cb1cf17eae69dfd8eed1892ceac35f17.ppt
- Количество слайдов: 66
 Securing JSF Applications Against the OWASP Top Ten OWASP & WASC App. Sec 2007 Conference San Jose – Nov 2007 http: //www. webappsec. org/ David Chandler Sr. Engineer, Intuit david_chandler@intuit. com 770 -349 -1294 Copyright © 2007 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the Creative Commons Attribution-Share. Alike 2. 5 License. To view this license, visit http: //creativecommons. org/licenses/by-sa/2. 5/ The OWASP Foundation http: //www. owasp. org/
Securing JSF Applications Against the OWASP Top Ten OWASP & WASC App. Sec 2007 Conference San Jose – Nov 2007 http: //www. webappsec. org/ David Chandler Sr. Engineer, Intuit david_chandler@intuit. com 770 -349 -1294 Copyright © 2007 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the Creative Commons Attribution-Share. Alike 2. 5 License. To view this license, visit http: //creativecommons. org/licenses/by-sa/2. 5/ The OWASP Foundation http: //www. owasp. org/
 JSF is a Great Framework < Tool-friendly < MVC < Component-orientation makes reuse easy < But…. Is it safe? OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF is a Great Framework < Tool-friendly < MVC < Component-orientation makes reuse easy < But…. Is it safe? OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 Framework Security Continuum More secure Framework makes it impossible for developers to write insecure code Developers must do all the right stuff, but you can use code scanning tools and limited inspection to find holes Possible, but developers must do all the right stuff Not possible to create a secure app (framework is flawed) Less secure OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
Framework Security Continuum More secure Framework makes it impossible for developers to write insecure code Developers must do all the right stuff, but you can use code scanning tools and limited inspection to find holes Possible, but developers must do all the right stuff Not possible to create a secure app (framework is flawed) Less secure OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 Security Analysis Goals
Security Analysis Goals
 Our Mission Today
Our Mission Today
 What is Java. Server Faces (JSF)?
What is Java. Server Faces (JSF)?
 What’s in a Typical JSF App
What’s in a Typical JSF App
 Major JSF Concepts
Major JSF Concepts
 JSF Components < Separate business logic from presentation < Every view is composed of a component hierarchy < Components can be added to view programmatically or via template (JSP by default, Facelets for superior performance and ease of development) < Standard components divided into two groups: 4 Faces Core
JSF Components < Separate business logic from presentation < Every view is composed of a component hierarchy < Components can be added to view programmatically or via template (JSP by default, Facelets for superior performance and ease of development) < Standard components divided into two groups: 4 Faces Core
 JSF Renderers
JSF Renderers
 JSF Managed Beans
JSF Managed Beans
 JSF Value Binding
JSF Value Binding
 JSF Value Binding Example view. xhtml In logger object OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Value Binding Example view. xhtml In logger object OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 JSF Value Binding Example view. xhtml Managed beans are registered in faces-config. xml OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Value Binding Example view. xhtml Managed beans are registered in faces-config. xml OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 JSF Converters / Validators
JSF Converters / Validators
 JSF Converters / Validators OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Converters / Validators OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 JSF Converter Example Converter is registered in faces-config. xml, so all Valued. Typesafe. Enum properties of any bean will use this converter Validators also registered in faces-config. xml, but not by class OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Converter Example Converter is registered in faces-config. xml, so all Valued. Typesafe. Enum properties of any bean will use this converter Validators also registered in faces-config. xml, but not by class OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 JSF Controller < Stateful or stateless navigation model < Framework selects next view based on 4 Previous view 4 Outcome of the event handler 4 Event itself (regardless of outcome) 4 Any combination of the above < Possibilities 4 Universal error view (triggered by “error” outcome) 4 Wildcard matching permitted in outcomes, view IDs OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Controller < Stateful or stateless navigation model < Framework selects next view based on 4 Previous view 4 Outcome of the event handler 4 Event itself (regardless of outcome) 4 Any combination of the above < Possibilities 4 Universal error view (triggered by “error” outcome) 4 Wildcard matching permitted in outcomes, view IDs OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 JSF Event Handling <
JSF Event Handling <
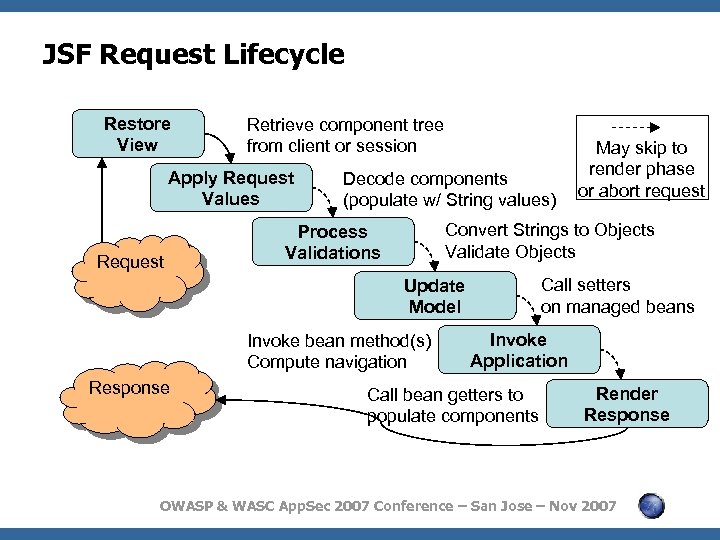 JSF Request Lifecycle Restore View Retrieve component tree from client or session Apply Request Values Request Decode components (populate w/ String values) Convert Strings to Objects Validate Objects Process Validations Call setters on managed beans Update Model Invoke bean method(s) Compute navigation Response May skip to render phase or abort request Invoke Application Call bean getters to populate components Render Response OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Request Lifecycle Restore View Retrieve component tree from client or session Apply Request Values Request Decode components (populate w/ String values) Convert Strings to Objects Validate Objects Process Validations Call setters on managed beans Update Model Invoke bean method(s) Compute navigation Response May skip to render phase or abort request Invoke Application Call bean getters to populate components Render Response OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 JSF Extension Points
JSF Extension Points
 JSF Configuration
JSF Configuration
 OWASP Top Ten (2004 Release) MA 1 Unvalidated Input MA 6 Injection Flaws MA 2 Broken Access Control MA 7 Improper Error Handling MA 3 Broken Authentication and Session Mgmt MA 8 Insecure Storage MA 4 Cross Site Scripting MA 9 Application Denial of Service MA 5 Buffer Overflow MA 10 Insecure Configuration Mgmt OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
OWASP Top Ten (2004 Release) MA 1 Unvalidated Input MA 6 Injection Flaws MA 2 Broken Access Control MA 7 Improper Error Handling MA 3 Broken Authentication and Session Mgmt MA 8 Insecure Storage MA 4 Cross Site Scripting MA 9 Application Denial of Service MA 5 Buffer Overflow MA 10 Insecure Configuration Mgmt OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 A 1 Unvalidated Input
A 1 Unvalidated Input
 A 1 Unvalidated Input JSF Validation Process
A 1 Unvalidated Input JSF Validation Process
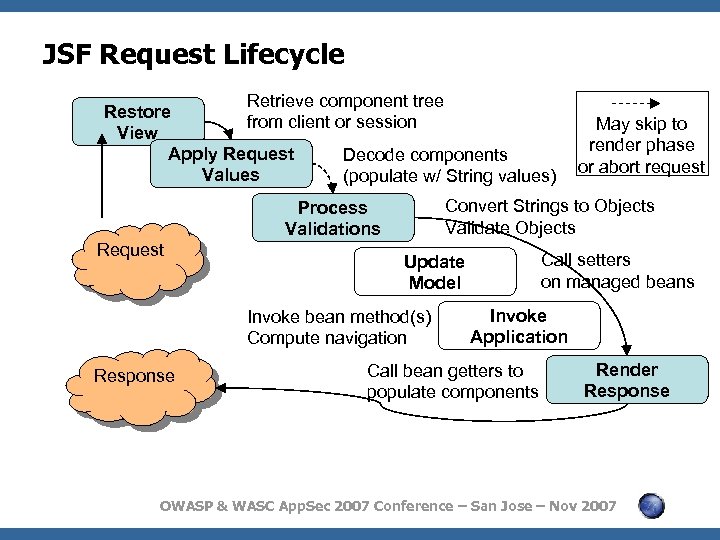 JSF Request Lifecycle Retrieve component tree Restore from client or session View Apply Request Decode components Values (populate w/ String values) Convert Strings to Objects Validate Objects Process Validations Request Call setters on managed beans Update Model Invoke bean method(s) Compute navigation Response May skip to render phase or abort request Invoke Application Call bean getters to populate components Render Response OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
JSF Request Lifecycle Retrieve component tree Restore from client or session View Apply Request Decode components Values (populate w/ String values) Convert Strings to Objects Validate Objects Process Validations Request Call setters on managed beans Update Model Invoke bean method(s) Compute navigation Response May skip to render phase or abort request Invoke Application Call bean getters to populate components Render Response OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 A 1 Unvalidated Input JSF Validation Process < Thing of beauty! 4 Model values never updated with invalid data 4 User remains on current view 4 No action methods called 4 Messages tagged with component ID < Unless… 4 immediate=“true” for some component 4 If so, managed bean can access raw component values through component tree (don’t!) 4 JSF will NEVER update model unless validation passes OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
A 1 Unvalidated Input JSF Validation Process < Thing of beauty! 4 Model values never updated with invalid data 4 User remains on current view 4 No action methods called 4 Messages tagged with component ID < Unless… 4 immediate=“true” for some component 4 If so, managed bean can access raw component values through component tree (don’t!) 4 JSF will NEVER update model unless validation passes OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 A 1 Unvalidated Input Parameter Tampering
A 1 Unvalidated Input Parameter Tampering
 A 1 Unvalidated Input Parameter Tampering (Hidden Fields) < Did you say hidden fields…? YUCK! < Of course, they can be tampered with! < Must rely on validation as with any other field OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
A 1 Unvalidated Input Parameter Tampering (Hidden Fields) < Did you say hidden fields…? YUCK! < Of course, they can be tampered with! < Must rely on validation as with any other field OWASP & WASC App. Sec 2007 Conference – San Jose – Nov 2007
 A 1 Unvalidated Input Parameter Tampering (Select Options)
A 1 Unvalidated Input Parameter Tampering (Select Options)
 A 1 Unvalidated Input Parameter Tampering (Req’d Fields)
A 1 Unvalidated Input Parameter Tampering (Req’d Fields)
 A 1 Unvalidated Input Validating Length, Format, Data Type
A 1 Unvalidated Input Validating Length, Format, Data Type
 A 1 Unvalidated Input Custom Validators
A 1 Unvalidated Input Custom Validators
 A 1 Unvalidated Input Custom Converters
A 1 Unvalidated Input Custom Converters
 A 1 Unvalidated Input Rich Type (Model Centric) Converter <
A 1 Unvalidated Input Rich Type (Model Centric) Converter <
 A 1 Unvalidated Input JSF Validation Summary
A 1 Unvalidated Input JSF Validation Summary
 A 1 Unvalidated Input JSF Validation Summary
A 1 Unvalidated Input JSF Validation Summary
 A 1 Unvalidated Input JSF Validation Extra
A 1 Unvalidated Input JSF Validation Extra
 A 1 Unvalidated Input What About JSF and AJAX?
A 1 Unvalidated Input What About JSF and AJAX?
 A 1 Unvalidated Input Forced Browsing
A 1 Unvalidated Input Forced Browsing
 A 1 Unvalidated Input Forced Browsing
A 1 Unvalidated Input Forced Browsing
 A 2 Broken Access Control
A 2 Broken Access Control
 A 2 Broken Access Control Forced Browsing Past Access Control
A 2 Broken Access Control Forced Browsing Past Access Control
 A 2 Broken Access Control Forced Browsing Past Access Control
A 2 Broken Access Control Forced Browsing Past Access Control
 A 2 Broken Access Control Forced Browsing Past Access Control
A 2 Broken Access Control Forced Browsing Past Access Control
 A 2 Broken Access Control Client Side Caching
A 2 Broken Access Control Client Side Caching
 A 3 Broken Authentication and Session Management
A 3 Broken Authentication and Session Management
 A 4 Cross Site Scripting
A 4 Cross Site Scripting
 A 4 Cross Site Scripting Approach 1: Input Filtering
A 4 Cross Site Scripting Approach 1: Input Filtering
 A 4 Cross Site Scripting Approach 2: Output Filtering
A 4 Cross Site Scripting Approach 2: Output Filtering
 A 4 Cross Site Scripting XSS Code Review
A 4 Cross Site Scripting XSS Code Review

















