ad59ed90939367d313e4f4d538cd25bf.ppt
- Количество слайдов: 42
 Securing computer networks in youth houses The information security policy in the youth houses TCP Event - 18 February 2011
Securing computer networks in youth houses The information security policy in the youth houses TCP Event - 18 February 2011
 1. What is it made of? 2. What is being covered? 3. Why implement one? 4. How to implement it? 2
1. What is it made of? 2. What is being covered? 3. Why implement one? 4. How to implement it? 2
 Introduction > What is information security ? 3 main criteria • Confidentiality • Integrity • Availability What do these criteria refer to? Everything that has a value to an organisation computers / servers files But also paper documents communication tools buildings staff "Secrets" 3
Introduction > What is information security ? 3 main criteria • Confidentiality • Integrity • Availability What do these criteria refer to? Everything that has a value to an organisation computers / servers files But also paper documents communication tools buildings staff "Secrets" 3
 Introduction > What is information security ? Every day, everybody is trying to protect himself against risks How to define a risk? The possibility for an attacker to exploit vulnerabilities and cause an impact 4
Introduction > What is information security ? Every day, everybody is trying to protect himself against risks How to define a risk? The possibility for an attacker to exploit vulnerabilities and cause an impact 4
 Introduction > What is information security ? Example of a risk : the burglar Vulnerability : Keys under the carpet is the vulnerability of the door Threat : Impact: Burglar breaks Burglar (attacker) tries to get in furniture, steals money and causes trouble Risk = Vulnerability x Threat x Impact 5
Introduction > What is information security ? Example of a risk : the burglar Vulnerability : Keys under the carpet is the vulnerability of the door Threat : Impact: Burglar breaks Burglar (attacker) tries to get in furniture, steals money and causes trouble Risk = Vulnerability x Threat x Impact 5
 Introduction > What is information security ? Can we succeed in reducing the risks and be fully protected? Total security at 100% doesn't exist 6
Introduction > What is information security ? Can we succeed in reducing the risks and be fully protected? Total security at 100% doesn't exist 6
 The role of the information security policy The information security policy serves to formalise and to coordinate all technical and organisational approaches to security of an organisation 7
The role of the information security policy The information security policy serves to formalise and to coordinate all technical and organisational approaches to security of an organisation 7
 The role of the information security policy The information security policy is one solution • to ensure security on the three criteria (CID) • that is not limited to computers • for all information and resources • Oral • Written on whatever medium (paper, electronic) • To manage and share information • buildings, staff, computers, … 8
The role of the information security policy The information security policy is one solution • to ensure security on the three criteria (CID) • that is not limited to computers • for all information and resources • Oral • Written on whatever medium (paper, electronic) • To manage and share information • buildings, staff, computers, … 8
 2. What is being covered? 9
2. What is being covered? 9
 The basis of the information security policy International standard ISO 27002: 2005 • 11 security chapters • 133 security measures Information security policy blue-print for SME • Based upon ISO 17799: 2000 • 10 security chapters • Selection of a subset of 41 security checks (non exhaustive) http: //www. cases. public. lu/publications/politique/ 10
The basis of the information security policy International standard ISO 27002: 2005 • 11 security chapters • 133 security measures Information security policy blue-print for SME • Based upon ISO 17799: 2000 • 10 security chapters • Selection of a subset of 41 security checks (non exhaustive) http: //www. cases. public. lu/publications/politique/ 10
 The 11 chapters of the information security policy 11
The 11 chapters of the information security policy 11
 The 11 chapters of the information security policy > the 44 security checks (1) 12
The 11 chapters of the information security policy > the 44 security checks (1) 12
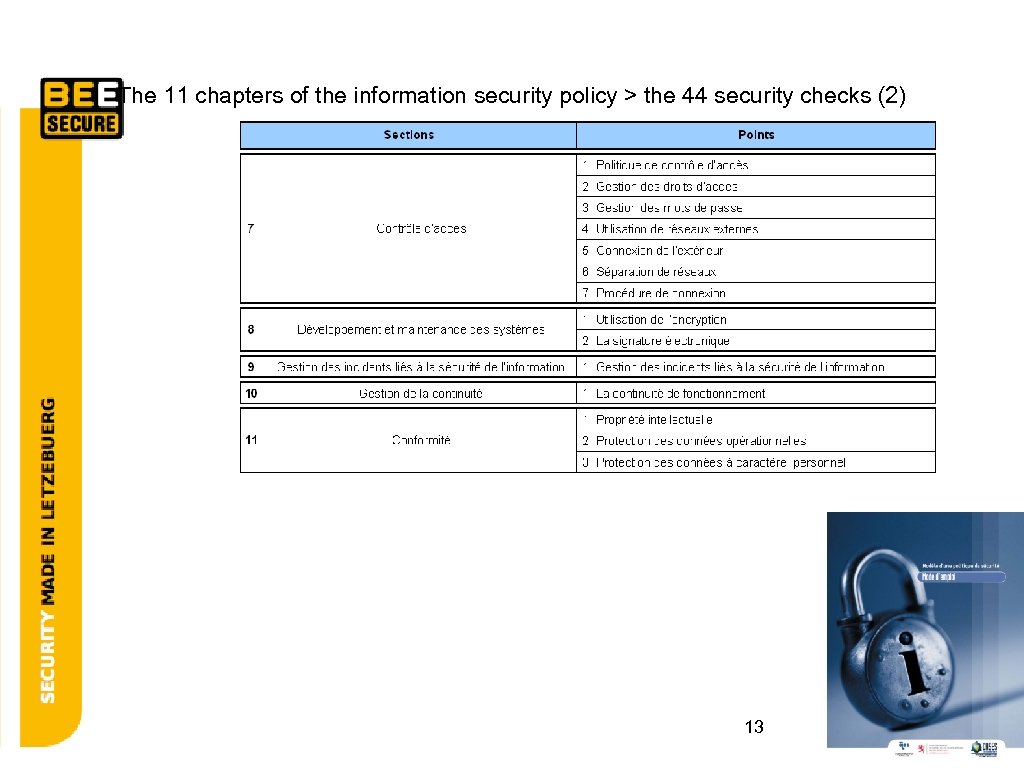 The 11 chapters of the information security policy > the 44 security checks (2) 13
The 11 chapters of the information security policy > the 44 security checks (2) 13
 3) Why implement one? 14
3) Why implement one? 14
 Why implement an information security policy_? Obligation to have means of protection Costs for the implementation Risk to privacy Implementation of a consistent level of security State of the Art 15
Why implement an information security policy_? Obligation to have means of protection Costs for the implementation Risk to privacy Implementation of a consistent level of security State of the Art 15
 Compliance with legislation The Youth House has responsibilities with respect to the law in relation to its activities and its members • Protection of personal data • IP / Copyright • Downloads • Blogs • Fight against the inappropriate behaviour • • • Paedophilia Viewing pornography in presence of young children Violence, incitement to hatred Xenophobia Cyber bullying … … 16
Compliance with legislation The Youth House has responsibilities with respect to the law in relation to its activities and its members • Protection of personal data • IP / Copyright • Downloads • Blogs • Fight against the inappropriate behaviour • • • Paedophilia Viewing pornography in presence of young children Violence, incitement to hatred Xenophobia Cyber bullying … … 16
 Compliance with legislation Protection of personal data • Law of 2 August 2002 on the Protection of Individuals with regard to processing of personal data - NCDB • • Declaration of data and their processing Authorization request (if necessary) Data quality / legitimacy of treatments Right of objection of people concerned • Legal obligation to protect • Justice recognizes and punishes The responsibility of the author of the attack The responsibility of the intermediary of the attack The responsibility of the victim of the attack Failure to secure data in relation with treatment of personal data • 8 days to 1 year in prison and 251 to 125, 000 euro fine • Any organisation must establish a certain level of security • coherent • adapted 17
Compliance with legislation Protection of personal data • Law of 2 August 2002 on the Protection of Individuals with regard to processing of personal data - NCDB • • Declaration of data and their processing Authorization request (if necessary) Data quality / legitimacy of treatments Right of objection of people concerned • Legal obligation to protect • Justice recognizes and punishes The responsibility of the author of the attack The responsibility of the intermediary of the attack The responsibility of the victim of the attack Failure to secure data in relation with treatment of personal data • 8 days to 1 year in prison and 251 to 125, 000 euro fine • Any organisation must establish a certain level of security • coherent • adapted 17
 Compliance with legislation • The information security policy applies to all the members of the Youth House • Committee • Educators / PIJ • Young It aims to inform and explain • their duties and obligations • their responsibilities • The consequences in case of non respect of laws and regulations in • information security • IP • Protection of personal data 18
Compliance with legislation • The information security policy applies to all the members of the Youth House • Committee • Educators / PIJ • Young It aims to inform and explain • their duties and obligations • their responsibilities • The consequences in case of non respect of laws and regulations in • information security • IP • Protection of personal data 18
 4. How to implement it? 19
4. How to implement it? 19
 The implementation of on information security policy. Collaboration with a "pilot" Youth House Re-usage of the information security policy blue-print for SME on www. cases. lu Adaptation to the specific context National Youth Service Youth House Proposition of a blue-print of an information security policy It's on of many possible blue-prints It is not THE blue-print 20
The implementation of on information security policy. Collaboration with a "pilot" Youth House Re-usage of the information security policy blue-print for SME on www. cases. lu Adaptation to the specific context National Youth Service Youth House Proposition of a blue-print of an information security policy It's on of many possible blue-prints It is not THE blue-print 20
 The 6 pillars of security i. awareness raising vi. Legal aspects • • ii. Committee's commitment to the information security Involve the entire organization of the Youth House in the implementation of the information security policy identification and classification of assets and threats • iii. identification of threats / risk assessment in order to identify the critical assets Defining responsibilities • iv. Responsibilise persons depending on assets and associated risks Implementation of organisational and technical measures • v. Implement controls / counter-measures to attain security objectives Continual reassessment of security • Strive for continuous improvement of the overall information security management system 21
The 6 pillars of security i. awareness raising vi. Legal aspects • • ii. Committee's commitment to the information security Involve the entire organization of the Youth House in the implementation of the information security policy identification and classification of assets and threats • iii. identification of threats / risk assessment in order to identify the critical assets Defining responsibilities • iv. Responsibilise persons depending on assets and associated risks Implementation of organisational and technical measures • v. Implement controls / counter-measures to attain security objectives Continual reassessment of security • Strive for continuous improvement of the overall information security management system 21
 Implementation examples Minimum security recommendations for Youth Houses • Guarantee a separation of network zones • Guarantee a level of security for the computers under the responsibility of the Youth House • Propose a Internet filter for the « surf » computers • Implement backup procedures 22
Implementation examples Minimum security recommendations for Youth Houses • Guarantee a separation of network zones • Guarantee a level of security for the computers under the responsibility of the Youth House • Propose a Internet filter for the « surf » computers • Implement backup procedures 22
 Implementation examples Minimum security recommendations for Youth Houses • Guarantee a separation of network zones • Separation of the zones • Implement access controls • Guarantee a level of security for the computers under the responsibility of the Youth House • Propose a Internet filter for the « surf » computers • Implement backup procedures 23
Implementation examples Minimum security recommendations for Youth Houses • Guarantee a separation of network zones • Separation of the zones • Implement access controls • Guarantee a level of security for the computers under the responsibility of the Youth House • Propose a Internet filter for the « surf » computers • Implement backup procedures 23
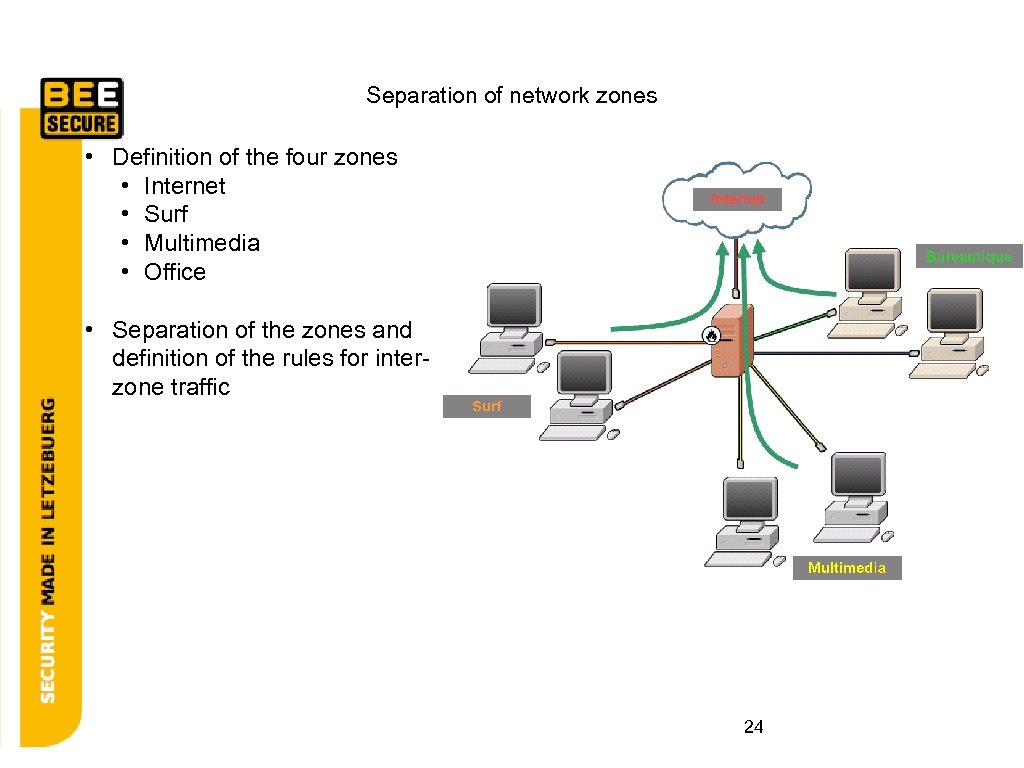 Separation of network zones • Definition of the four zones • Internet • Surf • Multimedia • Office • Separation of the zones and definition of the rules for interzone traffic 24
Separation of network zones • Definition of the four zones • Internet • Surf • Multimedia • Office • Separation of the zones and definition of the rules for interzone traffic 24
 Separation of network zones Possible adaptation of Secure. MJ to all needs 25
Separation of network zones Possible adaptation of Secure. MJ to all needs 25
 Separation of network zones Raise awareness for the correct usage of passwords 26
Separation of network zones Raise awareness for the correct usage of passwords 26
 Implementation examples Minimum security recommendations for Youth Houses Guarantee a separation of network zones Guarantee a level of security for the computers under the responsibility of the Youth House Anti-virus usage Propose a Internet filter for the « surf » computers Implement backup procedures 27
Implementation examples Minimum security recommendations for Youth Houses Guarantee a separation of network zones Guarantee a level of security for the computers under the responsibility of the Youth House Anti-virus usage Propose a Internet filter for the « surf » computers Implement backup procedures 27
 Guarantee a level of security for the computers Example of a security control • Anti-virus usage • regular updates • regular scans • installation on computers http: //www. cases. public. lu/fr/pratique/solutions/freeantivirus/ http: //www. cases. public. lu/fr/publications/fiches/anti-virus/ + Usage of a Secure. MJ box • Define an Access Control List for computers • Do not give uncontrolled access to the computers of educators 28
Guarantee a level of security for the computers Example of a security control • Anti-virus usage • regular updates • regular scans • installation on computers http: //www. cases. public. lu/fr/pratique/solutions/freeantivirus/ http: //www. cases. public. lu/fr/publications/fiches/anti-virus/ + Usage of a Secure. MJ box • Define an Access Control List for computers • Do not give uncontrolled access to the computers of educators 28
 Implementation examples Minimum security recommendations for Youth Houses Guarantee a separation of network zones Guarantee a level of security for the computers under the responsibility of the Youth House Propose a Internet filter for the « surf » computers Filter the visited sites Manage the "surf" time Implement backup procedures 29
Implementation examples Minimum security recommendations for Youth Houses Guarantee a separation of network zones Guarantee a level of security for the computers under the responsibility of the Youth House Propose a Internet filter for the « surf » computers Filter the visited sites Manage the "surf" time Implement backup procedures 29
 Internet filter for the "surf" computers BEE SECURE tips • Ideas • Limit surfing to "special" sites • usage of filters • Manage the "surf" time • The Youth House is not only a cyber café use the Secure. MJ box 30
Internet filter for the "surf" computers BEE SECURE tips • Ideas • Limit surfing to "special" sites • usage of filters • Manage the "surf" time • The Youth House is not only a cyber café use the Secure. MJ box 30
 Implementation examples Minimum security recommendations for Youth Houses Guarantee a separation of network zones Guarantee a level of security for the computers under the responsibility of the Youth House Propose a Internet filter for the « surf » computers Implement backup procedures Identify the data that has to be backed-up Storage of backup media 31
Implementation examples Minimum security recommendations for Youth Houses Guarantee a separation of network zones Guarantee a level of security for the computers under the responsibility of the Youth House Propose a Internet filter for the « surf » computers Implement backup procedures Identify the data that has to be backed-up Storage of backup media 31
 security back-up Appoint a responsible for backup • Define • information to be backed-up • backup frequency • backup media (CD, DVD, external hard disk, . . . ) • location for backups storage • the security of backed-up data • do not forget • to regularly test back-ups • to store copies of paper documents 32
security back-up Appoint a responsible for backup • Define • information to be backed-up • backup frequency • backup media (CD, DVD, external hard disk, . . . ) • location for backups storage • the security of backed-up data • do not forget • to regularly test back-ups • to store copies of paper documents 32
 Deliverables 33
Deliverables 33
 Deliverables Information security policy implementation guide Guide complete à destination du personnel de la Youth House. • Committee • Educators • Technical operators Examples of applications, forms, tips, legal annexes 34
Deliverables Information security policy implementation guide Guide complete à destination du personnel de la Youth House. • Committee • Educators • Technical operators Examples of applications, forms, tips, legal annexes 34
 All this is not so complicated 35
All this is not so complicated 35
 All this is not so complicated • You all know the most important information of your Youth Houses • You already have implemented security measures that are in the information security policy blue-print • Just write what you are doing or must do • . . . and not say that you do something you don't or can't do • The information security policy blue-print gives you the bricks and the means to meet the security requirements that you must complete 36
All this is not so complicated • You all know the most important information of your Youth Houses • You already have implemented security measures that are in the information security policy blue-print • Just write what you are doing or must do • . . . and not say that you do something you don't or can't do • The information security policy blue-print gives you the bricks and the means to meet the security requirements that you must complete 36
 To keep in mind Security must not be an obstacle 37
To keep in mind Security must not be an obstacle 37
 38
38
 2 key messages security is everyone's business Everybody is responsible for the information security of the Youth House. 39 © Jostein Nordengen, Agder University College
2 key messages security is everyone's business Everybody is responsible for the information security of the Youth House. 39 © Jostein Nordengen, Agder University College
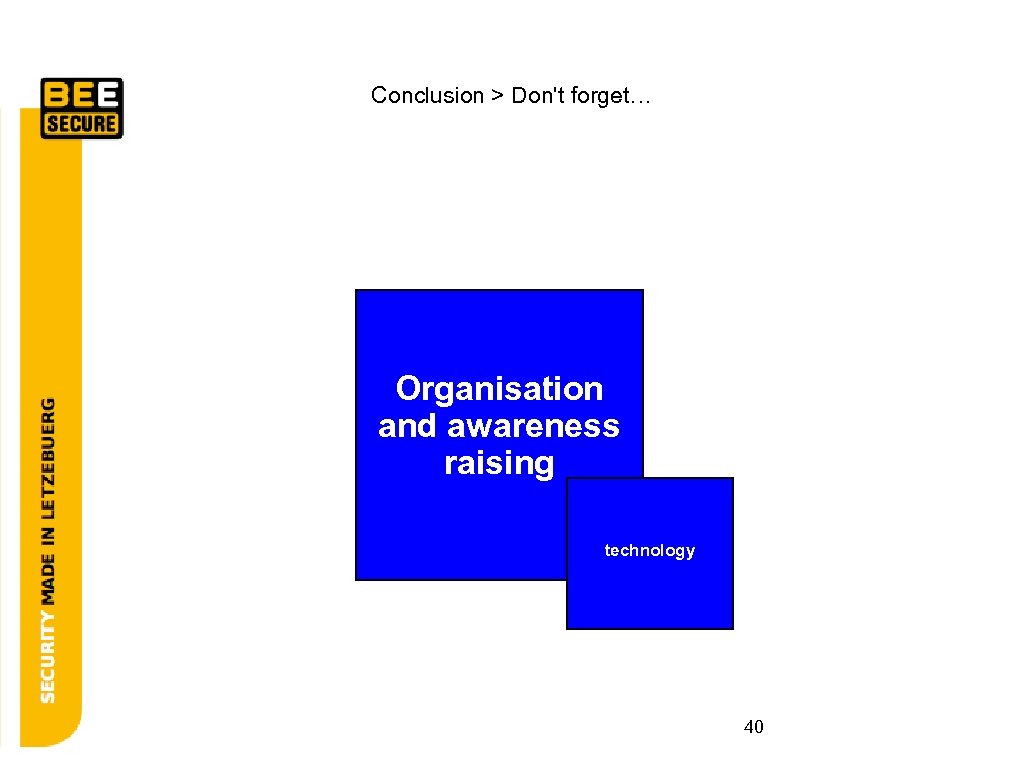 Conclusion > Don't forget… security is Organisation and awareness raising technology 40
Conclusion > Don't forget… security is Organisation and awareness raising technology 40
 Link CASES - the information security portal www. cases. lu Behaviour rules provided by CASES www. cases. public. lu/fr/pratique/comportement/ fact sheets www. cases. public. lu/fr/publications/fiches/ free anti-virus www. cases. public. lu/fr/pratique/solutions/freeantivirus/ information security policy (SME) www. cases. public. lu/fr/publications/politique/ BEE-SECURE www. bee-secure. lu 41
Link CASES - the information security portal www. cases. lu Behaviour rules provided by CASES www. cases. public. lu/fr/pratique/comportement/ fact sheets www. cases. public. lu/fr/publications/fiches/ free anti-virus www. cases. public. lu/fr/pratique/solutions/freeantivirus/ information security policy (SME) www. cases. public. lu/fr/publications/politique/ BEE-SECURE www. bee-secure. lu 41
 Thank you for your attention François Thill , francois. thill@eco. etat. lu
Thank you for your attention François Thill , francois. thill@eco. etat. lu


