3230e019d4e5680d2c3bfd8decdd4168.ppt
- Количество слайдов: 22

SECURE ORIGIN BGP (so. BGP) draft-ng-sobgp-extensions-00 Editor: James Ng (jamng@cisco. com) Session Number Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 1

Goals of so. BGP Verify the origin of advertisements Prevent the advertisement of unauthorized prefixes Sanity check the path of an update Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 2

Design Constraints • Signaling mechanism to provide security information should be as flexible as possible • Must be incrementally deployable • Should provide security benefit without the participation of every AS Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 3
Design Constraints • Should not rely on routing to secure routing (No external database connection on system initialization is required) • Flexibility should be provided to allow operators to configure the level of security vs. overhead and convergence speed • Minimize impact to current optimizations in the implementation of the BGP protocol Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 4

so. BGP Doesn’t Protect • Inter-AS (peer to peer) Connections • BGP Attribute authentication • The full validity of the AS_PATH; while an AS_PATH can be checked for correctness, so. BGP does not verify that the AS_PATH of any given route has not been modified in transit Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 5
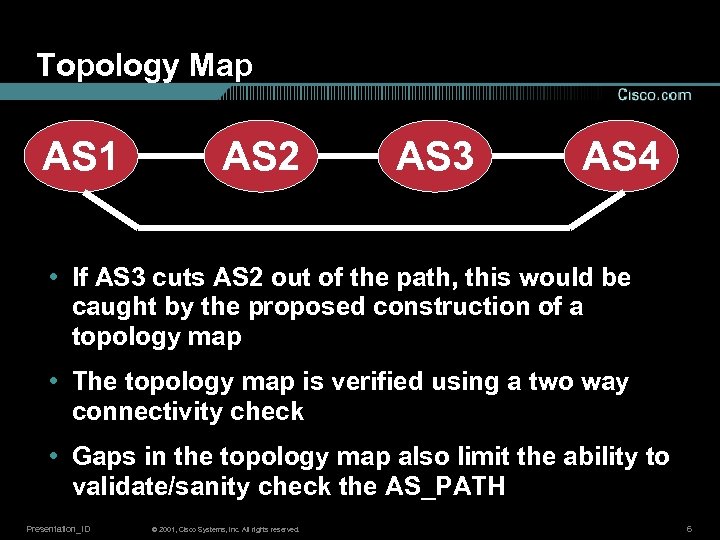
Topology Map AS 1 AS 2 AS 3 AS 4 • If AS 3 cuts AS 2 out of the path, this would be caught by the proposed construction of a topology map • The topology map is verified using a two way connectivity check • Gaps in the topology map also limit the ability to validate/sanity check the AS_PATH Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 6

The Security Message • New BGP message type 7 • Used to carry security information within the protocol (security info can also be transported outside of BGP) • Transmits 3 types of certificates and a request • Negotiated at session startup Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 7

Certificate Types • Entity Certificate (Entitycert) • Policy Certificate (Policycert) • Authorization Certificate (Authcert) Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 8

Entity Certificate Entitycert function Distributes the public keys Used to authenticate other security messages Provides a way to change keys/authentication info without causing routing disruption Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 9

Who Signs the Entity Certificates • Authority which issued the AS number • Commercial authority • Any universally known and trusted party in the Internet domain • Web of trust model • Private keys are never transmitted inside or outside the AS Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 10

Policy Certificate Policycert function Specifies security options Communicates level of security requested by Originating AS (Allows Flexibility) Lists attached AS’ for AS_Path sanity checking Also provides a non-disruptive way to invalidate old security information Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 11

Authentication Certificate Authcert function Used to authorize an AS to advertise a prefix block Information is used to build a database the BGP speaker can use to verify the origin of a prefix Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 12

so. BGP Operation Manually Entered Entity Certificate (Entitycert) Begin with a small set of manually configured Entitycerts for well-known parties Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 13
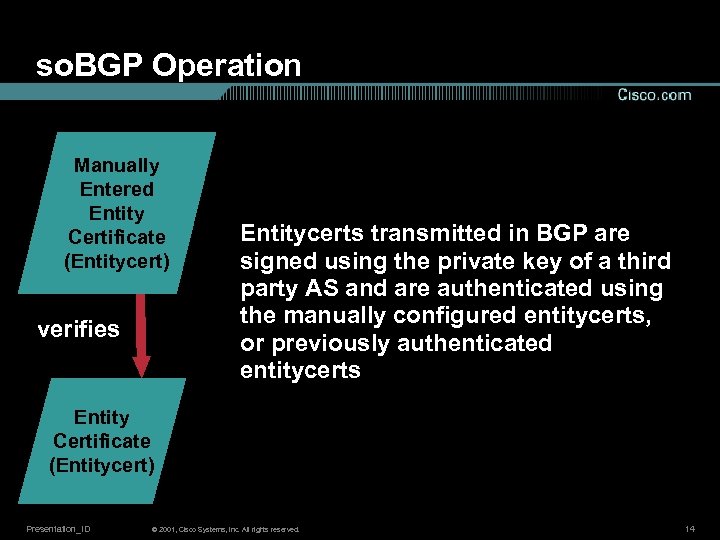
so. BGP Operation Manually Entered Entity Certificate (Entitycert) verifies Entitycerts transmitted in BGP are signed using the private key of a third party AS and are authenticated using the manually configured entitycerts, or previously authenticated entitycerts Entity Certificate (Entitycert) Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 14
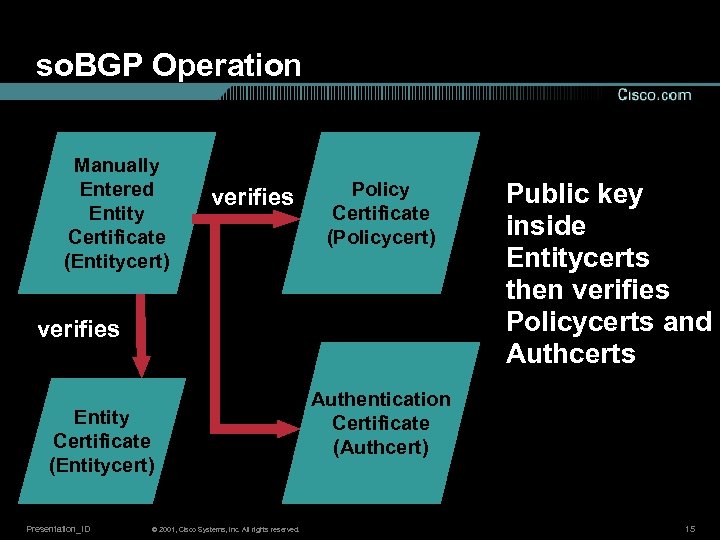
so. BGP Operation Manually Entered Entity Certificate (Entitycert) verifies Policy Certificate (Policycert) verifies Entity Certificate (Entitycert) Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. Public key inside Entitycerts then verifies Policycerts and Authcerts Authentication Certificate (Authcert) 15
so. BGP Operation Authorization Certificate (Authcert) Prefix Block – A, B, C • Authcert contains a list of AS’ authorized to originate an address block • Each prefix is then checked against the Authcert database to verify the correct origin AS Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 16
so. BGP Operation Policy Certificate (Policycert) A attached to (X, Y, Z) • Policycert contains a list of attached AS’ and security policy options • Each AS_PATH can then be sanity checked against the Policycert database • Placing policies in a certificate allows us to expand change policy options in the future Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 17

Certificate Advertisement • Advertisement of certificates is not restricted to the Originating AS • Once an AS generates a certificate, it may be advertised by another AS or third party Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 18

Request • Security messages may be filtered for various reasons • The Request message provides the ability to readvertise all security information or just a subset Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 19

Aggregation • Aggregation is a problem for any mechanism that uses the AS_PATH to authenticate information • The problem can be avoided by restricting AS’ to only aggregate for prefixes that they are authorized to originate Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 20

Next Steps • Modify the WG charter to include BGP Security as a work item. • Wait for requirements document from RPsec. • Possibly form a subgroup to look at BGP security solutions (? ). Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 21

For Further Discussion • ftp: //ftp-eng. cisco. com/sobgp/index. html • Mailing List: • sobgp@external. cisco. com • Send request sobgp-approval@cisco. com Presentation_ID © 2001, Cisco Systems, Inc. All rights reserved. 22
3230e019d4e5680d2c3bfd8decdd4168.ppt