1840e8d29f8591a7ab6bbd57f2f53dbe.ppt
- Количество слайдов: 51

Securing Mobile Networks in an Operational Setting Will Ivancic wivancic@grc. nasa. gov (216) 433 -3494 1

Outline n n Security Considerations Neah Bay Project Cost of Connectivity NASA’s Mobile Network Needs 2

Security Considerations 3

Securing Networks n Constraints/Tools n Policy n n n Security Policy Education Enforcement Architecture Protocols Must be done up front to be done well 4
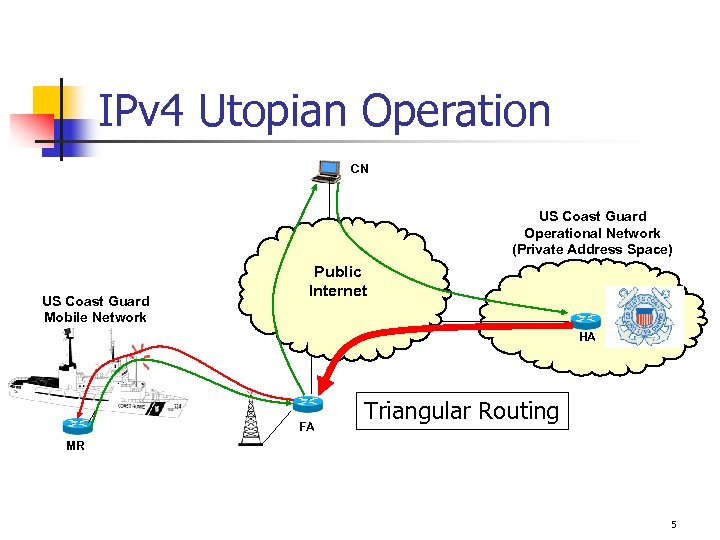
IPv 4 Utopian Operation CN US Coast Guard Operational Network (Private Address Space) US Coast Guard Mobile Network Public Internet HA FA Triangular Routing MR 5
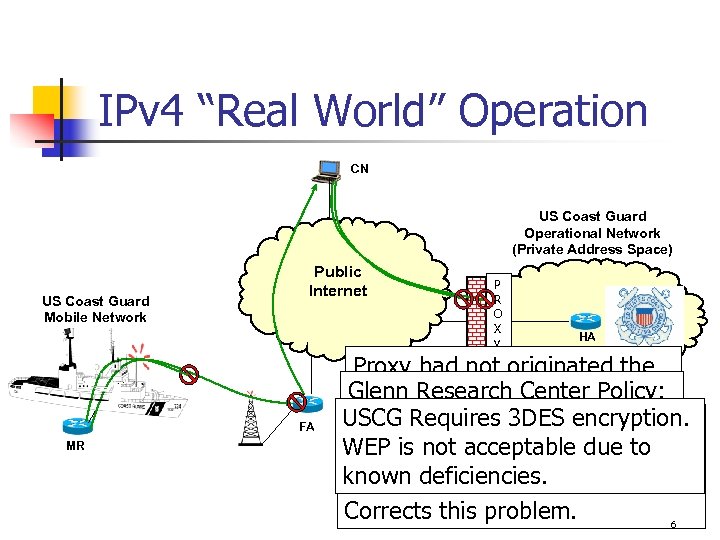
IPv 4 “Real World” Operation CN US Coast Guard Operational Network (Private Address Space) US Coast Guard Mobile Network Public Internet FA MR P R O X y HA Proxy had not originated the Glenn Research Center Policy: request; therefore, the USCG Requires 3 DES encryption. No UDP, No IPSec, etc… stops response Egress Filtering Ingress or is squelched. WEP is notstoppedto topologically Mobile-IP acceptable due to Peer-to-peer networking Transmission due in its tracks. known deficiencies. What’s your policy? at IPv 6 becomes problematic Incorrect source address. best. Corrects this problem. 6
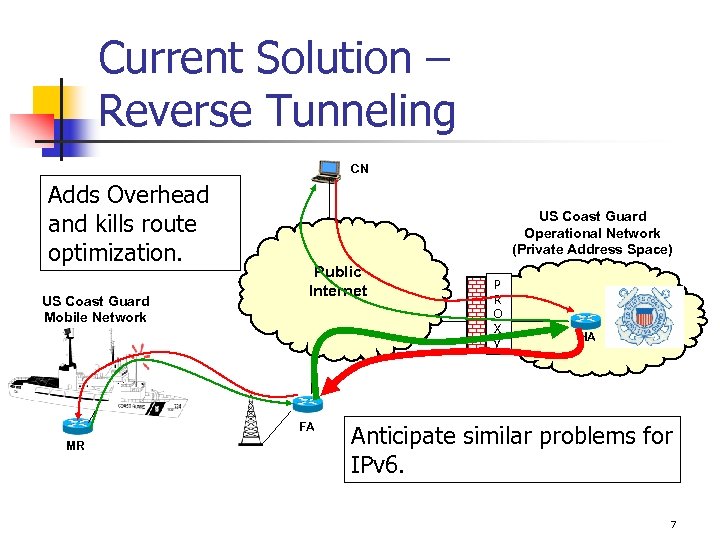
Current Solution – Reverse Tunneling CN Adds Overhead and kills route optimization. US Coast Guard Mobile Network US Coast Guard Operational Network (Private Address Space) Public Internet FA MR P R O X y HA Anticipate similar problems for IPv 6. 7
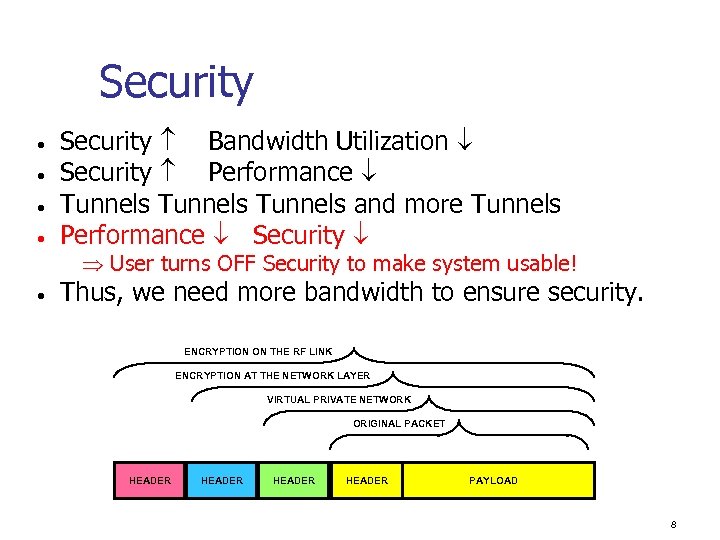
Security • • Security Bandwidth Utilization Security Performance Tunnels and more Tunnels Performance Security User turns OFF Security to make system usable! • Thus, we need more bandwidth to ensure security. ENCRYPTION ON THE RF LINK ENCRYPTION AT THE NETWORK LAYER VIRTUAL PRIVATE NETWORK ORIGINAL PACKET HEADER PAYLOAD 8

Conclusions Regarding Security n Security Breaks Everything n n n At least it sometimes feels like that. “The Ultimate Denial of Service Attack” – D. S. Need to change policy where appropriate. Need to develop good architectures that consider how the wireless systems and protocols operate. Possible solutions that should be investigated: n Dynamic, protocol-aware firewalls and proxies. n Possibly incorporated with Authentication and Authorization. 9

Neah Bay / Mobile Router Project 10
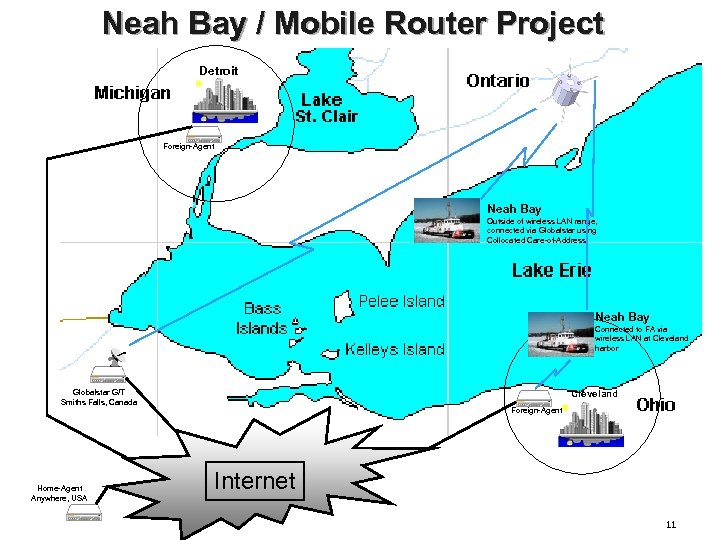
Neah Bay / Mobile Router Project Detroit Foreign-Agent Neah Bay Outside of wireless LAN range, connected via Globalstar using Collocated Care-of-Address. Neah Bay Connected to FA via wireless LAN at Cleveland harbor Globalstar G/T Smiths Falls, Canada Home-Agent Anywhere, USA Cleveland Foreign-Agent Internet 11

Why NASA/USCG/Industry n n n Real world deployment issues can only be addressed in an operational network. USCG has immediate needs, therefore willingness to work the problem. USCG has military network requirements. USCG is large enough network to force us to investigate full scale deployment issues USCG is small enough to work with. NASA has same network issues regarding mobility, security, network management and scalability. 12

Mobile-Router Advantages n Share wireless and network resources with other organizations n n Set and forget n n n No onsite expertise required However, you still have to engineer the network Continuous Connectivity n n $$$ savings (May or may not be important to your organization) Robust n Secondary Home Agent (Dynamic HA) 13

Mobile Network Design Goals n n n Secure Scalable Manageable Ability to sharing network infrastructure Robust 14
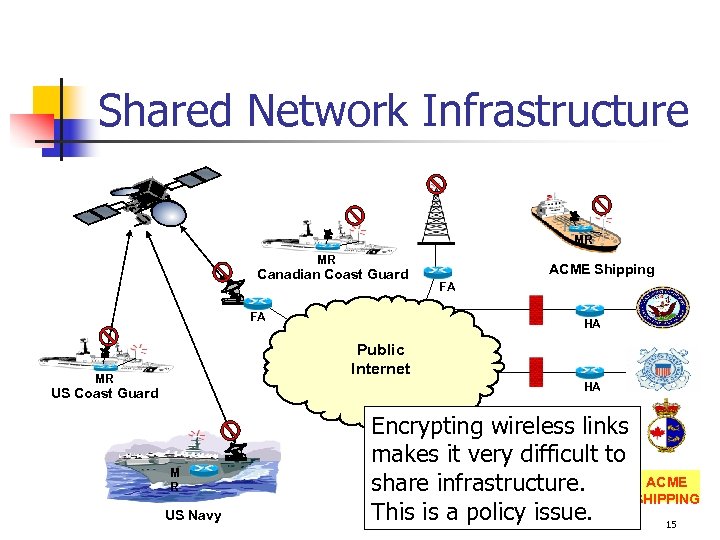
Shared Network Infrastructure MR MR Canadian Coast Guard FA ACME Shipping FA HA Public Internet MR HA US Coast Guard M R US Navy Encrypting wireless links HA makes it very difficult to ACME share infrastructure. SHIPPING HA This is a policy issue. 15
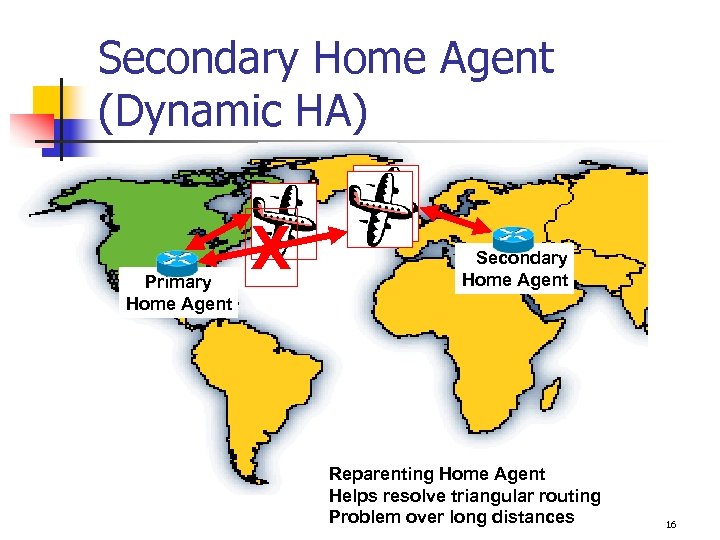
Secondary Home Agent (Dynamic HA) Primary Home Agent X Secondary Home Agent Reparenting Home Agent Helps resolve triangular routing Problem over long distances 16
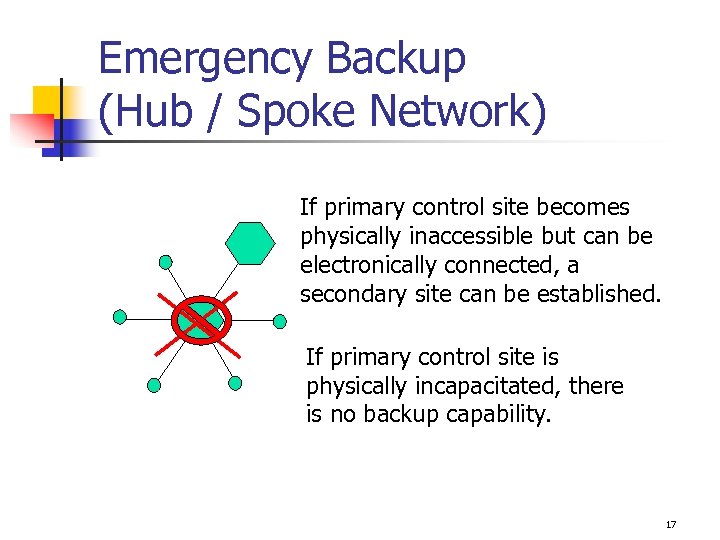
Emergency Backup (Hub / Spoke Network) If primary control site becomes physically inaccessible but can be electronically connected, a secondary site can be established. If primary control site is physically incapacitated, there is no backup capability. 17
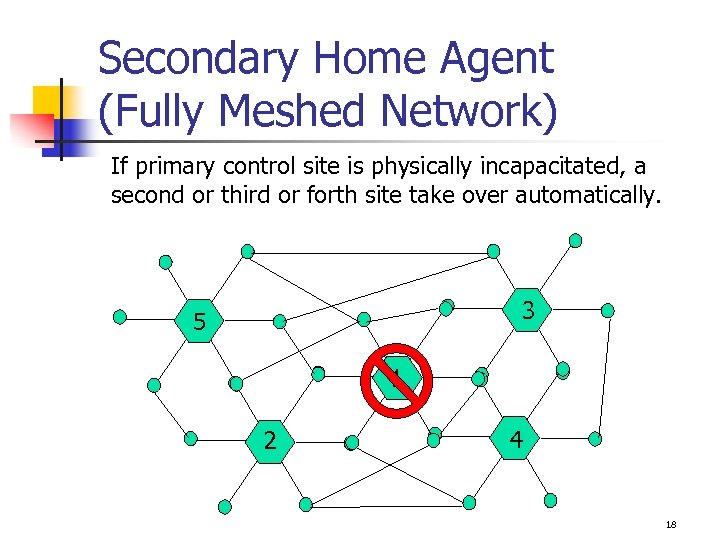
Secondary Home Agent (Fully Meshed Network) If primary control site is physically incapacitated, a second or third or forth site take over automatically. 3 5 1 2 4 18

We Are Running with Reverse Tunneling n Pros n n n Ensures topologically correct addresses on foreign networks Required as requests from MR LAN hosts must pass through Proxy inside main firewall Greatly simplifies setup and management of security associations in encryptors Greatly simplifies multicast – HA makes for an excellent rendezvous point. Mobile Router does NOT have to be in public address space so long as the Collocated Care-of-Address is. Cons n n Uses additional bandwidth Destroys route optimization 19
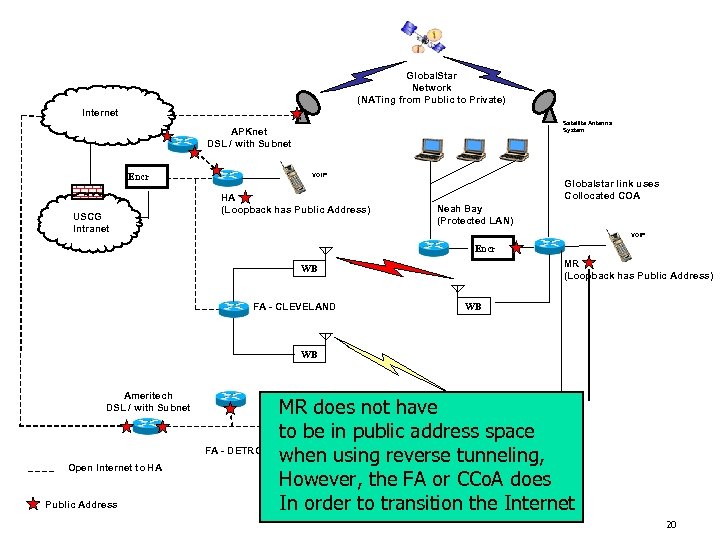
Global. Star Network (NATing from Public to Private) Internet Satellite Antenna System APKnet DSL / with Subnet Encr USCG Intranet VOIP HA (Loopback has Public Address) Globalstar link uses Collocated COA Neah Bay (Protected LAN) VOIP Encr MR (Loopback has Public Address) WB FA - CLEVELAND WB WB Ameritech DSL / with Subnet FA - DETROIT Open Internet to HA Public Address MR does not have WB to WB in public address space be when using reverse tunneling, However, the FA or CCo. A does In order to transition the Internet 20
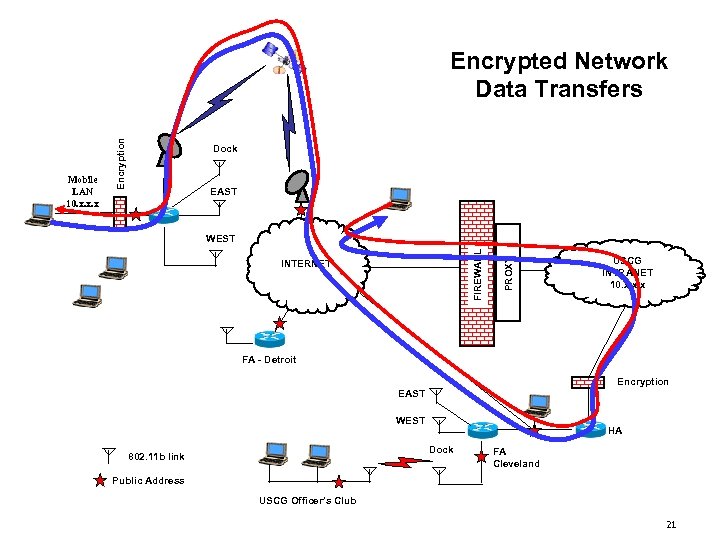
Dock EAST INTERNET PROXY WEST FIREWALL Mobile LAN 10. x. x. x Encryption Encrypted Network Data Transfers USCG INTRANET 10. x. x. x FA - Detroit Encryption EAST WEST HA Dock 802. 11 b link FA Cleveland Public Address USCG Officer’s Club 21

Use and Deployments n n 1 st Demonstrated August 23 & November 6, 2002 Used in operational setting July – Sept 2003 n New York and Boston Harbor n n n NY had no land line Boston land line was poor – switched to satellite Used Oct – Nov 2003 at shipyard during maintenance n 802. 11 b at 11 Mbps 22
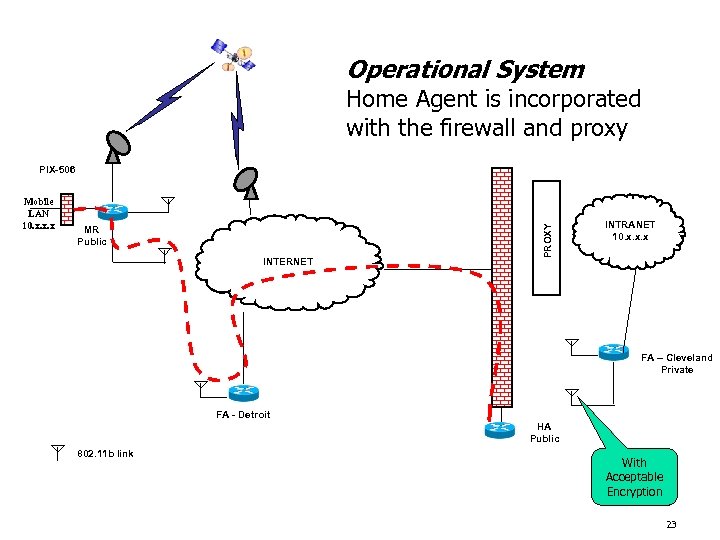
Operational System Home Agent is incorporated with the firewall and proxy Mobile LAN 10. x. x. x MR Public INTERNET PROXY PIX-506 INTRANET 10. x. x. x FA – Cleveland Private FA - Detroit HA Public 802. 11 b link With Acceptable Encryption 23
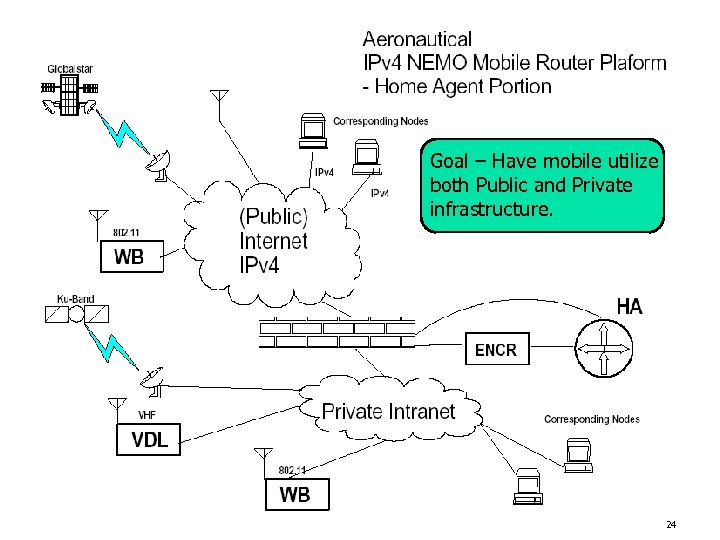
Goal – Have mobile utilize both Public and Private infrastructure. 24
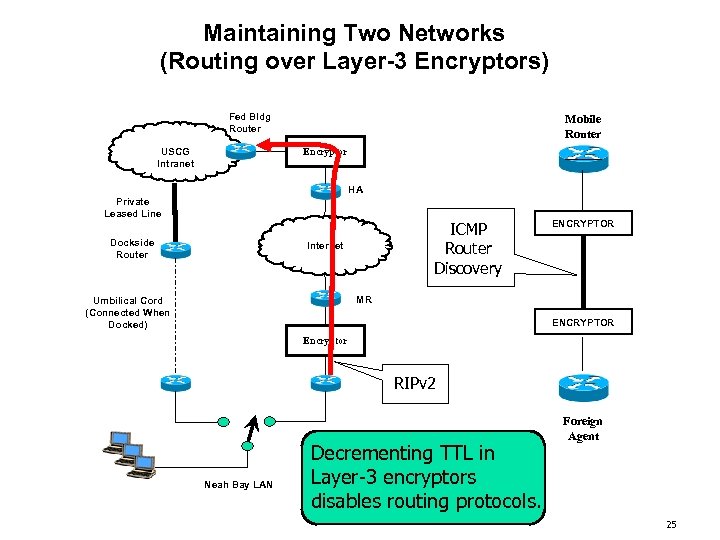
Maintaining Two Networks (Routing over Layer-3 Encryptors) Fed Bldg Router USCG Intranet Mobile Router Encryptor HA Private Leased Line Dockside Router ICMP Router Discovery Internet ENCRYPTOR MR Umbilical Cord (Connected When Docked) ENCRYPTOR Encryptor RIPv 2 Neah Bay LAN Decrementing TTL in Layer-3 encryptors disables routing protocols. Foreign Agent 25

Globalstar/Sea Tel MCM-8 n n Initial market addresses maritime and pleasure boaters. Client / Server architecture – a common architecture n n Current implementation requires call to be initiated by client (ship). Multiplexes eight channels to obtain 56 kbps total data throughput. Full bandwidth-on-demand. Requires use of Collocated Care-of-Address 26
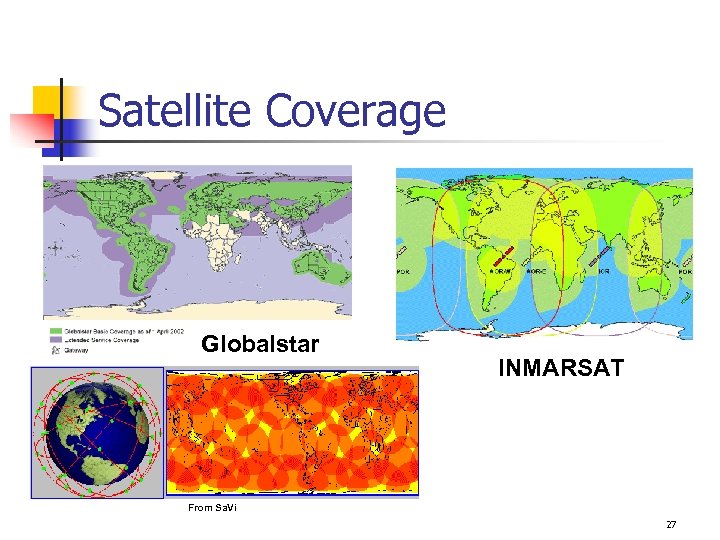
Satellite Coverage Globalstar INMARSAT From Sa. Vi 27
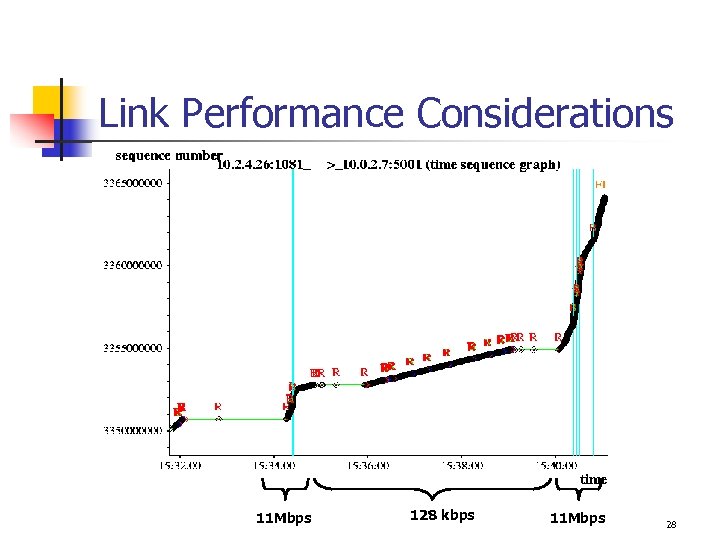
Link Performance Considerations 11 Mbps 128 kbps 11 Mbps 28
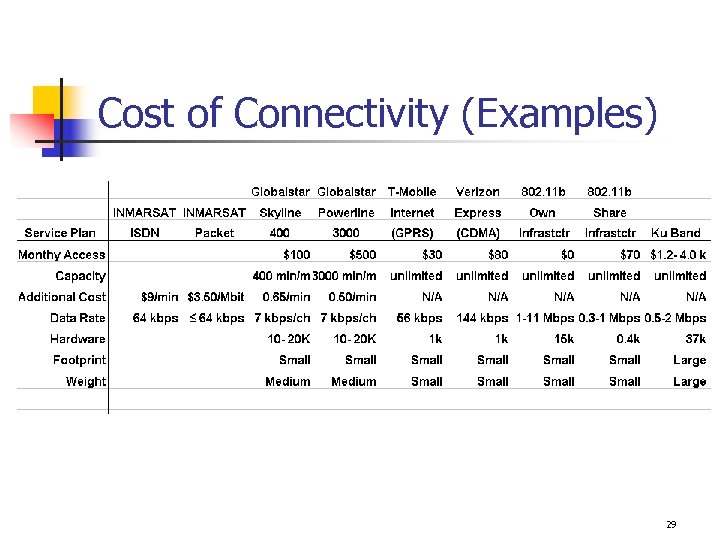
Cost of Connectivity (Examples) 29
Deployment issues (mobile) n n n Equipment Costs Service Cost Network Peculiarities n n n Network Address Translators Performance Enhancing Proxies Security Mechanisms n n Packet Filtering Connection Mechanisms n n n Smart Card Authentication MAC and/or Static Key (manual login is unacceptable) 30

NASA’s Mobile Network Needs n n Space-based systems Aeronautics (in partnership with FAA) n n Weather Dissemination Air Traffic Management Free Flight Terrestrial (surface) Systems n n Rovers Astronauts 31
Earth Observation T 3 T 1 T 2 ? 32
Sensor Web 33

Pick “Papers and Presentations” at http: //roland. grc. nasa. gov/~ivancic/ Neah Bay 34

Backup Slides 35
Networks in Motion (NEMO) Experiments IPv 4 & IPv 6 36
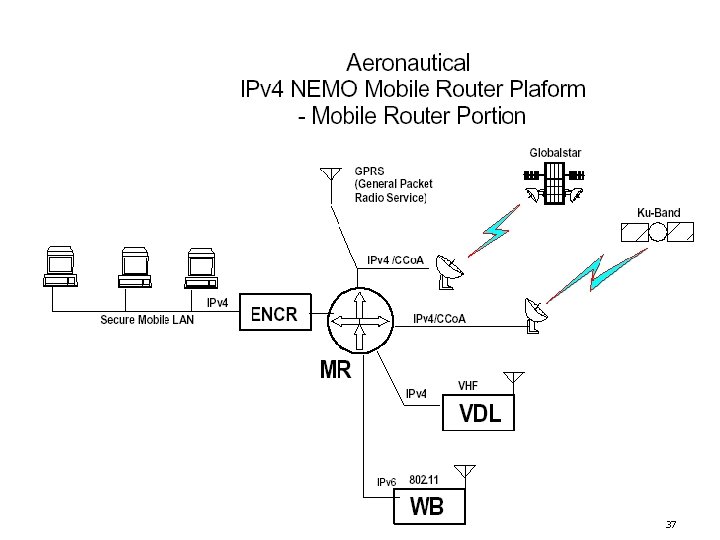
37
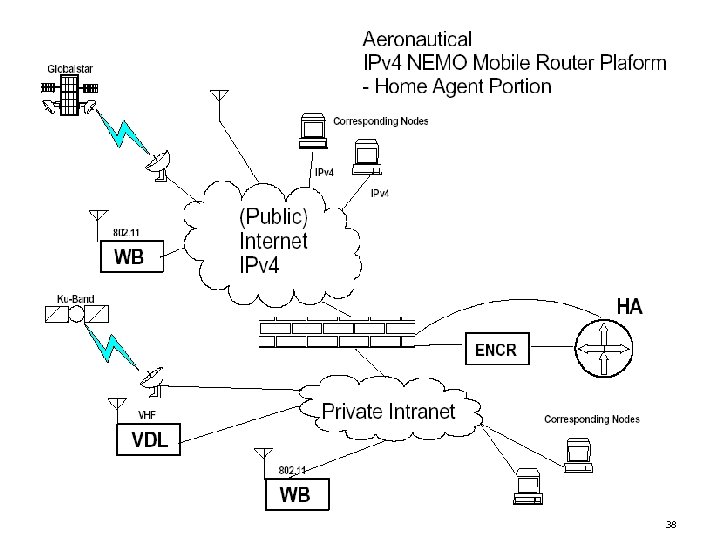
38
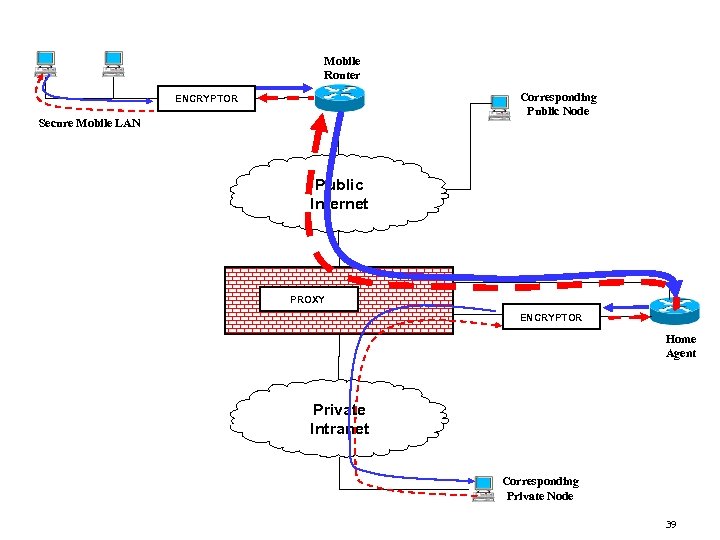
Mobile Router Corresponding Public Node ENCRYPTOR Secure Mobile LAN Public Internet PROXY ENCRYPTOR Home Agent Private Intranet Corresponding Private Node 39
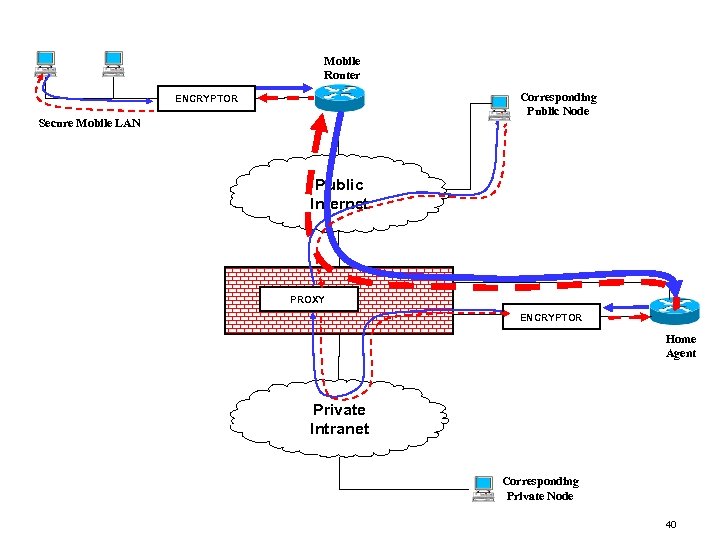
Mobile Router Corresponding Public Node ENCRYPTOR Secure Mobile LAN Public Internet PROXY ENCRYPTOR Home Agent Private Intranet Corresponding Private Node 40
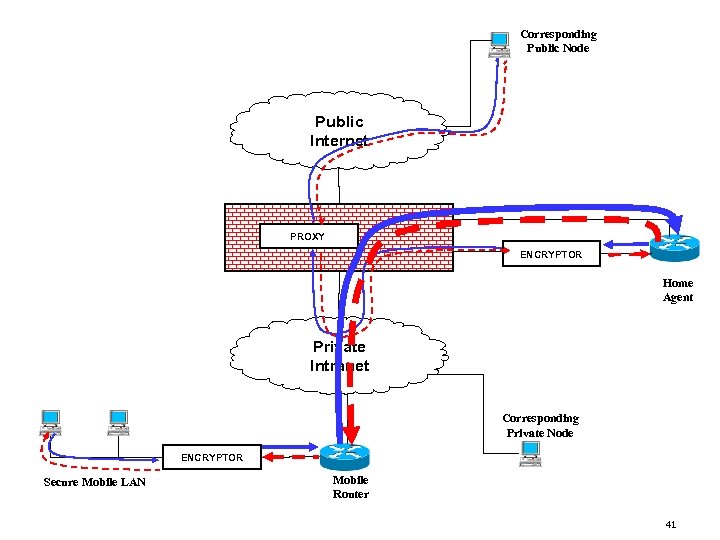
Corresponding Public Node Public Internet PROXY ENCRYPTOR Home Agent Private Intranet Corresponding Private Node ENCRYPTOR Secure Mobile LAN Mobile Router 41
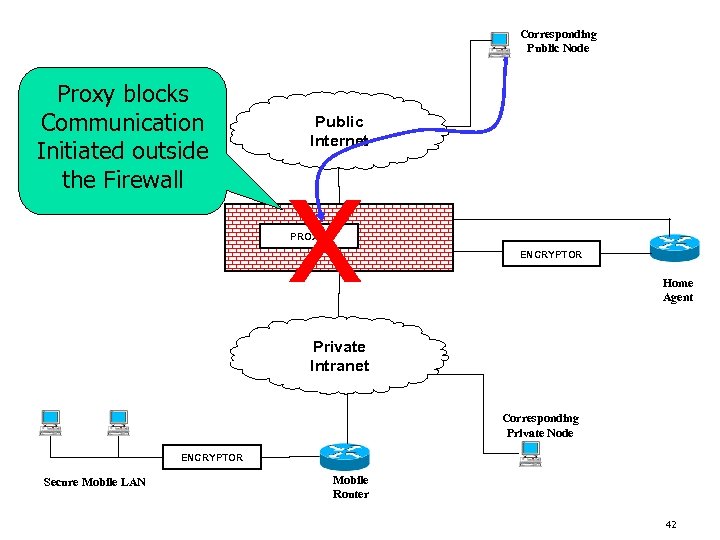
Corresponding Public Node Proxy blocks Communication Initiated outside the Firewall Public Internet x PROXY ENCRYPTOR Home Agent Private Intranet Corresponding Private Node ENCRYPTOR Secure Mobile LAN Mobile Router 42
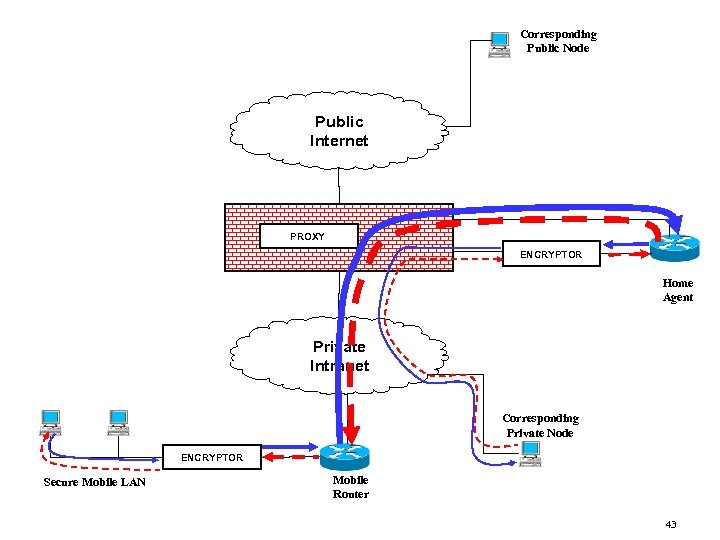
Corresponding Public Node Public Internet PROXY ENCRYPTOR Home Agent Private Intranet Corresponding Private Node ENCRYPTOR Secure Mobile LAN Mobile Router 43
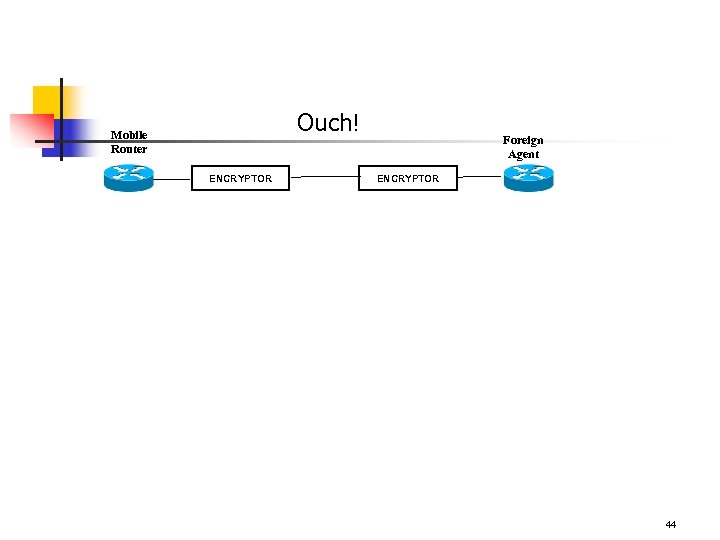
Ouch! Mobile Router ENCRYPTOR Foreign Agent ENCRYPTOR 44
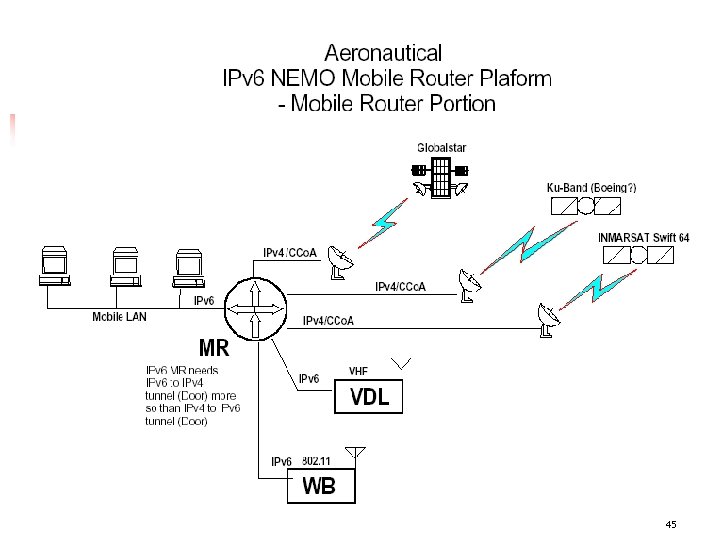
45
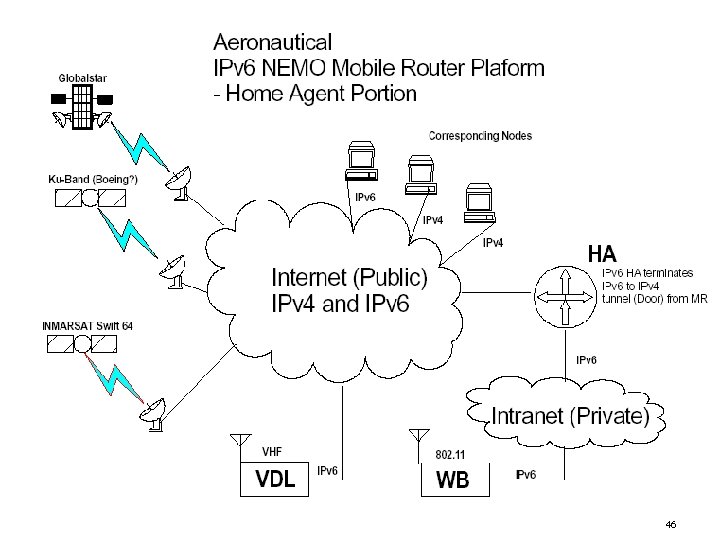
46

Layer 2 Technology Globalstar MCM-8 L 3 -Comm 15 d. Bic Tracking Antenna Hypergain 802. 11 b Flat Panel 8 d. Bi Dipole Sea Tel Tracking Antenna 47
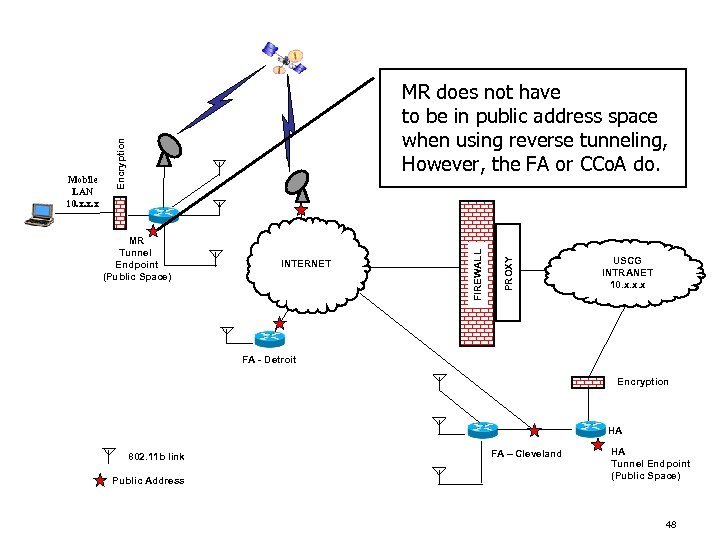
INTERNET PROXY MR Tunnel Endpoint (Public Space) FIREWALL Encryption Mobile LAN 10. x. x. x MR does not have to be in public address space when using reverse tunneling, However, the FA or CCo. A do. USCG INTRANET 10. x. x. x FA - Detroit Encryption HA 802. 11 b link Public Address FA – Cleveland HA Tunnel Endpoint (Public Space) 48
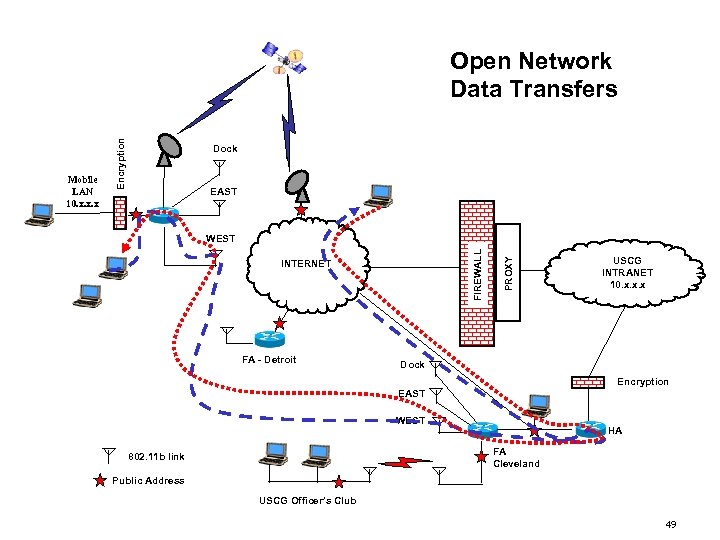
Dock EAST INTERNET FA - Detroit PROXY WEST FIREWALL Mobile LAN 10. x. x. x Encryption Open Network Data Transfers USCG INTRANET 10. x. x. x Dock Encryption EAST WEST HA FA Cleveland 802. 11 b link Public Address USCG Officer’s Club 49
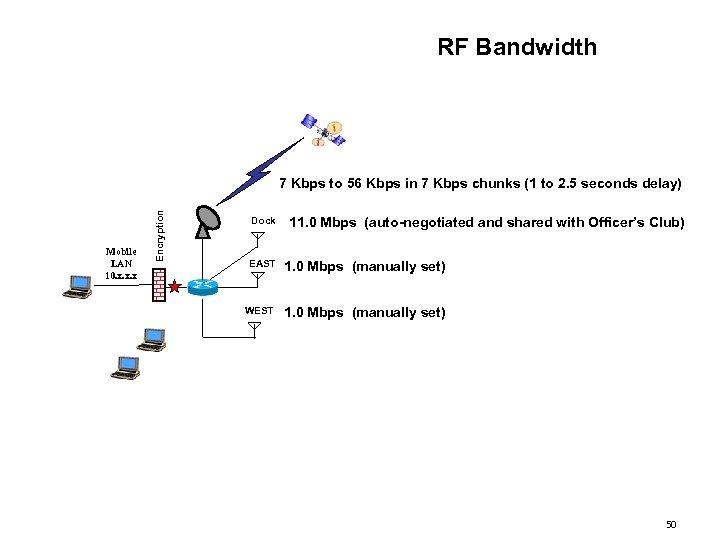
RF Bandwidth Mobile LAN 10. x. x. x Encryption 7 Kbps to 56 Kbps in 7 Kbps chunks (1 to 2. 5 seconds delay) Dock 11. 0 Mbps (auto-negotiated and shared with Officer’s Club) EAST 1. 0 Mbps (manually set) WEST 1. 0 Mbps (manually set) 50

Wireless Only? n Wireless can be jammed (intentionally or unintentionally) n n Particularly unlicensed spectrum such as 802. 11 Satellites is a bit harder Solution is to find interferer and make them stop. You may still want land line connections n Mobile Routing can be used over land lines. 51
1840e8d29f8591a7ab6bbd57f2f53dbe.ppt