c14a57b54b86b62bc294bb533e47c081.ppt
- Количество слайдов: 36
 Secure Routing in Wireless Sensor Networks : Attacks and Countermeasures Authors: Chris Karlof and David Wagner Presenter: Ivanka Todorova 1
Secure Routing in Wireless Sensor Networks : Attacks and Countermeasures Authors: Chris Karlof and David Wagner Presenter: Ivanka Todorova 1
 Outline n n n n Introduction and Contributions Background Sensor vs. ad-hoc wireless networks Problem Statement Attacks on sensor network routing Attacks on specific sensor network protocols Countermeasures Conclusions 2
Outline n n n n Introduction and Contributions Background Sensor vs. ad-hoc wireless networks Problem Statement Attacks on sensor network routing Attacks on specific sensor network protocols Countermeasures Conclusions 2
 Introduction and Contributions n n Threat models and security goals for routing in WSNs Two new attacks q q n n n Sinkhole attacks HELLO floods How to adapt attacks against ad-hoc wireless networks into powerful attacks against WSNs Practical attacks against routing protocols and topology maintenance algorithms for WSNs Countermeasures and design considerations for secure routing protocols in WSNs 3
Introduction and Contributions n n Threat models and security goals for routing in WSNs Two new attacks q q n n n Sinkhole attacks HELLO floods How to adapt attacks against ad-hoc wireless networks into powerful attacks against WSNs Practical attacks against routing protocols and topology maintenance algorithms for WSNs Countermeasures and design considerations for secure routing protocols in WSNs 3
 Background n n WSNs consist of hundreds or thousands of low-power, low-cost nodes having a CPU, power source, radio, and other sensing elements Have one or more points of centralized control called base stations or sinks Sensor readings from multiple nodes processed at aggregation points Power is the scarcest resource 4
Background n n WSNs consist of hundreds or thousands of low-power, low-cost nodes having a CPU, power source, radio, and other sensing elements Have one or more points of centralized control called base stations or sinks Sensor readings from multiple nodes processed at aggregation points Power is the scarcest resource 4
![Background n A representative sensor network architecture Picture from [7] 5 Background n A representative sensor network architecture Picture from [7] 5](https://present5.com/presentation/c14a57b54b86b62bc294bb533e47c081/image-5.jpg) Background n A representative sensor network architecture Picture from [7] 5
Background n A representative sensor network architecture Picture from [7] 5
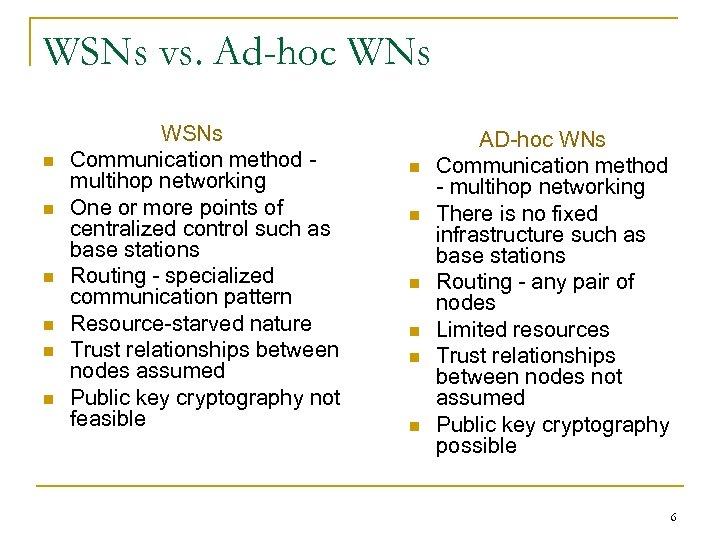 WSNs vs. Ad-hoc WNs n n n WSNs Communication method - multihop networking One or more points of centralized control such as base stations Routing - specialized communication pattern Resource-starved nature Trust relationships between nodes assumed Public key cryptography not feasible n n n AD-hoc WNs Communication method - multihop networking There is no fixed infrastructure such as base stations Routing - any pair of nodes Limited resources Trust relationships between nodes not assumed Public key cryptography possible 6
WSNs vs. Ad-hoc WNs n n n WSNs Communication method - multihop networking One or more points of centralized control such as base stations Routing - specialized communication pattern Resource-starved nature Trust relationships between nodes assumed Public key cryptography not feasible n n n AD-hoc WNs Communication method - multihop networking There is no fixed infrastructure such as base stations Routing - any pair of nodes Limited resources Trust relationships between nodes not assumed Public key cryptography possible 6
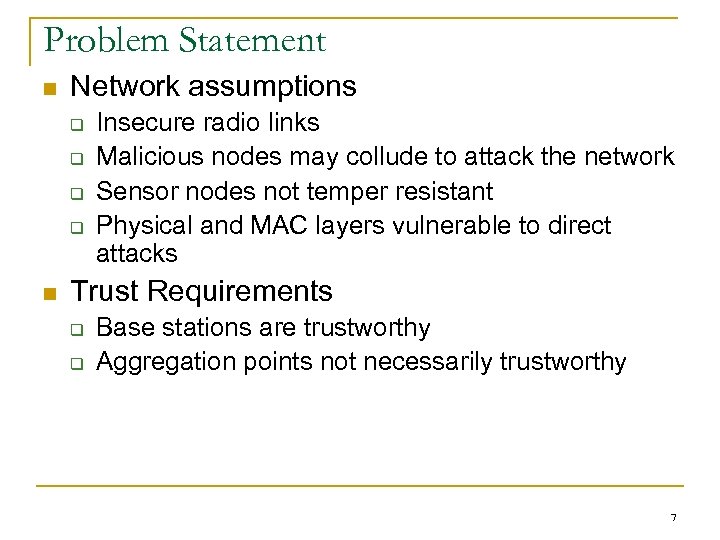 Problem Statement n Network assumptions q q n Insecure radio links Malicious nodes may collude to attack the network Sensor nodes not temper resistant Physical and MAC layers vulnerable to direct attacks Trust Requirements q q Base stations are trustworthy Aggregation points not necessarily trustworthy 7
Problem Statement n Network assumptions q q n Insecure radio links Malicious nodes may collude to attack the network Sensor nodes not temper resistant Physical and MAC layers vulnerable to direct attacks Trust Requirements q q Base stations are trustworthy Aggregation points not necessarily trustworthy 7
 Problem Statement cont’d n n Two types of threat models Based on type of attacking devices q q n Based on attacker location q q n Mote-class attackers Laptop-class attackers Outsider attacks Insider attacks Security goals q Confidentiality, integrity, authenticity, and availability of all messages 8
Problem Statement cont’d n n Two types of threat models Based on type of attacking devices q q n Based on attacker location q q n Mote-class attackers Laptop-class attackers Outsider attacks Insider attacks Security goals q Confidentiality, integrity, authenticity, and availability of all messages 8
 Attacks on sensor network routing n n n Spoofed, altered, or replayed routing information Selective forwarding Sinkhole attacks q q q Adversary’s goal is to lure traffic through a compromised node Work by making the compromised node look attractive Makes selective forwarding trivial 9
Attacks on sensor network routing n n n Spoofed, altered, or replayed routing information Selective forwarding Sinkhole attacks q q q Adversary’s goal is to lure traffic through a compromised node Work by making the compromised node look attractive Makes selective forwarding trivial 9
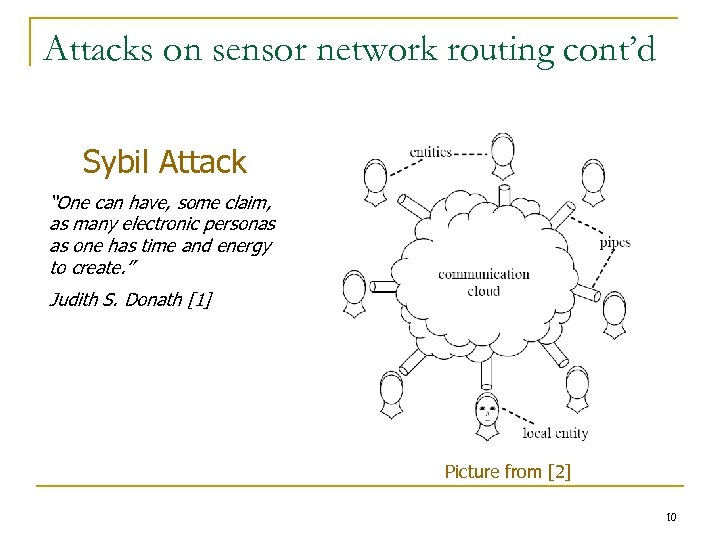 Attacks on sensor network routing cont’d Sybil Attack “One can have, some claim, as many electronic personas as one has time and energy to create. ” Judith S. Donath [1] Picture from [2] 10
Attacks on sensor network routing cont’d Sybil Attack “One can have, some claim, as many electronic personas as one has time and energy to create. ” Judith S. Donath [1] Picture from [2] 10
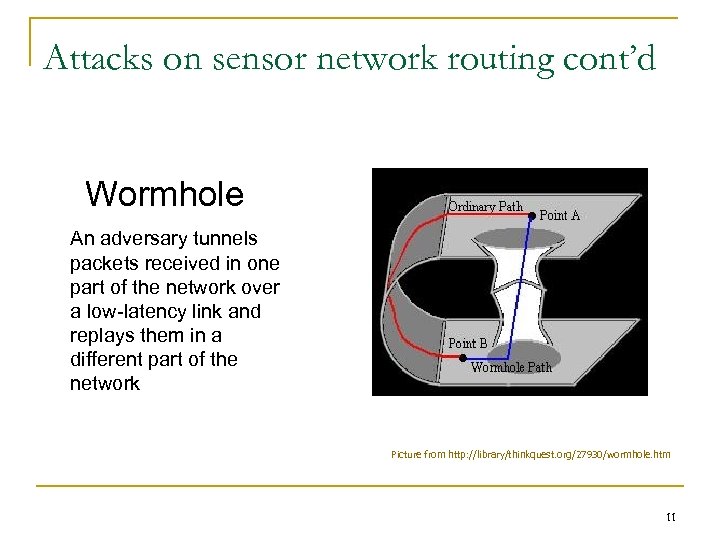 Attacks on sensor network routing cont’d Wormhole An adversary tunnels packets received in one part of the network over a low-latency link and replays them in a different part of the network Picture from http: //library/thinkquest. org/27930/wormhole. htm 11
Attacks on sensor network routing cont’d Wormhole An adversary tunnels packets received in one part of the network over a low-latency link and replays them in a different part of the network Picture from http: //library/thinkquest. org/27930/wormhole. htm 11
 Attacks on sensor network routing cont’d n HELLO flood attack q q n Many protocols require that nodes broadcast HELLO packets to announce themselves to their neighbors Laptop-class attacker can convince all nodes that it is their neighbor by transmitting at high power Acknowledgement spoofing 12
Attacks on sensor network routing cont’d n HELLO flood attack q q n Many protocols require that nodes broadcast HELLO packets to announce themselves to their neighbors Laptop-class attacker can convince all nodes that it is their neighbor by transmitting at high power Acknowledgement spoofing 12
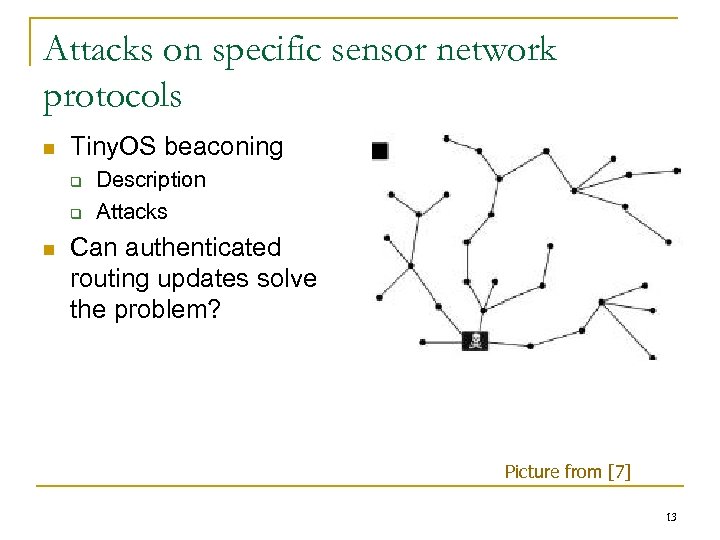 Attacks on specific sensor network protocols n Tiny. OS beaconing q q n Description Attacks Can authenticated routing updates solve the problem? Picture from [7] 13
Attacks on specific sensor network protocols n Tiny. OS beaconing q q n Description Attacks Can authenticated routing updates solve the problem? Picture from [7] 13
![Attacks on specific sensor network protocols cont’d n Combined wormhole/sinkhole attack Picture from [7] Attacks on specific sensor network protocols cont’d n Combined wormhole/sinkhole attack Picture from [7]](https://present5.com/presentation/c14a57b54b86b62bc294bb533e47c081/image-14.jpg) Attacks on specific sensor network protocols cont’d n Combined wormhole/sinkhole attack Picture from [7] 14
Attacks on specific sensor network protocols cont’d n Combined wormhole/sinkhole attack Picture from [7] 14
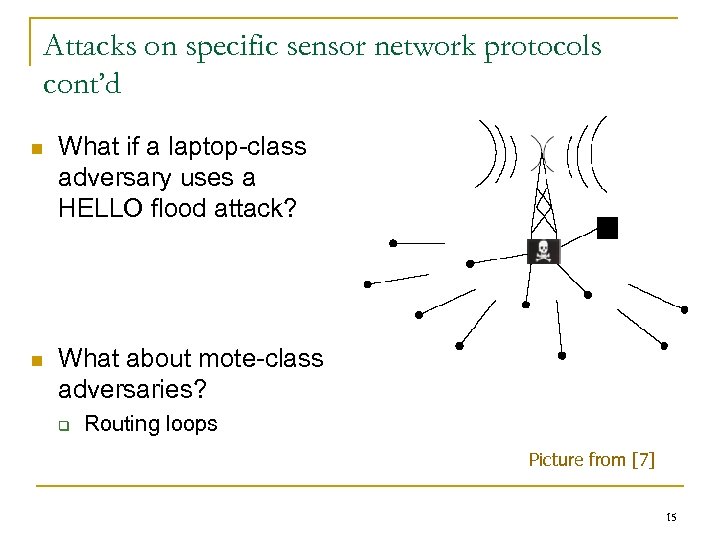 Attacks on specific sensor network protocols cont’d n What if a laptop-class adversary uses a HELLO flood attack? n What about mote-class adversaries? q Routing loops Picture from [7] 15
Attacks on specific sensor network protocols cont’d n What if a laptop-class adversary uses a HELLO flood attack? n What about mote-class adversaries? q Routing loops Picture from [7] 15
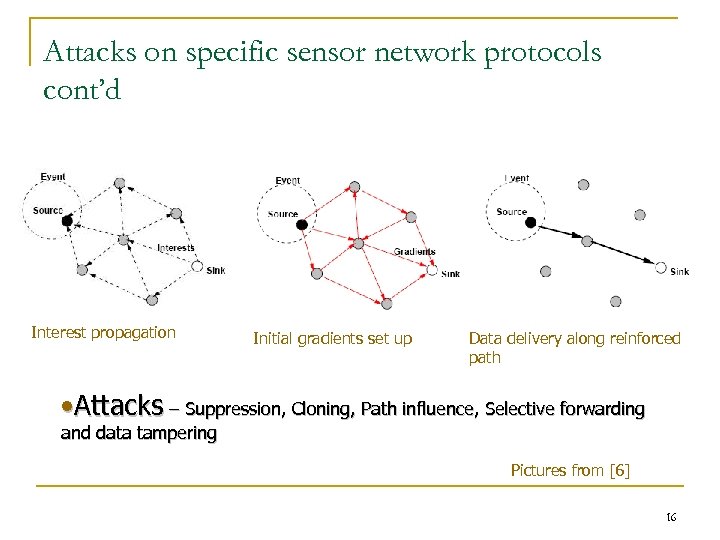 Attacks on specific sensor network protocols cont’d Interest propagation Initial gradients set up Data delivery along reinforced path • Attacks – Suppression, Cloning, Path influence, Selective forwarding and data tampering Pictures from [6] 16
Attacks on specific sensor network protocols cont’d Interest propagation Initial gradients set up Data delivery along reinforced path • Attacks – Suppression, Cloning, Path influence, Selective forwarding and data tampering Pictures from [6] 16
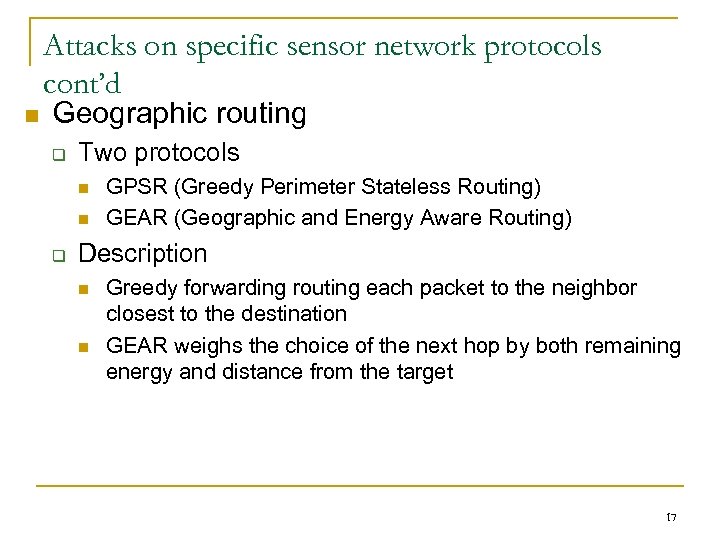 Attacks on specific sensor network protocols cont’d n Geographic routing q Two protocols n n q GPSR (Greedy Perimeter Stateless Routing) GEAR (Geographic and Energy Aware Routing) Description n n Greedy forwarding routing each packet to the neighbor closest to the destination GEAR weighs the choice of the next hop by both remaining energy and distance from the target 17
Attacks on specific sensor network protocols cont’d n Geographic routing q Two protocols n n q GPSR (Greedy Perimeter Stateless Routing) GEAR (Geographic and Energy Aware Routing) Description n n Greedy forwarding routing each packet to the neighbor closest to the destination GEAR weighs the choice of the next hop by both remaining energy and distance from the target 17
 Attacks on specific sensor network protocols cont’d n Geographic routing Greedy forwarding example: y is x’s closest neighbor to D Greedy forwarding failure: x is a local maximum in its geographic proximity to D; w and y are farther from D. Pictures from [14] 18
Attacks on specific sensor network protocols cont’d n Geographic routing Greedy forwarding example: y is x’s closest neighbor to D Greedy forwarding failure: x is a local maximum in its geographic proximity to D; w and y are farther from D. Pictures from [14] 18
 Attacks on specific sensor network protocols cont’d n Geographic routing Node x’s void with respect to destination D. Picture from [14] 19
Attacks on specific sensor network protocols cont’d n Geographic routing Node x’s void with respect to destination D. Picture from [14] 19
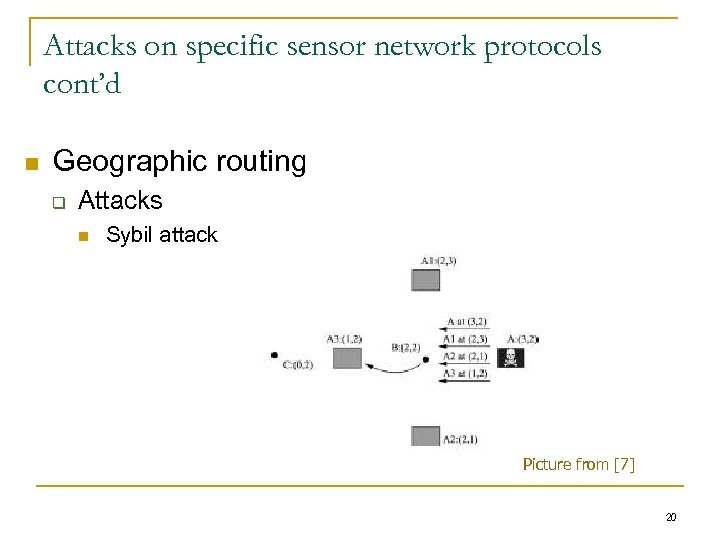 Attacks on specific sensor network protocols cont’d n Geographic routing q Attacks n Sybil attack Picture from [7] 20
Attacks on specific sensor network protocols cont’d n Geographic routing q Attacks n Sybil attack Picture from [7] 20
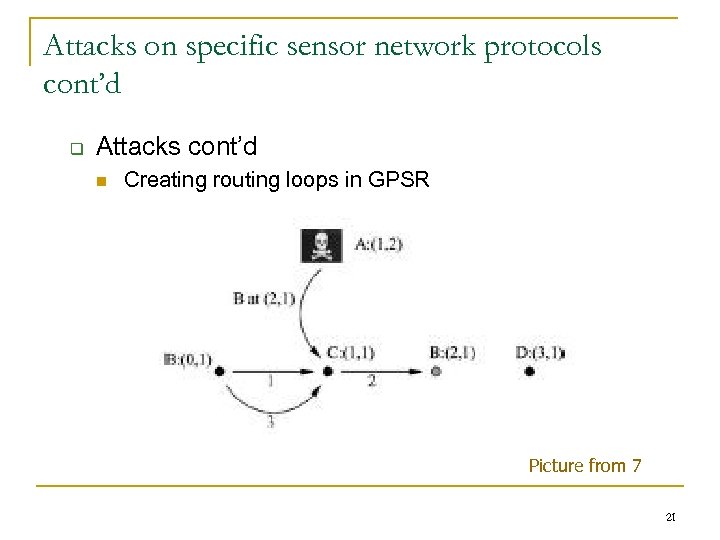 Attacks on specific sensor network protocols cont’d q Attacks cont’d n Creating routing loops in GPSR Picture from 7 21
Attacks on specific sensor network protocols cont’d q Attacks cont’d n Creating routing loops in GPSR Picture from 7 21
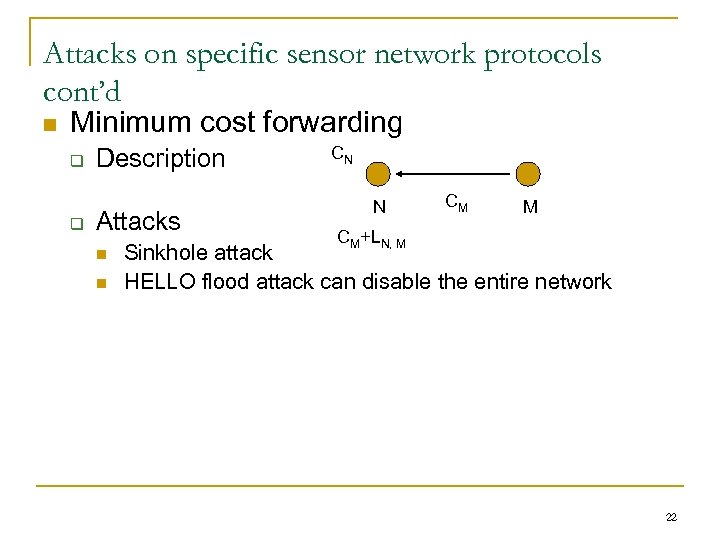 Attacks on specific sensor network protocols cont’d n Minimum cost forwarding q q Description Attacks n n CN N CM M CM+LN, M Sinkhole attack HELLO flood attack can disable the entire network 22
Attacks on specific sensor network protocols cont’d n Minimum cost forwarding q q Description Attacks n n CN N CM M CM+LN, M Sinkhole attack HELLO flood attack can disable the entire network 22
 Attacks on specific sensor network protocols cont’d n LEACH: low-energy adaptive clustering hierarchy q Description n n q Nodes organized into clusters with one node serving as a cluster-head Cluster-heads aggregate data for transmission to a base station Attacks n n HELLO flood attack Countermeasures defeated by a Sybil attack 23
Attacks on specific sensor network protocols cont’d n LEACH: low-energy adaptive clustering hierarchy q Description n n q Nodes organized into clusters with one node serving as a cluster-head Cluster-heads aggregate data for transmission to a base station Attacks n n HELLO flood attack Countermeasures defeated by a Sybil attack 23
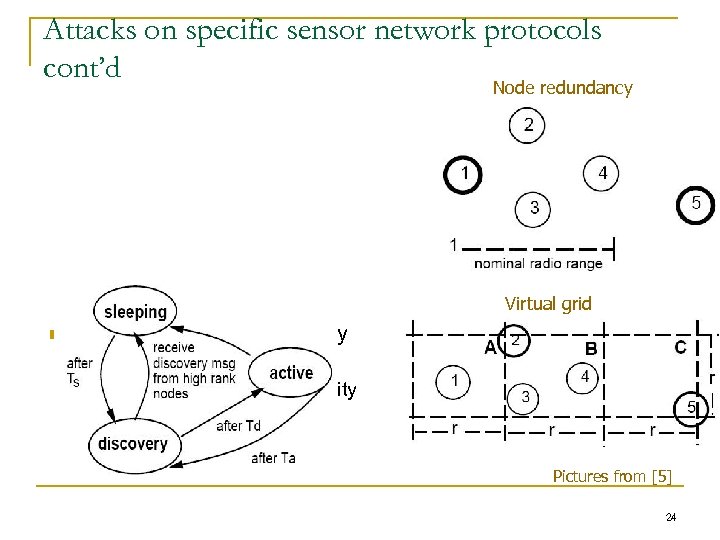 Attacks on specific sensor network protocols cont’d Node redundancy Virtual grid n Energy conserving topology maintenance q Geographic Adaptive Fidelity (GAF) State transitions Pictures from [5] 24
Attacks on specific sensor network protocols cont’d Node redundancy Virtual grid n Energy conserving topology maintenance q Geographic Adaptive Fidelity (GAF) State transitions Pictures from [5] 24
 Countermeasures n Shared key and link layer encryption q q Prevent outsider attacks - Sybil attacks, selective forwarding, ACK spoofing Cannot handle insider attacks - Wormhole, HELLO flood, Tiny. OS beaconing attacks n n In case of a wormhole encryption may make selective forwarding more difficult but cannot prevent blackholes Sybil and HELLO flood attacks q q A globally shared key allows an insider to masquerade as any node A pair of nodes can use a Needham-Schroeder protocol to establish a shared key Limit the number of neighbors for a node Verify the bidirectionality of the link for a HELLO flood attack 25
Countermeasures n Shared key and link layer encryption q q Prevent outsider attacks - Sybil attacks, selective forwarding, ACK spoofing Cannot handle insider attacks - Wormhole, HELLO flood, Tiny. OS beaconing attacks n n In case of a wormhole encryption may make selective forwarding more difficult but cannot prevent blackholes Sybil and HELLO flood attacks q q A globally shared key allows an insider to masquerade as any node A pair of nodes can use a Needham-Schroeder protocol to establish a shared key Limit the number of neighbors for a node Verify the bidirectionality of the link for a HELLO flood attack 25
 Countermeasures n Amended Needham Schroeder Symmetric Key q q Author(s): Roger Needham and Michael Schroeder (1987) Distribution of a shared symmetric key by a trusted server and mutual authentication. Symmetric key cryptography with server. 26
Countermeasures n Amended Needham Schroeder Symmetric Key q q Author(s): Roger Needham and Michael Schroeder (1987) Distribution of a shared symmetric key by a trusted server and mutual authentication. Symmetric key cryptography with server. 26
 Countermeasures n Wormhole and sinkhole attacks q q n Geographic routing attacks q n Protocols that construct a topology initiated by a base station are the most vulnerable Good routing protocol design may be the solution – geographic routing protocols Use fixed topology to eliminate the need for location information Selective forwarding q q q Multipath routing Braided paths Allowing nodes to dynamically choose a packet’s next hop probabilistically from a set of possible candidates 27
Countermeasures n Wormhole and sinkhole attacks q q n Geographic routing attacks q n Protocols that construct a topology initiated by a base station are the most vulnerable Good routing protocol design may be the solution – geographic routing protocols Use fixed topology to eliminate the need for location information Selective forwarding q q q Multipath routing Braided paths Allowing nodes to dynamically choose a packet’s next hop probabilistically from a set of possible candidates 27
![Countermeasures Braided path Picture from [10] 28 Countermeasures Braided path Picture from [10] 28](https://present5.com/presentation/c14a57b54b86b62bc294bb533e47c081/image-28.jpg) Countermeasures Braided path Picture from [10] 28
Countermeasures Braided path Picture from [10] 28
 Countermeasures n Authenticated broadcast and flooding q μTESLA protocol to prevent replay of broadcast messages issued by the base station n q Replay is prevented because messages authenticated with previously disclosed keys are ignored Flood the information about the malicious nodes in the network 29
Countermeasures n Authenticated broadcast and flooding q μTESLA protocol to prevent replay of broadcast messages issued by the base station n q Replay is prevented because messages authenticated with previously disclosed keys are ignored Flood the information about the malicious nodes in the network 29
 Conclusions n n n End-to-end security mechanisms between a sensor node and a base station unlikely to guarantee integrity, authenticity, and confidentiality of messages Link layer security not enough to protect against insider attacks The routing protocol itself must be secure 30
Conclusions n n n End-to-end security mechanisms between a sensor node and a base station unlikely to guarantee integrity, authenticity, and confidentiality of messages Link layer security not enough to protect against insider attacks The routing protocol itself must be secure 30
 Conclusions n n Protection against the replay of data packets should not be a security goal of a routing protocol Sinkhole attacks and wormholes are a significant challenge q q n Wormholes are hard to detect because they use private, out-of-band channel invisible to the underlying network Sinkholes are difficult to defend against because they leverage hard to verify information such as remaining energy Protocols that construct topology initiated by a base station are most vulnerable Geographic routing protocols are resistant Crucial to design routing protocols in which these attacks are meaningless 31
Conclusions n n Protection against the replay of data packets should not be a security goal of a routing protocol Sinkhole attacks and wormholes are a significant challenge q q n Wormholes are hard to detect because they use private, out-of-band channel invisible to the underlying network Sinkholes are difficult to defend against because they leverage hard to verify information such as remaining energy Protocols that construct topology initiated by a base station are most vulnerable Geographic routing protocols are resistant Crucial to design routing protocols in which these attacks are meaningless 31
 Conclusions n Geographic routing relatively secure against wormhole, sinkhole, and Sybil attacks n n n Traffic naturally routed toward the physical location of a base station The main remaining problem is that location information must be trusted Restricting the structure of the topology eliminates the need for nodes to advertise their locations n If nodes are arranged in a grid every node can easily derive its neighbors’ locations 32
Conclusions n Geographic routing relatively secure against wormhole, sinkhole, and Sybil attacks n n n Traffic naturally routed toward the physical location of a base station The main remaining problem is that location information must be trusted Restricting the structure of the topology eliminates the need for nodes to advertise their locations n If nodes are arranged in a grid every node can easily derive its neighbors’ locations 32
 Conclusions n n Clustering protocols like LEACH may yield the most secure solutions against node compromise and insider attacks Virtual base stations can be used to create an overlay network 33
Conclusions n n Clustering protocols like LEACH may yield the most secure solutions against node compromise and insider attacks Virtual base stations can be used to create an overlay network 33
 Future Work n n How the feature of autonomic computing can be applied to WSNs to improve security [11, 12] Self-healing in WSNs [13] 34
Future Work n n How the feature of autonomic computing can be applied to WSNs to improve security [11, 12] Self-healing in WSNs [13] 34
 References 1. 2. 3. 4. 5. 6. 7. J. S. Donath, “Identity and Deception in the Virtual Community”, Communities in Cyberspace, Routledge, 1998. J. R. Douceur, The Sybil attack, in: 1 st International Workshop on Peer-to. Peer Systems (IPTPS 02), 2002. L. Zhou, Z. Haas, Securing ad hoc networks, IEEE Network Magazine 13 (6) (1999) 24– 30. F. Stajano, R. J. Anderson, The resurrecting duckling: security issues for adhoc wireless networks, in: Seventh International Security Protocols Workshop, 1999, pp. 172– 194. Y. Xu, J. Heidemann, D. Estrin, Geography-informed energy conservation for ad hoc routing, in: Proceedings of the Seventh Annual ACM/IEEE International Conference on Mobile Computing and Networking, 2001. C. Intanagonwiwat, R. Govindan, D. Estrin, Directed diffusion: a scalable and robust communication paradigm for sensor networks, in: Proceedings of the Sixth Annual International Conference on Mobile Computing and Networks (Mobi-COM 00), 2000. C. Karlof and D. Wagner, "Secure Routing in Wireless Sensor Networks: Attacks and Countermeasures, " in IEEE SPNA, 2002 35
References 1. 2. 3. 4. 5. 6. 7. J. S. Donath, “Identity and Deception in the Virtual Community”, Communities in Cyberspace, Routledge, 1998. J. R. Douceur, The Sybil attack, in: 1 st International Workshop on Peer-to. Peer Systems (IPTPS 02), 2002. L. Zhou, Z. Haas, Securing ad hoc networks, IEEE Network Magazine 13 (6) (1999) 24– 30. F. Stajano, R. J. Anderson, The resurrecting duckling: security issues for adhoc wireless networks, in: Seventh International Security Protocols Workshop, 1999, pp. 172– 194. Y. Xu, J. Heidemann, D. Estrin, Geography-informed energy conservation for ad hoc routing, in: Proceedings of the Seventh Annual ACM/IEEE International Conference on Mobile Computing and Networking, 2001. C. Intanagonwiwat, R. Govindan, D. Estrin, Directed diffusion: a scalable and robust communication paradigm for sensor networks, in: Proceedings of the Sixth Annual International Conference on Mobile Computing and Networks (Mobi-COM 00), 2000. C. Karlof and D. Wagner, "Secure Routing in Wireless Sensor Networks: Attacks and Countermeasures, " in IEEE SPNA, 2002 35
 References 8. 9. 10. 11. 12. 13. 14. F. Ye, A. Chen, S. Lu, L. Zhang, A scalable solution to minimum cost forwarding in large sensor networks, in: Tenth International Conference on Computer Communications and Networks, 2001, pp. 304– 309. W. R. Heinzelman, A. Chandrakasan, H. Balakrishnan, Energy-efficient communication protocol for wireless microsensor networks, in: 33 rd Annual Hawaii International Conference on System Sciences, 2000, pp. 3005– 3014. Deepak Ganesan, Ramesh Govindan, Scott Shenker, Deborah Estrin, Highlyresilient, energy-efficient multipath routing in wireless sensor networks, in: Proceedings of the 2 nd ACM International Symposium on Mobile Ad Hoc Networking & Computing, 2001, pp. 251 -254. http: //s 3 lab. cs. okstate. edu/projects/CIP-WSN/ http: //www. cse. msu. edu/~mckinley/920/Spring-2006/920 -reading-final. html Tatiana Bokareva, Nirupama Bulusu, Sanjay Jha, SASHA: Toward a Self. Healing Hybrid Sensor Network Architecture. Retrieved from http: //web. cecs. pdx. edu/~nbulusu/papers/emnets. pdf on March 2, 2008. Brad Karp, H. T. Kung, GPSR: Greedy Perimeter Stateless Routing for Wireless. Networks, Retrieved March 4, 2008 from http: //www. eecs. harvard. edu/~htk/publication/2000 -mobi-karp-kung. pdf 36
References 8. 9. 10. 11. 12. 13. 14. F. Ye, A. Chen, S. Lu, L. Zhang, A scalable solution to minimum cost forwarding in large sensor networks, in: Tenth International Conference on Computer Communications and Networks, 2001, pp. 304– 309. W. R. Heinzelman, A. Chandrakasan, H. Balakrishnan, Energy-efficient communication protocol for wireless microsensor networks, in: 33 rd Annual Hawaii International Conference on System Sciences, 2000, pp. 3005– 3014. Deepak Ganesan, Ramesh Govindan, Scott Shenker, Deborah Estrin, Highlyresilient, energy-efficient multipath routing in wireless sensor networks, in: Proceedings of the 2 nd ACM International Symposium on Mobile Ad Hoc Networking & Computing, 2001, pp. 251 -254. http: //s 3 lab. cs. okstate. edu/projects/CIP-WSN/ http: //www. cse. msu. edu/~mckinley/920/Spring-2006/920 -reading-final. html Tatiana Bokareva, Nirupama Bulusu, Sanjay Jha, SASHA: Toward a Self. Healing Hybrid Sensor Network Architecture. Retrieved from http: //web. cecs. pdx. edu/~nbulusu/papers/emnets. pdf on March 2, 2008. Brad Karp, H. T. Kung, GPSR: Greedy Perimeter Stateless Routing for Wireless. Networks, Retrieved March 4, 2008 from http: //www. eecs. harvard. edu/~htk/publication/2000 -mobi-karp-kung. pdf 36


