aa367855b699ffcaed3933821cd3366b.ppt
- Количество слайдов: 19

Secure Proactive Recovery – a Hardware Based Mission Assurance Scheme Ruchika Mehresh 1 Shambhu J. Upadhyaya 1 Kevin Kwiat 2 rmehresh@buffalo. edu shambhu@buffalo. edu kwiatk@rl. af. mil 1 Department of Computer Science and Engineering, State University of New York at Buffalo, NY, USA 2 Air Force Research Laboratory, Rome, NY, USA Research Supported in Part by ITT Grant No. 200821 J and NSF Grant No. DUE-0802062 6 th International Conference on Information Warfare and Security, 2011 1
Outline Structure Motivation Threat model System design Performance analysis Conclusion 2
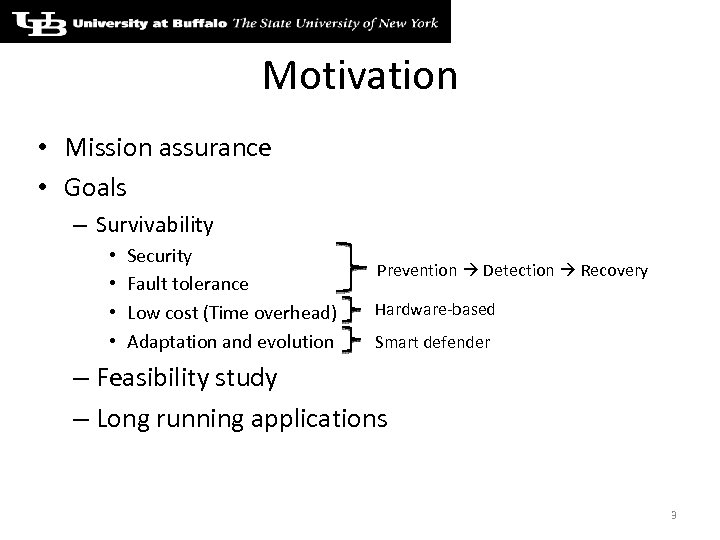
Motivation • Mission assurance • Goals – Survivability • • Security Fault tolerance Low cost (Time overhead) Adaptation and evolution Prevention Detection Recovery Hardware-based Smart defender – Feasibility study – Long running applications 3
Outline Structure Motivation Threat model System design Performance analysis Conclusion 4
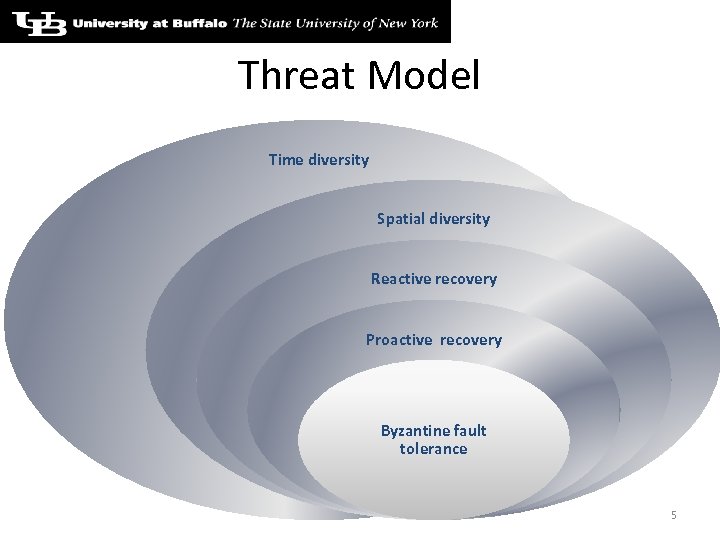
Threat Model Time diversity Spatial diversity Reactive recovery Proactive recovery Byzantine fault tolerance 5

The Quiet Invader • Smart attacker – Make decisions to maximize the potential of achieving their objectives based on dynamic information • Quiet invader – Camouflages to buy more time – Plan to attack mission during critical stage (Why? ) – Example: • Long running countdown for a space shuttle launch that runs for several hours 6
Outline Structure Motivation Threat model System design Performance analysis Conclusion 7
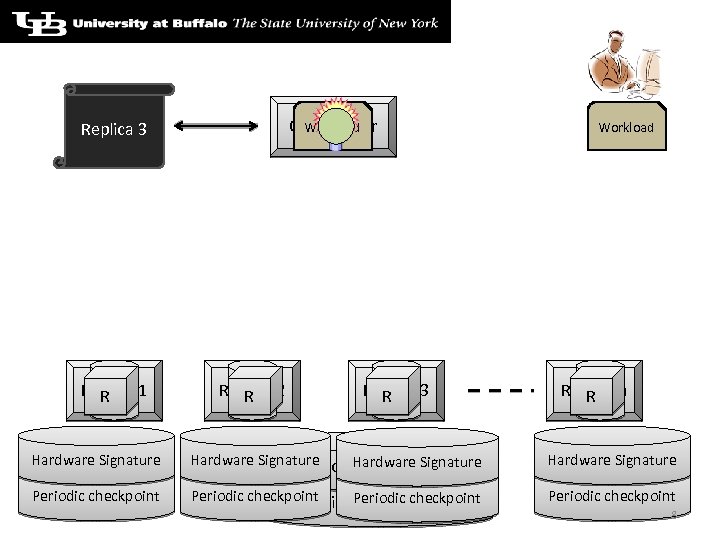
Workload Coordinator Replica 3 C Replica 1 RH C Replica 2 R H C Replica 3 RH Workload C Replica n RH Hardware Signature Hardware Signature Periodic checkpoint Periodic checkpoint 8
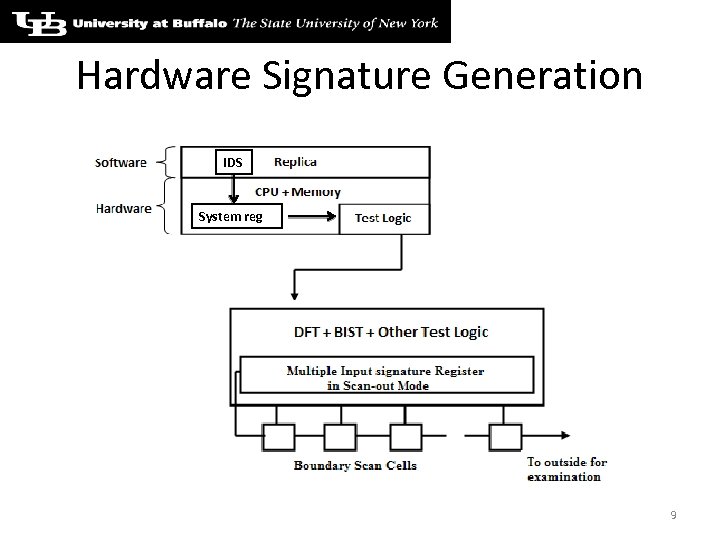
Hardware Signature Generation IDS System reg 9
Outline Structure Motivation Threat model System design Performance analysis Conclusion 10
Performance Analysis • Cases – Case 1: Systems with no checkpointing – Case 2: Systems with checkpointing, no failures/attacks – Case 3: Systems with checkpointing, failures/attacks • Workload – Java Sci. Mark 2. 0 benchmark workloads: FFT, SOR, Sparse, LU • Multi-step simulation based evaluation approach [Reference: Mehresh, R. , Upadhyaya, S. and Kwiat, K. (2010) “A Multi-Step Simulation Approach Toward Fault Tolerant system Evaluation”, Third International Workshop on Dependable Network Computing and Mobile Systems, October] 11
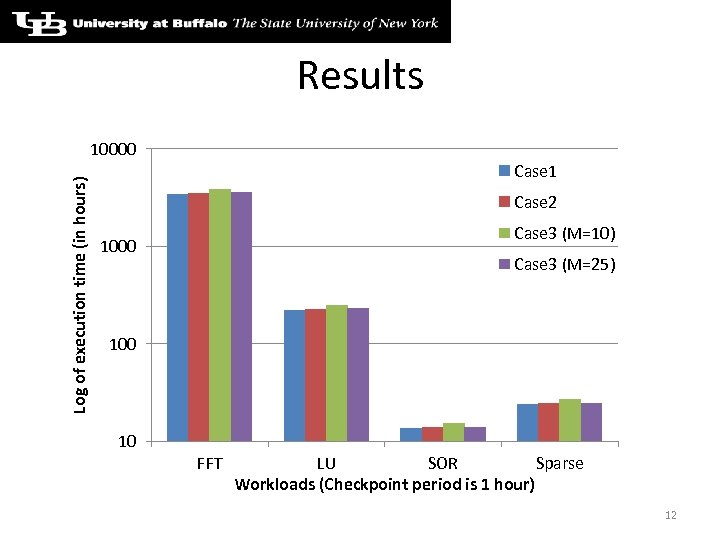
Results Log of execution time (in hours) 10000 Case 1 Case 2 Case 3 (M=10) 1000 Case 3 (M=25) 100 10 FFT LU SOR Sparse Workloads (Checkpoint period is 1 hour) 12
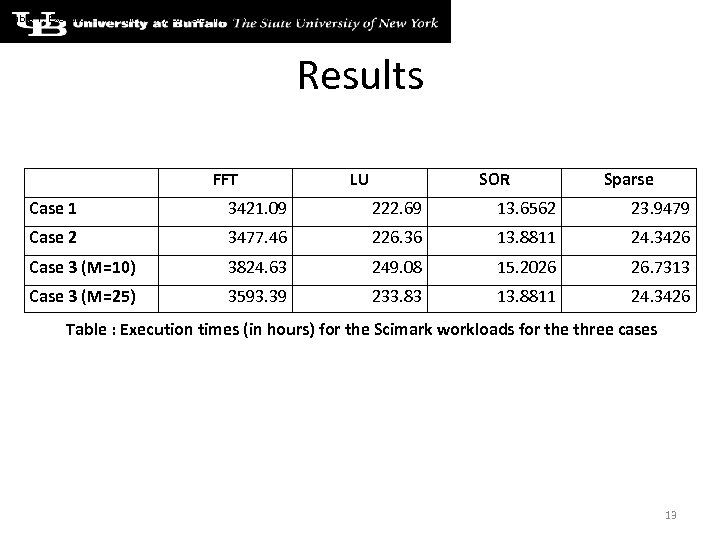
Table 1: Execution Times (in hours) for the Scimark workloads across three cases Results FFT LU SOR Sparse Case 1 3421. 09 222. 69 13. 6562 23. 9479 Case 2 3477. 46 226. 36 13. 8811 24. 3426 Case 3 (M=10) 3824. 63 249. 08 15. 2026 26. 7313 Case 3 (M=25) 3593. 39 233. 83 13. 8811 24. 3426 Table : Execution times (in hours) for the Scimark workloads for the three cases 13
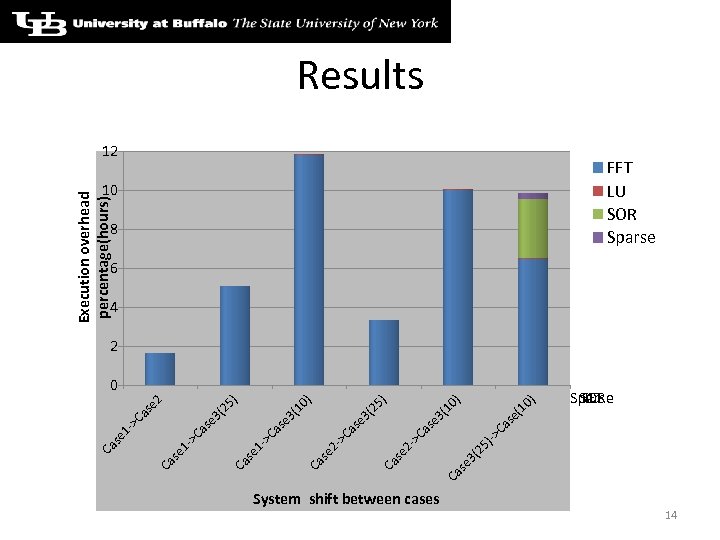
System shift between cases 0) (1 se ) 10 3( se >C a ) 25 3( se >C a 2 se >C a )-> Ca 25 3( se Ca 2 - se Ca 1 - se Ca Execution overhead percentage(hours) Results 12 10 8 FFT LU SOR Sparse 6 4 2 0 Sparse SOR FFT LU 14
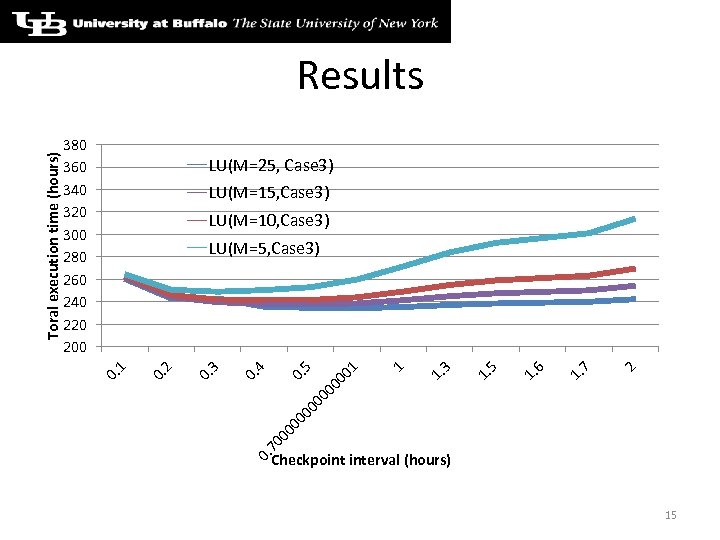
380 360 340 320 300 280 260 240 220 200 LU(M=25, Case 3) LU(M=10, Case 3) 2 1. 7 1. 6 1. 5 1. 3 1 00 1 0. 7 00 00 0. 5 0. 4 0. 3 0. 2 LU(M=5, Case 3) 0. 1 Toral execution time (hours) Results Checkpoint interval (hours) 15
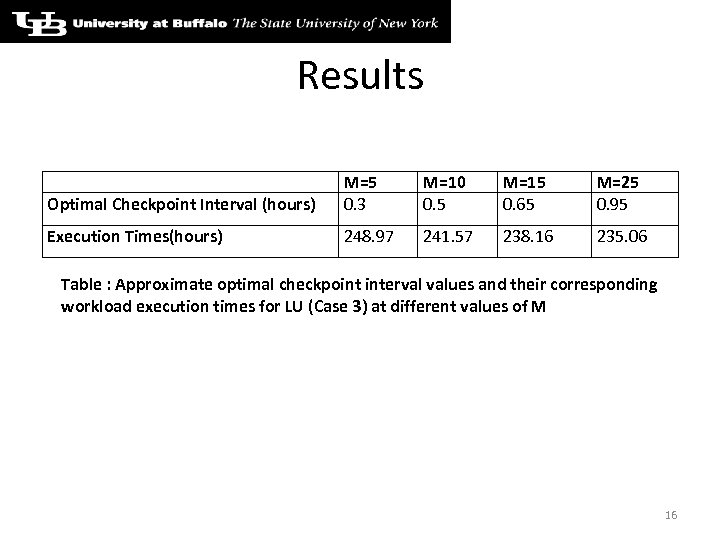
Results Optimal Checkpoint Interval (hours) M=5 0. 3 M=10 0. 5 M=15 0. 65 M=25 0. 95 Execution Times(hours) 248. 97 241. 57 238. 16 235. 06 Table : Approximate optimal checkpoint interval values and their corresponding workload execution times for LU (Case 3) at different values of M 16
Outline Structure Motivation Threat model System design Performance analysis Conclusion 17

Conclusion • • Low cost solution to secure proactive recovery Mission survivability Utilized redundant hardware Small overhead in absence of failures – Effective preventive measure • Future work – To evaluate this scheme for a distributed system 18

Thank You !! 19
aa367855b699ffcaed3933821cd3366b.ppt