Call Routing Policies • Vo. IP Intrusion Prevention • Vo. IP Anti-spam DMZ External FW/NAT Internal FW Enterprise A IP PBX Soft Clients & IP Phones
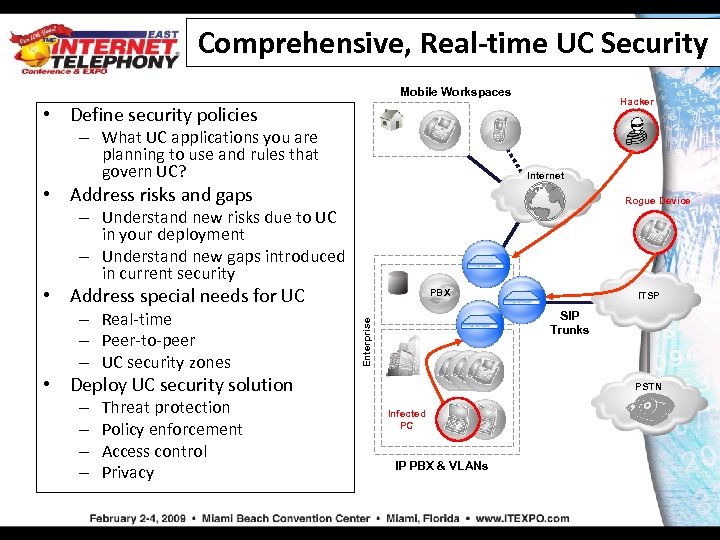 Comprehensive, Real-time UC Security Mobile Workspaces Hacker • Define security policies – What UC applications you are planning to use and rules that govern UC? Internet • Address risks and gaps Rogue Device – Understand new risks due to UC in your deployment – Understand new gaps introduced in current security • Address special needs for UC • Deploy UC security solution – – Threat protection Policy enforcement Access control Privacy ITSP SIP Trunks Enterprise – Real-time – Peer-to-peer – UC security zones PBX PSTN Infected PC IP PBX & VLANs
Comprehensive, Real-time UC Security Mobile Workspaces Hacker • Define security policies – What UC applications you are planning to use and rules that govern UC? Internet • Address risks and gaps Rogue Device – Understand new risks due to UC in your deployment – Understand new gaps introduced in current security • Address special needs for UC • Deploy UC security solution – – Threat protection Policy enforcement Access control Privacy ITSP SIP Trunks Enterprise – Real-time – Peer-to-peer – UC security zones PBX PSTN Infected PC IP PBX & VLANs
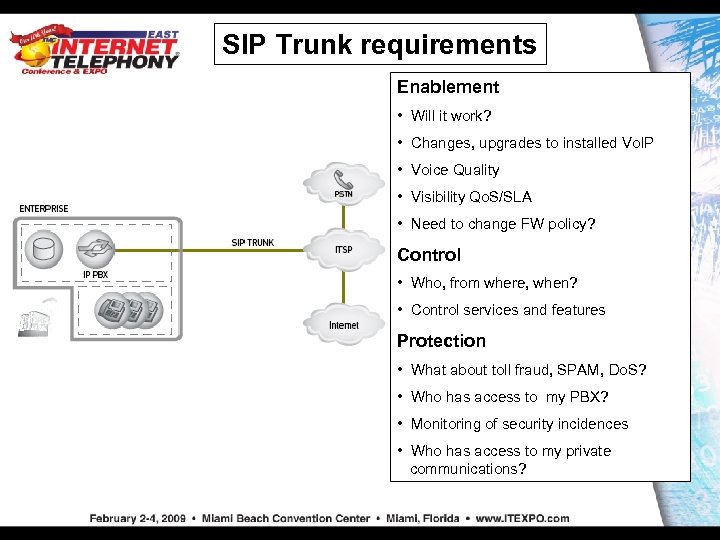 SIP Trunk requirements Enablement • Will it work? • Changes, upgrades to installed Vo. IP • Voice Quality • Visibility Qo. S/SLA • Need to change FW policy? Control • Who, from where, when? • Control services and features Protection • What about toll fraud, SPAM, Do. S? • Who has access to my PBX? • Monitoring of security incidences • Who has access to my private communications?
SIP Trunk requirements Enablement • Will it work? • Changes, upgrades to installed Vo. IP • Voice Quality • Visibility Qo. S/SLA • Need to change FW policy? Control • Who, from where, when? • Control services and features Protection • What about toll fraud, SPAM, Do. S? • Who has access to my PBX? • Monitoring of security incidences • Who has access to my private communications?
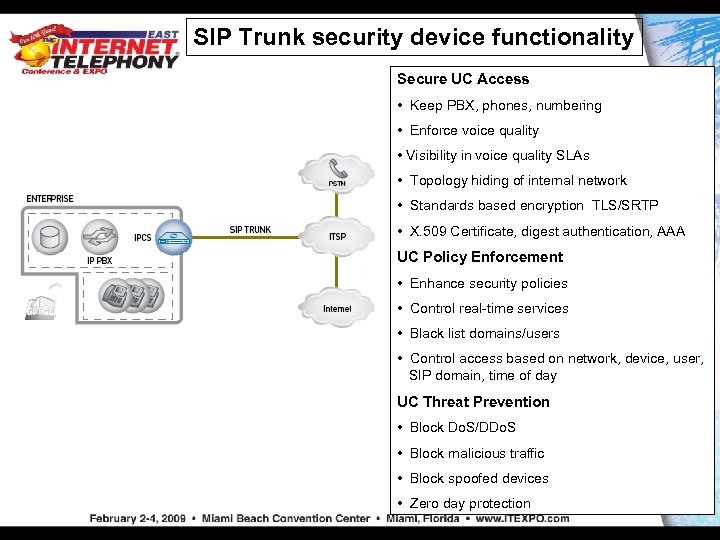 SIP Trunk security device functionality Secure UC Access • Keep PBX, phones, numbering • Enforce voice quality • Visibility in voice quality SLAs • Topology hiding of internal network • Standards based encryption TLS/SRTP • X. 509 Certificate, digest authentication, AAA UC Policy Enforcement • Enhance security policies • Control real-time services • Black list domains/users • Control access based on network, device, user, SIP domain, time of day UC Threat Prevention • Block Do. S/DDo. S • Block malicious traffic • Block spoofed devices • Zero day protection
SIP Trunk security device functionality Secure UC Access • Keep PBX, phones, numbering • Enforce voice quality • Visibility in voice quality SLAs • Topology hiding of internal network • Standards based encryption TLS/SRTP • X. 509 Certificate, digest authentication, AAA UC Policy Enforcement • Enhance security policies • Control real-time services • Black list domains/users • Control access based on network, device, user, SIP domain, time of day UC Threat Prevention • Block Do. S/DDo. S • Block malicious traffic • Block spoofed devices • Zero day protection
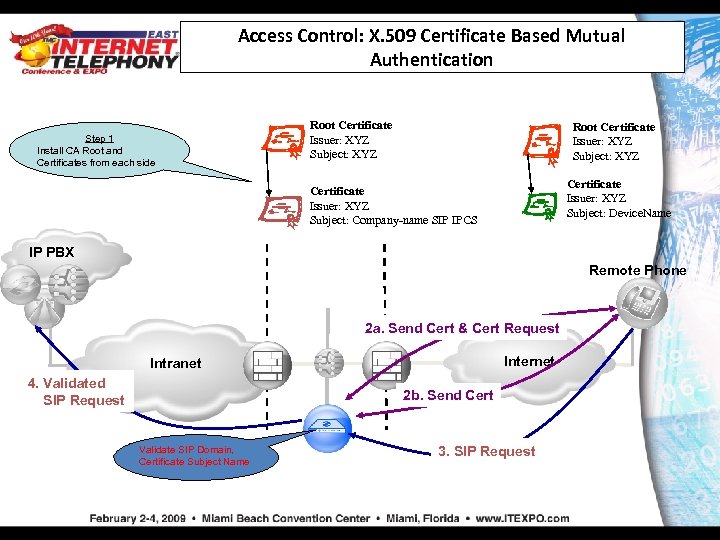 Access Control: X. 509 Certificate Based Mutual Authentication Step 1 Install CA Root and Certificates from each side Root Certificate Issuer: XYZ Subject: XYZ Certificate Issuer: XYZ Subject: Device. Name Certificate Issuer: XYZ Subject: Company-name SIP IPCS IP PBX Remote Phone 2 a. Send Cert & Cert Request Internet Intranet 4. Validated SIP Request 2 b. Send Cert Validate SIP Domain, Certificate Subject Name 3. SIP Request
Access Control: X. 509 Certificate Based Mutual Authentication Step 1 Install CA Root and Certificates from each side Root Certificate Issuer: XYZ Subject: XYZ Certificate Issuer: XYZ Subject: Device. Name Certificate Issuer: XYZ Subject: Company-name SIP IPCS IP PBX Remote Phone 2 a. Send Cert & Cert Request Internet Intranet 4. Validated SIP Request 2 b. Send Cert Validate SIP Domain, Certificate Subject Name 3. SIP Request
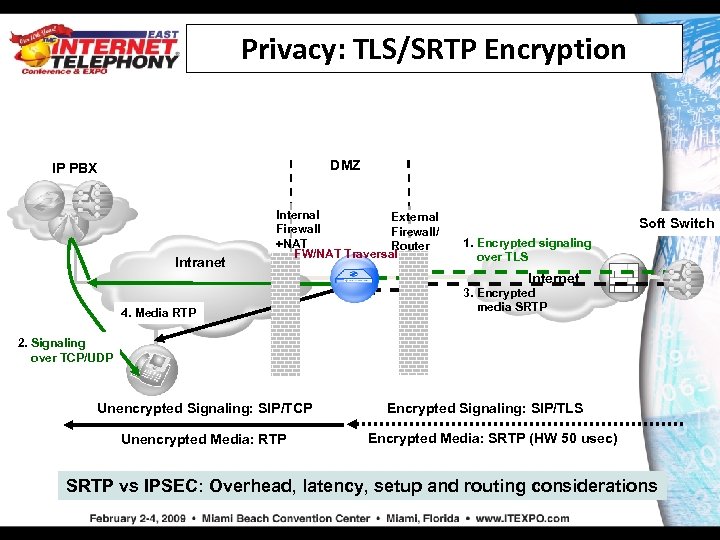 Privacy: TLS/SRTP Encryption DMZ IP PBX Intranet Internal External Firewall/ +NAT Router FW/NAT Traversal Soft Switch 1. Encrypted signaling over TLS Internet 4. Media RTP 3. Encrypted media SRTP 2. Signaling over TCP/UDP Unencrypted Signaling: SIP/TCP Unencrypted Media: RTP Encrypted Signaling: SIP/TLS Encrypted Media: SRTP (HW 50 usec) SRTP vs IPSEC: Overhead, latency, setup and routing considerations
Privacy: TLS/SRTP Encryption DMZ IP PBX Intranet Internal External Firewall/ +NAT Router FW/NAT Traversal Soft Switch 1. Encrypted signaling over TLS Internet 4. Media RTP 3. Encrypted media SRTP 2. Signaling over TCP/UDP Unencrypted Signaling: SIP/TCP Unencrypted Media: RTP Encrypted Signaling: SIP/TLS Encrypted Media: SRTP (HW 50 usec) SRTP vs IPSEC: Overhead, latency, setup and routing considerations
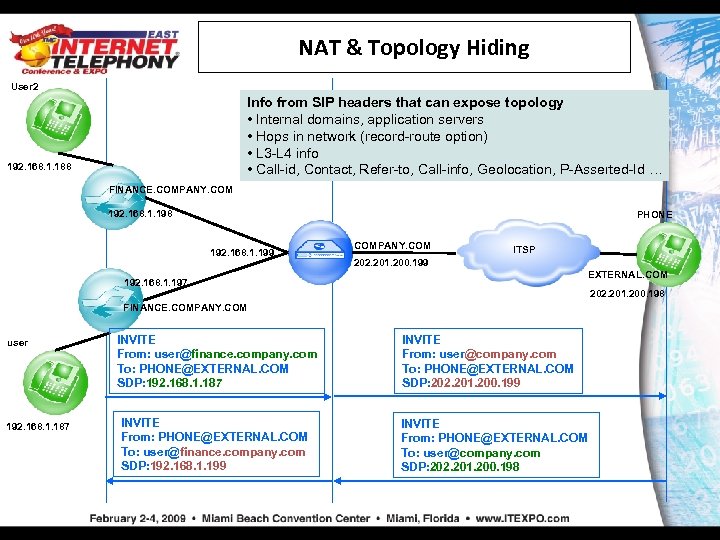 NAT & Topology Hiding User 2 Info from SIP headers that can expose topology • Internal domains, application servers • Hops in network (record-route option) • L 3 -L 4 info • Call-id, Contact, Refer-to, Call-info, Geolocation, P-Asserted-Id … 192. 168. 1. 188 FINANCE. COMPANY. COM 192. 168. 1. 198 PHONE 192. 168. 1. 199 COMPANY. COM ITSP 202. 201. 200. 199 EXTERNAL. COM 192. 168. 1. 197 202. 201. 200. 198 FINANCE. COMPANY. COM user 192. 168. 1. 187 INVITE From: user@finance. company. com To: PHONE@EXTERNAL. COM SDP: 192. 168. 1. 187 INVITE From: PHONE@EXTERNAL. COM To: user@finance. company. com SDP: 192. 168. 1. 199 INVITE From: user@company. com To: PHONE@EXTERNAL. COM SDP: 202. 201. 200. 199 INVITE From: PHONE@EXTERNAL. COM To: user@company. com SDP: 202. 201. 200. 198
NAT & Topology Hiding User 2 Info from SIP headers that can expose topology • Internal domains, application servers • Hops in network (record-route option) • L 3 -L 4 info • Call-id, Contact, Refer-to, Call-info, Geolocation, P-Asserted-Id … 192. 168. 1. 188 FINANCE. COMPANY. COM 192. 168. 1. 198 PHONE 192. 168. 1. 199 COMPANY. COM ITSP 202. 201. 200. 199 EXTERNAL. COM 192. 168. 1. 197 202. 201. 200. 198 FINANCE. COMPANY. COM user 192. 168. 1. 187 INVITE From: user@finance. company. com To: PHONE@EXTERNAL. COM SDP: 192. 168. 1. 187 INVITE From: PHONE@EXTERNAL. COM To: user@finance. company. com SDP: 192. 168. 1. 199 INVITE From: user@company. com To: PHONE@EXTERNAL. COM SDP: 202. 201. 200. 199 INVITE From: PHONE@EXTERNAL. COM To: user@company. com SDP: 202. 201. 200. 198
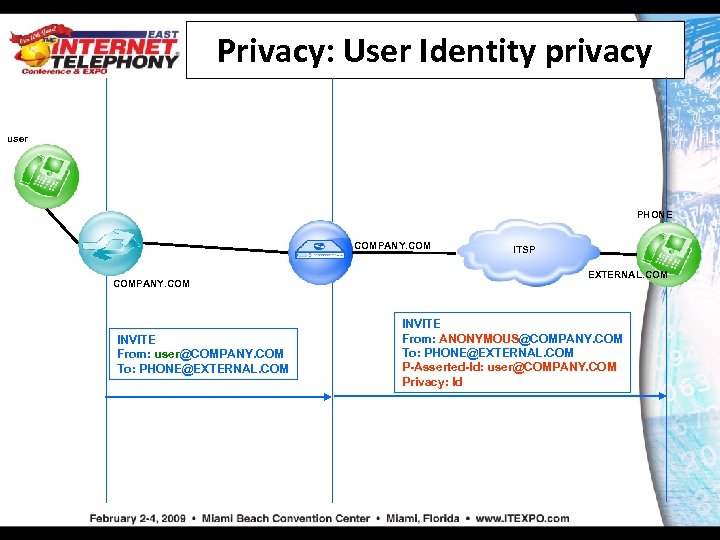 Privacy: User Identity privacy user PHONE COMPANY. COM INVITE From: user@COMPANY. COM To: PHONE@EXTERNAL. COM ITSP EXTERNAL. COM INVITE From: ANONYMOUS@COMPANY. COM To: PHONE@EXTERNAL. COM P-Asserted-Id: user@COMPANY. COM Privacy: Id
Privacy: User Identity privacy user PHONE COMPANY. COM INVITE From: user@COMPANY. COM To: PHONE@EXTERNAL. COM ITSP EXTERNAL. COM INVITE From: ANONYMOUS@COMPANY. COM To: PHONE@EXTERNAL. COM P-Asserted-Id: user@COMPANY. COM Privacy: Id
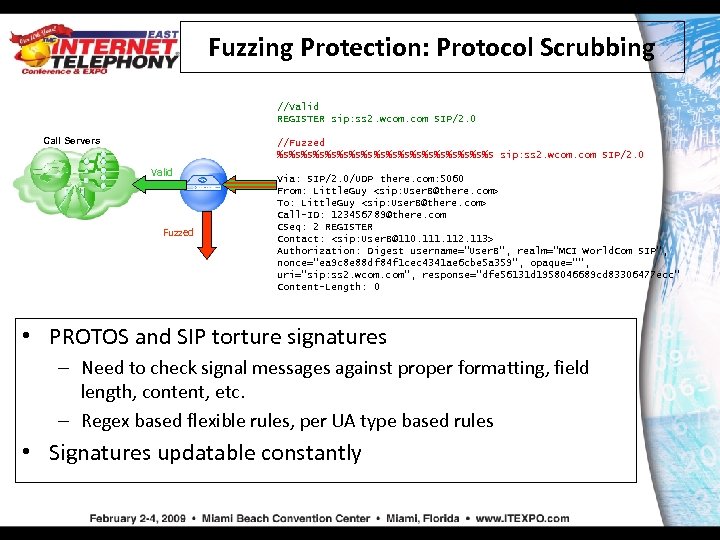 Fuzzing Protection: Protocol Scrubbing //Valid REGISTER sip: ss 2. wcom. com SIP/2. 0 Call Servers //Fuzzed %S%S%S%S%S%S%S%S%S sip: ss 2. wcom. com SIP/2. 0 Valid Fuzzed Via: SIP/2. 0/UDP there. com: 5060 From: Little. Guy
Fuzzing Protection: Protocol Scrubbing //Valid REGISTER sip: ss 2. wcom. com SIP/2. 0 Call Servers //Fuzzed %S%S%S%S%S%S%S%S%S sip: ss 2. wcom. com SIP/2. 0 Valid Fuzzed Via: SIP/2. 0/UDP there. com: 5060 From: Little. Guy
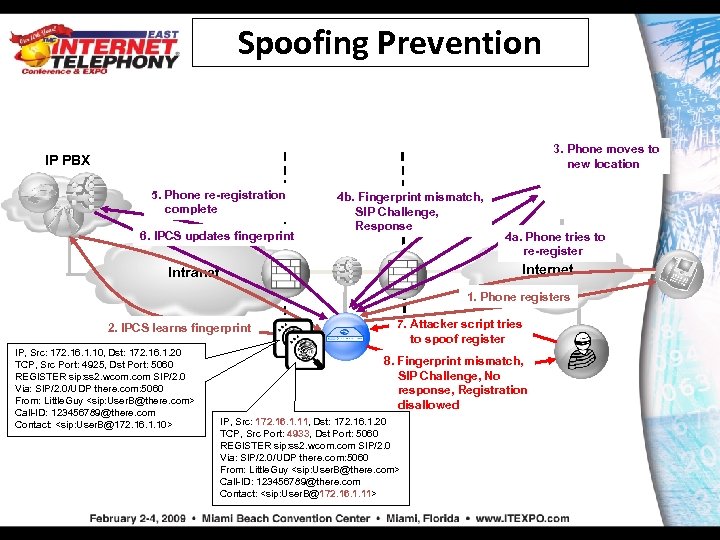 Spoofing Prevention 3. Phone moves to new location IP PBX 5. Phone re-registration complete 6. IPCS updates fingerprint 4 b. Fingerprint mismatch, SIP Challenge, Response 4 a. Phone tries to re-register Internet Intranet 1. Phone registers 2. IPCS learns fingerprint IP, Src: 172. 16. 1. 10, Dst: 172. 16. 1. 20 TCP, Src Port: 4925, Dst Port: 5060 REGISTER sip: ss 2. wcom. com SIP/2. 0 Via: SIP/2. 0/UDP there. com: 5060 From: Little. Guy
Spoofing Prevention 3. Phone moves to new location IP PBX 5. Phone re-registration complete 6. IPCS updates fingerprint 4 b. Fingerprint mismatch, SIP Challenge, Response 4 a. Phone tries to re-register Internet Intranet 1. Phone registers 2. IPCS learns fingerprint IP, Src: 172. 16. 1. 10, Dst: 172. 16. 1. 20 TCP, Src Port: 4925, Dst Port: 5060 REGISTER sip: ss 2. wcom. com SIP/2. 0 Via: SIP/2. 0/UDP there. com: 5060 From: Little. Guy
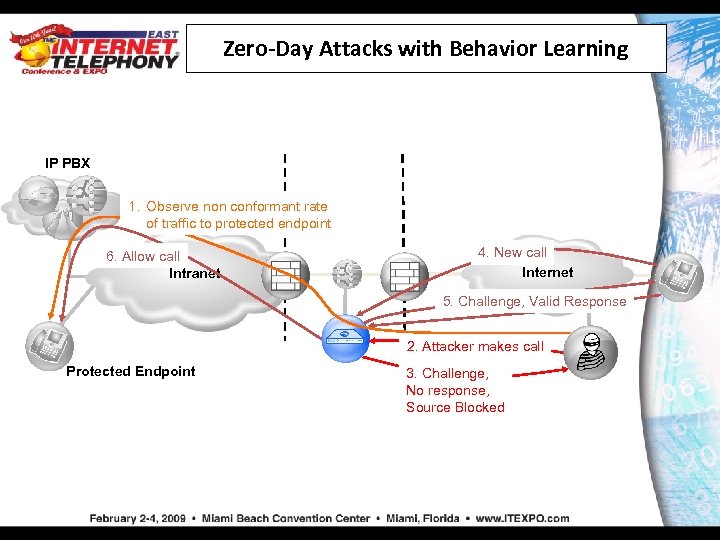 Zero-Day Attacks with Behavior Learning IP PBX 1. Observe non conformant rate of traffic to protected endpoint 6. Allow call Intranet 4. New call Internet 5. Challenge, Valid Response 2. Attacker makes call Protected Endpoint 3. Challenge, No response, Source Blocked
Zero-Day Attacks with Behavior Learning IP PBX 1. Observe non conformant rate of traffic to protected endpoint 6. Allow call Intranet 4. New call Internet 5. Challenge, Valid Response 2. Attacker makes call Protected Endpoint 3. Challenge, No response, Source Blocked
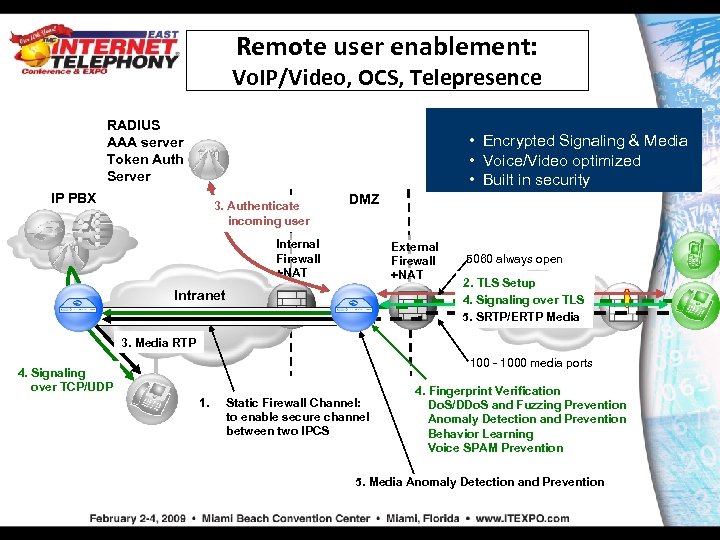 Remote user enablement: Vo. IP/Video, OCS, Telepresence RADIUS AAA server Token Auth Server • Encrypted Signaling & Media • Voice/Video optimized • Built in security IP PBX 3. Authenticate incoming user DMZ Internal Firewall +NAT External Firewall +NAT Intranet 5060 always open 2. TLS Setup Internet 4. Signaling over TLS 5. SRTP/ERTP Media 3. Media RTP 100 - 1000 media ports 4. Signaling over TCP/UDP 1. Static Firewall Channel: to enable secure channel between two IPCS 4. Fingerprint Verification Do. S/DDo. S and Fuzzing Prevention Anomaly Detection and Prevention Behavior Learning Voice SPAM Prevention 5. Media Anomaly Detection and Prevention
Remote user enablement: Vo. IP/Video, OCS, Telepresence RADIUS AAA server Token Auth Server • Encrypted Signaling & Media • Voice/Video optimized • Built in security IP PBX 3. Authenticate incoming user DMZ Internal Firewall +NAT External Firewall +NAT Intranet 5060 always open 2. TLS Setup Internet 4. Signaling over TLS 5. SRTP/ERTP Media 3. Media RTP 100 - 1000 media ports 4. Signaling over TCP/UDP 1. Static Firewall Channel: to enable secure channel between two IPCS 4. Fingerprint Verification Do. S/DDo. S and Fuzzing Prevention Anomaly Detection and Prevention Behavior Learning Voice SPAM Prevention 5. Media Anomaly Detection and Prevention
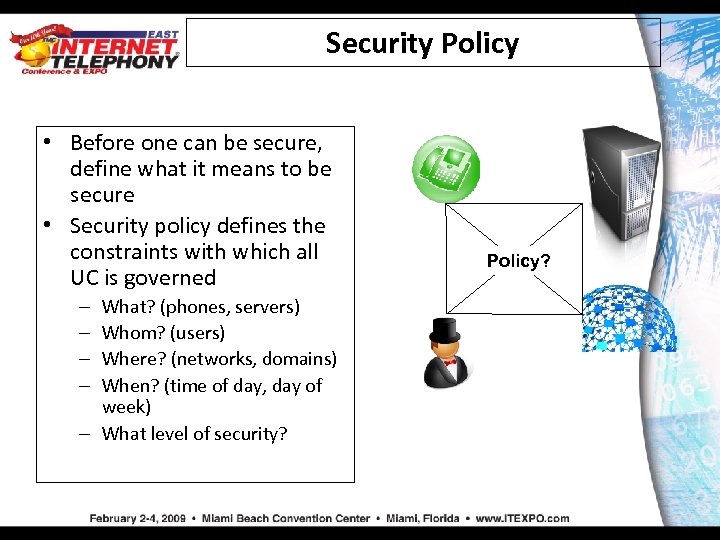 Security Policy • Before one can be secure, define what it means to be secure • Security policy defines the constraints with which all UC is governed What? (phones, servers) Whom? (users) Where? (networks, domains) When? (time of day, day of week) – What level of security? – – Policy?
Security Policy • Before one can be secure, define what it means to be secure • Security policy defines the constraints with which all UC is governed What? (phones, servers) Whom? (users) Where? (networks, domains) When? (time of day, day of week) – What level of security? – – Policy?
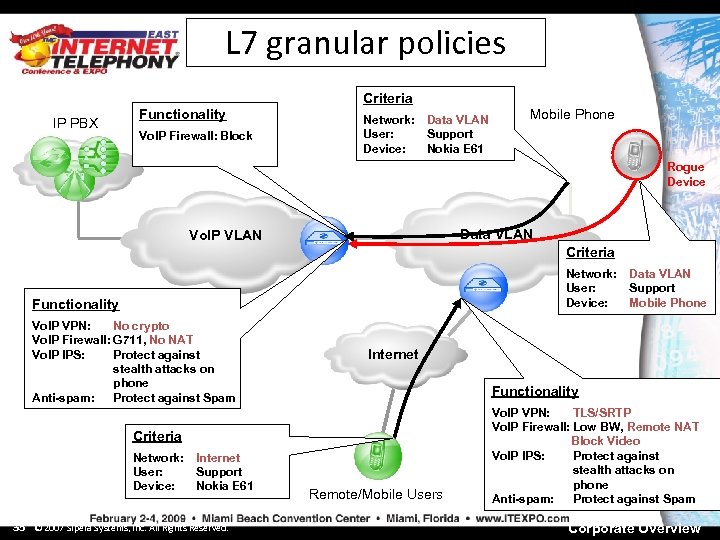 L 7 granular policies Criteria IP PBX Functionality Vo. IP Firewall: Block Network: User: Device: Data VLAN Support Nokia E 61 Mobile Phone Rogue Device Data VLAN Vo. IP VLAN Criteria Network: User: Device: Functionality Vo. IP VPN: No crypto Vo. IP Firewall: G 711, No NAT Vo. IP IPS: Protect against stealth attacks on phone Anti-spam: Protect against Spam Internet Functionality Criteria Network: User: Device: Internet Support Nokia E 61 35 © 2007 Sipera Systems, Inc. All Rights Reserved. Data VLAN Support Mobile Phone Remote/Mobile Users Vo. IP VPN: TLS/SRTP Vo. IP Firewall: Low BW, Remote NAT Block Video Vo. IP IPS: Protect against stealth attacks on phone Anti-spam: Protect against Spam Corporate Overview
L 7 granular policies Criteria IP PBX Functionality Vo. IP Firewall: Block Network: User: Device: Data VLAN Support Nokia E 61 Mobile Phone Rogue Device Data VLAN Vo. IP VLAN Criteria Network: User: Device: Functionality Vo. IP VPN: No crypto Vo. IP Firewall: G 711, No NAT Vo. IP IPS: Protect against stealth attacks on phone Anti-spam: Protect against Spam Internet Functionality Criteria Network: User: Device: Internet Support Nokia E 61 35 © 2007 Sipera Systems, Inc. All Rights Reserved. Data VLAN Support Mobile Phone Remote/Mobile Users Vo. IP VPN: TLS/SRTP Vo. IP Firewall: Low BW, Remote NAT Block Video Vo. IP IPS: Protect against stealth attacks on phone Anti-spam: Protect against Spam Corporate Overview
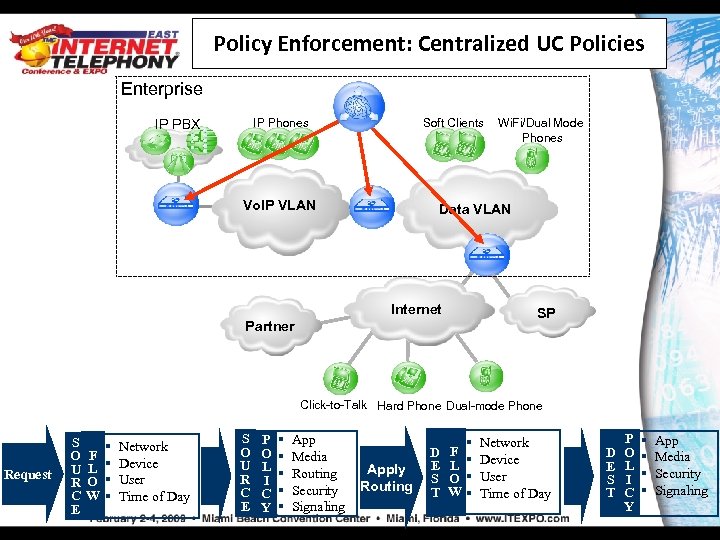 Policy Enforcement: Centralized UC Policies Enterprise IP PBX IP Phones Soft Clients Vo. IP VLAN Wi. Fi/Dual Mode Phones Data VLAN Internet SP Partner Click-to-Talk Hard Phone Dual-mode Phone Request S O U R C E F L O W § § Network Device User Time of Day S O U R C E P O L I C Y § § § App Media Routing Security Signaling Apply Routing D E S T § F L § O § W§ Network Device User Time of Day D E S T P O L I C Y § § App Media Security Signaling
Policy Enforcement: Centralized UC Policies Enterprise IP PBX IP Phones Soft Clients Vo. IP VLAN Wi. Fi/Dual Mode Phones Data VLAN Internet SP Partner Click-to-Talk Hard Phone Dual-mode Phone Request S O U R C E F L O W § § Network Device User Time of Day S O U R C E P O L I C Y § § § App Media Routing Security Signaling Apply Routing D E S T § F L § O § W§ Network Device User Time of Day D E S T P O L I C Y § § App Media Security Signaling
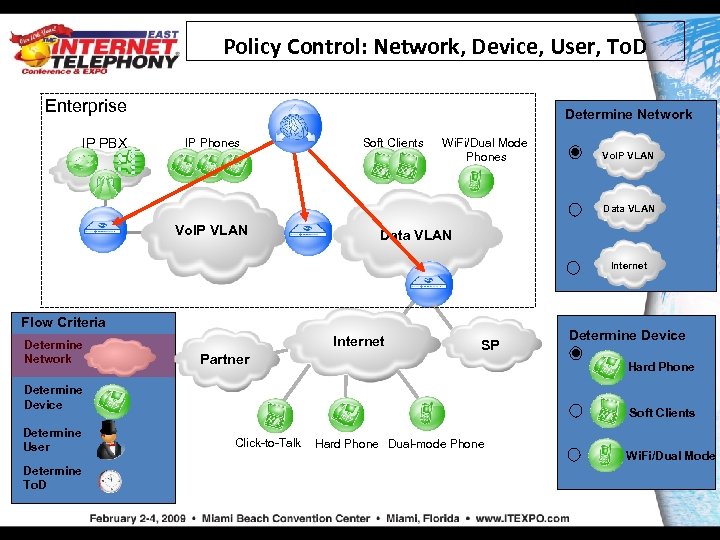 Policy Control: Network, Device, User, To. D Enterprise IP PBX Determine Network IP Phones Soft Clients Wi. Fi/Dual Mode Phones Vo. IP VLAN Data VLAN Internet Flow Criteria Determine Network Internet Partner SP Hard Phone Determine Device Determine User Determine To. D Determine Device Soft Clients Click-to-Talk Hard Phone Dual-mode Phone Wi. Fi/Dual Mode
Policy Control: Network, Device, User, To. D Enterprise IP PBX Determine Network IP Phones Soft Clients Wi. Fi/Dual Mode Phones Vo. IP VLAN Data VLAN Internet Flow Criteria Determine Network Internet Partner SP Hard Phone Determine Device Determine User Determine To. D Determine Device Soft Clients Click-to-Talk Hard Phone Dual-mode Phone Wi. Fi/Dual Mode
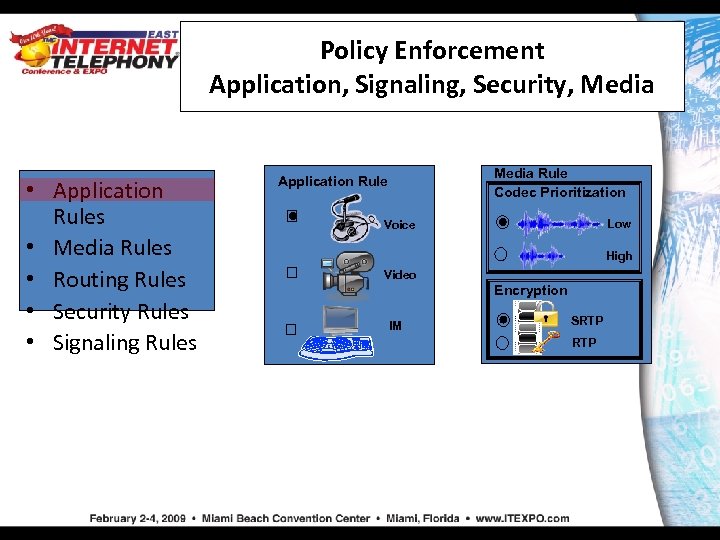 Policy Enforcement Application, Signaling, Security, Media • Application Rules • Media Rules • Routing Rules • Security Rules • Signaling Rules Media Rule Codec Prioritization Application Rule Low Voice High Video Encryption IM SRTP
Policy Enforcement Application, Signaling, Security, Media • Application Rules • Media Rules • Routing Rules • Security Rules • Signaling Rules Media Rule Codec Prioritization Application Rule Low Voice High Video Encryption IM SRTP
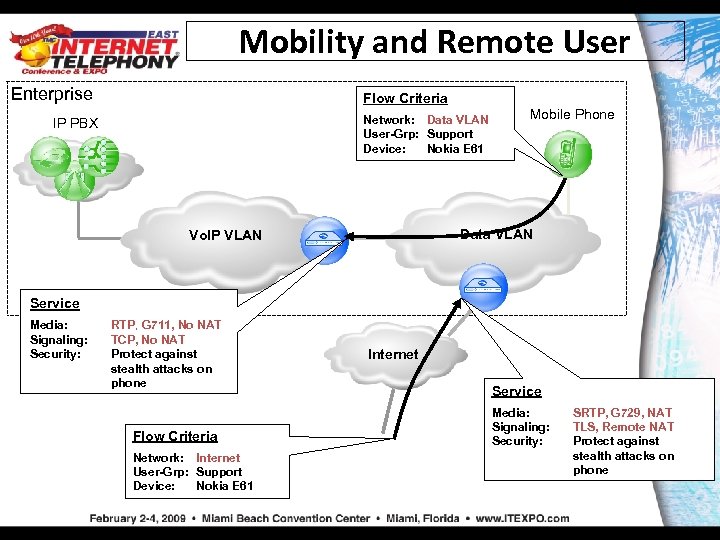 Mobility and Remote User Enterprise Flow Criteria Network: Data VLAN User-Grp: Support Device: Nokia E 61 IP PBX Mobile Phone Data VLAN Vo. IP VLAN Service Media: Signaling: Security: RTP, G 711, No NAT TCP, No NAT Protect against stealth attacks on phone Flow Criteria Network: Internet User-Grp: Support Device: Nokia E 61 Internet Service Media: Signaling: Security: SRTP, G 729, NAT TLS, Remote NAT Protect against stealth attacks on phone
Mobility and Remote User Enterprise Flow Criteria Network: Data VLAN User-Grp: Support Device: Nokia E 61 IP PBX Mobile Phone Data VLAN Vo. IP VLAN Service Media: Signaling: Security: RTP, G 711, No NAT TCP, No NAT Protect against stealth attacks on phone Flow Criteria Network: Internet User-Grp: Support Device: Nokia E 61 Internet Service Media: Signaling: Security: SRTP, G 729, NAT TLS, Remote NAT Protect against stealth attacks on phone
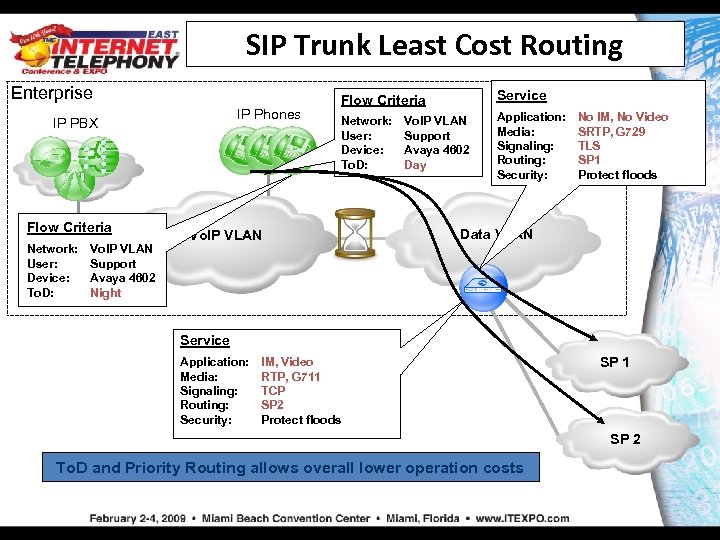 SIP Trunk Least Cost Routing Enterprise IP Phones IP PBX Flow Criteria Network: User: Device: To. D: Vo. IP VLAN Support Avaya 4602 Night Flow Criteria Service Network: User: Device: To. D: Application: Media: Signaling: Routing: Security: Vo. IP VLAN Support Avaya 4602 Day No IM, No Video SRTP, G 729 TLS SP 1 Protect floods Data VLAN Service Application: Media: Signaling: Routing: Security: IM, Video RTP, G 711 TCP SP 2 Protect floods SP 1 SP 2 To. D and Priority Routing allows overall lower operation costs
SIP Trunk Least Cost Routing Enterprise IP Phones IP PBX Flow Criteria Network: User: Device: To. D: Vo. IP VLAN Support Avaya 4602 Night Flow Criteria Service Network: User: Device: To. D: Application: Media: Signaling: Routing: Security: Vo. IP VLAN Support Avaya 4602 Day No IM, No Video SRTP, G 729 TLS SP 1 Protect floods Data VLAN Service Application: Media: Signaling: Routing: Security: IM, Video RTP, G 711 TCP SP 2 Protect floods SP 1 SP 2 To. D and Priority Routing allows overall lower operation costs
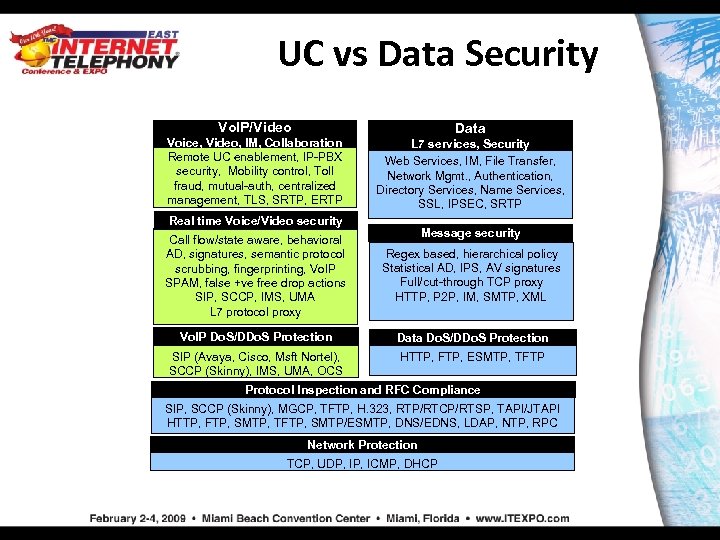 UC vs Data Security Vo. IP/Video Voice, Video, IM, Collaboration Remote UC enablement, IP-PBX security, Mobility control, Toll fraud, mutual-auth, centralized management, TLS, SRTP, ERTP Data L 7 services, Security Web Services, IM, File Transfer, Network Mgmt. , Authentication, Directory Services, Name Services, SSL, IPSEC, SRTP Real time Voice/Video security Message security Call flow/state aware, behavioral AD, signatures, semantic protocol scrubbing, fingerprinting, Vo. IP SPAM, false +ve free drop actions SIP, SCCP, IMS, UMA L 7 protocol proxy Regex based, hierarchical policy Statistical AD, IPS, AV signatures Full/cut-through TCP proxy HTTP, P 2 P, IM, SMTP, XML Vo. IP Do. S/DDo. S Protection Data Do. S/DDo. S Protection SIP (Avaya, Cisco, Msft Nortel), SCCP (Skinny), IMS, UMA, OCS HTTP, FTP, ESMTP, TFTP Protocol Inspection and RFC Compliance SIP, SCCP (Skinny), MGCP, TFTP, H. 323, RTP/RTCP/RTSP, TAPI/JTAPI HTTP, FTP, SMTP, TFTP, SMTP/ESMTP, DNS/EDNS, LDAP, NTP, RPC Network Protection TCP, UDP, ICMP, DHCP
UC vs Data Security Vo. IP/Video Voice, Video, IM, Collaboration Remote UC enablement, IP-PBX security, Mobility control, Toll fraud, mutual-auth, centralized management, TLS, SRTP, ERTP Data L 7 services, Security Web Services, IM, File Transfer, Network Mgmt. , Authentication, Directory Services, Name Services, SSL, IPSEC, SRTP Real time Voice/Video security Message security Call flow/state aware, behavioral AD, signatures, semantic protocol scrubbing, fingerprinting, Vo. IP SPAM, false +ve free drop actions SIP, SCCP, IMS, UMA L 7 protocol proxy Regex based, hierarchical policy Statistical AD, IPS, AV signatures Full/cut-through TCP proxy HTTP, P 2 P, IM, SMTP, XML Vo. IP Do. S/DDo. S Protection Data Do. S/DDo. S Protection SIP (Avaya, Cisco, Msft Nortel), SCCP (Skinny), IMS, UMA, OCS HTTP, FTP, ESMTP, TFTP Protocol Inspection and RFC Compliance SIP, SCCP (Skinny), MGCP, TFTP, H. 323, RTP/RTCP/RTSP, TAPI/JTAPI HTTP, FTP, SMTP, TFTP, SMTP/ESMTP, DNS/EDNS, LDAP, NTP, RPC Network Protection TCP, UDP, ICMP, DHCP
 THANK YOU!! Ravi Varanasi Vice President, Engineering Sipera Systems. ravi@sipera. com 214 -269 -2437.
THANK YOU!! Ravi Varanasi Vice President, Engineering Sipera Systems. ravi@sipera. com 214 -269 -2437.


