fffadea3372f35e245b3ce20ee2e368f.ppt
- Количество слайдов: 13

 Securing Open Source Enterprise Vo. IP Christian Stredicke/snom
Securing Open Source Enterprise Vo. IP Christian Stredicke/snom
 SIP is the ketchup of the burger September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California The Past: Everything is provided (more or less) by one large company Problem: Products are getting very complex and it is hard to stay competitive The Future: Specialized vendors offering excellent products in a specific area ITSP IVR SIP PBX Soft Phones Hosting Consulting ATA Hard Phones SBC Finally the Vo. IP industry is splitting up into layers: SIP is the ketchup that makes it a tasty combination 3 www. ITEXPO. com
SIP is the ketchup of the burger September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California The Past: Everything is provided (more or less) by one large company Problem: Products are getting very complex and it is hard to stay competitive The Future: Specialized vendors offering excellent products in a specific area ITSP IVR SIP PBX Soft Phones Hosting Consulting ATA Hard Phones SBC Finally the Vo. IP industry is splitting up into layers: SIP is the ketchup that makes it a tasty combination 3 www. ITEXPO. com
 Selling Security September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • There is probably no company without firewall any more – Security for Email and Web is a must have today – Administrators who don‘t understand that are jobless • Offer two contracts – One where you make the customer responsible for all security breaks (system without security) – Another one where they just waive your liability (system with security) • They will pick the contract that includes security 4 www. ITEXPO. com
Selling Security September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • There is probably no company without firewall any more – Security for Email and Web is a must have today – Administrators who don‘t understand that are jobless • Offer two contracts – One where you make the customer responsible for all security breaks (system without security) – Another one where they just waive your liability (system with security) • They will pick the contract that includes security 4 www. ITEXPO. com
 The Evolution of Vo. IP Privacy September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California “We got transfer working” Use SRTP (but no TLS) TLS + SRTP VPN 5 www. ITEXPO. com
The Evolution of Vo. IP Privacy September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California “We got transfer working” Use SRTP (but no TLS) TLS + SRTP VPN 5 www. ITEXPO. com
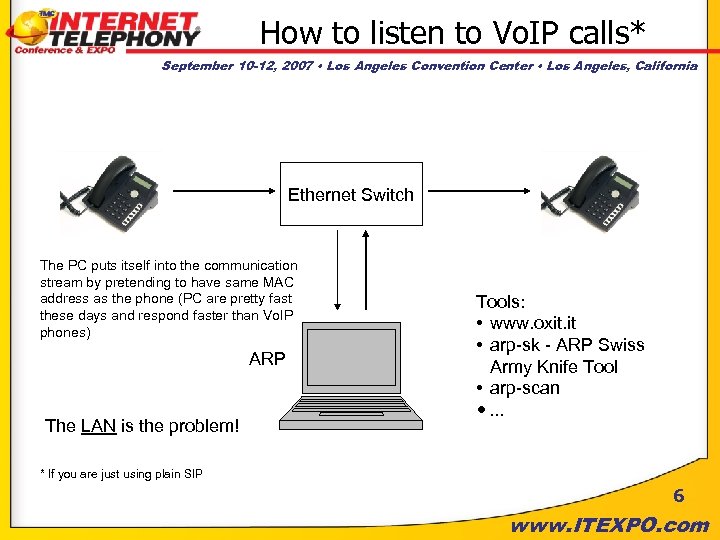 How to listen to Vo. IP calls* September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California Ethernet Switch The PC puts itself into the communication stream by pretending to have same MAC address as the phone (PC are pretty fast these days and respond faster than Vo. IP phones) ARP The LAN is the problem! Tools: • www. oxit. it • arp-sk - ARP Swiss Army Knife Tool • arp-scan • … * If you are just using plain SIP 6 www. ITEXPO. com
How to listen to Vo. IP calls* September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California Ethernet Switch The PC puts itself into the communication stream by pretending to have same MAC address as the phone (PC are pretty fast these days and respond faster than Vo. IP phones) ARP The LAN is the problem! Tools: • www. oxit. it • arp-sk - ARP Swiss Army Knife Tool • arp-scan • … * If you are just using plain SIP 6 www. ITEXPO. com
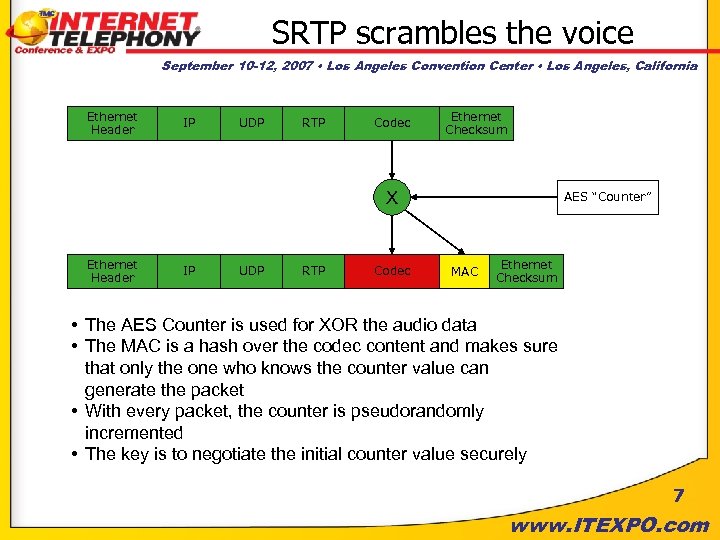 SRTP scrambles the voice September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California Ethernet Header IP UDP RTP Codec Ethernet Checksum X Ethernet Header IP UDP RTP Codec AES “Counter” MAC Ethernet Checksum • The AES Counter is used for XOR the audio data • The MAC is a hash over the codec content and makes sure that only the one who knows the counter value can generate the packet • With every packet, the counter is pseudorandomly incremented • The key is to negotiate the initial counter value securely 7 www. ITEXPO. com
SRTP scrambles the voice September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California Ethernet Header IP UDP RTP Codec Ethernet Checksum X Ethernet Header IP UDP RTP Codec AES “Counter” MAC Ethernet Checksum • The AES Counter is used for XOR the audio data • The MAC is a hash over the codec content and makes sure that only the one who knows the counter value can generate the packet • With every packet, the counter is pseudorandomly incremented • The key is to negotiate the initial counter value securely 7 www. ITEXPO. com
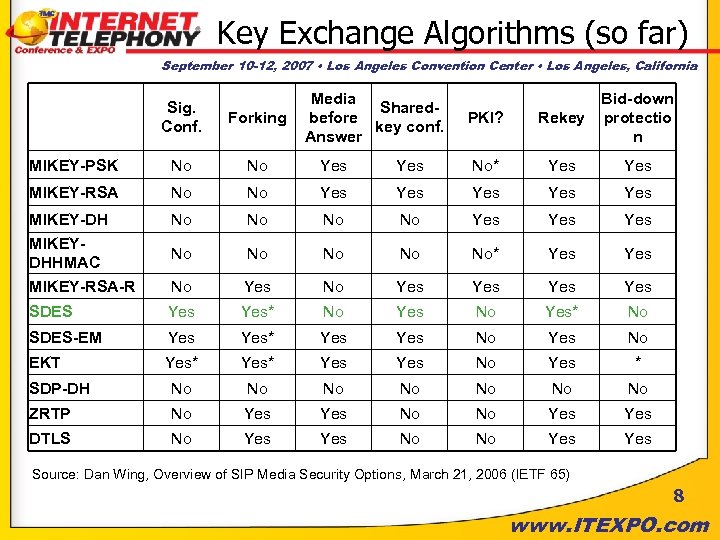 Key Exchange Algorithms (so far) September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California Media Sharedbefore key conf. Answer PKI? Rekey Bid-down protectio n Yes No* Yes Yes No No No Yes Yes No No No* Yes No Yes Yes Yes SDES Yes* No SDES-EM Yes* Yes No EKT Yes* Yes No Yes * SDP-DH No No ZRTP No Yes No No Yes DTLS No Yes No No Yes Sig. Conf. Forking MIKEY-PSK No No Yes MIKEY-RSA No No MIKEY-DH No MIKEYDHHMAC MIKEY-RSA-R Source: Dan Wing, Overview of SIP Media Security Options, March 21, 2006 (IETF 65) 8 www. ITEXPO. com
Key Exchange Algorithms (so far) September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California Media Sharedbefore key conf. Answer PKI? Rekey Bid-down protectio n Yes No* Yes Yes No No No Yes Yes No No No* Yes No Yes Yes Yes SDES Yes* No SDES-EM Yes* Yes No EKT Yes* Yes No Yes * SDP-DH No No ZRTP No Yes No No Yes DTLS No Yes No No Yes Sig. Conf. Forking MIKEY-PSK No No Yes MIKEY-RSA No No MIKEY-DH No MIKEYDHHMAC MIKEY-RSA-R Source: Dan Wing, Overview of SIP Media Security Options, March 21, 2006 (IETF 65) 8 www. ITEXPO. com
 How TLS works September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • • Known from other protocols (https, secure SMTP, …) Looks like TCP from the application point of view Uses strong cryptographical methods (RSA, DH) How can you trust the other side? – Certificates – Must be issued by someone that you trust – Preset list or load the root certificate • Problem: – Requires at the very least TCP support (most PBXs don't have this today) – Problems for embedded devices (Open. SSL takes several MB) 9 www. ITEXPO. com
How TLS works September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • • Known from other protocols (https, secure SMTP, …) Looks like TCP from the application point of view Uses strong cryptographical methods (RSA, DH) How can you trust the other side? – Certificates – Must be issued by someone that you trust – Preset list or load the root certificate • Problem: – Requires at the very least TCP support (most PBXs don't have this today) – Problems for embedded devices (Open. SSL takes several MB) 9 www. ITEXPO. com
 Is VPN the solution? September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • Very well established • Secure • Latest generations address latency – UDP or GRE • Nice side effects: – No more NAT problems – VPN servers are widely available (Open. VPN) – No more port-playing with national carriers • Problems: – Media Relay through the central VPN node – Setup is not as easy as TLS 10 www. ITEXPO. com
Is VPN the solution? September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • Very well established • Secure • Latest generations address latency – UDP or GRE • Nice side effects: – No more NAT problems – VPN servers are widely available (Open. VPN) – No more port-playing with national carriers • Problems: – Media Relay through the central VPN node – Setup is not as easy as TLS 10 www. ITEXPO. com
 Do. S is becoming a pain September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California “If you have Gigabit Ethernet, make sure you can process one million ping packets per second” • Brute force attacks: – ping –f (start is several times) – Downloading of emails (LOL) – Just don‘t hang up (ENUM) • Bad software – INVITE of Death (Do. S LOL) – Accepting INVITE without any kind of authentication 11 www. ITEXPO. com
Do. S is becoming a pain September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California “If you have Gigabit Ethernet, make sure you can process one million ping packets per second” • Brute force attacks: – ping –f (start is several times) – Downloading of emails (LOL) – Just don‘t hang up (ENUM) • Bad software – INVITE of Death (Do. S LOL) – Accepting INVITE without any kind of authentication 11 www. ITEXPO. com
 Simple Steps to Increase Security September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • Put your Vo. IP network into a VLAN – Give higher priority bits for that LAN – Have a mini-SBC between the LANs – Limit bandwidth on trunk level • Set the expectations right – Making phone calls over the public Internet has no Qo. S – Seriously consider PSTN termination • Think about upgrade paths • Backup 12 www. ITEXPO. com
Simple Steps to Increase Security September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • Put your Vo. IP network into a VLAN – Give higher priority bits for that LAN – Have a mini-SBC between the LANs – Limit bandwidth on trunk level • Set the expectations right – Making phone calls over the public Internet has no Qo. S – Seriously consider PSTN termination • Think about upgrade paths • Backup 12 www. ITEXPO. com
 The Bottom Line September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • You must address privacy in the enterprise • TLS and SRTP are a good solution • VPN is even better as is solves NAT as well • Think pessimistic about bandwidth utilization 13 www. ITEXPO. com
The Bottom Line September 10 -12, 2007 • Los Angeles Convention Center • Los Angeles, California • You must address privacy in the enterprise • TLS and SRTP are a good solution • VPN is even better as is solves NAT as well • Think pessimistic about bandwidth utilization 13 www. ITEXPO. com


