ad0454f81c90dc5496bc13263028466f.ppt
- Количество слайдов: 14
 Securing the Private Key - Crypto. Modules Ruchin Kumar Principal Solution Architect – India and SAARC Safe. Net Inc. ruchin. kumar@safenet-inc. com
Securing the Private Key - Crypto. Modules Ruchin Kumar Principal Solution Architect – India and SAARC Safe. Net Inc. ruchin. kumar@safenet-inc. com
 Security Requirements today § § § § Data Integrity Non Repudiation Confidentiality Non Duplication Strong Authentication Security without impacting performance Centralized and distributed key management Compliance to the IT ACT 2000/2008
Security Requirements today § § § § Data Integrity Non Repudiation Confidentiality Non Duplication Strong Authentication Security without impacting performance Centralized and distributed key management Compliance to the IT ACT 2000/2008
 Benefits of Public Key Cryptography Entity Authentication – Validates the identity of machines and users. Data Confidentiality – Encodes data to ensure that data cannot be viewed by unauthorized users or machines. § Data Integrity – Protect data to ensure that data cannot be alter by unauthorized users or machines. § Digital Signature – Provides the electronic equivalent of a hand-written signature § Non Repudiation – Ensures that communications, data exchanges, and transactions are legally valid and irrevocable. § § Not other security technologies or standards available today can provide the same level of benefits as PKI.
Benefits of Public Key Cryptography Entity Authentication – Validates the identity of machines and users. Data Confidentiality – Encodes data to ensure that data cannot be viewed by unauthorized users or machines. § Data Integrity – Protect data to ensure that data cannot be alter by unauthorized users or machines. § Digital Signature – Provides the electronic equivalent of a hand-written signature § Non Repudiation – Ensures that communications, data exchanges, and transactions are legally valid and irrevocable. § § Not other security technologies or standards available today can provide the same level of benefits as PKI.
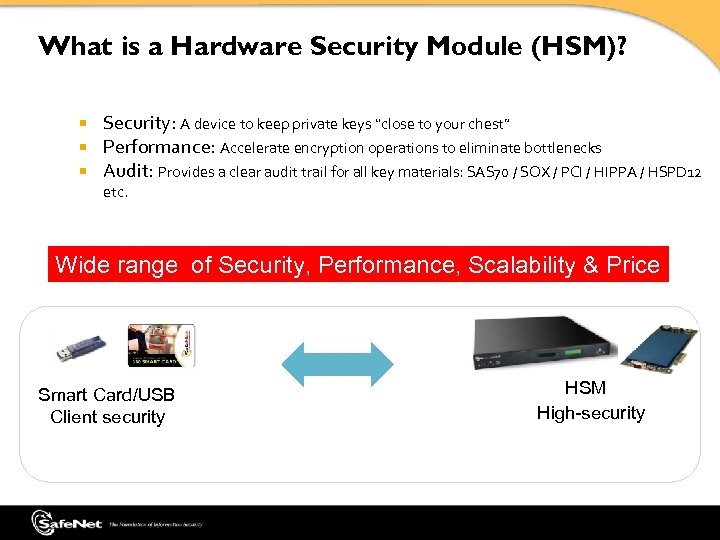 What is a Hardware Security Module (HSM)? Security: A device to keep private keys “close to your chest” Performance: Accelerate encryption operations to eliminate bottlenecks Audit: Provides a clear audit trail for all key materials: SAS 70 / SOX / PCI / HIPPA / HSPD 12 etc. Wide range of Security, Performance, Scalability & Price Smart Card/USB Client security HSM High-security
What is a Hardware Security Module (HSM)? Security: A device to keep private keys “close to your chest” Performance: Accelerate encryption operations to eliminate bottlenecks Audit: Provides a clear audit trail for all key materials: SAS 70 / SOX / PCI / HIPPA / HSPD 12 etc. Wide range of Security, Performance, Scalability & Price Smart Card/USB Client security HSM High-security
 Junior Crypto. Modules “Anywhere “- Don’t need the drivers USB Smartcard Hybrid USB Smartcard & OTP Smartcard Hybrid USB Smartcard & Flash Virtual Token
Junior Crypto. Modules “Anywhere “- Don’t need the drivers USB Smartcard Hybrid USB Smartcard & OTP Smartcard Hybrid USB Smartcard & Flash Virtual Token
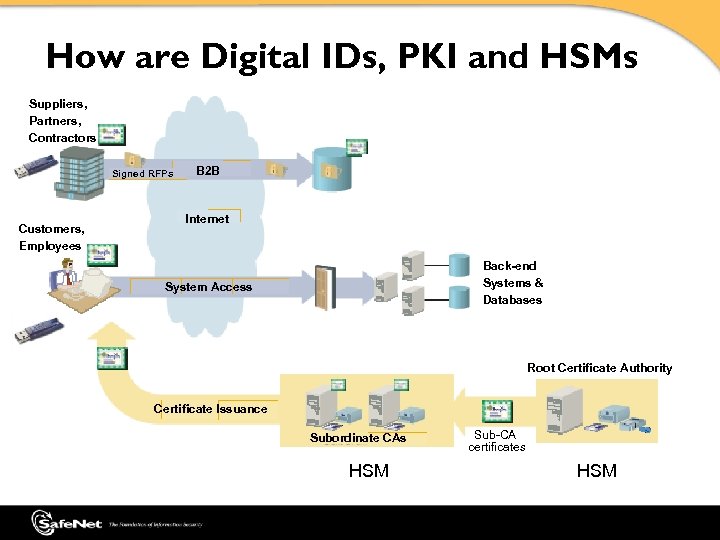 How are Digital IDs, PKI and HSMs Used? Suppliers, Partners, Contractors Signed RFPs Customers, Employees B 2 B Internet Back-end Systems & Databases System Access Root Certificate Authority Certificate Issuance Subordinate CAs HSM Sub-CA certificates HSM
How are Digital IDs, PKI and HSMs Used? Suppliers, Partners, Contractors Signed RFPs Customers, Employees B 2 B Internet Back-end Systems & Databases System Access Root Certificate Authority Certificate Issuance Subordinate CAs HSM Sub-CA certificates HSM
 Benefits of H/W Crypto Module Key Generation of all private keys in hardware Key Storage of private keys 100% of the time in hardware Certificate Signing performed on hardware Key Backup in controlled hardware 100% of the time Trusted Path used to enter critical security parameters Recognized validation from FIPS 140 -2 or Common Criteria Why hardware and not software? Software implementation has weak memory protection, weak integrity protection, no protection against reverse engineering, no secure key storage, subject to operating system vulnerability… Will any hardware be enough? Need FIPS 140 validated security hardware such as hardware security module
Benefits of H/W Crypto Module Key Generation of all private keys in hardware Key Storage of private keys 100% of the time in hardware Certificate Signing performed on hardware Key Backup in controlled hardware 100% of the time Trusted Path used to enter critical security parameters Recognized validation from FIPS 140 -2 or Common Criteria Why hardware and not software? Software implementation has weak memory protection, weak integrity protection, no protection against reverse engineering, no secure key storage, subject to operating system vulnerability… Will any hardware be enough? Need FIPS 140 validated security hardware such as hardware security module
 Toolkits 3 rd Party or Customer Developed Host Application PKCS#11, Java, CAPI, Open. SSL, Custom, XML WSDL, Payments API’s Windows, Solaris, Linux, HP UX, AIX, Solaris Networked to single or multiple SSM smart card Write your own applications and load them directly onto the device
Toolkits 3 rd Party or Customer Developed Host Application PKCS#11, Java, CAPI, Open. SSL, Custom, XML WSDL, Payments API’s Windows, Solaris, Linux, HP UX, AIX, Solaris Networked to single or multiple SSM smart card Write your own applications and load them directly onto the device
 Large Deployments - RTGS § § § § Fastest possible money transfer system Financial messages are signed and encrypted between PI and RTGS server Huge volumes – HSM is securing the keys as well as providing acceleration to PKI processes. Audit Trails Machine authentication before transaction is initiated Multiple sites for DR M x N Authentication for stronger controls PKI supported by HSM has been instrumental in making it a reality
Large Deployments - RTGS § § § § Fastest possible money transfer system Financial messages are signed and encrypted between PI and RTGS server Huge volumes – HSM is securing the keys as well as providing acceleration to PKI processes. Audit Trails Machine authentication before transaction is initiated Multiple sites for DR M x N Authentication for stronger controls PKI supported by HSM has been instrumental in making it a reality
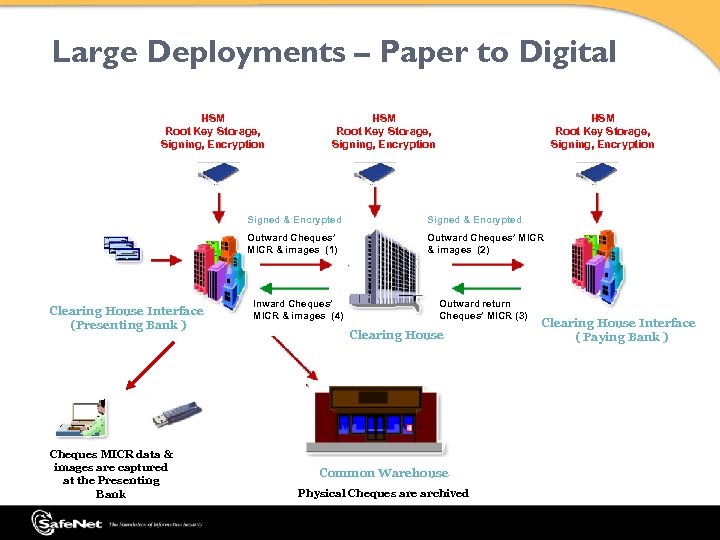 Large Deployments – Paper to Digital HSM Root Key Storage, Signing, Encryption Signed & Encrypted Outward Cheques’ MICR & images (1) Clearing House Interface (Presenting Bank ) Cheques MICR data & images are captured at the Presenting Bank Signed & Encrypted Outward Cheques’ MICR & images (2) Inward Cheques’ MICR & images (4) Outward return Cheques’ MICR (3) Clearing House Common Warehouse Physical Cheques are archived Clearing House Interface ( Paying Bank )
Large Deployments – Paper to Digital HSM Root Key Storage, Signing, Encryption Signed & Encrypted Outward Cheques’ MICR & images (1) Clearing House Interface (Presenting Bank ) Cheques MICR data & images are captured at the Presenting Bank Signed & Encrypted Outward Cheques’ MICR & images (2) Inward Cheques’ MICR & images (4) Outward return Cheques’ MICR (3) Clearing House Common Warehouse Physical Cheques are archived Clearing House Interface ( Paying Bank )
 New Avenues – HSM Supported PKI § DNSSEC § e – Invoicing § Secure Manufacturing § e - Governance Projects § Mobile Transactions Security List goes on ………………. .
New Avenues – HSM Supported PKI § DNSSEC § e – Invoicing § Secure Manufacturing § e - Governance Projects § Mobile Transactions Security List goes on ………………. .
 What to look for in an HSM? § § § § § Certified by Standard Bodies Performance Level of security Auditability Ease of integration Ease of management Flexibility in use Scalability (multiple partitions) High Availability & Disaster Recovery Keys in always in hardware
What to look for in an HSM? § § § § § Certified by Standard Bodies Performance Level of security Auditability Ease of integration Ease of management Flexibility in use Scalability (multiple partitions) High Availability & Disaster Recovery Keys in always in hardware
 Best Practices for Hardware Security Modules 1. Hardware-secured key generation ü ü ü 2. Hardware-secured key storage 3. Hardware-secured key backup ü ü Hardware-secured digital signing ü PKI authenticated software 4. 5. 6. Controlled physical access 7. Host independent 2 factor authentication 8. Enforced operational roles ü 9. Independent Audit ü 10. FIPS 140 -1 & Common Criteria validation
Best Practices for Hardware Security Modules 1. Hardware-secured key generation ü ü ü 2. Hardware-secured key storage 3. Hardware-secured key backup ü ü Hardware-secured digital signing ü PKI authenticated software 4. 5. 6. Controlled physical access 7. Host independent 2 factor authentication 8. Enforced operational roles ü 9. Independent Audit ü 10. FIPS 140 -1 & Common Criteria validation
 Q&A
Q&A


