ecff9c7a2292d9ba15b2e173f73c07e1.ppt
- Количество слайдов: 16
 Secure Shell – SSH Tam Ngo Steve Licking cs 265
Secure Shell – SSH Tam Ngo Steve Licking cs 265
 Overview ¢ Introduction Brief History and Background of SSH l Differences between SSH-1 and SSH 2 l Brief Overview of how SSH works l ¢ Attack on SSH l ¢ Key-Stroke Timing Attack Conclusion
Overview ¢ Introduction Brief History and Background of SSH l Differences between SSH-1 and SSH 2 l Brief Overview of how SSH works l ¢ Attack on SSH l ¢ Key-Stroke Timing Attack Conclusion
 History and Background Password-sniffing attack ¢ SSH-1 was developed, Finland, 1995 ¢ SSH Communications Security Ltd. ¢ Replacement for telnet and rcommands ¢ Version 2, SSH-2 released in 1998 ¢
History and Background Password-sniffing attack ¢ SSH-1 was developed, Finland, 1995 ¢ SSH Communications Security Ltd. ¢ Replacement for telnet and rcommands ¢ Version 2, SSH-2 released in 1998 ¢
 SSH-1 vs. SSH-2 ¢ ¢ ¢ All in one protocol CRC-32 integrity check One session per connection No password change No public-key certificate authentication ¢ ¢ ¢ Separate protocols Strong integrity check Multiple sessions per connection Password change provide public-key certificate authentication
SSH-1 vs. SSH-2 ¢ ¢ ¢ All in one protocol CRC-32 integrity check One session per connection No password change No public-key certificate authentication ¢ ¢ ¢ Separate protocols Strong integrity check Multiple sessions per connection Password change provide public-key certificate authentication
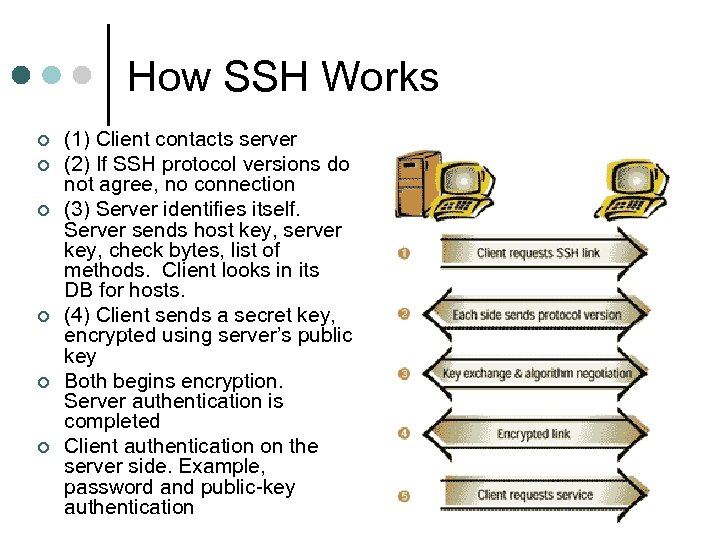 How SSH Works ¢ ¢ ¢ (1) Client contacts server (2) If SSH protocol versions do not agree, no connection (3) Server identifies itself. Server sends host key, server key, check bytes, list of methods. Client looks in its DB for hosts. (4) Client sends a secret key, encrypted using server’s public key Both begins encryption. Server authentication is completed Client authentication on the server side. Example, password and public-key authentication
How SSH Works ¢ ¢ ¢ (1) Client contacts server (2) If SSH protocol versions do not agree, no connection (3) Server identifies itself. Server sends host key, server key, check bytes, list of methods. Client looks in its DB for hosts. (4) Client sends a secret key, encrypted using server’s public key Both begins encryption. Server authentication is completed Client authentication on the server side. Example, password and public-key authentication
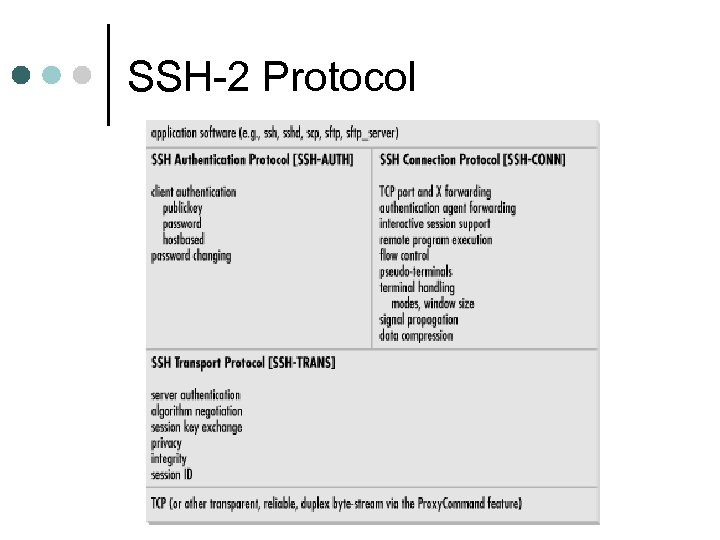 SSH-2 Protocol
SSH-2 Protocol
 SSH 2’s “Secure” Channel What SSH does: What it means: ¢ Packets are padded ¢ Data size can be up to the first 8 byte estimated multiple ¢ Keystroke timing is ¢ Input is sent as feasible each key-down is read ¢ Password sessions ¢ Not all input is are identifiable echoed by the server
SSH 2’s “Secure” Channel What SSH does: What it means: ¢ Packets are padded ¢ Data size can be up to the first 8 byte estimated multiple ¢ Keystroke timing is ¢ Input is sent as feasible each key-down is read ¢ Password sessions ¢ Not all input is are identifiable echoed by the server
 Identifying Password Transfers Doesn’t SSH transfer passwords all at once? Yes, but… ¢ Only when logging into the server ¢ Not when running any applications (e. g. su) l Not when chaining logins l
Identifying Password Transfers Doesn’t SSH transfer passwords all at once? Yes, but… ¢ Only when logging into the server ¢ Not when running any applications (e. g. su) l Not when chaining logins l
 Is this Useful? ¢ ¢ Everything is encrypted, more information is required than just a password What good is a password if you don’t know the host/user/application it is for Attackers can sniff traffic to determine the host it is destined for With access to the ps command attackers can narrow it down to a user running a specific application
Is this Useful? ¢ ¢ Everything is encrypted, more information is required than just a password What good is a password if you don’t know the host/user/application it is for Attackers can sniff traffic to determine the host it is destined for With access to the ps command attackers can narrow it down to a user running a specific application
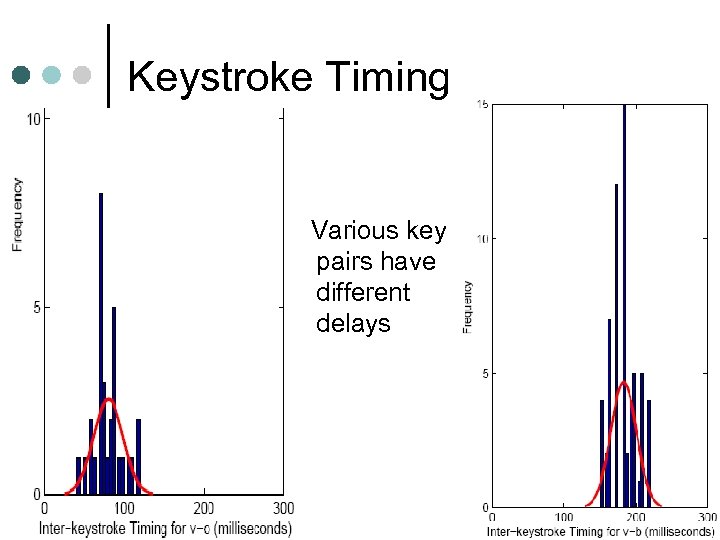 Keystroke Timing Various key pairs have different delays
Keystroke Timing Various key pairs have different delays
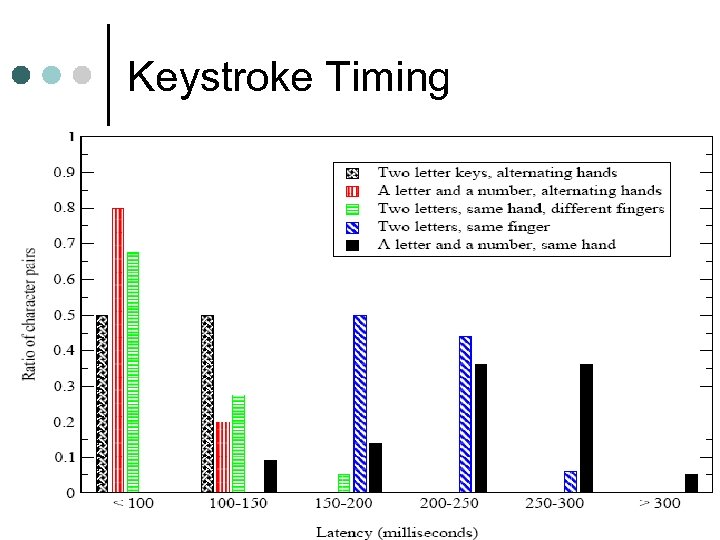 Keystroke Timing
Keystroke Timing
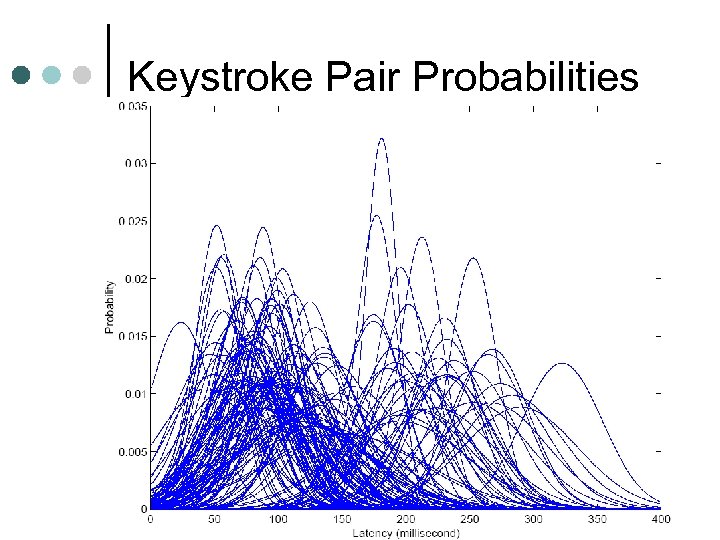 Keystroke Pair Probabilities
Keystroke Pair Probabilities
 Hidden Markov Model ¢ ¢ ¢ State machine The current state cannot be observed, only the output Transition to next state depends only on current state The likely state path can be deduced from observed output Let each state be a key pair and the output be the delay between the two key presses
Hidden Markov Model ¢ ¢ ¢ State machine The current state cannot be observed, only the output Transition to next state depends only on current state The likely state path can be deduced from observed output Let each state be a key pair and the output be the delay between the two key presses
 Does It Work The HMM can be solved using known algorithms to find a likely solution ¢ The large amount of guesswork involved means the most likely solution isn’t always the correct one ¢ Instead look at the n most likely solutions ¢
Does It Work The HMM can be solved using known algorithms to find a likely solution ¢ The large amount of guesswork involved means the most likely solution isn’t always the correct one ¢ Instead look at the n most likely solutions ¢
 Does It Work Given a subset of all possible 8 character random passwords ¢ This method can reduce work by a factor of 50 ¢ Translates to roughly 1 bit per character entered ¢
Does It Work Given a subset of all possible 8 character random passwords ¢ This method can reduce work by a factor of 50 ¢ Translates to roughly 1 bit per character entered ¢
 Does It Work ¢ Can timing information be collected? l ¢ Are the timing metrics useful if the user creating them isn’t pre-tested? l ¢ Yes Is it feasible to use a HMM to crack passwords? l Depends on who you ask
Does It Work ¢ Can timing information be collected? l ¢ Are the timing metrics useful if the user creating them isn’t pre-tested? l ¢ Yes Is it feasible to use a HMM to crack passwords? l Depends on who you ask


