aa932f1304192fb315a15ad648849d58.ppt
- Количество слайдов: 13
Securing Information Transmission by Redundancy Jun Li Peter Reiher Gerald Popek Computer Science Department UCLA NISS Conference October 21, 1999 3/18/2018

Outline • Interruption threats are hard to counter • Redundant transmission makes interruptions harder • But redundant transmission is not as easy as using redundancy in other areas • Sample uses • Conclusion 3/18/2018
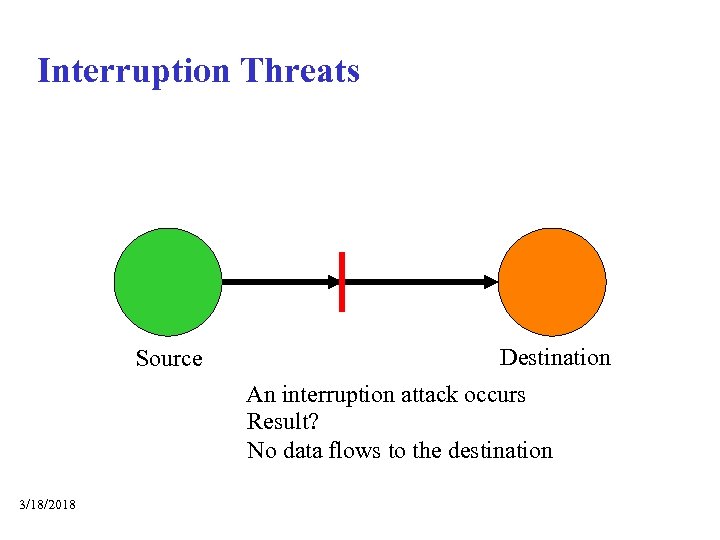
Interruption Threats Source Destination An interruption attack occurs Result? No data flows to the destination 3/18/2018

Problem • Many kinds of interruption threats – Corrupted routers drop packets – Transmitting over packets on shared media – Congesting links or routers • Conventional approaches won’t help – Encrypted/signed message can still be interrupted • Acknowledgement won’t help either – The acknowledgement itself is subject to interruption – Retransmission means possibly failing again • So? 3/18/2018
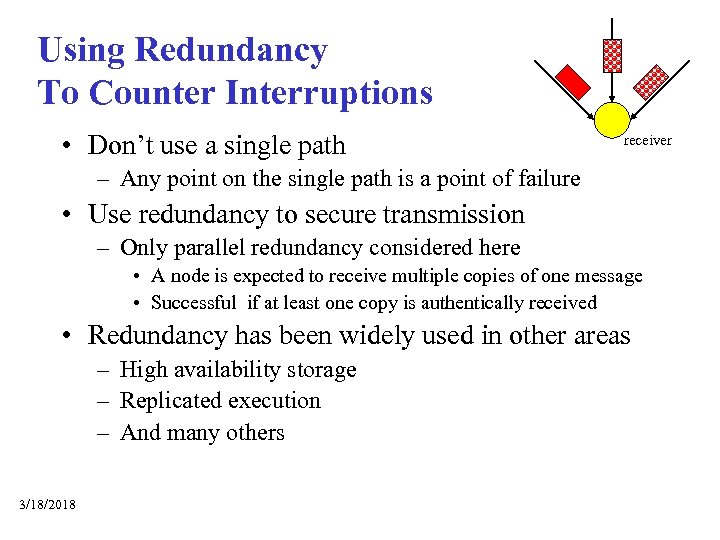
Using Redundancy To Counter Interruptions • Don’t use a single path receiver – Any point on the single path is a point of failure • Use redundancy to secure transmission – Only parallel redundancy considered here • A node is expected to receive multiple copies of one message • Successful if at least one copy is authentically received • Redundancy has been widely used in other areas – High availability storage – Replicated execution – And many others 3/18/2018
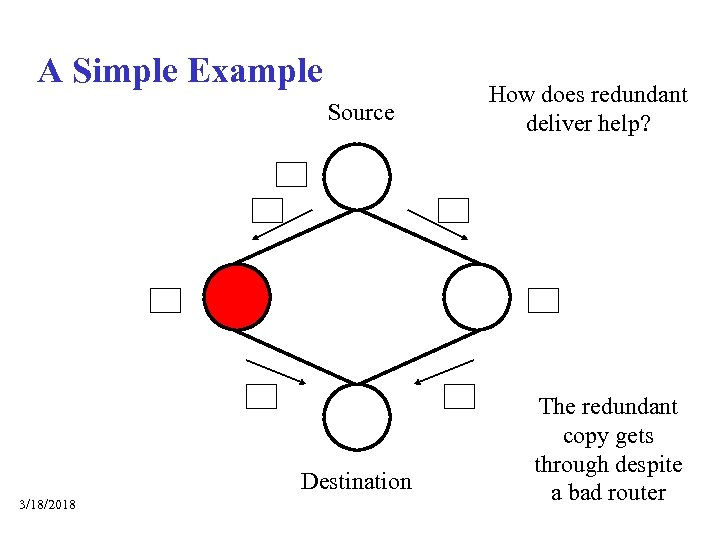
A Simple Example Source Normal delivery uses a default path What if a router is corrupted? Destination 3/18/2018 How does redundant deliver help? The redundant copy gets through despite a bad router

sender But. . . • Redundant transmission is tough – Discovering disjoint paths is difficult • Routing is transparent to applications – Using disjoint paths is difficult – They may not exist at all • Can try to be as disjoint as possible nevertheless – An attacker has to find a choke point or break multiple points • Scale can also cause big problems • And what about costs of sending multiple copies? 3/18/2018 receiver

Sample Uses of Redundancy • Revere – Secure delivery of security updates • General purpose redundant packet delivery service – Redundancy for every network user? 3/18/2018
Revere 1. Goal: disseminate security updates to large number of machines 2. Assume a trusted dissemination center 3. Security updates 1. Small size but critical information 2. Examples: 1. New virus signature 2. New intrusion detection signature 3. CRL (certificate revocation lists) 4. Offending characteristics for a firewall to monitor 3/18/2018
Revere Structure - Acks/Nacks inappropriate - Scaling, lack of complete trust, etc. - Use redundancy to send multiple copies to each node - Each node can also forward security updates to others - A node can contact multiple repository nodes for missed updates 3/18/2018

General Redundant Packet Delivery Services • How could we add a redundant packet delivery service to the Internet? • What would be the best method of achieving redundancy? – Know a lot about the network? – Or rely on randomness and obscurity? • What are the costs of doing so? • How could it be easily deployable? – Proxy-based solutions? 3/18/2018

Conclusion - Conventional security approaches and transmission primitives don’t adequately counter interruption threats - Redundancy is a promising tool - But effective use of redundancy is challenging - Are there other problems that redundancy can solve? - Does redundancy itself lead to new security threats? 3/18/2018
Questions - Contact information - Peter Reiher: reiher@cs. ucla. edu - Jun Li: lijun@cs. ucla. edu - Gerald Popek: popek@cs. ucla. edu 3/18/2018
aa932f1304192fb315a15ad648849d58.ppt