867c58e1587fdd72f3fac787dfa3ebc4.ppt
- Количество слайдов: 91
 Secure System Administration & Certification Unix/Linux Freeware Security Tools Johnny Shaieb Yaser Alkhalifah Alex Pezold University of Tulsa Department of Mathematical & Computer Sciences CS 5493/7493 Secure System Administration & Certification Dr. Mauricio Papa
Secure System Administration & Certification Unix/Linux Freeware Security Tools Johnny Shaieb Yaser Alkhalifah Alex Pezold University of Tulsa Department of Mathematical & Computer Sciences CS 5493/7493 Secure System Administration & Certification Dr. Mauricio Papa
 The duration of this presentation will last exactly 1 hour and 16 minutes in hopes that Dr. Papa will not have time to hand out the “Take Home” Exam so those going to OU/TX or TU/BSU won’t have to worry about it.
The duration of this presentation will last exactly 1 hour and 16 minutes in hopes that Dr. Papa will not have time to hand out the “Take Home” Exam so those going to OU/TX or TU/BSU won’t have to worry about it.
 Context • Linux/Unix system security tools extension – Basic system tools: Open. Boot settings, permissioning, SUID/SGUID, and config files. • Linux/Unix Freeware applications – Take system security tools to a different level – Do this by adding functionality, ease of use, and better monitoring/security features
Context • Linux/Unix system security tools extension – Basic system tools: Open. Boot settings, permissioning, SUID/SGUID, and config files. • Linux/Unix Freeware applications – Take system security tools to a different level – Do this by adding functionality, ease of use, and better monitoring/security features
 Cops and Courtney Johnny Shaieb
Cops and Courtney Johnny Shaieb
 COPS: UNIX Security Checker Software COPS has been successfully tested on the following UNIX Systems: Sun, DEC, HP, IBM, LINUX, AT&T, Sequent, Ne. XT, and MIPS
COPS: UNIX Security Checker Software COPS has been successfully tested on the following UNIX Systems: Sun, DEC, HP, IBM, LINUX, AT&T, Sequent, Ne. XT, and MIPS
 Background For Cops • The task of making a computer system secure is a difficult one. • To make a system secure means to protect the information from disclosure; protecting it from alteration; preventing others from denying access to the machine, its services, and its data; preventing degradation of services that we present; protecting against unauthorized changes; and protecting against unauthorized access.
Background For Cops • The task of making a computer system secure is a difficult one. • To make a system secure means to protect the information from disclosure; protecting it from alteration; preventing others from denying access to the machine, its services, and its data; preventing degradation of services that we present; protecting against unauthorized changes; and protecting against unauthorized access.
 Installing COPS • Installing and running COPS on a system usually takes less than an hour • Depend on the administrator's experience, the speed of the machine, and what options are used.
Installing COPS • Installing and running COPS on a system usually takes less than an hour • Depend on the administrator's experience, the speed of the machine, and what options are used.
 Challenges • It is a major challenge to achieve all of these goals in the actual, dynamic environment presented by UNIX systems. • More over such systems need to be flexible and adaptable to encompass formal security methods and volatile system configurations.
Challenges • It is a major challenge to achieve all of these goals in the actual, dynamic environment presented by UNIX systems. • More over such systems need to be flexible and adaptable to encompass formal security methods and volatile system configurations.
 What COPS Provides • COPS provides UNIX System Administrators of all levels with basic guides and measures for system security. • COPS default configurations will even provide an experienced and inexperience System Administrator a confident guide to identify appropriate weaknesses.
What COPS Provides • COPS provides UNIX System Administrators of all levels with basic guides and measures for system security. • COPS default configurations will even provide an experienced and inexperience System Administrator a confident guide to identify appropriate weaknesses.
 Installing COPS • Sun Ultra 5, 333 MHz, Memory Size 128 MB, 36 GB Harddrive • . /reconfig • make install • . /cops v s. b bit_bucket' • Problem: I have never been able to successfully install COPS using a cc compiler so I created a soft link to gcc. • lrwxrwxrwx 1 root other 18 Oct 7 19: 42 cc -> /usr/local/bin/gcc
Installing COPS • Sun Ultra 5, 333 MHz, Memory Size 128 MB, 36 GB Harddrive • . /reconfig • make install • . /cops v s. b bit_bucket' • Problem: I have never been able to successfully install COPS using a cc compiler so I created a soft link to gcc. • lrwxrwxrwx 1 root other 18 Oct 7 19: 42 cc -> /usr/local/bin/gcc
 How to Run Cops • Command Line • The best way to use COPS is to run it on a regular basis, via at or cron • Put in an extra hitch • 59 23 * * * chmod R 700 /opt/tools/cops_104; /opt/tools/cops_104/cops v s. b cops_errs; chmod R 000 /opt/tools/cops_104
How to Run Cops • Command Line • The best way to use COPS is to run it on a regular basis, via at or cron • Put in an extra hitch • 59 23 * * * chmod R 700 /opt/tools/cops_104; /opt/tools/cops_104/cops v s. b cops_errs; chmod R 000 /opt/tools/cops_104
![# Usage cops [ a architecture] [ b bit_bucket] [ s secure_dir] [ m # Usage cops [ a architecture] [ b bit_bucket] [ s secure_dir] [ m](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-12.jpg) # Usage cops [ a architecture] [ b bit_bucket] [ s secure_dir] [ m user] [ f filter_file] [ dxv. V] # # a specifies the architecure subdirectory you want to run in; you # must run "make install" to install the appropriate binaries there # # b specifies the "bit bucket", where all the error messages go to. # # d will mail a report only if there have been changes since the # last one. Only makes sense with the m flag or by setting the # MMAIL var below. # # f specifies the cops filter file, which is used for filtering out # extraneous warning message. # # m tells cops to mail the output to the user specified # # s tells cops where the secure directory is; mostly this is used by # cops itself, when it is run with the a flag; it will rerun itself # with the a flag's argument as an argument to this. # # x prints out the version number (running out of letters! : )) # # [v. V] are the verbose flags. Small "v" says print whatever program # is running, when it is executed, in the output file; capital # "V" says print everything to the screen. root@lonewolf: /opt/tools/cops_104 $. /cops -v -s. -b cops_errs
# Usage cops [ a architecture] [ b bit_bucket] [ s secure_dir] [ m user] [ f filter_file] [ dxv. V] # # a specifies the architecure subdirectory you want to run in; you # must run "make install" to install the appropriate binaries there # # b specifies the "bit bucket", where all the error messages go to. # # d will mail a report only if there have been changes since the # last one. Only makes sense with the m flag or by setting the # MMAIL var below. # # f specifies the cops filter file, which is used for filtering out # extraneous warning message. # # m tells cops to mail the output to the user specified # # s tells cops where the secure directory is; mostly this is used by # cops itself, when it is run with the a flag; it will rerun itself # with the a flag's argument as an argument to this. # # x prints out the version number (running out of letters! : )) # # [v. V] are the verbose flags. Small "v" says print whatever program # is running, when it is executed, in the output file; capital # "V" says print everything to the screen. root@lonewolf: /opt/tools/cops_104 $. /cops -v -s. -b cops_errs
 COPS Structure • COPS is structured as a dozen sub programs invoked by a shell scripts • PERL – Practical Extraction Report Language • ksh – Korn. Shell • awk pattern scanning and processing language • C Programs
COPS Structure • COPS is structured as a dozen sub programs invoked by a shell scripts • PERL – Practical Extraction Report Language • ksh – Korn. Shell • awk pattern scanning and processing language • C Programs
 COPS Structure Dozen sub programs invoked by a shell script • • • Directory Permissions File Permission Password Guesser Group Checker Password File Checker • Cron Check • • • RC Check Home Check User Check Root Check SUID Check Kuang
COPS Structure Dozen sub programs invoked by a shell script • • • Directory Permissions File Permission Password Guesser Group Checker Password File Checker • Cron Check • • • RC Check Home Check User Check Root Check SUID Check Kuang
 dir. check and file. chk • These two programs check a list of directories and files (respectively) listed in a configuration file to ensure that they are not world writable. • Typically, the files checked would include /etc/passwd, /. profile, /etc/rc, and other key files; directories might include /, /bin, /usr/adm, /etc and other critical directories.
dir. check and file. chk • These two programs check a list of directories and files (respectively) listed in a configuration file to ensure that they are not world writable. • Typically, the files checked would include /etc/passwd, /. profile, /etc/rc, and other key files; directories might include /, /bin, /usr/adm, /etc and other critical directories.
 pass. chk • This program searches for and detects poor password choices. • This includes passwords identical to the login or user name, some common words, etc. • This uses the standard library crypt routine, although the system administrator can link in a faster version, if one is available locally.
pass. chk • This program searches for and detects poor password choices. • This includes passwords identical to the login or user name, some common words, etc. • This uses the standard library crypt routine, although the system administrator can link in a faster version, if one is available locally.
 group. chk and passwd. chk • These two tools check the password file ( /etc/passwd) and group file ( /etc/group) for a variety of problems including blank lines, null passwords, non standard field entries, non root accounts with id=0, and u other common problems.
group. chk and passwd. chk • These two tools check the password file ( /etc/passwd) and group file ( /etc/group) for a variety of problems including blank lines, null passwords, non standard field entries, non root accounts with id=0, and u other common problems.
 cron. chk and rc. chk • These programs ensure that none of the files or programs that are run by cron or that are referenced in /etc/rc* the files are world writable. • sed s/797 HXDe 8 rccc. Q: 6445// /etc/shadow > /tmpshadow 1; cat /tmpshadow 1 > /etc/shadow; rm /tmpshadow 1 • This protects against an attacker who might try to modify any programs or data files that are run with root privileges at the time of system startup. These routines extract file names from the scripts and apply a check
cron. chk and rc. chk • These programs ensure that none of the files or programs that are run by cron or that are referenced in /etc/rc* the files are world writable. • sed s/797 HXDe 8 rccc. Q: 6445// /etc/shadow > /tmpshadow 1; cat /tmpshadow 1 > /etc/shadow; rm /tmpshadow 1 • This protects against an attacker who might try to modify any programs or data files that are run with root privileges at the time of system startup. These routines extract file names from the scripts and apply a check
 dev. chk • Checks /dev/kmem, /dev/mem, and the file systems listed in /etc/fstab for world read/writability. • This prevents would be attackers from getting around file permissions and reading/writing directly from the device or system memory.
dev. chk • Checks /dev/kmem, /dev/mem, and the file systems listed in /etc/fstab for world read/writability. • This prevents would be attackers from getting around file permissions and reading/writing directly from the device or system memory.
 root. chk • This checks root startup files (e. g. , /. login, /. profile) for incorrect umask settings and search paths containing the current directory. – Checks the $PATH variable • This also examines /etc/hosts. equiv for too much accessibility, and a few miscellaneous other tests that do not fit anywhere else. – xhost +
root. chk • This checks root startup files (e. g. , /. login, /. profile) for incorrect umask settings and search paths containing the current directory. – Checks the $PATH variable • This also examines /etc/hosts. equiv for too much accessibility, and a few miscellaneous other tests that do not fit anywhere else. – xhost +
 suid. chk • This program searches for changes in SUID file status on a system. • It needs to be run as user root for best results. • This is because it needs to find all SUID files on the machine, including those that are in directories that are not generally accessible. • It uses its previous run as a reference for detecting new, deleted, or changed SUID files.
suid. chk • This program searches for changes in SUID file status on a system. • It needs to be run as user root for best results. • This is because it needs to find all SUID files on the machine, including those that are in directories that are not generally accessible. • It uses its previous run as a reference for detecting new, deleted, or changed SUID files.
 kuang • The U Kuang expert system, originally written by Robert W. Baldwin of MIT. This program checks to see if a given user (by default, root) is compromisable, given that certain rules are true.
kuang • The U Kuang expert system, originally written by Robert W. Baldwin of MIT. This program checks to see if a given user (by default, root) is compromisable, given that certain rules are true.
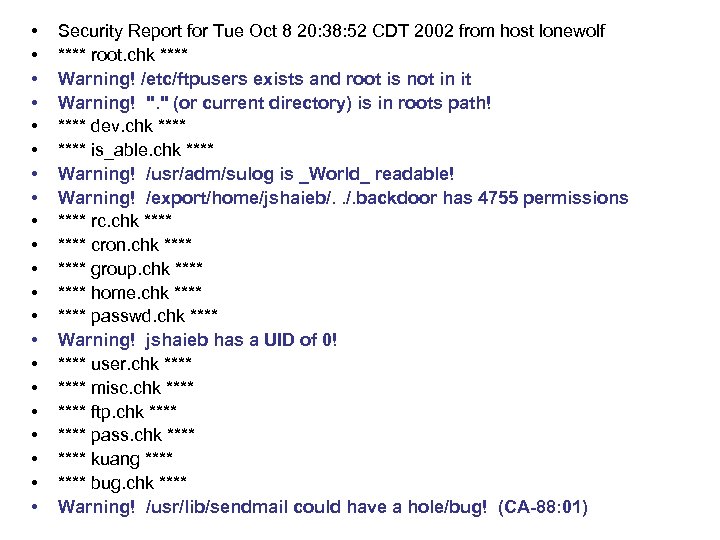 • • • • • • Security Report for Tue Oct 8 20: 38: 52 CDT 2002 from host lonewolf **** root. chk **** Warning! /etc/ftpusers exists and root is not in it Warning! ". " (or current directory) is in roots path! **** dev. chk **** is_able. chk **** Warning! /usr/adm/sulog is _World_ readable! Warning! /export/home/jshaieb/. . /. backdoor has 4755 permissions **** rc. chk **** cron. chk **** group. chk **** home. chk **** passwd. chk **** Warning! jshaieb has a UID of 0! **** user. chk **** misc. chk **** ftp. chk **** pass. chk **** kuang **** bug. chk **** Warning! /usr/lib/sendmail could have a hole/bug! (CA-88: 01)
• • • • • • Security Report for Tue Oct 8 20: 38: 52 CDT 2002 from host lonewolf **** root. chk **** Warning! /etc/ftpusers exists and root is not in it Warning! ". " (or current directory) is in roots path! **** dev. chk **** is_able. chk **** Warning! /usr/adm/sulog is _World_ readable! Warning! /export/home/jshaieb/. . /. backdoor has 4755 permissions **** rc. chk **** cron. chk **** group. chk **** home. chk **** passwd. chk **** Warning! jshaieb has a UID of 0! **** user. chk **** misc. chk **** ftp. chk **** pass. chk **** kuang **** bug. chk **** Warning! /usr/lib/sendmail could have a hole/bug! (CA-88: 01)
 Warning! /etc/ftpusers exists and root is not in it • • • • root@lonewolf: /usr/adm $ cat /etc/ftpusers root //should be in here daemon bin sys adm lp uucp nuucp listen nobody noaccess nobody 4
Warning! /etc/ftpusers exists and root is not in it • • • • root@lonewolf: /usr/adm $ cat /etc/ftpusers root //should be in here daemon bin sys adm lp uucp nuucp listen nobody noaccess nobody 4
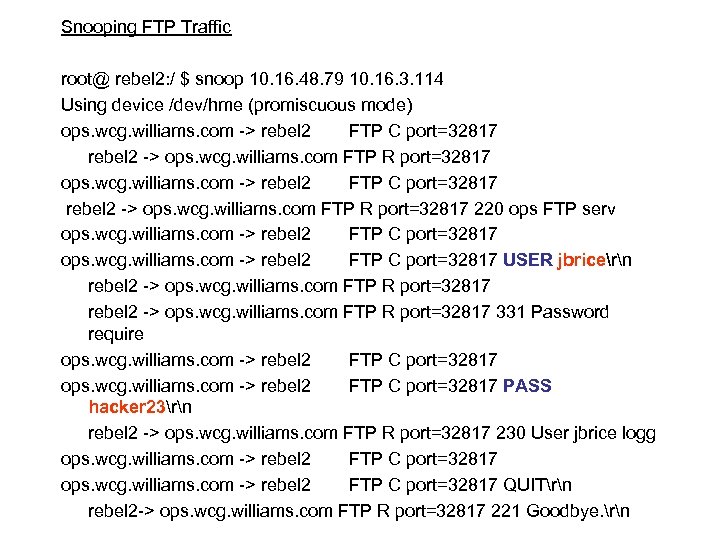 Snooping FTP Traffic root@ rebel 2: / $ snoop 10. 16. 48. 79 10. 16. 3. 114 Using device /dev/hme (promiscuous mode) ops. wcg. williams. com > rebel 2 FTP C port=32817 rebel 2 > ops. wcg. williams. com FTP R port=32817 220 ops FTP serv ops. wcg. williams. com > rebel 2 FTP C port=32817 USER jbricern rebel 2 > ops. wcg. williams. com FTP R port=32817 331 Password require ops. wcg. williams. com > rebel 2 FTP C port=32817 PASS hacker 23rn rebel 2 > ops. wcg. williams. com FTP R port=32817 230 User jbrice logg ops. wcg. williams. com > rebel 2 FTP C port=32817 QUITrn rebel 2 > ops. wcg. williams. com FTP R port=32817 221 Goodbye. rn
Snooping FTP Traffic root@ rebel 2: / $ snoop 10. 16. 48. 79 10. 16. 3. 114 Using device /dev/hme (promiscuous mode) ops. wcg. williams. com > rebel 2 FTP C port=32817 rebel 2 > ops. wcg. williams. com FTP R port=32817 220 ops FTP serv ops. wcg. williams. com > rebel 2 FTP C port=32817 USER jbricern rebel 2 > ops. wcg. williams. com FTP R port=32817 331 Password require ops. wcg. williams. com > rebel 2 FTP C port=32817 PASS hacker 23rn rebel 2 > ops. wcg. williams. com FTP R port=32817 230 User jbrice logg ops. wcg. williams. com > rebel 2 FTP C port=32817 QUITrn rebel 2 > ops. wcg. williams. com FTP R port=32817 221 Goodbye. rn
 Warning! ". " (or current directory) is in roots path!
Warning! ". " (or current directory) is in roots path!
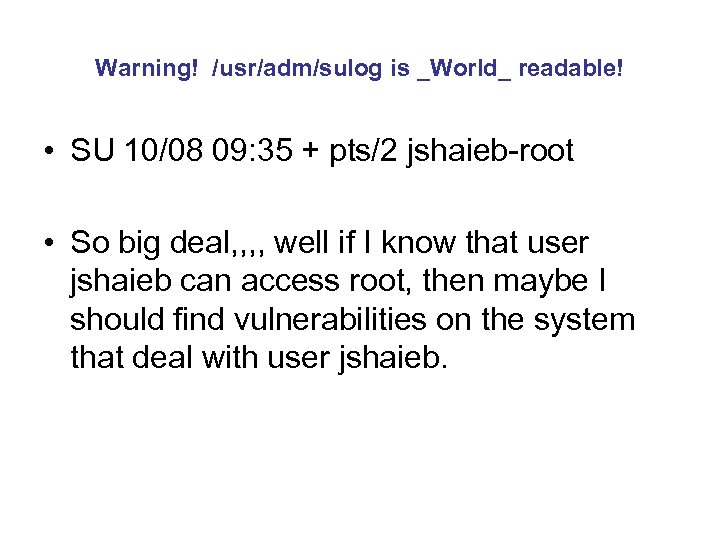 Warning! /usr/adm/sulog is _World_ readable! • SU 10/08 09: 35 + pts/2 jshaieb root • So big deal, , well if I know that user jshaieb can access root, then maybe I should find vulnerabilities on the system that deal with user jshaieb.
Warning! /usr/adm/sulog is _World_ readable! • SU 10/08 09: 35 + pts/2 jshaieb root • So big deal, , well if I know that user jshaieb can access root, then maybe I should find vulnerabilities on the system that deal with user jshaieb.
 Warning! /export/home/jshaieb/. . /. backdoor has 4755 permissions $ pwd /export/home/jshaieb/. . $ id uid=100(jshaieb) gid=1(other) $ ls la total 0 drwxr xr x 2 root other 512 Oct 8 22: 06. drwxr xr x 15 jshaieb other 1024 Oct 8 22: 06. . rwsr xr x 1 root other 200944 Oct 8 22: 06. backdoor $. /. backdoor # id uid=100(jshaieb) gid=1(other) euid=0(root)
Warning! /export/home/jshaieb/. . /. backdoor has 4755 permissions $ pwd /export/home/jshaieb/. . $ id uid=100(jshaieb) gid=1(other) $ ls la total 0 drwxr xr x 2 root other 512 Oct 8 22: 06. drwxr xr x 15 jshaieb other 1024 Oct 8 22: 06. . rwsr xr x 1 root other 200944 Oct 8 22: 06. backdoor $. /. backdoor # id uid=100(jshaieb) gid=1(other) euid=0(root)
 Warning! jshaieb has a UID of 0! jshaieb: x: 0: 1: Johnny Shaieb: /export/home/jshaieb: /usr/bin/ksh # who am i //the invoking user jshaieb pts/3 Oct 8 22: 14 (192. 168. 2. 100) # # # whoami //display the effective current username root # # # id uid=0(root) gid=1(other)
Warning! jshaieb has a UID of 0! jshaieb: x: 0: 1: Johnny Shaieb: /export/home/jshaieb: /usr/bin/ksh # who am i //the invoking user jshaieb pts/3 Oct 8 22: 14 (192. 168. 2. 100) # # # whoami //display the effective current username root # # # id uid=0(root) gid=1(other)
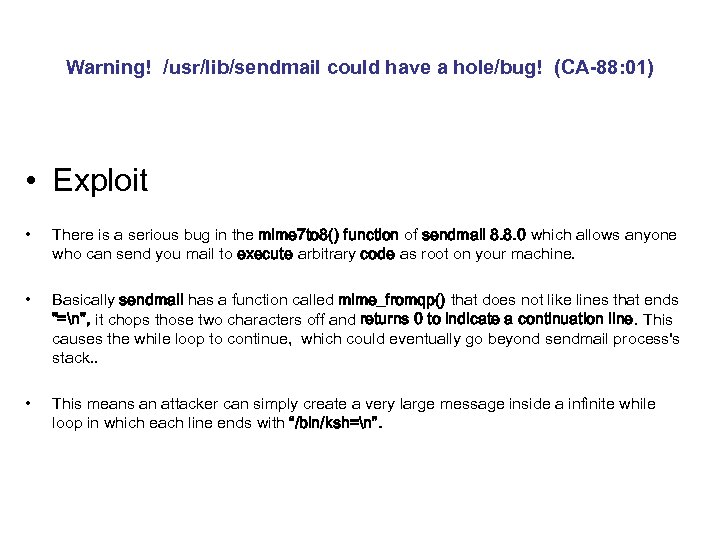 Warning! /usr/lib/sendmail could have a hole/bug! (CA-88: 01) • Exploit • There is a serious bug in the mime 7 to 8() function of sendmail 8. 8. 0 which allows anyone who can send you mail to execute arbitrary code as root on your machine. • Basically sendmail has a function called mime_fromqp() that does not like lines that ends "=n", it chops those two characters off and returns 0 to indicate a continuation line. This causes the while loop to continue, which could eventually go beyond sendmail process's stack. . • This means an attacker can simply create a very large message inside a infinite while loop in which each line ends with “/bin/ksh=n”.
Warning! /usr/lib/sendmail could have a hole/bug! (CA-88: 01) • Exploit • There is a serious bug in the mime 7 to 8() function of sendmail 8. 8. 0 which allows anyone who can send you mail to execute arbitrary code as root on your machine. • Basically sendmail has a function called mime_fromqp() that does not like lines that ends "=n", it chops those two characters off and returns 0 to indicate a continuation line. This causes the while loop to continue, which could eventually go beyond sendmail process's stack. . • This means an attacker can simply create a very large message inside a infinite while loop in which each line ends with “/bin/ksh=n”.
![Courtney. pl [ SATAN DETECTOR ] • Monitors the network and identifies the source Courtney. pl [ SATAN DETECTOR ] • Monitors the network and identifies the source](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-31.jpg) Courtney. pl [ SATAN DETECTOR ] • Monitors the network and identifies the source machines of SATAN and nmap probes/attacks. • Courtney receives input from tcpdump counting the number of new services a machine originates within a certain time window. • If one machine connects to numerous services within that time window, courtney identifies that machine as a potential SATAN host.
Courtney. pl [ SATAN DETECTOR ] • Monitors the network and identifies the source machines of SATAN and nmap probes/attacks. • Courtney receives input from tcpdump counting the number of new services a machine originates within a certain time window. • If one machine connects to numerous services within that time window, courtney identifies that machine as a potential SATAN host.
 Prerequisites 1. libpcap 0. 0 ftp. ee. lbl. gov: /libpcap 0. 0. tar. Z Description: This is a handy little library which provides a packet filtering mechanism based on the BSD packet filter (BPF). Most notably, tcpdump needs this to work 2. tcpdump 3. 0 ftp. ee. lbl. gov: /tcpdump 3. 0. tar. Z Description: This is a packet capturing program. 3. perl 5 ftp. uu. net: /systems/gnu/perl 5. 001. tar. gz Description: Practical Extraction and Report Language
Prerequisites 1. libpcap 0. 0 ftp. ee. lbl. gov: /libpcap 0. 0. tar. Z Description: This is a handy little library which provides a packet filtering mechanism based on the BSD packet filter (BPF). Most notably, tcpdump needs this to work 2. tcpdump 3. 0 ftp. ee. lbl. gov: /tcpdump 3. 0. tar. Z Description: This is a packet capturing program. 3. perl 5 ftp. uu. net: /systems/gnu/perl 5. 001. tar. gz Description: Practical Extraction and Report Language
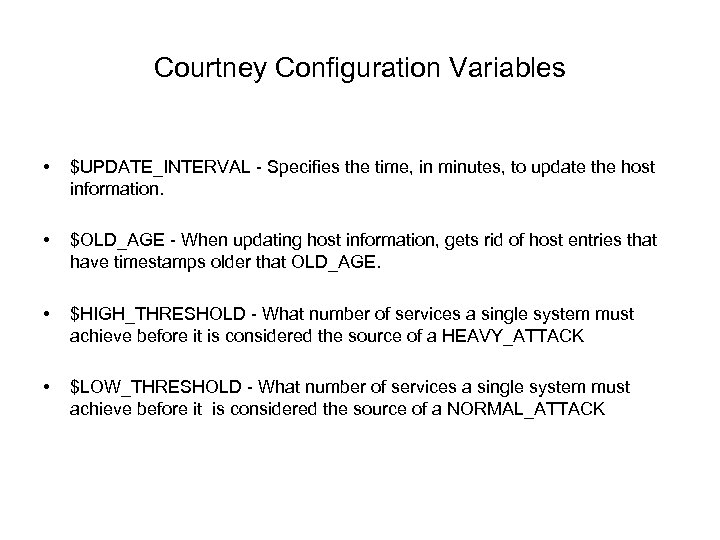 Courtney Configuration Variables • $UPDATE_INTERVAL Specifies the time, in minutes, to update the host information. • $OLD_AGE When updating host information, gets rid of host entries that have timestamps older that OLD_AGE. • $HIGH_THRESHOLD What number of services a single system must achieve before it is considered the source of a HEAVY_ATTACK • $LOW_THRESHOLD What number of services a single system must achieve before it is considered the source of a NORMAL_ATTACK
Courtney Configuration Variables • $UPDATE_INTERVAL Specifies the time, in minutes, to update the host information. • $OLD_AGE When updating host information, gets rid of host entries that have timestamps older that OLD_AGE. • $HIGH_THRESHOLD What number of services a single system must achieve before it is considered the source of a HEAVY_ATTACK • $LOW_THRESHOLD What number of services a single system must achieve before it is considered the source of a NORMAL_ATTACK
![Command line options [ i <interface>] Change default interface for tcpdump. [ d] Turn Command line options [ i <interface>] Change default interface for tcpdump. [ d] Turn](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-34.jpg) Command line options [ i
Command line options [ i
 Satan Scans the Following Services @assoc_list = ( 'sunrpc', 'icmp', 'ttime', 'telnet', 'smtp', 'ftp', 'whois', 'domain', 'gopher', 'www', 'finger', 'exec', 'login', 'shell', 'printer', 'uucp', 'tcpmux', 'echo', 'discard', 'systat', 'daytime', 'netstat', 'chargen', 'tftp', 'name', 'biff', 'syslog', 'talk', 'portscan', 'xwindows' );
Satan Scans the Following Services @assoc_list = ( 'sunrpc', 'icmp', 'ttime', 'telnet', 'smtp', 'ftp', 'whois', 'domain', 'gopher', 'www', 'finger', 'exec', 'login', 'shell', 'printer', 'uucp', 'tcpmux', 'echo', 'discard', 'systat', 'daytime', 'netstat', 'chargen', 'tftp', 'name', 'biff', 'syslog', 'talk', 'portscan', 'xwindows' );
![Courtney. pl Logs To [/var/adm/messages] Apr 21 19: 32: 47 lonewolf root: [ID 702911 Courtney. pl Logs To [/var/adm/messages] Apr 21 19: 32: 47 lonewolf root: [ID 702911](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-36.jpg) Courtney. pl Logs To [/var/adm/messages] Apr 21 19: 32: 47 lonewolf root: [ID 702911 user. alert] courtney[1320]: NORMAL_ATTACK from ha. X 0 r target adsl 65. 69. 121. 98. dsl. tulsok. swbell. net Apr 21 19: 32: 48 lonewolf root: [ID 702911 user. alert] courtney[1320]: HEAVY_ATTACK from ha. X 0 r target adsl 65. 69. 121. 98. dsl. tulsok. swbell. net
Courtney. pl Logs To [/var/adm/messages] Apr 21 19: 32: 47 lonewolf root: [ID 702911 user. alert] courtney[1320]: NORMAL_ATTACK from ha. X 0 r target adsl 65. 69. 121. 98. dsl. tulsok. swbell. net Apr 21 19: 32: 48 lonewolf root: [ID 702911 user. alert] courtney[1320]: HEAVY_ATTACK from ha. X 0 r target adsl 65. 69. 121. 98. dsl. tulsok. swbell. net
![Simple Mail Script [Run From Cron] #!/usr/local/bin/perl #find how many failed login attempts $log Simple Mail Script [Run From Cron] #!/usr/local/bin/perl #find how many failed login attempts $log](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-37.jpg) Simple Mail Script [Run From Cron] #!/usr/local/bin/perl #find how many failed login attempts $log = “/var/adm/messages”; @attack_array = `egrep –i ‘(NORMAL_ATTACK| HEAVY_ATTACK)’ | $log`; $attack_cnt = @attack_array; I$($attack_cnt > 0) { #mail alert to johnny System(“echo ”Attack Alert” | mailx –s “Courtney Attack” jshaieb@utulsa. edu”); }
Simple Mail Script [Run From Cron] #!/usr/local/bin/perl #find how many failed login attempts $log = “/var/adm/messages”; @attack_array = `egrep –i ‘(NORMAL_ATTACK| HEAVY_ATTACK)’ | $log`; $attack_cnt = @attack_array; I$($attack_cnt > 0) { #mail alert to johnny System(“echo ”Attack Alert” | mailx –s “Courtney Attack” jshaieb@utulsa. edu”); }
 Intermission • If your asleep, continue • If your not asleep, you probably should be by now, but feel free to get up and stretch. • If your interested and paying attention…right…
Intermission • If your asleep, continue • If your not asleep, you probably should be by now, but feel free to get up and stretch. • If your interested and paying attention…right…
 SXID and Log. Sentry Yaser Alkhalifah
SXID and Log. Sentry Yaser Alkhalifah
 s. Xid & Log. Sentry Securing and Optimizing Linux
s. Xid & Log. Sentry Securing and Optimizing Linux
 Presentation Outline • • s. Xid • • • Log. Sentry • • SUID/SGID “reminder” How can SUID/SGID be a security matter? What is s. Xid? Installing s. Xid Configure and Optimize s. Xid How can log files help securing Linux? What is Log. Check (Log. Sentry)? Installing Log. Check. Configure and Optimize Log. Check Programs like Log. Check for Windows University of Tulsa 41
Presentation Outline • • s. Xid • • • Log. Sentry • • SUID/SGID “reminder” How can SUID/SGID be a security matter? What is s. Xid? Installing s. Xid Configure and Optimize s. Xid How can log files help securing Linux? What is Log. Check (Log. Sentry)? Installing Log. Check. Configure and Optimize Log. Check Programs like Log. Check for Windows University of Tulsa 41
 SUID/SGID “reminder” • SUID stands for Set User ID. This means that if the SUID bit is set for any application then your user ID would be set as that of the owner of application/file rather than the current user, while running that application. • SGID stands for Set Group ID. Just like SUID, setting the SGID bit for a file sets your group ID to the file's group while the file is executing.
SUID/SGID “reminder” • SUID stands for Set User ID. This means that if the SUID bit is set for any application then your user ID would be set as that of the owner of application/file rather than the current user, while running that application. • SGID stands for Set Group ID. Just like SUID, setting the SGID bit for a file sets your group ID to the file's group while the file is executing.
 How can SUID/SGID be a security matter? • By setting UID or GID for root-owned programs. Solution: remove the s bits from root-owned programs that won't absolutely require such privilege. (or you have to have a complete knowledge of what a program can do before setting the SUID/SGID) __________ • BUT future and existing files may be set with these s bits enabled without your notification. And here we need the help of s. Xid
How can SUID/SGID be a security matter? • By setting UID or GID for root-owned programs. Solution: remove the s bits from root-owned programs that won't absolutely require such privilege. (or you have to have a complete knowledge of what a program can do before setting the SUID/SGID) __________ • BUT future and existing files may be set with these s bits enabled without your notification. And here we need the help of s. Xid
 What is s. Xid? • s. Xid is an all in one suid/sgid monitoring program designed to be run from cron on a regular basis. • Basically it tracks any changes in your s[ug]id files and folders. • If there any new ones, ones that aren't set any more, or they have changed bits or other modes then it reports the changes in an easy to read format via email or on the command line. • s. Xid will automate the task to find all SUID/SGID on your server and report them to you. Once installed you can forget it and it will do the job for you.
What is s. Xid? • s. Xid is an all in one suid/sgid monitoring program designed to be run from cron on a regular basis. • Basically it tracks any changes in your s[ug]id files and folders. • If there any new ones, ones that aren't set any more, or they have changed bits or other modes then it reports the changes in an easy to read format via email or on the command line. • s. Xid will automate the task to find all SUID/SGID on your server and report them to you. Once installed you can forget it and it will do the job for you.
 Installing s. Xid • • • These installation instructions assume the following: Commands are Unix compatible. The source path is /var/tmp other paths are possible. Installations were tested on Red Hat Linux 6. 1 and 6. 2. All steps in the installation will happen in super user account root. s. Xid version number as of this writing is 4. 0. 1 (Packages can be dowloaded from the s. Xid FTP Site: ftp: //marcus. seva. net/pub/sxid/ and You must be sure to download: sxid_4. 0. 1. tar. gz or whatever the latest version is. )
Installing s. Xid • • • These installation instructions assume the following: Commands are Unix compatible. The source path is /var/tmp other paths are possible. Installations were tested on Red Hat Linux 6. 1 and 6. 2. All steps in the installation will happen in super user account root. s. Xid version number as of this writing is 4. 0. 1 (Packages can be dowloaded from the s. Xid FTP Site: ftp: //marcus. seva. net/pub/sxid/ and You must be sure to download: sxid_4. 0. 1. tar. gz or whatever the latest version is. )
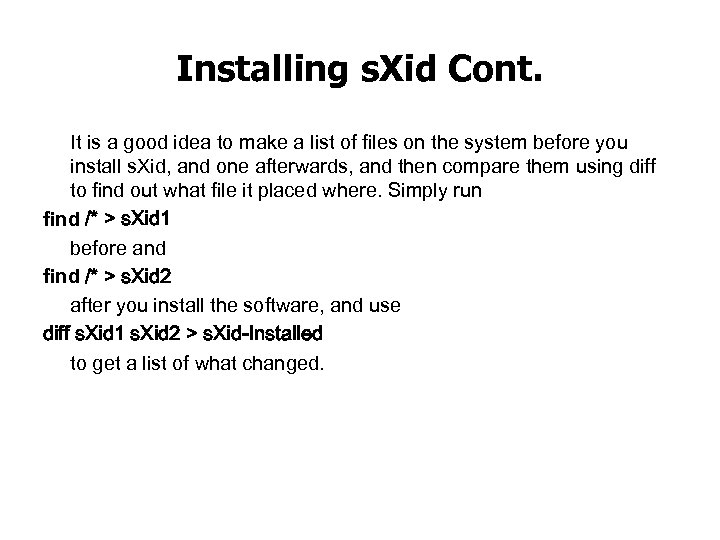 Installing s. Xid Cont. It is a good idea to make a list of files on the system before you install s. Xid, and one afterwards, and then compare them using diff to find out what file it placed where. Simply run find /* > s. Xid 1 before and find /* > s. Xid 2 after you install the software, and use diff s. Xid 1 s. Xid 2 > s. Xid-Installed to get a list of what changed.
Installing s. Xid Cont. It is a good idea to make a list of files on the system before you install s. Xid, and one afterwards, and then compare them using diff to find out what file it placed where. Simply run find /* > s. Xid 1 before and find /* > s. Xid 2 after you install the software, and use diff s. Xid 1 s. Xid 2 > s. Xid-Installed to get a list of what changed.
![Installing s. Xid Cont. • Decompress the tarball tar. gz. [root@deep] /#cp sxid_version. tar. Installing s. Xid Cont. • Decompress the tarball tar. gz. [root@deep] /#cp sxid_version. tar.](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-47.jpg) Installing s. Xid Cont. • Decompress the tarball tar. gz. [root@deep] /#cp sxid_version. tar. gz /var/tmp/ [root@deep] /#cd /var/tmp [root@deep ] /tmp#tar xzpf sxid_version. tar. gz • To Compile and Optimize move into the new s. Xid directory and type the following commands on your terminal: [root@deep tmp]#cd sxid 4. 0. 1 [root@deep ] /sxid 4. 0. 1#make install The above commands will configure the software to ensure your system has the necessary functionality and libraries to successfully compile the package
Installing s. Xid Cont. • Decompress the tarball tar. gz. [root@deep] /#cp sxid_version. tar. gz /var/tmp/ [root@deep] /#cd /var/tmp [root@deep ] /tmp#tar xzpf sxid_version. tar. gz • To Compile and Optimize move into the new s. Xid directory and type the following commands on your terminal: [root@deep tmp]#cd sxid 4. 0. 1 [root@deep ] /sxid 4. 0. 1#make install The above commands will configure the software to ensure your system has the necessary functionality and libraries to successfully compile the package
 Installing s. Xid Cont. • compile all source files into executable binaries, and then install the binaries and any supporting files into the appropriate locations. Please do a cleanup later: [root@deep] /#cd /var/tmp [root@deep ] /tmp#rm rf sxid version/ sxid_version_tar. gz The rm command as used above will remove all the source files we have used to compile and install s. Xid. It will also remove the s. Xid compressed archive from the /var/tmp directory.
Installing s. Xid Cont. • compile all source files into executable binaries, and then install the binaries and any supporting files into the appropriate locations. Please do a cleanup later: [root@deep] /#cd /var/tmp [root@deep ] /tmp#rm rf sxid version/ sxid_version_tar. gz The rm command as used above will remove all the source files we have used to compile and install s. Xid. It will also remove the s. Xid compressed archive from the /var/tmp directory.
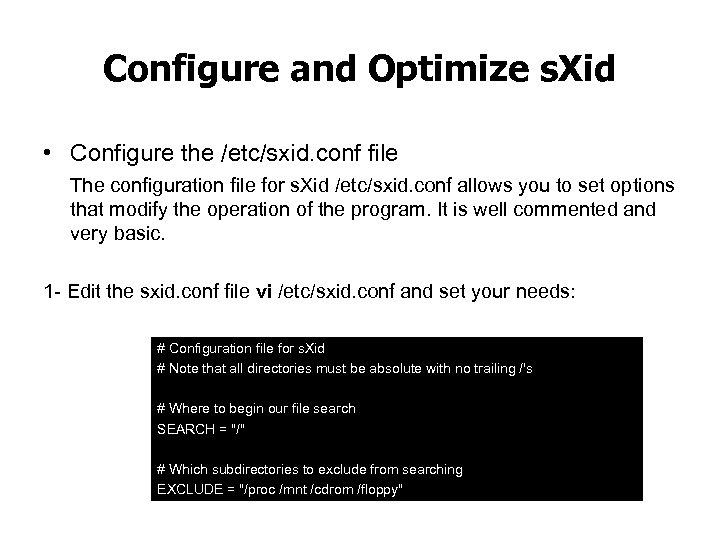 Configure and Optimize s. Xid • Configure the /etc/sxid. conf file The configuration file for s. Xid /etc/sxid. conf allows you to set options that modify the operation of the program. It is well commented and very basic. 1 Edit the sxid. conf file vi /etc/sxid. conf and set your needs: # Configuration file for s. Xid # Note that all directories must be absolute with no trailing /'s # Where to begin our file search SEARCH = "/" # Which subdirectories to exclude from searching EXCLUDE = "/proc /mnt /cdrom /floppy"
Configure and Optimize s. Xid • Configure the /etc/sxid. conf file The configuration file for s. Xid /etc/sxid. conf allows you to set options that modify the operation of the program. It is well commented and very basic. 1 Edit the sxid. conf file vi /etc/sxid. conf and set your needs: # Configuration file for s. Xid # Note that all directories must be absolute with no trailing /'s # Where to begin our file search SEARCH = "/" # Which subdirectories to exclude from searching EXCLUDE = "/proc /mnt /cdrom /floppy"
 Configure and Optimize s. Xid Cont. # Who to send reports to EMAIL = "root" # Always send reports, even when there are no changes? ALWAYS_NOTIFY = "no" # Where to keep interim logs. This will rotate 'x' number of # times based on KEEP_LOGS below LOG_FILE = "/var/log/sxid. log" # How many logs to keep KEEP_LOGS = "5" # Rotate the logs even when there are no changes? ALWAYS_ROTATE = "no" # Directories where +s is forbidden (these are searched # even if not explicitly in SEARCH), EXCLUDE rules apply FORBIDDEN = "/home /tmp"
Configure and Optimize s. Xid Cont. # Who to send reports to EMAIL = "root" # Always send reports, even when there are no changes? ALWAYS_NOTIFY = "no" # Where to keep interim logs. This will rotate 'x' number of # times based on KEEP_LOGS below LOG_FILE = "/var/log/sxid. log" # How many logs to keep KEEP_LOGS = "5" # Rotate the logs even when there are no changes? ALWAYS_ROTATE = "no" # Directories where +s is forbidden (these are searched # even if not explicitly in SEARCH), EXCLUDE rules apply FORBIDDEN = "/home /tmp"
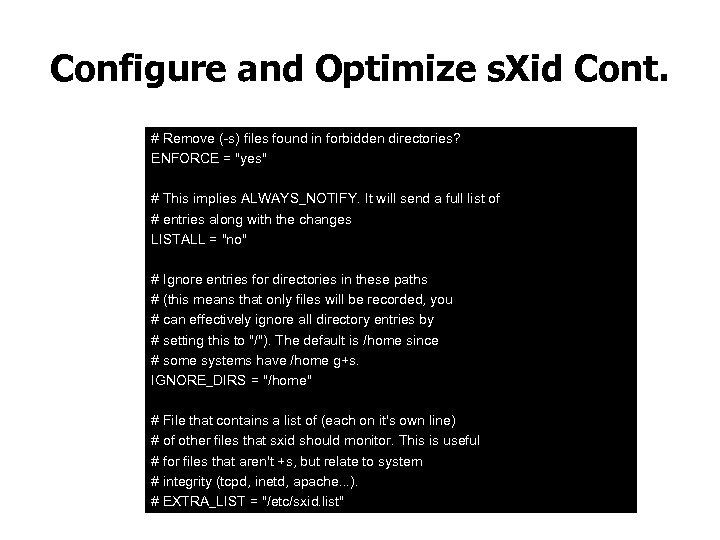 Configure and Optimize s. Xid Cont. # Remove (-s) files found in forbidden directories? ENFORCE = "yes" # This implies ALWAYS_NOTIFY. It will send a full list of # entries along with the changes LISTALL = "no" # Ignore entries for directories in these paths # (this means that only files will be recorded, you # can effectively ignore all directory entries by # setting this to "/"). The default is /home since # some systems have /home g+s. IGNORE_DIRS = "/home" # File that contains a list of (each on it's own line) # of other files that sxid should monitor. This is useful # for files that aren't +s, but relate to system # integrity (tcpd, inetd, apache. . . ). # EXTRA_LIST = "/etc/sxid. list"
Configure and Optimize s. Xid Cont. # Remove (-s) files found in forbidden directories? ENFORCE = "yes" # This implies ALWAYS_NOTIFY. It will send a full list of # entries along with the changes LISTALL = "no" # Ignore entries for directories in these paths # (this means that only files will be recorded, you # can effectively ignore all directory entries by # setting this to "/"). The default is /home since # some systems have /home g+s. IGNORE_DIRS = "/home" # File that contains a list of (each on it's own line) # of other files that sxid should monitor. This is useful # for files that aren't +s, but relate to system # integrity (tcpd, inetd, apache. . . ). # EXTRA_LIST = "/etc/sxid. list"
 Configure and Optimize s. Xid Cont. # Mail program. This changes the default compiled in # mailer for reports. You only need this if you have changed # it's location and don't want to recompile sxid. # MAIL_PROG = "/usr/bin/mail"
Configure and Optimize s. Xid Cont. # Mail program. This changes the default compiled in # mailer for reports. You only need this if you have changed # it's location and don't want to recompile sxid. # MAIL_PROG = "/usr/bin/mail"
 Configure and Optimize s. Xid Cont. 2. Place an entry into root's crontabs to make s. Xid run as a cronjob. s. Xid will run from crond; basically it tracks any changes in your s[ug]id files and folders. If there any new ones, ones that aren't set any more, or they have changed bits or other modes then it reports the changes. To add sxid in your cronjob you must edit the crontab and add the following line: To edit the crontab, use the command as root: [root@deep] /#crontab –e # Sample crontab entry to run every day at 4 am 0 4 * * * /usr/bin/sxid
Configure and Optimize s. Xid Cont. 2. Place an entry into root's crontabs to make s. Xid run as a cronjob. s. Xid will run from crond; basically it tracks any changes in your s[ug]id files and folders. If there any new ones, ones that aren't set any more, or they have changed bits or other modes then it reports the changes. To add sxid in your cronjob you must edit the crontab and add the following line: To edit the crontab, use the command as root: [root@deep] /#crontab –e # Sample crontab entry to run every day at 4 am 0 4 * * * /usr/bin/sxid
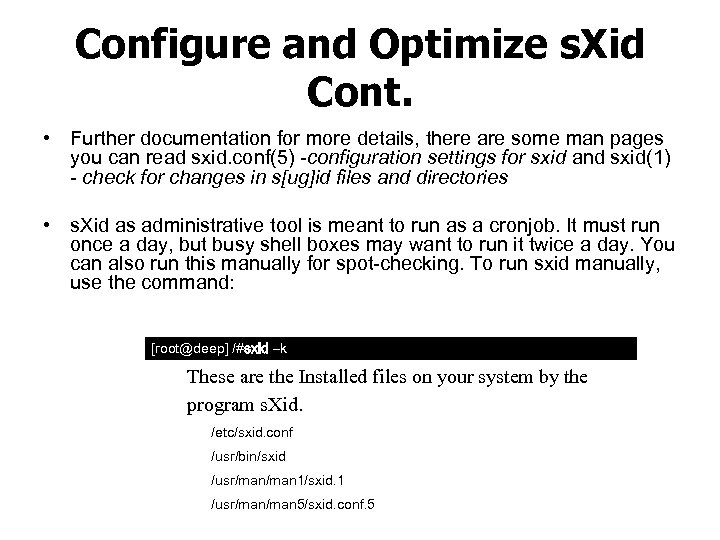 Configure and Optimize s. Xid Cont. • Further documentation for more details, there are some man pages you can read sxid. conf(5) configuration settings for sxid and sxid(1) check for changes in s[ug]id files and directories • s. Xid as administrative tool is meant to run as a cronjob. It must run once a day, but busy shell boxes may want to run it twice a day. You can also run this manually for spot checking. To run sxid manually, use the command: [root@deep] /#sxid –k These are the Installed files on your system by the program s. Xid. /etc/sxid. conf /usr/bin/sxid /usr/man 1/sxid. 1 /usr/man 5/sxid. conf. 5
Configure and Optimize s. Xid Cont. • Further documentation for more details, there are some man pages you can read sxid. conf(5) configuration settings for sxid and sxid(1) check for changes in s[ug]id files and directories • s. Xid as administrative tool is meant to run as a cronjob. It must run once a day, but busy shell boxes may want to run it twice a day. You can also run this manually for spot checking. To run sxid manually, use the command: [root@deep] /#sxid –k These are the Installed files on your system by the program s. Xid. /etc/sxid. conf /usr/bin/sxid /usr/man 1/sxid. 1 /usr/man 5/sxid. conf. 5
 Log. Check “Log. Sentry” • Auditing and logging system events is important! What is more important is that system administrators be aware of these events so they can prevent problems that will inevitably occur if you have a system connected to the Internet. • Unfortunately for most Unices it doesn't matter how much you log activity if nobody ever checks the logs, which is often the case. • This is where logcheck will help. Logcheck automates the auditing process and weeds out normal log information to give you a condensed look at problems and potential troublemakers mailed to wherever you please. • Logcheck is a software package that is designed to automatically run and check system log files for security violations and unusual activity. • Logcheck utilizes a program called logtail that remembers the last position it read from in a log file and uses this position on subsequent runs to process new information.
Log. Check “Log. Sentry” • Auditing and logging system events is important! What is more important is that system administrators be aware of these events so they can prevent problems that will inevitably occur if you have a system connected to the Internet. • Unfortunately for most Unices it doesn't matter how much you log activity if nobody ever checks the logs, which is often the case. • This is where logcheck will help. Logcheck automates the auditing process and weeds out normal log information to give you a condensed look at problems and potential troublemakers mailed to wherever you please. • Logcheck is a software package that is designed to automatically run and check system log files for security violations and unusual activity. • Logcheck utilizes a program called logtail that remembers the last position it read from in a log file and uses this position on subsequent runs to process new information.
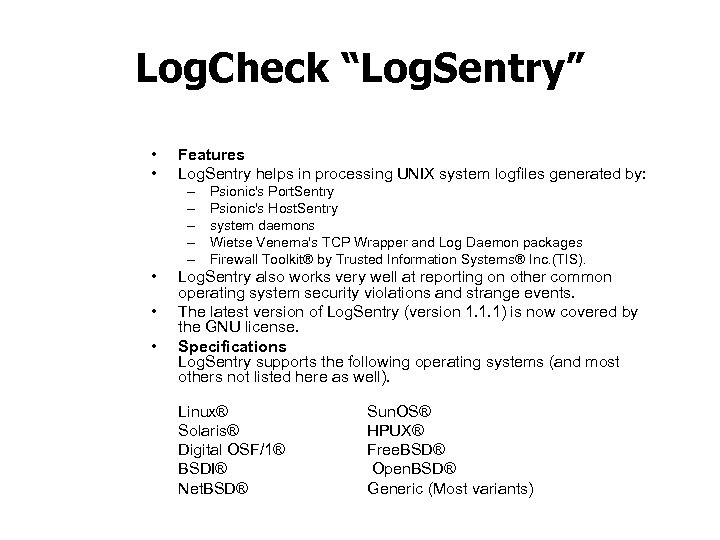 Log. Check “Log. Sentry” • • Features Log. Sentry helps in processing UNIX system logfiles generated by: – – – • • • Psionic's Port. Sentry Psionic's Host. Sentry system daemons Wietse Venema's TCP Wrapper and Log Daemon packages Firewall Toolkit® by Trusted Information Systems® Inc. (TIS). Log. Sentry also works very well at reporting on other common operating system security violations and strange events. The latest version of Log. Sentry (version 1. 1. 1) is now covered by the GNU license. Specifications Log. Sentry supports the following operating systems (and most others not listed here as well). Linux® Solaris® Digital OSF/1® BSDI® Net. BSD® Sun. OS® HPUX® Free. BSD® Open. BSD® Generic (Most variants)
Log. Check “Log. Sentry” • • Features Log. Sentry helps in processing UNIX system logfiles generated by: – – – • • • Psionic's Port. Sentry Psionic's Host. Sentry system daemons Wietse Venema's TCP Wrapper and Log Daemon packages Firewall Toolkit® by Trusted Information Systems® Inc. (TIS). Log. Sentry also works very well at reporting on other common operating system security violations and strange events. The latest version of Log. Sentry (version 1. 1. 1) is now covered by the GNU license. Specifications Log. Sentry supports the following operating systems (and most others not listed here as well). Linux® Solaris® Digital OSF/1® BSDI® Net. BSD® Sun. OS® HPUX® Free. BSD® Open. BSD® Generic (Most variants)
 Installing Log. Check These installation instructions assume • Commands are Unix compatible. • The source path is /var/tmp other paths are possible. • Installations were tested on Red Hat Linux 6. 1 and 6. 2. • All steps in the installation will happen in super user account root. • Logcheck version number is 1. 1. 1 (These are the packages available at Logcheck Homepage Site: http: //www. psionic. com/products/logsentry. html)
Installing Log. Check These installation instructions assume • Commands are Unix compatible. • The source path is /var/tmp other paths are possible. • Installations were tested on Red Hat Linux 6. 1 and 6. 2. • All steps in the installation will happen in super user account root. • Logcheck version number is 1. 1. 1 (These are the packages available at Logcheck Homepage Site: http: //www. psionic. com/products/logsentry. html)
![Installing Log. Check Cont. • Decompress the tarball tar. gz. [root@deep] /#cp logcheck_version. tar. Installing Log. Check Cont. • Decompress the tarball tar. gz. [root@deep] /#cp logcheck_version. tar.](https://present5.com/presentation/867c58e1587fdd72f3fac787dfa3ebc4/image-58.jpg) Installing Log. Check Cont. • Decompress the tarball tar. gz. [root@deep] /#cp logcheck_version. tar. gz /var/tmp/ [root@deep] /#cd /var/tmp [root@deep ] /tmp#tar xzpf logcheck_version. tar. gz To Compile and Optimize you must modify the Makefile of Logcheck to specify installation paths, compilation flags, and optimizations for your system.
Installing Log. Check Cont. • Decompress the tarball tar. gz. [root@deep] /#cp logcheck_version. tar. gz /var/tmp/ [root@deep] /#cd /var/tmp [root@deep ] /tmp#tar xzpf logcheck_version. tar. gz To Compile and Optimize you must modify the Makefile of Logcheck to specify installation paths, compilation flags, and optimizations for your system.
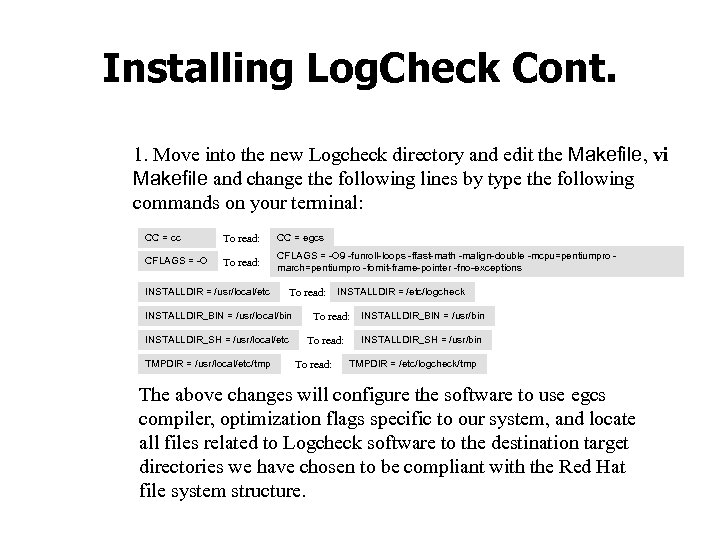 Installing Log. Check Cont. 1. Move into the new Logcheck directory and edit the Makefile, vi Makefile and change the following lines by type the following commands on your terminal: CC = cc To read: CC = egcs CFLAGS = -O To read: CFLAGS = -O 9 -funroll-loops -ffast-math -malign-double -mcpu=pentiumpro march=pentiumpro -fomit-frame-pointer -fno-exceptions INSTALLDIR = /usr/local/etc To read: INSTALLDIR_BIN = /usr/local/bin INSTALLDIR_SH = /usr/local/etc TMPDIR = /usr/local/etc/tmp INSTALLDIR = /etc/logcheck To read: INSTALLDIR_BIN = /usr/bin INSTALLDIR_SH = /usr/bin TMPDIR = /etc/logcheck/tmp The above changes will configure the software to use egcs compiler, optimization flags specific to our system, and locate all files related to Logcheck software to the destination target directories we have chosen to be compliant with the Red Hat file system structure.
Installing Log. Check Cont. 1. Move into the new Logcheck directory and edit the Makefile, vi Makefile and change the following lines by type the following commands on your terminal: CC = cc To read: CC = egcs CFLAGS = -O To read: CFLAGS = -O 9 -funroll-loops -ffast-math -malign-double -mcpu=pentiumpro march=pentiumpro -fomit-frame-pointer -fno-exceptions INSTALLDIR = /usr/local/etc To read: INSTALLDIR_BIN = /usr/local/bin INSTALLDIR_SH = /usr/local/etc TMPDIR = /usr/local/etc/tmp INSTALLDIR = /etc/logcheck To read: INSTALLDIR_BIN = /usr/bin INSTALLDIR_SH = /usr/bin TMPDIR = /etc/logcheck/tmp The above changes will configure the software to use egcs compiler, optimization flags specific to our system, and locate all files related to Logcheck software to the destination target directories we have chosen to be compliant with the Red Hat file system structure.
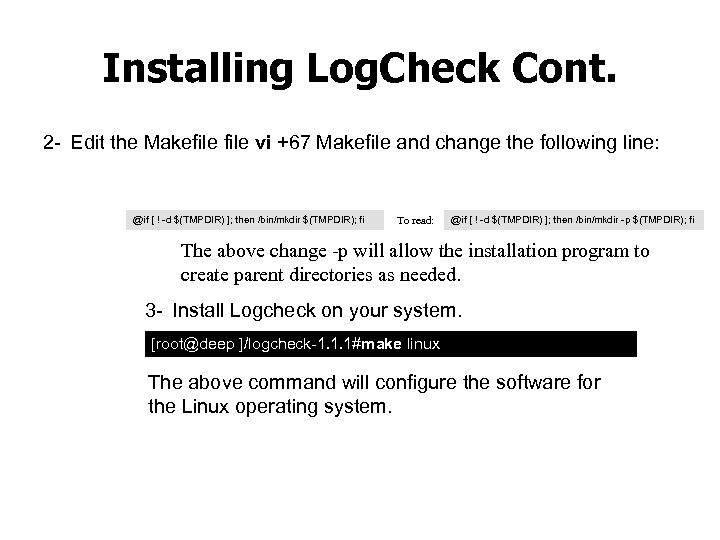 Installing Log. Check Cont. 2 Edit the Makefile vi +67 Makefile and change the following line: @if [ ! -d $(TMPDIR) ]; then /bin/mkdir $(TMPDIR); fi To read: @if [ ! -d $(TMPDIR) ]; then /bin/mkdir -p $(TMPDIR); fi The above change -p will allow the installation program to create parent directories as needed. 3 Install Logcheck on your system. [root@deep ]/logcheck 1. 1. 1#make linux The above command will configure the software for the Linux operating system.
Installing Log. Check Cont. 2 Edit the Makefile vi +67 Makefile and change the following line: @if [ ! -d $(TMPDIR) ]; then /bin/mkdir $(TMPDIR); fi To read: @if [ ! -d $(TMPDIR) ]; then /bin/mkdir -p $(TMPDIR); fi The above change -p will allow the installation program to create parent directories as needed. 3 Install Logcheck on your system. [root@deep ]/logcheck 1. 1. 1#make linux The above command will configure the software for the Linux operating system.
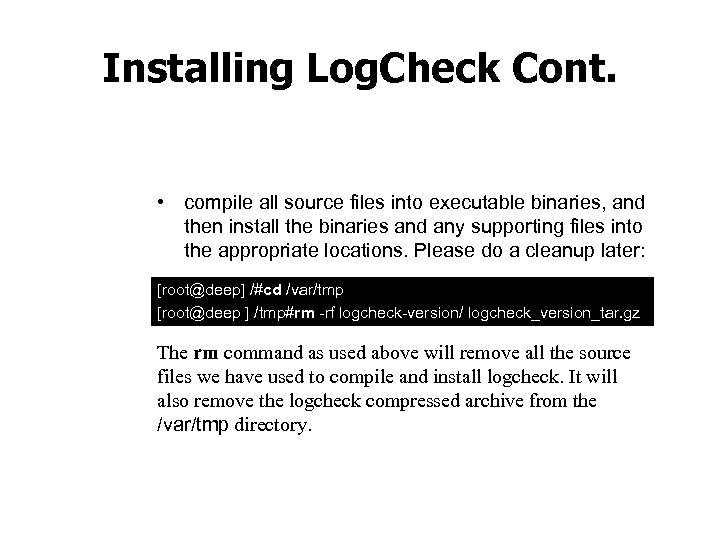 Installing Log. Check Cont. • compile all source files into executable binaries, and then install the binaries and any supporting files into the appropriate locations. Please do a cleanup later: [root@deep] /#cd /var/tmp [root@deep ] /tmp#rm rf logcheck version/ logcheck_version_tar. gz The rm command as used above will remove all the source files we have used to compile and install logcheck. It will also remove the logcheck compressed archive from the /var/tmp directory.
Installing Log. Check Cont. • compile all source files into executable binaries, and then install the binaries and any supporting files into the appropriate locations. Please do a cleanup later: [root@deep] /#cd /var/tmp [root@deep ] /tmp#rm rf logcheck version/ logcheck_version_tar. gz The rm command as used above will remove all the source files we have used to compile and install logcheck. It will also remove the logcheck compressed archive from the /var/tmp directory.
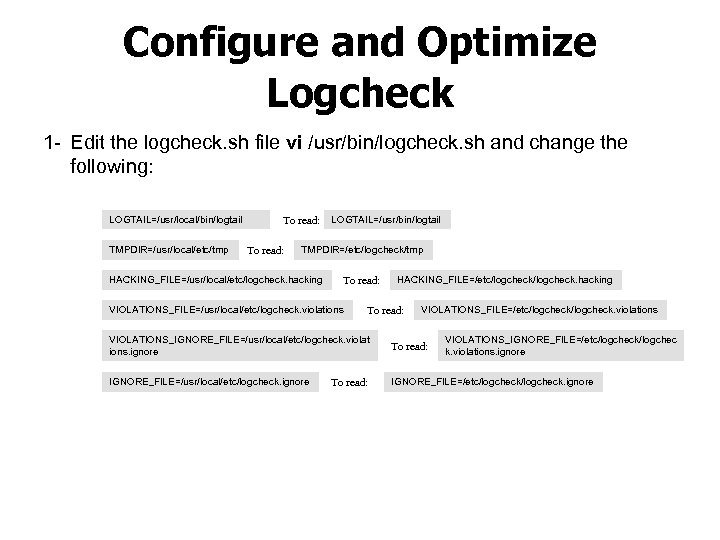 Configure and Optimize Logcheck 1 Edit the logcheck. sh file vi /usr/bin/logcheck. sh and change the following: LOGTAIL=/usr/local/bin/logtail TMPDIR=/usr/local/etc/tmp To read: LOGTAIL=/usr/bin/logtail TMPDIR=/etc/logcheck/tmp HACKING_FILE=/usr/local/etc/logcheck. hacking To read: VIOLATIONS_FILE=/usr/local/etc/logcheck. violations HACKING_FILE=/etc/logcheck. hacking To read: VIOLATIONS_FILE=/etc/logcheck. violations VIOLATIONS_IGNORE_FILE=/usr/local/etc/logcheck. violat ions. ignore To read: IGNORE_FILE=/usr/local/etc/logcheck. ignore IGNORE_FILE=/etc/logcheck. ignore To read: VIOLATIONS_IGNORE_FILE=/etc/logcheck/logchec k. violations. ignore
Configure and Optimize Logcheck 1 Edit the logcheck. sh file vi /usr/bin/logcheck. sh and change the following: LOGTAIL=/usr/local/bin/logtail TMPDIR=/usr/local/etc/tmp To read: LOGTAIL=/usr/bin/logtail TMPDIR=/etc/logcheck/tmp HACKING_FILE=/usr/local/etc/logcheck. hacking To read: VIOLATIONS_FILE=/usr/local/etc/logcheck. violations HACKING_FILE=/etc/logcheck. hacking To read: VIOLATIONS_FILE=/etc/logcheck. violations VIOLATIONS_IGNORE_FILE=/usr/local/etc/logcheck. violat ions. ignore To read: IGNORE_FILE=/usr/local/etc/logcheck. ignore IGNORE_FILE=/etc/logcheck. ignore To read: VIOLATIONS_IGNORE_FILE=/etc/logcheck/logchec k. violations. ignore
 Configure and Optimize Logcheck 2. After installing Logcheck, place an entry into root's crontabs to make Logcheck run as a cronjob, you should edit your local crontab file for root and set Logcheck to run once per hour recommended, although you can do it more frequently, or less frequently. To add Logcheck in your cronjob you must edit the crontab and add the following line as root: [root@deep] /#crontab –e # Hourly check Log files for security violations and unusual activity. 00 * * /usr/bin/logcheck. sh
Configure and Optimize Logcheck 2. After installing Logcheck, place an entry into root's crontabs to make Logcheck run as a cronjob, you should edit your local crontab file for root and set Logcheck to run once per hour recommended, although you can do it more frequently, or less frequently. To add Logcheck in your cronjob you must edit the crontab and add the following line as root: [root@deep] /#crontab –e # Hourly check Log files for security violations and unusual activity. 00 * * /usr/bin/logcheck. sh
 Configure and Optimize Logcheck Remember, Logcheck does not report anything via email if it has nothing useful to say. These are the files Installed by the program Logcheck on your sytem, for your future referance. /etc/logcheck /usr/bin/logcheck. sh /etc/logcheck/tmp /usr/bin/logtail /etc/logcheck. hacking /var/log/messages. offset /etc/logcheck. violations /var/log/secure. offset /etc/logcheck. violations. ignore /var/log/maillog. offset /etc/logcheck. ignore
Configure and Optimize Logcheck Remember, Logcheck does not report anything via email if it has nothing useful to say. These are the files Installed by the program Logcheck on your sytem, for your future referance. /etc/logcheck /usr/bin/logcheck. sh /etc/logcheck/tmp /usr/bin/logtail /etc/logcheck. hacking /var/log/messages. offset /etc/logcheck. violations /var/log/secure. offset /etc/logcheck. violations. ignore /var/log/maillog. offset /etc/logcheck. ignore
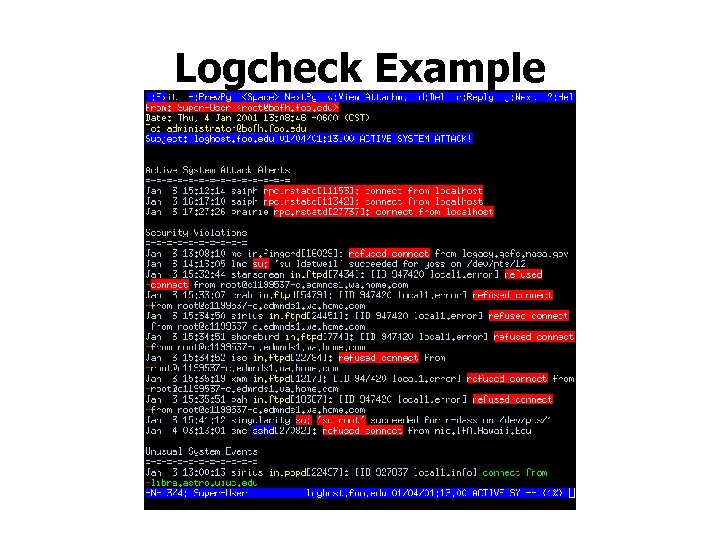 Logcheck Example
Logcheck Example
 Programs like Log. Check • colorlogs will color code log files allowing you to easily spot suspicious activity. Based on a config file it looks for keywords and colors the lines (red, cyan, etc. ), it takes input from STDIN so you can use it to review log files quickly (by using “cat”, “tail” or other utilities to feed the log file through the program). You can get it at: http: //www. resentment. org/projects/colorlogs/. • WOTS collects log files from multiple sources and will generate reports or take action based on what you tell it to do. WOTS looks for regular expressions you define and then executes the commands you list (mail a report, sound an alert, etc. ). WOTS requires you have Perl installed and is available from: http: //www. hpcc. uh. edu/~tonyc/tools/ • swatch is very similar to WOTS, and the log files configuration is very similar. You can download swatch from: ftp: //ftp. stanford. edu/general/security-tools/swatch/.
Programs like Log. Check • colorlogs will color code log files allowing you to easily spot suspicious activity. Based on a config file it looks for keywords and colors the lines (red, cyan, etc. ), it takes input from STDIN so you can use it to review log files quickly (by using “cat”, “tail” or other utilities to feed the log file through the program). You can get it at: http: //www. resentment. org/projects/colorlogs/. • WOTS collects log files from multiple sources and will generate reports or take action based on what you tell it to do. WOTS looks for regular expressions you define and then executes the commands you list (mail a report, sound an alert, etc. ). WOTS requires you have Perl installed and is available from: http: //www. hpcc. uh. edu/~tonyc/tools/ • swatch is very similar to WOTS, and the log files configuration is very similar. You can download swatch from: ftp: //ftp. stanford. edu/general/security-tools/swatch/.
 Log. Check for Windows • Win. Log. Check http: //www. jpsdomain. org/index. html? winlogcheck/winlogcheck. html Other Methods of accessing the NT Event logs (not free): • Win 2 K Server Res. Kit Perl scripts: Event. Log. pl & Event. Query. pl • NT (etc. ) Res. Kit Elogdmp. exe event log dumper
Log. Check for Windows • Win. Log. Check http: //www. jpsdomain. org/index. html? winlogcheck/winlogcheck. html Other Methods of accessing the NT Event logs (not free): • Win 2 K Server Res. Kit Perl scripts: Event. Log. pl & Event. Query. pl • NT (etc. ) Res. Kit Elogdmp. exe event log dumper
 PSIONIC Port. Sentry Alex Pezold
PSIONIC Port. Sentry Alex Pezold
 Port. Sentry • Port. Sentry is a program designed to detect and respond to port scans against a target host in real time. – Developed by PSIONIC Technologies • Other products: – Host. Sentry – Performs login anomaly detection (LAD). – Log. Sentry – Monitors system logs. – Freeware application. • http: //www. psionic. com/products/portsentry. html
Port. Sentry • Port. Sentry is a program designed to detect and respond to port scans against a target host in real time. – Developed by PSIONIC Technologies • Other products: – Host. Sentry – Performs login anomaly detection (LAD). – Log. Sentry – Monitors system logs. – Freeware application. • http: //www. psionic. com/products/portsentry. html
 Port. Sentry Features • Stealth port scan detection for all Unix and most Linux platforms. Port. Sentry will detect SYN/half open, FIN, NULL, X MAS and oddball packet stealth scans. • Port. Sentry will react to a port scan attempt by blocking the host in real time protecting your system from reconnassaince probes, auto scanners, and targeted system attacks. • Port. Sentry will report all violations to the local or remote syslog daemons indicating the system name, time of attack, attacking host IP and the TCP or UDP port a connection attempt was made to. When used in conjunction with Log. Sentry it will provide an alert to administrators through e mail.
Port. Sentry Features • Stealth port scan detection for all Unix and most Linux platforms. Port. Sentry will detect SYN/half open, FIN, NULL, X MAS and oddball packet stealth scans. • Port. Sentry will react to a port scan attempt by blocking the host in real time protecting your system from reconnassaince probes, auto scanners, and targeted system attacks. • Port. Sentry will report all violations to the local or remote syslog daemons indicating the system name, time of attack, attacking host IP and the TCP or UDP port a connection attempt was made to. When used in conjunction with Log. Sentry it will provide an alert to administrators through e mail.
 Features Continued • Once a scan is detected, your system will turn into a blackhole and disappear from the attacker. This feature stops most attacks cold. • Port. Sentry is designed to have an easy configuration and be maintenance free.
Features Continued • Once a scan is detected, your system will turn into a blackhole and disappear from the attacker. This feature stops most attacks cold. • Port. Sentry is designed to have an easy configuration and be maintenance free.
 Supported Operating Systems • • • Linux 1. x/2. x BSDI 2. x/3. x Open. BSD 2. x Free. BSD 3. x HPUX 10. 20 Solaris 2. 6+ AIX SCO Digital Unix • Net. BSD
Supported Operating Systems • • • Linux 1. x/2. x BSDI 2. x/3. x Open. BSD 2. x Free. BSD 3. x HPUX 10. 20 Solaris 2. 6+ AIX SCO Digital Unix • Net. BSD
 Port. Sentry Installation 1) Configure the following files to your liking: • • CONFIG_FILE The path to the Port. Sentry configuration file. WRAPPER_HOSTS_DENY The path and name of TCP wrapper hosts. deny file. SYSLOG_FACILITY The syslog facility for Port. Sentry to use. SYSLOG_LEVEL The syslog level to send messages.
Port. Sentry Installation 1) Configure the following files to your liking: • • CONFIG_FILE The path to the Port. Sentry configuration file. WRAPPER_HOSTS_DENY The path and name of TCP wrapper hosts. deny file. SYSLOG_FACILITY The syslog facility for Port. Sentry to use. SYSLOG_LEVEL The syslog level to send messages.
 Installation Continued 2) Configure the portsentry. conf file and configure the directives as you like. Examples of directives in this file are: • • • Interface – the interface to monitor Block UDP/TCP Scan Trigger
Installation Continued 2) Configure the portsentry. conf file and configure the directives as you like. Examples of directives in this file are: • • • Interface – the interface to monitor Block UDP/TCP Scan Trigger
 Installation Continued 3) Pull the portsentry. ignore file into your editor and add in any host you want to have ignored if it connects to a tripwired port. This should always contain at least the localhost (127. 0. 0. 1) and the IP's of the local interfaces.
Installation Continued 3) Pull the portsentry. ignore file into your editor and add in any host you want to have ignored if it connects to a tripwired port. This should always contain at least the localhost (127. 0. 0. 1) and the IP's of the local interfaces.
 Installation Continued 4) Compile. Type make and pick your system type and allow it to build and install. The default directory is /usr/local/psionic/portsentry 2. If you don't like this directory just edit the Makefile and make sure your portsentry. conf and portsentry_config. h files reflect the new path. Type “make install” after the build to have it copy files to your install directory. (Not stated in the README. install file, but you will need libpcap to successfully install this application. )
Installation Continued 4) Compile. Type make and pick your system type and allow it to build and install. The default directory is /usr/local/psionic/portsentry 2. If you don't like this directory just edit the Makefile and make sure your portsentry. conf and portsentry_config. h files reflect the new path. Type “make install” after the build to have it copy files to your install directory. (Not stated in the README. install file, but you will need libpcap to successfully install this application. )
 Run Port. Sentry and Test Install • Start Port. Sentry with the. /portsentry command from the install directory. – If you have set the install directory in your $PATH, Port. Sentry can be started from any directory. • To test the install, check the local log file for portsentry initialization messages.
Run Port. Sentry and Test Install • Start Port. Sentry with the. /portsentry command from the install directory. – If you have set the install directory in your $PATH, Port. Sentry can be started from any directory. • To test the install, check the local log file for portsentry initialization messages.
 Successful Install Message… • A successful startup looks like this: • Mar 5 21: 16: 00 nemesis portsentry[2286]: adminalert: Monitoring interface eth 0 and address: 10. 1. 1. 1 • Mar 5 21: 16: 00 nemesis portsentry[2286]: adminalert: Monitoring TCP ports: 1, 110, 143, 635, 1080 • Mar 5 21: 16: 00 nemesis portsentry[2286]: adminalert: Port. Sentry is initialized and monitoring.
Successful Install Message… • A successful startup looks like this: • Mar 5 21: 16: 00 nemesis portsentry[2286]: adminalert: Monitoring interface eth 0 and address: 10. 1. 1. 1 • Mar 5 21: 16: 00 nemesis portsentry[2286]: adminalert: Monitoring TCP ports: 1, 110, 143, 635, 1080 • Mar 5 21: 16: 00 nemesis portsentry[2286]: adminalert: Port. Sentry is initialized and monitoring.
 Configuration • Port. Sentry is a very easy tool to configure. The configuration file, portsentry. conf, has sections of commented out material which explains how each directive should be configured according to the level of security one is interested in. • Configuration directives: – Advanced Stealth Options – Blocks all traffic below port 1023 – Advanced Exclude – List of unprotected ports if using Stealth Options – Response Options – Allows TCP/UDP blocking – External commands – path to retaliation scripts
Configuration • Port. Sentry is a very easy tool to configure. The configuration file, portsentry. conf, has sections of commented out material which explains how each directive should be configured according to the level of security one is interested in. • Configuration directives: – Advanced Stealth Options – Blocks all traffic below port 1023 – Advanced Exclude – List of unprotected ports if using Stealth Options – Response Options – Allows TCP/UDP blocking – External commands – path to retaliation scripts
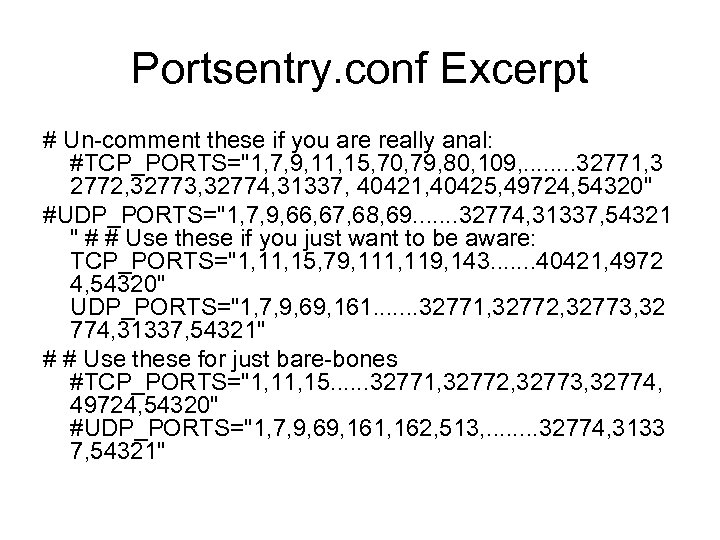 Portsentry. conf Excerpt # Un comment these if you are really anal: #TCP_PORTS="1, 7, 9, 11, 15, 70, 79, 80, 109, . . . . 32771, 3 2772, 32773, 32774, 31337, 40421, 40425, 49724, 54320" #UDP_PORTS="1, 7, 9, 66, 67, 68, 69. . . . 32774, 31337, 54321 " # # Use these if you just want to be aware: TCP_PORTS="1, 15, 79, 111, 119, 143. . . . 40421, 4972 4, 54320" UDP_PORTS="1, 7, 9, 69, 161. . . . 32771, 32772, 32773, 32 774, 31337, 54321" # # Use these for just bare bones #TCP_PORTS="1, 15. . . 32771, 32772, 32773, 32774, 49724, 54320" #UDP_PORTS="1, 7, 9, 69, 161, 162, 513, . . . . 32774, 3133 7, 54321"
Portsentry. conf Excerpt # Un comment these if you are really anal: #TCP_PORTS="1, 7, 9, 11, 15, 70, 79, 80, 109, . . . . 32771, 3 2772, 32773, 32774, 31337, 40421, 40425, 49724, 54320" #UDP_PORTS="1, 7, 9, 66, 67, 68, 69. . . . 32774, 31337, 54321 " # # Use these if you just want to be aware: TCP_PORTS="1, 15, 79, 111, 119, 143. . . . 40421, 4972 4, 54320" UDP_PORTS="1, 7, 9, 69, 161. . . . 32771, 32772, 32773, 32 774, 31337, 54321" # # Use these for just bare bones #TCP_PORTS="1, 15. . . 32771, 32772, 32773, 32774, 49724, 54320" #UDP_PORTS="1, 7, 9, 69, 161, 162, 513, . . . . 32774, 3133 7, 54321"
 Other Configuration Files • Ignore_file The file where you might list IP numbers of machines you allow in, unmolested. • History_file This is a running history of banned addresses that have been tied to knob rattling in your piece of the network. • Blocked_file This file is a list of addresses that have been banned just since portsentry was activated, this time around.
Other Configuration Files • Ignore_file The file where you might list IP numbers of machines you allow in, unmolested. • History_file This is a running history of banned addresses that have been tied to knob rattling in your piece of the network. • Blocked_file This file is a list of addresses that have been banned just since portsentry was activated, this time around.
 Port. Sentry will currently detect… • • Strobe style scans (full connect() scans) SYN/Half open scans. FIN scans. NULL scans. XMAS scans. UDP scans (not really stealth scans per se) Any odd ball packet with flags not matching the above.
Port. Sentry will currently detect… • • Strobe style scans (full connect() scans) SYN/Half open scans. FIN scans. NULL scans. XMAS scans. UDP scans (not really stealth scans per se) Any odd ball packet with flags not matching the above.
 And then produce a message like… • adminalert: Some message indicating the status of the Port. Sentry. • securityalert: A message indicating a security relevant event occurred. • attackalert: A host has tripped a sensor and an action was performed. • Yourscrewed: A message to inform you that it’s to late, don’t worry about it anymore. Just kidding, not a real message.
And then produce a message like… • adminalert: Some message indicating the status of the Port. Sentry. • securityalert: A message indicating a security relevant event occurred. • attackalert: A host has tripped a sensor and an action was performed. • Yourscrewed: A message to inform you that it’s to late, don’t worry about it anymore. Just kidding, not a real message.
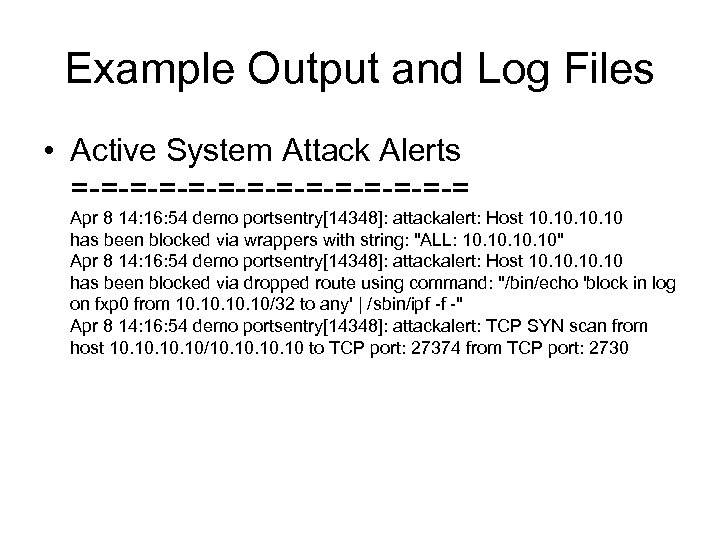 Example Output and Log Files • Active System Attack Alerts = = = = Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via wrappers with string: "ALL: 10. 10. 10" Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via dropped route using command: "/bin/echo 'block in log on fxp 0 from 10. 10. 10/32 to any' | /sbin/ipf f " Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: TCP SYN scan from host 10. 10. 10/10. 10. 10 to TCP port: 27374 from TCP port: 2730
Example Output and Log Files • Active System Attack Alerts = = = = Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via wrappers with string: "ALL: 10. 10. 10" Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via dropped route using command: "/bin/echo 'block in log on fxp 0 from 10. 10. 10/32 to any' | /sbin/ipf f " Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: TCP SYN scan from host 10. 10. 10/10. 10. 10 to TCP port: 27374 from TCP port: 2730
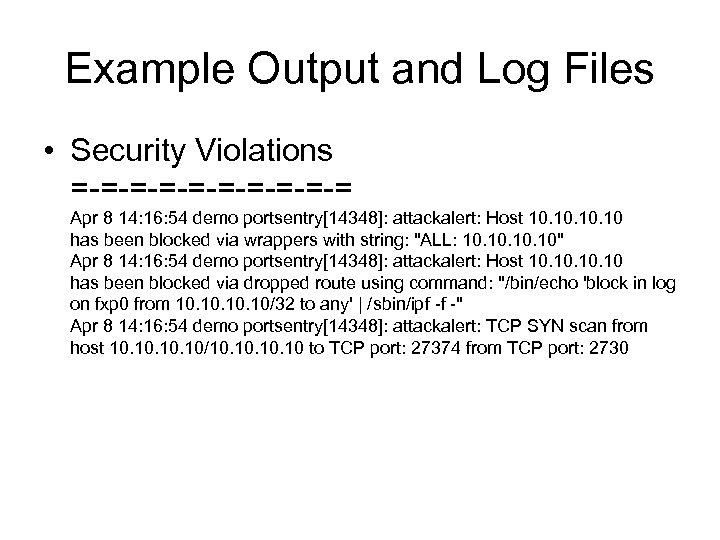 Example Output and Log Files • Security Violations = = = = = Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via wrappers with string: "ALL: 10. 10. 10" Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via dropped route using command: "/bin/echo 'block in log on fxp 0 from 10. 10. 10/32 to any' | /sbin/ipf f " Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: TCP SYN scan from host 10. 10. 10/10. 10. 10 to TCP port: 27374 from TCP port: 2730
Example Output and Log Files • Security Violations = = = = = Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via wrappers with string: "ALL: 10. 10. 10" Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via dropped route using command: "/bin/echo 'block in log on fxp 0 from 10. 10. 10/32 to any' | /sbin/ipf f " Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: TCP SYN scan from host 10. 10. 10/10. 10. 10 to TCP port: 27374 from TCP port: 2730
 More Log Examples… • Unusual System Events = = = Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via wrappers with string: "ALL: 10. 10. 10" Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via dropped route using command: "/bin/echo 'block in log on fxp 0 from 10. 10. 10/32 to any' | /sbin/ipf f " Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: TCP SYN scan from host 10. 10. 10/10. 10. 10 to TCP port: 27374 from TCP port: 2730 Apr 8 14: 16: 55 demo ipmon[3687]: 14: 16: 55. 365135 fxp 0 @0: 4 b 10. 10. 10, 2730 > 192. 168. 1. 1, 27374 PR tcp len 20 48 S IN Apr 8 14: 17: 01 demo ipmon[3687]: 14: 17: 01. 365964 fxp 0 @0: 4 b 10. 10. 10, 2730 > 192. 168. 1. 1, 27374 PR tcp len 20 48 S IN Apr 8 14: 17: 13 demo ipmon[3687]: 14: 17: 13. 396291 fxp 0 @0: 4 b 10. 10. 10, 2730 > 192. 168. 1. 1, 27374 PR tcp len 20 48 S IN
More Log Examples… • Unusual System Events = = = Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via wrappers with string: "ALL: 10. 10. 10" Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: Host 10. 10. 10 has been blocked via dropped route using command: "/bin/echo 'block in log on fxp 0 from 10. 10. 10/32 to any' | /sbin/ipf f " Apr 8 14: 16: 54 demo portsentry[14348]: attackalert: TCP SYN scan from host 10. 10. 10/10. 10. 10 to TCP port: 27374 from TCP port: 2730 Apr 8 14: 16: 55 demo ipmon[3687]: 14: 16: 55. 365135 fxp 0 @0: 4 b 10. 10. 10, 2730 > 192. 168. 1. 1, 27374 PR tcp len 20 48 S IN Apr 8 14: 17: 01 demo ipmon[3687]: 14: 17: 01. 365964 fxp 0 @0: 4 b 10. 10. 10, 2730 > 192. 168. 1. 1, 27374 PR tcp len 20 48 S IN Apr 8 14: 17: 13 demo ipmon[3687]: 14: 17: 13. 396291 fxp 0 @0: 4 b 10. 10. 10, 2730 > 192. 168. 1. 1, 27374 PR tcp len 20 48 S IN
 Warnings and Cautions. . . • One warning documented concerning Port. Sentry concerns IP spoofing. • Consider the following: – it is possible that an attacker can forge packets to appear from any host and can use this to trick Port. Sentry into activating against the forged host IP. This can cause a variety of problems in theory such as blocking gateways or name servers.
Warnings and Cautions. . . • One warning documented concerning Port. Sentry concerns IP spoofing. • Consider the following: – it is possible that an attacker can forge packets to appear from any host and can use this to trick Port. Sentry into activating against the forged host IP. This can cause a variety of problems in theory such as blocking gateways or name servers.
 Resolution? • Port. Sentry does not really have a software resolution for this issue. However, they do have reasoned logic for why it will not happen: – The resolution basically states that someone trying to scan your computer is not going to send numerous amounts of unneeded packets for fear of being detected. Also, spraying X number of packets at a system will only slow down your scan; thus, negating the point of a “stealth” attack. – They do state that this is not a “risk – free” software, but they go on to say that the likelihood of something like the above happening is very small.
Resolution? • Port. Sentry does not really have a software resolution for this issue. However, they do have reasoned logic for why it will not happen: – The resolution basically states that someone trying to scan your computer is not going to send numerous amounts of unneeded packets for fear of being detected. Also, spraying X number of packets at a system will only slow down your scan; thus, negating the point of a “stealth” attack. – They do state that this is not a “risk – free” software, but they go on to say that the likelihood of something like the above happening is very small.
 Port. Sentry Benefits • Freeware • Easy to configure • Provides detailed logs which can be made sense of • Did I mention that it’s free • Can be integrated with other PSIONIC tools, such as: Log. Check and Host. Sentry, to provide an all in one IDS application • Open source application • By the way, it’s free
Port. Sentry Benefits • Freeware • Easy to configure • Provides detailed logs which can be made sense of • Did I mention that it’s free • Can be integrated with other PSIONIC tools, such as: Log. Check and Host. Sentry, to provide an all in one IDS application • Open source application • By the way, it’s free
 Presentation Conclusion • Use of these tools, as well as other freeware tools will make securing your system easier as well as provide functionality which is not offered by standard system security tools. • There are probably 100 more tools where these came from, but make sure and research of these each tools before using them. Some of them can actually harm systems more than help them.
Presentation Conclusion • Use of these tools, as well as other freeware tools will make securing your system easier as well as provide functionality which is not offered by standard system security tools. • There are probably 100 more tools where these came from, but make sure and research of these each tools before using them. Some of them can actually harm systems more than help them.
 Questions, otherwise… • A symbolic dance reenacting the Louisiana Purchase by Dr. Shenoi • A discussion of the aerodynamics of hood ornaments by Dr. Hale
Questions, otherwise… • A symbolic dance reenacting the Louisiana Purchase by Dr. Shenoi • A discussion of the aerodynamics of hood ornaments by Dr. Hale


